001 this_is_flag

题目内给出来了,大部分flag格式是flag{},比如flag{th1s_!s_a_d4m0_4la9},这个就是flag。
002 pdf

打开附件以后发现是这么个玩意,仔细查找,发现下面没有flag,猜想flag就在图片里,只是看不到,把鼠标放在上面移动一下试试,:


很神奇,也可以==ctrl+A==全选,可以达到一样的效果。
也可以用word打开,把图片移开,也可以看到flag。
003 如来十三掌

打开附件以后,可以看到以下内容:
夜哆悉諳多苦奢陀奢諦冥神哆盧穆皤三侄三即諸諳即冥迦冥隸數顛耶迦奢若吉怯陀諳怖奢智侄諸若奢數菩奢集遠俱老竟寫明奢若梵等盧皤豆蒙密離怯婆皤礙他哆提哆多缽以南哆心曰姪罰蒙呐神。舍切真怯勝呐得俱沙罰娑是怯遠得呐數罰輸哆遠薩得槃漫夢盧皤亦醯呐娑皤瑟輸諳尼摩罰薩冥大倒參夢侄阿心罰等奢大度地冥殿皤沙蘇輸奢恐豆侄得罰提哆伽諳沙楞缽三死怯摩大蘇者數一遮
这一看就不是人可以看懂的内容,应该是某种加密,打开与佛论禅,按照==普渡众生==里的使用方法试试:

揭秘以后得到上面这个:
MzkuM3gvMUAwnzuvn3cgozMlMTuvqzAenJchMUAeqzWenzEmLJW9
看下题目如来十三掌应该是有提示吧(没想出来,最后看wp的,嘿嘿)然后用==rot13替换加密算法==解密一下:

下面这个解密以后的内容用==base64==解密一下就得到了flag。

flag{bdscjhbkzmnfrdhbvckijndskvbkjdsab}PS:不要用工具站的rot13加解密,会不分大小写.
004 give_you_flag

打开附件发现是一个GIF文件,看完以后发现最后有一下,出现了一个二维码,打开stegsolve使用Frame Browser挨个查看帧,找到了这个二维码

但是这个二维码少了定位符,用ps补上就可以了。

在线二维码识别一下

得到flag{e7d478cf6b915f50ab1277f78502a2c5}
005 stegano

打开附件,

好吧,脑子懵逼了一秒,它背景都说了,flag不在里面,就不看了,猜想可能没显示出来,ctrl+A全选复制到记事本里去
发现了一串神奇的字符BABA BBB BA BBA ABA AB B AAB ABAA AB B AA BBB BA AAA BBAABB AABA ABAA AB BBA BBBAAA ABBBB BA AAAB ABBBB AAAAA ABBBB BAAA ABAA AAABB BB AAABB AAAAA AAAAA AAAAB BBA AAABB只有A和B,莫非是。。。
str = "BABA BBB BA BBA ABA AB B AAB ABAA AB B AA BBB BA AAA BBAABB AABA ABAA AB BBA BBBAAA ABBBB BA AAAB ABBBB AAAAA ABBBB BAAA ABAA AAABB BB AAABB AAAAA AAAAA AAAAB BBA AAABB";
str1 = str.replace("A", "."); str2 = str1.replace("B", "-");
print(str2)运行完脚本以后得到
-.-. --- -. --. .-. .- - ..- .-.. .- - .. --- -. ... --..-- ..-. .-.. .- --. ---... .---- -. ...- .---- ..... .---- -... .-.. ...-- -- ...-- ..... ..... ....- --. ...--
再丢到摩斯电码里:

不能直接提交,要改为指定格式:
==flag{1nv151bl3m3554g3}==
nice!!!!
006 坚持60s

打开附件,发现是一个游戏。

玩一下试试,祭了,还是作弊吧。
解法一:jd-gui

==flag{RGFqaURhbGlfSmlud2FuQ2hpamk=}==
把flag输入发现不对,仔细观察,发现flag里面是一个base64编码,解码一下就得到:
==flag{DajiDali_JinwanChiji}==
大吉大利,今晚吃鸡!
解法二:修改大小
将.jar文件改为.rar文件,修改掉里面的图片,改成一个小点,到60s出来送死,很容易就能通关。
或者用winhex挨个打开,也能发现上面的flag。
解法三:躲藏
开局躲到最右边只露出来一点点,程序判定必须得有一定重合才算失败,所以在最右边就不死了。60多秒出来就行了。

007 gif

打开附件,发现是一个压缩包,解压一下,可以看到很多黑白块

一共104块,联想到二进制。
按照黑1白0可以得到01100110011011000110000101100111011110110100011001110101010011100101111101100111011010010100011001111101
输入到二进制转换器里可以发现:

本题也可以采用脚本进行解题。
根据==Hel1antHu5==师傅的wp,脚本如下:
from PIL import Image
result = ""
for num, i in enumerate(range(104)):
img = Image.open(f"{i}.jpg")
im = img.convert("RGB")
r,g,b = im.getpixel((1,1))
if r != 255:
result += "1"
else:
result += "0"
for i in range(0, len(result),8):
byte = result[i:i+8]
print(chr(int(byte, 2)), end="")运行即可得flag。
008 掀桌子

啥附件都没有,只给了这么个字符串。
c8e9aca0c6f2e5f3e8c4efe7a1a0d4e8e5a0e6ece1e7a0e9f3baa0e8eafae3f9e4eafae2eae4e3eaebfaebe3f5e7e9f3e4e3e8eaf9eaf3e2e4e6f2
最大不超过f,猜测是16进制,两个一组进行16进制转10进制,发现数字太大超过128,减低128就可以了。
xctf-wp里面给出的脚本是这样子的:
string = "c8e9aca0c6f2e5f3e8c4efe7a1a0d4e8e5a0e6ece1e7a0e9f3baa0e8eafae3f9e4eafae2eae4e3eaebfaebe3f5e7e9f3e4e3e8eaf9eaf3e2e4e6f2"
flag = ''
for i in range(0,len(string), 2):
s = "0x" + string[i] + string[i+1]
flag += chr(int(s, 16) - 128)
print(flag)渣渣禹师傅给出的脚本是这样的:
import re
a = 'c8e9aca0c6f2e5f3e8c4efe7a1a0d4e8e5a0e6ece1e7a0e9f3baa0e8eafae3f9e4eafae2eae4e3eaebfaebe3f5e7e9f3e4e3e8eaf9eaf3e2e4e6f2'
b = re.findall(r'.{2}',a)
flag = ""
for i in b:
flag += chr(int(int(i,16)-128))
print(flag)师傅用的是正则,也能得到最后的flag
Hi, FreshDog! The flag is: hjzcydjzbjdcjkzkcugisdchjyjsbdfr
009 ext3

下载附件显示是这样一个文件

题目都说了是一个linux系统光盘,打开kali挂载一下,运行下列命令即可得到最终的flag。
┌──(kali㉿kali)-[~/Desktop]
└─$ ls
-~ f1fc23f5c743425d9e0073887c846d23
┌──(kali㉿kali)-[~/Desktop]
└─$ mount f1fc23f5c743425d9e0073887c846d23 /mnt/
mount: /mnt/: mount failed: Operation not permitted.
┌──(kali㉿kali)-[~/Desktop]
└─$ sudo su
[sudo] password for kali:
┌──(root💀kali)-[/home/kali/Desktop]
└─# mount f1fc23f5c743425d9e0073887c846d23 /mnt/
┌──(root💀kali)-[/home/kali/Desktop]
└─# cd /mnt
┌──(root💀kali)-[/mnt]
└─# cat flag.txt
cat: flag.txt: No such file or directory
┌──(root💀kali)-[/mnt]
└─# find ./ -name flag.txt
./O7avZhikgKgbF/flag.txt
┌──(root💀kali)-[/mnt]
└─# cat ./O7avZhikgKgbF/flag.txt
ZmxhZ3tzYWpiY2lienNrampjbmJoc2J2Y2pianN6Y3N6Ymt6an0=
┌──(root💀kali)-[/mnt]
└─# echo "ZmxhZ3tzYWpiY2lienNrampjbmJoc2J2Y2pianN6Y3N6Ymt6an0=" | base64 --decode
flag{sajbcibzskjjcnbhsbvcjbjszcszbkzj} 
最后的查找命令用
find | grep 'flag'也可以关于linux下的查找命令可以看下民宿师傅的博客。
==kali下的base64编解码==
base64 [选项] [输入文件] [输出文件]
选项:
-e 或 –encode
-d 或 –decode
-n 或 –noerrcheck
-u 或 -help
-i, --ignore-garbage
010 SimpleRAR

附件是一个.rar的压缩包,用winrar解压缩一下可以看到一个名为flag.txt的文件,然而。。。。


再看一遍题目,可以知道,这个rar文件里面肯定藏了点东西,而且这个secret.png头文件损坏,首先要了解一下块开头的基本格式:

可以看到文件块是A8 3C 74 而不是A8 3C 7A 修改一下即可。保存,重新解压缩,发现多了一个secret.png的文件,正常打开看不到东西,查看一下文件头。
==常见文件头==
文件 文件头 JPEG (jpg) FFD8FF PNG (png) 89504E47 GIF (gif) 47494638 TIFF (tif) 49492A00 Windows Bitmap (bmp) 424D CAD (dwg) 41433130 Adobe Photoshop (psd) 38425053 Rich Text Format (rtf) 7B5C727466 XML (xml) 3C3F786D6C HTML (html) 68746D6C3E Email [thorough only] (eml) 44656C69766572792D646174653A Outlook Express (dbx) CFAD12FEC5FD746F Outlook (pst) 2142444E MS Word/Excel (xls.or.doc) D0CF11E0 MS Access (mdb) 5374616E64617264204A WordPerfect (wpd) FF575043 Postscript (eps.or.ps) 252150532D41646F6265 Adobe Acrobat (pdf) 255044462D312E Quicken (qdf) AC9EBD8F Windows Password (pwl) E3828596 ZIP Archive (zip) 504B0304 RAR Archive (rar) 52617221 Wave (wav) 57415645 AVI (avi) 41564920 Real Audio (ram) 2E7261FD Real Media (rm) 2E524D46 MPEG (mpg) 000001BA MPEG (mpg) 000001B3 Quicktime (mov) 6D6F6F76 Windows Media (asf) 3026B2758E66CF11 MIDI (mid) 4D546864
winhex里的secret.png文件头却写的是GIF,所以该文件其实是一个gif文件,修改拓展名。

根据题目上说的,这个题目里的图片是个双图层,用PS打开分别保存,再用stegsolve进行查看,得到下面这个残缺的二维码。

将两个图片保存,用PS合并并补全定界符,用在线二维码识别扫一下即可出来最后的flag。

011 base64stego

打开附件,是一个.zip文件,准备解压,但是解压需要密码。

啊这,用winhex打开看一下,发现这是一个zip伪加密
ZIP是一种相当简单的分别压缩每个文件的存档格式。分别压缩文件允许不必读取另外的数据而检索独立的文件;理论上,这种格式允许对不同的文件使用不同的算法。不管用何种方法,对这种格式的一个告诫是对于包含很多小文件的时候,存档会明显的比压缩成一个独立的文件(在类Unix系统中一个经典的例子是普通的tar.gz存档是由一个使用gzip压缩的TAR存档组成)要大。
ZIP支持基于对称加密系统的一个简单的密码,现在已知有严重的缺陷,已知明文攻击,字典攻击和暴力攻击。ZIP也支持分卷压缩。在近来一段时间,ZIP加入了包括新的压缩和加密方法的新特征,不过这些新特征并没有被许多工具所支持并且没有得到广泛应用。
ZIP文件是一种压缩文件,可进行加密,也可不加密。而伪加密是在未加密的zip文件基础上修改了它的压缩源文件目录区里的全局方式位标记的比特值,使得压缩软件打开它的时候识别为加密文件,提示输入密码, 而在这个时候,不管你用什么软件对其进行密码破解,都无法打开它!这就是它存在的意义!
==zip伪加密破解方法==
-
使用ZipCenOp.jar(需要java环境),在cmd中使用 java -jar ZipCenOp.jar r xxx.zip 成功后压缩包可以直接打开
-
使用winRAR
-
进入工具,压缩修复文件,修复完后压缩包就可以打开了
-
上述两种方法很多情况都可以用,但是有时不行,第三种方法可以应对各种zip伪加密
- 修改文件头的加密标志位(见下方)
==压缩源文件数据区:==
4B 03 04:这是头文件标记(0x04034b50)
00:解压文件所需 pkware 版本
00:全局方式位标记(有无加密)
00:压缩方式
5A 7E:最后修改文件时间
F7 46:最后修改文件日期
B5 80 14:CRC-32校验(1480B516)
00 00 00:压缩后尺寸(25)
00 00 00:未压缩尺寸(23)
00:文件名长度
00:扩展记录长度 6B65792E7478740BCECC750E71ABCE48CDC9C95728CECC2DC849AD284DAD0500
==压缩源文件目录区:==4B 01 02:目录中文件文件头标记(0x02014b50)
3F 00:压缩使用的 pkware 版本
14 00:解压文件所需 pkware 版本
00 00:全局方式位标记(有无加密,这个更改这里进行伪加密,改为09 00打开就会提示有密码了)
00:压缩方式
5A 7E:最后修改文件时间
F7 46:最后修改文件日期
B5 80 14:CRC-32校验(1480B516)
00 00 00:压缩后尺寸(25)
00 00 00:未压缩尺寸(23)
00:文件名长度00:扩展字段长度
00:文件注释长度
00:磁盘开始号
00:内部文件属性
00 00 00:外部文件属性 00 00 00:局部头部偏移量
==压缩源文件目录结束标志:==4B 05 06:目录结束标记
00:当前磁盘编号
00:目录区开始磁盘编号
00:本磁盘上纪录总数
00:目录区中纪录总数
00 00 00:目录区尺寸大小
3E 00 00 00:目录区对第一张磁盘的偏移量
00:ZIP 文件注释长度
解法一:手动改进
搜索504B,点击第二个504B(压缩源文件目录区),这里使用的是010 Editor,修改以后:

解法二:ZipCenOp
┌──(kali㉿kali)-[~/zipcenop]
└─$ java -jar ZipCenOp.jar r 1.zip
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
WARNING: An illegal reflective access operation has occurred
WARNING: Illegal reflective access by zip.CenOp$1 (rsrc:./) to method java.nio.DirectByteBuffer.cleaner()
WARNING: Please consider reporting this to the maintainers of zip.CenOp$1
WARNING: Use --illegal-access=warn to enable warnings of further illegal reflective access operations
WARNING: All illegal access operations will be denied in a future release
Exception in thread "main" java.lang.reflect.InvocationTargetException
at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke0(Native Method)
at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke(NativeMethodAccessorImpl.java:62)
at java.base/jdk.internal.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43)
at java.base/java.lang.reflect.Method.invoke(Method.java:566)
at org.eclipse.jdt.internal.jarinjarloader.JarRsrcLoader.main(JarRsrcLoader.java:58)
Caused by: java.lang.NoClassDefFoundError: sun/misc/Cleaner
at zip.CenOp$1.run(CenOp.java:95)
at java.base/java.security.AccessController.doPrivileged(Native Method)
at zip.CenOp.clean(CenOp.java:89)
at zip.CenOp.operate(CenOp.java:80)
at zip.CenOp.main(CenOp.java:32)
... 5 more
Caused by: java.lang.ClassNotFoundException: sun.misc.Cleaner
at java.base/java.net.URLClassLoader.findClass(URLClassLoader.java:476)
at java.base/java.lang.ClassLoader.loadClass(ClassLoader.java:589)
at java.base/java.lang.ClassLoader.loadClass(ClassLoader.java:522)
... 10 more保存,再次打开.zip文件,顺利解压,得到下列字符串:
解密完的文本(1.txt)
U3RlZ2Fub2dyYXBoeSBpcyB0aGUgYXJ0IGFuZCBzY2llbmNlIG9m
IHdyaXRpbmcgaGlkZGVuIG1lc3NhZ2VzIGluIHN1Y2ggYSB3YXkgdGhhdCBubyBvbmV=
LCBhcGFydCBmcm9tIHRoZSBzZW5kZXIgYW5kIGludGVuZGVkIHJlY2lwaWVudCwgc3VzcGU=
Y3RzIHRoZSBleGlzdGVuY2Ugb2YgdGhlIG1lc3M=
YWdlLCBhIGZvcm0gb2Ygc2VjdXJpdHkgdGhyb3VnaCBvYnNjdXJpdHkuIFS=
aGUgd29yZCBzdGVnYW5vZ3JhcGh5IGlzIG9mIEdyZWVrIG9yaWdpbiBhbmQgbWVhbnMgImNvbmNlYW==
bGVkIHdyaXRpbmciIGZyb20gdGhlIEdyZWVrIHdvcmRzIHN0ZWdhbm9zIG1lYW5pbmcgImNv
dmVyZWQgb3IgcHJvdGVjdGVkIiwgYW5kIGdyYXBoZWluIG1lYW5pbmcgInRvIHc=
cml0ZSIuIFRoZSBmaXJzdCByZWNvcmRlZCB1c2Ugb2YgdGhlIHRlcm0gd2FzIGluIDE0OTkgYnkgSm9o
YW5uZXMgVHJpdGhlbWl1cyBpbiBoaXMgU3RlZ2Fub2dyYXBoaWEsIGEgdHJlYV==
dGlzZSBvbiBjcnlwdG9ncmFwaHkgYW5kIHN0ZWdhbm9ncmFwaHkgZGlzZ8==
dWlzZWQgYXMgYSBib29rIG9uIG1hZ2ljLiBHZW5lcmFsbHksIG1lc3P=
YWdlcyB3aWxsIGFwcGVhciB0byBiZSBzb21ldGhpbmcgZWxzZTogaW1hZ2VzLCBhcnRp
Y2xlcywgc2hvcHBpbmcgbGlzdHMsIG9yIHNvbWUgb3R=
aGVyIGNvdmVydGV4dCBhbmQsIGNsYXNzaWNhbGx5LCB0aGUgaGlkZGVuIG1lc3NhZ2UgbWF5IGJlIGluIGludmm=
c2libGUgaW5rIGJldHdlZW4gdGhlIHZpc2libGUgbGluZXMgb2YgYSBwcml2YXRlIGxldHRlci4NCg0KVGhl
IGFkdmFudGFnZSBvZiBzdGVnYW5vZ3JhcGh5LCBvdmVyIGNy
eXB0b2dyYXBoeSBhbG9uZSwgaXMgdGhhdCBtZXNzYWdlcyBkbyBub3QgYXR0cmFjdCBhdHRlbnRpb25=
IHRvIHRoZW1zZWx2ZXMuIFBsYWlubHkgdmlzaWJsZSBlbmNyeXB0ZWQgbWVzc2FnZXOXbm8gbWF0dGVyIF==
aG93IHVuYnJlYWthYmxll3dpbGwgYXJvdXNlIHN=
dXNwaWNpb24sIGFuZCBtYXkgaW4gdGhlbXNlbHZlcyBiZSBpbmNyaW1pbmF0aW5nIP==
aW4gY291bnRyaWVzIHdoZXJlIGVuY3J5cHRpb24gaXMgaWxsZWdhbC4gVGhlcmVmb3JlLH==
IHdoZXJlYXMgY3J5cHRvZ3JhcGh5IHByb3RlY3RzIHRoZSBjb250ZW50cyBvZj==
IGEgbWVzc2FnZSwgc3RlZ2Fub2dyYXBoeSBjYW4gYmUgc2FpZCB0byBwcm90ZWN0IGJ=
b3RoIG1lc3NhZ2VzIGFuZCBjb21tdW5pY2F0aW5nIHBhcnRpZXMuDQoNClN0ZWdhbm9ncmFwaHkgaW5jbHW=
ZGVzIHRoZSBjb25jZWFsbWVudCBvZiBpbmZvcm1hdGlvbiB3aXRoaW4gY29t
cHV0ZXIgZmlsZXMuIEluIGRpZ2l0YWwgc3RlZ2Fub2dyYXBoeSwgZWxlY3Ryb25pYyBjb21tdW5pY2F0aW9u
cyBtYXkgaW5jbHVkZSBzdGVnYW5vZ3JhcGhpYyBjb2RpbmcgaW5zaZ==
ZGUgb2YgYSB0cmFuc3BvcnQgbGF5ZXIsIHN1Y2ggYXMgYSBkb2N1bWVudCBmaWxlLCBpbWFnZSBmaWx=
ZSwgcHJvZ3JhbSBvciBwcm90b2NvbC4gTWVkaWEg
ZmlsZXMgYXJlIGlkZWFsIGZvciBzdGVnYW5vZ3JhcGhpYyB0cmFuc21pc3Npb+==
biBiZWNhdXNlIG9mIHRoZWlyIGxhcmdlIHNpemUuIEFzIB==
YSBzaW1wbGUgZXhhbXBsZSwgYSBzZW5kZXIgbWlnaHQgc3RhcnQgd2l0aCBh
biBpbm5vY3VvdXMgaW1hZ2UgZmlsZSBhbmQgYWRqdXN0IHRoZSBjb2xvciBvZiBldmVyeSAxMDB0aCBwaXhlbCD=
dG8gY29ycmVzcG9uZCB0byBhIGxldHRlciBpbiB0aGUgYWxwaGFiZXQsIGF=
IGNoYW5nZSBzbyBzdWJ0bGUgdGhhdCBzb21lb25lIG5vdCBzcGVjaWZpY2FsbHkgbG9va2luZyBm
b3IgaXQgaXMgdW5saWtlbHkgdG8gbm90aWNlIGl0Lg0KDQpUaGU=
IGZpcnN0IHJlY29yZGVkIHVzZXMgb2Ygc3RlZ2Fub2dyYXBoeSBjYW4gYmUgdHJ=
YWNlZCBiYWNrIHRvIDQ0MCBCQyB3aGVuIEhlcm9kb3R1cyBtZW50aW9ucyB0d28gZXhhbXBsZXMgb+==
ZiBzdGVnYW5vZ3JhcGh5IGluIFRoZSBIaXN0b3JpZXMgb2Yg
SGVyb2RvdHVzLiBEZW1hcmF0dXMgc2VudCBhIHdhcm5pbmcgYWJvdXQgYSB=
Zm9ydGhjb21pbmcgYXR0YWNrIHRvIEdyZWVjZSBieSB3
cml0aW5nIGl0IGRpcmVjdGx5IG9uIHRoZSB3b29kZW4gYmFja2luZyBvZiBhIHdheCB0YWJsZXQgYmVm
b3JlIGFwcGx5aW5nIGl0cyBiZWVzd2F4IHN1cmZhY2UuIFdheCB0YWJsZXRzIHdlcmUgaW4gY29tbW9uIHVzZV==
IHRoZW4gYXMgcmV1c2FibGUgd3JpdGluZyBzdXJmYWNlcywgc29tZXRpbWX=
cyB1c2VkIGZvciBzaG9ydGhhbmQuIEFub3RoZXIgYW5jaWVudCBleGFtcGxlIGlzIHRoYXQgb9==
ZiBIaXN0aWFldXMsIHdobyBzaGF2ZWQgdGhlIGhlYWQgb2YgaGlzIG1vc3QgdHJ1c3RlZCBz
bGF2ZSBhbmQgdGF0dG9vZWQgYSBtZXNzYWdlIG9uIGl0LiBBZnRlciBoaXMgaGFpciBoYWQgZ5==
cm93biB0aGUgbWVzc2FnZSB3YXMgaGlkZGVuLiBUaGUgcHVycG9zZSB3YXMgdG+=
IGluc3RpZ2F0ZSBhIHJldm9sdCBhZ2FpbnN0IHRoZSBQZXJzaWFucy4NCg0KU3RlZ2Fub2dyYXBoeSBoYXMgYm==
ZWVuIHdpZGVseSB1c2VkLCBpbmNsdWRpbmcgaW4gcmVjZW50IGhpc3RvcmljYWwgdGltZXMgYW5kIHT=
aGUgcHJlc2VudCBkYXkuIFBvc3NpYmxlIHBlcm11dGF0aW9ucyBhcmUgZW5kbGVzcyBhbmT=
IGtub3duIGV4YW1wbGVzIGluY2x1ZGU6DQoqIEhpZGRlbiBtZXNzYWdlcyB3aXRoaW4gd2F4IHRh
YmxldHM6IGluIGFuY2llbnQgR3JlZWNlLCBwZW9wbGUgd3JvdGUgbWV=
c3NhZ2VzIG9uIHRoZSB3b29kLCB0aGVuIGNvdmVyZWQgaXQgd2l0aCB3YXggdXBvbiB3aGljaCBhbiBpbm5vY2Vu
dCBjb3ZlcmluZyBtZXNzYWdlIHdhcyB3cml0dGVu
Lg0KKiBIaWRkZW4gbWVzc2FnZXMgb24gbWVzc2VuZ2VyJ3MgYm9keTogYWxzbyB1c2VkIGluIGFuY2llbt==
dCBHcmVlY2UuIEhlcm9kb3R1cyB0ZWxscyB0aGUgc3Rvcnkgb1==
ZiBhIG1lc3NhZ2UgdGF0dG9vZWQgb24gYSBzbGF2ZSdzIHNoYXZlZCBoZWFkLCBoaWRkZW4gYnkgdGhl
IGdyb3d0aCBvZiBoaXMgaGFpciwgYW5kIGV4cG9zZWQgYnkgc2hhdmluZyBoaXMgaGVhZM==
IGFnYWluLiBUaGUgbWVzc2FnZSBhbGxlZ2VkbHkgY2FycmllZCBhIHdhcm5pbmcgdG8gR3JlZWNlIGFib5==
dXQgUGVyc2lhbiBpbnZhc2lvbiBwbGFucy4gVGh=
aXMgbWV0aG9kIGhhcyBvYnZpb3VzIGRyYXdiYWNrcyz=
IHN1Y2ggYXMgZGVsYXllZCB0cmFuc21pc3Npb24gd2hpbGUgd2FpdGluZyBmb3IgdGhlIHP=
bGF2ZSdzIGhhaXIgdG8gZ3JvdywgYW5kIHRoZSByZXN0cmljdGlvbnMgb3==
biB0aGUgbnVtYmVyIGFuZCBzaXplIG9mIG1lc3M=
YWdlcyB0aGF0IGNhbiBiZSBlbmNvZGVkIG9uIG9uZSBwZXJzb24=
J3Mgc2NhbHAuDQoqIEluIFdXSUksIHRoZSBGcmVuY2ggUmVzaXN0YW5jZSBzZW50IHNvbWUgbWVzc2FnZXMgd2==
cml0dGVuIG9uIHRoZSBiYWNrcyBvZiBjb3VyaWVycyD=
dXNpbmcgaW52aXNpYmxlIGluay4NCiogSGlkZGVuIG1lc3NhZ2VzIG9uIHBhcGVyIHdy
aXR0ZW4gaW4gc2VjcmV0IGlua3MsIHVuZGVyIG90aGVyIG1lc3NhZ2Vz
IG9yIG9uIHRoZSBibGFuayBwYXJ0cyBvZiBvdGhlct==
IG1lc3NhZ2VzLg0KKiBNZXNzYWdlcyB3cml0dGVuIGluIE1vcnNlIGNvZGUgb24ga25pdHRpbmcgeWFybiBhbmQg
dGhlbiBrbml0dGVkIGludG8gYSBwaWVjZSBvZiBjbG90aGluZyB3b3K=
biBieSBhIGNvdXJpZXIuDQoqIE1lc3NhZ2VzIHdyaXR0ZW4gb24gdGhlIGJhY2sgb5==
ZiBwb3N0YWdlIHN0YW1wcy4NCiogRHVyaW5nIGFuZCBhZnRlcm==
IFdvcmxkIFdhciBJSSwgZXNwaW9uYWdlIGFnZW50cyB1c2VkIHBob3RvZ3JhcGhpY2FsbHkgcO==
cm9kdWNlZCBtaWNyb2RvdHMgdG8gc2VuZCBpbmZvcm1hdGlvbiBiYWNrIGFuZH==
IGZvcnRoLiBNaWNyb2RvdHMgd2VyZSB0eXBpY2FsbHkg
bWludXRlLCBhcHByb3hpbWF0ZWx5IGxlc3MgdGhhbiB0aGUgc2l6ZSBvZiB0aGUgcGVyaW9kIHByb2R=
dWNlZCBieSBhIHR5cGV3cml0ZXIuIFdXSUkgbWljcm9kb3RzIG5lZWRlZCB0byBiZSBlbWJlZGRlZB==
IGluIHRoZSBwYXBlciBhbmQgY292ZXJlZCB3aXRoIGFuIGFkaGVzaXZlIChzdWNoIGFzIGNvbGxvZGlvbikuIFR=
aGlzIHdhcyByZWZsZWN0aXZlIGFuZCB0aHVzIGRldGVjdGFibGUg
Ynkgdmlld2luZyBhZ2FpbnN0IGdsYW5jaW5nIGxpZ2h0LiBBbHRlcm5hdGl2ZSB0ZWNobmlxdWVzIGluY2x1ZGVk
IGluc2VydGluZyBtaWNyb2RvdHMgaW50byBzbGl0cyBjdXQgaW50byB0aGUgZWRnZSBvZv==
IHBvc3QgY2FyZHMuDQoqIER1cmluZyBXb3JsZCBXYXIgSUksIGEgc3B5IGZvciB=
SmFwYW4gaW4gTmV3IFlvcmsgQ2l0eSwgVmVsdmFsZWW=
IERpY2tpbnNvbiwgc2VudCBpbmZvcm1hdGlvbiB0byBhY2NvbW1vZGF0aW9=
biBhZGRyZXNzZXMgaW4gbmV1dHJhbCBTb3V0aCBBbWVyaWO=
YS4gU2hlIHdhcyBhIGRlYWxlciBpbiBkb2xscywgYW5kIG==
aGVyIGxldHRlcnMgZGlzY3Vzc2VkIGhvdyBtYW55IG9mIHRoaXMgb3IgdGhhdCBkb2xs
IHRvIHNoaXAuIFRoZSBzdGVnb3RleHQgd2FzIHRoZSBkb2xsIG9yZGVycywgd2hpbGUgdGhl
IGNvbmNlYWxlZCAicGxhaW50ZXh0IiB3YXMgaXRzZWxmIGVuY2+=
ZGVkIGFuZCBnYXZlIGluZm9ybWF0aW9uIGFib3V0IHNoaXAgbW92ZW1lbnRzLF==
IGV0Yy4gSGVyIGNhc2UgYmVjYW1lIHNvbWV3aGF0IGZh
bW91cyBhbmQgc2hlIGJlY2FtZSBrbm93biBhcyB0aGX=
IERvbGwgV29tYW4uDQoqIENvbGQgV2FyIGNvdW50
ZXItcHJvcGFnYW5kYS4gSW4gMTk2OCwgY3JldyBtZW1iZW==
cnMgb2YgdGhlIFVTUyBQdWVibG8gKEFHRVItMikgaW50ZWxsaWdlbmNlIHNoaXAgaGVsZCBhcyBwcm==
aXNvbmVycyBieSBOb3J0aCBLb3JlYSwgY29tbXVuaWNhdGVkIGluIHNpZ25=
IGxhbmd1YWdlIGR1cmluZyBzdGFnZWQgcGhvdG8gb3Bwb3J0
dW5pdGllcywgaW5mb3JtaW5nIHRoZSBVbml0ZWQgU3RhdGVzIHRoZXkg
d2VyZSBub3QgZGVmZWN0b3JzIGJ1dCByYXRoZXIgd2VyZSBiZWluZyBoZWxkIGNh
cHRpdmUgYnkgdGhlIE5vcnRoIEtvcmVhbnMuIEluIG90aGVyIHBob3Rv
cyBwcmVzZW50ZWQgdG8gdGhlIFVTLCBjcmV3IG1lbWJlcnMgZ2F2ZSAidGhlIGZpbmdlciIgdG8g
dGhlIHVuc3VzcGVjdGluZyBOb3J0aCBLb3JlYW5zLCBpbiBhbiBhdHRlbXB0IHRvIE==
ZGlzY3JlZGl0IHBob3RvcyB0aGF0IHNob3dlZCB0aGVtIHNtaQ==
bGluZyBhbmQgY29tZm9ydGFibGUuDQoNCi0tDQpodHRwOi8vZW4ud2lraXBlZGlhLm9yZw==
L3dpa2kvU3RlZ2Fub2dyYXBoeQ0K
很明显就是base64编码,解码以后:
┌──(kali㉿kali)-[~/Desktop]
└─$ base64 -d stego.txt
Steganography is the art and science of writing hidden messages in such a way that no one, apart from the sender and intended recipient, suspects the existence of the message, a form of security through obscurity. The word steganography is of Greek origin and means "concealed writing" from the Greek words steganos meaning "covered or protected", and graphein meaning "to write". The first recorded use of the term was in 1499 by Johannes Trithemius in his Steganographia, a treatise on cryptography and steganography disguised as a book on magic. Generally, messages will appear to be something else: images, articles, shopping lists, or some other covertext and, classically, the hidden message may be in invisible ink between the visible lines of a private letter.
The advantage of steganography, over cryptography alone, is that messages do not attract attention to themselves. Plainly visible encrypted messages�no matter how unbreakable�will arouse suspicion, and may in themselves be incriminating in countries where encryption is illegal. Therefore, whereas cryptography protects the contents of a message, steganography can be said to protect both messages and communicating parties.
Steganography includes the concealment of information within computer files. In digital steganography, electronic communications may include steganographic coding inside of a transport layer, such as a document file, image file, program or protocol. Media files are ideal for steganographic transmission because of their large size. As a simple example, a sender might start with an innocuous image file and adjust the color of every 100th pixel to correspond to a letter in the alphabet, a change so subtle that someone not specifically looking for it is unlikely to notice it.
The first recorded uses of steganography can be traced back to 440 BC when Herodotus mentions two examples of steganography in The Histories of Herodotus. Demaratus sent a warning about a forthcoming attack to Greece by writing it directly on the wooden backing of a wax tablet before applying its beeswax surface. Wax tablets were in common use then as reusable writing surfaces, sometimes used for shorthand. Another ancient example is that of Histiaeus, who shaved the head of his most trusted slave and tattooed a message on it. After his hair had grown the message was hidden. The purpose was to instigate a revolt against the Persians.
Steganography has been widely used, including in recent historical times and the present day. Possible permutations are endless and known examples include:
* Hidden messages within wax tablets: in ancient Greece, people wrote messages on the wood, then covered it with wax upon which an innocent covering message was written.
* Hidden messages on messenger's body: also used in ancient Greece. Herodotus tells the story of a message tattooed on a slave's shaved head, hidden by the growth of his hair, and exposed by shaving his head again. The message allegedly carried a warning to Greece about Persian invasion plans. This method has obvious drawbacks, such as delayed transmission while waiting for the slave's hair to grow, and the restrictions on the number and size of messages that can be encoded on one person's scalp.
* In WWII, the French Resistance sent some messages written on the backs of couriers using invisible ink.
* Hidden messages on paper written in secret inks, under other messages or on the blank parts of other messages.
* Messages written in Morse code on knitting yarn and then knitted into a piece of clothing worn by a courier.
* Messages written on the back of postage stamps.
* During and after World War II, espionage agents used photographically produced microdots to send information back and forth. Microdots were typically minute, approximately less than the size of the period produced by a typewriter. WWII microdots needed to be embedded in the paper and covered with an adhesive (such as collodion). This was reflective and thus detectable by viewing against glancing light. Alternative techniques included inserting microdots into slits cut into the edge of post cards.
* During World War II, a spy for Japan in New York City, Velvalee Dickinson, sent information to accommodation addresses in neutral South America. She was a dealer in dolls, and her letters discussed how many of this or that doll to ship. The stegotext was the doll orders, while the concealed "plaintext" was itself encoded and gave information about ship movements, etc. Her case became somewhat famous and she became known as the Doll Woman.
* Cold War counter-propaganda. In 1968, crew members of the USS Pueblo (AGER-2) intelligence ship held as prisoners by North Korea, communicated in sign language during staged photo opportunities, informing the United States they were not defectors but rather were being held captive by the North Koreans. In other photos presented to the US, crew members gave "the finger" to the unsuspecting North Koreans, in an attempt to discredit photos that showed them smiling and comfortable.
--
http://en.wikipedia.org/wiki/Steganography企图在一堆英文中找到flag,然并卵,上面解密出来的其实是一段关于隐写术(Steganography)的介绍,可以看出剩下的就是base64隐写。
入山梵行 师傅给出的脚本如下:(其他很多wp里给出的脚本无法在我电脑内正常运行,感谢师傅的脚本)
import base64
b64chars = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/'#参考注释1
with open('1.txt', 'rb') as f:
bin_str = ''
for line in f.readlines():
stegb64 = str(line, "utf-8").strip("\r\n")#参考注释2
rowb64 = str(base64.b64encode(base64.b64decode(stegb64)), "utf-8").strip("\r\n")#参考注释3
equalnum = stegb64.count('=')
if equalnum:#参考注释4
offset = abs(b64chars.index(stegb64.replace('=','')[-1])-b64chars.index(rowb64.replace('=','')[-1]))#参考注释5
bin_str += bin(offset)[2:].zfill(equalnum * 2)
print(''.join([chr(int(bin_str[i:i + 8], 2)) for i in range(0, len(bin_str), 8)]))
#注释正文:
#1.在这一行我们的工作就是简单的做一个base64的参照表,后面会解释作用。
#2.这里我想说一下我踩的坑,我第一次写这段代码的时候,并没有写'\r'我只写了’\n‘但是后来我发现输出的时候好像还是有回车,于是就又加了一个(但是据说好像用默认,两个就都删?(混乱
#3.要加“utf-8”不加会报错
#4.刚刚从我们的分析过程中可以看到,如果在一串base64编码的字符串中,没有等号是不可能隐藏数据的,所以这里要判断一下
#5.这里要算一下偏移量,可能就这么说偏移量大家可能不是很懂,我就用简单通俗的话来讲吧。如果咱们不去隐写数据的话,最后补位的一定全是零,那么用咱们得到的隐写数据的二进制减去那些补位是零的二进制数据(他们两个的头部都是从前面继承的),那么就会得到咱们隐写进去的非零二进制数据。
#原文链接:https://blog.csdn.net/Mrs_H/article/details/108514352运行该脚本,可得到flag:
~~~~~
Base_sixty_four_point_fiv↓
Base_sixty_four_point_fiv↓
Base_sixty_four_point_fiv↓
Base_sixty_four_point_five
Base_sixty_four_point_five
Base_sixty_four_point_five
Base_sixty_four_point_five我们也可以使用github上大佬给出的脚本
usage: b64steg.py [-h] [-f FILE] [-s SAVE]
optional arguments: -h, --help show this help message and exit -f FILE, --file FILE Chose input file -s SAVE, --save SAVE Save the result(optional)
012 功夫再高也怕菜刀

打开附件可以看到,是一个pacpng文件,用文本文档打开全都是乱码,搜一下可以看到这是wireshark保存下来的数据流量包。
压缩包有密码,接下来咱们直接爆破

可以看到

但是解压需要密码,这道题应该就是需要让我们根据流量包求压缩密码。
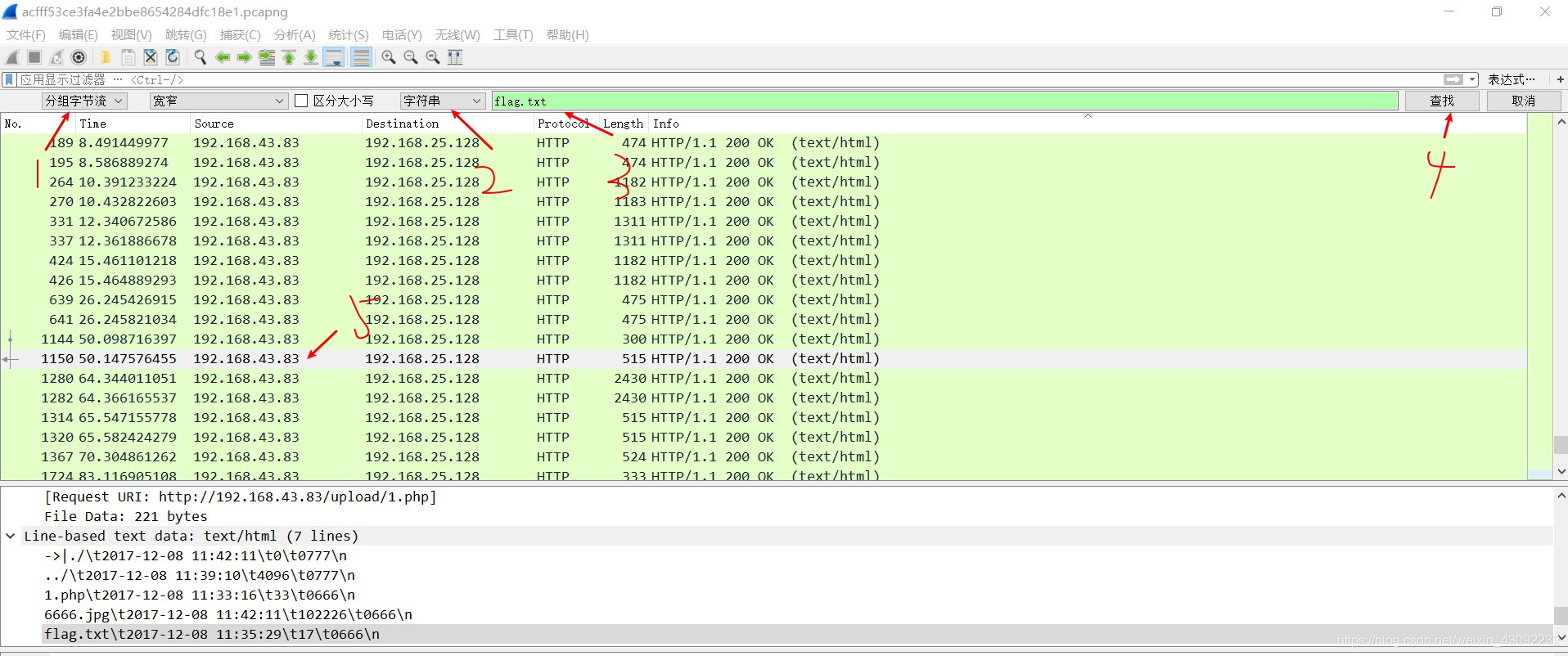
打开wireshark,搜索flag文件:
注意此处有坑:
按照上面的配置结果,可以发现有一个6666.jpg文件很可疑,追踪一下TCP流,找一下FFD8FF以及FFD8因为FFD8FF是jpg文件的文件头!
然后将这两者之间的部分(包括这两个在内)复制粘贴到一个新的winhex文件内



导入后,进行保存,修改后缀名为.png,则:

解压密码就是这个,进行解压即可得到flag!
┌──(kali㉿kali)-[~/Desktop/output/zip]
└─$ unzip 00002778.zip
Archive: 00002778.zip
well,you need passwd!
[00002778.zip] flag.txt password:
extracting: flag.txt
┌──(kali㉿kali)-[~/Desktop/output/zip]
└─$ ls
00002778.zip flag.txt
┌──(kali㉿kali)-[~/Desktop/output/zip]
└─$ cat flag.txt
flag{3OpWdJ-JP6FzK-koCMAK-VkfWBq-75Un2z} kali牛批!!